Chapter2 DataStorage
戴尔 OptiPlex 3090 微型机重新映像指南说明书

OptiPlex 3090 MicroRe-imaging guide for WindowsNotes, cautions, and warningsA NOTE indicates important information that helps you make better use of your product.A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoidA WARNING indicates a potential for property damage, personal injury, or death.© 2021 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners.Chapter 1: Installation overview (4)Chapter 2: Introduction (5)Chapter 3: Order of reinstallation (6)Chapter 4: Updating or resetting the BIOS (7)Flashing the BIOS (7)Clearing CMOS settings (7)Trusted Platform Module (TPM) security (7)Chapter 5: Reinstalling the operating system (9)Chapter 6: Reinstalling drivers and applications (10)Displaying drivers and applications on your computer (10)Chapter 7: Reinstallation sequence for drivers and applications (11)Intel chipset device software (11)Downloading and installing the chipset driver (11)Critical Microsoft Knowledge Base (KB) updates (11)Intel Rapid Storage Technology (IRST) (11)Downloading and installing the IRST APPX (12)Downloading and installing the IRST driver (12)Graphics (12)Downloading and installing the Dell graphics driver (12)Audio (13)Downloading and installing the Dell audio driver (13)Wireless Local Network (WLAN) drivers and applications (13)Downloading and installing the Wi-Fi driver (13)Chapter 8: .NET Framework (14)Chapter 9: Getting help and contacting Dell (15)Contents3Installation overviewThis re-imaging guide is designed for system administrators. Do not attempt to re-image the systemInformation provided in this guide is only applicable to computers with Windows 10 or Windows 11 installed.Dell recommends that you download and install the device drivers from the Dell Drivers & Downloads website. Device drivers must be updated when you reinstall the operating system using either a CD, DVD, USB key, or when you are facing networking, graphics, sound or other hardware-related problems. Dell recommends that you install or update device drivers if you have performed a factory reset of your Dell computer using the Dell Backup and Recovery application or other factory-reset methods. This ensures that you have the latest device drivers installed on your computer and that the devices function optimally.Installing or updating device drivers may lead to the following improvements:●Increases in system performance●Patched security risks●Expanded compatibility●Fixed device issues●Support for new featuresHowever, if your computer is operating normally and there are no driver issues or updates being prompted by Windows, driver updates may be unnecessary. Updating drivers unnecessarily may create new problems.Review the importance of each driver update on the Dell Drivers & Downloads page before assessing the need to continue with an update.4Installation overviewIntroductionThis re-imaging guide is designed for system administrators. Do not attempt to re-image the systemInformation that is provided in this guide is only applicable to computers with Windows 10 or Windows 11 installed. Re-imaging is the process of removing all software on the computer and reinstalling the removed software. Re-imaging is required when software in the computer is corrupted or damaged and it can also be used as a means of removing harmful and malicious software in your computer. This re-imaging guide provides the steps that are required for re-imaging your computer. This guide assists you in installing Dell-recommended software stack and settings, drivers, and applications, which are tested and validated on the computer. The installation of the listed drivers and applications as described in the guide enhances the optimal performance of your computer.Dell also provides drivers and applications that are not included with the Windows operating system. These drivers are required to enable the following solid-state drives (SSDs):●256 GB PCIe SSD●512 GB PCIe SSD●1024 GB PCIe SSD●2048 GB PCIe SSD and larger capacity size PCIe SSDsIt is always recommended to re-image on a newly installed operating system and not from any previous image-build. Ensure BIOS settings, including SATA configurations and modes, are appropriately set and the latest drivers and applications are used when re-imaging the computer.Introduction5Order of reinstallationSome drivers and application installation steps may not be applicable, depending on the configuration of theThe hidden partition in the shipping storage serves for the maintenance purpose and has the ability to recover fromTo achieve optimal performance, install the drivers and applications in the following sequence:1.BIOS: Enables the operating system and the initial setup process to be loaded into the memory on your computer.2.Windows operating system: The operating system controls the computers hardware to be a base on which other softwarecan operate on.3.Intel chipset driver: Allows Windows to communicate and adjust settings on components on the system board whichincludes:●Intel Chipset Device Software Driver●Intel Management Engine Components Installer●Intel Serial IO Driverworking and communication drivers, which include:●Wireless Local Area Network (WLAN) adapter driver: Enables and enhances the wireless adapter.●Bluetooth driver: Enables and enhances the Bluetooth adapter.5.Install latest updates and drivers:●For commercial computers, use Dell Command Updates (DCU).●For consumer computers, use SupportAssist.Drivers can be downloaded and installed manually from the Drivers and downloads.6.: Microsoft updates that fix and optimize the operating system. Formore information, see Windows release information.7.Intel Rapid Storage Technology (IRST): Enables and enhances data storage vitalization for the storage drives installed inthe computer.8.Graphics driver:●Enhances and optimizes video performance.●Enables and provides additional functionality not included in the native Microsoft VGA driver, including:○User-customizable power management features○Portability and behavioral profiles○Multiple-monitor support9.Audio driver: Enables and enhances the audio controller.10.Dell applications, which include:●Dell Update application6Order of reinstallationUpdating or resetting the BIOS Flashing the BIOSAbout this taskIt is recommended to flash the BIOS when an update is available or when you replace the system board. To flash the BIOS:Steps1.Turn on your computer.2.Go to /support.3.Click Product support, enter the Service Tag of your computer, and then click Search.If you do not have the Service Tag, use the product ID or manually browse for your computer model.4.Click Drivers & downloads > Find drivers.5.Select the operating system installed on your computer.6.Scroll down the page and expand BIOS.7.Click Download to download the latest version of the BIOS for your computer.8.After the download is complete, navigate to the folder where you saved the BIOS update file.9.Double-click the BIOS update file icon and follow the instructions on the screen.Clearing CMOS settingsAbout this taskIf flashing your computer with the latest BIOS update results in your computer being unable to boot, a BIOS reset is necessary. Clearing the CMOS settings will reset the BIOS to factory settings. For more information about clearing the CMOS settings see your computer's Service Manual.Trusted Platform Module (TPM) securityAbout this taskTPM must be enabled in the BIOS setup program for it to be deployed on the computer. Follow these steps to enable and configure the TPM:Steps1.Turn on or restart your computer.2.Press F2 when the Dell logo is displayed on the screen to enter the BIOS setup program.The BIOS setup program is displayed.3.On the left pane, select Security.4.Select or clear any of the following options to enable or disable it, respectively:●TPM state (Enabled or Disabled):Enabled: The BIOS will enable the TPM during POST and it can be accessed by the operating system.Disabled: The BIOS will not enable the TPM during POST and it cannot be accessed by the operating system.