专业英语大作业
专业英语大作业2

Information on Power SuppliesThere are many types of electrical and electronic power supplies, providing various alternating current (AC) and direct current (DC) voltages for equipment operation.DC voltages are needed for most electronic circuits, and generally an electronic power supply is considered as a device that converts AC into DC. The AC voltage from the power lines can be rectified directly or passed through an isolation transformer ( a turn's ratio of 1:1). Depending on the value of DC voltage needed, the transformer may be of either a step-up or step-down type.After the transformer, the AC is rectified into pulsating DC by diodes in the form of a half-wave rectifier, a full-wave rectifier, or a bridge (full-wave) rectifier The pulsating DC is then filtered or smoothed out by capacitors, inductors, and resistors so as to produce a constant DC output.Bridge (Full-wave) RectifierThe bridge rectifier produces a full-wave DC output with the use of four diodes (Fig 5.1). When the positive half-cycle appears, the anode of diode 1 is positive and it conducts, and the cathode of diode 2 is negative and it conducts.Current flows from the AC source through diode 1, through R L,through diode 2, and back to the source. Diodes 3 and 4 are reversed biased and no current flows through them. They appear as open circuits. On the negative half-cycle the anode of diode 4 is positive and it conducts, and the cathode of diode 3 is negative and it conducts. Current flows from the AC source through diode 4, through RL, through diode 3, and back to the source. Diodes 1 and 2 are reverse.V oltage output Uo is the peak voltage less two times the UF across the diodes ( two diodes are conducting at a time): Full-wave bridge rectifier modules containing four diodes in a single unit are commercially available.Fpeak o U U U 2-=。
专业英语作业4.doc

MetalsMan fist began using metals at least 5000 years ago. He found that they could be hammered into tools and weapons that remained sharp. From small beginnings the use of metals has brown to such an extent that civilization as we know it today could not exist with them.Metals make up a large part of the earth's outer layer, or crust. But only a few of them appear in the metal form we are familiar with. Most metals, such as iron and tin, are found combined with other chemical elements. Most of these compounds do not look anything like metals. They are often lumps of rocks. But many of them can be treated to produce metals. These are called ores.Not many metals are used widely in their pure state. Other metals are usually added to them to form mixtures called alloys. Sometimes chemical elements other than metals are included in alloys. The most important is carbon. In engineering, metals and alloys are usually called metals. Metals are divided into tow groups, the ferrous, which contain a large percentage of iron, and the nonferrous, which contain no iron.Steel, our most useful metals is alloy of iron and carbon. Because of its strength, steel is used in large buildings and bridges. It is also used to make motor cars, railways and ships. Most of the machinery that makes practically everything we use is made of iron or steel.Many other metals are important to us, too. The spoons, knives and forks we eat with are made of stainless steel. We cook in aluminum boilers. Copper cables carry electricity to factories and families. The coins we carry in our pockets contain copper, nickel, and zinc. The list of the uses of metals is endless.Pure iron is quite a weak metal, and it is not very hard, either. But add a little carbon as well as traces of certain other metals, and it becomes both strong and hard. According to what is added, the iron can be given other desirable properties as well. Adding other substances to a metal to change its properties is called alloying, and the product an alloy.Most of the alloys of iron are better known to us as steels. Many other metals form useful alloys, too. Brass and bronze are common alloys of copper. Solder is a well-known lead alloy. Aluminum and zinc alloys are also in widespread use. However, it is the iron alloys that are by far the most important.The pig iron that is made in the blast furnace can be considered one kind of iron alloy, but it is a very crude one. It contains far too many impurities and other materials as well as being uneven in composition. By only slight refining , it can be made into cast iron. Cast iron is an ideal material formaking engine blocks and machine frames. It is strong, hard, rigid, and absorbs shock well. Its main disadvantage is that it is brittle.Wrought iron is a more refined form of pig iron which is quite pure iron (0.1 〜0.2 per cent carbon) with threads of slag running through it. Wrought iron is made by heating the pig iron with iron oxide in a “puddling" furnace. The oxygen in the oxide combines with the impurities, which either boil away as gas or form a slag. But the temperature of the furnace is not high enough to make the metal melt. That is why it contains threads of slag. Wrought iron is seldom used directly in industry.Refining pig iron in the various steelmaking furnaces reduces the carbon content and removes other unwanted substance. The steel-maker stops the refining process when the metal has reached the carbon content he wants. Then he adds controlled amounts of other elements to bring the steel to the desired composition.There are two principal kinds of steels, carbon steels and alloy steels. The properties of carbon steels depend mainly on the amount of carbon present. Mild steel (up to 0.25 per cent carbon) is the ordinary kind of steel that is used for girders, automobile bodies, bicycle frames, and so on. Medium-carbon steel (0.25〜0.45 per cent) is stronger than mild steel and is used for bridge members, nuts and bolts, and tools of many kinds. High-carbon steel (0.45〜1.5 per cent) is hard and tough, and is used for cutting tools, drill bits, saws, and so on.The properties of alloy steels depend not on the carbon they contain, but on other alloying elements. One of the most familiar alloys is stainless steel. As we all know, ordinary steel corrodes, or rusts if it is left out in the rain, is stained by fruit juices, and so on. But adding chromium and nickel to steel makes it resist corrosion and stains. Both chromium and nickel resist corrosion well, and they tend to impart that property to their alloys. One of the most common kinds of stainless steels contains about 18 percent chromium and 8 percent nickel.Exercises1.Mark the following sentences with T(true) of F(false) according to the article.(1)The civilization could exist without metals.(2)Many metals appear in the metal form we are familiar with.(3)Only a few of metal are used in their pure state.(4)Metal mixtures are called alloys.(5)Carbon is the most important element to form alloy.(6)Solder is a well-known iron alloy.(7)The pig iron is a kind of iron alloy.(8)Iron alloys are the most important alloys in engineering.(9)Most engine blocks and machine frames are made of cast iron.(10)Wrought iron can be used directly in industry.(11)The properties of alloy steels depend mainly on the amount of carbon present.(12)Carbon steels and alloy steels are two main kinds of steels.(13)Cutting tools and drill bits are made of medium-carbon steel.2.Answer the following questions according to the article・(1)When did man first begin using metals?(2)How many groups of metals? What are they?(3)What kind of metal is most useful in engineering?(4)Is steel an alloy? What is it made from?(5)Please list the usages of iron and steel in daily life.3.Translate the following sentences into Chines・(1)In the old days, man found that metals could be hammered into tools and weapons that remainedsharp.(2)Most metals, such as iron and tin, are found combined with other chemical elements.(3)Other metals are usually added to pure metals to form mixtures called alloys.(4)Metals are divided into two groups, the ferrous, which contain a large percentage of iron, and thenonferrous, which contain no iron.(5)Most of the machinery that makes practically everything we use is made of iron or steel.4.Fill in the blanks with the words or expressions given below and change the forms wherenecessary.Corrosion, contain, element, stain, property, corrode, depend, leave, alloy, add The properties of alloy steels (1) not on the carbon they contain, but on other alloying (2) . One of the most familiar (3) is stainless steel. As we all know, ordinary steel(4) , or rusts if it (5) out in the rain, (6) by fruit juices, and so on but (7)chromium and nickel to steel makes it resist (8) and stains. Both chromium and nickel resist corrosion well, and they tend to impart (9) to their alloys. One of the most common kinds of stainlesssteels (10) about 18 percent chromium and 8 per cent nickel.。
专业英语大作业优选10篇(英文原文)

