System and networks-43
贵州省施秉县2024届毕业升学考试模拟卷英语卷含答案

贵州省施秉县2024届毕业升学考试模拟卷英语卷含答案考生须知:1.全卷分选择题和非选择题两部分,全部在答题纸上作答。
选择题必须用2B铅笔填涂;非选择题的答案必须用黑色字迹的钢笔或答字笔写在“答题纸”相应位置上。
2.请用黑色字迹的钢笔或答字笔在“答题纸”上先填写姓名和准考证号。
3.保持卡面清洁,不要折叠,不要弄破、弄皱,在草稿纸、试题卷上答题无效。
Ⅰ. 单项选择1、In our school library there _________ a number of books on science and the number of the books _________ growing. A.are; is B.is; are C.is; is D.are; are2、Alex and Tom are brothers. ______ often help their father wash the car.A.I B.You C.We D.They3、— What time do you usually get up?— I usually_____ up at 6:30.A.get B.got C.will get D.was getting4、— We are proud of ________ school. I will miss it after I leave it.— So do we. ________ is also a great school with lots of hardworking teachers andstudents.A.our; Ours B.ours; Our C.we; Ours D.us; Our5、____ I was in the US, I made a lot of American friends.A.While B.Although C.Unless D.Until6、Although you failed four times, I still hope you can have ______ try.A.the fifth B.a fifth C.the fourth D.a fourth7、Jiayuguan is the west of Gansu Province and it is famous the Great Wall.A.on;for B.in;of C.to;of D.in ;for8、—_______ you able to see the sea from this window?—Yes, it’s peaceful. Some people are swimming in the sea.A.Do B.Are C.Will D.Have9、---Could you please tell me ________?---Yes, she came to teach here just last week.A.that she is a new teacher B.when did she come hereC.whether she is a new teacher D.what’s wrong with her10、Both of my parents ______ /wɜ:k/ in a bank.A.walk B.week C.work D.weakⅡ. 完形填空11、There is nothing wrong with being shy. In fact, 1 happy, successful people are shy. You can try to say goodbye to your shyness. Here’s how to do so.1. Start Small. At home, practice 2 and saying hi while looking at yourself in the mirror. Then try this at schoolw ith kids you know well. Once that becomes a habit, try doing the same with kids you don’t know as well.2. 3 Are Key. Once you 4 smiling and saying hi, it’s time to start a conversation. All you really have to do is to ask a question or two about a person’s 5 : What’s your favorite movie? Do you like playing tennis? Just be careful not to ask questions that are too personal 6 might be hurtful.3. Choose Face-to-face Time. Many shy girls say it’s easier for them to talk to people7 . In a recent survey, nearly two out of every 10 shy girls said being online has made them even shyer in real life. So 8 your cell phone, step away from the computer, and put in some face-to-face time with the people in your life.4. Star in Your Own Life. Looking people in the eye, saying hi with a smile, and starting conversations will probably feel strange at first, but every time you practice your new skills, it will become a little 9you keep working at it, you will become more comfortable talking to other people.1.A.few B.some C.many2.A.crying B.smiling C.thinking3.A.Talks B.Conversations C.Questions4.A.are used as B.are used to C.are used for5.A.questions B.problems C.interests6.A.or B.and C.but7.A.face to face B.online C.at home8.A.put down B.take down C.take out9.A.hard B.easy C.easier10.A.When B.As long as C.UnlessⅢ. 语法填空12、IV.语法填空:用所给单词的适当形式填空,未提供单词的根据上下文填入适当的词。
计算机组成原理 英文

计算机组成原理英文Computer Organization Principles。
Computer organization is a fundamental topic in the field of computer science and engineering. It deals with the structure and components of a computer system, including the hardware and software aspects. Understanding the principles of computer organization is essential for computer professionals to design, develop, and optimize computer systems. In this document, we will explore the key concepts and principles of computer organization.1. Basic Concepts of Computer Organization。
