Cisco路由器安全配置方案
Cisco系列路由器NAT配置详解-电脑资料

Cisco系列路由器NAT配置详解-电脑资料INTERNET共享资源的方式越来越多,就大多数而言,DDN专线以其性能稳定、扩充性好的优势成为普遍采用的方式,DDN方式的连接在硬件的需求上是简单的,仅需要一台路由器(router)、代理服务器(proxyserver)即可,但在系统的配置上对许多的网络管理人员来讲是一个比较棘手的问题,。
下面以CISCO路由器为例,笔者就几种比较成功的配置方法作以介绍,以供同行借鉴:一、直接通过路由器访问INTERNET资源的配置1.总体思路和设备连接方法一般情况下,单位内部的局域网都使用INTERNET上的保留地址:10.0.0.0/8:10.0.0.0~10.255.255.255172.16.0.0/12:172.16.0.0~172.31.255.255192.168.0.0/16:192.168.0.0~192.168.255.255在常规情况下,单位内部的工作站在直接利用路由对外访问时,会因工作站使用的是互联网上的保留地址,而被路由器过滤掉,从而导致无法访问互联网资源。
解决这一问题的办法是利用路由操作系统提供的NAT (Network AddressTranslation)地址转换功能,将内部网的私有地址转换成互联网上的合法地址,使得不具有合法IP地址的用户可以通过NAT访问到外部Internet。
这样做的好处是无需配备代理服务器,减少投资,还可以节约合法IP地址,并提高了内部网络的安全性。
NAT有两种类型:Single模式和global模式。
使用NAT的single模式,就像它的名字一样,可以将众多的本地局域网主机映射为一个Internet地址,电脑资料《Cisco系列路由器NAT配置详解》(https://www.)。
局域网内的所有主机对外部Internet网络而言,都被看做一个Internet用户。
本地局域网内的主机继续使用本地地址。
使用NAT的global模式,路由器的接口将众多的本地局域网主机映射为一定的Internet地址范围(IP地址池)。
Cisco路由器IPsec配置

Cisco路由器IPsec配置Cisco路由器IPsec配置本文档将详细介绍如何在Cisco路由器上配置IPsec。
IPsec (Internet Protocol Security)是一种安全协议,用于在Internet上的通信中保护数据传输的机密性和完整性。
通过配置IPsec,您可以为您的网络连接提供更高的安全性。
以下是配置IPsec的步骤:1.准备工作在开始配置IPsec之前,请确保您拥有以下准备工作:- 一台运行Cisco IOS的路由器- 适当的网络连接和配置- 了解网络拓扑和连接要求2.IPsec基础知识在配置IPsec之前,了解以下IPsec的基本概念和术语将非常有帮助:- 安全关联(SA):包含用于加密和验证数据包的安全参数。
- 安全策略数据库(SPD):定义将被保护的数据流以及如何保护它们的规则集合。
- 安全策略管理器(SPM):用于管理SPD和SA的组件。
- IPsec隧道:通过互联网在两个网络之间创建加密的虚拟通道。
3.IPsec配置示例下面是一个IPsec配置示例,用于在两个路由器之间建立安全连接:步骤1:配置IKE策略- 定义IKE策略,包括加密算法、验证方法和生命周期设置。
- 将策略应用于本地和远程对等体。
步骤2:配置IPsec策略- 定义IPsec策略,包括加密和验证算法、生命周期设置和流量选择。
- 将策略应用于本地和远程对等体。
步骤3:配置IPsec隧道- 配置本地和远程对等体之间的IPsec隧道。
- 配置隧道的安全参数,包括隧道模式、加密算法和身份验证方法。
步骤4:验证IPsec配置- 使用测试工具验证IPsec隧道是否成功建立。
- 监控IPsec隧道状态和流量。
4.附件附件1:IPsec配置示例文件本文档涉及附件,附件1为IPsec配置示例文件,可供参考。
5.法律名词及注释- IPsec: 一种用于保护数据传输安全的协议,提供机密性和完整性保护。
- SA: 安全关联,包含用于加密和验证数据包的安全参数。
Cisco路由器配置实例(经典)
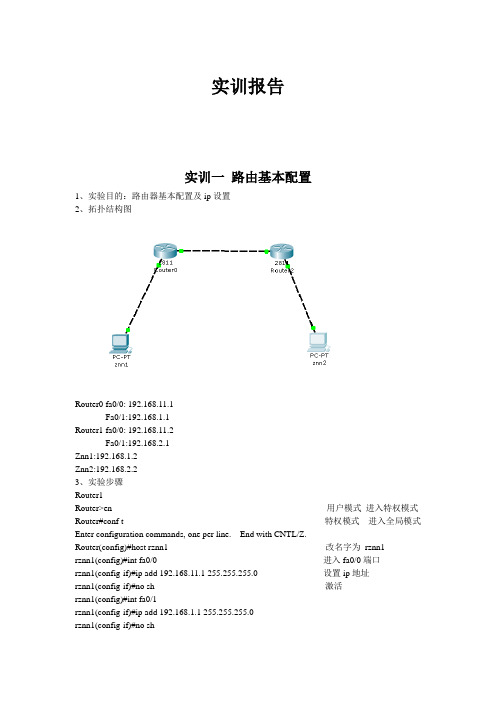
实训报告实训一路由基本配置1、实验目的:路由器基本配置及ip设置2、拓扑结构图Router0 fa0/0: 192.168.11.1Fa0/1:192.168.1.1Router1 fa0/0: 192.168.11.2Fa0/1:192.168.2.1Znn1:192.168.1.2Znn2:192.168.2.23、实验步骤Router1Router>en 用户模式进入特权模式Router#conf t 特权模式进入全局模式Enter configuration commands, one per line. End with CNTL/Z.Router(config)#host rznn1 改名字为rznn1rznn1(config)#int fa0/0 进入fa0/0端口rznn1(config-if)#ip add 192.168.11.1 255.255.255.0 设置ip地址rznn1(config-if)#no sh 激活rznn1(config)#int fa0/1rznn1(config-if)#ip add 192.168.1.1 255.255.255.0rznn1(config-if)#no shrznn1(config-if)#exitrznn1(config)#exitrznn1#copy running-config startup-config 保存Destination filename [startup-config]? startup-configrznn1#conf trznn1(config)#enable secret password 222 设置密文rznn1#show ip interface b 显示Interface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.1 YES manual up up FastEthernet0/1 192.168.1.1 YES manual up upVlan1 unassigned YES manual administratively down downrouter 2outer>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host rznn2rznn2(config)#int fa0/0rznn2(config-if)#ip add 192.168.11.2 255.255.255.0rznn2(config-if)#no shrznn2(config)#int fa0/1rznn2(config-if)#ip add 192.168.2.1 255.255.255.0rznn2(config-if)#no shRznn2#copy running-config startup-config 保存Destination filename [startup-config]? startup-configrznn2(config-if)#exitrznn2(config)#exitrznn2#conf trznn2(config)#enable secret 222rznn2#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.2 YES manual up up FastEthernet0/1 192.168.2.1 YES manual up upVlan1 unassigned YES manual administratively down down实训二1、远程登录、密码设置及验证为路由器开设telnet端口,PC机可以远程登陆到Rznn3(Router 1)拓扑结构图Router0:192.168.1.1Pc:192.168.1.2步骤rznn3>rznn3>enrznn3#conf tEnter configuration commands, one per line. End with CNTL/Z.rznn3(config)#no ip domain lookuprznn3(config)#line cons 0rznn3(config-line)#password znnrznn3(config-line)#loginrznn3(config-line)#no exec-trznn3(config-line)#logg syncrznn3(config-line)#exitrznn3(config)#int fa0/0rznn3(config-if)#ip add 192.168.1.1 255.255.255.0rznn3(config-if)#no shrznn3(config-if)#exitrznn3(config)#line vty 0 4 打通五个端口rznn3(config-line)#password cisco 设置密码rznn3(config-line)#login 保存rznn3(config-line)#exit4、测试:实训三命令组1、目的:八条命令(no ip domain lookup\line cons 0\password\login\no exec-t\logg sync\show version\reload\copy running-config startup-config)\show cdp neighbors)2、拓扑结构图Router0 fa0/0: 192.168.11.1Router1 fa0/0: 192.168.11.23、步骤rznn1#conf tEnter configuration commands, one per line. End with CNTL/Z.1、rznn1(config)#no ip domain lookup 取消域名查找转换2、rznn1(config)#line cons 0 打开cons 0端口3、rznn1(config-line)#password znn 设置密码为znnrznn1(config-line)#login 保存rznn1(config-line)#no exec-t 设置永不超时4、rznn1(config-line)#logg sync 产生日志5、rznn1#show version 显示思科路由系统版本信息Cisco IOS Software, 2800 Software (C2800NM-ADVIPSERVICESK9-M), Version 12.4(15)T1, RELEASE SOFTWARE (fc2)Technical Support: /techsupportCopyright (c) 1986-2007 by Cisco Systems, Inc.Compiled Wed 18-Jul-07 06:21 by pt_rel_team6、rznn1#show cdp neighbors 查看路由器连接的相邻路由器的相关信息Capability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDrznn2 Fas 0/0 139 R C2800 Fas 0/07、rznn1#copy running-config startup-config 保存刚才指令Destination filename [startup-config]? startup-configBuilding configuration...[OK]8、rznn1#reload 重启路由器Proceed with reload? [confirm]System Bootstrap, Version 12.1(3r)T2, RELEASE SOFTWARE (fc1)Copyright (c) 2000 by cisco Systems, Inc.cisco 2811 (MPC860) processor (revision 0x200) with 60416K/5120K bytes of memorySelf decompressing the image :########################################################################## [OK] Restricted Rights Legendrznn1#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.1 YES manual up up FastEthernet0/1 192.168.1.1 YES manual up upVlan1 unassigned YES manual administratively down down9、rznn1(config-if)#ip add 192.168.3.1 255.255.255.0 重置ip地址rznn1#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.3.1 YES manual up up FastEthernet0/1 192.168.1.1 YES manual up up Vlan1 unassigned YES manual administratively down down实训四发现协议1、实训目的通过发现协议显示路由器相邻路由的端口信息2、拓扑结构Router0:192.168.11.1Router1:fa0/0 192.168.11.2Fa0/1 192.168.12.1Router2:192.168.12.23、步骤R1路由器Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r1r1(config)#int fa0/0r1(config-if)#ip add 192.168.11.1 255.255.255.0r1(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to upr1(config-if)#r1(config-if)#exitr1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.1 YES manual up down FastEthernet0/1 unassigned YES manual administratively down downVlan1 unassigned YES manual administratively down downR2 路由器Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r2r2(config)#int fa0/0r2(config-if)#ip add 192.168.11.2 255.255.255.0r2(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up r2(config-if)#exitr2(config)#exitr2#%SYS-5-CONFIG_I: Configured from console by consoler2#conf tEnter configuration commands, one per line. End with CNTL/Z.r2(config)#int fa0/0r2(config-if)#int