●TPM 2.0 security On: The TPM is enabled and activated.Updating or resetting the BIOS7●Clear: The BIOS clears the information stored in the TPM.5.Save the settings and exit.8Updating or resetting the BIOSReinstalling the operating system The Windows operating system is validated for use on this computer. You can reset or reinstall the operating system under different scenarios. For more information about reinstalling the operating system, see the knowledge base article 000176966 at /support.For installing Windows on Intel 12th Generation computers using ISO images, see the knowledge base article 000184834 at /support.Before attempting a reinstall of your operating system, Dell recommends that you backup all data as described in the Microsoft knowledge base article.Reinstalling the operating system9Reinstalling drivers and applications Drivers and applications are software that enables Windows to communicate with the hardware devices and software in your computer. Devices such as video and sound cards require drivers to function correctly within Windows, and enable users to adjust hardware settings.Windows includes drivers for most devices, but device-specific drivers may have to be downloaded and installed separately. Dell recommends that you download the device drivers for your Dell computer from Drivers & Downloads.Applications must be downloaded and installed separately. Dell recommends that you download the required applications for your Dell computer from the Dell Download Center.Displaying drivers and applications on your computerSteps1.Turn on your computer.2.Go to /support.3.Click Product support, enter the Service Tag of your computer, and then click Search.If you do not have the Service Tag, use the product ID or manually browse for your computer model.4.Click Drivers & downloads > Find drivers.5.Select the Windows operating system installed on your computer to get a list of the drivers and applications available on yourcomputer.10Reinstalling drivers and applicationsReinstallation sequence for drivers andapplications Driver installation is critical after reinstalling the Windows operating system on your Dell computer. Install the drivers in the correct sequence for your computer to function correctly. In some scenarios, you may have to reinstall or update the device driver if you are encountering issues with a specific device.For more information, see the Dell knowledge base article 000132394 at /support.The Windows operating system includes touchpad drivers; no other touchpad-driver installation is required.The Windows operating system includes the webcam drivers; no additional webcam-driver installation is required. Dell recommends installing drivers or applications in the following sequence.Intel chipset device softwareThe Windows operating system may not include the updated Intel chipset device software for Dell computers. The Intel chipset device software is available on Dell’s support site /support.Downloading and installing the chipset driverSteps1.Turn on your computer.2.Go to /support.3.Click Product support, enter the Service Tag of your computer, and then click Search.If you do not have the Service Tag, use the product ID or manually browse for your computer model.4.Click Drivers & downloads > Find drivers.5.Scroll down the page and expand Chipset.6.Click Download to download the chipset driver for your computer.7.After the download is complete, navigate to the folder where you saved the chipset driver file.8.Double-click the chipset driver file icon and follow the instructions on the screen.Critical Microsoft Knowledge Base (KB) updatesDell recommends installing all the latest available KB updates from the latest Windows Service Pack. Service packs are automatically downloaded and installed when Windows Updates are enabled and can also be manually downloaded and installed from the Microsoft support site. For more information, see Windows release information.Intel Rapid Storage Technology (IRST)The IRST software package enables and enhances high-performance Serial ATA (SATA) and SATA RAID capabilities for supported operating systems. The IRST software package provides an added protection against data loss in the event of ahard-drive failure.7Reinstallation sequence for drivers and applications11The following conditions must be met before you can install IRST on your computer.Your computer has a RAID I/O controller hub (ICH). If your computer does not have a RAID ICH, you cannot install IRST unless a third-party RAID controller card is installed.If a SATA hard drive is already installed, disabling the RAID controller (switch to AHCI mode)Downloading and installing the IRST APPXSteps1.Turn on your computer.2.Go to /support.3.Click Product support, enter the Service Tag of your computer, and then click Search.If you do not have the Service Tag, use the product ID or manually browse for your computer model.4.Click Drivers & downloads > Find drivers.5.Scroll down the page and expand Serial ATA.6.Click Download to download the IRST APPX for your computer.7.After the download is complete, navigate to the folder where you saved the IRST APPX file.8.Double-click the IRST APPX file icon and follow the instructions on the screen.Downloading and installing the IRST driverSteps1.Turn on your computer.2.Go to /support.3.Click Product support, enter the Service Tag of your computer, and then click Search.If you do not have the Service Tag, use the product ID or manually browse for your computer model.4.Click Drivers & downloads > Find drivers.5.Scroll down the page and expand Serial ATA.6.Click Download to download the IRST driver for your computer.7.After the download is complete, navigate to the folder where you saved the IRST driver file.8.Double-click the driver file icon and follow the instructions on the screen.GraphicsThe Windows operating system includes the VGA-graphics driver only. For optimal graphics performance, install the Dell graphics driver applicable to your computer from /support.Downloading and installing the Dell graphics driverSteps1.Turn on your computer.2.Go to /support.3.Click Product support, enter the Service Tag of your computer, and then click Search.If you do not have the Service Tag, use the product ID or manually browse for your computer model.12Reinstallation sequence for drivers and applications4.Click Drivers & downloads > Find drivers.5.Scroll down the page and expand Video.6.Click Download to download the graphics driver for your computer.7.After the download is complete, navigate to the folder where you saved the graphics driver file.8.Double-click the graphics driver file icon and follow the instructions on the screen.AudioThe Windows operating system does not include the audio driver recommended by Dell. Install the HD audio driver available for download from /support.Downloading and installing the Dell audio driverSteps1.Turn on your computer.2.Go to /support.3.Click Product support, enter the Service Tag of your computer, and then click Search.If you do not have the Service Tag, use the product ID or manually browse for your computer model.4.Click Drivers & downloads > Find drivers.5.Scroll down the page and expand Audio.6.Click Download to download the audio driver for your computer.7.After the download is complete, navigate to the folder where you saved the audio driver file.8.Double-click the audio driver file icon and follow the instructions on the screen.Wireless Local Network (WLAN) drivers and applicationsThe Windows operating system does not provide native-device driver support for WLAN controllers on Dell computers. To obtain wireless network functionality, install the relevant WLAN drivers from the Dell support site. WLAN applications, which provide additional features including enterprise authentication enhancements, can also be installed from the Dell support site. Downloading and installing the Wi-Fi driverSteps1.Turn on the computer.2.Go to /support.3.Click Product support, enter the Service Tag of your computer, and then click Search.If you do not have the Service Tag, use the product ID or manually browse for your computer model.4.Click Drivers & downloads > Find drivers.5.Scroll down the page and expand Network.6.Click Download to download the Wi-Fi driver for your computer.7.After the download is complete, navigate to the folder where you saved the Wi-Fi driver file.8.Double-click the Wi-Fi driver file icon and follow the instructions on the screen.Reinstallation sequence for drivers and applications13.NET Framework The .NET Framework is a software framework from Microsoft, which is bundled with Windows operating systems. The .NET Framework is intended to be used by applications created for the Windows platform. FrameworkGetting help and contacting Dell Self-help resourcesYou can get information and help on Dell products and services using these self-help resources:Table 1. Self-help resourcesSelf-help resources Resource locationInformation about Dell products and services TipsContact Support In Windows search, type Contact Support, and pressEnter.Online help for operating system /support/windowsAccess top solutions, diagnostics, drivers and downloads, and learn more about your computer through videos, manuals and documents.Your Dell computer is uniquely identified by a Service Tag or Express Service Code. To view relevant support resources for your Dell computer, enter the Service Tag or Express Service Code at /support.For more information on how to find the Service Tag for your computer, see Locate the Service Tag on your computer.Dell knowledge base articles for a variety of computer concerns 1.Go to /support.2.On the menu bar at the top of the Support page, selectSupport > Knowledge Base.3.In the Search field on the Knowledge Base page, type thekeyword, topic, or model number, and then click or tap the search icon to view the related articles.Contacting Dell/contactdell.Availability varies by country/region and product, and some services may not be available in your country/region.If you do not have an active Internet connection, you can find contact information about your purchase invoice,Getting help and contacting Dell15。