At the core of computer organization are the concepts of data representation, storage, processing, and communication. Data representation involves encoding and interpreting data in various forms, such as binary, decimal, and hexadecimal. Storage refers to the mechanisms for storing and retrieving data, including primary storage (RAM) and secondary storage (hard drives, SSDs). Processing involves the manipulation of data through arithmetic and logic operations, as well as control flow. Communication encompasses the exchange of data between different components of a computer system, such as input/output devices, memory, and processors.2. Architecture and Organization。
自动化专业英语王宏文全文翻译

自动化专业英语PART 1Electrical and Electronic Engineering BasicsUNIT 1A Electrical Networks ————————————3B Three-phase CircuitsUNIT 2A The Operational Amplifier ———————————5B TransistorsUNIT 3A Logical Variables and Flip-flop ——————————8B Binary Number SystemUNIT 4A Power Semiconductor Devices ——————————11B Power Electronic ConvertersUNIT 5A Types of DC Motors —————————————15B Closed-loop Control of DC DriversUNIT 6A AC Machines ———————————————19B Induction Motor DriveUNIT 7A Electric Power System ————————————22B Power System AutomationPART 2Control TheoryUNIT 1A The World of Control ————————————27B The Transfer Function and the Laplace Transformation —————29 UNIT 2A Stability and the Time Response —————————30B Steady State—————————————————31 UNIT 3A The Root Locus —————————————32B The Frequency Response Methods: Nyquist Diagrams —————33 UNIT 4A The Frequency Response Methods: Bode Piots —————34B Nonlinear Control System 37UNIT 5 A Introduction to Modern Control Theory 38B State Equations 40UNIT 6 A Controllability, Observability, and StabilityB Optimum Control SystemsUNIT 7 A Conventional and Intelligent ControlB Artificial Neural NetworkPART 3 Computer Control TechnologyUNIT 1 A Computer Structure and Function 42B Fundamentals of Computer and Networks 43UNIT 2 A Interfaces to External Signals and Devices 44B The Applications of Computers 46UNIT 3 A PLC OverviewB PACs for Industrial Control, the Future of ControlUNIT 4 A Fundamentals of Single-chip Microcomputer 49B Understanding DSP and Its UsesUNIT 5 A A First Look at Embedded SystemsB Embedded Systems DesignPART 4 Process ControlUNIT 1 A A Process Control System 50B Fundamentals of Process Control 52UNIT 2 A Sensors and Transmitters 53B Final Control Elements and ControllersUNIT 3 A P Controllers and PI ControllersB PID Controllers and Other ControllersUNIT 4 A Indicating InstrumentsB Control PanelsPART 5 Control Based on Network and InformationUNIT 1 A Automation Networking Application AreasB Evolution of Control System ArchitectureUNIT 2 A Fundamental Issues in Networked Control SystemsB Stability of NCSs with Network-induced DelayUNIT 3 A Fundamentals of the Database SystemB Virtual Manufacturing—A Growing Trend in AutomationUNIT 4 A Concepts of Computer Integrated ManufacturingB Enterprise Resources Planning and BeyondPART 6 Synthetic Applications of Automatic TechnologyUNIT 1 A Recent Advances and Future Trends in Electrical Machine DriversB System Evolution in Intelligent BuildingsUNIT 2 A Industrial RobotB A General Introduction to Pattern RecognitionUNIT 3 A Renewable EnergyB Electric VehiclesUNIT 1A 电路电路或电网络由以某种方式连接的电阻器、电感器和电容器等元件组成。
计算机b类刊物与会议分类信息
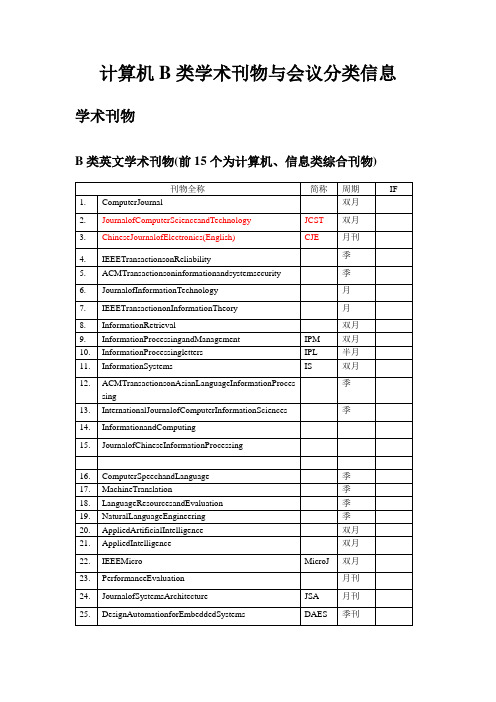
月
31.
