asp介绍 外文翻译
ASP的名词解释

ASP的名词解释ASP(Active Server Pages)是一种用于动态构建和交互网页的技术。
它是一种服务器端脚本语言,常用于开发Web应用程序,尤其是在动态内容处理方面。
本文将对ASP的名词进行解释,介绍ASP的相关概念和功能。
1. ASPASP指的是Active Server Pages,它是一种基于服务器端脚本的技术。
与传统的静态网页不同,ASP网页可以根据用户请求动态生成内容。
其基本原理是将ASP代码嵌入到HTML页面中,当访问ASP页面时,服务器会对ASP代码进行解析和执行,最后将生成的HTML代码发送给用户的浏览器。
2. IISIIS(Internet Information Services)是微软开发的Web服务器软件,用于托管和管理ASP网页。
IIS提供了对ASP的全面支持,能够解析和执行ASP代码。
它还提供了一套功能强大的管理工具,用于配置和维护Web服务器。
3. ASP对象模型ASP对象模型是ASP技术的一个重要概念。
它定义了一系列对象和属性,用于实现ASP页面的功能。
常用的ASP对象包括Request对象、Response对象、Server对象等。
这些对象可以通过ASP代码进行操作,实现与用户交互、数据处理、文件操作等功能。
4. ASP脚本语言ASP脚本语言指的是在ASP页面中使用的脚本语言。
ASP最初采用VBScript作为默认的脚本语言,后来也逐渐支持JScript等其他脚本语言。
脚本语言用于编写ASP页面中的逻辑代码,与HTML代码相互嵌入,实现动态内容的生成和处理。
5. 数据库连接ASP可以方便地与数据库进行连接和操作。
通过使用数据库连接对象和查询语言,ASP可以从数据库中读取数据,并将其展示在网页上。
常用的数据库连接方式包括ADO(ActiveX Data Objects)和ODBC(Open Database Connectivity)等。
6. Session和CookieASP提供了Session和Cookie这两个机制,用于实现用户状态的存储和传递。
外文翻译---ASP的开发准则及安全管理

附录外文原文:The exploitation criteria and security management of the asp Exploitation criteria :Application servers have been, or ultimately will be used in Web server, which usually operate in the IIS ASP page computer. ASP is the only object of your client. It offers specialized systems and security considerations. While many of the Web sites use ASP simply not components, but in this article that ASP is the Internet as a bridge between the client and components. The following ASP components Guidelines (English) :ASP and the division of services between componentsASP server in the most commonly used building for the client to use HTML or XML documents, so we focused on the use of the program. This leads to a common problem, if ASP page on the server, then they are part of the operational level? Components in the world, the answer usually is not. Although the ASP server is in operation, but may be related to space applications in the same server, but it can not make it a part of the business logic. With user interface development tool, or as the opening of more business to operational programs with the clear distinction will be tremendous returns.Let us look at some of the most important operational level and that level division guidelines :Separation of the UI code and business logic. This includes preparation coupled with the UI code, such as the use of ASP components MTS internal target it with the business logic code separation, as in a different DLL.affair will be separated with the ASP page. Services ASP in certain cases beyond compare, but the components and multi-storey applications will change this situation. Components should not be dependent on the client layer to manage their affairs and business logic semantics.Will be expressed components (use solicit and responsive components) and Web server on the same machine and / or tenor. If the use of ASP internal components of the target objects on remote machines, then all of the internal components will be available in retail form. Server client access is COM+ server, which significantly reduced the performance and security of complicated. These markings will be lay in COM+ applications mark as "library activated" .ASP exist in server, ASP pages must be consistent with resource sharing rules, andremember to flexibility. Look at the following details :In the "conversation", management should avoid user specific state. Keep ASP stateless and where possible to allow resources pool.Mode operation:In evaluating whether a code of business logic layer or expressed, may I ask myself: "If I have to use click-phone applications to replace my ASP page, then the code are there?</FONT></SPAN></P><P class=MsoNormal style="TEXT-JUSTIFY: inter-ideograph; MARGIN: 0cm0cm0pt; TEXT-ALIGN: justify"><SPAN lang=EN-US><FONT face="Times New Roman" size=3>"If the answer is" yes ", then it could try to business logic code into machine code or user interface to help.If changed after the client code can not be used, or if it is constructed with the help of the user interface, the code is expressed services layer. It ASP page, or in the internal components usedASP components. It does not belong to the operational targets of components. Understanding of the distinction between desktop and ASP clientIt was modular incumbent engine,different table's top' tradition uniline ran win32 application from that asp. Key distinction generalize as follows: Thread management : ASP is a multi-client threads. This means that it can have many activities in the operation, perhaps at the same time dealing with different ASP page. This shows that it is not the only pseudo-objects to exclusive system users. This may be unexpected reactions, for example, into a bad habit : the object stored in ASP application variables or conversation.Security environment : ASP is the Web site of the Internet Information Services 5.0 implementation, a low, medium, high three separate degrees. The Web site can even have different security setup, or refuse to allow anonymous access, for customer and so on. All these have generated a lot of programs, namely, the use of different end-user account is your object.Easy rose : This is not a technical issue, but Web applications provide facilities Deputy effect. Traditionally, the increase in user base for desktop applications, the number of requests carefully planned well known to the client transferred. ASP has changed the process in motion and operational, ASP-Visual Basic applications can be conveniently opened for local or worldwide for all staff, all business partners and customers all use. This approach can be used to describe - owned super links individual e-mail users can make a tenfold increase in the base. To prepare for yourapplications?The only way to understand the intensity of Web sites for testing to obtain the expected value of the actual performance. Detailed information on the intensity of the test, please refer to the "application life cycle" section.In the use of Visual Basic ASP should target? In the context of the establishment and abolition of pages of your audience.In other words, as far as possible so that no state ASP pages only in a state of dependence conversation or temporary applications variables. Not to target storage applications in English or variables. This will lock in your conversation ASP systems, the expected value of flexibility may cancel all. In other words, the Web servers handle no more than a few dozens of users. If required, in English or applications stored content, please turn it into the data rather than objects. There are many other criteria can be observed. We recommend that you read MSDN V oices, .J.D. Meier compose the column "Servin<SPAN style="mso-spacerun: yes"></SPAN>It Up. "The column includes a lot of technology, practice and skills development can contribute to the expansion and reliable ASP components and applications.Not to be quoted or applications memory at conversation all the inserted object components are Visual Basic 6.0 "cell thread", that is to say they are operating in the Inter module. This means that if the thread established targets, then the object of all resources must use the same threads. Many threads (from it Web site users) use the same examples Agency targets, raises a series of activities, the application process may become bottlenecks.In addition, in conversation with Server .Create Object stored within the object STA to be implemented threads can be effectively linked to the current user, thus it will be the largest applications to give users a few restrictions the 20xN (N = number of processors).Mode operation:If you according to our suggest to take object stateless, are not used for storage of a client, and stored in the context of their applications. Client will be able to establish an independent, use and cancellation of their own target. This reduces the need for maintaining conversation - because they do not retain the skills unique to the state. Recommended approach is to target a state, it needs a database or other storage area to visit (such as cookies and LDAP). If applications require the use of English or the scope of the data, the data should instead deal with the subject of data stored in it. The dispose of the you could begin one genera,came encapsulation versus desirable value.ASP security management :The basic concept of security managementSafety management is based on information and ASP solution to manage the security strategy has set the security level definition process. Including management of the response to violations of the security act. ASP can be controlled without fear of attack and ASP clients business continuity, so to be able to deal with malicious attacks could really an art.Safety management in large measure dependent on the security strategy. These strategies could produce from different sources. To be considered when designing security strategy are :Service level agreement on the definition of external customer needs external security law requires external suppliers within the ASP security strategy and security strategy in the ASP environment integrated customer circumstances, the internal / external security strategy, For each solution, ASP must be defined security strategy. The strategy should be based on the various aspects of the most reliable Hop. According to customer needs, and even the basic structure will be very different design. Usually use three safety design:The dedicated network joint of the both asp solution and safety precautions completeness by asp proceed end-to-end Control usually,these purport asp versus proprietary basic structure subassembly possess full control,include asp and client of compartment.Public : ASP solutions and security measures by ASP component control. Usually, this means that within the ASP is in control of its own website, but does not guarantee to provide solutions to the public network with control. However, the ASP can be used as "virtual private network" (VPN) to carry out such technical links between ASP and client security.Mixed : the solution is a combination of the previous two. "dedicated" and "common" solutions are used. In ensuring security solutions, and also involves ASP customers.There are five dimensions of the process needed to improve the MOF model : planning : planning activities including in customer requirements, as well as internal and external strategies based on the legitimate demands of the SLA security component. In a dialogue with clients at the same time, it may be necessary to establish or adjust internal security strategy. Of course we should decide whether to do so by the ASP. This resulted in a level of security planning, including all aspects of the security strategy and design (infrastructure, personnel, steps, the environment, basic contracts, etc.).Implementation : Put stratification plane execute possession necessary safety precautions,withal observe SLA suffer have definitive security part for in force. at a pinch,this phase return should put make ultra internal security policy over in force..Assessment : Assessment is essential to end security management process. It involves determining the strategy and measures adopted by the state and effectiveness.Maintenance : maintenance based on the following security measures on the basis of : the results of regular inspections, the risk of changes in the situation clearly, and SLA or other conditions change.Control : control activities can organize and guide the security management process itself. Definition of a process control activities, functions, roles, responsibilities assigned, organizational structure and reporting structure. It is a continuing process and to ensure the engine improvements.Security management process must be continuous self improvement. New solutions, new technologies, new personnel, new steps, negligence may lead to the installation of integrated security attackers solution.ASP security configuration tool, ASP configuration tool for security managers should be very familiar with, because the system was associated with all aspects of information security, it is essential.These tools should be very easy for you to answer the following questions : "My computer security?