专业英语

Chapter 1物流管理logistics management 客户服务customer service物资搬运material handling 订单处理order processing需求处理demand forecasting 退货处理return goods handling零配件和服务支持parts and service support工厂及仓库选址factory and warehouse site selection存货管理inventory management 逆向物流reverse logistics产出点point of origin 消费点point of consumption物流成本logistics cost 条码bar coding销售损失lost sale 内部成本internal cost退货处理成本return goods handling 外部成本external cost潜在的销售potential future sale 订单传输order transmittal运输成本transportation cost 订单输入order entry进货渠道inbound channel 批量成本lot quantity cost出货渠道outbound channel 缺货stockout订单处理成本order processing cost 库存持有成本inventory carrying cost需求预测demanding forecasting 资金成本capital cost销售沟通distribution communication 仓储空间成本storage space cost电子数据交换系统electronic data interchange 风险成本risk cost卫星数据传输satellite data transmissionChapter 2供应链supply chain 人力资源human resource最终用户end-customer 上游供应商upper stream supplier供应链管理supply chain management 供应链整合supply chain integration货物流product flow 下游企业down stream firm核心能力core competency 物资供应material procurement信息流information flow供应链战略管理Supply chain strategy 多数供应商战略Many suppliers strategy 少数供应商战略Few suppliers strategy 纵向整合战略Vertical integration企业集团Keiretsu networks 虚拟企业Virtual company前项整合Foreward integration 后项整合Backward integration规模经济Economy of scale 成本降低Cost reductionChapter 3产品移动product movement 门到门door-to-door在途库存in-transit inventory 有效利用能源energy-efficient有害物质hazardous material 灵活性和通用性flexibility and versatility 远洋运输Ocean going ships 建筑材料building materials价格优势price advantage 跨西伯利亚铁路the Trans Siberian railway多式联运工业中心multi-modal transport industrial center空箱装货地empty container place of loading拼箱系统化运输groupage container systematic transfer公铁运输长距离运输road-rail transport long distance movement LASH: lighter abroad shipCFS: container freight stationFCL: full container loadLCL: less than container loadTEU:twenty-foot equivalent units商业交易运输环境Commercial transactions transportation environment 信息流服务业务Information flow service business合理的费用潜在的买主reasonable cost potential vendors主要优势商业企业primary advantage commercial enterprises安全标准运输需求safety standards transportation demandsChapter 4资金周转Cash flow 运输成本transport cost现场仓库field warehouse 中间商Intermediary-consumer/user网络结构Network structure 运输工具Transport vestment延期交货订单back- orders分拨渠道distribution channel 库存周转inventory turnover库存管理Inventory Management 存置成本holding cost生产时间进度安排Production schedule 按程序工作Work in process库存单位stock keeping units 前置期Lead time搬运成本carrying cos t 容量计划Capacity planning撤回Withdraw 分类assortment装配线assembly line 在手上On hand大量客户化mass customization 与……联合associated with交通堵塞Traffic congestion 裁剪tailorChapter 5竞争武器competitive weapon 库存水平inventory levels潜在的问题potential problem 物流活动logistics activities最终顾客ultimate customer 信息技术information technologies物流信息系统logistics information system 实时销售信息real-time sales data决策相关信息decision-relevant information决策支持系统Decision support systems 长期预测long-term forecast 库存控制inventory controlwarehouse management systems (WMS) :仓储管理系统Transportation management systems (TMS):运输管理系统material flows :物料流material handling automation :物料处理的自动化Enterprise resource planning systems (ERP) :企业资源计划系统purchasing orders :采购订单duplicate records :备份记录financial records :财务记录sales orders:销售订单promise system:保证系统最终用户和销售伙伴end-use customers and reseller partners.替代程序alternative program 客户服务customers service产品和价格信息products and price information网上销售on-line sales 运营成本operating cost前置期l ead time 软件下载download software复印成本duplicate costs 技术支持technical support订单递交order submissionChapter 6仓储操作warehousing operation 运送路线delivery route基本布局basic layout 标识marking按订单分解order pick 产品编号product number储存区storage area 仓库管理系统warehouse management system 大批量运输large quantity shipments 订单要求order requirement办公管理clerical/office administration 运输目的地shipping destination装运检验shipment content checking 运输工具transportation facilities升降货车lift truck 搬运信息handling information仓储设施warehouse facility 温控仓库temperature-controlled warehouse 公共仓库public warehousing 进口税imported duty自用仓库private warehousing 罐装储存tank storage广告成本advertising cost 易腐食品perishable products首笔投资initial investment 农产品agricultural products客户服务customer service 大宗散装存储产品bulk storage products服务水平service level 普通商品库存general commodity warehouse 竞争动力competitive drive 冷藏仓库refrigerated warehouse制造商manufacturer 特种商品库存special commodity warehouse 经销商distributor 保税仓库bonded warehouseChapter 7物资操作系统materials handling system机械化操作系统mechanized materials handling system自动化操作系统automated materials handling system信息导向操作系统information-directed materials handling system存储和订单处理设备storage and order picking equipment运输和分类设备transportation and sorting equipment出货设备shipping equipment自动化导向车辆系统automated guided vehicle systems(AGVS)计算机分类computerized sortation活动货架live rack高层自动化存取系统high-rise storage and retrieval systems射频波控制设备RF-controlled equipment光导向操作light-directed operations订货拣选系统order selection system叉车lift truck 步行码垛车walkie-rider pallet truck拖缆towline 旋转式输送带carousel单元负载unit load 动力结构装置power configuration installation高垛叉车high-stacking truck 库存存储位置inventory storage location出运货物和收货入库作业shipping and receiving operation订单拣货order selection 高密度旋转储存high-density carousel storageChapter 8商业包装marketing package 国内外市场the domestic and world markets工业包装industrial package 包装工业packaging industry产品质量quality of products 无损伤货物damage-free goods包装的功能functions of packaging通用商品码UPC (Universal Product Code)主箱master carton 处理成本disposal cost运输容积和重量transportation cube and weight可回收使用的容器returnable container标准结构standard configuration 容积利用率cube utilization订货数量order quantities 体积最小化cube minimization运输成本transportation cost 运输效率transportation efficiency 包装尺寸packaging size/cube 真空包装vacuum-packed环保包装environmental packaging 载重量weight utilizationChapter 9实物配送Physical distribution 实物履行Physical fulfillment订单处理Order process 客户要求Customer requirements集约式分销intensive distribution 选择性分销selective distribution独家分销exclusive distribution 零售价retail price配送中心Distribution center 物流节点Logistics link总装配Final assembly 成批地value-added activities销售时点信息系统point of sales information system有效顾客反应Efficient consumer response需求链Demand chain 外部顾客external customer增值活动接受订单take orders作文SHANGHAI OCEAN SHIPPING COMPANY378 Dong Daming Road, Shanghai, P.C. 200080, ChinaTelephone: 65416620Telex: 33057 COSCO CNFax: 65458984Cable Address: COSCO SHNAGHAIMarch 3, 2007 Diamond Logistics Ltd.47 Federal StreetSpringfieldMassachusetts 01101U.S.A.Attention: Mr. David SmithDear Mr. Smith,Re: Chartering a VesselThank you for your letter of February 25.We are pleased to inform you that we have been able to secure the vessel you asked for. She is the M.V. Dong Fang, a bulk carrier, and is docked at present in Ningbo. She has a cargo capacity of ten thousand tons and a speed of 24 knots which will certainly be able to make the number of trips you mentioned.Please give us an early reply to confirm the charter and we will send you the charter party.Yours sincerely,COSCO SHANGHAI(Signed)…Wu Chen, ManagerCharter Department。
英文版统计学_Chapter2

uniform, or skewed).
90
4. Outliers: Sample values 80
that lie very far away
70
60
from the vast majority of 50
East
other sample values.
40
West
30
North
5. Time: Changing characteristics of the data over time.
Class Midpoints
64.5 74.5 84.5 94.5 104.5 114.5 124.5
Copyright © 2010,P2e0a0r7so, n20E0d4uPcaetairosnon Education, Inc. All Rights Reserved.
2.1 - 14
Class Width
6. Take each individual data value and put a tally mark in the appropriate class. Add the tally marks to get the frequency.
Copyright © 2010,P2e0a0r7so, n20E0d4uPcaetairosnon Education, Inc. All Rights Reserved.