fa0/1r2(config-if)#ip add 192.168.12.1 255.255.255.0r2(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/1, changed state to upr2(config-if)#exitr2(config)#exitr2#%SYS-5-CONFIG_I: Configured from console by consoler2#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.11.2 YES manual up upFastEthernet0/1 192.168.12.1 YES manual up down Vlan1 unassigned YES manual administratively down downR3路由器Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r3r3(config)#int fa0/0r3(config-if)#ip add 192.168.12.2 255.255.255.0r3(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up r3(config-if)#exitr3(config)#exitr3#%SYS-5-CONFIG_I: Configured from console by consoler3#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.12.2 YES manual up up FastEthernet0/1 unassigned YES manual administratively down downVlan1 unassigned YES manual administratively down downR1发现邻居r1#show cdp neighborsCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDr2 Fas 0/0 165 R C2800 Fas 0/0R2发现邻居r2#show cdp neighborsCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDr1 Fas 0/0 176 R C1841 Fas 0/0r3 Fas 0/1 130 R C1841 Fas 0/0R3发现邻居r3#show cdp neighborsCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDr2 Fas 0/0 166 R C2800 Fas 0/14、总结show 命令(1)show ip interface b (显示端口ip信息)(2)show version (显示ios版本信息)(3)show running-config (显示刚才使用的命令配置信息)(4)show cdp neighbors (显示发现邻居直连设备信息)(5)show interface (显示所有端口详细信息)实训五静态路由1、实验目的:将不同网段的网络配通(ip route)Ip route语法:ip route 目标地址子网掩码相邻路由器接口地址Show ip route2、试验拓扑:Router0:192.168.11.1Router1:fa0/0 192.168.11.2Fa0/1 192.168.12.1Router2:192.168.12.23、实验步骤:Router1Router>enRouter#conf tRouter(config)#host r1r1(config)#int fa0/0r1(config-if)#ip add 192.168.11.1 255.255.255.0r1(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to upr1(config-if)#exitr1(config)#exitr1#show ip interface bInterface IP-Address OK? Method Status ProtocolFastEthernet0/0 192.168.11.1 YES manual up downFastEthernet0/1 unassigned YES manual administratively down downVlan1 unassigned YES manual administratively down downr1#%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up r1#ping 192.168.12.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.1, timeout is 2 seconds:.....Success rate is 0 percent (0/5)r1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#ip route 192.168.12.0 255.255.255.0 192.168.11.2r1(config)#exitr1#ping 192.168.12.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 msr1#ping 192.168.12.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:.....Success rate is 0 percent (0/5)r1#ping 192.168.12.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 47/62/78 msr1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0S 192.168.12.0/24 [1/0] via 192.168.11.2Router3Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r3r3(config)#int fa0/0r3(config-if)#ip add 192.168.12.2 255.255.255.0r3(config-if)#no sh%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up r3(config-if)#exitr3(config)#exitr3#%SYS-5-CONFIG_I: Configured from console by consoler3#show ip interface bInterface IP-Address OK? Method Status Protocol FastEthernet0/0 192.168.12.2 YES manual up up FastEthernet0/1 unassigned YES manual administratively down downVlan1 unassigned YES manual administratively down downr3#conf tEnter configuration commands, one per line. End with CNTL/Z.r3(config)#ip route 192.168.11.0 255.255.255.0 192.168.12.1r3(config)#exitr3#ping 192.168.11.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.2, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 msr3#ping 192.168.11.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 62/62/63 msr3#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setS 192.168.11.0/24 [1/0] via 192.168.12.1C 192.168.12.0/24 is directly connected, FastEthernet0/04、默认路由Route 1r1>enr1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#no ip route 192.168.12.0 255.255.255.0 192.168.11.2%No matching route to deleter1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0r1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#ip route 0.0.0.0 0.0.0.0 192.168.11.2r1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.11.2 to network 0.0.0.0C 192.168.11.0/24 is directly connected, FastEthernet0/0S* 0.0.0.0/0 [1/0] via 192.168.11.2r1#ping 192.168.12.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 16/28/31 msr1#ping 192.168.12.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 62/62/63 msRoute 3r1>enr1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#no ip route 192.168.12.0 255.255.255.0 192.168.11.2%No matching route to deleter1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0r1#conf tEnter configuration commands, one per line. End with CNTL/Z.r1(config)#ip route 0.0.0.0 0.0.0.0 192.168.11.2r1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoler1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.11.2 to network 0.0.0.0C 192.168.11.0/24 is directly connected, FastEthernet0/0S* 0.0.0.0/0 [1/0] via 192.168.11.2r3#ping 192.168.11.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.1, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 62/62/63 ms实训六动态路由RIP 协议1、实验目的使用配置动态路由启动Rip协议使用到的命令(router rip/network/show ip protocols/show ip route)2、实验拓扑R1 fa0/0 192.168.11.1R2 fa0/0 192.168.11.2fa0/1 192.168.12.1R3 fa0/0 192.168.12.23、实验步骤R1Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z. Router(config)#host r1r1(config)#int fa0/0r1(config-if)#ip add 192.168.11.1 255.255.255.0r1(config-if)#no shr1(config-if)#exitr1(config)#router ripr1(config-router)#network 192.168.11.0r1(config-router)#exitr1(config)#exitr1#%SYS-5-CONFIG_I: Configured from console by consoleR2Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z. Router(config)#host r2r2(config)#int fa0/0r2(config-if)#ip add 192.168.11.2 255.255.255.0r2(config-if)#no shr2(config-if)#exitr2(config)#int fa0/1r2(config-if)#ip add 192.168.12.1 255.255.255.0r2(config-if)#no shr2(config-if)#exitr2(config)#router ripr2(config-router)#network 192.168.11.0r2(config-router)#network 192.168.12.0r2(config-router)#exitr2(config)#exitr2#R3Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z. Router(config)#host r3r3(config)#int fa0/0r3(config-if)#ip add 192.168.12.2 255.255.255.0r3(config-if)#no shr3(config-if)#exitr3(config)#router ripr3(config-router)#network 192.168.12.0r3(config-router)#exitr3(config)#exitr3#%SYS-5-CONFIG_I: Configured from console by console4、实验测试R1r1#show ip protocolsRouting Protocol is "rip"Sending updates every 30 seconds, next due in 10 secondsInvalid after 180 seconds, hold down 180, flushed after 240 Outgoing update filter list for all interfaces is not setIncoming update filter list for all interfaces is not set Redistributing: ripDefault version control: send version 1, receive any version Interface