Open Policy Network
5GC核心网基本概念

Session lifecycle level
起始于UE会话建立,结束于UE会话结束。 Session 可以包含1个或多个Procedure 。
Transaction Procedure Session
不需要处理状态信息的VNFC是无状态的VNFC。 需要处理状态信息的VNFC可以实现为: 一个有状态的VNFC。 具有外部状态的无状态VNFC。
Service Logic
Stateless Load Balancer
Other NF 通用NF无状态设计原则
无状态设计
•有状态处理和无状态服务逻 辑解耦 •有状态本地缓存的轻量级上 下文,容纳更多数据
•无状态LB保证流量在无状态 服务之间更加平衡
LB
网络切片实现智能管道,满足多种应用场景需求
网络切片
Cloud Database (UDSF/SDSF)
Stateless Service Local Cache
Stateful Service Local Cache
•Procedure 级无状态 •处理完成后,将数据存储在 CDB的上下文中,删除本地数 据
CDB
New scaled
Service Logic
•全网通信 •缩短网络路径
PDNGW
PCRF
MME
Serving GW
AMF SMF
…
PCF
UDM
服务化
•IP 地址
NRF
•FQDN
•支持的服务
•…
•NF服务到独立NRF注册/注销 •NRF和NF服务之间的状态检测 •NF服务自动管理,自动选择和自动扩展
(完整版)图情常规术语(中英文对照)
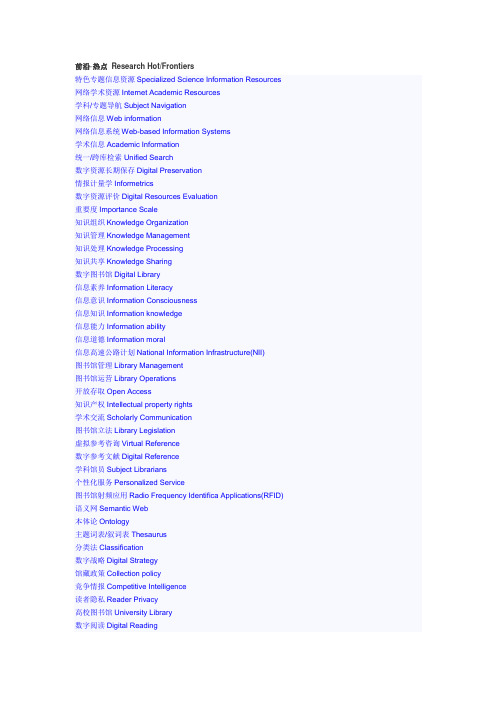
前沿·热点Research Hot/Frontiers特色专题信息资源Specialized Science Information Resources 网络学术资源Internet Academic Resources学科/专题导航Subject Navigation网络信息Web information网络信息系统Web-based Information Systems学术信息Academic Information统一/跨库检索Unified Search数字资源长期保存Digital Preservation情报计量学Informetrics数字资源评价Digital Resources Evaluation重要度Importance Scale知识组织Knowledge Organization知识管理Knowledge Management知识处理Knowledge Processing知识共享Knowledge Sharing数字图书馆Digital Library信息素养Information Literacy信息意识Information Consciousness信息知识Information knowledge信息能力Information ability信息道德Information moral信息高速公路计划National Information Infrastructure(NII)图书馆管理Library Management图书馆运营Library Operations开放存取Open Access知识产权Intellectual property rights学术交流Scholarly Communication图书馆立法Library Legislation虚拟参考咨询Virtual Reference数字参考文献Digital Reference学科馆员Subject Librarians个性化服务Personalized Service图书馆射频应用Radio Frequency Identifica Applications(RFID)语义网Semantic Web本体论Ontology主题词表/叙词表Thesaurus分类法Classification数字战略Digital Strategy馆藏政策Collection policy竞争情报Competitive Intelligence读者隐私Reader Privacy高校图书馆University Library数字阅读Digital Reading图像信息Image Information档案网站Archives website数字档案Digital Archive信息集成Information Integration社会网络分析Social Network Analysis网络图书馆Network Library整合性图书馆系统Integrated Library System图书馆联盟Library consortia复合图书馆Hybrid Library图书漂流Bookcrossing链接分析Link analysis信息伦理Information Ethics信息检索Information Retrieval信息安全Information Security信息构建Information Architecture捐赠政策Donation Policy图书馆学Library science图书Books期刊Journals/Periodicals报纸Newspapers百科全书Encyclopedia信息资源Information resources知识Knowledge道德规范ethics图书馆服务library service交叉学科interdisciplinary science美国图书馆运动American Library Movement图书馆学学术课程Academic courses in library science 采集管理Collection management信息系统技术Information systems and technology编目分类Cataloging and Classification保藏Preservation参考咨询Reference统计管理Statistics and management数据库管理Database management情报建设Information architecture知识管理Knowledge Management图书馆学分支学科Subdisciplines in library science人类情报行为Human Information Behaviors知识组织Knowledge Organization数字图书馆Digital libraries采集开发Collection development个人信息管理Personal information management(PIM)保存Preservation公共参考咨询Public reference and other services学术交流Scholarly communication信息计量学informetrics科学计量学scientometrics图书馆职位类型Types of library science professionals图书管理员Librarian档案保管员Archivist编目员Cataloger图书馆馆长Curator编索引员Indexers文摘员Abstractors研究员Researchers信息设计师Information architect信息代理商Information broker元数据设计师Metadata Architects元数据经理Metadata Managers保护员Conservators图书馆相关刊物Current issues in LIS图书馆员教育Education for librarianshipInformation policy信息交流技术Information communication technologies (ICT's) Information Society阅览公平Equity of