杜孟远PILOTING THE SMART GRIDAhmad Faruqui, Ryan Hledik and Sanem Sergici1The transformative power of the smart grid is enormous. It is receiving much consideration frutilities and commissions across North America. Several members of the European UniChina, Japan and other nations are also engaged in the same endeavor.The smart grid has the potential for revolutionizing the way we produce and consume electric but because it contains so many new elements; its core value proposition remains untested.The unanswered questions include:What new services will the smart grid provide customers?Do customers want these new services?Will they respond by changing their energy use patterns?The answers to these questions will help policymakers in federal and state government determine whether the benefits of the smart grid will cover its costs.It is widely understood that the new services enabled by the smart grid will include different rate designs that encourage curtailment of peak loads and make more efficient use of energy. Examples include dynamic pricing and inclining block rates.2These innovative rate designs will be enhanced by various automating technologies such as Energy Orbs, programmable communicating thermostats (PCTs), whole building energy management systems (Auto DR), and in-home displays (IHDs).The smart grid will of course go beyond smart meters and rate design and enable renewable energy resources to be connected to the grid. This will allow optimal use of intermittent resources, such as wind, which often reach their peak generating capacity during off-peak hours. New off-peak loads, such as plug-in hybrid electric vehicles, which reduce overall energy consumption and improve the carbon footprint, will be energized by the smart grid.To address the likely impact of the smart grid on customers, utilities, and society as a whole, it may be necessary to conduct a pilot. When should a pilot be conducted and how should it be conducted? To be useful, a pilot must yield credible results. This requires that the pilot satisfy various validity criteria. These issues form the focus of this paper. We provide examples from several recent pilots that involved dynamic pricing, a key element of the smart gird. The concluding section discusses how a hypothetical company, SMART POWER, should go about designing its own pilot. Should a Pilot be Conducted?3Policymakers should consider implementing a pilot if there is much uncertainty in the cost-benefit analysis of proceeding with full-scale deployment. A powerful method for resolving uncertainty is to assess the value of information that would be generated from a pilot. This point is best illustrated with a case study.California suffered the worst energy crisis in its history in 2001. Most analysts attributed the crisis in part to the lack of demand response in the market design. When prices rose in wholesale markets, there was no incentive for retail customers to lower demand. In the summer of 2002, the California Public Utilities Commission initiated proceedings on demand response, advanced metering, and dynamic pricing. Early in the proceedings, it became clear that the decision to deploy advanced metering was fraught with risk. The deployment would be costly and the benefits uncertain, as they depended on the customers’ price elasticity of demand.龚畅Electricity from the Oceans: Will It Really HappenAnytime Soon?By Doug PeeplesSGN News EditorGovernments and private industry have been casting a wide net to find alternative sources of sustainable power to meet accelerating demand and reduce greenhouse gas emissions. And electric power from ocean waves, tides and currents has been getting a lot more attention —and money — than ever before.But what are the chances that marine and hydrokinetic technologies (let's just call it ocean power to keep it short and sweet) are really going to take their place alongside more mature and relatively well-funded renewable energy sources such as wind and solar to feed the need for more greener power?We can't answer that question to a certainty, but we can round up a lot of the big issues: What's good about it, what's bad and what needs to happen to make ocean power a reality?The Good∙Oceans cover about 70% of the planet, and waves and tides offer a more predictable, reliable source of energy than wind and solar. And energy storage isn't an issue. The oceans are always on.∙ A British company built a large-scale tidal turbine in 2008 that's since been getting good reviews, and several countries have jumped onto the ocean power bandwagon.Globally, according to Pike Research, there are more than 300 ocean power projects"in the works." A New Jersey company has big plans for a pilot buoy project off theOregon coast and much bigger plans for a commercial-scale wave project there.∙ A January report from Pike said ocean power could generate 200 GW of electricity by 2025. A new analysis from Frost & Sullivan pegs global resources at more like2,000 to 4,000 TWh annually. The Frost & Sullivan analysis also anticipates thecommercialization of ocean power within the next 5-10 years as technology improves and production costs drop.∙In the U.S., attitudes of the federal government and private industry are taking a positive tack, too. The DOE and the Interior Department in June signed amemorandum of understanding to collaborate on commercial-scale development of offshore renewable energy projects, including wave power. The DOE has pouredmillions of dollars into hydrokinetic R&D and has put the technological and strategic muscle of its national laboratories behind it.The Bad∙Ocean power is still in the proof-of-concept phase, and initial deployments require unimaginably massive investments. Will investors bet on technologies with nosignificant track record and sky high upfront costs?∙While wave power is more reliable than wind and solar, the actual power in waves fluctuates a lot, as does the state of the oceans in general. Durability is a big issue.Pelamis Wave Power, which operated a highly regarded commercial-scale wave farm in Portugal, shut down its operations last year because of persistent technicalproblems and dwindling financing.∙How will regulations to protect aquatic ecosystems and fisheries evolve? The permitting and siting process for land-based renewable energy projects is complicated enough. The marine environment is more complex, so it seems reasonable thatpermitting and siting for ocean projects will be even more complicated.∙Standardizing technologies, connecting wave power to the electric grid and transmission also present obstacles.That Said, What's It All Mean?Who wouldn’t want to see a new, reliable, secure and green energy source? But even the most optimistic reports and analyses come with heavy disclaimers, most of them pointing at exceptionally high upfront costs and technological nightmares similar to those facing the new deepwater wind farm sector. While the future of ocean power looks a little brighter, it still looks like a long slog to the light at the end of the tunnel.What do YOU think? Will be generating significant amounts of electricity from ocean waves anytime soon ... if ever?甘凯元Radioactive Water Leaking From Crippled Japan Plantby The Associated PressWorkers spray resin on the ground near the reactor buildings to prevent the spread of radioactive substances at the Fukushima Dai-ichi nuclear power plant.April 2, 2011Highly radioactive water was leaking into the sea Saturday from a crack discovered at a nuclear power plant destabilized by last month's earthquake and tsunami, a new setback as frustrated survivors of the disasters complained that Japan's government was paying too much attention to the nuclear crisis.The contaminated water will quickly dissipate into the sea and is not expected to cause any health hazard. Nevertheless, the disturbing discovery points at the unexpected problems that can crop up and continue to hamper technicians trying to control the crisis.Word of the leak came as Prime Minister Naoto Kan toured the town of Rikuzentakata, his first trip to survey damage in one of the dozens of villages, towns and cities slammed by the March 11 tsunami that followed a magnitude 9.0 earthquake."The government has been too focused on the Fukushima power plant rather than the tsunami victims. Both deserve attention," said 35-year-old Megumi Shimanuki, who was visiting her family at a community center converted into a shelter in hard-hit Natori, about 100 miles from Rikuzentakata.The double disaster is believed to have left nearly 25,000 dead — 11,800 confirmed. More than 165,000 are still living in shelters, and tens of thousands more still do not have electricity or running water.Although the government had rushed to provide relief, its attention has been divided by the efforts to stabilize the Fukushima Dai-ichi nuclear plant, which suffered heavy damage and has dragged the country to its worst nuclear crisis since the atomic bombings of Hiroshima and Nagasaki during World War II.The plant's reactors overheated to dangerous levels after electrical pumps — deprived of electricity — failed to circulate water to keep the reactors cool. A series of almost daily problems have led to substantial amount of radiation leaking in the atmosphere, ground and sea.On Saturday, workers discovered an 8-inch long crack in a maintenance pit that was leaking highly radioactive water into the Pacific Ocean, said Japan Nuclear and Industrial Safety Agency spokesman Hidehiko Nishiyama.He said the water contaminated with levels of radioactive iodine far above the legal limit found inside the pit could be one of the sources of recent spikes in radioactivity in sea water."There could be other similar cracks in the area, and we must find them as quickly as possible," he told reporters.Soon after the discovery, the plant's operator, Tokyo Electric Power Co., started filling the pit with cement to seal the crack and prevent more contaminated water from seeping into the ocean.Nuclear safety officials said the crack was likely caused by the quake and may be the source of radioactive iodine that started showing up in the ocean more than a week ago.People living within 12 miles of the plant have been evacuated and the radioactive water will quickly dissipate in the sea, but it was unclear if the leak posed any new danger to workers. People have been uneasy about seafood from the area despite