Send Recv Triggered RIP Key-chain FastEthernet0/0 1 2 1Automatic network summarization is in effectMaximum path: 4Routing for Networks:192.168.11.0Passive Interface(s):Routing Information Sources:Gateway Distance Last UpdateDistance: (default is 120)r1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0R 192.168.12.0/24 [120/1] via 192.168.11.2, 00:00:24, FastEthernet0/0 r1#ping 192.168.12.0Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.12.0, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 msR2r2#show ip protocolsRouting Protocol is "rip"Sending updates every 30 seconds, next due in 21 secondsInvalid after 180 seconds, hold down 180, flushed after 240Outgoing update filter list for all interfaces is not setIncoming update filter list for all interfaces is not setRedistributing: ripDefault version control: send version 1, receive any versionInterface Send Recv Triggered RIP Key-chain FastEthernet0/0 1 2 1FastEthernet0/1 1 2 1Automatic network summarization is in effectMaximum path: 4Routing for Networks:192.168.11.0192.168.12.0Passive Interface(s):Routing Information Sources:Gateway Distance Last UpdateDistance: (default is 120)r2#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setC 192.168.11.0/24 is directly connected, FastEthernet0/0C 192.168.12.0/24 is directly connected, FastEthernet0/1R3r3#show ip protocolsRouting Protocol is "rip"Sending updates every 30 seconds, next due in 15 secondsInvalid after 180 seconds, hold down 180, flushed after 240Outgoing update filter list for all interfaces is not setIncoming update filter list for all interfaces is not setRedistributing: ripDefault version control: send version 1, receive any versionInterface Send Recv Triggered RIP Key-chain FastEthernet0/0 1 2 1Automatic network summarization is in effectMaximum path: 4Routing for Networks:192.168.12.0Passive Interface(s):Routing Information Sources:Gateway Distance Last UpdateDistance: (default is 120)r3#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is not setR 192.168.11.0/24 [120/1] via 192.168.12.1, 00:00:04, FastEthernet0/0 C 192.168.12.0/24 is directly connected, FastEthernet0/0r3#ping 192.168.11.0Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.0, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 ms实训七负载平衡试训目的实现负载平衡实训拓扑R1 fa0/0 192.168.11.1R2 eth0/0/0 192.168.11.2Fa0/0 192.168.12.1Fa0/0 192.168.13.1R3 fa0/0 192.168.12.2Fa0/1 192.168.14.1R4 fa0/0 192.168.13.2Fa0/1 192.168.15.1R5 fa0/0 192.168.14.2Fa0/1 192.168.15.2实训步骤(R1 )r1>enR1#conf tR1(config)#ip route 0.0.0.0 0.0.0.0 192.168.11.2R1(config)#exitr1#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.11.2 to network 0.0.0.0C 192.168.11.0/24 is directly connected, FastEthernet0/0S* 0.0.0.0/0 [1/0] via 192.168.11.2(R2)r2>enr2(config)#ip route 0.0.0.0 0.0.0.0 192.168.12.2r2(config)#ip route 0.0.0.0 0.0.0.0 192.168.13.2r2(config)#exitr2#%SYS-5-CONFIG_I: Configured from console by consoles% Ambiguous command: "s"r2#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.12.2 to network 0.0.0.0C 192.168.11.0/24 is directly connected, Ethernet0/0/0C 192.168.12.0/24 is directly connected, FastEthernet0/0C 192.168.13.0/24 is directly connected, FastEthernet0/1S* 0.0.0.0/0 [1/0] via 192.168.12.2[1/0] via 192.168.13.2(R3)r3>enr3#conf tEnter configuration commands, one per line. End with CNTL/Z.r3(config)#ip route 0.0.0.0 0.0.0.0 192.168.12.1r3(config)#exitr3#%SYS-5-CONFIG_I: Configured from console by consoler3#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.12.1 to network 0.0.0.0C 192.168.12.0/24 is directly connected, FastEthernet0/0C 192.168.14.0/24 is directly connected, FastEthernet0/1S* 0.0.0.0/0 [1/0] via 192.168.12.1(R4)r4>enr4#conf tEnter configuration commands, one per line. End with CNTL/Z.r4(config)#ip route 0.0.0.0 0.0.0.0 192.168.13.1r4(config)#exitr4#%SYS-5-CONFIG_I: Configured from console by consoler4#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.13.1 to network 0.0.0.0C 192.168.13.0/24 is directly connected, FastEthernet0/0C 192.168.15.0/24 is directly connected, FastEthernet0/1S* 0.0.0.0/0 [1/0] via 192.168.13.1(R5)r5>enr5#conf tEnter configuration commands, one per line. End with CNTL/Z.r5(config)#ip route 0.0.0.0 0.0.0.0 192.168.14.1r5(config)#ip route 0.0.0.0 0.0.0.0 192.168.15.1r5(config)#exitr5#%SYS-5-CONFIG_I: Configured from console by consoler5#show ip routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 192.168.14.1 to network 0.0.0.0C 192.168.14.0/24 is directly connected, FastEthernet0/0C 192.168.15.0/24 is directly connected, FastEthernet0/1S* 0.0.0.0/0 [1/0] via 192.168.14.1[1/0] via 192.168.15.1实训测试(R1)r1#ping 192.168.14.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.14.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 62/84/94 ms (R5)r5#ping 192.168.11.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.11.1, timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 79/91/94 ms实训八DHCP 协议配置实训目的全网配通实训拓扑Fa0/0 192.168.11.1Fa0/1 192.168.12.1实训步骤Router>enRouter#conf tEnter configuration commands, one per line. End with CNTL/Z.Router(config)#host r1r1(config)#int fa0/0r1(config-if)#ip add 192.168.11.1 255.255.255.0r1(config-if)#no shr1(config-if)#exitr1(config)#int fa0/1r1(config-if)#ip add 192.168.12.1 255.255.255.0r1(config-if)#no shr1(config-if)#exitr1(config)#ip dhcp pool znn //配置一个根地址池znnr1(dhcp-config)#network 192.168.11.0 255.255.255.0 //为所有客户机动态分配的地址段r1(dhcp-config)#default-router 192.168.11.1 //为客户机配置默认的网关r1(dhcp-config)#dns-server 192.168.11.1 //为客户机配置DNS服务器r1(dhcp-config)#exitr1(config)#ip dhcp pool znn1r1(dhcp-config)#network 192.168.12.0 255.255.255.0r1(dhcp-config)#default-router 192.168.12.1r1(dhcp-config)#dns-server 192.168.12.1r1(dhcp-config)#exit。
思科4506路由器全网络配置方案

思科4506全网络配置方案1. 网络拓扑2. 配置文档中心机房配置2台Catalyst4506,互为冗余备份,通过一台PIX525防火墙连接互联网。
接入交换机配置Catalyst3750/3560,每台接入交换机配置2条TRUNK端口,分别连接到核心交换机。
整个网络部署9个Vlan,Vlan1为管理vlan,其余8个Vlan为用户Vlan。
每个用户Vlan分配一个C类ip地址段,其中x.x.x.1为网关,x.x.x.1-x.x.x.99保留为手动ip配置,x.x.x.100-x.x.x.254作为dhcp动态分配的Vlan用户使用。
(1)主核心交换机Catalyst4506配置。