AccessSustainability and ICT's儿童互联网保护法规Children's Internet Protection Act审查制度Censorship信息爆炸Information explosion信息扫盲Information literacy政府信息Government Information复制权Copyright知识产权Intellectual property rights知识自由Intellectual freedom数字分水岭Digital divide开架阅览Open accessPatriot Act公共借阅权Public lending rightSerials crisisCurrent digital/scanning technologies远程存取Remote access数字图书馆Digital libraries信息检索系统information retrieval system电子信息系统Electronic Information System数字格式digital formats数字参考文献Digital Reference计算机获取accessible by computers电子图书馆electronic library电子书eBooks虚拟图书馆virtual library有声读物audiobooks原生数字born-digital数字化digitizing物理收藏physical collections数字收藏digital collections美国记忆American Memory数字档案Internet Archive电子出版ePrint电子书目ibiblio珀尔修斯项目Project Perseus古藤堡项目Project Gutenbergsearch engines元数据Metadata牛津文本档案馆Oxford Text Archive光学符号识别optical character recognition深度链接资源deep web resources/invisible web搜索引擎蜘蛛search engine crawlersOAI-PMH协议Open Archives Initiative Protocol for Metadata Harvesting (OAI-PMH) Z39.50协议Z39.50网络计量学Webmetrics情报学(信息学)Information science/Informatics迭代过程iterative design processes美国医学图书馆National Library of MedicineDialogCompuserve特殊利益团体Special interest groupsPaul OtletHenri La Fontaine文献计量学Bibliometrics影响因子Journal Impact Factor重要度Importance Scale网页Rank值PageRank数据建模Data modeling数据模型理论data model theory数据模型实例data model instance数据库模型database model非结构化数据unstructured data文档管理Document management电子档案electronic documents电子图像electronic images群件Groupware社交软件Social softwareonline dating services社交网Social networksFriendster计算机支持协作computer-supported collaboration人机交互Human-computer interactionMan-machine interaction (MMI)Computer-human interaction (CHI)用户界面User interface情报建设Information architecture结构化信息structuring information用户体验设计user experience design信息系统设计information system design易用性usability信息伦理Information ethics隐私Privacy信息生命周期life-cycle of information所有权ownership安全security获取access公众community信息检索Information retrieval信息过载information overload单机数据库stand-alone databases超文本数据库hypertextually-networked databases数据检索data retrieval文档检索document retrieval文本检索text retrieval信息社会Information society知识经济knowledge economy后工业化社会post-industrial society知识社会knowledge society网络社会network society知识管理Knowledge management知识工程Knowledge engineering个人信息管理Personal Information Management语义网Semantic web网页内容web content自然语言natural language软件代理software agentsTim Berners-Lee资源描述框架Resource Description Framework (RDF)数据交换格式data interchange formats网页本体语言Web Ontology Language (OWL)用户为中心设计User-centered design可扩展标记语言XMLW3C标记语言markup language标准标记语言Standard Generalized Markup Language (SGML) RSSMathMLGraphMLXHTML可升级向量制图法Scalable Vector GraphicsMusicXML。
conductor+NT6.0安装、组态、维护

输入组号(1~50),每个组中最多可以有30个结点。当选择“Isolated Console Group”时,不要使用组号1。
选择“IsolatedConsoleGroup”。如果项目中使用冗余Server配置则不需要选择此项。
选择安装目录为D:\ABB、D:\Conductor NT和D:\ICI。
关于报警和管理
报警:
10000个事件报警的汇总画面
最小报警显示窗口
报警打印
多种声调调节
多种颜色表示优先级
用户图形中动态显示控制报警
由报警组表示外部的报警输出
报警管理中的操作员响应
在最小报警窗:按矢量键进入系统中任意的画面。
用户图形画面:点击弹出面板
报警汇总画面:点矢量键进入系统中任意的画面
报警管理、报警汇总画面
•报警管理
通过先进的报警管理系统使操作人员能够对异常情况采取快速的响应,并帮助操作人员采取适当的措施处理报警,并减少不必要的报警发生。
•趋势和调整画面
趋势显示可以为分析过程目前的运行情况提供有利的历史数据,可显示各个不同过程时期的数据变化,或与其它变量的变化关系
ForeScout CounterACT SIEM Integration Module 产品说明书