<SPAN style="mso-spacerun: yes"></SPAN>"or" My network security?<SPAN style="mso-spacerun: yes"></SPAN>". These tools should allow for the definition of security strategy has covered all aspects of configuration and analysis, such as : account strategy. Installation or alteration visit strategies, including domain or local password strategies, domain or local domain Kerberos account lock strategy and tactics (where applicable).Local strategy. Of the local audit strategies, a wide range of user competence and the distribution of security option, such as diskettes, CD-ROM such control. Restricted group.To be embedded in the group and the allocation of any other specific group or modify designated members of the group (such as Administrators, Server Operators, Backup Operators and Power Users, etc.). This should not be used as a management tool to use general members-only used to control specific groups (with sensitive functions assigned to them). System services. Distribution system installed in different services (including network transmission services such as TCP/IP, NetBIOS, CIFS document sharing, printing, etc.) security. If we do not use will be stopped TCP/IP outside services. The detailed information, please refer to/technet/Document or folder sharing. Distribution systems and document services Reorientation of equipment services devices installed. This includes visiting various networks, the sharing of documents and the closure of anonymous visits opening packet signatures and security of the option.System Registry : installation or modification of the system of security of the Register. Storage systems : a local system or to modify the document tree inventory volumes and safety. Preparation : ASP for customers and prepare a secure environment for users to establish secure, and documents. These tools should also help to monitor security strategy has been defined in all its aspects, such as : account strategy - passwords, lock and Kerberos installation.The all these figure of the use, closed loop video frequency grade of the both the access control of the start-up mode and access control of the policy of the mount of the both local policy-look through, user purview and security option. Event log-system, application, security and directory services log has reference to security option. event log-system, application, security and directory services log 'mount. restricted group-compose a person engaged in some field of activity. System service-system service.registry key- key. File system-file and documentary access control.Physics visit system-versus equipment drawing visit, calorie type key. These instrument return ought to could analysis block policy,all the while descend solstice subscriber stage. command rest instrument came analyses surveillance course suffer make a raise of. These instrument usually in particular trust statistical technique to.The ASP managers can use Windows 2000 "Windows 2000 security configuration tool set" for the following components of some or all of the above security. "security templates" management module. "security templates" management module is an independent Microsoft management control (MMC) management module, which can create templates based on the text document that includes all aspects of security for security."security configuration and analysis" management module. "security configuration and analysis" management module is independent MMC management module, or it can analysis of the security of the Windows 2000 operating system. Based on its operational use "security templates" management modules security templates to establish the content.Secedit.exe. Secedit.exe is a "security configuration and analysis" of the ordermanagement module line version. It enables security configuration and analysis in the absence of graphical user interface (GUI) of the implementation.Group strategy for the security of expansion. "security configuration tool set" also includes a group of the expansion strategy editorial management modules for configuration and local security policy domain or organizational unit (OU) security strategy. Local security strategy include only the " Account number Strategy" and "local strategy" security. Domain or OU for the definition of security strategy may include all security.外文资料翻译译文:ASP的开发准则及安全管理开发准则:应用程序服务器被,或最终将被Web 服务器所使用,它通常是运行ASP 页面的IIS 计算机。
ASP外文翻译+原文

ASP外文翻译+原文ENGLISHE:Develop Web application program using ASP the architecture that must first establish Web application. Now in application frequently with to have two: The architecture of C/S and the architecture of B/S.Client/server and customer end / server hold the architecture of C/S.The customer / server structure of two floor.Customer / server ( Client/Server ) model is a kind of good software architecture, it is the one of best application pattern of network. From technology, see that it is a logic concept, denote will a application many tasks of decomposing difference carry out , common completion is entire to apply the function of task. On each network main computer of web site, resource ( hardware, software and data ) divide into step, is not balanced, under customer / server structure, without the client computer of resource through sending request to the server that has resource , get resource request, so meet the resource distribution in network not balancedness. With this kind of structure, can synthesize various computers to cooperate with work, let it each can, realize the scale for the system of computer optimization ( Rightsizing ) with scale reduce to melt ( Downsizing ). Picture is as follows:It is most of to divide into computer network application into two, in which the resource and function that part supports many users to share , it is realized by server; Another part faces every user , is realized by client computer, also namely, client computer is usual to carry out proscenium function , realizes man-machine interaction through user interface , or is the application program of specific conducted user. And server usually carries out the function of backstage supporter , manages the outside request concerning seting up, accepting and replying user that shared. For a computer, it can have double function , is being certain and momentary to carve to act as server , and again becomes client computer in another time.Customer / server type computer divide into two kinds, one side who offers service is called as server , asks one side of service to be called as customer. To be able to offer service, server one side must have certain hardware and corresponding server software; Also, customer one side must also have certain hardware and corresponding customer software.There must be a agreement between server and customer, both sides communicate according to this agreement.Apply customer / server model in Internet service , the relation betweencustomer and server is not immutable. Some Internet node offers service on the one hand , also gets service on the other hand from other node; It is even in one time dialogue course, mutual role also exchanges probably. As in carry out file transmission , if be called as one side who offers file server, is called as one side who gets file customer, when using get or mget order since another node takes file, can think that what self use and it is client computer , is using put or mput order to another node dispatch file can again think the machine that used self is server.Multilayer customer / server structureAlong with the development of enterprise application, recently, have again arisen a kind of new multilayer architecture, it applies customer end to divide into two minutes: Customer application and server apply. Customer application is the part of original customer application , is another and partial to have been transfered to server to apply. New customer application takes the responsibility for user interface and simple regular business logic and new server application resident core , changeable business logic. Therefore its structure has become new ( Client application + Server application )/Server structure. Following picture shows:This kind of structure has solved traditional Client/Server can expand problem, have reduced customer end business logic , and have reduced the requirement of customer end for hardware. At the same time because of a lot of business logic concentrations have gone to unitary application server on, the maintenance work of application system had been also concentrated together, have eliminated the problem in the traditional structure of Client/Server that software distributes. This kind of structure is called as the architecture of B/S.Browser/Server and browser / server hold the architecture of B/S. On essence, Browser/Server is also a kind of structure of Client/Server, it is a kind of from the traditional two levels of structural development of Client/Server come to thethree-layer structural special case of Client/Server that applied on Web.In the system of Browser/Server, user can pass through browser to a lot of servers that spread on network to send request. The structure of Browser/Server is maximum to have simplified the work of client computer, on client computer, need to install and deploy few customer end software only , server will bear more work, for database visit and apply program carry out will in server finish.Under the three-layer architecture of Browser/Server, express layer( Presentatioon ) , function layer ( Business Logic ) , data layer ( Data Service ) have been cut the unit of 3 relative independences:It is the first layer of to express layer: Web browser.In expressing layer contain system show logic, locate in customer end. It's task is to suggest by Web browser to the certain a Web server on network that service is asked , after verifying for user identity, Web server delivers needed homepage with HTTP agreement to customer end, client computer accept the homepage file that passed , and show it in Web browser on.Second layer function layer: Have the Web server of the application function of program extension.In function layer contain the systematic handling of general affairs logic, locate in Web server end. It's task is the request concerning accepting user , need to be first conducted and corresponding to expand application program and database to carry out connection , passes through the waies such as SQL to database server to put forward data handling to apply for, then etc. database server the result of handling data submit to Web server, deliver again by Web server to return customer end.The number of plies of 3th according to layer: Database server.In data layer contain systematic data handling logic, locate in database server end. It's task is to accept the request that Web server controls for database, realization is inquired and modified for database , update etc. function, submit operation result to Web server.Careful analysis is been easy to see , the architecture of Browser/Server ofthree-layer is the handling of general affairs of the two levels of structure ofClient/Server logic modular from the task of client computer in split , from the first floor of individual composition bear the pressure of its task and such client computer have alleviated greatly, distribute load balancedly and have given Web server, so from the structural change of Client/server of original two floor the structure ofBrowser/Server of three-layer. This kind of three-layer architecture following picture shows.This kind of structure not only client computer from heavy burden and the requirement of performance that rises continuously for it in liberation come out , also defend technology people from heavy maintenance upgrading work in free oneself. Since client computer handles general affairs , logic partial minutes have given function server, make client computer right off " slender " a lot of, do not take the responsibility for handling complex calculation and data again visit etc. crucial general affairs, is responsible to show part, so, maintenance people do not rush about again for the maintenance work of program between every client computer, and put major energy in the program on function server update work. Between this kind of three-layer structural layer and layer, the mutually independent change of any first floor does not affect the function of other layer. It has changed the defect of the two levels of architecture of Client/Server of tradition from foundation, it is the transform with deep once in application systematic architecture.The contrast of two architecturesThe architecture of Browser/Server and the architecture of Client/Server compare with all advantages that not only have the architecture of Client/Server and also have the architecture of Clinet/Server the unique advantage that place does not have:Open standard: The standard adopted by Client/Server only in department unification for but, it's application is often for special purpose.It is lower to develop and defend cost: It need to be implemented on all client computers that the application of Client/Server must develop the customer end software for special purpose, no matter installation and disposition escalate still, have wasted manpower and material resources maximumly. The application ofBrowser/Server need in customer end have general browser , defend and escalate to work in server end go on , need not carry out any change as customer holds , have reduced the cost of development and maintenance so greatly.It is simple to use , interface friendly: The interface of the user of Client/Server is decided by customer end software, interface and the method of its use are not identical each, per popularize a system of Client/Server ask user study from the beginning, is hard to use. The interface of the user of Browser/Server is unified on browser, browser is easy to use , interface friendly, must not study use again other software, the use of a Lao Yong Yi that has solved user problem.Customer end detumescence: The customer end of Client/Server has the function that shows and handles data , as the requirement of customer end is a client computer " it is fat " very high. The customer of Browser/Server holds the access that not takes the responsibility for database again and the etc. task of complex data calculation, need it only show , the powerful role that has played server fully is so large to have reduced the requirement for customer end, customer end become very " thin ".System is flexible: The 3 minutes of the system of Client/Server, in modular, have the part that need to change to want relation to the change of other modular, make system very difficult upgrading. The 3 minutes of the system of Browser/Server modular relative independence, in which a part of modular change, other modular does not get influence, it is very easy that system improve to become, and can form the system with much better performance with the product of different manufacturer.Ensure systematic safety: In the system of Client/Server, directly join with database server because of client computer, user can very easily change the data on server, can not guarantee systematic safety. The system of Browser/Server has increased a level of Web server between client computer and database server , makes two not to be directly linked again, client computer can not be directly controled for database, prevent user efficiently invade illegally.The architecture of Browser/Server of three-layer has the advantage that a lot of traditional architectures of Client/Server does not have , and is close to have combined the technology of Internet/Intranet, is that the tendency of technical development tends to , it application system tape into one brand-new develop times. From this us option the configuration of B/S the architecture that develops as system.what are C/S with B/SFor " C/S " with the technology of " B/S " develop change know , first,must make it clear that 3 problems.( 1 ) What is the structure of C/S.C/S ( Client/Server ) structure, the server structure and client computer that all know well. It is software systematic architecture, through it can hold hardware environment fully using two advantage, realize task reasonable distribution to Client end and Server end , have reduced systematic communication expense. Now, the most systems of application software are the two levels of structure of the form of Client/Server , are developing to the Web application of distribution type since current software application is systematic, Web and the application of Client/Server can carry out same business handling , apply different modular to share logic assembly; Therefore it is systematic that built-in and external user can visit new and existing application , through the logic in existing application system, can expand new application system. This is also present application system develop direction. Traditional C /S architecture though adopting is open pattern, but this is the openness that system develops a level , in specific application no matter Client end or Server end the software that need to still specify support. Because of the software software that need to develop different edition according to the different system of operating system that can not offer the structure of C/S and the open environment of user genuine expectation , besides, the renovation of product is very rapid, is nearly impossible to already meet the 100 computer above users of local area network at the same time use. Price has low efficiency high. If my courtyard uses , Shanghai exceed the orchid company's management software " statistics of law case" is typical C /S architecture management software.( 2 ) What is the structure of B/S.B/S ( Browser/Server ) structure browser and server structure. It is along with the technology of Internet spring up , it is for the structure of improvement or a kind of change of the structure of C/S. Under this kind of structure, user working interface is to realize through WWW browser, lose the logic of general affairs very much in front( Browser) realization, but the major logic of general affairs in server end( Server) realization, form the three-layer claimed 3-tier structure. So, have simplified customerend computer load greatly , have alleviated system to defend workload and the cost with upgrading , have reduced the overall cost of user ( TCO ). With present technology see , local area network the network application that establishes the structure of B/S , and under the pattern of Internet/Intranet, database application is easy to hold relatively , cost also is lower. It is that oneness goes to the development of position , can realize different people, never same place, with difference receive the way of entering ( for example LAN, WAN, Internet/Intranet etc.) visit and operate common database; It can protect data platform efficiently with management visit limits of authority, server database is also safe. Now in my courtyard, net ( Intranet ) , outer net ( Internet ) with Beijing eastern clear big company " law case and the management software of official business " is the structural management software of B/S , policemen each working station in local area network pass through WWW browser can realize working business. Especially in JAVA step platform language appearance after, the configuration management software of B/S is more facilitated , is shortcut, efficient.