SW4500-1#SW4500-1#wr tBuilding configuration...Current configuration : 9687 bytes!version 12.2no service padservice timestamps debug uptimeservice timestamps log uptimeno service password-encryptionservice compress-config!hostname SW4500-1!boot-start-markerboot system flash bootflash:cat4500-ipbase-mz.122-31.SGA6.bin boot-end-marker!enable secret cisco!no aaa new-modelip subnet-zerono ip domain-lookupip host fw 192.168.201.100ip host sw2 192.168.201.3ip dhcp excluded-address 192.168.202.1 192.168.202.99ip dhcp excluded-address 192.168.203.1 192.168.203.99ip dhcp excluded-address 192.168.204.1 192.168.204.99ip dhcp excluded-address 192.168.205.1 192.168.205.99ip dhcp excluded-address 192.168.206.1 192.168.206.99ip dhcp excluded-address 192.168.207.1 192.168.207.99ip dhcp excluded-address 192.168.208.1 192.168.208.99ip dhcp excluded-address 192.168.209.1 192.168.209.99ip dhcp excluded-address 192.168.210.1 192.168.210.99ip dhcp excluded-address 192.168.201.1 192.168.201.20ip dhcp excluded-address 192.168.201.100 192.168.201.126 !ip dhcp pool vlan2network 192.168.202.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.202.1lease 0 8!ip dhcp pool vlan3network 192.168.203.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.203.1lease 0 8!ip dhcp pool vlan4network 192.168.204.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.204.1lease 0 8!ip dhcp pool vlan5network 192.168.205.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.205.1lease 0 8!ip dhcp pool vlan6network 192.168.206.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.206.1lease 0 8!ip dhcp pool vlan7network 192.168.207.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.207.1lease 0 8!ip dhcp pool vlan8network 192.168.208.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.208.1lease 0 8!ip dhcp pool vlan9network 192.168.209.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.209.1lease 0 8!ip dhcp pool vlan10network 192.168.210.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.210.1lease 0 8!ip dhcp pool vlan1network 192.168.201.0 255.255.255.128 dns-server 202.99.224.8 202.106.0.20default-router 192.168.201.1lease 0 8!!!!power redundancy-mode redundantno file verify auto!spanning-tree mode pvstspanning-tree extend system-idspanning-tree vlan 1-10 priority 24576!vlan internal allocation policy ascending!interface GigabitEthernet1/1!interface GigabitEthernet1/2!interface GigabitEthernet2/1description LinkToSW4500-2 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet2/2switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet2/3 switchport mode trunk!interface GigabitEthernet2/4 switchport mode trunk!interface GigabitEthernet2/5 switchport mode trunk!interface GigabitEthernet2/6 switchport mode trunk!interface GigabitEthernet2/7 switchport mode trunk!interface GigabitEthernet2/8 switchport mode trunk!interface GigabitEthernet2/9 switchport mode trunk!interface GigabitEthernet2/10 switchport mode trunk!interface GigabitEthernet2/11 switchport mode trunk!interface GigabitEthernet2/12 switchport mode trunk!interface GigabitEthernet2/13 switchport mode trunk!interface GigabitEthernet2/14 switchport mode trunk!interface GigabitEthernet2/15 switchport mode trunk!interface GigabitEthernet2/16 switchport mode trunk!interface GigabitEthernet2/17 switchport mode trunk!interface GigabitEthernet2/18 switchport mode trunk!interface GigabitEthernet3/1 description LinkToFirewall switchport mode access spanning-tree portfast!interface GigabitEthernet3/2 switchport mode access spanning-tree portfast!interface GigabitEthernet3/3 description Cisco net manager switchport mode access spanning-tree portfast!interface GigabitEthernet3/4 switchport mode access spanning-tree portfast!interface GigabitEthernet3/5 switchport mode access spanning-tree portfast!interface GigabitEthernet3/6 switchport mode access spanning-tree portfast!interface GigabitEthernet3/7 switchport mode access spanning-tree portfast!interface GigabitEthernet3/8 switchport mode access spanning-tree portfast!interface GigabitEthernet3/9 switchport mode access spanning-tree portfastinterface GigabitEthernet3/10 switchport mode access spanning-tree portfast!interface GigabitEthernet3/11 switchport mode access spanning-tree portfast!interface GigabitEthernet3/12 switchport mode access spanning-tree portfast!interface GigabitEthernet3/13 switchport mode access spanning-tree portfast!interface GigabitEthernet3/14 switchport mode access spanning-tree portfast!interface GigabitEthernet3/15 switchport mode access spanning-tree portfast!interface GigabitEthernet3/16 switchport mode access spanning-tree portfast!interface GigabitEthernet3/17 switchport mode access spanning-tree portfast!interface GigabitEthernet3/18 switchport mode access spanning-tree portfast!interface GigabitEthernet3/19 switchport mode access spanning-tree portfast!interface GigabitEthernet3/20 switchport mode access spanning-tree portfastinterface GigabitEthernet3/21 switchport mode access spanning-tree portfast!interface GigabitEthernet3/22 switchport mode access spanning-tree portfast!interface GigabitEthernet3/23 switchport mode access spanning-tree portfast!interface GigabitEthernet3/24 switchport mode access spanning-tree portfast!interface GigabitEthernet3/25 switchport mode access spanning-tree portfast!interface GigabitEthernet3/26 switchport mode access spanning-tree portfast!interface GigabitEthernet3/27 switchport mode access spanning-tree portfast!interface GigabitEthernet3/28 switchport mode access spanning-tree portfast!interface GigabitEthernet3/29 switchport mode access spanning-tree portfast!interface GigabitEthernet3/30 switchport mode access spanning-tree portfast!interface GigabitEthernet3/31 switchport mode access spanning-tree portfastinterface GigabitEthernet3/32 switchport mode accessspanning-tree portfast!interface GigabitEthernet3/33!interface GigabitEthernet3/34!interface GigabitEthernet3/35!interface GigabitEthernet3/36!interface GigabitEthernet3/37!interface GigabitEthernet3/38!interface GigabitEthernet3/39!interface GigabitEthernet3/40!interface GigabitEthernet3/41 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/42 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/43 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/44 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/45 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/46 switchport trunk encapsulation dot1q switchport mode trunkinterface GigabitEthernet3/47switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/48switchport trunk encapsulation dot1q switchport mode trunk!interface Vlan1ip address 192.168.201.2 255.255.255.128 standby 1 ip 192.168.201.1standby 1 preempt!interface Vlan2ip address 192.168.202.2 255.255.255.0 standby 1 ip 192.168.202.1standby 1 preempt!interface Vlan3ip address 192.168.203.2 255.255.255.0 standby 1 ip 192.168.203.1standby 1 preempt!interface Vlan4ip address 192.168.204.2 255.255.255.0 standby 1 ip 192.168.204.1standby 1 preempt!interface Vlan5ip address 192.168.205.2 255.255.255.0 standby 1 ip 192.168.205.1standby 1 preempt!interface Vlan6ip address 192.168.206.2 255.255.255.0 standby 1 ip 192.168.206.1standby 1 preempt!interface Vlan7ip address 192.168.207.2 255.255.255.0 standby 1 ip 192.168.207.1standby 1 preempt!interface Vlan8ip address 192.168.208.2 255.255.255.0standby 1 ip 192.168.208.1standby 1 preempt!interface Vlan9ip address 192.168.209.2 255.255.255.0standby 1 ip 192.168.209.1standby 