2. Variation: A measure of the amount that the data values vary.
3. Distribution: The nature or shape of the spread of
data over the range of values (such as bell-shaped,
数据库系统基础教程(第二版)课后习题答案2
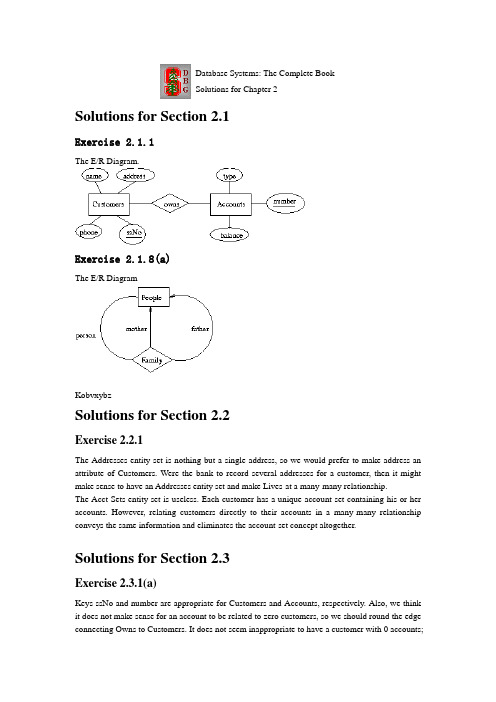
Database Systems: The Complete BookSolutions for Chapter 2Solutions for Section 2.1Exercise 2.1.1The E/R Diagram.Exercise 2.1.8(a)The E/R DiagramKobvxybzSolutions for Section 2.2Exercise 2.2.1The Addresses entity set is nothing but a single address, so we would prefer to make address an attribute of Customers. Were the bank to record several addresses for a customer, then it might make sense to have an Addresses entity set and make Lives-at a many-many relationship.The Acct-Sets entity set is useless. Each customer has a unique account set containing his or her accounts. However, relating customers directly to their accounts in a many-many relationship conveys the same information and eliminates the account-set concept altogether.Solutions for Section 2.3Exercise 2.3.1(a)Keys ssNo and number are appropriate for Customers and Accounts, respectively. Also, we think it does not make sense for an account to be related to zero customers, so we should round the edge connecting Owns to Customers. It does not seem inappropriate to have a customer with 0 accounts;they might be a borrower, for example, so we put no constraint on the connection from Owns to Accounts. Here is the The E/R Diagram,showing underlined keys andthe numerocity constraint.Exercise 2.3.2(b)If R is many-one from E1 to E2, then two tuples (e1,e2) and (f1,f2) of the relationship set for R must be the same if they agree on the key attributes for E1. To see why, surely e1 and f1 are the same. Because R is many-one from E1 to E2, e2 and f2 must also be the same. Thus, the pairs are the same.Solutions for Section 2.4Exercise 2.4.1Here is the The E/R Diagram.We have omitted attributes other than our choice for the key attributes of Students and Courses. Also omitted are names for the relationships. Attribute grade is not part of the key for Enrollments. The key for Enrollements is studID from Students and dept and number from Courses.Exercise 2.4.4bHere is the The E/R Diagram Again, we have omitted relationship names and attributes other than our choice for the key attributes. The key for Leagues is its own name; this entity set is not weak. The key for Teams is its own name plus the name of the league of which the team is a part, e.g., (Rangers, MLB) or (Rangers, NHL). The key for Players consists of the player's number and the key for the team on which he or she plays. Since the latter key is itself a pair consisting of team and league names, the key for players is the triple (number, teamName, leagueName). e.g., JeffGarcia is (5, 49ers, NFL).Database Systems: The Complete BookSolutions for Chapter 3Solutions for Section 3.1Exercise 3.1.2(a)We can order the three tuples in any of 3! = 6 ways. Also, the columns can be ordered in any of 3! = 6 ways. Thus, the number of presentations is 6*6 = 36.Solutions for Section 3.2Exercise 3.2.1Customers(ssNo, name, address, phone)Flights(number, day, aircraft)Bookings(ssNo, number, day, row, seat)Being a weak entity set, Bookings' relation has the keys for Customers and Flights and Bookings' own attributes.Notice that the relations obtained from the toCust and toFlt relationships are unnecessary. They are:toCust(ssNo, ssNo1, number, day)toFlt(ssNo, number, day, number1, day1)That is, for toCust, the key of Customers is paired with the key for Bookings. Since both include ssNo, this attribute is repeated with two different names, ssNo and ssNo1. A similar situation exists for toFlt.Exercise 3.2.3Ships(name, yearLaunched)SisterOf(name, sisterName)Solutions for Section 3.3Exercise 3.3.1Since Courses is weak, its key is number and the name of its department. We do not have arelation for GivenBy. In part (a), there is a relation for Courses and a relation for LabCourses that has only the key and the computer-allocation attribute. It looks like:Depts(name, chair)Courses(number, deptName, room)LabCourses(number, deptName, allocation)For part (b), LabCourses gets all the attributes of Courses, as:Depts(name, chair)Courses(number, deptName, room)LabCourses(number, deptName, room, allocation)And for (c), Courses and LabCourses are combined, as:Depts(name, chair)Courses(number, deptName, room, allocation)Exercise 3.3.4(a)There is one relation for each entity set, so the number of relations is e. The relation for the root entity set has a attributes, while the other relations, which must include the key attributes, have a+k attributes.Solutions for Section 3.4Exercise 3.4.2Surely ID is a key by itself. However, we think that the attributes x, y, and z together form another key. The reason is that at no time can two molecules occupy the same point.Exercise 3.4.4The key attributes are indicated by capitalization in the schema below:Customers(SSNO, name, address, phone)Flights(NUMBER, DAY, aircraft)Bookings(SSNO, NUMBER, DAY, row, seat)Exercise 3.4.6(a)The superkeys are any subset that contains A1. Thus, there are 2^{n-1} such subsets, since each of the n-1 attributes A2 through An may independently be chosen in or out.Solutions for Section 3.5Exercise 3.5.1(a)We could try inference rules to deduce new dependencies until we are satisfied we have them all.A more systematic way is to consider the closures of all 15 nonempty sets of attributes.For the single attributes we have A+ = A, B+ = B, C+ = ACD, and D+ = AD. Thus, the only new dependency we get with a single attribute on the left is C->A.Now consider pairs of attributes:AB+ = ABCD, so we get new dependency AB->D. AC+ = ACD, and AC->D is nontrivial. AD+ = AD, so nothing new. BC+ = ABCD, so we get BC->A, and BC->D. BD+ = ABCD, giving usBD->A and BD->C. CD+ = ACD, giving CD->A.For the triples of attributes, ACD+ = ACD, but the closures of the other sets are each ABCD. Thus, we get new dependencies ABC->D, ABD->C, and BCD->A.Since ABCD+ = ABCD, we get no new dependencies.The collection of 11 new dependencies mentioned above is: C->A, AB->D, AC->D, BC->A, BC->D, BD->A, BD->C, CD->A, ABC->D, ABD->C, and BCD->A.Exercise 3.5.1(b)From the analysis of closures above, we find that AB, BC, and BD are keys. All other sets either do not have ABCD as the closure or contain one of these three sets.Exercise 3.5.1(c)The superkeys are all those that contain one of those three keys. That is, a superkey that is not a key must contain B and more than one of A, C, and D. Thus, the (proper) superkeys are ABC, ABD, BCD, and ABCD.Exercise 3.5.3(a)We must compute the closure of A1A2...AnC. Since A1A2...An->B is a dependency, surely B is in this set, proving A1A2...AnC->B.Exercise 3.5.4(a)Consider the relationThis relation satisfies A->B but does not satisfy B->A.Exercise 3.5.8(a)If all sets of attributes are closed, then there cannot be any nontrivial functional dependenc ies. For suppose A1A2...An->B is a nontrivial dependency. Then A1A2...An+ contains B and thus A1A2...An is not closed.Exercise 3.5.10(a)We need to compute the closures of all subsets of {ABC}, although there is no need to think about the empty set or the set of all three attributes. Here are the calculations for the remaining six sets: A+ = AB+ = BC+ = ACEAB+ = ABCDEAC+ = ACEBC+ = ABCDEWe ignore D and E, so a basis for the resulting functional dependencies for ABC are: C->A and AB->C. Note that BC->A is true, but follows logically from C->A, and therefore may be omitted from our list.Solutions for Section 3.6Exercise 3.6.1(a)In the solution to Exercise 3.5.1 we found that there are 14 nontrivial dependencies, including the three given ones and 11 derived dependencies. These are: C->A, C->D, D->A, AB->D, AB-> C, AC->D, BC->A, BC->D, BD->A, BD->C, CD->A, ABC->D, ABD->C, and BCD->A.We also learned that the three keys were AB, BC, and BD. Thus, any dependency above that does not have one of these pairs on the left is a BCNF violation. These are: C->A, C->D, D->A, AC->D, and CD->A.One choice is to decompose using C->D. That gives us ABC and CD as decomposed relations. CD is surely in BCNF, since any two-attribute relation is. ABC is not in BCNF, since AB and BC are its only keys, but C->A is a dependency that holds in ABCD and therefore holds in ABC. We must further decompose ABC into AC and BC. Thus, the three relations of the decomposition are AC, BC, and CD.Since all attributes are in at least one key of ABCD, that relation is already in 3NF, and no decomposition is necessary.Exercise 3.6.1(b)(Revised 1/19/02) The only key is AB. Thus, B->C and B->D are both BCNF violations. The derived FD's BD->C and BC->D are also BCNF violations. However, any other nontrivial, derived FD will have A and B on the left, and therefore will contain a key.One possible BCNF decomposition is AB and BCD. It is