OmniPeek知识讲解
omnipeek过滤命令

omnipeek过滤命令
Omnipeek是一款网络分析软件,它可以帮助用户深入了解网络通信并解决网络问题。
为了方便用户进行数据过滤,Omnipeek提供了多种过滤命令。
1. 简单过滤
Omnipeek支持使用IP地址、端口号、协议类型等简单过滤条件进行数据过滤。
例如,可以使用以下命令过滤HTTP协议的数据包: proto http
2. 复合过滤
除了简单过滤条件外,Omnipeek还支持使用复合过滤条件进行数据过滤。
例如,可以使用以下命令过滤源IP地址为192.168.0.1的HTTP协议数据包:
ip.src == 192.168.0.1 && proto http
3. 正则表达式过滤
如果需要使用更灵活的过滤条件,Omnipeek也支持使用正则表达式进行数据过滤。
例如,可以使用以下命令过滤以GET开头的HTTP 请求:
http.request matches '^GET'
4. 统计过滤
Omnipeek还支持使用数据统计结果进行过滤。
例如,可以使用以下命令过滤数据包数量大于1000的IP地址:
ip.addr count > 1000
以上是Omnipeek的一些过滤命令,用户可以根据自己的需求选择合适的命令进行数据过滤。
PEEK应用及知识

乙二醇酯
Commodity
Polymers 普通塑料
PP 聚丙烯
PVC 聚氯乙烯
PE 聚乙烯
德国赛尔
武汉飞腾亚化工新材料有限公司
产品型号
FD-PEEK 封端聚醚醚酮——两大类、三大牌号、六大系列、52个品类
FC
GL
P
G
PF
CA
德国赛尔
武汉飞腾亚化工新材料有限公司
加工成型
挤出
模压
喷涂
注塑
优良的加工性能,多种加工成型方式
座椅系统 轴承衬套 插塞 齿轮 线缆保护
传动系统 止推垫圈 轴承衬套 密封环 垫圈
制动系统 止推垫圈 轴承衬套 阀体 活塞
德国赛尔
配重齿轮
发动机系统
武汉飞腾亚化工新材料有限公司
油泵齿轮
内齿轮
涡轮充电器叶轮
气缸垫圈
德国赛尔
武汉飞腾亚化工新材料有限公司
发动机系统-真空泵
真空泵
叶片
叶片
叶片
叶片
德国赛尔
密封领域
压缩机阀片
密封环 密封领域应用案例
密封套垫
德国赛尔
涂覆领域
弯头内外壁
其他领域
耐高温高压 耐化学腐蚀 电性能 耐磨损 耐候性 耐水解
武汉飞腾亚化工新材料有限公司 3D打印领域
新能源领域 特种电缆包覆线
3D打印机喷嘴支架
德国赛尔
汽车市场
汽车制造发展趋势 环保 更高的系统化要求 降低成本 降低噪音 安全标准提高 能源问题 电子产品增加
ZYPEEK优点 耐压力40 -> 15 N/cm 高抗冲击 成本降低 噪声降低
德国赛尔
武汉飞腾亚化工新材料有限公司
PEEK聚醚醚酮详解汇总总结

聚醚醚酮是继聚四氟乙烯(PTFE它与PTFE相比,承载能力和耐磨性能都有很大的提高,可在无润滑。
低速高载下,或在液体、固体粉尘污染等恶劣环境下使用,1.耐热性:高耐高温热塑性树脂,熔点334 ℃(与PTFE相似).PEEK棒聚醚醚酮棒耐高温性能:玻璃化温度高达151C,熔点为348C,经GF或CF填充后,热变形温度高达326C以上,美国UL认可的长期使用温度为260℃2.柔韧性:目前市售耐高温树脂中名列前茅,优于聚酰亚胺和二苯醚树脂3.阻燃性:UL940V-0级自燃性,低发烟.PEEK棒聚醚醚酮棒阻燃性和低发烟性:不需要添加其他的阻燃成分即具有阻燃的特性,1.45mm厚度的试样即可以达到UL-94 V0的标准,而且发烟量明显低于其他品种的树脂。
4.耐药性:只溶于浓硫酸.除了高浓度浓硫酸等强氧化性酸的侵蚀,具有近似于PTFE树脂的耐化学品性,而且在各种化学试剂中能够完整地保留其机械性能,是极为优异的抗腐蚀材料。
5.加工成型性:流动性好便于二次加工,可以采用注塑成型工艺直接加工出零件。
可进行车削、铣、钻孔、攻丝、粘接及超声波焊接等后加工。
6.优异的机械性能:是所有的树脂中韧性和刚性结合最完美的材料,其强度和耐疲劳性甚至优于一些金属和合金材料。
7.耐水解性:在高温蒸汽和热水中长期浸泡仍能够保持良好的机械性能,是所有树脂中抗水解性能最好的品种。
8.尺寸稳定性:具有极低的吸水率和线性热膨胀系数,其制品在各种应用环境下有优异的尺寸稳定性。
9.电性能和绝缘性能:在高温、高压、高速、高湿等环境下仍然具有优异的绝缘性和稳定的电性能。
10.耐辐照和耐侯性:对各种辐射具有优异的抵抗能力,可以经受高剂量的?、γ等射线的辐照并保持其各项特性,可以应用于各种恶劣环境。
11.高纯度、低挥发性和无毒性:PEEK棒聚醚醚酮棒树脂本身没有毒性,其分子结构非常稳定,不容易产生挥发物,还有抗辐射作用,提纯处理后的高纯度的树脂是优良的生化医疗材料。
OmniPeek_用户手册

OmniAnalysis™PlatformGetting Started GuideG e t t i n g S t a r t e d G u i d eCopyright © 2006, WildPackets, Inc. All rights reserved. Information in this document is subject to change withoutnotice. No part of this document may be reproduced or transmitted in any form, or by any means, electronic ormechanical, including photocopying, for any purpose, without the express written permission of WildPackets, Inc.AiroPeek SE, AiroPeek NX, AiroPeek VX, EtherPeek SE, EtherPeek NX, EtherPeek VX, Gigabit Analyzer Card (GAC),GigaPeek NX, iNetTools, NAX, NetDoppler, NetSense, Network Calculator, Omni³, Omni Capture Engine, OmniDesktop Engine, Omni DNX Engine, OmniEngine Desktop, OmniEngine Enterprise, OmniEngine Workgroup,Omni Management Console, Omni PacketGrabber, OmniPeek, OmniPeek Enterprise, OmniPeek Enterprise Connect,OmniPeek Personal, OmniPeek Workgroup, OmniPeek Workgroup Pro, OmniPeek Personal, Omnipliance,OmniSpectrum, PacketGrabber, Peek DNX, ProConvert, ProtoSpecs, RFGrabber, RMONGrabber, WAN AnalyzerCard (WAC), WANPeek NX, WildPackets, WildPackets Academy, and WildPackets OmniAnalysis Platform aretrademarks of WildPackets, Inc. All other trademarks are the property of their respective holders.The material in this document is for information purposes only and is subject to change without notice. Whilereasonable efforts have been made in the preparation of this document to assure its accuracy, WildPackets, Inc.assumes no liability resulting from errors or omissions in this document, nor from the use of the informationcontained herein.WildPackets, Inc. reserves the right to make changes in the product design without reservation and withoutnotification to its users.Contacting WildPacketsMailing AddressWildPackets, Inc.1340 Treat Blvd., Suite 500Walnut Creek, CA 94597Voice/Fax8 AM - 5 PM (PST)(925) 937-3200(800) 466-2447 (US only)Fax: (925) 937-3211info@Salessales@WebTechnical Support/supportResourcesSee /support/additional_resources/white_papers for white papers, tutorials, technicalbriefs and more.iiT raining and CertificationWildPackets Academy offers the most effective and comprehensive network and protocol analysis training available, meeting the professional requirements of corporate, educational, government, and private network managers. Our instructional methodology is centered on practical applications of protocol analysis techniques.See /services for course catalog, current public course scheduling, web-delivered courses,and consulting services.WildPackets