固如金汤 将RAR文件保卫起来
拯救大兵瘟豆子——系统维护全接触

魔法软地带编辑:丢丢 E- ma i l : di udi u@sndn. c om. c n版首语他费了一番功夫,我 们一起去看 看他的新版拯救大兵 吧;虽说亡羊补牢还不晚,可我 们还是积极采取措施预防意外发 生的好,这觉享受,众小编们想方设法,力争 不,风华老师在自己的电脑上架让自己的版式漂亮、漂亮、再漂 起了网络TMD 系统,这下可就高一年之际在于春。
2 004 年 亮!希望大家为《魔法软地带》多 枕无忧了;不过实在不行的话我的春天《少电》杂志将给广大读 多提供好的建议哦。
们还有 最后一 招—系 统还 原,者一个惊喜:从下一期开始,我小眼镜已经进入实习期,这 前提是你得事先做好相关的设置们的彩页将增加到总页码的一 不,精通电脑的他进了一家 IT 公 哦。
半。
为了给大家带来全新的视 司,可是公司里的机器却着实让拯救大兵“瘟豆子”●玉权—系统维护全接触大家好啊 ,开学有一段时间了吧。
告诉大家 一 个好消息,小眼镜已经在一家IT公司开始实习了。
工 作还不算很累,就是新公 司的电脑让人受不了,配 置倒是不低,运行却奇慢无比。
经过一番调查研究, 小眼镜终于发现,原来这些可怜的电脑整天被人用 来用去,却 从来没有接受起码的维护。
哎,看着 这 些原本风光无限的电脑们变成了名副其实的“瘟豆 子(w indows )”,小眼镜真是于心不忍,今天我们 就一起来救它们吧。
37 少年电脑世界魔法软地带垃 圾文 件, 赶尽 杀 绝Wi ndows 运行产生的临时性文件会夹杂在正常的文件中,充斥在电 脑硬盘的 每个角落。
这些惟一 的作用 就是影响 电脑运行 效率的垃圾非常狡猾,将自己隐藏在 Wi ndows 的系统文件夹和注册表中,查找起来既费时费力,还不容易判断准确。
好在小眼镜有“Wi ndows 优化 大师 ”,用 它来 制伏 这些 隐身 坏蛋 不费 吹灰 之力 。
打开“Wi ndows 优化大师”(见图 1 ),点击左侧的[系统清理维护],就可以看 到“大法师 ”对 付垃圾 文件 的 两项 法宝 ,第 一个 叫[ 注册信息清理],第 二个叫[垃圾文件 清理 ]。
2015_-_Jian_Geng_-_Thestabilityofboundchloridesincementpastewithsulfa[retrieved_2015-09-23]
![2015_-_Jian_Geng_-_Thestabilityofboundchloridesincementpastewithsulfa[retrieved_2015-09-23]](https://img.taocdn.com/s3/m/c873140459eef8c75fbfb32d.png)
The stability of bound chlorides in cement paste with sulfate attackJian Geng a ,b ,⁎,Dave Easterbrook b ,Long-yuan Li b ,Li-wei Mo aa Research Center of Green Building Materials and Waste Resources Reuse,Ningbo Institute of Technology,Zhejiang University,China bSchool of Marine Science and Engineering,University of Plymouth,UKa b s t r a c ta r t i c l e i n f o Article history:Received 10July 2014Accepted 25November 2014Available online 27December 2014Keywords:Sulfate attack (C)Bound chlorides (D)Stability (C)Fly ash (D)Ground granulated blast-furnace slag (D)This paper presents an experimental investigation on the stability of bound chlorides in chloride-contaminated cement pastes with and without FA/GGBS when subjected to Na 2SO 4and MgSO 4attack.It is shown that bound chlorides were released in the chloride-contaminated pastes when exposed to Na 2SO 4or MgSO 4solution.This is mainly attributed to the decomposition of Friedel's salt (FS),where Cl −bound in FS is replaced by SO 42−.How-ever there were fewer released chlorides found in the pastes exposed to MgSO 4solution than in those exposed to Na 2SO 4solution.This is partly due to the low pH in the pore solution and partly due to the blocking effect of brucite on ionic transport caused by MgSO 4.The inclusion of FA/GGBS in concrete can increase the decomposition of FS and thus the release of bound chlorides.However,it also resists the penetration of Na 2SO 4and thus reduces the attack of Na 2SO 4.©2014Elsevier Ltd.All rights reserved.1.IntroductionThe corrosion of reinforcing steel in concrete structures,due to chlo-ride ion contamination,is one of the main reasons for the deterioration of concrete structures.There are two forms of chloride ions in concrete.One is free chlorides and the other is bound chlorides.It is well-known that the corrosion of reinforcing steel is mainly induced by the free chlo-rides,so reducing free chlorides by increasing bound chlorides will be bene ficial to the durability of concrete structures.According to the bind-ing mechanism,chloride ions can be bound through chemical reactions and physical absorption.In the former,chloride ions are mainly bound in Friedel's salt (FS)(3CaO·Al 2O 3·CaCl 2·10H 2O)through hydration reactions between chloride ions,tricalcium aluminate (C 3A)and its hydration products.In the latter,chloride ions are mainly absorbed by calcium silicate hydrate (C –S –H gel).It was reported that the formation of bound chlorides could be affected by a multitude of factors such as the quantity of C 3A in cement,supplementary cementitious materials (SCM),alkalinity of pore solution,Ca/Si and Ca/Al of hydration products,chloride salt type,and service condition of concrete structures [1–5].In summary,the chloride binding capacity of concrete can be improved by using SCM or cement with high C 3A content.However,many researchers have identi fied that the stability of bound chlorides,espe-cially of FS,can be affected by pH,carbonation,and chemical erosion [6–9].Sulfate attack is another problem for the durability of concrete struc-tures.The attack of sodium sulfate (Na 2SO 4)and magnesium sulfate (MgSO 4)on concrete is a common phenomenon.The mechanisms of Na 2SO 4and MgSO 4attack on concrete are different,mainly due to the solubility of phases formed with sodium and magnesium ions [10–12].With regard to Na 2SO 4attack,the deterioration of concrete is attributed to the formation of expansion products such as gypsum (CaSO 4·2H 2O)and secondary ettringite (AFt)(3CaO·Al 2O 3·3CaSO 4·32H 2O)according to the following equations:Ca ðOH Þ2þNa 2SO 4þ2H 2O →CaSO 4·2H 2O þ2NaOHð1Þ3ðCaSO 4·2H 2O Þþ3CaO ·Al 2O 3þ26H 2O →3CaO ·Al 2O 3·3CaSO 4·32H 2Oð2Þ2ðCaSO 4·2H 2O Þþ3CaO ·Al 2O 3·CaSO 4·12H 2O þ16H 2O →3CaO ·Al 2O 3·3CaSO 4·32H 2O :ð3ÞWhereas for MgSO 4attack,the