HighlightsSee• Discover devices the instantthey connect to your networkwithout requiring agents• Profile and classify devices,users, applications andoperating systems• Continuously monitormanaged devices, includingcorporate, BYOD and IoTendpointsControl• Allow, deny or limit networkaccess based on deviceposture and security policies• Assess and remediatemalicious or high-riskendpoints as determined byyour SIEM product• Improve compliance withindustry mandates andregulationsOrchestrate• Receive contextualinformation from your SIEMproduct and pro-actively takeappropriate action• Automate common workflows,IT tasks and securityprocesses across systems• Leverage the integrationbetween ForeScout and yourSIEM product to provide real-time view of threats across theenterprise SIEM Integration ModuleImprove real-time visibility over managed and unmanaged devices while automating network access control and threat responseForeScout Integration with SIEMsForeScout CounterACT is a network security appliance that provides IT organizations with the unique ability to see devices, including non-traditional devices, the instantthey connect to the network. CounterACT provides policy-based control of these devices and works with ForeScout ControlFabric™ Architecture to orchestrate information sharing and automate operation among disparate security and IT management tools.The combination of using ForeScout CounterACT™ and a SIEM can result a significant increase in situational awareness and proactive risk reduction. Where most SIEM solutions offer situational awareness primarily through the collection of periodic log entries from many different products, they typically do not provide in-depth “real-time” endpoint data visibility. SIEMs are only as good as the information that is fed into them, and if the SIEM is not aware of all the network endpoints on a continuous basis, thenit is not able to produce an accurate security snapshot of your network. This “gap” in endpoint visibility exists in SIEMs without CounterACT. CounterACT discovers network endpoints, and feeds that data into the SIEM, closing the endpoint visibility gap in your situational awareness.By itself, a SIEM system doesn’t have any enforcement capabilities. Some SIEM systems are able to send commands to ForeScout CounterACT to automatically respond to endpoint security issues. For example: update the operating system, disable USB devices, or quarantine the endpoints.The ChallengesVisibility. Any serious attempt to manage security risk must start with knowledge of who and what is on your network, including visibility to whether the devices on your network are compliant with your security standards. Most organizations are unaware of a significant percentage of the endpoints on their network because they are either not managed (BYOD, guest and IoT), have disabled or broken agents, or aren’t detected by periodic scans (transient devices). As such, you are unaware of the attack surface on these devices. According to industry experts, a vast majority of successful attacks exploit well-known vulnerabilities and security gaps on endpoints connected to your network. Threat Detection. T oday’s cyber attacks are more sophisticated than ever. Multi-vectored, stealthy and targeted threats easily evade traditional security defenses such as firewalls, intrusion prevention systems, anti-virus platforms, and secure web and email gateways. Originating from highly motivated and well-funded threat actors and nation states, these attacks are focused on acquiring sensitive personal information, intellectual property or