obtained starting with any of the four violations mentioned above. AB is the only key for AB, and B is the only key for BCD.Since there is only one key for ABCD, the 3NF violations are the same, and so is the decomposition.Solutions for Section 3.7Exercise 3.7.1Since A->->B, and all the tuples have the same value for attribute A, we can pair the B-value from any tuple with the value of the remaining attribute C from any other tuple. Thus, we know that R must have at least the nine tuples of the form (a,b,c), where b is any of b1, b2, or b3, and c is any of c1, c2, or c3. That is, we can derive, using the definition of a multivalued dependency, that each of the tuples (a,b1,c2), (a,b1,c3), (a,b2,c1), (a,b2,c3), (a,b3,c1), and (a,b3,c2) are also in R.Exercise 3.7.2(a)First, people have unique Social Security numbers and unique birthdates. Thus, we expect the functional dependencies ssNo->name and ssNo->birthdate hold. The same applies to children, so we expect childSSNo->childname and childSSNo->childBirthdate. Finally, an automobile has a unique brand, so we expect autoSerialNo->autoMake.There are two multivalued dependencies that do not follow from these functional dependencies. First, the information about one child of a person is independent of other information about that person. That is, if a person with social security number s has a tuple with cn,cs,cb, then if there isany other tuple t for the same person, there will also be another tuple that agrees with t except that it has cn,cs,cb in its components for the child name, Social Security number, and birthdate. That is the multivalued dependencyssNo->->childSSNo childName childBirthdateSimilarly, an automobile serial number and make are independent of any of the other attributes, so we expect the multivalued dependencyssNo->->autoSerialNo autoMakeThe dependencies are summarized below:ssNo -> name birthdatechildSSNo -> childName childBirthdateautoSerialNo -> autoMakessNo ->-> childSSNo childName childBirthdatessNo ->-> autoSerialNo autoMakeExercise 3.7.2(b)We suggest the relation schemas{ssNo, name, birthdate}{ssNo, childSSNo}{childSSNo, childName childBirthdate}{ssNo, autoSerialNo}{autoSerialNo, autoMake}An initial decomposition based on the two multivalued dependencies would give us {ssNo, name, birthDate}{ssNo, childSSNo, childName, childBirthdate}{ssNo, autoSerialNo, autoMake}Functional dependencies force us to decompose the second and third of these.Exercise 3.7.3(a)Since there are no functional dependencies, the only key is all four attributes, ABCD. Thus, each of the nontrvial multivalued dependencies A->->B and A->->C violate 4NF. We must separate out the attributes of these dependencies, first decomposing into AB and ACD, and then decomposing the latter into AC and AD because A->->C is still a 4NF violation for ACD. The final set of relations are AB, AC, and AD.Exercise 3.7.7(a)Let W be the set of attributes not in X, Y, or Z. Consider two tuples xyzw and xy'z'w' in the relation R in question. Because X ->-> Y, we can swap the y's, so xy'zw and xyz'w' are in R. Because X ->-> Z, we can take the pair of tuples xyzw and xyz'w' and swap Z's to get xyz'w and xyzw'. Similarly, we can take the pair xy'z'w' and xy'zw and swap Z's to get xy'zw' and xy'z'w.In conclusion, we started with tuples xyzw and xy'z'w' and showed that xyzw' and xy'z'w must also be in the relation. That is exactly the statement of the MVD X ->-> Y-union-Z. Note that the above statements all make sense even if there are attributes in common among X, Y, and Z.Exercise 3.7.8(a)Consider a relation R with schema ABCD and the instance with four tuples abcd, abcd', ab'c'd, and ab'c'd'. This instance satisfies the MVD A->-> BC. However, it does not satisfy A->-> B. For example, if it did satisfy A->-> B, then because the instance contains the tuples abcd and ab'c'd, we would expect it to contain abc'd and ab'cd, neither of which is in the instance.Database Systems: The Complete BookSolutions for Chapter 4Solutions for Section 4.2Exercise 4.2.1class Customer {attribute string name;attribute string addr;attribute string phone;attribute integer ssNo;relationship Set<Account> ownsAcctsinverse Account::ownedBy;}class Account {attribute integer number;attribute string type;attribute real balance;relationship Set<Customer> ownedByinverse Customer::ownsAccts}Exercise 4.2.4class Person {attribute string name;relationship Person motherOfinverse Person::childrenOfFemalerelationship Person fatherOfinverse Person::childrenOfMalerelationship Set<Person> childreninverse Person::parentsOfrelationship Set<Person> childrenOfFemaleinverse Person::motherOfrelationship Set<Person> childrenOfMaleinverse Person::fatherOfrelationship Set<Person> parentsOfinverse Person::children}Notice that there are six different relationships here. For example, the inverse of the relationship that connects a person to their (unique) mother is a relationship that connects a mother (i.e., a female person) to the set of her children. That relationship, which we call childrenOfFemale, is different from the children relationship, which connects anyone -- male or female -- to their children.Exercise 4.2.7A relationship R is its own inverse if and only if for every pair (a,b) in R, the pair (b,a) is also in R. In the terminology of set theory, the relation R is ``symmetric.''Solutions for Section 4.3Exercise 4.3.1We think that Social Security number should me the key for Customer, and account number should be the key for Account. Here is the ODL solution with key and extent declarations.class Customer(extent Customers key ssNo){attribute string name;attribute string addr;attribute string phone;attribute integer ssNo;relationship Set<Account> ownsAcctsinverse Account::ownedBy;}class Account(extent Accounts key number){attribute integer number;attribute string type;attribute real balance;relationship Set<Customer> ownedByinverse Customer::ownsAccts}Solutions for Section 4.4Exercise 4.4.1(a)Since the relationship between customers and accounts is many-many, we should create a separate relation from that relationship-pair.Customers(ssNo, name, address, phone)Accounts(number, type, balance)CustAcct(ssNo, number)Exercise 4.4.1(d)Ther is only one attribute, but three pairs of relationships from Person to itself. Since motherOf and fatherOf are many-one, we can store their inverses in the relation for Person. That is, for each person, childrenOfMale and childrenOfFemale will indicate that persons's father and mother. The children relationship is many-many, and requires its own relation. This relation actually turns out to be redundant, in the sense that its tuples can be deduced from the relationships stored with Person. The schema:Persons(name, childrenOfFemale, childrenOfMale)Parent-Child(parent, child)Exercise 4.4.4Y ou get a schema like:Studios(name, address, ownedMovie)Since name -> address is the only FD, the key is {name, ownedMovie}, and the FD has a left side that is not a superkey.Exercise 4.4.5(a,b,c)(a) Struct Card { string rank, string suit };(b) class Hand {attribute Set theHand;};For part (c) we have:Hands(handId, rank, suit)Notice that the class Hand has no key, so we need to create one: handID. Each hand has, in the relation Hands, one tuple for each card in the hand.Exercise 4.4.5(e)Struct PlayerHand { string Player, Hand theHand };class Deal {attribute Set theDeal;}Alternatively, PlayerHand can be defined directly within the declaration of attribute theDeal. Exercise 4.4.5(h)Since keys for Hand and Deal are lacking, a mechanical way to design the database schema is to have one relation connecting deals and player-hand pairs, and another to specify the contents of hands. That is:Deals(dealID, player, handID)Hands(handID, rank, suit)However, if we think about it, we can get rid of handID and connect the deal and the player directly to the player's cards, as:Deals(dealID, player, rank, suit)Exercise 4.4.5(i)First, card is really a pair consisting of a suit and a rank, so we need two attributes in a relation schema to represent cards. However, much more important is the fact that the proposed schema does not distinguish which card is in which hand. Thus, we need another attribute that indicates which hand within the deal a card belongs to, something like:Deals(dealID, handID, rank, suit)Exercise 4.4.6(c)Attribute b is really a bag of (f,g) pairs. Thus, associated with each a-value will be zero or more (f,g) pairs, each of which can occur several times. We shall use an attribute count to indicate the number of occurrences, although if relations allow duplicate tuples we could simply allow duplicate (a,f,g) triples in the relation. The proposed schema is:C(a, f, g, count)Solutions for Section 4.5Exercise 4.5.1(b)Studios(name, address, movies{(title, year, inColor, length,stars{(name, address, birthdate)})})Since the