transformation of the cementitious C –S –H gel to the non-cementitious magnesium silicate hydrate mush (M –S –H),which has very little strength,is the main reason for the dete-rioration of concrete,although gypsum and secondary AFt are also formed during the attack.In addition,brucite,i.e.Mg(OH)2,will form when magnesium is present in the pore solution,which has low solubil-ity and could densify the pore system and thus affect the transport ofCement and Concrete Research 68(2015)211–222⁎Corresponding author.E-mail address:gengjian@ (J.Geng)./10.1016/j.cemconres.2014.11.0100008-8846/©2014Elsevier Ltd.All rightsreserved.Contents lists available at ScienceDirectCement and Concrete Researchj o u rn a l h o m e p a g e :h t tp ://e e s.e l s e v i e r.c o m /C EM C O N /d e f a u l t.a s pions in the cement paste.The mechanism of MgSO4attack occurs according to the following equations:CaðOHÞ2þMgSO4þ2H2O→CaSO4·2H2OþMgðOHÞ2ð4Þx CaO·y SiO2·z H2Oþx MgSO4þð3xþ0:5y−zÞH2O→xðCaSO4·2H2OÞþx MgðOHÞ2þ0:5yð2SiO2·H2OÞð5Þ4MgðOHÞ2þSiO2·nH2O→4MgO·SiO2·8:5H2Oþðn−4:5ÞH2O:ð6ÞIn fact,sulfate attack and chloride contamination are often found to coexist in concrete structures which are exposed to marine and saline environments.The effects of the sulfate and chloride on a concrete structure's durability are multifaceted.On the one hand,the existence of sulfate,especially of Na2SO4,inhibits the formation of FS and reduces the quantity of bound chlorides[13–15].On the other hand,the exis-tence of chloride ions is beneficial for the resistance of concrete to Na2SO4and MgSO4attack[15–18].However,Baghabra argued that the effect of chloride ions on MgSO4attack was slight because the trans-formation of cementitious C–S–H gel to non-cementitious M–S–H was not affected by chloride ions[19].Despite the work on the interaction of sulfate and chloride in con-crete mentioned above,there is very little work on the effect of sulfate attack on the stability of bound chlorides in concrete.Brown and Badger investigated the distributions of bound sulfates and chlorides infield concrete cores exposed to mixed NaCl,Na2SO4and MgSO4attack. They found that there was extensive AFt in the absence of a gypsum zone for some concrete cores[20].Xu et al.obtained similar results, i.e.that sulfate attack could lead to the release of bound chlorides[21]. Both studies suggested the transformation of FS to AFt due to sulfate attack,but the mechanism of FS transform to AFt and the stability of bound chlorides absorbed by C–S–H gel under sulfate attack were not discussed in depth.It is well known that the use offly ash(FA)and ground granulated blast-furnace slag(GGBS)in concrete can not only improve the chloride binding capacity of concrete,but also the resistance of concrete to sulfate attack[22,23].Hence,it would be interesting to know how they affect the stability of bound chlorides when the concrete is under sulfate attack.The purpose of this paper is to report the experimental in-vestigation on the stability of bound chlorides in cement paste under Na2SO4and MgSO4attack,and the corresponding influence of FA and GGBS on the stability of bound chlorides.The stability of bound chlorides in cement paste was examined by analyzing the change of a dimensionless index,R cl,which represents the mass ratio of bound chlo-rides to initial total chlorides in the sample after it was exposed to a5% Na2SO4solution or a5%MgSO4solution for28,56or90days.The mech-anisms of the release of bound chlorides are discussed based on the results of X-ray diffraction(XRD),Fourier transform infrared(FT-IR) and differential thermo-gravimetric analysis(DTG).2.Experiment2.1.MaterialsThe materials used in the experiments were Type42.5Ordinary Portland Cement(OPC),grade II FA and GGBS.The chemical composi-tions of OPC,FA and GGBS are listed in Table1.The potential phase com-positions of OPC,calculated from chemical analysis by Bogue,are given in Table2.All other chemical reagents used in the experiments,but not listed in the tables,are analytically pure.2.2.MethodsIn order to reduce the experimental running time but still able to achieve good and representative results,chloride binding was achieved by using0.5mol/L NaCl solution as the mixing water for the casting of samples.The mass ratio of the mixing water to the binder(cement and SCM)was0.5,which was the same for all samples.The influence of single and combined use of FA and GGBS on the stability of bound chlorides was also investigated.The replacement of cement with SCM was30%by weight,and the proportions of FA to GGBS in the combined samples were either1:1or7:3.The detailed mix proportions of the samples tested are listed in Table3.A total of106samples were tested.All samples were of a size of 40mm×40mm×160mm.There were three groups of samples.The first group(2×5×7samples)were cured at a standard curing condi-tion(20±2°C and95%RH)for periods of1,3,7,14,28,56and90days for the investigation of the effect of curing time and SCM on the evolu-tion