Exception handling in workflow systems
BIEE_常见问题解答

Oracle Business Intelligence Enterprise Edition 10g项目实施问题解答汇总2008年4月10日目录:仪表板: (4)仪表板分组下拉显示: (4)设置默认的仪表板: (7)撤销页面“刷新“按钮(不建议) (8)如何跳过注销页面,直接跳转到登陆界面 (9)交叉表行数限制 (9)报表显示上的列级别控制 (10)报表中现实自己有权限访问的第一个列 (10)登录界面“版权所有“信息客户化 (10)仪表盘顺序定制 (10)时间细度不一样 (11)Prompt值显示的顺序定制: (11)表格下的“125-”是1到25条记录的显示方式,需要改成“1-25”(附图) (11)查询大数量时,出现等待提示,可以在下面修改 (12)Dashboard中钻取返回提示修改: (12)友好打印PDF中的空格 (12)Answer中的主题文件夹层次现实: (13)Excel下载如果不自动变成科学计数法: (13)如何强制Answer中列的宽度 (13)个性化汇总查询: (14)在仪表板上加入当前client日期显示: (15)在Answer的Titel中加入变量显示: (15)客户化仪表盘右上角的产品清单,如去除等多产品中的Marketing (16)在仪表板制定位置显示Deliver的内容 (16)OBI EE and oracle stored procedures WITH parameter passing (16)如何将Go URL中的“页选项”按钮去除 (18)Configuration for the Dashboard Prompt Types Feature (19)图形: (21)中文显示方块问题 (21)BIEE中雷达图中文显示问题: (21)图形鼠标点到的地方的值的背景希望是透明的: (21)BIPublisher Chart Description (21)图形出现“Evaluation Time Limit“ (22)指定BIEE中图形的类型(flash,SVG,PNG) (22)图形中“上”字,“名”字和“作”字的链接错误 (22)配置和服务 (24)几处配置文件的作用优先级别 (24)禁止OC4J自动启动 (24)如何在Office 2003中启用BIEE Excel Add-in (24)BIP (25)BI Publisher 和Oracle BI Server 的安全集成 (25)报表复制 (27)RDF to RTF Template Generator (27)RDF to Data Template Generator (27)其他 (27)修改BIEE中的用户密码 (27)BIEE和其他应用集成,如果出现频繁登录提示: (32)Metadata report (32)Oracle BIEE性能提高 (33)使用BIP和iBot中的外部认证 (33)BIEE 10.1.3.2中ibot的配置: (34)其他Web程序调用BIEE的报表方式: (34)其他Web程序调用BIEE的仪表板方式: (35)Customizing OBI EE – GO URL Parameters (36)从BIEE的报表链接到其他系统: (39)Writeback for dashboard commentary in OBI EE (40)Siebel Analytics Web Catalog 升级到Oracle BIEE Presentation Catalog (46)How To Log An Oracle Support Service Request Via SupportWeb for Oracle BusinessIntelligence Enterprise Edition (OBIEE) (49)Applies to: (49)Goal (49)Create SR for BIEE from metalink: (51)仪表板:仪表板分组下拉显示:1.配置instanceconfig.xml,加入<DahboardMaxBeforeMenu>的配置,然后重启BI presentation server.数字3表示,当一个组的仪表板数量大于等于3时,会将仪表板分组下拉显示。
人简 历 吴维刚 - z 个人信息
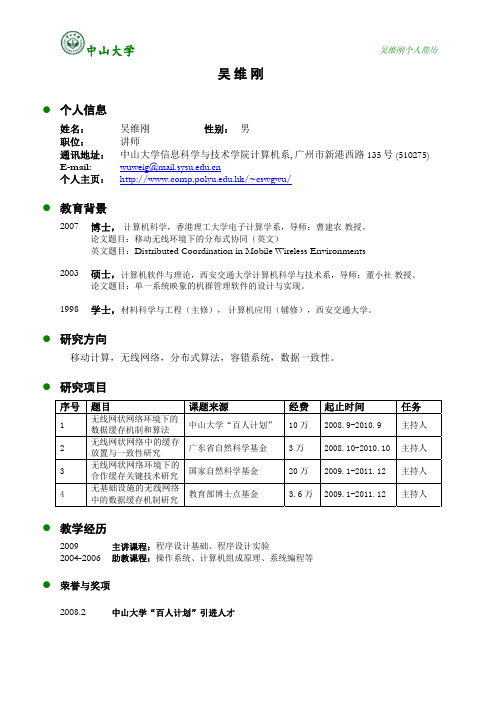
吴维刚z个人信息姓名:吴维刚性别:男职位:讲师通讯地址:中山大学信息科学与技术学院计算机系, 广州市新港西路135号 (510275) E-mail: wuweig@个人主页:.hk/~cswgwu/z教育背景2007 博士,计算机科学,香港理工大学电子计算学系,导师:曹建农教授。
论文题目:移动无线环境下的分布式协同(英文)英文题目:Distributed Coordination in Mobile Wireless Environments2003 硕士,计算机软件与理论,西安交通大学计算机科学与技术系,导师:董小社教授。
论文题目:单一系统映象的机群管理软件的设计与实现。
1998 学士,材料科学与工程(主修),计算机应用(辅修),西安交通大学。
z研究方向移动计算,无线网络,分布式算法,容错系统,数据一致性。
z研究项目序号题目课题来源经费起止时间任务1 无线网状网络环境下的数据缓存机制和算法中山大学“百人计划” 10万 2008.9-2010.9 主持人2 无线网状网络中的缓存放置与一致性研究广东省自然科学基金 3万 2008.10-2010.10 主持人3 无线网状网络环境下的合作缓存关键技术研究国家自然科学基金 20万 2009.1-2011.12 主持人4 无基础设施的无线网络中的数据缓存机制研究教育部博士点基金 3.6万2009.1-2011.12 主持人z教学经历2009主讲课程:程序设计基础、程序设计实验2004-2006 助教课程:操作系统、计算机组成原理、系统编程等z荣誉与奖项2008.2 中山大学“百人计划”引进人才z学术活动国际会议TPCEUC’09, EUC’08, ICCCN’08, NIMC’08, CODS’07, MSN’07论文评审期刊IEEE TC, IEEE TMC, JPDC, PMC会议ICDCS’08, MDM’08, ICPP’08, ICC’08DSN’07, PerCom’07, ICC’07, CCGrid07, AINA’07;ICDCS’06, PerCom’06, IPDPS’06;DSN’05, SRDS’05, ICCCN’05, Globecom’05.会议组织2005The 6th Int’l Workshop on Advanced Parallel Processing Technologies (APPT'05)2004The 2nd Int’l Symposium on Parallel and Distributed Processing and Applications (ISPA'04)z学术论文期刊论文:1.Weigang Wu, Jiannong Cao, Michel Raynal, Eventual Clusterer: a Modular Approach to DesigningHierarchical Consensus Protocols in MANETs, IEEE Transactions on Parallel and DistributedSystems (TPDS), 20(6), pp. 753-765, June 20092.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, Efficient Algorithms for Fault TolerantMobile Agent Execution, International Journal of High Performance Computing andNetworking(IJHPCN), 6(2), pp. 106-118, 20093.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, Using Asynchrony and Zero Degradation toSpeed up Indulgent Consensus Protocols, Journal of Parallel and Distributed Computing (JPDC),Elsevier, 68(7), Jul. 2008, pp. 984-996.4.Jin Yang, Jiannong Cao, Weigang Wu, Efficient Global Checkpointing Algorithms for MobileAgents, Concurrency and Computation: Practice and Experience, John Wiley & Sons, 20(7), May.2008, pp. 825-838.5.Weigang Wu, Jiannong Cao, Jin Yang, A Fault Tolerant Mutual Exclusion Algorithm for Mobile AdHoc Networks, Pervasive and Mobile Computing (PMC), Elsevier, 4(1), February 2008, pp. 139-160.6.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, Design and Performance Evaluation ofEfficient Consensus Protocols for Mobile Ad Hoc Networks, IEEE Transactions on Computers (TC),56(8), Aug. 2007, pp. 1055-1070.会议论文:1.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Contention-Aware Data Caching in Wireless Multi-hopAd Hoc Networks, 6th IEEE International Conference on Mobile Ad-hoc and SensorSystems(MASS’09), October 12 - 15, 2009, Macau2.Weigang Wu, Jiannon Cao, Xiaopeng Fan, Overhearing-aided Data Caching in Wireless Ad HocNetworks, 6th IEEE ICDCS International Workshop on Wireless Ad hoc and SensorNetworks (WWASN’09). June 22-26, 2009 Montreal, Canada3.Jiannong Cao, Kun Xie, Weigang Wu, Chuda Liu, et al., HAWK: Real-world Implementation ofHigh-performance Heterogeneous Wireless Network for Internet Access, 1st ICDCS International Workshop on Next Generation Network Architectures (NGNA’09), June 22-26, 2009Montreal, Canada.4.Ye Yan, Jiannong Cao, Chuda Liu, SeongWoo Kim, Weigang Wu, A Dual Re-authenticationScheme for Fast Handoff in IEEE 802.11 Wireless Mesh Networks, IEEE Wireless Communications and Networking Conference (WCNC’09), April 4 – 8, 2009. Budapest, Hungary.5.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Hui Cheng, Modeling Hierarchical Gossiping inReliable Multicast Protocols, Proc. The 2nd International Conference on Future Generation Communication and Networking(FGCN’08), December 2008, Sanya, Hainan Island, China.6.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Michel Raynal, On Modeling Fault Tolerance ofGossip-Based Reliable Multicast Protocols, Proc. of the 37th International Conference on Parallel Processing (ICPP’08), Portland, USA, Sep. 8 – 12 2008.7.Vaskar Raychoudhury, Jiannong Cao, Weigang Wu, Top K-leader Election in Wireless Ad HocNetworks, Proc. of the 17th International Conference on Computer Communication Networks (ICCCN'08), St. Thomas, US Virgin Islands, August 4-7, 2008.8.Jiannong Cao, Corentin Travers, Michel Raynal, Weigang Wu, The Eventual Leadership inDynamic Mobile Networking Environments, Proc. of the 13th IEEE Pacific Rim International Symposium on Dependable Computing (PRDC'07), Melbourne, Australia, December 17-19, 2007. 9.Weigang Wu, Jiannong Cao, Michel Raynal, A Dual-Token-based Fault Tolerant Mutual ExclusionAlgorithm for MANETs, Proc. of the 3rd International Conference on Mobile Ad-hoc and Sensor Networks (MSN’07), Beijing, China,12-14 December 2007.10.Weigang Wu, Jiannong Cao, Michel Raynal, The Eventual Clusterer Oracle and Its Application toConsensus in MANETs, Proc. of the 26th IEEE International Symposium on Reliable Distributed Systems (SRDS’07), Beijing China, Oct. 10-12, 2007.11.Jiannong Cao, Miaomiao Wang, Weigang Wu, Xianbing Wang, Stephen C.F. Chan, A GenericDistributed Monitor Construct for Programming Process Synchronization in Distributed Systems, Proc. of the5th International Symposium on Parallel and Distributed Processing and Applications (ISPA’07), Niagara Falls, Canada, Aug. 29-31, 200712.Jin Yang, Jiannong Cao, Weigang Wu, An Integrated Approach to Checkpointing in Mobile AgentSystems, Proc. of the 2nd International Conference on Semantics, Knowledge and Grid (SKG’06), Guilin, China, Nov. 1-3, 200613.Jin Yang, Jiannong Cao, Weigang Wu, Checkpoint Placement Algorithms for Mobile Agent System,Proc. of the5th International Conference on Grid and Cooperative Computing (GCC’06), Changsha, China, Oct. 21-23, 2006.14.Jiannong Cao, Michel Raynal, Xianbing Wang, Weigang Wu,The Power and Limit of AddingSynchronization Messages for Synchronous Agreement, Proc. of the 35th International Conference on Parallel Processing (ICPP’06), Columbus, USA, Aug. 14-18, 2006.15.Jin Yang, Jiannong Cao, Weigang Wu, Corentin Travers The Notification based Approach forImplementation Failure Detector, Proc. of the1st International Conference on Scalable Information System (InfoScale’06) , Hong Kong, May 29-Jun. 1, 2006.16.