official reassurances that the risk of contamination is low.The cracked pit houses cables for one of the six nuclear reactors, and the concentration of radioactive iodine was the same as in a puddle of contaminated water found outside the reactor earlier in the week. Because of that, officials believe the contaminated water is coming from the same place, though they are not sure where.A nuclear plant worker who fell into the ocean Friday while trying to board a barge carrying water to help cool the plant did not show any immediate signs of being exposed to unsafe levels of radiation, nuclear safety officials said Saturday, but they were waiting for test results to be sure.Radiation worries have compounded the misery for people trying to recover from the tsunami. Kan's visit Saturday to Rikuzentakata did little to alleviate their worries."The government fully supports you until the end," Kan told 250 people at an elementary school serving as an evacuation center. He earlier met with the mayor, whose 38-year-old wife was swept away.He bowed his head for a moment of silence in front of the town hall, one of the few buildings still standing, though its windows are blown out and metal and debris sit tangled out front.Kan also stopped at the sports complex being used as a base camp for nuclear plant workers, who have been hailed as heroes for laboring in dangerous conditions. He had visited the nuclear crisis zone once before, soon after the quake.Workers have been reluctant to talk to the media about what they are experiencing, but one who spent several days at the plant described difficult conditions in an anonymous interview published Saturday in the national Mainichi newspaper.When he was called in mid-March to help restore power at the plant, he said he did not tell his family because he did not want them to worry. But he did tell a friend to notify his parents if he did not return in two weeks."I feel very strongly that there is nobody but us to do this job, and we cannot go home until we finish the work," he said.Early on, the company ran out of full radiation suits, forcing workers to create improvised versions of items such as nylon booties they were supposed to pull over their shoes."But we only put something like plastic garbage bags you can buy at a convenience store and sealed them with masking tape," he said.He said the tsunami littered the area around the plant with dead fish and sharks, and the quake opened holes in the ground that tripped up some workers who could not see through large gas masks. They had to yell at one another to be heard through the masks."It's hard to move while wearing a gas mask," he said. "While working, the gas mask came off several times. Maybe I must have inhaled much radiation."Radiation is also a concern for people living around the plant. In the city of Koriyama, Tadashi and Ritsuko Yanai and their 1-month-old baby have spent the past three weeks in a sports arena converted into a shelter. Baby Kaon, born a week before the quake, has grown accustomed to life there, including frequent radiation screenings, but his parents have not. Their home is fine, but they had to leave because it is six miles from the nuclear plant.Asked if he had anything he would like to say to the prime minister, Tadashi, a32-year-old father, paused to think and then replied: "We want to go home. That's all, we just want to go home."In Natori, where about 1,700 people are living in shelters, others had stronger words for Kan. Toru Sato, 57, lost both his wife and his house in the tsunami and said he was bothered that Kan's visit to the quake zone was so brief about a half day."He's just showing up for an appearance," Sato said. "He should spend time to talk to various people, and listen to what they need."黄松强AEP, ITC Transmission to perform technical study on expanding 765-kV transmission into MichiganCOLUMBUS, Ohio, Nov. 6, 2006 – American Electric Power (NYSE: AEP) has signed a memorandum of understanding (MOU) with ITC Transmission, a subsidiary of ITC Holdings Corp. (ITC), to perform a technical study to evaluate the feasibilityof extending AEP’s 765-kilovolt (kV) transmission infrastructure through Michigan to enhance reliability and support a competitive market of generation supply.The study will explore the merit and benefits of building a 765-kV transmission network in Michigan’s Lower Peninsula that would link to AEP’s 765-kV transmission system in the Midwest. The study will be shared with the Midwest ISO (MISO) and the Michigan Public Servic e Commission’s (MPSC) 21st Century Energy Planning team.The study is projected to be complete in late 2006, in time for it to be shared with the MPSC 21st Century Planning team before they complete their deliberations. The MOU signed with ITC Transmission does not include provisions to build or operate transmission. Any future activities regarding Michigan transmission will be determined after the completion of the study.―Through this agreement, we will work with ITC Transmission to determine the benefits of enhancing the Michigan transmission grid by introducing 765-kV lines, the most robust transmission in the U.S., and linking it to AEP’s 2,100-mile 765-kV transmission network in the Midwest. After the completion of the study, we will provide our analysis to the Michigan Public Service Commission, Midwest ISO and other parties to help them determine the best way to serve Michigan’s future electric reliability needs and support a successful competitive marketplace,‖ said Michael G. Morris, AEP’s chairm an, president and chief executive officer.―ITC Transmission continues in its mission to invest in the transmission infrastructure as a means to improve electric reliability for its customers and lower the overall cost of delivered energy,‖ said Joseph L. Welch, president and chief executive officer of ITC Transmission. ―The transmission grid in Michigan has suffered after a 30-year trend of underinvestment, and we must begin actively looking to implement a long-term solution that will address Michigan’s current electric reliability needs now and for years to come.‖―ITC Transmission, a subsidiary of ITC Holdings Corp. (NYSE: ITC), is the first independently-owned and operated electricity transmission company in the United States. ITC Holdings Corp. is in the business of investing in electricity transmission infrastructure improvements as a means to improve electric reliability, reduce congestion and lower the overall cost of delivered energy. Through its operating subsidiaries, ITC Transmission and METC, it is the only publicly traded company engaged exclusively in the transmission of electricity in the United States. ITC is also the largest independent electric transmission company and the tenth largest electric transmission company in the country based on transmission load served. ITC Transmission and METC operate contiguous, fully regulated, high-voltage systems in Michigan´s Lower Peninsula, an area with a population of approximately 9.8 million people, that transmit electricity to local electricity distribution facilities fromgenerating stations throughout Michigan and surrounding areas. For more information on ITC Holdings Corp., please visit . For more information on ITC Transmission or METC, please visit or , respectively.American Electric Power is one of the largest electric utilities in the United States, delivering electricity to more than 5 million customers in 11 states. AEP ranks among the nation’s largest generators of electricity, owning nearly 36,000 megawatts of generating capacity in the U.S. AEP also owns the nation’s largest electricity transmission system, a nearly 39,000-mile network that includes more 765 kilovolt extra-high voltage transmission lines than all other U.S. transmission systems combined. AEP’s utility units operate as AEP Ohio, AEP Texas, Appalachian Power (in Virginia and West Virginia), AEP Appalachian Power (in Tennessee), Indiana Michigan Power, Kentucky Power, Public Service Company of Oklahoma, and Southwestern Electric Power Company (in Arkansas, Louisiana and east Texas). American Electric Power, based in Columbus, Ohio, is celebrating its 100th anniversary in 2006.杨萌Siemens Residential Surge Protection —Implementing the Right Line of Defense on the Home FrontUnexpected voltage spikes, surges and other electrical disturbances can ruin or severely damage computers, VCRs, televisions, fax machines, scanners and copiers, disrupt satellite signals, degrade the performance of audio/video components, and wreak havoc with telecommunications systems.Because no single device can protect an entire home or office against all electrical surges, the best way to prevent damage is by implementing a systematic, tiered surge protection plan that monitors every possible incoming signal path and protects against internally generated power fluctuations, providing protection at the service entrance and at the point of use.Protection at the point of entryThe first line of defense is protection at the point of entry where electricity,surges and voltage spikes from lightning hits can enter the electrical system. This requires an electrician-installed secondary surge arrestor or transient voltage surge suppressor installed at the service entrance to limit surge voltage by diverting and conducting large surge currents safely to ground. If an AC surge arrestor does its job right, it shields motor-driven appliances like refrigerators, dishwashers, electric washers, and dryers from damage. Additional specialized service entrance protectors can be added to protect cable TV and telephone lines, and minimize damage to TVs and modems. Homeowners also can arrange for installation of branch circuit feeder devices or trips in circuit breaker panels to prevent surges from damaging equipment on specific circuit branches.Protection at the point of useThe second line of defense is the point of use. Here, homeowners can reinforce point-of-entry protection by installing plug-in surge protectors (strips) into grounded wall receptacles where sensitive electronic equipment is located. These plug-in protectors, which generally have much lower limiting voltages than entry protectors, defend against externally and internally generated surges that travel through power, phone, data, and coaxial lines. Plug-in power strips should minimally include AC power protection and appropriate signal line protection and should protect against both catastrophic and small surges. These devices should be installed wherever expensive or sensitive electronic equipment like computers, VCRs, fax machines, PCs with modems, satellite systems, stereo systems, copiers and scanners are located. All types of equipment with signal lines, such as phones, cable TV, and satellites should be equipped with multi-port protectors, which protect signal and AC lines.If you have any questions or are interested in purchasing our surge protection products, please contact us via e-mail or call 1-800-964-4114.