Academy(800) 466-2447training@Product Support and MaintenanceWildPackets Product Maintenance Programs ensure that you grow along with our products as new features and enhancements to existing features are added. All WildPackets customers are entitled to technical support for the life oftheir purchased product(s).Enhanced support services are available through our Premium Maintenance Programs. Premium Maintenance offers Remote Trace File Analysis assistance and free seats in our WildPackets Academy Training courses, in addition to our standard maintenance services.Standard or Premium Maintenance can be purchased by contacting sales@.About WildPackets, Inc.Since 1990, WildPackets has been delivering real-time fault analysis solutions that enable the world's leading organizations to keep their networks running securely and reliably, day after day. From the desktop to the datacenter,from wireless LANs to Gigabyte backbones, on local segments and across distributed networks, WildPackets products enable IT organizations to quickly find and fix problems affecting mission-critical network services. WildPackets products are sold in over 60 countries through a broad network of channel and strategic partners. More than 5,000 customers, spanning all industrial sectors and including 80% of the Fortune 1000, use WildPackets products daily to troubleshoot networks and maximize network uptime. WildPackets customers include Agilent, Cisco Systems, Comcast, EDS, Microsoft, Siemens AG, Qualcomm, Unisys, Motorola, and Deutsche Bank. Strategic partners include Aruba, Atheros, Cisco, 3Com, Intel and Symbol Technologies. For further information, please visit.20060410-E-OP40_d4iiiContentsChapter 1Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1System requirements. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1Installing the OmniPeek console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3Installing an OmniEngine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3Main program window and Start Page. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4Displaying the Remote Engines window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5Connecting to a remote engine. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 Chapter 2Capturing Packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11Capturing packets into a Capture window. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11Capturing packets on a remote engine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14 Chapter 3Viewing Decoded Packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17The packet decode window. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17 Chapter 4Forensics Analysis . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21Creating forensic captures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21Using the remote engine files tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23 Chapter 5Monitoring the Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27Displaying Monitor statistics on the console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28Baselining with summary statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29Using the remote monitoring capture template . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31 Chapter 6Creating Graphs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33Creating a graph from a console Capture window. . . . . . . . . . . . . . . . . . . . . . . . . . . 33Creating a top ten protocols graph on a remote engine. . . . . . . . . . . . . . . . . . . . . . . 35 Chapter 7Wireless Statistics in Capture Windows . . . . . . . . . . . . . . . . . . 37The WLAN view . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37The Channels view . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39The Signal view . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40vContentsvi Chapter 8Troubleshooting with the Expert . . . . . . . . . . . . . . . . . . . . . . . . 41 The Expert view. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .41Using the Expert EventFinder Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42Using the Visual Expert . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43 Chapter 9Creating Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47 Enabling a filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47Creating filters with the Make Filter command. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48Creating a simple filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49 Chapter 10Using the Peer Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51 The Peer Map view . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51 Chapter 11Using VoIP Analysis . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55 The V oIP view . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55Analyzing a single call or channel. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57 Appendix A Keyboard Shortcuts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61 Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63C H A P T E R1 IntroductionWelcome to OmniPeek, the software console for distributed network analysis fromWildPackets!The OmniPeek console provides centralized expert analysis for 10/100 Ethernet, full-duplexGigabit Ethernet, 802.11 WLAN, and WAN networks by managing and interacting withremotely installed OmniEngines. With OmniPeek’s intuitive user interface, network engineerscan quickly troubleshoot problems on remote segments, drill down through multiple layers ofanalysis, and pinpoint problems that need correction.Important!The OmniPeek console and the OmniEngines are described here in their full-featuredversions. Please visit our web site at for details about how toorder the Omni features and media types that precisely fit the needs of your distributednetwork.System requirementsThe system requirements for the OmniPeek console are:●Windows XP Professional (SP2), Windows 2000 (SP4) or Windows Server 2003 (SP1)●Internet Explorer 6.0 (SP1)●Microsoft .NET Framework 2.0Note OmniPeek with Enhanced Voice Option does not support Windows Server 2003.OmniPeek supports most rack mount, desktop and portable computers as long as the basicsystem requirements to run the supported operating systems are met. Depending on trafficand the particular usage of OmniPeek, the requirements may be substantially higher.The following system is recommended for OmniPeek:1Chapter 1: Introduction 2System requirements●P4 2 GHz Processor (P4 2.4 GHz Processor for OmniPeek with Enhanced Voice Analysis)●512 MB RAM (1 GB RAM for OmniPeek with Enhanced Voice Analysis)●10 GB Available Hard Disk Space (20 GB Available Hard Disk Space for OmniPeek withEnhanced Voice Analysis)Factors that contribute towards superior performance include high speed CPU, dual CPUs, two or more GB of RAM, high performance disk storage subsystem (RAID 0), and as much additional hard disk space as is required to save the trace files that you plan to manage.Note Supported operating systems require users to have “Administrator” level privileges in order toload and unload device drivers, or to select a network adapter for the program’s use incapturing packets.For more information, please see our web site at /products.Optional hardware requirementsTo analyze wireless, Gigabit, WAN, or traffic, a supported network analyzer card (GAC orWAC) or wireless LAN adapter is required for OmniPeek:●Full-duplex capture of Gigabit Ethernet networks : requires a WildPackets GigabitAnalyzer Card (GAC).Note Capture on Gigabit Ethernet networks is also possible using other supported Gigabit Ethernetinterfaces, but not in full-duplex mode.●Capture from T1/E1 WAN links : requires a WildPackets WAN Analyzer Card (WAC).●Capture from T3/E3 WAN links : requires a WildPackets WAN Analyzer Card (WAC).For more information, refer to the documentation that ships with the product or visit ourwebsite at /products .For information on configuring wireless, Gigabit, and WAN analyzer cards, please refer to the OmniPeek User Guide or online help.Network connectivity and driversOmniPeek and the OmniEngines communicate over TCP/IP through port 6367, the default port for the WildPackets DNX proprietary protocol.OmniPeek Getting Started Guide WildPackets has developed a set of driver APIs for 802.11 WLAN cards, the Gigabit AnalyzerCards, and the WAN Analyzer Cards. OmniPeek and the OmniEngines ship with a number ofdrivers that support the WildPackets APIs.For the most recent information on network adapter cards and drivers, please visit http:///support/product_support/overview.Installing the OmniPeek consoleTo install the OmniPeek console, follow these steps:1.Uninstall any earlier versions of OmniPeek.2.Insert the OmniPeek Installer CD into your CD or DVD drive.3.Follow the installation instructions that appear on the screen.During installation you are asked to enter a valid Activation Key. When prompted, youcan select Automatic or Manual:●Automatic: The installer uses your Internet connection to send an encrypted messageto an activation server, which retrieves and displays your Activation Key. Please writedown the Activation Key for future reference.