information about a star is repeated once for each of their movies, there is redundancy. To eliminate it, we have to use a separate relation for stars and use pointers from studios. That is: Stars(name, address, birthdate)Studios(name, address, movies{(title, year, inColor, length,stars{*Stars})})Since each movie is owned by one studio, the information about a movie appears in only one tuple of Studios, and there is no redundancy.Exercise 4.5.2Customers(name, address, phone, ssNo, accts{*Accounts})Accounts(number, type, balance, owners{*Customers})Solutions for Section 4.6Exercise 4.6.1(a)We need to add new nodes labeled George Lucas and Gary Kurtz. Then, from the node sw (which represents the movie Star Wars), we add arcs to these two new nodes, labeled direc tedBy and producedBy, respectively.Exercise 4.6.2Create nodes for each account and each customer. From each customer node is an arc to a node representing the attributes of the customer, e.g., an arc labeled name to the customer's name. Likewise, there is an arc from each account node to each attribute of that account, e.g., an arc labeled balance to the value of the balance.To represent ownership of accounts by customers, we place an arc labeled owns from each customer node to the node of each account that customer holds (possibly jointly). Also, we placean arc labeled ownedBy from each account node to the customer node for each owner of that account.Exercise 4.6.5In the semistructured model, nodes represent data elements, i.e., entities rather than entity sets. In the E/R model, nodes of all types represent schema elements, and the data is not represented at all. Solutions for Section 4.7Exercise 4.7.1(a)<STARS-MOVIES><STAR starId = "cf" starredIn = "sw, esb, rj"><NAME>Carrie Fisher</NAME><ADDRESS><STREET>123 Maple St.</STREET><CITY>Hollywood</CITY></ADDRESS><ADDRESS><STREET>5 Locust Ln.</STREET><CITY>Malibu</CITY></ADDRESS></STAR><STAR starId = "mh" starredIn = "sw, esb, rj"><NAME>Mark Hamill</NAME><ADDRESS><STREET>456 Oak Rd.<STREET><CITY>Brentwood</CITY></ADDRESS></STAR><STAR starId = "hf" starredIn = "sw, esb, rj, wit"><NAME>Harrison Ford</NAME><ADDRESS><STREET>whatever</STREET><CITY>whatever</CITY></ADDRESS></STAR><MOVIE movieId = "sw" starsOf = "cf, mh"><TITLE>Star Wars</TITLE><YEAR>1977</YEAR></MOVIE><MOVIE movieId = "esb" starsOf = "cf, mh"><TITLE>Empire Strikes Back</TITLE><YEAR>1980</YEAR></MOVIE><MOVIE movieId = "rj" starsOf = "cf, mh"><TITLE>Return of the Jedi</TITLE><YEAR>1983</YEAR></MOVIE><MOVIE movieID = "wit" starsOf = "hf"><TITLE>Witness</TITLE><YEAR>1985</YEAR></MOVIE></STARS-MOVIES>Exercise 4.7.2<!DOCTYPE Bank [<!ELEMENT BANK (CUSTOMER* ACCOUNT*)><!ELEMENT CUSTOMER (NAME, ADDRESS, PHONE, SSNO)> <!A TTLIST CUSTOMERcustId IDowns IDREFS><!ELEMENT NAME (#PCDA TA)><!ELEMENT ADDRESS (#PCDA TA)><!ELEMENT PHONE (#PCDA TA)><!ELEMENT SSNO (#PCDA TA)><!ELEMENT ACCOUNT (NUMBER, TYPE, BALANCE)><!A TTLIST ACCOUNTacctId IDownedBy IDREFS><!ELEMENT NUMBER (#PCDA TA)><!ELEMENT TYPE (#PCDA TA)><!ELEMENT BALANCE (#PCDA TA)>]>Database Systems: The CompleteBookSolutions for Chapter 5Solutions for Section 5.2Exercise 5.2.1(a)PI_model( SIGMA_{speed >= 1000} ) (PC)Exercise 5.2.1(f)The trick is to theta-join PC with itself on the condition that the hard disk sizes are equal. That gives us tuples that have two PC model numbers with the same value of hd. However, these two PC's could in fact be the same, so we must also require in the theta-join that the model numbers be unequal. Finally, we want the hard disk sizes, so we project onto hd.The expression is easiest to see if we write it using some temporary values. We start by renaming PC twice so we can talk about two occurrences of the same attributes.R1 = RHO_{PC1} (PC)R2 = RHO_{PC2} (PC)R3 = R1 JOIN_{PC1.hd = PC2.hd AND PC1.model <> PC2.model} R2R4 = PI_{PC1.hd} (R3)Exercise 5.2.1(h)First, we find R1, the model-speed pairs from both PC and Laptop. Then, we find from R1 those computers that are ``fast,'' at least 133Mh. At the same time, we join R1 with Product to connect model numbers to their manufacturers and we project out the speed to get R2. Then we join R2 with itself (after renaming) to find pairs of different models by the same maker. Finally, we get our answer, R5, by projecting onto one of the maker attributes. A sequence of steps giving the desired expression is: R1 = PI_{model,speed} (PC) UNION PI_{model,speed} (Laptop)R2 = PI_{maker,model} (SIGMA_{speed>=700} (R1) JOIN Product)R3 = RHO_{T(maker2, model2)} (R2)R4 = R2 JOIN_{maker = maker2 AND model <> model2} (R3)R5 = PI_{maker} (R4)Exercise 5.2.2Here are figures for the expression trees of Exercise 5.2.1 Part (a)Part (f)Part (h). Note that the third figure is not really a tree, since it uses a common subexpression. We could duplicate the nodes to make it a tree, but using common subexpressions is a valuable form of query optimization. One of the benefits one gets from constructing ``trees'' for queries is the ability to combine nodes that represent common subexpressions.Exercise 5.2.7The relation that results from the natural join has only one attribute from each pair of equated attributes. The theta-join has attributes for both, and their columns are identical.Exercise 5.2.9(a)If all the tuples of R and S are different, then the union has n+m tuples, and this number is the maximum possible.The minimum number of tuples that can appear in the result occurs if every tuple of one relation also appears in the other. Surely the union has at least as many tuples as the larger of R and that is, max(n,m) tuples. However, it is possible for every tuple of the smaller to appear in the other, so it is possible that there are as few as max(n,m) tuples in the union.Exercise 5.2.10In the following we use the name of a relation both as its instance (set of tuples) and as its schema (set of attributes). The context determines uniquely which is meant.PI_R(R JOIN S) Note, however, that this expression works only for sets; it does not preserve the multipicity of tuples in R. The next two expressions work for bags.R JOIN DELTA(PI_{R INTERSECT S}(S)) In this expression, each projection of a tuple from S onto the attributes that are also in R appears exactly once in the second argument of the join, so it preserves multiplicity of tuples in R, except for those thatdo not join with S, which disappear. The DELTA operator removes duplicates, as described in Section 5.4.R - [R - PI_R(R JOIN S)] Here, the strategy is to find the dangling tuples of R and remove them.Solutions for Section 5.3Exercise 5.3.1As a bag, the value is {700, 1500, 866, 866, 1000, 1300, 1400, 700, 1200, 750, 1100, 350, 733}. The order is unimportant, of course. The average is 959.As a set, the value is {700, 1500, 866, 1000, 1300, 1400, 1200, 750, 1100, 350, 733}, and the average is 967. H3>Exercise 5.3.4(a)As sets, an element x is in the left-side expression(R UNION S) UNION Tif and only if it is in at least one of R, S, and T. Likewise, it is in the right-side expressionR UNION (S UNION T)under exactly the same conditions. Thus, the two expressions have exactly the same members, and the sets are equal.As bags, an element x is in the left-side expression as many times as the sum of the number of times it is in R, S, and T. The same holds for the right side. Thus, as bags the expressions also have the same value.Exercise 5.3.4(h)As sets, element x is in the left sideR UNION (S INTERSECT T)if and only if x is either in R or in both S and T. Element x is in the right side(R UNION S) INTERSECT (R UNION T)if and only if it is in both R UNION S and R UNION T. If x is in R, then it is in both unions. If x is in both S and T, then it is in both union. However, if x is neither in R nor in both of S and T, then it cannot be in both unions. For example, suppose x is not in R and not in S. Then x is not in R UNION S. Thus, the statement of when x is in the right side is exactly the same as when it is in the left side: x is either in R or in both of S and T.Now, consider the expression for bags. Element x is in the left side the sum of the number of times it is in R plus the smaller of the number of times x is in S and the number of times x is in T. Likewise, the number of times x is in the right side is the smaller ofThe sum of the number of times x is in R and in S.The sum of the number of times x is in R and in T.A moment's reflection tells us that this minimum is the sum of the number of times x is in R plus the smaller of the number of times x is in S and in T, exactly as for the left side.Exercise 5.3.5(a)For sets, we observe that element x is in the left side(R INTERSECT S) - T。
计算机导论第一章测试题