胡嘉滨Energy Storage: Can It Replace Transmission?Grid-scale storage offers potential benefits to transmission and distribution systems of utilities in regulated and market environments. These benefits derive from cost reductions due to the time and location shifting of energy for congestion relief, reliability via enhanced stability and outage response, and incremental voltage support—once the storage device and its power electronics are in place. .Between the transmission and distribution systems, at the subtransmission or distribution substation, storage can defer capital expenditures for power transformer upgrades to meet peak load conditions. In remote areas served by radial subtransmission, storage can also be a vehicle for reliability improvement as a way to ride through un-cleared faults on the transmission line(s) that serve the substation.The potential T&D CapEx deferral angle is an interesting area to explore. One example for a substation application is to support power transformer contingency operations during peak load periods that have grown in excess of the N-1 contingency capacity of the station.This potential application, however, suffers from the same barriers today as the transmission congestion relief application:•The planning and operational methodologies are not established•The regulatory process for approval is nonexistent•It, again, crosses the boundary between transmission and distribution regulated functionality and merchant functionality, because it potentially shifts off-peak energy to on-peak delivery.In addition, as this typical substation application is likely to be in the range of 1-10 MW, it may not require centralized storage systems, but rather distributed or utility-scale devices. As previously noted, these could be portable or semi-portable in nature.One More Hurdle … For Now, At LeastAn additional hurdle that needs to be mentioned is costs. One reason multiple roles are applied to a storage device is for a means to create additional revenue that can defer initial cost for the technologies. However, this hurdle needs to be evaluated in the context of an emerging technology and not ―set‖ at current levels.Advanced energy storage technologies are still in a rapid state of evolution and development. Hence, when comparing options, solutions for areas such as CapEx deferral need to be weighed not only against today’s current options, but also with expected prices of future technologies. The intent isn’t to mask cost as a hurdle; rather, there are a number of diffe rent technologies nearing demonstration stages that have potential to alter the current cost of devices. This perceived ―cost‖ hurdle may become a moot point in the near future.Storage is not yet in widespread use to the point that it could serve as a consistent application to defer new transmission. As challenges of siting new transmission continue though, additional modeling of energy storage going forward can help to understand its benefits for a given capacity challenge better.梁诗密A secure energy future requires that we use energy more efficiently and responsibly and improve the performance of the energy delivery system. We launched gridSMART® in 2007 to give customers greater control over their energy usage, increase the efficiency of the electric grid, improve service to our customers and lead us to a new era of energy delivery.From a technology standpoint, gridSMART® incorporates a two-way communications system between AEP and our customers that facilitates the more efficient use of electricity. For example, gridSMART® may allow us to send price signals to customers so they can decide when to run home appliances. It can also allow us to adjust customer thermostats automatically, with their pre-approval, when demand is high and we need to lessen the stress on the electric grid.AEP Ohio is pursuing a comprehensive gridSMART® project involving 110,000 smart meters and distributed grid management technologies on 70 circuits. The $150 million project was funded with a $75 million grant from the DOE, in-kind contributions from vendors and regulatory recovery support from Ohio regulators. The project features smart meters,time-of-use tariffs, home energy use display devices, smart grid-enabled appliances, plug-in electric vehicles, distributed automation equipment, community energy storage devices and a cyber security center.Our most extensive smart meter deployment project is in Texas, where we are installing close to 1 million smart meters. In addition, Indiana Michigan Power Co. (I&M) and Public Service Company of Oklahoma (PSO) are deploying smart grid technology pilots in their states.Our initial goal was to install 5 million smart meters by 2015 throughout the AEP system. Through our early deployments we hope to determine if the expense of the meters is offset by the benefits. We will continue to pursue the deployment of these smart grid technologies where regulators are supportive and there is a proven business case. We believe modernizing the grid is critical to reducing demand and energy consumption, contributing to energy reliability and security, and preparing for the future needs of customers.Get a state-by-state breakdown of gridSMART initiativesWe believe gridSMART® will transform our relationship with our customers and through our current projects we are learning more about how that will occur. For example, we have learned that:The technology that allows us to manage the grid from our back office systems, such as remote operation of the meter and distribution automation equipment, works asexpected. The technology that goes beyond the meter, into the customers’ home, is still evolving.A significant number of customers who participated in the time-of-day rate plan didshift their demand to different times. In a larger scale deployment, this program could provide relief to the distribution systems during peak times.Better system management, fewer crew trips, reduced fuel consumption, better energy theft detection and streamlined billing can create cost savings.When customers agree to the program, we can directly control electric use through wireless technology (e.g. a two-way communicating thermostat) which allows us to raise the temperature in homes to ease stress on the grid and help customers save energy during the cooling season.More education of consumers will be needed in future projects.For more data, please see indicators EU1 through EU12 of AEP's Global Reporting Initiative Electric Utility Sector Supplement.吕思颖Are geothermal power plants safe?For all our hand-wringing over the oil supply, it might shock you to realize that the solution to our dependence on fossil fuels lies right under our feet. In Western states like California, Nevada, Idaho, Alaska and Hawaii, underground pockets of geothermal energy — hot rock, superheated water and steam — can be tapped to generate electricity. According to backers of geothermal technology like Google, this carbon-neutral, inexhaustible energy source could meet 15 percent of America's electricity needs by 2030.Harnessing SteamIn the simplest geothermal power plant, called a dry steam plant, a well is drilled into the rock to tap a steam reservoir. The steam escapes the well under great pressure, which is used to turn a turbine and generate electricity.Since steam deposits aren't as common as hot water and hot rock reserves, the most promising geothermal technology is called a binary-cycle power plant. In this system, hot water from a deep well circulates through a heat exchanger. There, the。
(9019)《专业英语》大作业A
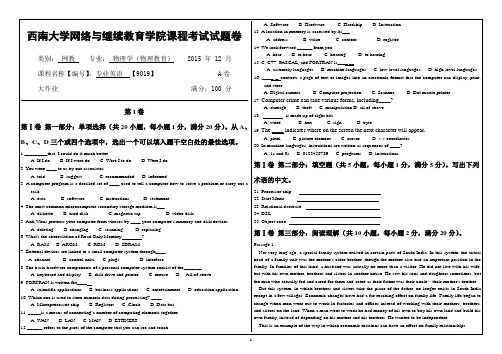
A.Microprocessor chipB.RegistersC.ClockD.Data bus
11._____is a means of connecting a number of computing elements together.
5.Anti-Virus protects your computer from viruses by ____ your computer's memory and disk devices.
A. deleting B. changing C. scanning D. replacing
6.What's the abbreviation of Read Only Memory?
A.If I doB.If I were doC.Were I to doD.Were I do
2.You were ____ to us by our associates.
rmed
3.A computer program is a detailed set of____used to tell a computer how to solve a problem or carry out a task.
C.very few familiesD.not any families
30.What has caused such a peculiar family system to die away ?_______
A.The fact that the mother has not got any brother .