●Manual: The installer allows you to enter the Activation Key manually. You canobtain an Activation Key in the following ways: Go to a computer with an Internetconnection and web browser and complete the request form, or call WildPacketsTechnical Support.For more information about the product activation process, please see our website at:/activation.4.When the Installer has finished installing the program files, you can choose to view theReadme or launch the program.Installing an OmniEngineFor complete instructions on how to install, configure, and update settings for anOmniEngine, See the Getting Started Guide that ships with the OmniEngine or the online helpin the Omni Management Console application.Installing the OmniPeek console3Chapter 1: Introduction4Main program window and Start Page Main program window and Start PageTo start OmniPeek:●Choose Start > All Programs > WildPackets OmniPeek .The main program window and Start Page appears. The parts of the main program window are described below.●T oolbar: Provides icons for frequently-used tasks in OmniPeek. The function of each iconappears at a tooltip. Choose View > Toolbars > Show Toolbars to toggle the display of the icons in this toolbar.●Status Bar: Shows brief context-sensitive messages on the left and the current monitoradapter on the right. Choose View > Status Bar under the menu to toggle the display of this status bar.●Start Page: Provides links to useful resources, both local and online. You can:●open recently saved Capture files (click Open Capture File button)●start a new OmniPeek console capture (click New Capture button)ToolbarStatus BarOmniPeek Getting Started Guide●start a new remote engine capture (click View Remote Engines button)●view the Readme file●open the HTML version of the Getting Started Guide●open PDF versions of related hardware documents●access online resources and technical support●Network Statistics Gauge:Shows network utilization as analog dials with correspondingdigital displays. Choose Monitor > Network to display.●OmniPeek Log: Records Start, Stop, and other OmniPeek events. Choose View > Log todisplay.Displaying the Remote Engines windowThe Remote Engines window is used for interaction between the OmniPeek console and theOmniEngines. The Remote Engine window allows you to perform many of the sameoperations on a remote engine that you can perform locally with OmniPeek.Do one of the following to display the Remote Engines window:●Choose View > Remote Engines.●Click the View Remote Engines button on the Start Page.The Remote Engines window appears.Insert Engine Discover EngineInsert Group DeleteConnectDisconnectDisplaying the Remote Engines window5Chapter 1: Introduction6Connecting to a remote engineConnecting to a remote engineIn order to view packets and data from a remote engine, you must first connect to the engine from the Remote Engines window.To connect to a remote engine:1.From the Remote Engines window, click the Insert Engine icon. The Connect dialogappears.plete the dialog:●Host: Enter the IP address of the OmniEngine that you want to connect to.●Port: Enter the TCP/IP Port used for communications. Port 6367 is the default portfor the WildPackets OmniEngine.●Authentication: Select the method used to authenticate the user. Typically, you wouldselect Default if you don’t use a third-party authentication server.●Domain: Type the Domain for login to the remote engine. If the remote engine is not a member of any Domain, leave this field blank.●Username: Type the Username for login to the remote engine.●Password: Type the Password for login to the remote engine.3.Click Connect . When the connection is established, the remote engine appears in theRemote Engines window.Connecting to a remote engine 7OmniPeek Getting Started GuideTip You can add multiple OmniEngines to the Remote Engines window by using the InsertEngine icon.4.Click the Insert Group icon to add a group of engines to the Remote Engines window.5.Select the engine group and click Insert Engine to add an engine to the group.Chapter 1: Introduction8Connecting to a remote engineDiscover OmniEnginesWhen you click the Discover button in the Remote Engines window, the Discover Engines dialog appears. This dialog lets you search for OmniEngines installed on the network. You can then select the specific OmniEngines that you want to display in the Remote Engines window.