insider information. As the attackers have gained the upper hand, organizations are being compromised at an accelerating rate. In order to effectively detect and block these sophisticated threats, new security controls that do not rely on signatures are needed.Response Automation. The velocity and evasiveness of today’s targeted attacks, coupled with increasing network complexity, mobility and BYOD, are creating a perfect storm for any incident response program. Without an automated system to monitor, install, update and reactivate security agents on managed systems, valuable time islost performing these tasks manually. Without the ability to apply security controls to unmanaged endpoints (BYOD, guest and IoT), you are increasing your attack surface and putting your infrastructure at risk. And without a system to automatically and quickly respond to attacks and security breaches, you are leaving the window open for cyber threats to propagate within your network and exfiltrate data.How it Works When CounterACT discovers infected endpoints, it can receive instructions from the SIEM and automatically take policy-based mitigation actions to contain and respond to the threat. Various actions can be performed depending on the severity or priority of the threat, such as quarantine endpoints, initiate direct remediation, share real-time context with other incident response systems, initiate a scan by another third party product, or notify the end user via email or SMS.ForeScout T echnologies, Inc. 900 E. Hamilton Avenue #300 Campbell, CA 95008 USA Toll-Free (US) 1-866-377-8771 Tel (Intl) +1-408-213-3191 Support 1-708-237-6591 Fax 1-408-371-2284Learn more at Copyright © 2016. All rights reserved. ForeScout T echnologies, Inc. is a privately held Delaware corporation. ForeScout, the ForeScout logo, ControlFabric, CounterACT Edge, ActiveResponse and CounterACT are trademarks or registered trademarks of ForeScout. Other names mentioned may be trademarks of their respective owners. Version 3_16Device connects to thenetwork.CounterACT informs SIEMsystem of device status.CounterACT receivesinstruction from SIEMassessment of device based on events and logs collected.CounterACT allows or deniesaccess based on compliance assessment.1234Supported SIEMs SIEMs that are supported by the ForeScout SIEM Integration Modules are:• ArcSight • IBM QRadar • Any SIEM that supports configurable messages in CEF, LEEF or plain Syslog Note that different SIEM products have different capabilities in terms of correlating the data provided by CounterACT with data that it obtains from other sources. Also, SIEM products vary in their ability to send triggers to CounterACT; some SIEM products provide both manual and automated ways to trigger CounterACT to take action on an endpoint. For a more complete description of the features available with each specific SIEM product, talk with your SIEM vendor or read the joint solution briefs at /solutions/siem . For details on our licensing policy, see /licensing .1Connect Allow Redirect Scan &Assess 234Figure 1: ForeScout CounterACT and your SIEM system work in concert to assess and manage devices as they access the network.。
Part4_思科配置专家CCP_路由器配置工具介绍

Firewall
IPS
Advanced configuration
Routing
© 2008 Cisco Systems, Inc. All rights reserved.
PDF created with pdfFactory trial version
Presentation_ID
Cisco Confidential
2
Why CCP?