Test Bank—Chapter One (Data Representation)Multiple Choice Questions1. Which of the following Boolean operations produces the output 1 for the fewest number of input patterns?A. ANDB. ORC. XORANSWER: A2. Which of the following best describes the NOR operation?A. An XOR followed by a NOTB. An OR followed by a NOTC. A NOT followed by a NOT C. An AND followed by a NOTANSWER: B3. Which of the following bit patterns cannot be expressed in hexadecimal notation?A. 11111111B. 1001C. 110011D. 100000000001ANSWER: C4. Which of the following is the binary representation of 4 5/8?A. 100.11B. 10.011C. 110.101D. 100.101ANSWER: D5. Which of the following bit patterns represents the value 5 in two’s complement notation?A. 00011010B. 11111011C. 00000101D. 11111011ANSWER: C6. Which of the following bit patterns represents the value -5 in two’s complement notation?A. 00011010B. 11111011C. 00000101D. 11111011ANSWER: D7. In which of the following addition prob lems (using two’s complement notation) does an overflow error occur?A. 0011B. 0100C. 1100+ 1010 + 0100 + 1100ANSWER: B8. Which of the following representations in two’s complement notation represents the largest value?A. 00000010B. 11111111C. 00000001D. 11111110ANSWER: A9. Which of the following bit patterns (represented in hexadecimal notation) represents a negative number in two’s complement notation?A. 7FB. 55C. A6D. 08ANSWER: C10. What value is represented by the bit pattern 01011100 when interpreted using floating-point format in which the most significant bit is the sign bit, the next three bits represent the exponent field in excess notation, and the last four bits represent the mantissa?A. -1 1/2B. 1 1/2C. -3/8D. 3/8ANSWER: B11. Which of the following values cannot be stored accurately using a floating-point format in which the most significant bit is the sign bit, the next three bits represent the exponent field in excess notation, and the last four bits represent the mantissa?A. 2 1/2B. 3/16C. 7D. 6 1/4ANSWER: D121. Which of the following bit-patterns represents the smallest value using the floating-point format in which the most significant bit is the sign bit, the next three bits represent the exponent field in excess notation, and the last four bits represent the mantissa?A. 01001000B. 01011000C. 00101000D. 01111000ANSWER: C13. Which of the following data storage systems provides the most efficient random access to individual data items?A. Main memoryB. Magnetic diskC. Optical CDs and DVDsANSWER: A14. Which of the following storage systems is best suited for storing and retrieving long strings of data that are processed in their sequential order?A. Main memoryB. Magnetic diskC. Optical CDs and DVDsANSWER: C15. Which of the following mass storage system does not require physical motion?A. Magnetic tapeB. Magnetic diskC. DVDsD. Flash drives ANSWER: D16. Assuming that each of the following bit patterns originally had even parity, which one contains an error?A. 10110100B. 11000011C. 00011000D. 10001001 ANSWER: D17. How many errors per pattern could be corrected when using an error-correcting code in which any two code patterns differ by a Hamming distance of 8?A. 3B. 4C. 5D. 6ANSWER: A18. Which of the following is a possible LZW compression of the message “xyz xyz xyz”?A. 1234B. 1234545C. 232D. 12ANSWER: B19. How many different symbols can be encoded using Unicode?A. 256B. 4,096C. 65,536D. 1,046,476ANSWER: C20. Which of the following systems is least efficient when encoding numeric values?A. Two’s complement notationB. Excess notationC. ASCIID. Floating-point notationANSWER: C21. Which of the following is a means of encoding music?A. ASCIIB. MIDIC. JPEGD. GIFANSWER: BVocabulary (Matching) QuestionsThe following is a list of terms from the chapter along with descriptive phrases that can be used to produce questions (depending on the topics covered in your course) in which the students are ask to match phrases and terms. An example would be a question of the form, “In the blank next to each phrase, write the term fr om the following list that is best described by the phrase.”Term Descriptive Phrasebit Binary digitBoolean operation AND, OR, XOR, NOTaddress A numeric value used to identify a memory cellhexadecimal notation An efficient way of representing bit patternssector A segment of a track in a mass storage systemzoned-bit recording A means of increasing the storage capacity of a magnetic disk system buffer A storage area used to hold data on a temporary basis, often as a stepin transferring the data from one device to anotherISO An international organization for establishing standardsANSI A major standardization organization within the United StatesASCII A system developed by the American Standards Institute for encodingtext.flip-flop A digital circuit capable of holding a single digittwo’s complement notation A means of encoding whole numbersfloating-point notation A means of encoding numeric values that may involve fractions truncation An error that may occur when using floating-point notationpixel A small part of an imageGIF A means of compressing an image file by restricting the number ofcolors availableJPEG A means of compressing images by blurring the boundaries betweendifferent colors while maintaining all brightness information Unicode A means of encoding text in which each symbol is represented by 16bitsLZW An example of adaptive dictionary encodingMIDI A means of encoding music in terms of notes and instruments ratherthan actual audioKey field A part of a logical record in a file used to identify the record.VLSI A means of constructing complex circuitry in a very small space.。
Chapter_02 实证分析工具

Observational Studies
Observational study – empirical study relying on observed data not obtained from experimental study Sources of observational data
2-3
Experimental Studies
Biased estimates Counterfactual Experimental (or randomized) study
2-4
Conducting an Experimental Study
Random assignment to control and treatment groups
Dependent variable Independent variables Parameters Stochastic error term L
Regression analysis
Regression line Standard error
Intercept is α0
Slope is α1
α0 wn
2-8
Types of Data
Cross-sectional data Time-series data Panel data
2-9
Pitfalls of Observational Studies
Data collected in non-experimental setting Specification issues
2-5
Pitfalls of Experimental Studies
Ethical issues Technical problems Response bias Impact of limited duration of experiment Generalization of results to other populations, settings, and related treatments Black box aspect of experiments
avid venue 12.2 手册- 使用单机软件说明书
Chapter 24: Using the Standalone SoftwareVENUE Standalone software lets you do all of the following to preconfigure performances, wherever you can use your lap-top:•Learn the basics of the VENUE software interface in prep-aration for working at a full VENUE system. •Assign hardware I/O and routing, and name channels.•Set channel input, EQ, dynamics, pan, and other set-tings. •Create and maintain a library of setups, with access to nearly all parameters available on the control surface. •Store and recall Snapshots, and configure Events.•Use the Filing features to transfer Shows, Shows Folders, and plug-in presets to/from a compatible USB storage de-vice to transfer data between the standalone software and VENUE.Differences Between Standalone Software and a VENUE SystemThe Standalone software is nearly identical to that on a full VENUE system, with the following differences:Audio ThroughputYou cannot play audio through the Standalone software. Real-time audio requires the VENUE hardware.Plug-In EditingWhen a Show is transferred from a complete VENUE system, all plug-ins installed on the D-Show system are visible in the Standalone software as offline (unavailable) plug-ins. You can assign offline plug-ins to racks, and assign plug-in rack routing in the Standalone software, and save the routing in snapshots.Hardware ConfigurationIn the Standalone software, you can simulate the hardware configuration of a destination system from the Devices tab of the Options page.System RequirementsThe following are the minimum system requirements for us-ing the VENUE Standalone software:•Computer running Windows XP Pro or XP HomeEdition O/S, Service Pack 1 (Macintosh not supported)•Minimum 1024 x 768 screen resolution•Minimum 16-bit color graphics, 32-bit recommended •Minimum 256 MB RAM, 512 MB recommended •Minimum 200 MB of available hard disk space, 512 MB recommended •CD-ROM drive for installation (unless installing from web-download)•Available USB 1.1 or 2.0 port and compatible USB storage device (such as a flash disk, key disk or other external hard drive) for file transfer Installation requires Windows Administrator permissions. Once installed, the software can be run under Admin or User accounts.Installing the Standalone SoftwareTo install the VENUE Standalone software:1 Do one of the following:•Download the VENUE Standalone Software Installer from the website ().