of bound chlorides in the cement paste.The second group(2×5×3 samples)were examined for the effect of Na2SO4attack on the stability of bound chlorides.In this group,all samples,after the56days standard curing,were dried at a room temperature(20±2°C and60%RH)for 1day.Then,for each sample itsfive surfaces were sealed by paraffin wax and one40mm×40mm surface was left untouched.After then, all samples were immersed in a covered plastic container(575mm ×400mm×275mm)of5%Na2SO4solution for28,56and90days at the standard curing condition(20±2°C and95%RH).The third group(2×1×3samples)were for the samples only with OPC,which were cured as the same as those done in the second group.The only dif-ference is that they were immersed in a similar covered container of5% MgSO4solution for28,56and90days at the standard curing condition (20±2°C and95%RH)for the examination of the effect of MgSO4at-tack on the stability of bound chlorides.The volume of the sulfate solu-tions used in the immersion tests was25L and the storage solutions were not renewed during the immersed tests.In the second and third groups,when the attack time reached28,56, and90days,the samples were dried at room temperature for1day,and then were sliced into four pieces parallel to the exposed surface (starting from the exposed surface)and each piece is one cm thick. Afterwards,each piece was broken into small blocks,which were then immersed in anhydrous ethanol for7days to terminate hydration. These small blocks were ground intofine powder by passing through a sieve of0.15mm mesh aperture size,which was then stored in a des-iccator with silica gel and soda lime at11%RH to minimize carbonation before it was used in the tests for chloride content titration and other material characterization analyses.The initial total chloride content(C t)of the sample cured at the stan-dard curing condition can be calculated based on the mixing water of Table1Chemical composition of main materials(data presented by mass%).SiO2CaO MgO Fe2O3Al2O3SO3Ignition loss OPC19.6760.43 4.56 4.20 5.70 2.30 2.54FA43.10 6.300.247.2638.200.70 2.04GGBS23.5052.80 6.500.7011.80 1.650.78Table2Potential phase composition of OPC(data presented by mass%).Potential phase composition OPCC3S51.58C2S17.77C3A8.01C4AF12.773.91212J.Geng et al./Cement and Concrete Research68(2015)211–2220.5mol/L NaCl solution,which is 8.863mg ·g −1.The free chloride content (C f )was measured using the traditional leaching method according to the standard of Test Code for Hydraulic Concrete (SL352-2006)and the total chloride content (C t )was measured using the acid-soluble method (SL352-2006).In order to analyze the stability of bound chlorides in concrete,the dimensionless index (R cl )was exam-ined,which is de fined as follows,R cl ¼C t −C f %ð7Þwhere 8.863mg.g −1is the initial total chloride content in the sample.X-ray diffraction (XRD)/reference intensity ratio (RIR)analysis and DTG can be used to approximately determine the quantity of FS,AFt and calcium hydroxide (CH)in the samples.XRD/RIR can determine the relative mass relations among different minerals in a sample,which is calculated according to the following equations [24,25]:W i ¼I i =RIR iX i ¼1I i=RIR i ðÞð8ÞW 1þW 2þW 3þ⋯þW l ¼1ð9Þwhere W i is the relative mass of mineral i ,RIR i is the reference intensityratio of mineral i ,which can be collected from the PDF card of the Inter-national Centre for Diffraction Data (ICDD),I i is the integral intensity of the highest peak of mineral i ,which is calculated using X'Pert HighScore Plus ™software,and N is the number of minerals in the sample.XRD/RIR is usually used to determine the quantity of substances in metals because of simple compositions [25].For cement based materials,it is rather complicated to accurately determine the kinds of hydration products,which increases the dif ficulty of the quantitative analysis.However,if the quantity of one of the minerals can be determinedusing other methods,the calculation process of XRD/RIR becomes pared with the FS and AFt,the quantity of CH can be accurately determined using DTG.Therefore,the quantities of the FS and AFt can be calculated by solving the following algebraic equations,m FS :m AFt ¼T 1ð10Þm FSFS þm AFt þm CH ¼T 2ð11Þm AFtm FS þm AFt þm CH ¼T 3ð12Þm CHm FS þm AFt þm CH¼T 4ð13Þwhere m FS ,m AFt and m CH are masses of FS,AFt and CH,respectively,T 1,T 2,T 3and T 4are the mass ratios,which can be calculated from Eqs.(8)and (9).Note that,m CH can be determined by DTG and thus m FS and m AFt can be determined by Eq.(10)plus any one taken from Eqs.