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, A Hierarchical Consensus Protocol forMobile Ad Hoc Networks, Proc. of the14th Euromicro Conference on Parallel, Distributed and Network based Processing (PDP’06), Montbéliard, France, Feb. 15~17, 2006.17.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, A Framework for Transactional MobileAgent Execution, Proc. of the4th International Conference on Grid and Cooperative Computing (GCC’05), Beijing, China, Nov. 30-Dec. 3, 2005.18.Jiannong Cao, Jin Yang, Weigang Wu, Chengzhong Xu, Exception Handling in DistributedWorkflow Systems Using Mobile Agents, Proc. of the IEEE International Conference on E-Business Engineering (ICEBE’05), Beijing, China, Oct. 18-20, 2005.19.Weigang Wu, Jiannong Cao, Jin Yang, A Scalable Mutual Exclusion Algorithm for Mobile Ad HocNetworks, Proc. of the14th International Conference on Computer Communications and Networks (ICCCN’05), San Diego, USA, Oct. 17-19, 2005.20.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, Parallel Algorithms for Fault-TolerantMobile Agent Execution, Proc. of the6th International Conference on Algorithms and Architectures(ICA3PP’05), Melbourne, Australia, Oct. 2-5, 2005.。
仓库工作流程 英文

仓库工作流程英文Warehouse WorkflowManaging a warehouse is a complex and multifaceted task that requires a well-organized and efficient workflow. Warehouse operations involve the coordination of various activities, from receiving goods to shipping them out, to ensure the smooth flow of inventory. In this essay, we will explore the key components of a warehouse workflow and how they contribute to the overall efficiency of the operation.Receiving Goods: The first step in the warehouse workflow is the receiving of goods. This process involves unloading and inspecting incoming shipments to ensure that the items match the order and are in good condition. Proper receiving procedures are crucial to maintaining accurate inventory records and identifying any discrepancies or damaged goods. Efficient receiving processes can help minimize delays and ensure that the warehouse is stocked with the necessary items to meet customer demands.Storage and Inventory Management: Once the goods have been received, they need to be stored in a systematic manner to facilitateeasy retrieval and organization. Warehouses often utilize various storage solutions, such as shelves, racks, or specialized storage systems, to maximize the use of available space. Effective inventory management practices, such as the use of barcodes or RFID technology, can help track the location and quantity of each item in the warehouse. This information is essential for maintaining accurate records, preventing stockouts, and ensuring that the right products are available when needed.Order Picking and Fulfillment: When a customer places an order, the warehouse must efficiently locate and retrieve the requested items. This process, known as order picking, is a critical component of the warehouse workflow. Warehouse staff may use manual methods, such as walking through the aisles and collecting the items, or utilize technology-based solutions, such as automated picking systems or pick-to-light systems, to streamline the process. Efficient order picking not only enhances customer satisfaction by ensuring timely deliveries but also reduces the risk of order errors.Packing and Shipping: After the items have been picked, they need to be properly packed and prepared for shipment. This may involve activities such as weighing the packages, applying shipping labels, and ensuring that fragile or perishable items are handled with care. Effective packing and shipping processes help minimize damage during transit and ensure that the goods arrive at the customer'slocation in good condition.Documentation and Reporting: Alongside the physical handling of goods, the warehouse workflow also involves extensive documentation and reporting. This includes maintaining accurate records of all incoming and outgoing shipments, tracking inventory levels, and generating reports for management and external stakeholders. Proper documentation and reporting help ensure compliance with industry regulations, support decision-making, and provide valuable insights into the warehouse's performance.Technology Integration: In modern warehouses, the integration of technology has become increasingly important to enhance workflow efficiency. Automation, such as the use of robotic systems or conveyor belts, can streamline material handling and reduce the risk of human error. Additionally, warehouse management systems (WMS) and other software solutions can help manage inventory, optimize picking and packing processes, and provide real-time data on warehouse operations.Continuous Improvement: Maintaining an efficient warehouse workflow requires ongoing efforts to identify and address areas for improvement. This may involve implementing lean manufacturing principles, conducting regular audits, and seeking feedback from warehouse staff and customers. By continuously evaluating andrefining the warehouse workflow, organizations can adapt to changing business needs, improve overall productivity, and deliver a superior customer experience.In conclusion, the warehouse workflow is a complex but essential component of an effective supply chain. By focusing on the key elements of receiving, storage, order fulfillment, packing, and documentation, while leveraging technology and continuously improving processes, organizations can create a well-organized and efficient warehouse operation that supports their business goals and meets the demands of their customers.。
简述机器人搬运工作站的主要工作流程

英文回答:Workstation robotic processes include three important steps:material receipt, handling and material placement。
Once the material arrives at the workstation, the robot can sense and identify through the sensor。
On the basis of pre—set removal paths and destinations, robots will plan the best removal routes and movements。
During handling, robots are able to accurately capture and hold materials to ensure accuracy and stability of handling。
The robots place the material at their destination andplete the handling in preparation for the next round of work。
工作站机器人的操作流程包括物料接收、搬运操作和物料放置三个重要步骤。
一旦物料到达工作站,机器人即可通过传感器感知并进行识别和确认。
依据预设的搬运路径和目的地,机器人将规划最佳的搬运路线和动作。
在搬运过程中,机器人能够准确地抓取和托举物料,确保搬运的准确性和稳定性。
机器人将物料放置到目的地,并完成搬运操作,为下一轮工作做好准备。
In logistics processing, robots have to see the materialing through the camera and rely on sensors to detect the material。
Work coordination, workflow, and workarounds in a medical context