专业英语作业1

《专业英语》作业global corporation全球公司economic boom 经济繁荣Ownership 所有权joint-venture合资企业headquarters 总部Competitive Advantage 竞争优势Entrepreneur企业家equity股权Insurance costs 保险费用bargaining power 议价能力overhead开销Insurance Company 保险公司stock options股票期权consumer appliance 家电消费Insurance contract 保险合同performance-based pay 基础薪酬policy-holder 投保人Commission 佣金personal effects 个人财物natural calamities 自然灾害Decision 决策insurance amount 保险金额insurance coverage 保险保障Venture Capital 风险资本marine coverage 海险salvage charge 救助费用Food chain 食物链general average 共同海损mass production 大规模生产containerization 集装箱distributor 经销商Chain stores 连锁商店phone interview 电话面试vending machine 自动售货机Selling point 卖点billboard 广告牌cinema commercials 影院广告Promotions 促销leaflet 传单poster 海报Search engine 搜索引擎stock prices股票价格Financial crisis 金融危机intellectual capital 智力资本national asset 国家资产Business Model 商业模式Electronic commerce 电子商务Globalization 全球化1、The multinational is big and rich. It often operates in industries which are difficult to enter and of vital national importance, e.g. the computer, chemical and automobile industries. Most important of all, the main objective of the multinational is to organize its activities around the world so as to maximize global profits and global market shares. Each subsidiary is part of an international network of affiliates. These all interact with each other. Each part serves the whole. The center controlling the network—the multinationals’ headquarters—is not under the control of the host government. It is frequently thousands of miles away from these subsidiaries.跨国公司不仅大而且富有。
专业英语课程大作业要求

专业英语课程大作业要求
要求:大作业必须包括以下(一)、(二)两部分内容,每个部分中可以选择一个题目撰写。
选题范围:
(一)、以下任选一个撰写(评分条件:具体、全面、准确、结合实际):
1、英文个人简历(表格形式,篇数不少于2页)
内容包括:个人自然情况、学的专业、爱好等特点。
投递对象:外企公司
要求:内容全面,针对性强。
2、英文求职信,根据应聘单位特点写出自己为什么应聘此
工作的原因。
(1000个单词以上)
(二)、以下任选一个完成:
1、请在下面三个方向中选择其一撰写小论文。
要求根据选题方向自立题目,文章重点突出,语句正确、连贯。
字数在2000个单词以上。
(1) internet Search Engines (work methods、categories、
example:goole/baidu/…..)
(2) advertisement on the web(why、how)
(3) virtual community(interview、categories、example:
blog/BBS)。
专业英语大作业
专业英语大作业专业班级姓名学号成绩OSI System structure1.1 OSI technology (soar technology)The OSI Technology is a kind of can accurately identify multiple transmission channels to bring their respective customers and turnover of technical system, and this technique system is called ordering source recognition Technology (Sources Identification Technology enough), abbreviation OSI Technology, Chinese named soar Technology.Common explanation: is a home business day receive 1000 orders, can accurately know where come of, whether television, newspaper and Internet advertising, or ground shop, or which individuals to bring, no slip through the net.1.1.1 harmonious business modelAccording to the OSI technology, can help sales enterprise monitoring each transmission channel sales contribution, generating a new business cooperation mode: transmission channel is responsible for sales promotion, enterprises are responsible for trading services, to achieve the sales of the both sides after long-term or permanent share profit. On this basis, join product supplier, spread agents, elevator operators, distribution Business, the payment services, call center service providers, various other service providers and technology platform service providers, forming a Shared resource, information transparency, Shared interests and common evolution of Business ecosystem Model that new pattern is called a Harmonious Business Model (for a friend, abbreviation Model HBM).Common explanation: just a small business society, there are production, have a message, answer the phone, distribution, everybody do each of live, each take all the money, do what do, can also discuss how much money after all agree. 1.1.2 BIZVIVA harmonious business operation platformThe world's first based on the OSI technology and harmonious development of commercial mode concept operation platform, the harmoniousbusiness BIZVIVA nine sakura operation platform. In this platform, any role can find other roles, participation or constructing the relevant ecological circle. Such as sales business, can use the platform develops voluntarily or in the platform directly find product suppliers, media, warehouse services, distribution business and various other service provider, etc., based on their respective contribution payment mode, rapidly after the enterprise established will run business models.Common explanation: this is an entirely pay for performance place, the ability of the person can find his place, not capable people also mix not bottom go to. The most important because the third-party platform between people and people build trust.2.1 OSI modelThe OSI/RM namely Open System Interconnection instead Model Open systems Interconnection basic Reference Model. Open, which is not monopoly. System is a realistic system and interconnection of relevant parts.2.1.1 OSI reference model proposed/RMThe world's first network architecture by IBM put forward (74 years, SNA), then other company successively put forward its own network architecture such as: Digital company DNA, us department of defense TCP/IP, a variety of network architecture coexist, the result is if you use the IBM structure, can choose IBM products, and only the same structure network connections.In order to promote the development of computer network international organization for standardization (ISO in 1977 a commission was set up in an existing network was put forward on the basis of not based on specific model, operating system or the company's network architecture, called the open systems interconnection model (OSI reference, open system interconnection) The OSI reference model formSpecific layer 7 Data format Function and connection modeTypicalequipmentApply networ k services an d user Applic ation Application layer between applications of an interfaceThe Presentati on layer wan g Presentation Data representation, data security, data compressionSession layer Session Session set up, manage and termination of conversationThe Transport layer data o rganization Tr ansport Transport intothe data Segment Segment)Segment with aaddressing mechanism toidentify a particularapplications (port)The Network layer Networ k Segmentation and retooling Packet PacketPacket based on theNetwork layer address(IP address) betweendifferent Networksystem path choice ofrouterRouterThe Data Lin Data Link will Data Link will bit Bridges andk layer Data Linkbit information encapsulationinto Data frames Frameinformationencapsulation into Dataframes in physicalityFrame establishment,dissolution, logo logicalLink and Link reuse anderror calibration, andother functions.switchesThe Physical Physical Physi cal Transmission bits (bit)Flow to establish, maintain and cancel the Physical connectionNic, Repeatersand Hubs2.1.2 OSI design purposesThe OSI model design goal is to become a all distributors can realize open network model, to overcome use many private network model brings difficulties and inefficient sex. The OSI is in a highly respected international standard groups participation, completion, the group is international organization for standardization (ISO). What is the OSI, OSI is Open System Interconnection abbreviations, meaning Open System Interconnection reference model. In the OSI before the emergence of computer Network in the presence of so many system structure, among them with IBM's SNA (systems Network Architecture) and DEC DNA (a Digital Architecture) Digital Network Architecture is the most famous. In order to solve different System structure of network Interconnection of international organization for standardization (ISO problems with the OSI (note that