ACMTransactionsonInternetTechnology
季
32.
JournalofParallelandDistributedComputing
JPDC
月
33.
ACMTransactionsonEmbeddedComputingSystems
TECS
月
34.
IEEETransactionsonSystems,ManandCybernetics
113.
InternationalJournalofPatternRecognitionandArtificialIntelligence
IJPRAI
双月刊
114.
IEEETransactionsonSystem,Man,andCybernetics
SMC
月刊
115.
InternationalJournalofDocumentAnalysisandRecognition
AIR
月刊
106.
ArtificialLife
AF
月刊
107.
EvolutionaryComputation
EC
双月刊
108.
NeuralNetworks
NN
9/12
2
109.
InternationalJournalofKnowledge-BasedandIntelligentEngineeringSystems
KES
月刊
110.
ArtificialIntelligenceinEngineering
AIE
月刊
111.
ComputationalIntelligence:AnInternationalJournal
自动化专业英语全文翻译

《自动化专业英语教程》-王宏文主编-全文翻译PART 1Electrical and Electronic Engineering BasicsUNIT 1A Electrical Networks ————————————3B Three-phase CircuitsUNIT 2A The Operational Amplifier ———————————5B TransistorsUNIT 3A Logical Variables and Flip-flop ——————————8B Binary Number SystemUNIT 4A Power Semiconductor Devices ——————————11B Power Electronic ConvertersUNIT 5A Types of DC Motors —————————————15B Closed-loop Control of DC DriversUNIT 6A AC Machines ———————————————19B Induction Motor DriveUNIT 7A Electric Power System ————————————22B Power System AutomationPART 2Control TheoryUNIT 1A The World of Control ————————————27B The Transfer Function and the Laplace Transformation —————29 UNIT 2A Stability and the Time Response —————————30B Steady State—————————————————31 UNIT 3A The Root Locus —————————————32B The Frequency Response Methods: Nyquist Diagrams —————33 UNIT 4A The Frequency Response Methods: Bode Piots —————34B Nonlinear Control System 37UNIT 5 A Introduction to Modern Control Theory 38B State Equations 40UNIT 6 A Controllability, Observability, and StabilityB Optimum Control SystemsUNIT 7 A Conventional and Intelligent ControlB Artificial Neural NetworkPART 3 Computer Control TechnologyUNIT 1 A Computer Structure and Function 42B Fundamentals of Computer and Networks 43UNIT 2 A Interfaces to External Signals and Devices 44B The Applications of Computers 46UNIT 3 A PLC OverviewB PACs for Industrial Control, the Future of ControlUNIT 4 A Fundamentals of Single-chip Microcomputer 49B Understanding DSP and Its UsesUNIT 5 A A First Look at Embedded SystemsB Embedded Systems DesignPART 4 Process ControlUNIT 1 A A Process Control System 50B Fundamentals of Process Control 52UNIT 2 A Sensors and Transmitters 53B Final Control Elements and ControllersUNIT 3 A P Controllers and PI ControllersB PID Controllers and Other ControllersUNIT 4 A Indicating InstrumentsB Control PanelsPART 5 Control Based on Network and InformationUNIT 1 A Automation Networking Application AreasB Evolution of Control System ArchitectureUNIT 2 A Fundamental Issues in Networked Control SystemsB Stability of NCSs with Network-induced DelayUNIT 3 A Fundamentals of the Database SystemB Virtual Manufacturing—A Growing Trend in AutomationUNIT 4 A Concepts of Computer Integrated ManufacturingB Enterprise Resources Planning and BeyondPART 6 Synthetic Applications of Automatic TechnologyUNIT 1 A Recent Advances and Future Trends in Electrical Machine DriversB System Evolution in Intelligent BuildingsUNIT 2 A Industrial RobotB A General Introduction to Pattern RecognitionUNIT 3 A Renewable EnergyB Electric VehiclesUNIT 1A 电路电路或电网络由以某种方式连接的电阻器、电感器和电容器等元件组成。