Work Coordination, Workflow, and Workarounds in aMedical ContextMarina Kobayashi, Susan R. Fussell Human Computer Interaction Institute Carnegie Mellon University5000 Forbes AvenuePittsburgh, PA 15213 USA {marinak, sfussell}@Yan Xiao, F. Jacob Seagull Human Factors & Technology Research University of Maryland School of MedicineBaltimore, MD USA{yxiao, jseag001}@ABSTRACTIn this paper we report an ethnographic study of workarounds—informal temporary practices for handling exceptions to normal workflow—in a hospital environment. Workarounds are a common technique for dealing with the inherent uncertainty of dynamic work environments. Workarounds can help coordinate work, especially under conditions of high time pressure, but they may result in information or work protocols that are unstable, unavailable, or unreliable. We investigated workarounds and their effects through observation and interviews in a major teaching medical center. Our results suggest 4 key features of workarounds that technologies might help address: (a) workarounds differ as a function of people’s role; (b) workarounds draw on tacit knowledge of others’ abilities and willingness to help; (c) workarounds can have a cascading effect, causing other workarounds down the line; (d) workarounds often rely on principles of fairness and who owes whom a favor. We provide recommendations for designing systems to better support workarounds in dynamic environments.Author KeywordsWorkarounds, problem-solving, breakdowns, modeling, workflow, coordination, social cognition, awareness, transactive memory, computer-supported collaborative work, CSCWACM Classification KeywordsH.5.3 Group and Organization Interfaces - Computer-supported cooperative work, Evaluation/methodology, Synchronous interaction, Theory and models INTRODUCTIONProviding safe, timely, assistance to medical patients requires optimal coordination of staff, resources, equipment, schedules, and tasks. In operating room (OR) suites, this is a difficult task because the workload is constantly changing. The arrival of new cases and changes in the criticalness of existing cases often necessitates last-minute juggling of OR and personnel schedules. To cope with the unexpected events that arise in these complex, dynamic conditions, medical personnel formulate workarounds—informal temporary practices for handling exceptions to normal workflow. For example, if an emergent case comes in when all the operating rooms are booked, the staff might perform the operation in the Trauma Resuscitation Unit, which is actually an admitting area. Although workarounds are common in medical settings [e.g., [1], [7]], little research has attempted to characterize properties of workarounds that might influence their effectiveness. By describing short-term benefits of workarounds (providing temporary fixes to potentially life-threatening problems), investigators may overlook longer-term differences in how workarounds impact a medical organization. Successful workarounds can provide organizational solutions for exceptions that recur, thereby reducing the cognitive effort required to deal with each new emergency. Unsuccessful workarounds, however, may lead to widespread instability in an organization. A deeper understanding of what features lead to successful versus unsuccessful workarounds can help us design tools to facilitate the handling of exceptions.In this paper, we use ethnographic and modeling techniques to identify how and where workarounds occur in a university trauma surgical suite. We first discuss related research on coordination of medical work. We then describe data we collected in a shock trauma center. We use workflow modeling to characterize the dimensions of work coordination activity in a shock trauma center. Based on the workarounds we found in this setting, we propose several design guidelines for new technology to assist medical personnel in their handling of workflow breakdowns. PREVIOUS RESEARCHA number of previous investigators have studied how medical workers coordinate their activities in time-critical contexts such as the OR [e.g., [1], [4], [8]]. Several lines ofCopyright is held by the author/owner(s).CHI 2005, April 2–7, 2005, Portland, Oregon, USA. ACM 1-59593-002-7/05/0004.research provide insights into the nature of workarounds in medical settings.First, dynamic artifacts, such as the large whiteboards used to display OR status, have been shown to play an important role in the moment-to-moment coordination of medical work by helping workers keep abreast of ongoing exceptions and problems [e.g., [1], [5], [8]]. However, many key artifacts leave no lasting body of knowledge. As a result, there is a lack of organizational memory for workarounds and their effectiveness.Second, despite the omnipresence of cognitive artifacts in the OR, much coordination takes place informally, through conversational and observation, rather than through information systems [e.g., [6], [8]]. Charge nurses and anesthesiologists balance the effort required to gather information against the value of accurate information by performing optimal sampling. [[9]]. This suggests that in many cases, workarounds are devised under situations of incomplete information.Third, there are limitations in how quickly information is distributed across different hospital locations, even when it is formally embedded in information systems [[3]]. Again, this suggests that workarounds may be performed without full access to the pertinent information.Fourth, problems in the specification of workflow patterns and the extent to which workflows can handle exceptions also have implications for the types of workarounds devised by personnel and the success of these workarounds [[3]]. For example, static assignments of personnel to roles can create problems when extra help is needed in an emergency. Finally, observational research on nurses’ problem-solving strategies indicates that in the majority of cases, they deal only with the immediate problem rather than addressing its source [[7]]. Attempts to alter the system in order to deal with the root cause occur much more rarely. This suggests that medical organizations have problems developing lasting solutions to workflow breakdowns.CURRENT STUDYThe present study builds on previous work by looking more closely at workarounds and their effects in medical collaboration. We use a combination of observational and interview methods to collect data on hospital workers’ coordination activities and use modeling techniques to illustrate the types of workarounds that occur in this setting. Our overall goals are to (a) develop a framework within which we can characterize different types of workarounds and analyze their short- and long-term effects (b) propose new technologies that take advantage of the characteristics of successful workarounds. Although we perform our analysis within the context of medical collaborations, our aim is to create a general framework that will generalize to the study of other large, complex organizations.METHODResearch ContextOur research was conducted in a six-room shock trauma center (STC) in which several units coordinate admissions, resuscitations, operations, and recovery. Work in the center is characteristically unpredictable, with fluctuations in load and cases coming in unexpectedly. Personnel frequently encounter situations in which they have little room for error, very little time to react, and insufficient information about how best to provide care. Surgeons, anesthesiologists, technicians, and nurses make frequent use of workarounds to optimize outcomes given these conditions.Data Collection and AnalysisOur data consists of approximately 120 hours of observations, interviews, and focus group discussion. Observations began at the hand-off time from night to day shift, in order to capture the period of peak coordination activities, and continued for the remainder of the shift. Interviews and focus groups were audio recorded and transcribed. Participants consisted of shock trauma center employees who were performing the targeted roles of charge nurse, charge anesthesiologist, and surgeons in different services (e.g. orthopedics, neurology).We drew upon user modeling techniques to identify breakdowns and workarounds in the workflow. User modeling provides a “graphical language to capture knowledge about work” and abstracts the context into focused models [[2], p. 84]. Workflow modeling uses symbols that represent the key information flow, repositories, users and roles. For example, a breakdown symbol can represent problems with communication orcoordination.Figure 1. Workaround symbol Recognizing the mechanism of workarounds and evaluating their reliability and successfulness can be made easier by including them in the modeling process. For this reason, we propose a new representation symbol