1 preempt!ip route 0.0.0.0 0.0.0.0 192.168.201.100ip http server!!!snmp-server community public-nm ROsnmp-server community private-nm RWsnmp-server chassis-id snmp-server enable traps snmp authentication linkdown linkup coldstart warmstart snmp-server enable traps ttysnmp-server enable traps fru-ctrlsnmp-server enable traps entitysnmp-server enable traps flash insertion removalsnmp-server enable traps cpu thresholdsnmp-server enable traps vtpsnmp-server enable traps vlancreatesnmp-server enable traps vlandeletesnmp-server enable traps envmon fan shutdown supply temperature statussnmp-server enable traps port-securitysnmp-server enable traps rfsnmp-server enable traps config-copysnmp-server enable traps configsnmp-server enable traps hsrpsnmp-server enable traps ipmulticastsnmp-server enable traps mac-notification change move thresholdsnmp-server enable traps pim neighbor-change rp-mapping-change invalid-pim-message snmp-server enable traps bridge newroot topologychangesnmp-server enable traps stpx inconsistency root-inconsistency loop-inconsistency snmp-server enable traps syslogsnmp-server enable traps vlan-membershipsnmp-server host 192.168.201.101 public-nm!control-plane!!line con 0stopbits 1line vty 0 4password ciscologin!endSW4500-1# sh cdp neiCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDSW4500-2 Gig 2/1 136 R S I WS-C4506 Gig 2/1 bangonglou2 Gig 3/48 162 S I WS-C3750G Gig 1/0/23 bangonglou1 Gig 3/47 126 S I WS-C3750G Gig 1/0/23SW4500-1#sw2Trying sw2 (192.168.201.3)... OpenUser Access VerificationPassword:SW4500-2>enPassword:SW4500-2#wr tBuilding configuration...Current configuration : 9011 bytes!version 12.2no service padservice timestamps debug uptimeservice timestamps log uptimeno service password-encryptionservice compress-config!hostname SW4500-2!boot-start-markerboot system flash bootflash:cat4500-ipbase-mz.122-31.SGA6.binboot-end-marker!enable secret 5 $1$qdQu$9POGVGQrtfz7hMOiRKf/k.!no aaa new-modelip subnet-zerono ip domain-lookupip host sw1 192.168.201.2ip dhcp excluded-address 192.168.202.1 192.168.202.99ip dhcp excluded-address 192.168.203.1 192.168.203.99ip dhcp excluded-address 192.168.204.1 192.168.204.99ip dhcp excluded-address 192.168.205.1 192.168.205.99ip dhcp excluded-address 192.168.206.1 192.168.206.99ip dhcp excluded-address 192.168.207.1 192.168.207.99ip dhcp excluded-address 192.168.208.1 192.168.208.99ip dhcp excluded-address 192.168.209.1 192.168.209.99ip dhcp excluded-address 192.168.210.1 192.168.210.99ip dhcp excluded-address 192.168.201.1 192.168.201.20ip dhcp excluded-address 192.168.201.100 192.168.201.126 !ip dhcp pool vlan2network 192.168.202.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.202.1lease 0 8!ip dhcp pool vlan3network 192.168.203.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.203.1lease 0 8!ip dhcp pool vlan4network 192.168.204.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.204.1lease 0 8!ip dhcp pool vlan5network 192.168.205.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.205.1lease 0 8!ip dhcp pool vlan6network 192.168.206.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.206.1lease 0 8!ip dhcp pool vlan7network 192.168.207.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.207.1lease 0 8!ip dhcp pool vlan8network 192.168.208.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.208.1lease 0 8!ip dhcp pool vlan9network 192.168.209.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.209.1lease 0 8!ip dhcp pool vlan10network 192.168.210.0 255.255.255.0dns-server 202.99.224.8 202.106.0.20default-router 192.168.210.1lease 0 8!ip dhcp pool vlan1network 192.168.201.0 255.255.255.128 dns-server 202.99.224.8 202.106.0.20default-router 192.168.201.1lease 0 8!!!!power redundancy-mode redundantno file verify auto!spanning-tree mode pvstspanning-tree extend system-idspanning-tree vlan 1-10 priority 28672 !vlan internal allocation policy ascending !interface GigabitEthernet1/1!interface GigabitEthernet1/2!interface GigabitEthernet2/1 description LINkToSW4500-1 switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet2/2!interface GigabitEthernet2/3!interface GigabitEthernet2/4!interface GigabitEthernet2/5!interface GigabitEthernet2/6!interface GigabitEthernet2/7!interface GigabitEthernet2/8!interface GigabitEthernet2/9!interface GigabitEthernet2/10!interface GigabitEthernet2/11!interface GigabitEthernet2/12!interface GigabitEthernet2/13!interface GigabitEthernet2/14!interface GigabitEthernet2/15!interface GigabitEthernet2/16!interface GigabitEthernet2/17interface GigabitEthernet2/18 !interface GigabitEthernet3/1 description LinkToFirewall switchport mode access spanning-tree portfast!interface GigabitEthernet3/2 switchport mode access spanning-tree portfast!interface GigabitEthernet3/3 description Cisco net manager switchport mode access spanning-tree portfast!interface GigabitEthernet3/4 switchport mode access spanning-tree portfast!interface GigabitEthernet3/5 switchport mode access spanning-tree portfast!interface GigabitEthernet3/6 switchport mode access spanning-tree portfast!interface GigabitEthernet3/7 switchport mode access spanning-tree portfast!interface GigabitEthernet3/8 switchport mode access spanning-tree portfast!interface GigabitEthernet3/9 switchport mode access spanning-tree portfast!interface GigabitEthernet3/10 switchport mode access spanning-tree portfastinterface GigabitEthernet3/11 switchport mode access spanning-tree portfast!interface GigabitEthernet3/12 switchport mode access spanning-tree portfast!interface GigabitEthernet3/13 switchport mode access spanning-tree portfast!interface GigabitEthernet3/14 switchport mode access spanning-tree portfast!interface GigabitEthernet3/15 switchport mode access spanning-tree portfast!interface GigabitEthernet3/16 switchport mode access spanning-tree portfast!interface GigabitEthernet3/17 switchport mode access spanning-tree portfast!interface GigabitEthernet3/18 switchport mode access spanning-tree portfast!interface GigabitEthernet3/19 switchport mode access spanning-tree portfast!interface GigabitEthernet3/20 switchport mode access spanning-tree portfast!interface GigabitEthernet3/21 switchport mode access spanning-tree portfastinterface GigabitEthernet3/22 switchport mode access spanning-tree portfast!interface GigabitEthernet3/23 switchport mode access spanning-tree portfast!interface GigabitEthernet3/24 switchport mode access spanning-tree portfast!interface GigabitEthernet3/25 switchport mode access spanning-tree portfast!interface GigabitEthernet3/26 switchport mode access spanning-tree portfast!interface GigabitEthernet3/27 switchport mode access spanning-tree portfast!interface GigabitEthernet3/28 switchport mode access spanning-tree portfast!interface