don't confuse) in 1981 formulated the OSI reference model (Open System Interconnection Reference Model, the OSI/RM). This model, the Network communication work is divided into seven layers, they from low to high Physical Layer (Layer respectively is Physical), the Data LinkLayer (Data Link Layer), the Network Layer (Layer), a Transport Layer (Layer), Transport Layer (Layer) Session Session, said wang Layer (Layer) and the Application Layer (Layer) apply. The first layer to the third belongs to the OSI reference model of low three layers, responsible for creating network communication link, The fourth floor to the seventh layer for the OSI reference model of high four layers, specifically in charge of end-to-end data communication. Each layer of the accomplishment of a certain function, each layer is directly upper-deck provide service, and all levels are mutually support each other, and network communication can be top-down (after the sender) or bottom-up (in the receiver) two-way. Of course not every communication needs through all the seven layers of the OSI, some even only needs both corresponding a layer can. The physical interface between Repeaters, and connecting with the connection between Repeaters are simply in the physical can; And the connection between the router and the router instead of simply through the network layer of the following three layers can. Generally speaking, both sides of the communication is equivalent level in, not in asymmetric level to communicate.The OSI standards of the method is used in the process of will whole large and complex problem is divided into several manageable small problems, this is a layered architecture measures. In the OSI is introduced in the tertiary abstraction, both system structure, service definition, agreement specifications. For the convenience of memory can be seven layers from high To low as: All Data To allow People like it. Every capital letters with the seven layers name first letters corresponds.2.1.3 OSI division level principleNetwork of each node has the same levelDifferent nodes same level has the same functionThe same node through the interface communication between adjacent layer Each layer can use lower provides services, and provide services to the upperDifferent nodes between layers of equal through agreement to achieve equivalence between layers of communication2.1.4 OSI/RM layered structurePeer-to-peer communication between layer entities when the flow of information processThe essence of equivalence layer communications:Peer-to-peer communication between virtual entity layer, Lowerlayer to provide services; upper Practical communication at the bottom was completed by sending data from lower top gradually to the receiving party data transmission, by the lowest layer gradually to top transfer.Protocol data unit units = pdusSI reference model, the equivalence between layer Protocol exchange information Unit collectively referred to as Protocol Data Unit (Protocol Data Unit, units = pdus).And the transport layer and the following each layer of units = pdus another specific name:The transport layer data Segment (Segment) --The network layer - group (Packet) (Packet)The data link layer data frames (Frame) --The physical bits (Bit) –The OSI 7-layer structureFirst floor: the physical (PhysicalLayer)Provisions communication equipment of mechanical, electrical, function and process characteristics, to establish, maintain and dismantle physics links. Second floor: the data link layer (DataLinkLayer)In the physical provide bittorrent service is developed on the basis of the data link between adjacent nodes, through error-controlling provide data frames (Frame) in the channel on error-free transmission, and each circuit action series. The third is a Network layer (layer)In computer network communication between the two computers may pass through many a data link, may also pass many communication subnet.The fourth floor is processing information transmission Transport layer (layer)Article 4 layers of unit of data packets (also known as packets). But, when you talk about TCP and so on the concrete agreement and have special hyphenates, TCP data unit called segments (provides) and UDP protocol data unit called "data submitted to (datagrams)".The fifth floor is Session layer (layer) SessionThis layer also can call meetings layer or dialogue layer, the session layer and above of high-level, data transmission unit no longer additional naming, referred to as a message.The sixth floor is the Presentation layer (layer) wangThis layer mainly resolves the problem of grammar said user information. It will be for exchange of data from suitable for a user's abstract syntax, convert OSI system suitable for internal use transmission of grammar. Namely, provide the formatting of representation and conversion of data services.Application layer (layer 7 apply layer)The application layer for operating system or network application provides access network service interface.Through the OSI layer, information can be either from one computer software applications transmission to a different application. For example, A computer on the application to sends messages to computer B applications, then the computer application needs A information sent to its first application layer (layer 7), then the layer sends messages to the presentation layer (6th level), the presentation layer data transferred to the fifth session layer (layer), so continue until physical layer (layer 1). In the physical layer, data is placed in the physical network medium and be sent to the computer B. Computer B of the physical layer receive from physical medium data and information sent up to the data link layer (layer 2), the data link layer turn again to the network layer, ordinal continue until the application layer information arrive computer B. Finally, the computer application layer of B again will transmit information for applicationsreceiver, thus completing communication process. Below is explained in this process.The seven layers of the OSI using a variety of control information to and other computer systems to communicate the corresponding layer. These control information requests and that contains special, they in the corresponding OSI layers exchange. Each layer data in the head and tail are two basic forms carry control information.For from a layer sends down data, additional in front of the control information called head, additional behind the control information called the tail. However, on a layer of data from increased agreement head and agreement for a tail, the OSI layers is not necessary.When data in each layer of transfer, each layer can be in data on head and tail, and increase the data already contains a layer of increase in the head and tail. Agreement header contains about layer and layer communications between the information. Head, tail and data are cognate concept, they depend on analysis information units agreement layer. For example, the transport layer head contains only the transport layer can see the information, the transport layer below other layer will only the head as part of data transfer. For the network layer, an information unit consists of layer 3 head and data structures. For the data link layer and network layer down by transfer all of the information or layer 3 head and data are considered as data. In other words, in a given an OSI layer, information unit of data section contains from all upper head and tail and data, this call encapsulation.2.1.5 OSI layered advantages(1) people can easily discuss and study protocol standard details.(2) layer between the standard interface convenient engineering modularization.(3) to create a better interconnection environment.(4) reduced complexity, makes the program easier to modify, product development faster.(5) each layer using adjacent to the lower service, easier to remember a layer of function.The OSI is a well-defined agreement standard set, and there are many optional part complete a similar tasks.It defines the open system structure, hierarchical relationship between each layer and include the possible task. As a framework to coordination and organization of each layer of service provided.The OSI reference model does not provide a realistic approach, but described some concepts, to coordinate inter-process communication standards. Namely the OSI reference model is not a standard, but a standard in making use of conceptual framework.开放式网络互联体系结构1.1 OSI技术(翱翔技术)OSI技术是一种可以精确识别多个传播渠道各自带来的客户和成交额情况的技术体系,这种技术体系被称为订购来源识别技术(Orders Sources Identification Technology),简称OSI技术,中文名叫翱翔技术。