小学下册I卷英语第3单元综合卷

小学下册英语第3单元综合卷英语试题一、综合题(本题有100小题,每小题1分,共100分.每小题不选、错误,均不给分)1.The __________ (气候研究) informs policy decisions.2. A raccoon is known for its black ________________ (面具).3.The plants need sunlight and _______ (植物需要阳光和_______).4.What is the name of the famous American singer known for her hit song "Rolling in the Deep"?A. AdeleB. Taylor SwiftC. BeyonceD. Mariah CareyA Adele5.The stars are ___ (shining) in the dark.6. A __________ is a substance that can conduct electricity when dissolved in water.7.We will go _____ the zoo tomorrow. (to)8. A _____ is made up of two or more different atoms bonded together.9.The _____ (生态恢复) aims to bring back native plants.10.What is the largest planet in our solar system?A. EarthB. MarsC. JupiterD. VenusC11.What is the largest mammal in the world?A. ElephantB. Blue WhaleC. GiraffeD. HippopotamusB12.She is studying to be a ________.13.What do we call the layer of gases surrounding the Earth?A. StratosphereB. AtmosphereC. HydrosphereD. LithosphereB14.I talk to my friends about ____.15.The fruit is ___. (fresh)16.We have ______ (很多) memories together.17.The ________ (experience) was unforgettable.18.What is the capital of South Africa?A. Cape TownB. PretoriaC. JohannesburgD. BloemfonteinB19.What fruit is yellow and curved?A. AppleB. OrangeC. BananaD. GrapeC20.The ________ was a famous treaty that ended World War II.21.How many players are on a baseball team?A. 9B. 10C. 11D. 1222.What do we call the people who study history?A. ScientistsB. HistoriansC. MathematiciansD. AuthorsB23.The ______ (果树) produces fruits in summer.24.The atomic model developed by Dalton was based on the idea that atoms are _______.25.What is the capital of Brazil?A. Rio de JaneiroB. BrasiliaC. Sao PauloD. Salvador26.The ______ is a vital part of agriculture.27.The chemical formula for aluminum chloride is _____.28.I took my ________ (玩具名称) on a trip.29. A __________ is formed by the melting of ice over time.30.The ancient Romans used _______ for their plumbing. (水管)31.The chemical formula for isopropanol is ______.32.He is reading a _______ (故事书).33.Planting native ______ (植物) supports local wildlife.34.I can reflect on my experiences with my ________ (玩具名称).35.What is the name of the famous American musician known for "Lose Yourself"?A. EminemB. Jay-ZC. Kanye WestD. 50 CentA36.What is the opposite of "young"?A. OldB. NewC. FreshD. Recent37.The first successful trachea transplant was performed in ________.38.We visit ______ (艺术馆) to see paintings.39.I need to _____ (buy/sell) groceries.40.What do you call a baby goat?A. KidB. LambC. CalfD. Foal41.The stars are ______ at night. (shining)42. A simple circuit includes a power source, a load, and ______ (wires).43.We celebrate ________ (success) as a group.44.What is the capital of Italy?A. LisbonB. RomeC. AthensD. Paris45.What is the name of the planets that have rings?A. Gas GiantsB. Rocky PlanetsC. Dwarf PlanetsD. Terrestrial Planets46.The teacher is in the ___. (classroom)47. A __________ is a measure of how acidic or basic a solution is.48.What is 7 4?A. 1B. 2C. 3D. 4C49. A _______ is a chemical change that produces heat.50.My uncle is a __________. (律师)51.The ________ was a popular form of entertainment in ancient Rome.52.In class, we learn about ________ and math.53.What is the capital of Niger?A. NiameyB. AgadezC. MaradiD. ZinderA54.My cousin is a great __________ (活动家).55.Which fruit is yellow and long?A. GrapeB. BananaC. AppleD. KiwiB56.My grandma loves to share her __________ (传统故事).57.She is _____ (singing) a song.58.The __________ (峡谷) is deep and wide.59.An octopus can change its ________________ (颜色).60.I found a ________ under the couch.61.The main product of cellular respiration is ______.62. A hermit crab finds a ______ (壳) to live in.63.What is the capital of Italy?A. RomeB. FlorenceC. VeniceD. Milan64.I have a toy _______ that can change its face.65.The ancient Romans were known for their ________ (军事战略).66.What type of animal is a salmon?A. MammalB. ReptileC. BirdD. FishD67.The concept of ecological networks focuses on the connections between ______ and their habitats.68.I like to _______ (给朋友写信) during the holidays.69.I like to watch the __________ change colors in the fall. (树叶)70.What is the name of the famous Roman gladiator?A. SpartacusB. MaximusC. CaesarD. Nero71.I love ________ with my family.72. A saturated solution can be created by heating a ______.73.The first human-made object to land on the moon was _______.74.The ________ (star) twinkles at night.75.I like visiting historical ________ (遗址) to learn more about my country’s past.76.The _____ (手链) is shiny.77.What is 5 + 5?A. 9B. 10C. 11D. 1278.__________ can change their state with temperature and pressure changes.79.The _____ (落叶) creates a beautiful scene in autumn.80.are small _________ (鸟). Spring i81.What do we call the place where animals are kept for public viewing?A. ZooB. AquariumC. FarmD. JungleA82. A ______ is a representation of a scientific relationship.83.What do we call the solid part of the Earth?A. AtmosphereB. HydrosphereC. LithosphereD. BiosphereC84.He can _____ a bicycle. (ride/sing/run)85.The _______ of an object can be calculated by measuring its volume.86.The __________ (历史的探讨) encourages open dialogue.87.What is the capital of Italy?A. AthensB. MadridC. RomeD. Paris88.The ________ (果蔬种植) is rewarding.89.What do we call the outer layer of the Earth?A. MantleB. CoreC. CrustD. AtmosphereC90.The farmer, ______ (农民), grows vegetables and fruits.91.The _____ (细胞) in leaves help with photosynthesis.92.The __________ (历史的教育意义) shapes future leaders.93.Who is famous for saying "I have a dream"?A. Albert EinsteinB. Martin Luther King Jr.C. Abraham LincolnD. Nelson MandelaB94.The _____ (香味) of lavender is calming.95.I love spending time outdoors, especially at the __________.96.What is the main ingredient in pizza?A. RiceB. BreadC. PastaD. Corn97.The ________ (传统习俗) are celebrated yearly.98.I think that friendships are built on __________.99. A _______ is an area of land that is lower than the surrounding land. 100.What do you call a group of stars?A. PlanetB. GalaxyC. UniverseD. Solar systemB。
Juniper Networks ISG Series 产品介绍说明书

demands dictated by various government regulations such as SarbanesOxley and GLBA, the ISG Series delivers the most advanced set of network segmentation features including Virtual Systems, Security Zones, Virtual Routers and VLANs.