GigabitEthernet3/29 switchport mode access spanning-tree portfast!interface GigabitEthernet3/30 switchport mode access spanning-tree portfast!interface GigabitEthernet3/31 switchport mode access spanning-tree portfast!interface GigabitEthernet3/32 switchport mode access spanning-tree portfastinterface GigabitEthernet3/33!interface GigabitEthernet3/34!interface GigabitEthernet3/35!interface GigabitEthernet3/36!interface GigabitEthernet3/37!interface GigabitEthernet3/38!interface GigabitEthernet3/39!interface GigabitEthernet3/40!interface GigabitEthernet3/41switchport trunk encapsulation dot1q switchport mode trunk!interface GigabitEthernet3/42!interface GigabitEthernet3/43!interface GigabitEthernet3/44!interface GigabitEthernet3/45!interface GigabitEthernet3/46!interface GigabitEthernet3/47!interface GigabitEthernet3/48!interface Vlan1ip address 192.168.201.3 255.255.255.128 standby 1 ip 192.168.201.1standby 1 priority 95standby 1 preempt!interface Vlan2ip address 192.168.202.3 255.255.255.0 standby 1 ip 192.168.202.1standby 1 priority 95standby 1 preempt!interface Vlan3ip address 192.168.203.3 255.255.255.0 standby 1 ip 192.168.203.1standby 1 priority 95standby 1 preempt!interface Vlan4ip address 192.168.204.3 255.255.255.0 standby 1 ip 192.168.204.1standby 1 priority 95standby 1 preempt!interface Vlan5ip address 192.168.205.3 255.255.255.0 standby 1 ip 192.168.205.1standby 1 priority 95standby 1 preempt!interface Vlan6ip address 192.168.206.3 255.255.255.0 standby 1 ip 192.168.206.1standby 1 priority 95standby 1 preempt!interface Vlan7ip address 192.168.207.3 255.255.255.0 standby 1 ip 192.168.207.1standby 1 priority 95standby 1 preempt!interface Vlan8ip address 192.168.208.3 255.255.255.0 standby 1 ip 192.168.208.1standby 1 priority 95standby 1 preempt!interface Vlan9ip address 192.168.209.3 255.255.255.0 standby 1 ip 192.168.209.1standby 1 priority 95standby 1 preempt!ip route 0.0.0.0 0.0.0.0 192.168.201.100ip http server!!!snmp-server community public-nm ROsnmp-server community private-nm RWsnmp-server chassis-id snmp-server enable traps snmp authentication linkdown linkup coldstart warmstart snmp-server enable traps ttysnmp-server enable traps fru-ctrlsnmp-server enable traps entitysnmp-server enable traps flash insertion removalsnmp-server enable traps cpu thresholdsnmp-server enable traps vtpsnmp-server enable traps vlancreatesnmp-server enable traps vlandeletesnmp-server enable traps envmon fan shutdown supply temperature statussnmp-server enable traps port-securitysnmp-server enable traps rfsnmp-server enable traps config-copysnmp-server enable traps configsnmp-server enable traps hsrpsnmp-server enable traps ipmulticastsnmp-server enable traps mac-notification change move thresholdsnmp-server enable traps pim neighbor-change rp-mapping-change invalid-pim-message snmp-server enable traps bridge newroot topologychangesnmp-server enable traps stpx inconsistency root-inconsistency loop-inconsistency snmp-server enable traps syslogsnmp-server enable traps vlan-membershipsnmp-server host 192.168.201.101 public-nm!control-plane!!line con 0stopbits 1line vty 0 4password ciscologin!endSW4500-2# sh cdp neiCapability Codes: R - Router, T - Trans Bridge, B - Source Route BridgeS - Switch, H - Host, I - IGMP, r - Repeater, P - PhoneDevice ID Local Intrfce Holdtme Capability Platform Port IDSW4500-1 Gig 2/1 167 R S I WS-C4506 Gig 2/1 bangonglou2 Gig 3/48 142 S I WS-C3750G Gig 1/0/24 bangonglou1 Gig 3/47 165 S I WS-C3750G Gig 1/0/24 SW4500-2#SW4500-2#SW4500-2#SW4500-2#SW4500-2#exit[Connection to sw2 closed by foreign host]SW4500-1#fwTrying fw (192.168.201.100)... OpenUser Access VerificationPassword:Type help or '?' for a list of available commands.YMMK-FIREWALL> enPassword: *****YMMK-FIREWALL# wr t: Saved:PIX Version 8.0(4)!hostname YMMK-FIREWALLdomain-name enable password ciscopasswd cisconames!interface Ethernet0nameif outsidesecurity-level 0ip address xx.xx.xx.xx 255.255.255.248!interface Ethernet1nameif insidesecurity-level 100ip address 192.168.201.100 255.255.255.128!ftp mode passivedns server-group DefaultDNSdomain-name access-list intoout extended permit icmp any anyaccess-list intoout extended deny tcp any any eq 135access-list intoout extended deny tcp any any eq netbios-ssnaccess-list intoout extended deny tcp any any eq 445access-list intoout extended deny tcp any any eq 1025access-list intoout extended deny tcp any any eq 4444access-list intoout extended deny tcp any any eq 5554access-list intoout extended deny tcp any any eq 9996access-list intoout extended deny tcp any any eq 69access-list intoout extended deny tcp any any eq 1433access-list intoout extended deny tcp any any eq 1434access-list intoout extended permit ip any anypager lines 24mtu inside 1500mtu outside 1500no failovericmp unreachable rate-limit 1 burst-size 1icmp permit any insideicmp permit any outsideasdm image flash:/asdm-613.binno asdm history enablearp timeout 14400global (outside) 1 interfacenat (inside) 1 192.168.0.0 255.255.0.0static (inside,outside) tcp interface 2741 192.168.201.101 1741 dnsaccess-group intoout in interface insideroute outside 0.0.0.0 0.0.0.0 xx.xx.xx.xx 1route inside 192.168.202.0 255.255.255.0 192.168.201.1 1route inside 192.168.203.0 255.255.255.0 192.168.201.1 1route inside 192.168.204.0 255.255.255.0 192.168.201.1 1route inside 192.168.205.0 255.255.255.0 192.168.201.1 1route inside 192.168.206.0 255.255.255.0 192.168.201.1 1route inside 192.168.207.0 255.255.255.0 192.168.201.1 1route inside 192.168.208.0 255.255.255.0 192.168.201.1 1route inside 192.168.209.0 255.255.255.0 192.168.201.1 1route inside 192.168.210.0 255.255.255.0 192.168.201.1 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolutedynamic-access-policy-record DfltAccessPolicyaaa authentication ssh console LOCALsnmp-server host inside 192.168.201.101 community public-nmno snmp-server locationno snmp-server contactsnmp-server community public-nmsnmp-server enable traps snmp authentication linkup linkdown coldstartsnmp-server enable traps syslogcrypto ipsec security-association lifetime seconds 28800crypto ipsec security-association lifetime kilobytes 4608000telnet 0.0.0.0 0.0.0.0 insidetelnet timeout 5ssh 0.0.0.0 0.0.0.0 outsidessh timeout 20console timeout 0threat-detection basic-threatthreat-detection statistics access-listno threat-detection statistics tcp-interceptusername cisco password 3q8ZgbRKJMLMsGri encrypted!class-map inspection_defaultmatch default-inspection-traffic!!policy-map type inspect dns preset_dns_mapparametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns preset_dns_mapinspect ftpinspect h323 h225inspect h323 rasinspect netbiosinspect rshinspect rtspinspect esmtpinspect sqlnetinspect sunrpcinspect