●Engines: Displays the OmniEngines found on the network. Select the check box of theOmniEngine that you want to display in the Remote Engines window.●Discover: Click to search for OmniEngines installed on the local segment of yournetwork. The box on the right will change from Listening... to Finished when all network-available OmniEngines are discovered.●Advanced Settings:●Listen time: Enter the number of seconds that the OMC will listen for responses tothe discovery request. You can enter a minimum of 2 and a maximum of 30 seconds.●Device backoff time: Enter the number of seconds that the devices will wait beforeresponding to a Discover request. The Device backoff time should always be less thanthe listen time. You can enter a minimum of 0 and a maximum of 10 seconds.Discover OmniEngines 9OmniPeek Getting Started GuideNote You will need to select an engine in the Remote Engines window and connect to it beforecapturing packets and analyzing data.Chapter 1: Introduction10Connecting to a remote engineC H A P T E R211Capturing Packets Packets are the units of data carried on the network and the basis for all higher level network analysis. The Packets view of a Capture window is where you can view information about the individual packets transmitted on your network.OmniPeek and the OmniEngines can capture packets in multiple configurable Capture windows, each with its own dedicated capture buffer and settings for filters, triggers, and statistics output. You can establish and view multiple Capture windows up to the limits of available system resources.Capture windows allow you to:●View and monitor network traffic in real time ●Use a different adapter for each Capture window, or use the same adapter for multiple Capture windows●Apply filters, both before and after capture●Start or stop capture based on network events or time settings●View statistics based on selected network traffic●View packet contents, raw and/or decoded●Save packets for post-capture analysis in Capture file windows Capturing packets into a Capture window Note For remote capture, see Capturing packets on a remote engine on page 14.To capture packets:1.To start a new capture, do one of the following:●Click the New Capture button on the Start Page ●Choose File > New…Chapter 2: Capturing Packets12Capturing packets into a Capture windowThe General view of the Capture Options dialog appears.2.Configure the options in the General view.3.Click the Adapter view to select the capture adapter.Note For information on configuring settings in the other views of the Capture Options dialog, seethe OmniPeek User Guide or online help.4.Click OK . A new Capture window appears.Capture window titleSave to disk options Continuous capture optionsPacket slicing optionsCapture buffer size“Show this dialog...”Capturing packets into a Capture window 13OmniPeek Getting Started Guide5.Click Start Capture to begin capturing packets. The Start Capture button changes to theStop Capture button and packets begin populating the Capture window.Note You can right-click a column heading to hide or display available column headings in thePackets tab.6.Click Stop Capture when you want to stop capturing packets.Start/Stop CaptureChapter 2: Capturing Packets14Capturing packets on a remote engine Tip To resume capturing from where you left off, hold down the Shift key and click the StartCapture button. To empty the capture buffer and start a new capture, simply click the Start Capture button again.Capturing packets on a remote engineTo capture packets on a remote engine, you must first be connected to a remote engine in the Remote Engines window. Please see Connecting to a remote engine on page 6.To capture packets on a remote engine:1.Select New Capture under Captures on the Home tab.Tip You can also click the Insert icon on the Captures tab, or select New Capture under the nameof the adapter you wish to use on the Adapters tab.The General view of the remote Capture Options dialog appears.2.Configure the options in the General view.3.Select an adapter in the Adapter view.Capture window titleSave to disk options Continuous captureoptionsPacket slicing optionsCapture buffer sizeSave as templateOpen capture windowStart capture immediatelyCapturing packets on a remote engine 15OmniPeek Getting Started GuideNote For information on configuring settings in the other views of the Capture Options dialog,please see the OmniPeek User Guide or online help.4.Click OK . A new remote engine Capture window appears.5.Click Start