for workarounds (Figure 1). The explicit modeling of workarounds helps clarify relationships between breakdowns, or potential breakdowns, and the types of solutions people attempt. It also makes the translation from workarounds to institutional practices more straightforward.Figure 2. Workflow Model of OR on 3 August 2004. Red thunderbolts represent breakdownsin the system; yellow triangles represent workarounds. (Note: CN-Charge Nurse, CRNA-Certified Registered NurseAnesthetist)RESULTSFigure 2 represents how work was distributed among people, places and things during the observed time period and how participants coordinated to accomplish their collective tasks. Breakdowns in this model represent problems in communication or coordination.Workarounds represent alternative ways to support workflow when events prevent the normal functioning of the system (e.g., obtaining substitutes, borrowing resources). From this model and our analysis of interview transcripts, we identified four key characteristics of workarounds: Workarounds differ as a function of people’s roles Depending on what role a person is acting in, they may have different goals and priorities. This difference can in turn affect the workarounds they practice. For example, those in managerial roles such as charge nurses can more easily request others’ assistance. Workarounds draw on tacit knowledge of others’ abilities and willingness to helpA workaround cannot be effective if the persons involved are not able or willing to perform. Initiators of workarounds take their tacit knowledge of others’ skills and abilities into account when deciding how to implement workarounds. As one charge anesthesiologist stated, "[You] just kind of know from experience who your stronger people are, who your weaker people are, who's flexible…".Workarounds can have a cascading effect Workarounds can initiate a series of further workarounds before the system is back to a stable state. In one case, for instance, a patient was taken to the OR without blood type information. To deal with this problem, personnel chose to substitute the universal donor blood type O+. However, the success of this workaround depended on a second workaround of borrowing the O+ blood from a neighboring resuscitation area, thereby leaving a potential shortage (and yet another workaround) in that area.Workarounds often rely on principles of fairness and who owes whom favorsInterviewees reported a sense of memory for workarounds and who was impacted by them. Workarounds were threaded in the sense that people who provide favors were likely to come back later with their own request for a favor. As one charge anesthesiologist stated, “[In any OR management situation] what you really want when you’re running the OR is you want everybody to owe you a favor at all times…Ok, now they’re the one who has to get bumped. It helps if they can remember last week when you helped them out…and it works the opposite way too, if somebody hurts us they’re not going to get the next break.” TECHNOLOGY RECOMMENDATIONSBased on these general workaround principles we’ve determined four system requirements for technology to better support workarounds.Training module. We propose a training module that helps new staff select workarounds and predict their outcomes. The module provides a library of previously used workarounds that indicates what was done by whom, and the outcome. Users are presented with a prioritized list of alternative workarounds.Memory module.We found that reciprocity of favors was an important principle in creating workarounds. The memory module provides a “score-keeping” mechanism to record persons impacted by each workaround. The module would help remind initiators of workarounds who they can call on for a favor, who can be counted on, and where to find people with particular experience or skills.Decision-making rmed decision-makers make much better decisions than uninformed ones. We propose a decision-making module that allows users to simulate and predict the short and long-term effects of different workarounds. The system could also suggest strategies to best handle repercussions if a workaround is unavoidable. Awareness module.Finally, we propose an awareness module that provides knowledge of available resources and personnel. An experienced user may already have a general sense of who they can count on or what materials they can substitute for others, but lack of knowledge of the availability of these persons or resources may hinder decisions, or lead to more workarounds later in time. CONCLUSION AND FUTURE DIRECTIONSThis study investigated workarounds in a trauma center. The most notable findings concern the ways that workarounds are embedded within a wider system: One workaround may lead to the need for others, and a request for a favor puts the requestor in a position of owing others favors in the future. Consequently, technological solutions to help workers cope with unexpected events will need to take into account the historical sequence and organizational embeddedness of workflow exceptions. In follow up research, we are looking in more depth at workarounds in medical contexts. We focus on the impact of workarounds in short- and long-term coordination of work and on the relationship between a workarounds’ effectiveness and its adoption as a standard approach to dealing with certain types of exceptions. We are also developing technology based on our recommendations. ACKNOWLEDGMENTSThis material is based upon work supported by the National Science Foundation under grant #0325087. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of NSF. We thank Mariesa Cash, Joseph Iloreta, Julia Ludwick, Jared Metter, Pablo Quinones, Katie Waite, and Jim Zheng for their help preparing data for analysis, Cheryl Plasters for assisting in collecting data and Tamas Gal for his technical support. REFERENCES[1]Bardram, J. E. (2000). Temporal coordination: On timeand coordination of collaborative activities at a surgical department. Proceedings of CSCW 2000, pp. 157-187.NY: ACM Press.[2]Beyer, H., & Holtzblatt, K. (1998). Contextual design:Defining customer-centered systems. San Diego:Morgan Kaufmann.[3]Bricon-Souf, N., Renard, J., & Beuscart, R. (1999).Dynamic workflow model for complex activity inintensive care unit. International Journal of MedicalInformatics, 53, pp.143-150.[4]Faraj, S. & Xiao, Y. (In Press) Coordination in fastresponse organizations. Management Science.[5]Nemeth, C. (2003). The Master Schedule: Howcognitive artifacts affect distributed cognition in acute care. Unpublished doctoral dissertation.[6]Plasters, C., Seagull, F.J., & Xiao, Y. (2003)Coordination challenges in operating roommanagement: An in-depth field study. AMIA 2003Symposium Proceedings, pp.524-528.[7]Tucker, A. & Edmondson, A. (2002). Managing routineexceptions: A model of nurse problem solving behavior.Advances in Health Care Management, pp.87-113. [8]Xiao, Y., Seagull, F.J., Faraj, S., & Mackenzie, C.F.(2003). Coordination Practices for Patient Safety:Knowledge, Cultural, and Supporting ArtifactRequirements. Proc. of International ErgonomicAssociation 2003 (Macroergonomics in Healthcare:Session).[9]Xiao, Y., Seagull, F.J., Hu, P., Mackenzie, C.F., deVisser, J., & Wieringa, P. (2003). DistributedMonitoring In a Dynamic Environment: Trade-offs ofInformation Access and Privacy. Proc. of 2003 IEEEInternational. Conference on Systems, Man, andCybernetics, pp.1772-1777.。
SAP workflow(OK)

第一节:现在开始总结workflow,虽然有些过时的技术,但是还是有很多公司在使用,特别是一些比较大的企业,系统升级比较慢。
也为自己知道的,做过的事情有一个总结,希望还能有点参考意义。
1.从目的上来说,就是让整个业务更加流畅,更加透明,更加方便快捷。
2.既然有了workflow,就应该相应的有一个管理系统,以及一个开发环境,这些我们都能够在sap中找到。
T-code: SWDM3.在使用workflow之前,我们必须明白一件事情,那就是不管什么样的workflow,都会有一整套的业务原型。
在定义workflow之前,应该找到相应的已经存在的模型(或许也可以自己开发)。
4.不要误会workflow的功能,其实它是很强大的,虽然我们经常只使用它的一部分功能。