(11)–(13).XRD was carried out using the D8Advance instrument of Bruker AXS with a Cu K αradiation generated with 40kV and 30mA.The diffraction spectra were collected in the range of 5–60°(2θ)scale,with a step sizeTable 3Mix proportions (data presented by mass %).Samples OPC FA GGBS w/b a NoteCN 100000.5Exposed to 5%Na 2SO 4solutionCF 703000.5CG 700300.5CF1G17015150.5CF7G3702190.5CM1000.5Exposed to 5%MgSO 4solutionaw/b represents the mass ratio of mixing water (i.e.0.5mol/L NaCl solution)to binder (cement +SCM).Fig.1.Variation of R cl with standard curing time in samples of differentmixes.Fig.2.Values of R cl in the surface layer of the sample at various different sulfate attack times (CM was exposed to MgSO 4,while all the others were exposed to Na 2SO 4).Fig.3.Values of R cl in different layers of the sample after 90days sulfate attack (1st layer is next to the surface and 4th layer is away from the surface.CM was exposed to MgSO 4,while all the others were exposed to Na 2SO 4).213J.Geng et al./Cement and Concrete Research 68(2015)211–222of 0.02°/s.FT-IR was performed for the samples on a Nicolet Nexus 470spectrometer using the KBr pellet technique in the range of 400–4000cm −1.DTG was carried out in a Netzsch TG-209F1thermal an-alyzer,using a heating rate of 20°C/min at the range of 25–1000°C,in N 2atmosphere.3.Stability of bound chlorides 3.1.Standard curing conditionThe variation of R cl during the standard curing time is shown in Fig.1.It can be seen from the figure that R cl in the samples with SCM is higher than that in the sample only with OPC when they have the same curing time,which is more obvious after the curing time exceeds 14days.Up to 28days,the combined use of FA and GGBS results in higher values of R cl in CF1G1and CF7G3than in the samples with only either FA (CF)or GGBS (CG).However,after the 28days standard curing,the R cl value of the samples has an order of CF ≈CF7G3N CF1G1N CG,which increases with the increased proportion of FA to GGBS.The latereffect of FA on chloride binding is mainly due to its slow pozzolanic re-action.The results shown in Fig.1indicate that the inclusion of SCM in concrete can increase the chloride binding capacity and the effect of FA on chloride binding is more signi ficant than that of GGBS.Furthermore,they also show that the R cl values of all samples increase very obviously before 28days but after that there is less change,suggesting that the equilibrium between free and bound chlorides has been reached.3.2.Sulfate attack conditionFig.2shows the expected decrease in R cl of the surface layer of all samples with the sulfate attack,but the rate of the decrease is higher than that was reported [21].The R cl value in the surface layer of sample CN exposed to Na 2SO 4solution,for example,decreases from 59.8%to 4.3%after only 28days.After that,R cl continuously decreases with the attack time but with a slow reduction rate,from 4.3%at 28days to 1.9%at 90days.The results for locations other than the surface layer at 90days are shown in Fig.3.It can be seen from the figure that,although the 4th layer of sample CN is far away from theexposedFig.4.XRD patterns of samples CN(CM),CF and CG at standard curing condition for (A)28and (B)56days (E:ettringite (AFt),F:Friedel's salt (FS),CH:calcium hydroxide,M:mono-sulfoaluminate,V:Vaterite,CSH:C –S –H gel,C:calcite).214J.Geng et al./Cement and Concrete Research 68(2015)211–222surface,there is still a notable decrease in the R cl value from59.8%at the beginning of the Na2SO4attack to16.6%after90days of attack.This demonstrates that the stability of bound chlorides in concrete is very susceptible to Na2SO4attack.Note that the data plotted in Fig.2show that there is also a decrease in the R cl values of the samples with SCM after Na2SO4attack for28days, but the R cl values are still higher than that of the sample CN only with OPC.This suggests that the use of SCM can alleviate the effect of Na2SO4attack on the stability of bound chlorides.This is partly because the effect of SCM on the diffusion of ions,since the ionic diffusion coef-ficient in cement paste with SCM is normally lower than that in OPC paste,and partly because the cement paste with SCM has more bound chlorides[26].Additionally,in contrast with the results obtained under the standard curing condition,the R cl values of the samples with SCM increase with the decreased proportion of FA to GGBS,and also the R cl value of the surface layer of sample CF is the lowest of all samples containing SCM,following the Na2SO4attack.This suggests that Na2SO4attack can also alter the effect of SCM on the stability of bound chlorides.This appears to be consistent with what is reported in literature[21].The stability of bound chlorides in concrete under MgSO4attack is also shown in Figs.2and3.When the MgSO4attack time extends from0to28days,the R cl value of the surface layer of sample CM decreases from59.8%to26.3%,which is slower than that of sample CN exposed to Na2SO4solution.When the attack time reaches90days, the R cl value of sample CM's surface layer decreases to7.5%,which is still almost four times as high as that of sample CN.This indicates that the stability of bound chlorides is less susceptible to MgSO4attack when compared with Na2SO4attack.Again,thisfinding is consistent with what is reported in other experiments[21,27].The different reductions of R cl in samples CM and CN