专业英语大作业2016
将下列几段翻译成中文或英语1.空间相机控制器是相机电子学系统中的重要组成部分,而相机控制器与卫星平台之间的通讯接口,作为空间相机实现各种功能的纽带起着举足轻重的作用。
随着我国航空航天技术的飞速发展,遥感卫星上空间相机所执行的任务变得更加多样化,因此相机控制器的功能也更加复杂,对通讯系统的传输速率要求更高,采用以往的低速率通讯系统的设计很难满足新的需求。
(10分)2. Light is an excellent means to externally control the properties of materials and small molecules for many applications. Light's ability to initiate chemistries largely independent of a material's local environment makes it particularly useful as a bio-orthogonal and on-demand trigger in living systems. Materials responsive to UV light are widely reported in the literature; however, UV light has substantial limitations for in vitro and in vivo applications. Many biological molecules absorb these energetic wavelengths directly, not only preventing substantial tissue penetration but also causing detrimental photochemical reactions. The more innocuous nature of long-wavelength light (>400nm) and its ability at longer wavelengths (600-950nm) to effectively penetrate tissues is ideal for biological applications. Multi-photon processes (e.g. two-photon excitation and upconversion) using longer wavelength light, often in the near-infrared (NIR) range, have been proposed as a means of avoiding the negative characteristics of UV light. However, high-power focused laser light and long irradiation times are often required to initiate photorelease using these inefficient non-linear optical methods, limiting their in vivo use in mammalian tissues where NIR light is readily scattered. The development of materials that efficiently convert a single photon of long-wavelength light to chemical change is a viable solution to achieve in vivo photorelease. However, to date only a few such materials have been reported. Here we review current technologies for photo-regulated release using photoactive organic materials that directly absorb visible and NIR light. (10分)3. The relentless advance of drug-resistance among pathogenic microbes, mandates a search for alternative approaches that will not cause resistance. Photodynamic inactivation (PDI) involves the combination of nontoxic dyes with harmless visible light to produce reactive oxygen species that can selectively kill microbial cells. PDI can be broad-spectrum in nature and can also destroy microbial cells in biofilms. Many different kinds of nanoparticles have been studied to potentiate antimicrobial PDI by improving photosensitizer solubility, photochemistry, photophysics and targeting. This review will cover photocatalytic disinfection with titania nanoparticles, carbon nanomaterials (fullerenes, carbon nanotubes and graphene), liposomes and polymeric nanoparticles. Natural polymers (chitosan and cellulose), gold and silver plasmonic nanoparticles, mesoporous silica, magnetic and upconverting nanoparticles have all been used for PDI.(10分)4. Coherent controlization, i.e., coherent conditioning of arbitrary single- or multi-qubit operations on the state of one or more control qubits, is an importantingredient for the flexible implementation of many algorithms in quantum computation. This is of particular significance when certain subroutines are changing over time or when they are frequently modified, such as in decision-making algorithms for learning agents. We propose a scheme to realize coherent controlization for any number of superconducting qubits coupled to a microwave resonator. For two and three qubits, we present an explicit construction that is of high relevance for quantum learning agents. We demonstrate the feasibility of our proposal, taking into account loss, dephasing, and the cavity self-Kerr effect.(10分)5. The ability to coherently control and manipulate individual quantum systems lies at the heart of modern quantum technologies and applications in quantum information. Any quantum computation can be realized as a sequence of elementary quantum gates, which are highly-controlled quantum interactions of few qubits at a time, and quantum measurements. Prominent applications include, e.g., quantum algorithms for efficient factoring and quantum simulation. More recently, applications of quantum algorithms to certain problems in machine learning, including data classification and search engine ranking, have been proposed. Other recent proposals, which are of particular interest for the current paper, are the quantum-enhanced deliberation of learning agents in the context of quantum artificial intelligence and the notion of autonomous and adaptive devices for quantum information processing. In parallel to these theoretical developments, the design of experimental implementations of quantum computational architectures in systems such as, e.g., trapped ions and optical setups has been greatly advanced.(10分)。
专业英语大作业
数控技术应用专业英语2011-2012年度第二学期补考姓名:______________________学号:______________________专业:______________________班级:______________________成绩:______________________一、Translate the following sentences into Chinese. (20×2.5=50分)·1.The CNC concept was proposed in the late 1940s.数控的概念,提出了在20世纪40年代末。
C lathes are primarily used to rotate body workpieces with turning.数控车床主要用于旋转与旋转体工件。
3.The program cannot be stored in some media.该方案不能被储存在一些媒体上。
4.The world’s major industrialized countries don’t pay attention to the research and development of NC machining technology.世界主要工业化国家不重视数控加工技术的研究和发展。
5.Vertical CNC lathes are used to turn large diameter disc -type workpieces.立式数控车床是用来打开大直径圆盘型工件。
6.In the fifity years from the time the first NC machine tools came out to now, itexperienced six generation NC systems.从第一数控机床出来到现在的时间fifity年,它经历了六代数控系统。
第一学期英文专业作业
第一学期英语作业U 11)Youmg as she is. Mary is very good at handling diffcult customers.2)After explaining his plan in great detail,Bob Suimmarized its main points in a few sentences 3)The newly-elected govermment has begun the painful process of working out its policies and strategies4)At first,Tom found it difficult to absorb what his teachers said in class.5) You will be are boyund to fail the exam if you don't do any rowiston(复习)6) Please feel free to call on us whenever you like,7)There are jobs more dangerous than truck driving,forinstance,training lions. (8)the marketing department is working on new strategies to improve the company's share of the market9)Many of the students Complained that the exam was too hard.,10)After reading the text three times,the clever boy has committed it to memory11)The doctor insisted that everything would be alright.Nevertheless I canmot help feeling anxious about the safety of the child12)Nowadays we rely more and more on computers to help us in doing everything13)Apart form being fun and good exercise,swimming is a very useful skill.14)Afer spending a year in Australia, the little girl has gained quite a good Command of spoken English3. Complete the following sentences,using the words in brackets(括号):1)I have warmed you over and over again to keep away from drugs.(over)2)If you try to leam toomany things at atime,you may getsonfused.(time)3)We won't know ifthe plan will work untilwe put it intoprctice(practice)4)You can't learmEnglish well withoutwatching out for diomaticways of saying things.5)Peter has tried manythings with no particularsuccess,but he is bu nomeans an incapableperson (means)6)Can you turn themusic down,please?Ican't concentrate on mywork.(concentrate)7)In adlition toteaching at theuniversity,ProfessorWilson also works as alegal adviser(法律顾问)to a high-techcompany.(addition)8)If you come to myoffice,I'l tell you the storyin latai l (detail)我坚信,阅读简写的英文小说是扩大我们词汇量的一种轻松愉快的方法。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