( 3 ) The management software technology of main stream.The technology of main stream of management software technology is as management thought , have also gone through 3 develop period. First, interface technology goes to Windows graph interface ( or graph user interface GUI ) from last century DOS character interface, till Browser browser interface 3 differences develop period. Secondly, today own the browser interface of computer, is not only visual and is easy to use , what is more major is that any its style of application software based on browser platform is as, make the requirement of choosing a person for the job for operating training not high and software operability is strong , is easy to distinguish; Moreover platform architecture the file that also goes to today from past single user development /server ( F /S ) system and client computer /server ( C /S ) system and browser /server ( B /S ) system.The comparison of C/S and B/SC/S and B/S is the now world two technologies of main stream of developing pattern technical configuration. C/S is that American Borland company researches and develop most early, B/S is that American Microsoft researches anddevelop. Now this two technologies with quilt world countries grasp , it is many that domestic company produce article with C/S and the technical development of B/S. This two technologies have the certain market share of self , is with customer crowd , each domestic enterprise says that own management software configuration technical function is powerful, advanced, convenient , the customer group that can lift , have a crowd scholar ink guest to shake flag self cry out , advertisement flies all over the sky , may be called benevolent to see kernel, sage sees wisdomC/S configures inferior position and the advantage of software( 1 ) Application server operation data load is lightcomparatively.The database application of the most simple architecture of C/S is become by two partial groups, customer applies program and database server program. Both can be called as proscenium program and the program of backstage supporter respectively. The machine of operation database server program is also called as application server. Once server program had been started , waits the request concerning responding customer program hair at any time; Customer application program operation can be called as customer computer on the own computer of user, in correspondence with database server, when needs carry out any operation for the data in database, customer program seeks server program voluntarily , and sends request to it, server program is regular as basis intends to make to reply, send to return result, application server operation data load is lighter.( 2 ) Data store management function relatively transparent.In database application data store management function, is carried out respectively independently by server program and customer application program , is regular as proscenium application can violate , and usually those different( no matter is have known still unknown ) operations data, in server program, do not concentrate realization, for instance visit limits of authority, serial number can be repeated , must have customer talent establishment the rule order. It is these to own , for the last user that works on proscenium program is " transparent ", they need not be interest in ( can not usually also interfere ) the course of behind, can complete own all work. In the application of customer server configuration proscenium program not is very " thin ",troublesome matter is delivered to server and network. In the system of C/S take off , database can not become public really , professionally more competent storehouse, it gets independent special management.( 3 ) The inferior position of the configuration of C/S is high maintenance cost make investment just big.First, with the configuration of C/S, will select proper database platform to realize the genuine "unification" of database data, make the data synchronism that spreads in two lands complete deliver by database system go to manage, but the logically two operators of land will directly visit a same database to realize efficiently , have so some problems, if needs establishment the data synchronism of " real time ", the database server that must establish real time communication connection between two places and maintains two lands is online to run , network management staff will again want to defend and manage for customer end as server defends management , maintenance and complex tech support and the investment of this high needs have very high cost, maintenance task is measured.Secondly, the software of the structure of C/S of tradition need to develop the software of different edition according to the different system of operating system , is very rapid because of the renovation of product, price is working needs high with inefficient already do not meet. In JAVA step platform language appearance after, the configuration of B/S is more vigorous impact C/S , and forms threat and challenge for it. .The advantage of B/S configuration software( 1 ) The Maintenance of inferior position and upgrading way are simple.Now upgrading and the improvement of software system more and more frequently, the product of the configuration of B/S embodies more convenient property obviously. For one a little a little bit big unit , if systematic administrator needs , between hundreds of 1000 even last computers round trip run , efficiency and workload is to can imagine, but the configuration of B/S software needs management server have been all right , all customer ends are browser only, need not do any maintenance at all. No matter the scale of user has , is what , has how many branch will not increase any workload of maintenance upgrading , is all to operate needs to aim at server to go on;If need differently only, net server connection specially , realize long-range maintenance and upgrading and share. So client computer more and more " thin ", and server more and more " fat " is the direction of main stream of future informative development. In the future, software upgrading and maintenance will be more and more easy , and use can more and more simple, this is for user manpower , material resources, time and cost save is obvious , it is astonishing. Therefore defend and escalate revolutionary way is the client computer " it is thin ", " is fat " server.( 2 ) Cost reduction, it is more to select.All know windows in the computer of top of a table on nearly one Tong world, browser has become standard disposition, but on server operating system, windows is in absolute dominance position not. Current tendency is the application management software that uses the configuration of B/S all , need to install only in Linux server on , and safety is high. The so server option of operating system is many, no matter choosing those operating system, can let the most of ones use windows in order to the computer of top of a table of operating system does not get influence, this for make most popular free Linux operating system develop fast, Linux except operating system is free besides, it is also free to link database, this kind of option is very pupular.Say, many persons on daily, "Sina website" nets , so long as having installed browser for can , and what need not know the server of " Sina website " to use is that what operating system, and in fact the most of websites do not use windows operating system really, but the computer of user is most of as installing to be windows operating system.( 3 ) Application server operation data load value comparatively.Since B/S configures management, software installation in server end ( Server ) on, it is been all right that network administrator need to manage server only, the user interface major logic of general affairs in server ( Server ) end pass through WWW browser completely realization, lose the logic of general affairs very much in front( Browser) realization, all customer ends has only browser, network administrator need to do hardware maintenance only. But application server operation data load is heavier, once occuring " server collapse " to wait for problem,consequence is unimaginable. Therefore a lot of units have database to stock server , are ready for any eventuality.原文翻译:利用ASP开发Web应用程序首先必须确立Web应用的体系结构。
ASP语言
学习ASP之前学习ASP 之前,应掌握HTML 和CSS,以保证你能够熟练地编写静态网页。
有关HTML 教程,CSS 教程,请参见HTML教程,CSS教程。
另外,你还需掌握VBScript 脚本语言,因为这是编写ASP 网页最合适的脚本语言。
有关VBScript 脚本语言,请参见VBScript教程。
ASP简介ASP,英文全称为Active Server Pages。
ASP 是一种动态网页,文件后缀名为.asp。
ASP 网页是包含有服务器端脚本(server-side script) 的HTML 网页。
Web 服务器会处理这些脚本,将其转换成HTML 格式,再传到客户的浏览器端。
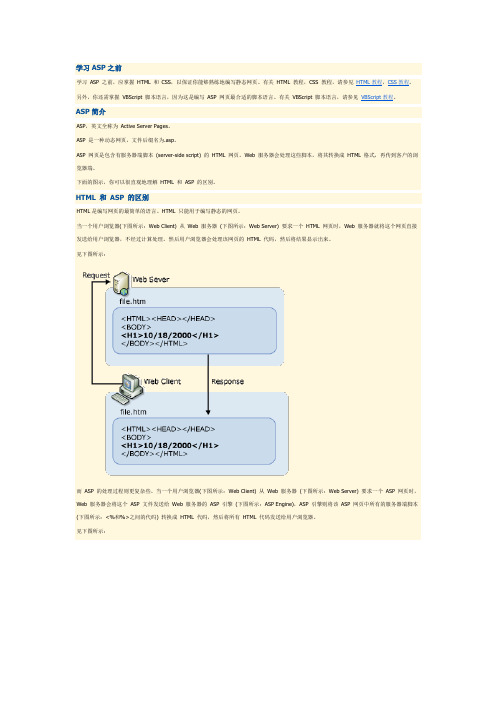
下面的图示,你可以很直观地理解HTML 和ASP 的区别。
HTML 和ASP 的区别HTML是编写网页的最简单的语言。
HTML 只能用于编写静态的网页。
当一个用户浏览器(下图所示:Web Client) 从Web 服务器(下图所示:Web Server) 要求一个HTML 网页时,Web 服务器就将这个网页直接发送给用户浏览器,不经过计算处理。
然后用户浏览器会处理该网页的HTML 代码,然后将结果显示出来。
见下图所示:而ASP 的处理过程则更复杂些。
当一个用户浏览器(下图所示:Web Client) 从Web 服务器(下图所示:Web Server) 要求一个ASP 网页时,Web 服务器会将这个ASP 文件发送给Web 服务器的ASP 引擎(下图所示:ASP Engine),ASP 引擎则将该ASP 网页中所有的服务器端脚本(下图所示:<%和%>之间的代码) 转换成HTML 代码,然后将所有HTML 代码发送给用户浏览器。
见下图所示:ASP能干什么?用HTML, CSS 已经能够编写非常漂亮的静态网页,但是这些网页缺乏和用户的互动性。
比如,你需要为你的网站增加用户注册和登录的功能;你可能还需要做一些网上调查,了解用户对于某个事件或者产品的反馈;你还可能需要一个电子商务网站,及时发布产品信息和满足用户在线订购的需要......编写ASP 动态网页能够帮助你实现这些和用户互动的功能。
asp.net外文文献+翻译

技术1.构建 页面 和结构 是微软.NET framework整体的一部分, 它包含一组大量的编程用的类,满足各种编程需要。
在下列的二个部分中, 你如何学会 很适合的放在.NET framework, 和学会能在你的 页面中使用语言。
.NET类库假想你是微软。
假想你必须支持大量的编程语言-比如Visual Basic 、C# 和C++. 这些编程语言的很多功能具有重叠性。
举例来说,对于每一种语言,你必须包括存取文件系统、与数据库协同工作和操作字符串的方法。
此外,这些语言包含相似的编程构造。
每种语言,举例来说,都能够使用循环语句和条件语句。
即使用Visual Basic 写的条件语句的语法不与用C++ 写的不一样,程序的功能也是相同的。
最后,大多数的编程语言有相似的数据变量类型。
以大多数的语言,你有设定字符串类型和整型数据类型的方法。
举例来说,整型数据最大值和最小值可能依赖语言的种类,但是基本的数据类型是相同的。
对于多种语言来说维持这一功能需要很大的工作量。
为什么继续再创轮子? 对所有的语言创建这种功能一次,然后把这个功能用在每一种语言中岂不是更容易。
.NET类库不完全是那样。
它含有大量的满足编程需要的类。
举例来说,.NET类库包含处理数据库访问的类和文件协同工作,操作文本和生成图像。
除此之外,它包含更多特殊的类用在正则表达式和处理Web协议。
.NET framework,此外包含支持所有的基本变量数据类型的类,比如:字符串、整型、字节型、字符型和数组。
最重要地, 写这一本书的目的, .NET类库包含构建的 页面的类。
然而你需要了解当你构建.NET页面的时候能够访问.NET framework 的任意类。
理解命名空间正如你猜测的, .NET framework是庞大的。
它包含数以千计的类(超过3,400) 。
幸运地,类不是简单的堆在一起。
.NET framework的类被组织成有层次结构的命名空间。
ASP术语解释

ASP术语解释activate(激活)一个编程过程。
它将一个对象装载到内存中,使其处于可执行或正运行状态。
或者,也指绑定对象使其进入运行状态的过程。
Active client(活动客户)活动平台的客户端元件。
它实现内容和应用程序的跨平台操作,包括对HTML、脚本语言(包括VBScript 和JScript)、Java小程序、ActiveX组件、ActiveX控件,以及Active文档的支持。
Active document(活动文档)一个基于Windows的、嵌入到浏览器中的非HTML应用程序,提供了从浏览器界面访问这些应用程序的功能的方法。
Active Group,The一个由The Open Group赞助的标准组织。
它是一个开放的、为客户服务的委员会,负责ActiveX技术和许可的发展和管理。
Active platform(活动平台)一个综合了客户、活动客户和服务器、活动服务器的完整集合。
它采用了基于组件的开发技术,使得开发者易于将Internet的连通性和个人计算机的强大功能结合起来。
Active server(活动服务器)活动平台的服务器方元件,具体来说,就是由Windows NT发布的服务器方技术的集合,它提供了一致的服务器方组件和脚本模式,以及一整套的针对组件应用程序管理、数据库访问、事务处理和消息处理的服务。
Active Server Page (ASP)Microsoft Internet Information Server 4.0中的服务器方执行环境。
它在服务器上执行ActiveX脚本和ActiveX组件。
ActiveX一套与语言无关的内部操作技术。
它使得采用不同语言编写的软件组件能够在网络环境中一起工作。
ActiveX的核心技术元件是COM和DCOM。
ActiveX automation(ActiveX自动化)一种与语言无关的、从应用程序外部操作ActiveX组件的方法的方式。
外文翻译---提高字符串处理性能的ASP应用程序

的。
这是一个设有一个可配置的字符串缓冲区并且管理新文本插入到该缓冲区,只有当文本长度超过字符串缓冲区的长度时,才产生字符串的充足。
微软网框架免费地提供了这种类别。
(System.Text.StringBuilder)。
这是在那种环境下进行串联操作所推荐的。
在ASP和传统的Visual Basic的世界中,我们无权使用此类别,因此我们需要建立我们自己的一个类别。
以下是一个范例是用Visual Basic 6.0创建的StringBuilder类(错误处理代码为了简便已省略)。