reflect the different effects of MgSO4and Na2SO4on bound chlorides.During the immersion process free chloride ions will diffuse out and sulfate ions will diffuse into the specimen.The former may decrease the bound chlo-ride level in the sample owing to the equilibrium between the free and bound chlorides.The latter can transform FS into AFt,which not only can reduce the bound chlorides but also can change the pore system and thus affect the diffusion rate of ions.In addition,when magnesium is present,brucite will be formed,which can also change the pore sys-tem and thus affect the transport of ions and the R cl value.The slower reduction of R cl found in sample CM shown in Figs.2and3indicates that the magnesium ions must have some influence on the sulfate attack to the bound chlorides.This influence could be physical and/or chemi-cal.The former is mainly due to the forming of brucite in the surface layer,which reduces the inward diffusion of sulfate ions and the out-ward diffusion of chloride ions.Indeed,the measured free chloride con-centration after the90days immersion was found to be higher in sample CM than in sample CN and have the ratios of about1:0.72for the surface layer and1:0.81for the4th layer.An accurate analysis for the diffusion effect on the bound chlorides requires having more data on thinner layers and knowing the binding isotherms.Nevertheless, the above results did indicate that the diffusion of chloride ions was affected by magnesium ions.The chemical effect of magnesium ions on bound chlorides will be discussed in the next section.Note that the ionic diffusion coefficient in concrete with SCM is nor-mally smaller than that in concrete only with OPC.Thus,the inclusion of SCM in cement paste can provide additional resistance to the ingress of sulfate ions,which in turn can affect the stability of bound chlorides. More discussion on this will be provided in the next section.4.Material characterization analyses4.1.X-ray diffractionThe XRD patterns of samples CN,CF and CG cured at the standard curing condition for28and56days are shown in Fig.4.From the XRD patterns one can identify the FS with a very obvious diffraction peak at around11°2θ.Fig.5shows the relative masses of AFt,FS and CH in samples CN,CF and CG after they were cured in the standard condition for56days.It can be seen from thefigure that the use of FA and GGBS is beneficial to forming more FS.This result can be attributed to two rea-sons.First,the forming process of FS in concrete has been associated with the quantity of aluminate in cementious materials.The higher the quantity of aluminate,the more FS is formed.According to the chemical composition shown in Table1,there is a larger quantity of alu-minate in GGBS and FA than in OPC,which can be released due to the latent hydraulic property of GGBS and the pozzolanic property of FA, which is beneficial to the formation of FS.Secondly,the formation of FS would be hindered because SO42−can react with aluminate prior to Cl−to form mono-sulfoaluminate(AFm)and AFt[13–15].In addition, C–A–H and C–S–H gel,formed due to the hydration reactions induced by FA and GGBS,are also beneficial to chloride binding.As shown in Fig.5,although the quantity of aluminate in FA is higher than that in GGBS,the quantity of FS in sample CF is still lower than that in sample CG after standard curing for56days.It was believed that only reactive alumina Al2O3r−in SCM could react with Cl−to form FS[5].The quantity of CaO in FA used in this study is6.3%,which is low calciumfly ash according to Chinese specification GB/T15696-2005,and where Mullite is the main form of Al2O3,so it is adverse to the formation of FS.Nevertheless,a notable decrease in the intensity of diffraction peak (IDP)of CH can be found in the XRD patterns of sample CF over the curing time from28to56days,which is induced due to the pozzolanic reaction between CH and FA.As a result,more C–S–H gel and C–A–H are formed,which could increase the bound chlorides in sample CF.It should be noticed that the IDP change at around30°(2θ)shown in Fig.4correlates with both C–S–H gel and calcite(CaCO3),because of the overlap of the two strongest diffraction peaks at29.25°(2θ)and 29.40°2θ,respectively[8,28].The XRD patterns of sample CN under Na2SO4attack are shown in Fig.6.It can be observed from Fig.6A that the IDP of FS in the surface layer of sample CN becomes very weak after Na2SO4attack for28 days,which indicates that FS has been decomposed due to the Na2SO4 attack.A quantitative analysis of FS,AFt and CH of sample CN after the Na2SO4attack for28and90days is shown in Fig.7.It can be seen from thefigure that the relative mass of FS in the sample decreases very quickly from2.04to0.45after the28days attack.This suggests that the stability of FS is very susceptible to Na2SO4attack,which may also explain why the decrease of R cl is quick as is shown in Fig.2.How-ever,when the attack time is extended from28to90days,the change in the quantity of FS is slight,which indicates that a large quantity of FShasFig.5.Analysis of ettringite(AFt),Friedel's salt(FS)and calcium hydroxide(CH)in sam-ples CN/CM,CF and CG after they had56days standard curing(wt.