包括,email的通知,transaction的集成,不同系统之间的数据交换(ALE/EDI)等等。
Workflow的定义:每个workflow都能在sap中找到业务流程;Workflow由很多的步骤组成;Workflow可以由事件触发;Workflow的创建:如果我们已经知道了业务如何执行,那么就可以创建自己的workflow了,于是我们会需要workflow builder.T-code: SWDD第二节:SAP提供了大量的Workflow的模板可以供大家参考,如果不符合具体的业务流程,可以对该模板做增强。
不过就像SAP标准程序一样,不能对其进行修改,当然,你可以把这个模板复制出来然后对其修改,具体就看你的需要了。
查看workflow 模板的方法:T-code FTC_DISTask type: WSWorkflow 助手:Business Workplace–SBWP当Workflow执行到某一步需要特定的用户确认或者批准的时候,就会发出work item到该用户的workplace,以使该用户做出相应的操作。
Business Workplace可以和很多外部工具集成,例如lotus note,MS outlook等等,这样使workflow的通知方式更加灵活。
工作流中的异常处理设计(精)

工作流系统的异常处理*李伟平,范玉顺(清华大学国家CIMS 工程研究中心,北京 100084 +Exception Handling in Workflow Management Systems-An OverviewLI Weiping, FAN Yushun(National CIMS Engineering & Research Center, Tsinghua University, Beijing 100084, China++Corresponding author: 86-10-62789636-1059, E-mail:wpli@Abstract: Workflow management system deals with the modeling and coordinated execution of business processes. These processes are often of long duration and may involving many executors, software and distributed resources. So there may exist potential exception when the workflow is running. After the Workflow Management System (WfMS is deployed in a certain enterprise, the enterprise become increasingly dependent on it to carry on their daily business activities. Thus some kinds of exception handling method will be introduced into the WfMS to resolve the exception when the workflow is running. While the exception handling of workflow has received increasing attention in recent years. This paper first introduces the question of exception handing in WfMS with the definition, classification and resolution of exception handling. Based on the evaluation of existing research methods, we indicate the developing trends of exception handling in WfMS and some key issue is put forward.Key words: workflow, workflow exception, exception handling, ECA rules, knowledge management, transaction, pattern摘要:工作流系统负责业务过程的建模和执行,这些业务过程往往涉及到多个参与者,需要使用分布的资源,调用多个软件系统,而且时间跨度很长,因此在工作流执行时可能存在多种潜在的工作流异常。
oracleBPEL工作流介绍

Receive PO
Transform
Transform
Receive PO
Send PO Ack
Ack
PO Acknowledgement
Receive PO Response
PO Response
Receive PO Response
Transform
Two BPEL workflow templates reflecting a business agreement
WSFL
(IBM)
WSCL
(HP)
BPEL4WS 1.0 BPEL4WS 1.1
(IBM, Microsoft)
(OASIS)
Orchestration vs Choreography
Orchestration – An executable business process describing a flow from the perspective and under control of a single endpoint (commonly: Workflow)
Industry wide language for business processes
– Common skill set and language for developers
Choice of process engines
– Standards lead to competitive offerings
</process>
BPEL Activities
Primitive Activities <invoke> <receive> <assign> <reply> <throw> <terminate> <wait>
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Exception Handling in Workflow SystemsZongwei Luo, Amit Sheth, Krys Kochut, and John MillerLarge Scale Distributed Information System Lab415 GSRC, Computer Science department, University of GeorgiaAthens, GA 30602{luo, amit, kochut, jam}@AbstractIn this paper, defeasible workflow is proposed as a framework to support exception handling for workflow management. By using the “justified” ECA rules to capture more contexts in workflow modeling, defeasible workflow uses context dependent reasoning to enhance the exception handling capability of workflow management systems. In particular, this limits possible alternative exception handler candidates in dealing with exceptional situations. Furthermore, a case-based reasoning (CBR) mechanism with integrated human involvement is used to improve the exception handling capabilities. This involves collecting cases to capture experiences in handling exceptions, retrieving similar prior exception handling cases, and reusing the exception handling experiences captured in those cases in new situations.Keyword: Case-based Reasoning (CBR), Context-dependent Reasoning, Exception Handling, Ontology, Workflow System1 IntroductionWorkflow technology is considered nowadays as an essential technique to integrate distributed and often heterogeneous applications and information systems as well as to improve the effectiveness and productivity of business processes [1,2,3,4]. A workflow management system (WfMS) is a set of tools providing support for the necessary services of workflow creation, workflow enactment, and administration and monitoring of workflow processes, which consist of a network of tasks. These workflow processes are constructed to conform to their workflow specifications. However, due to foreseen or unforeseen situations, such as system malfunctions due to failure of physical components or changes in business environment, deviations (exceptions) of those workflow processes from their specifications are unavoidable. Workflow systems need exception handling mechanism to deal with those deviations. Exception-handling constructs, as well as the underlying mechanisms, should be sufficiently general to cover various aspects of exception handling in a uniform way. In addition, it helps to separate the modulesfor handling exceptional situations from the modules for the normal cases. We believe that designing an integrated human-computer process may provide better performance than moving toward an entirely automated process in exception handling.Let’s take a look at a motivating workflow application to characterize the scope of exception handling (see Figure 1.1). This infant transportation application involves the transportation of a very low birth weight infant of less than 750 grams, at or below 25-26 weeks gestation, from a rural hospital located within 100 miles from the Neonatal Intensive Care Unit (NICU) at the Medical College of Georgia (MCG). Such transportation usually takes up to 2.5 hours. In the ambulance there are two or three healthcare professionals who perform different roles. During the transport the ambulance personnel perform the standard procedures to obtain medical data for the infant. The first step of this application involves the task that allocates resources, such as healthcare professionals, equipment, and so on. The last step is to prepare for admission to the NICU.Figure 1.1 High-level workflow for newborn infant transportationIf exceptions are raised during the transport, corrective actions must take place. The decision of the corrective procedures involves collaboration and coordination between the ambulance personnel and the consultants at MCG’s NICU. This application is very dynamic because the changes to the infant’s health status as indicated by the vital signs such as the known risk factors may lead to changes in the treatment plan. Such changes can occur rapidly. For example, a low weight infant can dehydrate in as few as ten minutes while an adult would take at least several hours to reach the same severity. Such changes to theinfant’s status are modeled as exceptions. Consider a “normal” treatment plan as shown at the top of Figure 1.2. Occurrence of heart murmur that is known as a risk factor related to cardiac disease would be modeled as an exception (from the normally expected and correspondingly modeled process). One way of handling such an exception is to change the process such that the cardiovascular related task is performed earlier than what was originally planned (as shown at the bottom of Figure 1.2).Figure 1.2 Treatment plan change in infant transportation taskThis healthcare application raises several requirements for workflow systems to support:•The processes in this application are very dynamic. To support coordination of such processes, a systematic way of workflow evolution, including dynamic structure modifications should be worked out.