Option Explicitdefault initial size of buffer and growth factorPrivate Const DEF_INITIALSIZE As Long = 1000Private Const DEF_GROWTH As Long = 1000buffer size and growthPrivate m_nInitialSize As LongPrivate m_nGrowth As Longbuffer and buffer countersPrivate m_sText As StringPrivate m_nSize As LongPrivate m_nPos As LongPrivate Sub Class_Initialize()set defaults for size and growthm_nInitialSize = DEF_INITIALSIZEm_nGrowth = DEF_GROWTHinitialize bufferInitBufferEnd Subset the initial size and growth amountPublic Sub Init(ByVal InitialSize As Long, ByVal Growth As Long)If InitialSize > 0 Then m_nInitialSize = InitialSizeIf Growth > 0 Then m_nGrowth = GrowthEnd Subinitialize the bufferPrivate Sub InitBuffer()m_nSize=-1m_nPos=1End Subgrow the bufferPrivate Sub Grow(Optional MinimimGrowth As Long) initialize buffer if necessaryIf m_nSize = -1 Thenm_nSize = m_nInitialSizem_sText = Space$(m_nInitialSize)Elsejust growDim nGrowth As LongnGrowth = IIf(m_nGrowth > MinimimGrowth,m_nGrowth, MinimimGrowth)m_nSize = m_nSize + nGrowthm_sText = m_sText & Space$(nGrowth)End IfEnd Subtrim the buffer to the currently used sizePrivate Sub Shrink()If m_nSize > m_nPos Thenm_nSize = m_nPos - 1m_sText = RTrim$(m_sText)End IfEnd Subadd a single text stringPrivate Sub AppendInternal(ByVal Text As String) If (m_nPos + Len(Text)) > m_nSize Then Grow Len(Text) Mid$(m_sText, m_nPos, Len(Text)) = Textm_nPos = m_nPos + Len(Text)End Subadd a number of text stringsPublic Sub Append(ParamArray Text())Dim nArg As LongFor nArg = 0 To UBound(Text)AppendInternal CStr(Text(nArg))Next nArgEnd Subreturn the current string data and trim the bufferPublic Function ToString() As StringIf m_nPos > 0 ThenShrinkToString = m_sTextElseToString = ""End IfEnd Functionclear the buffer and reinitPublic Sub Clear()InitBufferEnd Sub使用这个类别的基本原理是一个类别级的变量(m_sText)被保留,这个变相相当于一个字符串缓冲区,而这个缓冲区的大小设定是靠使用Space$功能来对其填充空格符号。
asp技术外文翻译

原文:(一)An Active Server Page (ASP)1. This paper firstly introduces multi-tier B/S Architecture and Web-related technology .Based on them , this paper presents system objection, system demand, main feather and system design solution ,particularly describes system design and implement in detail. In system design and implement,and key points in other sub-system are also analyzed further .This paper also introduces mostly technology of system . Lastly, this paper makes a summery and figures out some problem which need to be improved.2. computing has brought about a whole new standard of corporate computing productivity, but at the same time it has introduced many new problems for corporate IT organizations.The advent of low-cost desktop computers makes B/S possible. No longer is it necessary for users to wait even seconds to interact with their corporate data. With their own computer on their desktop they do not need to wait for the mainframe to respond.All of this cheap computer power has also made it possible to support computation- intensive graphical interfaces, which are much easier for users to understand.In order for B/S to work, the application program which used to reside entirely on the mainframe has been split into two pieces, the client piece and the server piece.The portion of the application that resides in the Client personal computer includes logic for the presentation of information to the user and mechanisms for accepting user input. It also includes logic for data interaction at the Client, such as changing the appearance of the graphical interface as the user make various choices.The Client software often includes corporate business rules that allow data to be validated before it is sent to the server.The portion of the application that remains on the Server is usually just the portion that stores data at a central location, accessible to other users. The once mighty mainframes have been reduced to database servers, while the rest of the application has migrated out to the clients.This migration has caused many problems. The Client machines have become "fat". As the complexity of applications has risen it has become necessary to supply users with more and more powerful computers with faster processors, more disk storage, and more RAM. It is true that personal computer manufacturers have been able to deliver better and better computers for the same amount of money, but the constant upgrades required are costly for corporations. It takes more people and time to upgrade hundreds or thousands of personal computers than it used to take to just upgrade the mainframes.Setting aside the cost of Client equipment, the proliferation of corporate applications, including business logic, to hundreds or thousands of machines has become a major cost factor for corporations. Where IT staffs used to be able to maintain all the corporate software assets in one central location, they now need to maintain corporate software spread all across the corporation, often housed in computers that are out of IT control.There are many estimates available that the cost of Client/Server computing is eight or more times the cost of the equipment alone. Several companies offer large, expensive systems that have the sole purpose of maintaining corporate software spread out all over the corporation.The issue here is not personal-productivity software such as word processors and spreadsheets. Personal software products have enabled knowledge workers to attain new heights of productivity. The issue is the maintenance of corporate software, such as order-entry and accounting. Imagine the difficulty of making a schema change in a corporate database, and synchronizing that change with the updating of thousands of copies of the corresponding Client software.It is true that the use of department-level LANs can bring down the number of copies that need to be updated to hundreds, instead of thousands. The size of the LANs must be limited, because the large size of the fat client software requires a responsive LAN or else the users will just copy the enterprise software to their own machines, bringing us back to thousands of copies to be maintained.The task of making simultaneous changes to even hundreds of copies of client software is still a daunting one.3. which in turn serves it back to the client in your personal computer, which displays the information for you.The client/server model has become one of the central ideas of network computing. Most business applications being written today use the client/server model. So does the Internet's main program, TCP/IP. In marketing, the term has been used to distinguish distributed computing by smaller dispersed computers from the "monolithic" centralized computing of mainframe computers. But this distinction has largely disappeared as mainframes and their applications have also turned to the client/server model and become part of network computing.In the usual client/server model, one server, sometimes called a daemon, is activated and awaits client requests. Typically, multiple client programs share the services of a common server program. Both client programs and server programs are often part of a larger program or application. Relative to the Internet, your Web browser is a client program that requests services (the sending of Web pages or files) from a Web server (which technically is called a Hypertext Transport Protocol or HTTP server) in another computer somewhere on the Internet. Similarly, your computer with TCP/IP installed allows you to make client requests for files from File Transfer Protocol (FTP) servers in other computers on the Internet.Other program relationship models included master/slave, with one program being in charge of all other programs, and peer-to-peer, with either of two programs able to initiate a transaction.ASP is also an abbreviation for application service provider.An Active Server Page (ASP) is an HTML page that includes one or more scripts (small embedded programs) that are processed on a Microsoft Web server before the page is sent to the user. An ASP is somewhat similar to a server-side include or a common gateway interface (CGI) application in that all involve programs that run on the server, usually tailoring a page for the user. Typically, the script in the Web pageat the server uses input received as the result of the user's request for the page to access data from a database and then builds or customizes the page on the fly before sending it to the requestor.ASP is a feature of the Microsoft Internet Information Server (IIS), but, since the server-side script is just building a regular HTML page, it can be delivered to almost any browser. You can create an ASP file by including a script written in VBScript or JavaScript in an HTML file or by using ActiveX Data Objects (ADO) program statements in the HTML file. You name the HTML file with the ".asp" file suffix. Microsoft recommends the use of the server-side ASP rather than a client-side script, where there is actually a choice, because the server-side script will result in an easily displayable HTML page. Client-side scripts (for example, with JavaScript) may not work as intended on older browsers.For Web service applications, Microsoft provides a new version of ASP support called .4. Browser/Server is a trademark for the new paradigm of corporate computing that is now possible using technology developed for the World Wide Web.At the present time the Web is used by the many corporations to distribute marketing materials. The corporate Web Server is usually just a Brochure Server for the Marketing department.The potential exists for using Web Browsers and Severs for much more, especially behind the corporate firewall. Browser/Server technology can be used to enhance most corporate computing systems, not just the system used for marketing.To understand the important new role that Browser/Server technology can play within a company it is useful to examine the previous paradigms that have paved the way for Browser/Server computing.Computers were first used in Batch mode. End users had little interaction with the corporate computing systems. Inputs would be gathered in a "batch" and keyed into punch cards, which were fed by operators into the mainframe computer when the computer was done running previous batch jobs. When the mainframe processed the job it usually produced printed output which eventually made its way to the end user. The batch process included no user interaction, and the only recourse a user had after discovering errors in the batch run was to go through the cycle, which often took hours or even days, again and again.The addition of dumb terminals to the mainframe gave the users direct, hands-on, connections to the corporate computer. Users no longer had to wait for a computer operator to run their jobs, they could enter the data and initiate processing themselves. There were still delays involved. Dumb terminals were useful for inputting and displaying information, but because they had no processing ability it was necessary for the user to interact with the mainframe in order to interact with their data. Batch jobs previously could be run one-by-one if necessary, but mainframes had to deal with all attached terminals seemingly at once. This lead