%represents the mass percentage of AFt/FS/CH in sample).215J.Geng et al./Cement and Concrete Research68(2015)211–222been decomposed following 28days of the Na 2SO 4attack.Moreover,it can be seen from Fig.7that the quantity of FS gradually decreases from the inside to the surface,which correlates with the change of the R cl value shown in Fig.3.In addition,one can see from Fig.6B that AFt with a diffraction peak at around 9°(2θ)can be detected in every layer of sample CN after the Na 2SO 4attack for 90days.The data shown in Fig.7for AFt indicate that the quantity of AFt in the fourth layer of sam-ple CN is higher than its initial value,which con firms that the attack of Na 2SO 4has reached the fourth layer of the sample.Fig.7also shows the expected opposite changes of FS and AFt with time.The XRD patterns of samples CF and CG after the Na 2SO 4attack for 90days are shown in Fig.8.Similar to the sample CN,the diffraction peaks of FS in the samples with SCM,especially in sample CF,become very weak.Similar to the analysis of the sample CN,Fig.9shows the relative mass of FS,AFt and CH of samples CF and CG after the Na 2SO 4attack for 90days.It seems that the quantities of FS in samples CF and CG are as high as that in sample CN after the Na 2SO 4attack.However,considering the higher quantity of FS in samples CF and CG before the Na 2SO 4attack as shown in Fig.5,the decrease of the quantity of FS in them is quicker than that in sample CN.Therefore,it can be concluded that the stability of FS in the samples with FA or GGBS is susceptible to Na 2SO 4attack when compared to the sample CN.The XRD patterns of samples CN and CM attacked by Na 2SO 4and MgSO 4for 90days are shown in Fig.10.An interesting finding is that there is still an obvious diffraction peak of FS in the sample CM,which is different from the sample CN attacked by Na 2SO 4.The analysis results shown in Fig.11demonstrate that there is more FS in sample CM than in sample CN.Therefore,it can be concluded that the Na 2SO 4attack has more effect on the decomposition of FS in hardened cement paste than the MgSO 4attack.In addition,the IDP of AFt in sample CM is lower than that in sample CN due to the different erosion mechanisms.However,there is still an obvious increase in AFt for sample CM from 0to 90days as demonstrated in Figs.5and 11,which indicates that MgSO 4attack can also lead to the formation of secondary AFt.NoteFig.6.XRD patterns of samples CN with Na 2SO 4attack.(A)1st layer at different days and (B)different layers at 90days (E:ettringite (AFt),F:Friedel's salt (FS),CH:calcium hydroxide,M:mono-sulfoaluminate,V:Vaterite,CSH:C –S –H gel,C:calcite).216J.Geng et al./Cement and Concrete Research 68(2015)211–222that,when magnesium is included in the exposure solution,brucite is formed at the expense of calcium hydroxide,which can affect not only the leaching of chloride from the specimen but also the inward trans-port of sulfate from the exposed solution and thus provide the in fluence on the decomposition of FS and the formation of AFt.However,our XRD result did not reveal a signi ficant amount of brucite and/or gypsum in the surface layer.This is probably due to the specimen layer used in the tests being too thick.Both Skaropoulou and Sotiriadis reported their test results in which brucite was detected in XRD patterns,but the IDP of it was very weak when compared to other phases [11,17].However,in other similar experiments brucite was not detected in XRD patterns [27,29,30].This is probably attributed to the consumption of brucite due to the formation of M –S –H as shown in Eqs.(4)–(6)[19].4.2.Fourier transform infrared (FT-IR)Fig.12shows the FT-IR spectra of sample CN after the Na 2SO 4attack for 28and 90days,respectively.The band at around 3640cm −1is due to the stretching vibration of \OH in Ca(OH)2[30],which is very weak in all samples due to Na 2SO 4attack.The presence of carbonate bands at around 1430and 870cm −1indicates that the samples have already absorbed CO 2molecules from the air before they were immersed into sulfate solution [31].The band at around 1110cm −1comes from asym-metric stretching vibration of S –O in SO 42−,which is identi fied as the fingerprint peak of AFt [32,33].As is shown in Fig.12,owing to more secondary AFt being formed,this band becomes stronger from the in-side to the surface over the attack time.The changes in the bands at around 3440and 1650cm −1are due to the stretching vibration of \OH in structural water of hydration products and the bending vibra-tion of \OH in the interlayer water of hydration products [30].The two bands are also related to the formation of secondary AFt,which be-come strong with the increased quantity of secondary AFt.In addition,the band at around 970cm −1comes from asymmetric stretching