Capture to begin capturing packets. The Start Capture button changes toStop Capture and packets begin populating the capture window.Tip You can right-click a column heading to hide or display available column headings in thePackets view.6.Click Stop Capture when you want to stop collecting packets into the remote capturebuffer.Chapter 2: Capturing PacketsFor instructions about using the Forensics Capture template, see Creating forensic captures onpage 21. For instructions about using the Monitoring Capture template, see Using the remotemonitoring capture template on page 31.Note Users without permission to create or modify remote engine Capture windows will find features grayed out, missing, or receive an error message indicating the task is not allowed. Fordetails, see the OmniEngine Getting Started Guide or the online help in the OmniManagement Console application.16Capturing packets on a remote engineC H A P T E R317Viewing Decoded Packets Network problems are revealed more quickly by looking at the detailed information contained in individual packets. Looking into the packets can help you troubleshoot your network, track down a security breach, or examine protocol structure and compliance.The packet decode windowYou can view detailed information about each packet by viewing the packet’s decode.To view the decode of a packet:1.Double-click a packet in the Packets view of a Capture window. The Packet Decode window appears. The decoded packet data is presented in byte order from top to bottom.Window navigationDecoder options Information addedby OmniPeekWindow header Decode viewHex andASCII viewOffsetsChapter 3: Viewing Decoded Packets 18The packet decode windowTip You can open individual Packet Decode windows for up to 10 packets at once. When multiplepackets are selected in the active Packet List, click Enter to open them all.2.Click on the - minus or + plus signs in the margin to collapse or expand the view of anyheader section.●Window header:●Click the Decode Previous or Decode Next buttons at the top of the window tostep through the packets shown in the Packet List of the active Capture window.●Decode view:●The items in green at the top of the Decode view include information on theFlags , Status , Packet Length , and Timestamp of the packet. This information isnot in the packet itself, but is added by OmniPeek.●The body of the Decode view is laid out in the same order as it appears in thepacket. A quick glance at this section often reveals the source of trouble.Problems like a misconfigured client, or incompatible versions of the sameprotocol from different vendors can be easily understood when you can see andcompare the packets themselves. ●Hexadecimal view:●The Hex view at the bottom of the decode window shows the offset of the firstcharacter in each line, the raw packet data in hex, and the ASCII version of rawpacket data3.Highlight an item in one part of the window. The same bytes of the packet are highlightedin all the other views or panes as well. The highlight matches in the Decode, Hex, andASCII panes.Color coding is used to link the Decode view with the Hex view for both Hex and itsASCII equivalent. The Hex and ASCII views are in turn linked to the color of the protocol shown in the Protocols column of the Packet List.Tip Right-click and choose Show Colors to toggle display of colors.The packet decode window 19OmniPeek Getting Started GuideTip Use the Toggle Orientation icon in the toolbar to tile the Decode and Hex views vertically orhorizontally.Toggle OrientationHighlights match:DecodeHexASCIIChapter 3: Viewing Decoded Packets 20The packet decode windowC H A P T E R4 Forensics AnalysisData reduction is the key to network forensics. Using the remote engine Files tab, you canselect one or more Capture files on the remote engine and search them for the specific datayou wish to analyze.Creating forensic capturesOn a remote engine, you can create a new Capture window based on a pre-defined ForensicsCapture template configured with capture settings optimized for post capture forensicanalysis.Forensics captures are saved automatically to the OmniEngine. Their filenames are listed inthe Dashboard view of Capture windows and in the remote engine Files tab. From the Filestab, you can refine your search by start time, end time, any available filter, and specify whichCapture window views you want to display for further analysis.To start a Forensics Capture:1.On the Home tab, select New Forensics Capture under New Capture. The remoteCapture Options dialog appears with settings configured for a Forensics Capture, such asContinuous capture with save to disk.2.Click the Adapters view and select an adapter for the capture.3.Click the Performance view. Notice that all of the statistics are disabled in order tooptimize packet capture to disk.4.Click OK. A remote engine Capture window appears with capture already under way.5.Click the Dashboard view. The Files area displays the list of files saved to theOmniEngine computer as the user-defined buffer fills.21。