§ Lower Total Cost of Ownership
Productivity: Up and running in under 30 minutes Simplicity: Configurations completed without touching CLI Cost Savings: Lower VAR skill requirements Reliability: CCP uses Cisco TAC approved configurations Increased Uptime: Easy-to-comprehend charts for troubleshooting & real-time monitoring
§ CCP 1.1
Content Filtering Voice –CUCME and CUE Platforms supported –85x, 86x, 87x, 88x, 18xx, 28xx, 38xx, 72xx
Free Download: /go/ciscocp Feedback for CCP: ccp-feedback@
Cisco Configuration Professional
PDF created with pdfFactory trial version
BigFix安装指导手册

1. 概述BigFix 企业管理套件是BigFix 公司研发的业界领先的企业级系统安全配置管理软件——可以为不同规模的企业提供可升级的,灵活的,强大的安全平台和分布式处理模型,实现统一的企业级系统管理、配置管理和安全管理,从根本上改变企业计算机网络的管理模式,降低IT管理成本。
BigFix定位于:Ø为企业计算机类资产提供全面实时的可视化安全和配置管理。
Ø通过提高基础平台的可靠性、可视性和可控性,在降低运行费用的同时提供更稳定的服务。
Ø满足补丁管理和安全配置的服务等级要求。
无论计算机系统何时何地,以何种方式接入网络,都可以通过BigFix 企业管理套件实现全面、快速、高效、安全,可控的管理,全面提升企业IT治理水平。
目前我们使用的是BES6.0.8.5中文版本。
2. 操作方法:2.1. 安装安装Bigfix包括服务器安装、控制台安装和客户端安装。
运行BES中文版安装文件,解压缩后可在C:\BESInstallers目录下生成服务器、控制台和客户端的安装程序包。
可将这些安装文件包分别拷贝到需要安装的计算机上,然后运行安装程序,完成服务器、控制台和客户端的安装。
2.1.1. BESServer的安装运行Bigfix安装程序。
对于测试使用,可选择评估版(可管理30各客户端,30天有效期)进行安装:选择要安装的站点:选择服务器IP地址和端口号:创建管理员帐号:选择证书文件的存放位置:设置完成后,开始安装BES组件:选择安装BESServer开始安装:如果SQLServer数据库安装在本机上,选择本地数据库。
初始化数据库需要验证管理员密码,选择前面添加的管理员证书和秘密:根据提示进行操作,安装完成后,继续完成Console和Client的安装。
对于Bigfix运行网络和Internet隔离的情况,需要使用Bigfix公司提供的工具MakeMirrorArchive.exe来完成所有订阅的Fixlet的内容。
云网一体化网络架构设计指南

技术创新,变革未来
云网一体化逻辑分层架构示意图
2
VMM
云管Fu理sio平nS台phere
OpenStack
1
FabricInsight
iMaster NCE-Fabric
SecoManager
业务呈现/ 协同层
网络分析/ 控制层
3
4
Spine
7Байду номын сангаас
Firewall
VXLAN
出 口
核 心 互 联
互 联 网
出 口
业
业
务
务
区
区
区
DMZ 2 1
VDC设计规划示意图
VXLAN
vFW
VDC 1
vLB
VM
vSwitch
vRouter
VM
vFW
VDC 2
vLB
VM
vSwitch
vRouter
VM
租户管理员设计VPC网络示意图
VDC
VPC 1
vRouter
Subnet
VM
vFW vLB Subnet VM
Fabric
2.1 租户发放EIP/ SNAT业务
2.2 控制器插件根据EIP/ SNAT所在的 subnet查找对应Internet 外部网络,控 制器 根据外 部网络 名称查 找对应 外部网
关
2.3 控制器调用SecoManager接口,下发EIP对 应的NAT和路由配置到防火墙和Service Leaf
2.3 控制器下发路由配置到防火 墙和Service Leaf
云网DHCP组件控制面架构图
Neutron Server
政策科学复习

一、名词解释(4分,16分)英文两个:1.policy science:multidisciplinary,problem-solving,explicitly normative.2.Policy analysis: the disciplined application of intellect to publicproblems.3.Policy cycle:”stage heuristic”,is a political process through which mostpublic policies pass over the course of their lifetime. Is often viewed as a “vonveyor belt”.4.Kuhn’s Scientific Revolution:As the natural sciences progressed,theyamassed(积累,收集) a body of ever-changing theory.Scientific advances were not based on the accumulation of knowledge and facts,but rather on a dominant paradigm used in any specific period to explain the phenomena under study.Rather than refuting previous theories,each paradigm would build upon the body of relevant knowledge and theories.Once a paradigm was accepted by consensus among current scholars,it would last as long as it remained useful.Ultimately it would be displaced by a more relevant and useful paradigm,this process of replacement was Kuhn’s Specific Revolution.5.Policy universe:Afundamental unit containing all possibleinternational state,social actors and institutions directly or indirectly affecting a specific policy area.6.Policy subsystem:A space where relevant actors discuss policy issuesand persuade and bargain in pursuit of their interests.7.Counteracting:growth