vibra-tion of Si –O in C –S –H gel [31,34].It can be observed from Fig.12that there is no obvious change in this band over the attack time,which sug-gests that the stability of C –S –H gel is independent of Na 2SO 4attack.With regard to FS,because chloride ions are not absorbed in the range 400–4000cm −1,the bands at around 730,530and 460cm −1,which are due to Al –O vibrations of [Al(OH)6]3−,can be identi fied as the fin-gerprint peaks of FS [35,36].Owing to the decomposition of FS under Na 2SO 4attack,the strength of these bands appears very weak.Fig.13shows the FT-IR spectra of samples CF and CG after the Na 2SO 4attack.There is no obvious band at around 3640cm −1in thespectra due to the consumption of CH induced by hydration reactions of FA and GGBS and sulfate attack.It can be observed from Fig.13that there is an increase in the strength of the band of C –S –H gel at 976cm −1in sample CF over the attack time from 56to 90days.Guerre-ro et al.attributed this to the further activating action on FA due to the increase in alkalinity induced by Na 2SO 4attack [15].Moreover,this re-sult also indicates that the stability of C –S –H gel is independent of Na 2SO 4attack.The difference of the bands at 714,535and 458cm −1be-tween samples CF and CG is slight.Fig.14shows the FT-IR spectra of samples CN and CM after Na 2SO 4and MgSO 4attack for 90days,respectively.It is observed from Fig.14that the strength of the band at around 710cm −1in sample CM is much stronger than that in sample CN.Also there is more FS in sample CM than in sample CN,which agrees with the results shown in Figs.10and 11.Moreover,it can be seen clearly from Fig.14that the strength of the band at around 970cm −1in sample CM is lower than that in sample CN.This is likely attributed to the decomposition of C –S –H gel induced by MgSO 4attack.As a result of that,the bound chlorides absorbed by C –S –H gel are released.A weak band at around 1110cm −1in sample CM due to the attack of MgSO 4can induce the formation of secondary AFt.4.3.Derivative thermo-gravimetric analysis (DTG)The DTG curves of sample CN attacked by Na 2SO 4are shown in Fig.15.There are some notable endothermic peaks in the DTG curves.The peak near 100°C is mainly attributed to the dehydration of C –S –H gel and AFt,which are dif ficult to distinguish because of the overlap of dehydration temperature from 85to 130°C [23].The peak near 160°C is attributed to AFm [23].Besides these,the peaks near 340,450and 710°C are attributed to the dehydration of FS,CH and the decomposi-tion of calcite.The absence of the peak for FS in the DTG curve after the Na 2SO 4attack for 28days shown in Fig.15further demonstrates that the stability of FS is susceptible to Na 2SO 4attack.The change in the peak of AFm,which plays an important role in the formation of sec-ondary AFt during the Na 2SO 4attack,is also consistent with the change of FS.Fig.16shows the DTG curves of samples CF and CG after the Na 2SO 4attack for pared to sample CG,sample CF has a weak strength of the peak for FS,which is consistent with the analysis result shown in Fig.9and the R cl data shown in Fig.2.Fig.17shows similar DTG results of samples CN and CM after Na 2SO 4and MgSO 4attack for 90days.It is noticed from the figure that the strength of the peak for C –S –H gel and AFt in sample CM is far lower than that in sample CN.Ac-cording to the FT-IR results shown in Fig.14,this result further indicates that MgSO 4attack will lead to the decomposition of C –S –H gel,resulting in the release of bound chlorides.5.Discussion5.1.Stability of Friedel's saltSuryavanshi and Swamy reported that a drop in alkalinity of pore so-lution due to carbonation could induce the decomposition of FS [8].Con-versely,Na 2SO 4attack can increase the alkalinity of the pore solution,which has a negative effect on chloride binding [23,27,37].The question now is how Na 2SO 4attack affects the stability of FS.The exchange be-tween Cl −and SO 42−is the main mechanism in the formation of FS,which can be explained by the following reaction [27]:3CaO ·Al 2O 3·CaSO 4·12H 2O ðAFm Þþ2Cl −→3CaO ·Al 2O 3·CaCl 2·10H 2O ðFS ÞþSO 2−4þ2H 2O :ð14ÞEssentially,FS belongs to a phase of the AFm family,which has a complex chemical and structural constitution.A general formula for AFm phase is [Ca 2(Al,Fe)(OH)6]+X·m H 2O,where the bracketsindicateFig.7.Analysis of ettringite (AFt),Friedel's salt (FS)and calcium hydroxide (CH)in sample CN after Na 2SO 4attack for 0,28and 90days (wt.%represents the mass percentage of AFt/FS/CH in sample).217J.Geng et al./Cement and Concrete Research 68(2015)211–222。
重要安全说明

重要安全说明z为了减少火灾、触电或产品损坏的危险,请勿让本机遭受雨淋、受潮或滴溅上液体,也不要将诸如花瓶等盛水之器物置于本机之上。
z为了确保良好的通风条件,请勿将本机安装或置于书柜、内藏式机柜或其它密闭的空间里。
勿让窗帘或任何其它物体堵塞通风孔,以免因机器过热而造成触电或火灾危险。
z切勿将诸如点燃的蜡烛灯明火火源置于本机之上。
z废弃处理电池时要尽量采取不破坏环境的方式z机器应放在交流电源输出插孔附近,电源插头应放在出现故障时能够便于拔插之处。
z本机使用过程中,可能受到移动电话的无线电波干扰。
如果这种干扰明显的话,请将移动电话远离本机使用。
z请阅读本说明书中说明事项及操作方法。
妥善保管本说用说明书,以备日后参考。
放置请将本机放在平坦的平面,应远离直射阳光,并避免高温、高湿和频繁的振动。
否则会造成机壳和其它内部零件的损坏,从而缩短本机的寿命。