•There are potential collaboration activities in this transport process; e.g., the healthcare professionals may need advice from specialists in the NICU. The advice is context based. The results from the collaborations may affect the progress of the ongoing process coordination.•The health professionals on board are not necessarily experienced in every aspect of intensive care. A case repository used in the case-based reasoning (CBR) [5] based exception-handling system stores valuable experience learned to help them make decisions.•Exceptions are not avoidable in such an environment. An abnormal situation can cause special attention for healthcare professionals. Those abnormal situations should be resolved as soon as possible due to the nature of this application -- newborn infant transport. Prior experience gained in handling similar abnormal situations can facilitate the exception resolution process. At the same time the set of exception handlers that need to be checked, can be limited by capturing more workflow execution context.Approaches to address the first two requirements, although topics of our research are beyond the scope of this paper. In this paper, we discuss an approach of defeasible workflow to address the last two requirements. Defeasible workflows target workflow applications in the dynamic and uncertain business environment by modeling organizational processes through justified ECA (JECA) rules developed to support context-dependent reasoning processes. There are three major contributions to exception handling in workflow management systems in this approach.1. By using the JECA rules to capture more contexts in workflow modeling, defeasible workflowenhances the exception handling capabilities of WfMSs through supporting context dependent reasoning in dealing with uncertainties. It can limit possible alternative exception handlers in dealing with exceptional situations.2. It considers workflow evolution, which is an active research topic, a good candidate to exceptionhandling,which is usually called adaptive exception handling. That is, possible modifications of workflows are considered as exception handlers, along with other candidates such as ignore, retry, workflow recovery, and so on. Thus, several modification primitives are given in defeasible workflow that will ensure the modified workflows meet the correctness criteria established.3. A case-based reasoning (CBR) [5] based exception handling mechanism with integrated humaninvolvements is used in defeasible workflow to support exception-handling processes. This mechanism enhances the exception handling capabilities through collecting cases to capture experiences in handling exceptions, retrieving similar prior exception handling cases, and reusing the exception handling experiences captured in those cases in new situations.The organization of this paper is as follows: We give a perspective on exceptions in section 2 that provides directions on how exception aware systems should be built. We introduce defeasible workflow in section 3 that is used to support such healthcare applications like the infant transport. In section 4, we introduce a CBR-based approach for the exception handling. In section 5, we discuss related works. Finally, section 6 concludes this paper.2 What is an exception?Exceptions in our view refer to facts or situations that are not modeled by the information systems or deviations between what we plan and what actually happen.Exceptions are raised to signal errors, faults, failures, and other deviations. They depend on what we want and what we can achieve. For example, in the infant transport application, space provided by an ambulance is limited. So is the transport time. The exception handling mechanisms might be different from that used in NICUs because of the differences in time, space and places. In most realistic situations and non-trivial systems, there are always interests conflicts between what we want and what we can achieve. It is more acceptable to design a system that canoperate as best as it can; when there is an exception, it can be handled by the system. We call such a system an exception-aware system.Exceptions provide great opportunities for the systems to learn, correct themselves, and evolve. To build an exception aware system, it is beneficial to clarify the nature of exceptions to get guidelines in the systems development. As shown in Figure 2.1, known, detectable, and resolvable form three dimensions for the exception knowledge space. The known dimension is usually captured through exception specification. Supervision is one of the approaches to enlarge exception knowledge space in the detectable dimension. To resolve exceptions, capable exception handlers should be available that make up the resolvable dimension of the exception knowledge space. Any position in this exception knowledge space can be represented as an exception point. The exception knowledge of an exception aware system is the set of all those points.KnownResolvable DetectableLearning systemSupervisionHandlingFigure 2.1 Three-dimensional analyses of exceptions•Known: Every person’s knowledge is limited. The same is true for a system. The world is governed by rules that either we know or we are still investigating, and our knowledge continues to expand through learning. As this learning process continues and unknown or uncertainties become known, the decision may be revised and other uncertainties may be considered. When a system cannot meet the new situation, exceptions occur. We call these kinds of exceptions unknown exceptions, since they are beyond the system’s current knowledge. Otherwise, we consider them known. For example, during the transport of the newborn infant, an unknown exception may be caused by an abnormal situation that has not been met before. A basic solution to unknown exceptions is to build an open system that is able to learn and can be adapted to handle those exceptions.•Detectable: Exceptions can be classified based on a system’s capabilities to detect an exception. If systems can notice the occurrence of an exception then we call it a detectable exception; otherwise we consider it undetectable. An unknown exception is usually undetectable because there is no way forthe system to know about it until further improvement to the system is accomplished to achieve that capability. Sometimes an unknown exception might be detected as another known exception.Detection of an exception depends on the system’s capabilities. For example, if there is no equipment on board to measure certain situations, e.g., neurologic checking of the newborn infant, exceptions related to neurologic situations might not be detected. Moreover, if there is no mapping from the errors occurring in the measuring equipment in which an equipment related exception should be raised to a workflow system’s exception, that equipment exception will not be detected either. If the system can notice that there is an exception, it may be possible for the system to derive capable exception handlers to handle such exceptional situations.