in the size,scope and complexity ofgovernment functions over the years prevents generalist politicians from controlling.8.Prime mover(发起者,原动力) in the policy respone:problemstructuring is a central guidance system or steering mechanism that affects the success of all subsequent phases of policy analysis…policy analysts…fail more often because they solve the wrong problem than because they get the wrong solutions to the right problem.9.Problem:substantial discrepancy between what is and what shouldbe.10.P roblem Recognition:According to Kingdon 1995,problem recognitionis often stimulated by widely agreed-upon indicators and routine monitoring that turns up discrepancies or patterns that hint that something is amiss(出了差错的).11.P olicy images:a mixture of empirical information and emotiveappeals that explain the issue and justify the public policy respone. 12.A ttention Cycle:explain how policy problems evolve on the politicalagenda by Downs.Public attention rarely remains focused to any one issue.13.P unctuated Equilibrium(间断平衡):convey a process thatsimultaneously combines ong stable periods of policy consensus followed by bursts of change around new issues and new policyimages.14.I ncrementalism(渐进主义):seem to describe most budgetarydecision-making in Western democracies,less useful when encounter some considerable shock:a war,crisis.15.P olicy design:the process of organizing and delivering outcomesthrough the chosen policy instruments.16.P olicy tool or instrument:an identifiable method through whichcollective action is structured to address a public problem.17.P olicy implementation:implementation is the process of putting agovernment program into effect;it is the total process of translating a legal mandate(授权),whether an executive order an enacted statute(法规),into appropriate program directives and structures that provide services or create goods.18.P olicy evaluation:policy evaluation refers broadly to the stage of thepolicy process at which it is determined how a public policy has actually fared in action.It involves the means being employed and the objectives being served.中文两个:1.什么是政策过程?从政治系统论看,政策过程指政策主体、政策客体以及政策环境之间相互联系和相互作用,政策系统呈现的动态运行过程;从政策过程的是只看,政策过程实质上是一种政治过程。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Open Policy Network As of 2 April 2013. Open Policy Network: Ensuring open access to publicly funded resources Contents [hide] 1 Overview
2 Description and rationale
3 Mission
4 Guiding principles
5 Operational Work Plan
6 Governance
7 Work Product: OPN services and resources
8 Funding
9 Roadmap
Overview In 2011-2012, Creative Commons (CC) and other open organizations were contacted by multiple institutions and governments seeking assistance to develop materials and strategies for open policies. The need for open policy support was amplified at the CC 2011 Global Summit in Warsaw, Poland. CC Affiliates from 35 countries called for a central hub where open policies could be shared and discussed. They were clear: without clearly defined support, open policies are significantly less likely to be introduced and adopted. In October 2012 Creative Commons continued this exploration by convening a meeting of “open” leaders to brainstorm possibilities and challenges in developing resources and services to increase open policies.