omnipeek 解析

omnipeek 解析Omnipeek是一种网络分析工具,它提供了全面而强大的功能,可以帮助用户解析网络数据包,识别网络问题,并提供有效的解决方案。
Omnipeek具有强大的数据包捕获和分析功能。
它能够捕获网络流量中的各种数据包,并对其进行深入分析。
用户可以通过查看捕获的数据包来了解网络中发生的事情,比如查看网络连接、查找异常流量、监控网络性能等。
此外,Omnipeek还可以对捕获的数据包进行解码,以便用户更好地理解其中的信息。
Omnipeek提供了丰富的网络分析功能。
用户可以利用Omnipeek 来进行网络流量统计分析,例如查看网络流量的来源和目的地,分析流量的协议分布等。
此外,Omnipeek还支持对网络流量进行过滤和搜索,用户可以根据自己的需求设置过滤条件,以便只关注特定的网络流量。
这些功能使得用户能够更好地理解网络中的数据流动情况,发现潜在的问题。
Omnipeek还具有强大的网络故障诊断功能。
当网络出现问题时,用户可以利用Omnipeek来识别问题的根源。
Omnipeek可以通过分析网络流量和数据包,找到网络中的瓶颈、延迟、丢包等问题,并提供相应的解决方案。
用户可以根据Omnipeek提供的信息来优化网络配置,改善网络性能。
Omnipeek还支持对无线网络进行分析。
它可以捕获和解码无线网络中的数据包,帮助用户了解无线网络的连接状态、信号强度、数据传输速率等。
用户可以利用Omnipeek来查找无线网络中的干扰源,优化无线网络的覆盖范围和性能。
除了上述功能,Omnipeek还具有其他一些特性。
例如,它支持多种操作系统,包括Windows和macOS等。
此外,Omnipeek还提供了直观易用的用户界面,使得用户能够方便地进行网络分析工作。
用户可以通过图形化界面来查看和分析网络数据包,而无需编写复杂的命令。
Omnipeek是一种强大的网络分析工具,它具有全面而强大的功能,可以帮助用户解析网络数据包,识别网络问题,并提供有效的解决方案。
聚醚知识 ppt课件

H2 CH O C
CH3
CH OK +
CH2 O CH2 CH OK CH3
CH3
n-1H2C CH
O
CH3
CH2 O CH2 CH2 OK
H2 CH3 n
CH O C
CH OK
n
CH2 O CH2 CH
OK
n
CH3
链转移
根据以上反应历程,当无外加终止剂时,往往链增长不会 终止,始终具有活性聚合物的特性,但事实上,在KOH 催化剂下,聚醚多元醇的分子量很难达到10000.这是由 于
以山梨醇、甘露醇等六羟基化合物为起始剂与氧化丙烯及在KOH 催化 剂作用下,100~110℃加压聚合,可得六羟基聚醚。这类聚醚因含有六 个羟基,官能度高,所以制得的聚氨酯硬泡交联度大,制品的耐油性、 耐热氧化性及尺寸稳定性均较好。我国有丰富的山梨醇、甘露醇资源, 尤其甘露醇是海藻制碘工业中的一种联产品。六羟基聚醚由于官能度
2.聚醚反应机理
阴离子开环聚合机理一般认为: 环氧化物与碱金属氢氧化物 或其醇盐作用产生了醇盐阴离子引发聚合, 该阴离子段通过 与单体分子的连续开环反应不断增长成聚合物链。环氧化物 的阴离子聚合反应具有活性阴离子聚合的特点, 通常不发生 终止反应。连续加入不同的环氧单体, 形成嵌端共聚物; 加入 混合单体, 形成无规共聚物。
4.五羟基聚醚 五羟基聚氧化丙烯醚也有二种,一种是以二亚乙基三胺(二乙烯三胺)为
起始剂,与氧化丙烯聚合生成五羟基含氮聚醚,具有自催化作用;另一 种是以含五个羟基的木糖醇为起始剂,经催化与氧化丙烯聚合,生成五 羟基聚醚。这二种聚醚均适用于硬质聚氨酯泡沫塑料。由于五羟基聚醚 的粘度大,实际生产中,一般把五官能度起始剂与低官能度起始剂混合 ,制备官能度在3~5 之间的聚醚多元醇。二乙烯三胺基聚醚多元醇结构 中具有叔胺,所以可用于硬泡、半硬泡的具催化作用的交联剂,与三羟 基或四羟基等低官能度聚醚混合使用,可制得尺寸稳定、压缩强度较高 的硬泡,且特别适宜于现场喷涂发泡配方。木糖醇一般是通过农副产品 玉米芯等经水解、加氢,结晶提纯后所得,资源丰富,价廉。聚醚五醇 制得的硬泡具有比甘油、季戊四醇聚醚为基硬泡更高的耐温性和尺寸稳 定性。 5.高官能度聚醚
OmniPeek使用手册入门版
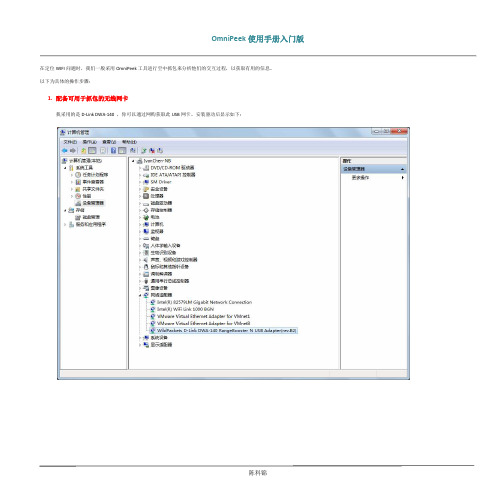
1. 配备可用于抓包的无线网卡
我采用的是 D-Link DWA-140 ,你可以通过网购获取此 USB 网卡。安装驱动后显示如下:
陈科锦
2. 启动抓包
完成网卡的驱动安装后,我就可以开始启动抓包工具进行空中抓包操作了。 OmniPeekFile New Capture ,跳出抓包选项框; 注意 Continuous capture 选勾,并根据需要选择是否要实时存储抓取的报文。
陈科锦omnipeek使用手册入门版在定位wifi问题时我们一般采用omnipeek工具进行空中抓包来分析他们的交互过程以获取有用的信息
OmniPeek 使用手册入门版
在定位 WIFI 问题时,我们一般采用 OmniPeek 工具进行空中抓包来分析他们的交互过程,以获取有用的信息。 以下为具体的操作步骤:
Filter 里面输入名字,选择以太网地址,并输入地址,然后点击 ok:
陈科锦
然后把这两项选勾:
最后重新回到 packets 页面点击 start capture 开始抓包。
4. 结尾 因空口抓包对应环境的特殊性,不一dapter 选择抓包用网卡:
陈科锦
如果你能够确定当前需要抓包的信道号的话,则点击 802.11,选择抓包用信道,否则用“Scan”:
点击确定,进入抓包页面,然后启动抓包:
陈科锦
3. MAC 地址过滤
如果在复杂的环境下做抓包,报文量会很大,所以我们可以增加特定的 AP 和特定的 STA 的 MAC 地址过滤,比如 AP MAC 地址为 00:11:22:33:44:55,而 STA MAC 为 50:44:33:22:11:00,则点击 filter 里面的 insert 来增加过滤选项:
WildPackets+OmniPeek+6.5安装

WildPackets OmniPeek 6.5 安装作为Omni企业网络分析平台的控制台软件,OmniPeek提供了直观易用的图形界面供工程师快速分析和解决企业网络故障。
OmniPeek对管理下的所有网络提供了集中专家分析,使用OmniPeek的直观界面,网络工程师即使是入门者也可以快速分析多个网段中的故障,深入多层次分析,指出问题所在。
安装前确认:1.保证PC未安装WildPackets OmniPeek 或者已卸载旧版本2.无线网卡是否支持WildPackets OmniPeek 6.5常用可支持网卡:ATHEROS 5212A、BROADCOM 430XMP、Cisco AIR-CB21AG、NEC WL54SCTP-LINK系列:TL-WN550G TL-WN551G TL-WN510G TLWN610G TL-WN650G TL-WN65GD-Link Air DWL-610 Wireless Cardbus AdapterD-Link Air DWL-510 Wireless PCI AdapterD-Link Air DWL-650 Wireless Cardbus Adapter (rev. M- version 3 only)D-Link Air DWL-520 Wireless PCI Adapter (rev. D only)D-Link AirPro DWL-AB650 Multimode Wireless Cardbus Adapter (A/B)D-Link AirXpert DWL-AG650 Wireless Cardbus Adapter (A/B/G)D-Link AirPro DWL-A650 rev.B Wireless Cardbus AdapterD-Link AirPlus Xtreme G DWL-G650 Adapter芯片系列:AR5001, AR5002, AR5004, AR5005 and AR5006 、AR5008WildPackets OmniPeek支持的网卡驱动下载地址/support/downloads/driversSetup 1运行安装包里的setup.exe文件,出现如下界面:Setup 2点击“Next”按钮后出现如下界面:Setup 3选择“Manual”单选按钮,点击“Next”,出现如下界面:Setup 4此时运行安装包里的破解文件w-kg11.exe(运行前请关闭杀毒软件、防火墙或者运行时放行)出现如下界面:将Serial Number Copy 安装程序所要输入的Serial Number文本框(暂时勿关闭该破解程序,之后需要用到Key)Setup 6在界面上点击“Next”按钮,出现如下界面:在界面上点击“Next”按钮,出现如下界面:此时再把刚才打开的破解程序中的Key Copy到安装程序中所要输入Key的文本框,点击“Next”出现如下界面:Setup 9选择同意安装,点击“Next”按钮如果PC中未安装.NET Framework 2.0的话会出现如下界面:当然如果已安装了就略过.NET Framework 2.0安装步骤。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
OmniPeek知识讲解
一、OmniPeek作用?