to delays as users waited for the mainframe to "turn around" their terminal messages while they interacted with their data.Still, the delays were now down to seconds or minutes, instead of hours or days.Client/Server computing has brought about a whole new standard of corporate computing productivity, but at the same time it has introduced many new problems for corporate IT organizations.The advent of low-cost desktop computers makes Client/Server possible. No longer is it necessary for users to wait even seconds to interact with their corporate data. With their own computer on their desktop they do not need to wait for the mainframe to respond.All of this cheap computer power has also made it possible to support computation- intensive graphical interfaces, which are much easier for users to understand.In order for Client/Server to work, the application program which used to reside entirely on the mainframe has been split into two pieces, the client piece and the server piece.The portion of the application that resides in the Client personal computer includes logic for the presentation of information to the user and mechanisms for accepting user input. It also includes logic for data interaction at the Client, such as changing the appearance of the graphical interface as the user make various choices.The Client software often includes corporate business rules that allow data to be validated before it is sent to the server.The portion of the application that remains on the Server is usually just the portion that stores data at a central location, accessible to other users. The once mighty mainframes have been reduced to database servers, while the rest of the application has migrated out to the clients.This migration has caused many problems. The Client machines have become "fat". As the complexity of applications has risen it has become necessary to supply users with more and more powerful computers with faster processors, more disk storage, and more RAM. It is true that personal computer manufacturers have been able to deliver better and better computers for the same amount of money, but the constant upgrades required are costly for corporations. It takes more people and time to upgrade hundreds or thousands of personal computers than it used to take to just upgrade the mainframes.Setting aside the cost of Client equipment, the proliferation of corporate applications, including business logic, to hundreds or thousands of machines has become a major cost factor for corporations. Where IT staffs used to be able to maintain all the corporate software assets in one central location, they now need to maintain corporate software spread all across the corporation, often housed in computers that are out of IT control.There are many estimates available that the cost of Client/Server computing is eight or more times the cost of the equipment alone. Several companies offer large, expensive systems that have the sole purpose of maintaining corporate software spread out all over the corporation.The issue here is not personal-productivity software such as word processors and spreadsheets. Personal software products have enabled knowledge workers to attain new heights of productivity. The issue is the maintenance of corporate software, such as order-entry and accounting. Imagine the difficulty of making a schema change in acorporate database, and synchronizing that change with the updating of thousands of copies of the corresponding Client software.It is true that the use of department-level LANs can bring down the number of copies that need to be updated to hundreds, instead of thousands. The size of the LANs must be limited, because the large size of the fat client software requires a responsive LAN or else the users will just copy the enterprise software to their own machines, bringing us back to thousands of copies to be maintained.The task of making simultaneous changes to even hundreds of copies of client software is still a daunting one.The split-up of the corporate applications is different for Browser/Server . The user interface and the data interaction components are still run on the user machine, but the business logic usually remains on the Server, usually in a special Server called an Application Server.The user interface and data interaction components do run on the Client, but they are not ultimately stored there. They are most probably Java applets stored in a corporate Intranet Web Server, and they are automatically loaded into the Browser software on the user machine as they are needed. If a newer version becomes available, then that version is automatically loaded.We have achieved the same benefits as with Client/Server, but without the enormous distribution and maintenance problem. The only software that the user machine needs, besides an operating system and personal productivity software, is a Web Browser that runs Java applets.Since much of the "fat" of the application resides in the business logic Application Server, the need to constantly upgrade the user machines is greatly reduced. There is no need to spend precious time and hard disk space installing corporate software on thousands of user machines, or hundreds of departmental LANs.Corporate software assets now all reside in corporate servers, under IT control. Updates to systems are now easily coordinated.So exactly what is Browser/Server technology? Browser/Server is an important adaptation of modern network-centric computing that optimizes the performance of mission critical enterprise applications deployed via the corporate intranet and/or World Wide Web.Browser/Server accomplishes these performance gains with customized multi-tiered infrastructure and application designs that produce production solutions with reduced network requests and increased user interaction.(二)SOFTWARE QUALITY ASSURANCEThe activity of software quality assurance is closely related to verification and validation activities carried out at each stage of the software life cycle[1].Indeed,in many organizations there is no distinction made between these activities.However,quality assurance and other verification and validation activities are actually quite separate,with quality assurance being a management function and verification andvalidation being part of the process of software development[2].An appropriate definition of software quality assurance is provided by Bersoff(1984):Quality assurance consists of those procedures,techniques and tools applied by professionals to ensure that a product meets or exceeds prespecified standards during a products development cycle[3];and without specific prescribed standards,quality assurance entails ensuring that a product meets or exceed a minimal industrial and / or commercially acceptable level of excellence.This definition is,of course[4],a fairly general one and it suggests that,firstly,software standards can be established and,secondly,the level of excellence of a software product can be estimated.The development of software engineering project standards is an extremely difficult process. A standard is some abstract representation of a product which defines the minimal level of performance,robustness,organization,etc.,which the developed product must attain[5].At the time of writing,some software standards have been developed by the IEEE,ANSI and military organizations.These standards describe configuration management plans,documentation,specification practices,software comparisons,etc.Other standards which are currently under development include standards for reliability,measurement,the use of Ada as PDL[6],software testing and others.Bransta d and Powell(1984)describe both existing and planned software standards as well as discussing standardization in more general terms.The problem with national software standards is that they tend to be very general in nature. This is inevitable as,unlike hardware,we are not yet capable of quantifying most software characteristics.Effective quality assurance within an organization thus requires the development of more specific organizational standards.Of course,the problem which arises in developing software standards for quality assurance and which makes the assessment of the level of excellence of a software product difficult to assess is the elusive nature of software quality.Boehm et al.(1978)suggest that quality criteria include but are not limited to:Economy Correctness ResilienceIntegrity Reliability UsabilityDocumentation Modifiability ClarityUnderstandability Validity MaintainabilityFlexibility Generality PortabilityInteroperability Testability EfficiencyModularity ReusabilityExactly how some of these criteria may be quantified is not clear.Furthermore,as Buckley and Poston(1984)point out,parts of this definition may have no value for a particular product.It may be possible to transfer a system from a microcomputer to a large mainframe but this is often a nonsensical thing to do.Assessment of software quality thus still relies on the judgement of skilled individuals although this does not mean that it is necessarily inferior to quantitative assessment.After all,we cannotassess a painting or a play quantitatively yet this does not preclude a judgement of its quality.Within an organization,quality assurance should be carried out by an independent software quality assurance team who reports directly to management above the project manager level.The quality assurance team should not be associated with any particular development group but should be responsible for quality assurance across all project groups in an organization.The activity of quality assurance involves sitting in on design reviews[7],program walkthroughs,etc. ,and reporting on the overall quality of the product as it is developed.It also involves checking that the finished product and its associated documentation conform to those standards which exist.The quality assurance team may also assess if the different representations of a product(requirements,design,code)are consistent and complete.Notice that quality assurance is not the same as system testing.It is the development or testing team’s responsibility to validate the system,with the quality assurance team reporting on both the validation and the adequacy of the validation effort.This naturally involves quality assurance being closely associated with the final integration testing of the system.Software quality assurance is now an emerging subdiscipline of software engineering[8].As Buckly and Poston point out,effective software quality assurance is likely to lead to an ultimate reduction in software costs.However,the major hurdle in the path of software management in this area is the lack of usable software standards.The development of accepted and generally applicable standards should be one of the principal goals of research in software engineering.