As open advocates, organizations and policy makers recognize the potential for open policies to significantly increase the amount and quality of publicly funded education, research, data, and software, there is a pressing need to provide them support so they can successfully create, adopt and implement open policies. Open policies promote open licensing of resources financed through public funding in order to maximize the impact of the investment.
Open Policy = publicly funded resources are openly licensed resources.
If we are going to unleash the power of hundreds of billions of dollars of publicly funded education, research, data, and software, we need broad adoption of open policies. For the purposes of open policies that contribute to the public good, we define policy broadly as legislation, institutional policies, and/or funder mandates.
We have observed that current open policy efforts are decentralized, uncoordinated and insular; there is poor and/or sporadic information sharing. There are at least two major barriers that have prevented broad open policy adoption. (1) There is limited support for open policy advocates, organizations and policy makers who want to create, adopt and implement open policies. (2) Existing policy makers need help in articulating and messaging how open policies can increase the impact of public investments.
The open community needs access to existing open policies, legislation, and action plans for how open policies were created, discussed and passed. Advocates need to know what barriers were encountered and how they were overcome, and because politics and opportunities are local, open advocates may need support customizing an open policy solution and strategy.
If we get this simple idea right, open sustainability could cease to be an issue because: (a) there is plenty of public funding to build and maintain all of the education, research, data, and software the world needs, and (b) “open” becomes the default and “closed” becomes the exception for publicly funded resources.
翻译结果: 双语对照查看 开放的政策网络 在四月2日2013。 开放的网络:确保开放获取政府资助的资源 内容 [隐藏] 1概述 2描述和理由 3个任务 4指导原则 5工作计划 6治理 7工作产品:OPN服务和资源 8资金 9路线图 概述 在2011-2012年,Creative Commons(CC)和其他开放组织进行联系,由多个机构和政府寻求援助开发开放政策的材料和策略。开放的政策支持的需要在CC 2011全球峰会在华沙扩增,波兰。CC公司来自35个国家呼吁中央枢纽,开放的政策可以分享和讨论。他们很清楚:没有明确的支持,开放的政策是不太可能被引入。2012十月,Creative Commons继续探索召开“开放”的领导人,在资源开发和服务来增加开放头脑风暴的可能性和挑战的会议。
作为开放的主张,组织和政策制定者认识到潜在的开放政策大大增加的数量和质量的公共教育,研究,数据,和软件,有向他们提供的支持,他们可以成功地创建了一个迫切的需要,采用和实施开放政策。开放政策促进融资通过公共资金最大化投资的影响资源的开放式许可。
开放政策的公共资助的资源开放许可的资源。 如果我们要释放的公立教育,数千亿美元的电力研究,数据,和软件,我们需要广泛采用开放政策。开放的政策,有助于公共利益的目的,我们定义政策的广泛的立法,政策,和/或在任务。
我们观察到,目前开放的政策力度是分散的,不协调的和狭隘的;有不良和/或零星信息共享。至少有两个主要的障碍,阻碍了广泛的开放政策选择。(1)有开放的政策主张有限的支持,组织和政策制定者想要创建,采用和实施开放政策。(2)现有的政策制定者需要帮助的阐明和消息如何开放的政策可以增加公共投资的影响。
开放的社会需要访问现有的开放政策,立法,和行动计划,如何创建开放政策,讨论通过。倡导者需要知道什么障碍以及他们是如何克服遇到的,因为政治和机会的地方,公开主张可能需要支持定制的开放政策和战略的解决方案。
如果我们把这个简单的想法是,开放的可持续性将不再是一个问题,因为:(一)有公共基金来建立和维护所有的教育,研究,数据丰富,和软件的世界需要,和(b)的“开放”和“封闭”成为默认为公共资助资源异常
Description and rationale Open policies promote access to, and open licensing of, resources financed through public funding. Open policies can maximize the impact of public investments in science, data, education, libraries,