OmniPeek可以针对无线网卡进行监控,通过对无线数据包的分析了解无线网络的运行状况,让用户可以清楚的知道无线网络使用的频段,信号强弱,SSID信息等内容。
二、安装OmniPeek软件:
笔者以OmniPeek 5.0为例进行介绍,首先我们到
https:///evals/eval.php?id=58055386地址下载主程序。
第一步:下载后运行主程序将进行自解压操作,我们指定一个路径点“unzip”解压按钮即可。
第二步:到解压缩目录中找到可执行安装程序,运行后选择第一行的install OmniPeek。
第三步:出现OmniPeek安装向导,我们点“NEXT”按钮继续操作。
第四步:经过注册步骤后同意安装许可协议。
第五步:在安装过程中会要求在本机安装.NET Framework 2.0程序,我们点YES即可自动安装。
第六步:软件会自动将.NET Framework 2.0安装到本地硬盘,大概需要几分钟的时间。
第七步:顺利安装.NET Framework 2.0后点完成按钮返回到OmniPeek安装向导。
第八步:选择安装类型,一般为了更好的分析网络我们选择“Complete”完全安装,点“NEXT”按钮继续。
第九步:接下来是选择安装的语言,只有英文和日文两种,对于我们大多数用户来说选择英文界面即可。
第十步:同样除了.NET Framework 2.0程序外我们还需要在本机安装Microsoft Visual C++ 2005程序,点确定开始安装。
第十一步:安装完Microsoft Visual C++ 2005后才是正式的复制OmniPeek软件必须文件到本地硬盘。
第十二步:完成全部安装设置工作,最后我们点“Finish”按钮结束安装。
至此我们就完成了OmniPeek软件的全部安装工作,我们可以通过他来分析无线网络了。
三、无线扫描从OmniPeek开始:
当然并不是说OmniPeek支持所有无线网卡,和我们以前讲过的要将自己的无线网卡升级为基于Atheros核心芯片一样,我们先要升级驱动,关于升级驱动的方法笔者已经在多个文章中进行过介绍,由于篇幅关系,在这里就不详细说明了。
下面我们就开始通过OmniPeek扫描无线网络。
第一步:通过“开始”->“程序”,找到wildpackets OmniPeek启动项,运行该选项开始扫描。
第二步:启动OmniPeek后首先我们选择建立一个新的捕获扫描事件——NEW Capture。
第三步:OmniPeek支持有线网卡和无线网卡,我们只需要在捕获选项窗口中的左边选择“Adapter”适配器,然后指定对应的无线网络连接即可针对无线网卡进行扫描。
第四步:设置完毕后点右上角的绿色捕获按钮开始拦截和分析经过无线网卡的数据包,找到对应数据包后将根据时间顺序显示在主窗口中,我们可以看到对应数据包的源MAC地址,目标MAC地址,对应的BSSID信息等。
同样点右上角的红色按钮将停止捕获。
小提示:
在捕获和分析无线数据包时可能会在数据包内容中看到BSSID和ESSID的信息,那么他们之间有什么区别呢?BSSID是48 bit数值,用来对较小BSS区域进行标识,每个主机在这个较小的区域里进行通讯。
而(eventually with an Access Point)ESSID可以让不同的BSS扩展至Extended Service Set (ESS)。
每个BSS有一个基点(Access Point),如果ESSID相同就可以相互通讯。
说白了如果你的网路较大,最少拥有两个基点(Access Point),那么你就需要用到ESSID信息了,如果只有一个无线接入点那么使用BSSID信息即可。
第五步:通过XP系统自带的扫描工具来扫描当前的无线网络,可以看到只有一个名为SSID信息为default的经过加密的安全无线网络。
第六步:而通过OmniPeek扫描也能够验证该网络的存在,即顺利找出该无线网络发送信号源头的MAC地址——00:15:E9:DF:DA:63,这是通过XP系统自带程序无法找出来的。
另外还能够发现其他没有广播SSID信息的无线网络信号,即隐藏SSID信息的无线网络的通讯数据包,这些都帮助我们更好的分析当前无线网络。
第七步:寻找无线网络还有一个好方法就是通过OmniPeek扫描到数据的expert列查看,如果显示wireless AP Broadcasting信息的话说明这个数据包对应的源地址为无线接入点的MAC。
第八步:我们通过双击该数据行进入到具体的数据包分析窗口,从而分析数据包的每一侦信息,可以了解到该无线网络使用的频段以及发射用到的诸多信息,当然也包括SSID信息。
第九步:对于隐藏SSID信息的无线网络来说,虽然我们可以通过OmniPeek发现他的存在,以及找到发射源的MAC地址,但是查看具体信息对应SSID处确实空白的,这是因为当前该无线网络没有客户端顺利连接并与之通讯,只要有主机通过该无线网络和无线接入点通讯的话我们查看数据包中SSID段内容将能够顺利找到隐藏SSID广播的无线网络所使用的SSID名称,和第八步中显示的信息将是一致的。