Network friendly: Support for key routing protocols, such as OSPF, RIPv2, and BGP, along with transparent Layer 2 operation, NAT and Route mode help facilitate network integration. To satisfy complex internal network segmentation
ISG 2000:
The ISG 2000 is a fully integrated FW/VPN/IDP system with multi-gigabit performance, a modular architecture and rich virtualization capabilities. The base FW/VPN system allows for up to four I/O modules and three security modules for IDP integration. The ISG 2000 can be upgraded to support GPRS (General Packet Radio Service) to provide stateful firewalling and filtering capabilities and to protect key nodes like the SGSN and the GGSN in the mobile operators’ network.
英语移动支付安全演讲稿(3篇)

第1篇Ladies and Gentlemen,Good morning/afternoon/evening. It is my great pleasure to stand before you today to discuss a topic that has become an integral part of our daily lives: mobile payment security. With the rapid advancement of technology, mobile payment has transformed the way we conduct financial transactions, making it faster, more convenient, and more accessible than ever before. However, as with any innovation, it comes with its own set of challenges, especially when it comes to security. In this speech, I will delve into the importance of mobile payment security, the potential risks involved, and the steps we can take to ensure a safe and secure digital wallet.The Rise of Mobile PaymentOver the past decade, mobile payment has seen exponential growth. According to a report by Statista, the global mobile payment transaction value is projected to reach approximately 5.3 trillion U.S. dollars by 2025. This trend is primarily driven by the increasing adoption of smartphones, the convenience of mobile payment solutions, and the integration of digital payment options into various aspects of our lives.The Importance of Mobile Payment SecurityWith such a significant shift towards mobile payment, it is crucial to emphasize the importance of security. Here are a few key reasons why mobile payment security is paramount:1. Financial Protection: Mobile payment involves transferring funds from one account to another. If your payment information is compromised, it can lead to financial loss, identity theft, and other fraudulent activities.2. Privacy Concerns: Mobile payment requires sharing sensitive personal information, such as bank account details and credit card numbers. Ensuring this information is secure is essential to protect your privacy.3. Consumer Trust: A secure mobile payment ecosystem is essential for building consumer trust. If users feel their transactions are not safe, they are less likely to adopt mobile payment solutions, which can hinder the growth of this industry.Potential Risks in Mobile PaymentDespite the numerous benefits, mobile payment is not without its risks. Here are some of the potential threats:1. Phishing Attacks: Cybercriminals often use phishing techniques to trick users into providing their sensitive information. This can be done through fraudulent websites, emails, or messages that mimic legitimate mobile payment platforms.2. Malware: Malware, such as viruses and trojans, can be used to steal your personal and payment information. This can happen when you download malicious apps or click on suspicious links.3. Insufficient Authentication: Weak authentication methods, such as using only a PIN or password, can make it easier for attackers to gain unauthorized access to your mobile payment account.4. Network Vulnerabilities: Public Wi-Fi networks and other unsecured connections can be exploited by hackers to intercept your payment information.Steps to Ensure Mobile Payment SecurityTo protect yourself and your digital wallet, here are some essential steps to follow:1. Use Secure Payment Platforms: Always opt for reputable and secure mobile payment platforms that offer robust security features.2. Keep Your Device Updated: Regularly update your smartphone's operating system and apps to ensure you have the latest security patches.3. Install Antivirus Software: Use reliable antivirus software to detect and prevent malware infections.4. Enable Two-Factor Authentication: Whenever possible, enable two-factor authentication (2FA) to add an extra layer of security to your mobile payment account.5. Be Wary of Public Wi-Fi: Avoid conducting sensitive transactions over public Wi-Fi networks. If you must use them, ensure your connection is encrypted.6. Monitor Your Accounts: Regularly check your bank and credit card statements for any unauthorized transactions and report them immediately.7. Educate Yourself: Stay informed about the latest mobile payment security threats and best practices.ConclusionIn conclusion, mobile payment has revolutionized the way we conduct financial transactions, offering convenience and efficiency. However, it is crucial to remain vigilant about security to protect your digital wallet. By following the steps outlined in this speech, you can minimize the risks associated with mobile payment and enjoy the benefits itoffers with peace of mind.Thank you for your attention, and I hope this speech has provided you with valuable insights into mobile payment security. Remember, a secure digital wallet is a smart digital wallet.