tftpinspect sipinspect xdmcp!service-policy global_policy globalprompt hostname contextCryptochecksum:3cf0203d19fdb4ac1e58ce9fd4c4af44: end[OK]YMMK-FIREWALL# sh routeCodes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area* - candidate default, U - per-user static route, o - ODRP - periodic downloaded static routeGateway of last resort is 58.18.222.49 to network 0.0.0.0S 192.168.209.0 255.255.255.0 [1/0] via 192.168.201.1, insideS 192.168.208.0 255.255.255.0 [1/0] via 192.168.201.1, insideS 192.168.210.0 255.255.255.0 [1/0] via 192.168.201.1, insideC 192.168.201.0 255.255.255.128 is directly connected, insideC xx.xx.xx.xx 255.255.255.248 is directly connected, outsideS 192.168.202.0 255.255.255.0 [1/0] via 192.168.201.1, insideS 192.168.203.0 255.255.255.0 [1/0] via 192.168.201.1, insideS 192.168.204.0 255.255.255.0 [1/0] via 192.168.201.1, insideS 192.168.205.0 255.255.255.0 [1/0] via 192.168.201.1, insideS 192.168.206.0 255.255.255.0 [1/0] via 192.168.201.1, insideS 192.168.207.0 255.255.255.0 [1/0] via 192.168.201.1, insideS* 0.0.0.0 0.0.0.0 [1/0] via xx.xx.xx.xx, outsideYMMK-FIREWALL# sh xlate172 in use, 389 most usedPAT Global xx.xx.xx.xx(59231) Local 192.168.208.100(15005)PAT Global xx.xx.xx.xx(61203) Local 192.168.202.101(1747)PAT Global xx.xx.xx.xx(6897) Local 192.168.208.104(1491)PAT Global xx.xx.xx.xx(23487) Local 192.168.208.103(2972)PAT Global xx.xx.xx.xx(25050) Local 192.168.208.105(1252)…………YMMK-FIREWALL#$YMMK-FIREWALL# exiLogoff[Connection to fw closed by foreign host] SW4500-1#SW4500-1#SW4500-1#SW4500-1#192.168.201.10Trying 192.168.201.10 ... OpenUser Access VerificationPassword:bangonglou1>enPassword:bangonglou1#wr tBuilding configuration...Current configuration : 3815 bytes!version 12.2no service padservice timestamps debug uptime service timestamps log uptimeno service password-encryption!hostname bangonglou1!enable cisco!no aaa new-modelswitch 1 provision ws-c3750g-24t system mtu routing 1500ip subnet-zero!!!!no file verify autospanning-tree mode pvstspanning-tree extend system-id!vlan internal allocation policy ascending !interface GigabitEthernet1/0/1 switchport access vlan 8spanning-tree portfast!interface GigabitEthernet1/0/2 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/3 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/4 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/5 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/6 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/7 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/8 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/9 switchport access vlan 2spanning-tree portfast!interface GigabitEthernet1/0/10 switchport access vlan 2spanning-tree portfast。
强化Cisco路由器的安全配置

导作 用。 关 键 词 : 由 器 ; t n t 网络 攻 击 路 I e e; nr
中图分 类号 : P9 .8 1 3 30 1
文献 标识 码 : A
文章 编号 :6 2 7 0 (0 8 0 — 15 0 17 — 8 0 2 0 )6 0 9 — 3
路 由器 是一 种连接 多个 网络 或 网段 的 网络设 备 , 能将不 它 同网络或 网段之 间 的数 据信 息进 行 “ 翻译 ” 以使 它们 能够 相互 。 “ ” 对方 的数据 , 而构 成一个 更大 的 网络 。 目前 大多 数 的 读 懂 从 企事业 单位 和部 门连接Itme ,都是 通过 一 台路 由器 与IP ne t S 连 结实现 。这 台路 由器 就是 沟通外 部It n t 内部 网络 的桥梁 。 ne e和 r
R ue(of -ie#lgnlcl otrcni l ) oi a g n o
R ue(o f ) evc as od ecy t n o trc ni #sriep sw r- n rpi g o 1 . 禁 用 W e 服 务 5 b
口令 帐号 。这就 意味着 , 问权 的获 得需要 用户 名 和 口令 来 实 访
现 。 此 之 外 , 议 为 用 户 名 配 置 一 个 秘 密 口令 , 不 仅 只 有 一 除 建 而 个 常 规 口令 。 它 用 MD  ̄ 密 方 法 来 加 密 口令 , 大 提 高 了 安 全 5I 1 大 性 。举 例 如 下 : R ue (of ) sma ot ert ¥ as od o t cn g #u e mero ce My P sw r r i s
Cso 由器在 缺 省情 况 下 启用 了We 服 务 ( : 有一 部 i 路 c b 注 只 分C so 由器有 We 服务 功能 ) 它是 一个 安全风 险 。 i 路 c b , 如果 你不 打算 使用 它 , 最好 将它 关闭 。设 置如下 :
Cisco(思科)路由器静态路由的配置

Cisco(思科)路由器静态路由的配置实验拓扑实验步骤我们要使得 1.1.1.0/24、2.2.2.0/24、3.3.3.0/24 ⽹络之间能够互相通信。
(1)步骤 1:在各路由器上配置 IP 地址、保证直连链路的连通性R1(config)#int loopback0R1(config-if)#ip address 1.1.1.1 255.255.255.0R1(config)#int s0/0/0R1(config-if)#ip address 192.168.12.1 255.255.255.0R1(config-if)#no shutdownR2(config)#int loopback0R2(config-if)#ip address 2.2.2.2 255.255.255.0R2(config)#int s0/0/0R2(config-if)#clock rate 128000R2(config-if)#ip address 192.168.12.2 255.255.255.0R2(config-if)#no shutdownR2(config)#int s0/0/1R2(config-if)#clock rate 128000R2(config-if)#ip address 192.168.23.2 255.255.255.0R2(config-if)#no shutdownR3(config)#int loopback0R3(config-if)#ip address 3.3.3.3 255.255.255.0R3(config)#int s0/0/1R3(config-if)#ip address 192.168.23.3 255.255.255.0R3(config-if)#no shutdown(2)步骤 2:R1上配置静态路由R1(config)#ip route 2.2.2.0 255.255.255.0 s0/0/0//下⼀跳为接⼝形式,s0/0/0 是点对点的链路,注意应该是 R1 上的s0/0/0 接⼝R1(config)#ip route 3.3.3.0 255.255.255.0 192.168.12.2//下⼀跳为IP 地址形式,192.168.12.2 是R2 上的IP 地址(3)步骤 3:R2上配置静态路由R2(config)#ip route 1.1.1.0 255.255.255.0 s0/0/0R2(config)#ip route 3.3.3.0 255.255.255.0 s0/0/1(4)步骤 4:R3上配置静态路由R3(config)#ip route 1.1.1.0 255.255.255.0 s0/0/1R3(config)#ip route 2.2.2.0 255.255.255.0 s0/0/1实验调试(1)在 R1、R2、R3 上查看路由表R1#show ip routeCodes: C - connected, S - static, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static routeo - ODR, P - periodic downloaded static routeGateway of last resort is not setC 192.168.12.0/24 is directly connected, Serial0/0/01.0.0.0/24 is subnetted, 1 subnetsC 1.1.1.0 is directly connected, Loopback02.0.0.0/24 is subnetted, 1 subnetsS 2.2.2.0 is directly connected, Serial0/0/03.0.0.0/24 is subnetted, 1 subnetsS 3.3.3.0 [1/0] via 192.168.12.2R2#show ip routeCodes: C - connected, S - static, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2ia - IS-IS inter area, * - candidate default, U - per-user static routeo - ODR, P - periodic downloaded static routeGateway of last resort is not setC 192.168.12.0/24 is directly connected, Serial0/0/01.0.0.0/24 is subnetted, 1 subnetsS 1.1.1.0 is directly connected, Serial0/0/02.0.0.0/24 is subnetted, 1 subnetsC 2.2.2.0 is directly connected, Loopback03.0.0.0/24 is subnetted, 1 subnetsS 3.3.3.0 is directly connected, Serial0/0/1C 192.168.23.0/24 is directly connected, Serial0/0/1R3#show ip routeCodes: C - connected, S - static, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2ia - IS-IS inter area, * - candidate default, U - per-user static routeo - ODR, P - periodic downloaded static routeGateway of last resort is not set1.0.0.0/24 is subnetted, 1 subnetsS 1.1.1.0 is directly connected, Serial0/0/12.0.0.0/24 is subnetted, 1 subnetsS 2.2.2.0 is directly connected, Serial0/0/13.0.0.0/24 is subnetted, 1 subnets C 3.3.3.0 is directly connected, Loopback0C 192.168.23.0/24 is directly connected, Serial0/0/1(2)从各路由器的环回⼝ ping 其他路由器的环回⼝:R1#ping//不带任何参数的 ping命令,允许我们输⼊更多的参数Protocol [ip]:Target IP address: 2.2.2.2 //⽬标IP地址Repeat count [5]: //发送的ping 次数Datagram size [100]: //ping包的⼤⼩Timeout in seconds [2]: //超时时间Extended commands [n]: y //是否进⼀步扩展命令Source address or interface: 1.1.1.1 //源IP地址Type of service [0]:Set DF bit in IP header? [no]:Validate reply data? [no]:Data pattern [0xABCD]:Loose, Strict, Record, Timestamp, Verbose[none]:Sweep range of sizes [n]:Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:Packet sent with a source address of 1.1.1.1Success rate is 100 percent (5/5), round-trip min/avg/max = 12/14/16 ms//以上说明从 R1 的 loopback0 可以ping 通R2 上的 loopback0。