(三)SOFTWARE TESTING1. Purpose of TestingNo matter how capably we write programs,it is clear front the variety of possible errors that we should check to insure that our modules are coded correctly.Many programmers view testing as a demonstration that their programs perform properly.However,the idea of demonstrating correctness is really the reverse of what testing is all about.We test a program in order to demonstrate he existence of an error.Because our goal is to discover errors,we can consider a test successful only when an error is discovered.Once an error is found,“debugging”or error correction is the process of determining what causes the error and of making changes to the system so that the error no longer exists.2.Stages of TestingIn the development of a large system,testing involves several stages.First,each program module is tested as a single program,usually isolated from the other programs in the system.Such testing,known as module testing or unit-testing,verifies that the module functions properly with the types of input expected from studying themodule design.Unit testing is done in a controlled environment whenever possible so that the test team can feed a predetermined set of data to the module being tested and observe what output data are produced[1].In addition,the test team checks the internal data structures,the logic,and the boundary conditions for the input and output data.When collections of modules have been unit-tested,the next step is to insure that the interfaces among the modules are defined and handled properly.Integration testing is the process of verifying that the components of a system work together as described in the program design and system design specifications.When collections of modules have been unit-tested,the next step is to insure that the interfaces among the modules are defined and handled properly.Integration testing is the process of verifying that the components of a system work together as described in the program design and system design specifications.Once we are sure that information is passed among modules according to the design prescriptions,we test the system to assure that it has the desired functionality.A function test evaluates the system to determine if the functions described by the requirements specification are actually performed by the integrated system [2].The result,then,is a functioning system.Recall that the requirements were specified in two ways:first in the customer’s terminology and again as a set of software and hardware requirements.The function test compares the system being built with the functions described in the software and hardware requirements.Then,a performance test compares the system with the remainder of the software and hardware requirements.If the test is performed in the customer’s actual working environment,a successful test yields a validated system.However,if the test must be performed in a simulated environment,the resulting system is a verified system.When the performance test is complete,we as developers are certain that the system functions according to our understanding of the system description.The next step is to confer with the customer to make certain that the system works according to the customer’s expectations.We join with the customer to perform an acceptance test in which the system is checked against the customer’ s requirements description.When the acceptance test is complete,the accepted system is installed in the environment in which it will be used;a final I nstallation test is performed to make sure that the system still functions as it should.Fig. 8-2 illustrates the several stages of testing.Although systems may differ in size,the type of testing described in each stage is necessary for assuring the proper performance of any system being developed.译文:(一) asp技术1. 本文首先介绍了课题研究所用的技术:浏览器/服务器结构以及Web应用的相关数据库访问技术。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
毕业论文外文翻译ASP from A to ZNancy Winnick ClutsDeveloper Technology EngineerMicrosoft CorporationOctober 22, 1998ContentsIntroductionWhat ASP IsHow ASP WorksASP from A to ZBibliographyIntroductionThere's lots of helpful information about Active Server Pages (ASP) available on this site and other sites. If you have plenty of time to search for the information, you can find answers to most of your questions. But if you want to find out what tools you can use to debug ASP or how to handle errors, you need to do some digging. This article provides an easy way to find information that pertains to ASP, including a short definition of what ASP is, how ASP works, and an alphabetical list of terms and tips that relate to ASP. In the A-to-Z list, you will see a brief description as well as pertinent links to more detailed information (when that information is available). This article is meant to be a "living" document. That means that I plan on updating it with new tips and removing tips that no longer apply. If you are an ASP developer and have a "juicy" tip, send it to me. If I publish it here, you'll get credit and the everlasting gratitude of throngs of other ASP developers.What ASP IsActive Server Pages is a programming environment that provides the ability to combine HTML, scripting, and components to create powerful Internet applications that run on your server. If you are already creating Web sites that combine HTML, scripting, and some reusable components, you can use ASP to glue these items together. You can create an HTML interface for your application by adding script commands to your HTML pages and you can encapsulate your business logic into reusable components. These components can be called from script or other components.How ASP WorksWhen you incorporate ASP into your Web site, here's what happens:1.The user brings up a Web site (like MSDN Library) where the default page has the extension .asp.2.The browser requests the ASP file from the Web server.3.The server-side script begins to run with ASP.4.ASP processes the requested file sequentially (top-down), executes any script commands contained in thefile, and produces an HTML Web page.5.The Web page is sent to the browser.Because your script runs on the server, the Web server does all of the processing and standard HTML pages can be generated and sent to the browser. This means that your Web pages are limited only by what your Web server supports. Another benefit of having your script reside on the server is that the user cannot "view source" on the original script and code. Instead, the user sees only the generated HTML as well as non-HTML content, such as XML, on the pages that are being viewed.ASP from A to ZThis section contains a list of terms and tips to help you understand ASP. They are listed in alphabetical order. Scroll down to the topic that interests you or click the letter in the alphabet below to jump down to the section containing the topic. I cribbed, er, I mean, compiled these tips and definitions from a number of sources, including technical articles (listed in the bibliography below), Knowledge Base articles, and a beta version of the Microsoft® Internet Information Server (IIS) 5.0 documentation (I'm so lucky!).A B C D E F G I J L M O P Q R S T V W X ADOActive Data Objects (ADO) provides a programming model for an OLE-DB data source. It is the database model that ASP uses; however, ASP can use other database access mechanisms. ADO supports the following installable objects, which are often used in ASP files: Command, Connection, Recordset, Field, and Error. Refer to the ADO Web site at /data/ado/ for more information than you can shake a stick at.ApplicationsASP is not just for prototyping. When using ASP as a solution, design your solution as an application instead of designing stand-alone ASP pages. As far as objects are concerned, it's best to take a look at what you need to accomplish and decide what you need, then whether you can buy the objects or will need to create the objects yourself. Take into consideration caching, scalability, reusability, security, and consistency.BottlenecksIdentify your bottlenecks (that is, the database, network card, or network connection) using the tools available: WCAT, NetMon, and performance counters. To improve server performance, take a look at all parts of the system for potential bottlenecks, including hardware configuration and software settings. This way, if you are ever asked to scale the project larger, you will know where the work needs to be done.Browser ConnectionIn IIS 4.0, use the Response.IsClientConnected property to determine if the browser is still connected. If the browser is not connected, you can conserve CPU cycles by ceasing the processing of the ASP page. Refer to the Knowledge Base article Use IsClientConnected to Check if Browser is Connected.BufferingTurn buffering ON. By default it is OFF in IIS 4.0; in IIS 5.0, buffering is ON by default. You should buffer your ASP files so that you can abort sending a Web page. This might happen if the script being processed runs into a problem or if a user does not have appropriate security credentials. If this happens, and if you are using IIS 5.0, you can transfer the user to another page using Server.Transfer, or clear the buffer (using the Clear method of the Response object) to send different content to the user.C++If you are creating page-level components, you can use server scriptlets, Visual Basic®, V isual J++™, and VisualC++®. If you are writing components that will be in application or session state, we recommend that you write them in C++ or Java so you can create them as both-threaded. Visual Basic is apartment-threaded. See the section below on threading for more details.CachingIf your application sends pages to the client via a proxy server, the proxy server may cache pages to return them more quickly to the client. This reduces the load on the network and the Web server. To prevent a browser from caching ASP pages, set Response.Expires to some negative number. This will force the cached pages to expire immediately. If you set Response.Expires to 0, and if your browser clock is behind by a few minutes, the page won't expire immediately. If your Web site contains objects that do not expire often, such as images, set the expiration to some time in the future. This will greatly increase the speed at which a page is refreshed or downloaded. Proxy caching via pragma:nocache is already done for you by IIS, so you don't have to set this in your headers. More information about caching can be found in Got Any Cache?Client-Side ScriptsDistribute the work on your Web site by providing script on both the client and the server. See Client-Side and Server-Side Objects.COM Object DebuggingIf you create a COM object and use it through ASP with Server.CreateObject, you