第2篇Ladies and Gentlemen,Good morning/afternoon/evening. It is my great pleasure to stand before you today to discuss a topic that has become an integral part of ourdaily lives – mobile payment security. With the rapid advancement of technology, mobile payment has revolutionized the way we conductfinancial transactions. However, this convenience comes with its own set of challenges, particularly in ensuring the security of our transactions. In this speech, I will explore the importance of mobile payment security, the common threats we face, and the measures we can take to safeguardour financial information.I. The Importance of Mobile Payment SecurityA. Convenience and EfficiencyMobile payment allows us to perform transactions quickly and conveniently, without the need for cash or credit cards. This has led to a significant increase in the adoption of mobile payment solutions worldwide.B. Cost ReductionBy reducing the need for physical cash and reducing the risk of credit card fraud, mobile payment can help individuals and businesses save money in the long run.C. Enhanced Financial InclusionMobile payment solutions have the potential to bring financial services to underserved populations, especially in developing countries, by providing them with access to basic banking services.II. Common Threats to Mobile Payment SecurityA. Phishing AttacksPhishing attacks are one of the most common threats to mobile payment security. Cybercriminals send fraudulent emails or messages, tricking users into providing their personal and financial information.B. MalwareMalware, such as viruses, spyware, and trojans, can infect a user's mobile device, steal sensitive information, and intercept financial transactions.C. Man-in-the-Middle AttacksIn a man-in-the-middle attack, cybercriminals intercept and alter communications between two parties, including financial transactions, to steal sensitive information.D. Social EngineeringSocial engineering involves manipulating individuals into providing sensitive information or performing actions that compromise their security.III. Measures to Ensure Mobile Payment SecurityA. Use Secure Payment AppsWhen selecting a mobile payment app, choose one that is reputable, has a strong security track record, and offers features such as two-factor authentication.B. Keep Your Device SecureRegularly update your mobile device's operating system and antivirus software to protect against malware. Also, use strong passwords and biometric authentication methods to secure your device.C. Be Wary of Phishing AttemptsNever provide your personal or financial information in response to unsolicited emails or messages. Always verify the sender's identity before taking any action.D. Use Secure Wi-Fi NetworksAvoid conducting financial transactions on public Wi-Fi networks, as they are more susceptible to hacking. If you must use public Wi-Fi, use a virtual private network (VPN) to encrypt your data.E. Monitor Your Accounts RegularlyKeep a close eye on your bank and credit card statements for any unauthorized transactions. Report any suspicious activity immediately to your financial institution.F. Educate Yourself and OthersStay informed about the latest mobile payment security threats and educate your friends, family, and colleagues about best practices for protecting their financial information.IV. The Role of Financial InstitutionsA. Implement Strong Security MeasuresFinancial institutions must invest in robust security measures toprotect their customers' financial information, including encryption, firewalls, and intrusion detection systems.B. Educate CustomersFinancial institutions should provide their customers with comprehensive education on mobile payment security, including best practices and common threats.C. Offer Fraud ProtectionFinancial institutions should offer fraud protection services, such as zero liability policies, to cover customers in the event of unauthorized transactions.V. ConclusionIn conclusion, mobile payment security is a critical concern in today's digital age. As we continue to embrace the convenience and efficiency of mobile payment solutions, it is essential to remain vigilant about the security of our financial information. By taking proactive measures to protect our devices, being aware of common threats, and educating ourselves and others, we can enjoy the benefits of mobile payment while minimizing the risks.Thank you for your attention. I hope this speech has provided you with valuable insights into the importance of mobile payment security and the steps we can take to ensure a safe and secure financial future.