•Resolvable: Undetectable exceptions are not resolvable at the time of occurrence, for their occurrences are unknown to the system. Also, there are certain known exceptions that may be ignored during system modeling time for certain specific reasons, such as the frequency of their occurrences is so low, the effect caused by the exceptions to the system can be ignored. When such exceptions actually occur, the system cannot handle them (e.g., the Y2K bug). For example, on board there are necessary medicines for commonly occurring health conditions for newborn infants. When a medicine is not on board but is needed for a situation that rarely occurs, then the corresponding exception to the process is not resolvable at that time. Based on the system’s handling capability, exceptions can be categorized into two categories: resolvable and irresolvable. When exceptions occur, the system can derive a solution to resolve the deviations. Such exceptions are called resolvable exceptions. When exceptions occur, but the system cannot derive a solution to solve the deviation to meet the requirement, then it is called irresolvable exceptions.Based on the above perspective, exception aware systems should be built to have adequate initial exception knowledge represented as exception points. To deal with exceptional situations, a system actually finds an exception point in the exception knowledge space through propagation and masking. Propagation allows a system to propagate an exception to a more appropriate system component to find an appropriate exception point. Masking usually means when there are several exception points, the one that is close to where exception is detected is the best candidate. Defeasible workflow is proposed in section 3 to support a systematic way of propagation and masking.3Defeasible workflowOrganizational processes are often dynamic. They evolve over time and often involve uncertainty. To adapt to its environment, a workflow should be flexible enough that necessary modifications to its specifications and instances are allowed. They need to be complemented with execution support or run-time solutions such as dynamic scheduling, dynamic resource binding, runtime workflow specification, and infrastructure reconfiguration. For example, uncertainties in clinical decision-making processes, such as incomplete datain the report, should be eliminated as early as possible, preferably at the design stage. However, if this is not possible at runtime exceptions should be raised and handled. The clinical decision-making is a process by which alternative strategies of care are considered and selected. Those alternatives can be potentially limited if more useful contexts are available during the clinical decision-making. Furthermore, the following basic facts about clinical decision processes [6] have shown that in very complicated situations, necessary contexts should be captured in order to make correct decisions efficiently:•“Human and environmental influences are frequently complex, uncertain and difficult to control”.Necessary context can help analyze the complex situations.•“Decisions should be clear-cut and error-free. The nursing and medical professions have expressed an interest in the precision and objectivity by which decisions are made, while simultaneously retaining an individualistic, holistic approach to patient management”. The context-dependent reasoning approach is one of the solutions to support such decision-making processes.•“Standardization of management plans is usually accompanied by paying less attention to differences in patients’ needs”. This actually means such standardization should consider individual differences that can only be achieved by adding exceptions to the standardization. Those exceptions are actually used to capture necessary context when the standardized plans are enforced.Defeasible workflows target workflow applications in the dynamic and uncertain business environment by capturing more workflow contexts and supporting context-dependent reasoning processes. They are characterized as follows:•Organizational processes are modeled through JECA rules (see below).•When no default consequences can be derived during the execution, or the conflicts occur that cannot be resolved in the default evaluation, exceptions will be raised. WfMSs will try to derive capable handlers to handle the raised exceptions.•If none of the derived handlers are suitable, or handlers cannot be derived, past experiences in handling exceptions will be sought and reused by retrieving and adapting similar exception handling cases stored in the case repository.•Human interaction will be necessary if no acceptable solutions can be automatically derived. Solutions provided by a person, who is usually a specialist, will be abstracted, and stored into the case repository.3.1 JECA RulesW e have extended the well known ECA rules specification as Justified Event-Condition-Action (JECA) rules to model business logic based on work in context-dependent reasoning [7]. There are several workflow prototypes (e.g. [8, 9]) that have adopted ECA rules as modeling tools. However, the contexts that can be captured by ECA rules are limited. The C in an ECA rule, which is used to capture rules evaluation context, is used as a condition that should be satisfied so that the action specified in that ECArule can be executed. That is, an ECA rule, once triggered, can only be denied if its condition cannot be satisfied. This makes ECA rules incapable in modeling workflows in uncertain business environments. In JECA rules, justification (J) provides a reasoning context for the evaluations of ECA rules to support context dependent reasoning processes in dealing with uncertainties. Each JECA rule r (j, e, c, a) consists of four parts as follows:•Justification (j): Justification forms the reasoning context in which evaluation of the specific JECA rule to be performed. Usually it is specified as a disqualifier, i.e., a JECA rule will be disqualified if its justification is evaluated true.•Event (e): when event occurs, related JECA rules will be evaluated. We say the JECA rules are triggered.•Condition (c): logic constraints to be satisfied so the action in the rule can be taken if the rule is not disqualified.•Action (a): necessary actions to be taken if this rule is not disqualified, and events occur, conditions are met.Consider a simple rule-processing algorithm given in Algorithm 3.1. This algorithm executes JECA rules by picking up a triggered rule one by one. When there are no more triggered rules, execution will terminate.while there are triggered JECA rules do:1. find a triggered JECA rule r2. evaluate r’s condition and justification3. if r’s condition is true, and justification is not true then execute r’s actionAlgorithm 3.1 A simple JECA rule execution algorithmConsider the following example of exception handling rule in dealing with an exception related to cardiac disease d. In this rule, the exception is related to certain type of cardiac disease d, and the corrective action is to take an initial assessment for this type of cardiac disease d. The justification provides a reasoning context (as commonly followed in this medical specialty) that if there are one or more blood family members of opposite sex who had this type of cardiac disease d before, then this disease cannot be this type of cardiac disease d. The initial assessment can only be performed if the justification doesn’t disqualify this JECA rule.Event: Cardiac disease d related exception eventCondition: Risk factor is heart murmurs (related to the type Cardiac Disease d)Action: Initial Assessment for Cardiac Disease dJustification: Blood family member of opposite sex does have this type of Cardiacdisease dThe above example, if modeled in ECA rules, can be:Event: Cardiac disease d related exception eventCondition: Risk factor is heart murmur (related to the type Cardiac Disease d) and Blood family member of opposite sex doesn't have this type of Cardiac disease dAction: Initial Assessment for Cardiac Disease d.When a cardiac disease d related exception event actually occurs, necessary contexts should be available so that the condition in that ECA rule can be checked, i.e., the risk factor is heart murmur and blood family member of opposite sex does have this type of cardiac disease. If the condition "Blood family member of opposite sex does have this type of cardiac disease d" cannot be checked true, then this ECA rule cannot be satisfied. Is it correct not to model that condition of "Blood family member of opposite sex does have this type of cardiac disease d" in