cannot go back into your development environment and recompile the COM DLL without restarting the IIS Admin and W3SVC (Web server) service. Otherwise, the COM DLL will be locked. To restart these services, do the following:1.At a command prompt, type net stop iisadmin /y. Please note that this will shut down IIS' parent service,IIS Admin. This will also shut down FTP and other services that are children of IIS Admin. If you type only net stop w3svc, inetinfo.exe will not be unloaded.2.At a command prompt, type net start w3svc. This will restart IIS Admin and the W3SVC service (Webserver).3.You may recompile at any point after Step 1. Once you refer to an object that loads your DLL, you must repeatStep 1 before building the component successfully.ComponentsUse components to encapsulate the business logic in your ASP applications. You can create your own components or buy them "off the shelf." Once you have a component, you can reuse it wherever you need it. Develop your components using C++ or Java. Because Visual Basic is not marked as both-threaded, you cannot use Visual Basic components within application scope. If you design your own components, be sure to design components that are stateless (that is, the methods you define take parameters, rather than having a script set properties then call the method without the parameters).Stateless components are far more flexible and reusable. In addition, if you have areas in your script where you have more than 100 lines of contiguous script, consider turning that script into a server scriptlet. More information about creating components can be found in the Active Server Components section of the Server area of the MSDN Library.A comprehensive list of third-party components available for ASP can be found in the ASP Component Catalog. ConnectionsPool your connections for optimal performance. By pooling your connections, your resources are allocated more efficiently. For support of multiple logons, provide one connection for read-only access and one connection forread/write access. In general, avoid putting ADO connections in session state. ODBC (version 3.0 and later) automatically does connection pooling for you, and OLE-DB provides session pooling.Cookie MungerASP uses cookies to store the session identifier (ASP SessionID). For machines that have cookies turned off, the Cookie Munger tool can be used to strip out cookies and put the information in a URL. This enables the use of "cookies" without actually sending out cookies. For more information, see Simulating Cookies with the Cookie Munger.CPUDesign for scalability. Stress your ASP applications at 100% CPU to determine how to best allocate your resources. Use WCAT or a third-party tool such as Mercury's LoadRunner to tune your performance.Data Access ComponentsRead Improving the Performance of Data Access Components in IIS 4.0 for a detailed explanation of the techniques that you can use to improve performance.DatabaseUse ADO for adding database access to your Web pages via components. ADO can be used to create small components that connect to any OLE-DB compliant data source, whether it's relational or non-relational. This includes spreadsheets, databases, or e-mail directories.DebuggingThere are many tools available for debugging, including the Microsoft Script Debugger. The Script Debugger lets you run your server-side scripts one line at a time, monitor the value of variables, properties, or array elements during execution, and trace procedures.Important:Once you have finished debugging your Web site, don't forget to turn off debuggingon your live servers. This will increase performance.Dictionary ObjectThe Dictionary object enables you to look up and store arbitrary key-data pairs rapidly. The Dictionary object gives you access to items in the array by key, so it is faster to find things that aren't stored contiguously in memory. Instead, you use a key rather than having to know where in the array the object is stored.Disconnected RecordsetsDisconnecting a Recordset means you can view the Recordset's data after severing the connection to the data store that generated the Recordset. You can create a disconnected ADO Recordset in-process with a Recordset whose CursorLocation property is adUseClient and whose ActiveConnection property is set to NULL/Nothing. You can then put the Recordset into ASP application state and use the Recordset Clone method to share and access the Recordset in your ASP files. You can then pass this Recordset to a remote client using either RDS or DCOM (or both together). Read the Knowledge Base articles HOWTO: Getting ADO Disconnected Recordsets in VBA/C++/Java and INFO: Disconnected Recordsets with ADO or RDS for detailed information.Error HandlingYou can use the ASPError object to obtain information about an IIS 5.0 error condition that has occurred in an ASP file. The ASPError object is returned by the Server.GetLastError method. If the error condition generates an exception and you are using VBScript, use OnErr. In JScript™, use the try…catch method. Detailed information about error handling can be found in the article Microsoft JScript Version 5.0 Adds Exception Handling, by Michael Edwards.Flow ControlFlow control is the ability to set the flow of your ASP application. Flow is controlled through Response methods and two new Server methods (for IIS 5.0). Using Response.Redirect causes posted data to be lost. The Response.End method causes ASP to stop when an error is found. You do not need to call this method after callingResponse.Redirect. The Server.Transfer method is the same as Response.Redirect, except that the work is done on the server and posted data is not lost. The Server.Execute method will flow into a nested ASP call and return execution to where you were before the error occurred.FileSystem ObjectThe FileSystem object blocks on files. If you are running a high-volume Web site, don't use the FileSystem object because the performance of accessing a single file will degrade. If you are using multiple files that are not being accessed at the same time, use of the FileSystem object will not result in a performance hit.Global.asaThe Global.asa file is an optional file in which you can specify event procedures and declare objects that have session or application scope. It is not a content file displayed to the users; it stores event information and objects used globally by the application. This file must be named Global.asa and must be stored in the root directory of the application. An application can have only one Global.asa file. Instead of using the ASP FileSystem object to read files on a page, load the file(s) into an Application level array in Global.asa.GlueUse ASP for the glue and components for the business logic. If you have 100 or more lines of consecutive script, turn it into a component using server scriptlets (bearing in mind that server scriptlets have the same limitations as Visual Basic components).InetLoadThe InetLoad tool can be used to tune your Web site. This tool generates customizable loads on various Internet services, over a broad range of Internet protocols, including HTTP, SMTP, POP3, and LDAP. You can use this tool to simulate traffic on your Web site. InetLoad is available at /software/internet/IN00470.htm. See also WCATW and Mercury LoadRunner for tuning tools.InternationalizationIf you are providing a Web site that will be viewed in countries other than the United States, you can use the CODEPAGE tag within the <% %> delimiters to specify the proper code page. Alternatively, you can use the Session.CodePage property. Read all about it at /library/en-us/dnasp/html/nextgen.asp. In addition to CODEPAGE, you can also use the Local Language Identifier (LCID) to determine the language that the user has set as her preference. Detailed information about LCID can be found in the IMultiLanguage Reference.IsolationYou can separate IIS, ASP, and components into different processes for better performance. The drawback to putting these in different processes is the cross-process communication performance hit. You can put IIS, ASP, and your components in one process. This is the fastest method, but if your component goes down, it can bring down ASP and IIS. You can put IIS in one process and ASP with your components in another so that IIS will not crash if your component or ASP crashes. You can put IIS and ASP in one process and your component in another process. This is slower than the previous option due to all of the cross-process communication; however, it does insulate IIS and ASP from a buggy component. The slowest but "safest" option is to put IIS, ASP, and your components all in separate processes. If one crashes, nothing else will, but the performance will be very, very slow. It's a better idea to test your components really well.Component Configuration Protection SpeedIIS, ASP, and components in one process 1 4IIS in one process, ASP and components in another process 2 3IIS and ASP in one process, components in another process 3 2IIS in one process, ASP in one process, components in one process 4 1Legend: 1 = Least, 4 = MostJavaUse Java (or C++) to write components. Java is a powerful language that you can use to create components that are both-threaded.LoggingYou can turn on URI_Query extended logging to log ASP failures. This is not turned on by default. Turning it on is tricky, so here are the steps:1.Select a Web or FTP site and open its property sheets.2.Enable logging if it is disabled and select the W3C Extended log file format.3.Click Properties.4.On the Extended Properties property sheet, select the fields you want to log (in this instance, URI_Query).By default, Time, Client IP Address, Method, URI Stem, and HTTP Status are enabled.5.Click Apply.You can also log to the Windows NT® Server Event Log; however, logging to the Windows NT Server Event Log is not a good idea if you've got lots of errors or are in debugging mode because you can fill up the log quickly. Using the Windows NT Performance Monitor, you can log a variety of error conditions, including how many ASP requests have failed and how many errors occurred during the script run-time.MailUse Collaboration Data Objects (CDO) to send mail for Windows NT Server. CDO is a lightweight version of CDO for Exchange. It works on SMTP or Exchange. If you are using another e-mail protocol, use a third-party component. A comprehensive list is at /workshop/server/components/catalog.asp.<OBJECT> tagIf you need to refer to objects that may not be used, instantiate them by using the <OBJECT> tag rather than using Server.CreateObject. Using Server.CreateObject causes the object to be created immediately. If you don't use that object later, you end up wasting resources.译文内容介绍什么是ASPASP怎样工作图书目录介绍ASP有很多有用的信息被用在这个网站或者其它网站。