第3篇Ladies and gentlemen,Good morning/afternoon/evening. It is my great pleasure to stand before you today to discuss a topic that has become increasingly important in our modern, digital world: the safety of mobile payments. With the rapiddevelopment of technology, mobile payment has become an integral part of our daily lives, allowing us to make purchases, transfer money, and pay bills with just a few taps on our smartphones. However, along with the convenience, there are also significant security risks that we need to be aware of and address.Firstly, let's take a look at the current state of mobile payment. According to a report by Statista, the global mobile payment transaction value is expected to reach $4.9 trillion by 2025. This indicates that mobile payment is not only a popular choice for consumers but also a lucrative market for businesses. In China, mobile payment has been a game-changer, with Alipay and WeChat Pay accounting for a significant share of the market. This success has prompted other countries to explore and implement their own mobile payment systems.Despite the convenience and popularity of mobile payment, it is crucial to recognize the potential security risks. Here are some of the common threats:1. Phishing attacks: Cybercriminals may send fraudulent emails or messages, tricking users into providing their sensitive information, such as login credentials or bank account details.2. Malware: Malicious software can be installed on your device, allowing hackers to access your personal data and financial information.3. Unauthorised access: If your device is lost or stolen, an unauthorised person can gain access to your mobile payment accounts and misuse them.4. Data breaches: Hackers may attempt to steal sensitive data, such as credit card numbers, from mobile payment systems or merchants.To address these risks, we need to take several security measures:1. Strong passwords: Set a strong, unique password for your mobile payment accounts and avoid using the same password for multiple accounts.2. Two-factor authentication (2FA): Enable 2FA on your mobile payment accounts, which adds an extra layer of security by requiring a second form of verification, such as a one-time password sent to your phone.3. Keep your device secure: Install a reputable antivirus software on your device, update your operating system and apps regularly, and avoid downloading apps from untrusted sources.4. Be cautious of public Wi-Fi: Avoid using public Wi-Fi networks for sensitive transactions, as they can be easily intercepted by hackers.5. Monitor your accounts: Regularly check your mobile payment accounts for any unusual activity and report any suspicious transactions to your bank or payment provider immediately.6. Use secure payment methods: Some mobile payment systems offer additional security features, such as biometric authentication (fingerprint or facial recognition) or tokenisation, which can help protect your financial information.7. Educate yourself: Stay informed about the latest mobile payment security threats and best practices to protect yourself.In conclusion, mobile payment has revolutionised the way we conduct financial transactions, offering convenience and efficiency. However, we must not overlook the security risks associated with this technology. By implementing these security measures and staying vigilant, we can enjoy the benefits of mobile payment while minimising the risks.Ladies and gentlemen, as we continue to embrace the digital era, it is our responsibility to ensure that mobile payment remains a safe and secure option for everyone. Let us work together to create a safer and more secure mobile payment environment for the future.Thank you for your attention.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Spanning Tree Example
LAN Switch Types
Cut-through / FastForward
FragmentFree / Modified cut-through Store-and-forward
Note:
A router is a three-layer (physical, data link, and network) device.
Note:
A routeБайду номын сангаас changes the physical addresses in a packet.
(又稱為位元組導向協定) 訊框或封包被解釋為一系列的 字元。所有控制資訊都是以既 有的字元編碼系統(如ASCII)型 式表示。 如:二元同步通訊(BSC)
訊框或封包被解釋為一系列的位 元。沒有事先存在的編碼系統, 控制資訊可以是單一或多個位元 (與資訊在樣本的中的展現有關) 如:高階資料鏈結控制(HDLC) ……
Forward/Filter Decisions
Loop Avoidance
Spanning Tree Protocol (STP)
STP is a layer 2 protocol that is used to
maintain a loop-free switched network STP (DEC) 802.1D (IEEE)
Note:
A repeater or a bridge connects segments of a LAN. A router connects independent LANs or WANs to create an internetwork (internet).
Figure 3.33
Routing example