Cisco路由器VPN配置

Cisco路由器VPN配置Cisco路由器VPN配置本文档提供了基于Cisco路由器的VPN(虚拟私有网络)配置指南,帮助您在网络中建立安全的连接。
以下是VPN配置的详细步骤和说明。
1:确保路由器和网络连接在开始配置VPN之前,请确保您的Cisco路由器已正确连接到网络,并且具备正常的互联网连接。
确保您具备管理员权限以及登录您的路由器的凭据。
2:配置VPN基础设置2.1 登录路由器管理界面使用SSH、Telnet或Web界面登录您的Cisco路由器。
输入正确的IP地址和认证凭据。
2.2 进入全局配置模式在路由器命令行界面(CLI)中,输入以下命令进入全局配置模式:```enableconfigure terminal```2.3 启用IPSec VPN功能输入以下命令启用IPSec VPN功能并设置预共享密钥:```crypto isakmp enablecrypto isakmp key <pre-shared-key> address <remote-peer-address>```注意: `<pre-shared-key>` 是您与远程对等方共享的密钥,`<remote-peer-address>` 是远程对等方的IP地址。
3:配置VPN隧道参数3.1 配置加密协议输入以下命令配置VPN隧道的加密协议:```crypto ipsec transform-set <transform-set-name><encryption-algorithm> <encryption-key-size> <hashing-algorithm> <dh-group>```注意: `<transform-set-name>` 是您为加密协议设置的唯一名称,`<encryption-algorithm>` 是加密算法(例如DES、3DES、AES),`<encryption-key-size>` 是加密密钥的大小(例如128位、256位),`<hashing-algorithm>` 是散列算法(例如SHA1、SHA256),`<dh-group>` 是Diffie-Hellman群组(例如Group 2、Group 5)。
图解思科路由器配置教程

图解思科路由器配置教程图解思科路由器配置教程第一章:介绍思科路由器1.1 路由器的概念和作用1.2 思科路由器的特点和优势1.3 路由器的基本组成部分第二章:思科路由器的硬件配置2.1 路由器的接口类型和数量2.2 路由器的功能模块2.3 路由器的内存和存储器配置2.4 路由器的电源和供电方式第三章:思科路由器的软件配置3.1 路由器的操作系统和版本3.2 路由器的启动过程和配置文件3.3 路由器的基本配置命令3.4 路由器的网络接口配置3.5 路由器的路由协议配置3.6 路由器的安全配置第四章:思科路由器的网络连接与管理4.1 路由器与局域网的连接配置4.2 路由器与广域网的连接配置4.3 路由器的远程管理与监控第五章:思科路由器的网络故障排除5.1 路由器故障的诊断与定位5.2 路由器故障的常见解决方法5.3 路由器故障排除的工具和命令第六章:思科路由器的高级配置与扩展6.1 路由器的高级功能配置6.2 路由器的扩展模块和接口配置6.3 路由器的QoS配置6.4 路由器的安全配置与防火墙第七章:附件本文档涉及附件:- 示例配置文件(示例路由器配置文件的详细说明)第八章:法律名词及注释本文所涉及的法律名词及注释:- 路由器:一种用于将数据包从一个网络传输到另一个网络的设备。
- 思科路由器:思科公司(Cisco)生产的路由器产品。
- 接口:路由器上的物理或逻辑端口,用于与其他设备进行通信。
- 配置文件:路由器上保存的配置信息,包括路由协议、接口配置等。
- 路由协议:路由器用来学习和选择最佳路径的协议,如静态路由、RIP、OSPF等。
- QoS:Quality of Service(服务质量),用于优化网络流量和提供更好的用户体验。
- 防火墙:用于保护网络安全的设备或软件,可以控制网络流量和过滤恶意数据。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Cisco路由器安全配置方案一、路由器网络服务安全配置1 禁止CDP(Cisco Discovery Protocol)。
如:Router(Config)#no cdp run Router(Config-if)# no cdp enable2 禁止其他的TCP、UDP Small服务。
Router(Config)# no service tcp-small-serversRouter(Config)# no service udp-samll-servers3 禁止Finger服务。
Router(Config)# no ip fingerRouter(Config)# no service finger4 建议禁止HTTP服务。
Router(Config)# no ip http server 如果启用了HTTP服务则需要对其进行安全配置:设置用户名和密码;采用访问列表进行控制。
5 禁止BOOTp服务。
Router(Config)# no ip bootp server6 禁止IP Source Routing。
Router(Config)# no ip source-route7 建议如果不需要ARP-Proxy 服务则禁止它,路由器默认识开启的。
Router(Config)# no ip proxy-arpRouter(Config-if)# no ip proxy-arp8禁止IP Directed Broadcast。
Router(Config)# no ip directed-broadcast9 禁止IP Classless。
Router(Config)# no ip classless10 禁止ICMP协议的IP Unreachables, Redirects, Mask Replies。
Router(Config-if)# no ip unreacheablesRouter(Config-if)# no ip redirectsRouter(Config-if)# no ip mask-reply11 建议禁止SNMP协议服务。
在禁止时必须删除一些SNMP服务的默认配置。
如:Router(Config)# no snmp-server community public RoRouter(Config)# no snmp-server community admin RW12 如果没必要则禁止WINS和DNS服务。
Router(Config)# no ip domain-lookup如果需要则需要配置:Router(Config)# hostname RouterRouter(Config)# ip name-server219、150、32、xxx13 明确禁止不使用的端口。
如:Router(Config)# interface eth0/3Router(Config)# shutdown二、路由器访问控制的安全配置(可选)路由器的访问控制是比较重要的安全措施,但是目前由于需求不明确,可以考虑暂时不实施。
作为建议提供。
1 建议不要远程访问路由器。
即使需要远程访问路由器,建议使用访问控制列表和高强度的密码控制。
2 严格控制CON端口的访问。
配合使用访问控制列表控制对CON 口的访问。
如:Router(Config)#Access-list1 permit192、168、0、1Router(Config)#line con 0Router(Config-line)#Transport input noneRouter(Config-line)#Login localRouter(Config-line)#Exec-timeoute5 0Router(Config-line)#access-class1 inRouter(Config-line)#end同时给CON 口设置高强度的密码。
3 如果不使用AUX端口,则禁止这个端口。
默认是未被启用。
禁止如:Router(Config)#line aux 0Router(Config-line)#transport input noneRouter(Config-line)#no exec4 建议采用权限分级策略。
如:Router(Config)#username test privilege10全文结束》》xxRouter(Config)#privilege EXEC level10 telnetRouter(Config)#privilege EXEC level10 show ip access-list5 为特权模式的进入设置强壮的密码。
不要采用enable password设置密码。
而要采用enable secret命令设置。
并且要启用Service password-encryption。
Router(config)#service password-encryptionRouter(config)#enable secret6 控制对VTY的访问。
如果不需要远程访问则禁止它。
如果需要则一定要设置强壮的密码。
由于VTY 在网络的传输过程中为加密,所以需要对其进行严格的控制。
如:设置强壮的密码;控制连接的并发数目;采用访问列表严格控制访问的地址;可以采用AAA 设置用户的访问控制等。
三、路由器路由协议安全配置 1 建议启用IP Unicast Reverse-Path Verification。
它能够检查源IP地址的准确性,从而可以防止一定的IP Spooling。
但是它只能在启用CEF(Cisco Express Forwarding)的路由器上使用。
uRPF有三种方式,strict方式、ACL方式和loose方式。
在接入路由器上实施时,对于通过单链路接入网络的用户,建议采用strict方式;对于通过多条链路接入到网络的用户,可以采用ACL方式和loose方式。
在出口路由器上实施时,采用loose方式。
Strict方式:Router# config t! 启用CEFRouter(Config)# ip cef!启用Unicast Reverse-Path VerificationRouter(Config)# interfaceeth0/1Router(Config-if)# ip verify unicast reverse-pathACL方式:interface pos1/0ip verify unicast reverse-path190access-list190 permit ip {customer network} {customer network mask} any access-list190 deny ip any any[log] 这个功能检查每一个经过路由器的数据包的源地址,若是不符合ACL 的,路由器将丢弃该数据包。
Loose方式:interface pos1/0ip ver unicast source reachable-via any这个功能检查每一个经过路由器的数据包,在路由器的路由表中若没有该数据包源IP地址的路由,路由器将丢弃该数据包。
2 启用OSPF路由协议的认证。
默认的OSPF认证密码是明文传输的,建议启用MD5认证。
并设置一定强度密钥(key,相对的路由器必须有相同的Key)。
3 RIP 协议的认证。
只有RIP-V2支持,RIP-1不支持。
建议启用RIP-V2。
并且采用MD5认证。
普通认证同样是明文传输的。
4 启用passive-interface命令可以禁用一些不需要接收和转发路由信息的端口。
建议对于不需要路由的端口,启用passive-interface。
但是,在RIP协议是只是禁止转发路由信息,并没有禁止接收。
在OSPF协议中是禁止转发和接收路由信息。
5 启用访问列表过滤一些垃圾和恶意路由信息,控制网络的垃圾信息流。
如:Router(Config)# access-list10 deny192、168、1、0 0、0、0、255Router(Config)# access-list10 permit any ! 禁止路由器接收更新192、168、1、0网络的路由信息Router(Config)# router ospf100Router(Config-router)# distribute-list10 in!禁止路由器转发传播192、168、1、0网络的路由信息Router(Config)# router ospf100Router(Config-router)# distribute-list10 out四、路由器其他安全配置1 IP欺骗简单防护。
如过滤非公有地址访问内部网络。
过滤自己内部网络地址;回环地址(127、0、0、0/8);RFC1918私有地址;DHCP自定义地址(169、254、0、0/16);科学文档作者测试用地址(192、0、2、0/24);不用的组播地址(224、0、0、0/4);SUN公司的古老的测试地址(20、20、20、0/24;204、152、64、0/23);全网络地址(0、0、0、0/8)。
Router(Config)# access-list100 deny ip127、0、0、0 0、255、255、255 any Router(Config)# access-list100 deny ip192、168、0、0 0、0、255、255 any Router(Config)# access-list100 deny ip172、16、0、0 0、15、255、255 any Router(Config)# access-list100 deny ip10、0、0、0 0、255、255、255 any Router(Config)# access-list100 deny ip169、254、0、0 0、0、255、255 any Router(Config)# access-list100 deny ip192、0、2、0 0、0、0、255 any Router(Config)# access-list100 deny ip224、0、0、015、255、255、255 any Router(Config)# access-list100 deny ip20、20、20、0 0、0、0、255 any Router(Config)# access-list100 deny ip204、152、64、0 0、0、2、255 any Router(Config)# access-list100 deny ip 0、0、0、0 0、255、255、255 any Router(Config)# access-list100 permit ip any anyRouter(Config-if)# ip access-group100 in2 建议采用访问列表控制流出内部网络的地址必须是属于内部网络的。