专业英语大作业一:英译汉翻译范围TCP/IP Illustrated, V olume 1: The Protocols 5.1~5.5 15.1~15.2第5章RARP:逆地址解析协议5.1简介5.2 RARP报文格式5.3 RARP示例5.4 RARP服务的设计5.5小结练习5.1简介一个拥有本地磁盘的系统通常是从磁盘文件读取配置文件中获取其IP地址。
但一个没有磁盘的系统,如X终端或无盘工作站,需要一些其它方式去获得其IP地址。
每个系统在网络上都有一个唯一的硬件地址,由网络接口的制造商分配。
RARP的原则是无盘系统从接口卡上读取其独特的硬件地址,并发送RARP请求(网络上的广播帧)要求别人对无盘系统的IP地址(使用RARP回应)进行应答。
虽然这个概念很简单,执行往往比ARP更难,在本章后面会描述其原因。
RARP的正式规范是RFC 903。
5.2 RARP报文格式RARP报文的格式几乎与ARP报文是相同的(图4.3)。
唯一的区别是,RARP 的请求或应答帧类型为0×8035,并且在操作层RARP请求值为3、RARP应答值为4。
图4-3 ARP在网络上请求与应答报文的格式与ARP一样,RARP服务器请求是广播和RARP应答通常是单播。
5.3 RARP示例在我们的网络,我们可以强制sun主机从网络引导,而不是它的本地磁盘。
如果我们在主机bsdi上运行RARP服务器和tcpdump,我们得到如图5.1所示的输出。
我们使用-e参数去标记tcpdump的打印硬件地址:图5.1 RARP请求和应答。
该RARP请求是广播(1号线)的,第2行的RARP应答是单播的。
第2行的输出,“at sun”,意味着RARP应答包含了主机sun(140.252.13.33)的IP地址。
在第3行,我们看到,一旦sun接收其IP地址,它会发出一个TFTP读请求(RRQ)的文件8CFCOD21.SUN4C。
(TFTP是简单文件传输协议,我们在第15章进行详细描述)。
在文件名中的8个十六进制数字是sun主机的IP地址140.252.13.33的十六进制表示形式。
这是在RARP应答中返回的IP地址。
该文件名的其余部分,后缀SUN4C表示系统正在引导的类型。
Tcpdump表示第3行是一个长度为65的IP数据报,而不是一个UDP数据报(实际上它确实是),因为我们运行tcpdump命令使用-e参数,看硬件级别的地址。
另一点,在图5.1要注意的是在第2行的以太网帧的长度似乎比最小较短(我们所说的是在4.5节60字节)。
原因是我们的系统,该系统上运行的tcpdump 发送该以太网帧(BSDI)。
该应用程序rarpd,写42字节到BSD分组过滤器装置(14字节的以太网报头和28字节的RARP应答),这是什么的tcpdump收到的副本。
但以太网设备驱动程序垫这个短帧的最小尺寸为传输(60 )。
如果我们在另一个系统上已经运行的tcpdump ,长度会是60。
我们可以看到在这个例子,当这种无盘系统接收在RARP应答它的IP地址,它会发出一个TFTP请求来读取一个引导映像。
在这一点上,我们不会进入其他详细介绍无盘系统是如何引导自己。
(第16章介绍了使用RARP ,BOOTP和TFTP无盘X终端的引导顺序。
)图5.2表示出了如果有在网络上没有RARP服务器所得到的数据包。
每个数据包的目的地址为以太网的广播地址。
以太网地址跟随的是目标硬件地址,并按照发送端的硬件地址发送。
图5.2 网络上没有RARP服务器时的RARP请求注意重发的次数。
第一重传发生6.55秒之后再增加到42.80秒,然后下降至5.34秒,然后6.55,然后它的工作方式回到42.79秒。
这将继续下去。
如果我们计算每个超时间隔之间的差异,我们看到了翻倍的效果:从5.34到6.55为1.21秒,从6.55到8.97为2.42秒,从8.97到13.80是4.83秒,依此类推。
当超时间隔达到一定限度(大于42.80秒),它的复位至5.34秒。
增加这样的超时值和每次都使用相同的值相比,是一个更好的方法。
在图6.8中,我们将看到一个错误的方式来执行超时和重传,并在第21章我们将看到TCP的方法。
5.4 RARP服务器设计虽然RARP的概念很简单,RARP服务器的设计取决于系统和复杂度。
相反地,提供一个ARP服务器简单,并且通常是在内核中的TCP/IP实现的一部分。
由于内核知道它的IP地址和硬件地址,当它收到一个ARP请求其IP地址中的一个,它只是在回复中提供相应的硬件地址。
5.4.1RARP服务器作为用户进程RARP服务器的复杂之处为通常为许多在服务器的主机提供从硬件地址到IP地址的映射(网络上所有的无盘系统)。
此映射包含在一个磁盘文件(在U n i x系统中一般位于/etc/ethers目录中)。
由于内核一般不读取和分析磁盘文件,因此RARP服务器的功能是作为一个用户进程,而不是作为内核的TCP / IP实现的一部分。
更为复杂的是,发送RARP请求以太网与特定的以太网帧类型字段帧(从图2.1 0 ×8035)。
这意味着RARP服务器必须具备发送和接收这种类型的以太网帧的一些方法。
在附录A中,我们介绍了如何在BSD分组过滤器,Sun的网络接口点选,SVR4的数据链路提供者接口可以用来接收这些帧。
由于发送和接收这些帧的系统有关,因此RARP服务器的实现是依赖于该系统。
5.4.2 每个网络的多个RARP服务器另一个复杂因素是RARP请求被发送作为硬件级的广播,如图5.2。
这意味着它们不被路由器转发。
为了让无盘系统来引导,即使在RARP服务器主机关闭,多个RARP服务器通常提供一个单一的网络(例如,一个单一的电缆)上。
随着服务器数量的增加(以提供冗余),网络流量的增加,因为每个服务器发送的每个RARP请求的RARP应答,发送该RARP请求的无盘系统通常使用第一个RARP应答来接收。
(我们用ARP从来没有过这样的问题,因为只有一台主机发送一个ARP应答。
)另外,还有一种可能发生的情况是每个RARP服务器同时应答,这样会增加以太网发生冲突的概率。
5.5小结RARP是被许多无盘系统自举时获得他们的IP地址。
该RARP报文格式与ARP报文几乎是相同的。
一个RARP请求的是广播,识别发送者的硬件地址,要求任何人都可以用发送者的IP地址响应。
答复通常是单播。
RARP的相关问题包括其使用链路层广播,阻止大多数路由器转发RARP请求,并返回最小信息:只是系统的IP地址。
第16章中,我们将看到BOOTP返回更多信息无盘系统的引导方法:它的IP地址,主机由自举的名字,等等。
虽然RARP的概念很简单,但RARP服务器的实现取决于系统。
因此,并非所有的TCP/IP实现提供了一个RARP服务。
第15章TFTP:简单文件传输协议15.1简介15.2协议15.3示例15.4安全机制15.5总结15.1简介TFTP是简单文件传输协议。
它被用于自举无盘系统(通常是工作站或X终端)时被使用。
不同于文件传输协议(FTP),我们描述了第27章,并使用TCP,TFTP被设计为使用UDP,使其简单和小。
TFTP(和其所需的UDP,IP和设备驱动程序)的实现方式可以适合于只读存储器。
本章对TFTP进行概述,因为我们将在下一章的引导程序协议遇到它。
我们也在引导网络主机sun时在图5.1遇到过TFTP。
它使用RARP获取其IP地址后,发出一个TFTP请求。
RFC1350[Sollins1992]是TFTP的第2版的官方规范。
文献[Stevens 1990]的第12章提供了完整的源代码实现TFTP客户端和服务器,并介绍了一些与TFTP 使用的编程技术。
15.2协议每次客户端和服务器之间的交换开始于客户端要求服务器上为客户端读或写一个文件。
在自举无盘系统的正常情况下,第一请求是读请求(RRQ )。
图15.1显示了五个TFTP消息的格式(操作码1和2共享相同的格式。
)图15.1 五种TFTP报文格式前2个字节的TFTP消息是操作码。
对于读请求(RRQ)和写请求(WRQ)的文件名指定客户端要读取或写入到服务器上的文件。
我们明确表明,这个文件名是由0个字节结束,在图15.1。
该模式的ASCII字符串NETASCII或八位字节(大写或小写字母的任意组合)之一,再次为0字节结束。
NETASCII意味着数据是由一个回车后跟一个换行符(称为CR / LF )的2字符序列结束每一行的ASCII文本行。
两端必须以此格式和任何本地主机使用的行定界符之间进行转换。
一个八位字节传输将数据视为8位字节,不需要解释。
每个数据包包含一个后一个确认数据包使用的块数。
作为一个例子,读取一个文件时,客户端发送一个读请求(RRQ)指定文件名和模式。
如果文件可以被客户端读取时,服务器响应为1的块号的数据包。
客户端发送的块编号为1的ACK 。
服务器与下一个数据包进行响应,发送编号为2的块号。
客户端发送的块编号为2的ACK 。
这种情况持续下去,直到该文件被转移。
每个数据包包含512个字节的数据,除最后的包,其中包含0-511个字节的数据。
当客户端接收到少于512字节数据的数据包时,它知道它已经收到最终的数据包。
在一个写请求(WRQ)的情况下,客户端发送WRQ指明文件名和模式。
如果文件可以被写入客户端,服务器响应的块号为0的ACK 。
然后,客户端发送第一个512字节的文件,块号编号为0。
服务器响应的块编号为1的ACK 。
这种类型的数据传输称为停止和等待协议。
它只有在简单的协议如TFTP中被发现。
我们将看到在第20.3节的TCP提供不同形式的确认,那种可以提供更高的吞吐量。
TFTP是专为简单性实现,而不是高吞吐量。
最后的TFTP报文类型是错误消息,操作码为5。
这是服务器与如果读请求或写请求不能被处理的响应。
阅读和文件传输过程中写入错误也导致发送该消息,并传输终止。
错误编号提供一个数字错误代码,后面可能包含额外的、操作系统的特定信息的ASCII错误消息。
因为TFTP使用不可靠的UDP ,它是由TFTP来处理丢失和重复的数据包。
丢失的数据包检测与超时和重传由发送方实施。
(请注意所谓的“魔法师的学徒综合症”,当超时和重传都发生问题时就会产生。
文献[Stevens 1990 ]的第12.2节说明该问题如何发生。
)与大多数UDP应用程序一样,TFTP没有校验消息,这假设数据的任何损坏将在UDP校验和中被捕获(11.3节)。
二:词汇题1 X terminal X终端2 diskless workstation 无盘终端3 RARP 逆地址解析协议4 ARP 地址解析协议5 Tcpdump 侦听相关的网络性能数据6 RRQ TFTP读请求7 Bsdi 以太网帧的系统8 BSD Packet Filter BSD分组过滤器9 Network Interface Tap 网络接口点选10 Data Link 数据链路11 Frame 帧12 Redundancy 冗余13 Ethernet 以太网14 Unicast 单播15 Broadcast 广播16 BOOTP 自举协议17 TFTP 简单文件传输协议18 FTP 文件传输协议19 read-only memory 只读存储器20 UDP 用户数据报协议21 IP 互联网协议22 RRQ 读请求23 WRQ 写请求24 opcode 操作码25 data packet 数据包26 stop-and-wait protocol 停止和等待协议27 tcp/ip 传输控制协议/网际协议?28 router 路由器29 gateway 网关30 vpn 虚拟专用网络三:英文写作My major is computer science and technology. During f our years’s study, I have had lots of knowledge of the computer for a more clear understanding to the IT.Through the study, I mastered the basic computer science and technology analysis of basic theory, basic knowledge, master the basic techniques of computer systems analysis and design method, and the understanding of the dynamic development of computer science and technology.I think our school courses, although did not keep pace with the times, but to teachknowledge as the most basic to us.Like data structure to let me to understand the way data how to stored , the computer system architecture to let me understand the constitution of the computer, computer network to let me understand how to communicate between computers , and so on. Like the old saying gose ,To teach fishing is better than teach them to fish, the school give us established a relatively complete system of knowledge, let us convenient to expand the knowledge learning in the future. Learning in school let me understand how to learn about computer knowledge, and let me have a preliminary plan for the future work , I think this is the most important.For the development of my own future,I hope I can calculate the direction of study in the cloud, be harvested. Cloud computing is not only a hot topic, but also I think a promising topic , any traditional application , such as the traditional business model ,if combine with cloud computing,would be a huge innovation. My current research direction is the junk mail sorting based on cloud computing. Through the research, I found that, on the basis of cloud computing, sorting and accuracy can be greatly improved, which can reduce the network load, reduce the burden of the mail server.It is very meaningful.Anyway , I think my university life in this school taught me a lot of things, I love this profession ,but also sincerely hope can contribute to the study of the future.。