– or –•Insert your VENUE Software Installer into the CD-ROM drive on your Windows XP-compatible computer.2 Launch the installer and follow the instructions on-screen.The VENUE Standalone software requires no authorization.Removing the Standalone SoftwareTo remove the VENUE Standalone software:1 Launch the Add/Remove Programs Control Panel.2 Choose VENUE , then follow the instructions on-screen.Transferring data must be done to/from a compatible USB storage device such as a USB key disk or other external USB hard drive.You cannot install plug-ins or adjust plug-in parametersunless you are working on the complete VENUE system.Simulating a VENUE ConfigurationYou can use the Standalone software to simulate a VENUE sys-tem with any number of input and outputs. The correspond-ing inputs and outputs become available in the Patchbay, al-lowing you to prepare a show that can transfer directly to the destination system.To simulate a VENUE system:1 Launch the Standalone software.2 Go to the Options page and click the Devices tab.3 Right-click the console graphic and choose the type of con-sole you will be working with.4 Right-click an I/O graphic and choose the type of I/O (as available) and specify the number of Input and Output cards on the destination system.Transfer and Filing Quick StartThe basic steps for using the Standalone software and data transfer are as follows:•Save data to disk, then transfer it to an external USB storage device.•Transfer data from the USB device, then load the data. Save and Transfer Data from aVENUE SystemTo save and transfer data from the complete system:1 Connect a USB storage device to a VENUE USB port.2 Use the Save tab of the Filing page to save VENUE data to disk.3 Go to the Filing page and click the Transfer tab.4 Do one of the following to select the type of data to transfer:•To transfer all data, click the Console icon.•To transfer Console Settings, click the Settings icon.•To transfer Show Folders, click the Show Folders icon.•To transfer individual Shows, click the Shows icon.•To transfer Preset Folders, click the Preset Folders i con.•To transfer Presets for individual items, click the Built-In icon or the Plug-In i con and choose a processor, plug-in or Input Channel Presets item from the pop-up menu, orclick the Scope Sets icon.5 In the left column, select the items you want to transfer from VENUE to the portable storage device.6 Click the Transfer button.Adding Stage Rack inputs and outputsFor complete instructions on transferring data, see Chapter20, “Shows and File Management.”Transferring Show files from VENUETransfer and Load Data to theStandalone Software1 Connect the USB storage device to your laptop. Make sure the drive is mounted before proceeding.2 Launch the VENUE standalone software.3 Go to the Filing page and click the Transfer tab.4 Make sure your USB disk is available in the list at right.5 Click the Console, Settings, Show Folders, Shows, Preset Fold-ers, Built-In, Plug-In or Scope Set selectors to select the type of data you want to transfer.6 Click the Transfer button. The data is transferred from the USB device to the appropriate VENUE data folders on the lap-top.7 If you chose Console, data is automatically loaded and ap-plied. If you chose any other data type, go to the Filing page and click the Load tab, and load the newly transferred data into the Standalone software.Creating and Editing Shows and PresetsUse the techniques explained throughout this guide to assign routing, rename channels, and to configure other parameters. Then do the following to save and transfer your work to a complete system.To save and transfer VENUE data from the standalone software to the complete system:1 Connect a USB storage device to an available USB port on your laptop.2 Using the Save tab of the Filing page, save data to disk.3 Go to the Filing page and click the Transfer tab, and transfer saved data to a compatible USB storage device.4 Connect the USB storage device to an available USB port on the complete system.5 Use the Transfer tab of the Filing page to transfer the VENUE data from the USB storage device.6 Use the Load tab of the Filing page to load the transferred data.CD TransferThe VENUE system provides a CD-ROM drive that can also be used as a source device for VENUE data transfer. (You cannot write data to the FOH Rack CD-ROM drive; it is read-only.)To use a CD for transfer:1 Using the Standalone software on a laptop or other com-puter, create and save a show.2 Locate the VENUE data folder on the system drive.3 Copy that folder and its contents to a CD-ROM. Make sure the folder is at the root level of the CD-ROM.4 Burn or write the disc as a Windows-compatible CD-ROM.5 Insert the CD-ROM into a VENUE CD-ROM drive.6 In the Filing screen, select the CD-ROM drive as the source for file transfer.7 When the transfer is complete, eject the CD-ROM.Transferring a Scope Set for the standalone softwareClickLeaving a disc in the CD-ROM drive of a VENUE systemcan slow down the response of some software screens, so itis recommended that you not leave any disc in the drive dur-ing a performance. This only applies to a VENUE CD-ROMdrive (not the laptop on which you’re running the stand-alone software).Exporting System Information and Patchbay InformationWith Standalone software, a complete system description and/or the contents of each Patchbay page can be exported to a text file. These can be useful for generating an input list (line list) directly from the system. For example, build and custom-ize the Patchbay for an upcoming show, then export and print the channel names list for use during sound check. To print a system description:1 Go to the Options > System tab.2 Click the Info button and follow the on-screen instructionsto print a complete system description.For more information, see “VENUE System Information Ex-port” on page 110. To export Patchbay names:1 Go to the Patchbay page you want to export.2 Click the Export Patch List icon in the upper right corner ofthe screen.The Patchbay names appear in an open HTML file that you can save and print, or open in an HTML-compatible applica-tion for formatting or other modification. For more informa-tion, see “Patch List Export” on page 111.Export Patch List buttonClick to export as HTML。
计算机专业英语 第二章
标点符号
Seven-and Eight-Bit Codes
排列
With 7 bits , it’s possible to provide 128 变化, different arrangements; With 8 bits , 256 变种 variations are possible. They are sufficient number to code 小写字母 lower-case-letters (26) , and a large number of other characters (28) .
Registers
跟踪
全部的, 全面的
A register is a storage location inside the processor . Register in the control unit are used to keep track of the overall status of the program that is running . Control unit registers store information such as the current instruction .
2-2 WHAT IS A PROCESSOR
2-2
什么是处理器
Notes:
Instruction set 指令系统 Processor 处理器 Operation 操作 Operand 操作码 Clock 时钟 Megahertz(MHz) 兆赫 Word size 字长
Seven-and Eight-Bit Codes
The 7-bit American Standard Code for Information Interchange (ASCII) is widely used in data communications work and is by far the most popular code used to represent data internally in personal computers . by far 修饰比较级、最高级,强调数量、程度 等,意为“……得多,最……”。
数据库系统概念(英文精编版.第六版)
Atomicity of updates
Failures
may lead to inconsistencies (1) account_A = account_A – 100 (2) account_B = account_B + 100
Example:
Concurrent access by multiple users
Exercises
Computer users interacts with data in the _______ level A. physical B. logical C. view D. all of the above Application users interact with data in the _______ level. A. physical B. logical C. view D. all of the above How the data are actually stored is called _______ A. Physical level B. Logical level C. View level D. Conceptual level
property is called ( )
A. Data inconsistency C. Data isolation B. Data redundancy D. Data integrity
1.3 View of Data
Hierarchy of Abstraction Levels
Three Abstraction Levels of Data
机械工业出版社
本课程学习内容
关系数据模型 关系数据库语言
仓库温度分布测试
Understanding Temperature Mapping仓库温度分布测试探讨Is your organisation having to start, or repeat, temperature mapping efforts due to increasing regulations on warehouse storage and distribution practices? Are you facing difficulties in maintaining control of the temperature distribution within your storage areas? Are you looking to implement a simple framework of validation testing that aims to establish a sound strategy and approach for performing environmental mapping of storage areas?是否你的公司已经开始、或者重复进行温度分布测试活动,以便增加在仓库储存和分发上的法规符合性?你是否正在面对库房存储区域的温度维护控制的困难呢?你是否正在找一个可实现的验证测试,目的就是要建立一个合理的策略和方法用于存储区域的环境温度分布。
There is an increasing awareness that storage areas need to be environmentally mapped to protect product quality and customer safety. A comprehensive temperature mapping study will ensure that your storage area is accurately monitored, properly maintained and in compliance with all the applicable regulations.现在大家越来越意识到存储区域需要环境温度分布用于保障产品的质量和用户安全。