the ECA rule? The ECA rule then becomes:Event: Cardiac disease d related exception eventCondition: Risk factor is heart murmur (related to the type Cardiac Disease d)Action: Initial Assessment for Cardiac Disease d.However, the answer is no, because this ECA rule cannot model that the action should not be executed when condition "Blood family member of opposite sex does have this type of cardiac disease d" is true. In the approach of JECA rules, the condition of "Blood family member of opposite sex does have this type of cardiac disease d" is a justification for that JECA rule. If the justification cannot be evaluated true, then the JECA rule will not be disqualified. So the action in that JECA rule can be executed if the risk factor of heart murmur is true.3.2 JECA rules evaluationTo apply the context-dependent reasoning processes [7], those JECA rules are transformed into a form that is usually used in the context-dependent reasoning, called default [7]. A default has three parts, prerequisite(P), justification (J), and consequence(C) specified in logic expressions. Those defaults are constructed through JECA rules with mappings from J to justifications, C to prerequisite and A to consequence. Usually E in a JECA rule is associated with the justifications and prerequisite in the default that the JECA rule is mapped to. In order to apply the defaults, the prerequisite of the defaults should be proved. It is required the defaults should be justified. This means the justifications should not deny the applicability of the default. Consequence, the third part in default, forms a belief set through extension computation [7]. Please refer to [7] for detailed information about extension computation. Conflicts such as inconsistencies existing in the belief set should be resolved by non-monotonic reasoning process in whichreasoning results may become invalid if more facts become available, or reasoning context has changed. An algorithm of execution of JECA rules through default evaluation is given in Algorithm 3.2.while there are triggered defaults do:1. find related defaults2. evaluate defaults through context dependent reasoning, resolve anyconflicts in the belief set3. actions in the belief set will be executedAlgorithm 3.2 JECA rule processing through default evaluationT he defaults will be clustered into several sets called domains. Each default is associated with a local reasoning unit. If the local reasoning unit cannot make an acceptable decision, another reasoning unit at that domain that can get access to domain context will be consulted. A global reasoning unit is responsible for decision making in the global context. The local reasoning unit can also make a decision according to the partially available information without consulting another local unit or a unit at a higher level. This clustered reasoning architecture is well suited in workflow management because organizational processes modeled by workflows are clustered and/or layered in nature in which local decisions can often be reached. The criteria used in clustering can be either one or a combination of the following:•Security: For security reasons, defaults must be clustered so sensitive information can be exchanged ina controlled manner. In the infant transport example certain medical records that may contain sensitiveinformation, such as HIV, abnormal behavior of the infant's parents, should be securely controlled. •Organization: It is natural to cluster defaults into several domains to model the organizational structure in that organization. In the infant transport example the defaults can be grouped according to the organizational roles those health professionals can play.•Performance: To provide better performance, it is necessary to cluster the defaults into several domains in which defaults can be more efficiently found and evaluated.3.3 Conflict resolutionD uring JECA rules evaluation, dynamic resolution is used to select default values (resources, algorithms, routing, numerical values, etc.) and resolve conflicts. Inconsistent information as well as coarse rule granularity in JECA rules can lead to conflicts during default evaluation. The conflicts may lead to exceptions if the conflicts cannot be resolved in the default evaluation. Conflicts in default evaluation can be either one or more of the following:•Temporal conflict: defaults formed in subsequent time result in conflicts. For example, the healthcare professionals make two decisions separately. The decisions are specified in defaults that are fed into the workflow systems in the order the decisions are made. It is possible that the two decisions mayresult in conflicts. The first decision may involve certain kinds of drugs to be applied. The second decision may involve drugs that should not be applied after the drugs in the first decision are applied. •Role conflict: defaults formed or evaluated by different role may result in conflicts. The healthcare professionals on board may have different opinions about the situation of the infant. During the assignment of healthcare professionals to the transport of infant, there may exist role conflicts, such as agents not available, an agent who can play that the caregiver role is not suitable to attend the infant. •Semantic conflict: An example that might lead to semantic conflicts is alternative interpretation of the consequence of defaults. This is possible due to the nature of non-monotonic reasoning that is context dependent. If the contexts are different, interpretations in different contexts may also be different.T o resolve those conflicts, the defaults are assigned priorities, or more generally, are ordered by partial ordering relations regulated in business policies (organizational, security, etc.). That is, some defaults may be preferable to others, and assuming they are applicable, they should be used first. To resolve any inconsistencies, polices are based on one of the following criteria:•Special: Preference will be given to exceptions over normal cases. For example, whenever a local decision cannot be made in the default evaluation, an exception is always raised.•Hierarchical: Consequences derived at higher positions in the hierarchy will be favored over those at lower positions. In the infant transport application, if the medical situation of the infant becomes serious, the decision made from the personnel at a higher position who can be responsible for the action taken will be preferred.•Temporal: Consequences from latest defaults will be favored over earlier ones. In the infant transport application, the personnel on board may consult the experts in the MCG’s care unit (NICU). During the decision making process, the experts in the NICU might give one suggestion at one time, and later they might come up with another suggestion. The later one might be given a higher priority during the decision making process.•Semantic: Interpretations that are more plausible will be preferred to less plausible ones. In the example application, if a symptom is discovered and if it might be caused by several different reasons, the personnel on board may derive one that he believes is the most reasonable.3.4 Rule graphsIn rule execution, there is a danger of non-termination. In this section, we give a sufficient condition for the termination of rule execution over a JECA rule set by extending the rule graphs in [10]. Furthermore we adapt the results from rule analysis [11] for workflow modeling. Further details about rule analysis related proofs appear in [10, 11]. We ensure termination of evaluation of J and C in JECA rule evaluation, we limit the logic expressions used in specifying J and C components of JECA rules to be quantifier free. Furthermore, we assume that facts that need to be checked in rule evaluations are finite.。