请不要在本机上放置重物。
放置本机时,请与墙壁保持20厘米以上距离。
由于本机较重,放置本机时,请务必考虑婴幼儿或儿童的安全,以免造成人身伤害。
荷重不可在机器上放置重物或踩踏机器。
否则,会造成严重的人身伤害,也会损伤机器。
通风机壳上的槽缝和散热孔时为保证通风,避免过热,以使机器工作可靠而设计的,因而不要使其堵塞或遮挡。
不要将机器置于床、沙发、布匹或类似的物料上,以免堵塞通风孔。
不能确保通风或违反厂家规定的物件如书架、框架等,也不可作为放置本机的场所。
电源请勿使用过高的电压源,否则会造成本机过载并引起火灾。
应正确地连接交流电源线,并保证电源线没有损伤。
连接不良或电源线损坏会引起火灾和触电事故。
请不要拉扯、折弯电源线或在电源线上放置重物。
插座上的电源不可超载,延长电源线、集成式插座等也要倍加小心,因为这些都可能造成触电或引起火灾。
在拔交流电源时,应牢固地握住插头。
勿用湿手插入或拔出插头,否则可能会引起触电事故。
为了防止雷电引起的损坏或长时间不使用本机器时,应将其从电源插座上拔下。
The Chubby lock service for loosely-coupled DS

The Chubby lock service for loosely-coupled distributed systemsMike Burrows,Google Inc.AbstractWe describe our experiences with the Chubby lock ser-vice,which is intended to provide coarse-grained lock-ing as well as reliable(though low-volume)storage for a loosely-coupled distributed system.Chubby provides an interface much like a distributedfile system with ad-visory locks,but the design emphasis is on availability and reliability,as opposed to high performance.Many instances of the service have been used for over a year, with several of them each handling a few tens of thou-sands of clients concurrently.The paper describes the initial design and expected use,compares it with actual use,and explains how the design had to be modified to accommodate the differences.1IntroductionThis paper describes a lock service called Chubby.It is intended for use within a loosely-coupled distributed sys-tem consisting of moderately large numbers of small ma-chines connected by a high-speed network.For example, a Chubby instance(also known as a Chubby cell)might serve ten thousand4-processor machines connected by 1Gbit/s Ethernet.Most Chubby cells are confined to a single data centre or machine room,though we do run at least one Chubby cell whose replicas are separated by thousands of kilometres.The purpose of the lock service is to allow its clients to synchronize their activities and to agree on basic in-formation about their environment.The primary goals included reliability,availability to a moderately large set of clients,and easy-to-understand semantics;through-put and storage capacity were considered secondary. Chubby’s client interface is similar to that of a simplefile system that performs whole-file reads and writes,aug-mented with advisory locks and with notification of var-ious events such asfile modification.We expected Chubby to help developers deal with coarse-grained synchronization within their systems,and in particular to deal with the problem of electing a leader from among a set of otherwise equivalent servers.For example,the Google File System[7]uses a Chubby lock to appoint a GFS master server,and Bigtable[3]uses Chubby in several ways:to elect a master,to allow the master to discover the servers it controls,and to permit clients tofind the master.In addition,both GFS and Bigtable use Chubby as a well-known and available loca-tion to store a small amount of meta-data;in effect they use Chubby as the root of their distributed data struc-tures.Some services use locks to partition work(at a coarse grain)between several servers.Before Chubby was deployed,most distributed sys-tems at Google used ad hoc methods for primary elec-tion(when work could be duplicated without harm),or required operator intervention(when correctness was es-sential).In the former case,Chubby allowed a small sav-ing in computing effort.In the latter case,it achieved a significant improvement in availability in systems that no longer required human intervention on failure. Readers familiar with distributed computing will rec-ognize the election of a primary among peers as an in-stance of the distributed consensus problem,and realize we require a solution using asynchronous communica-tion;this term describes the behaviour of the vast ma-jority of real networks,such as Ethernet or the Internet, which allow packets to be lost,delayed,and reordered. (Practitioners should normally beware of protocols based on models that make stronger assumptions on the en-vironment.)Asynchronous consensus is solved by the Paxos protocol[12,13].The same protocol was used by Oki and Liskov(see their paper on viewstamped replica-tion[19,§4]),an equivalence noted by others[14,§6]. Indeed,all working protocols for asynchronous consen-sus we have so far encountered have Paxos at their core. Paxos maintains safety without timing assumptions,but clocks must be introduced to ensure liveness;this over-comes the impossibility result of Fischer et al.[5,§1]. Building Chubby was an engineering effort required tofill the needs mentioned above;it was not research. We claim no new algorithms or techniques.The purpose of this paper is to describe what we did and why,rather than to advocate it.In the sections that follow,we de-scribe Chubby’s design and implementation,and how ithas changed in the light of experience.We describe un-expected ways in which Chubby has been used,and fea-tures that proved to be mistakes.We omit details that are covered elsewhere in the literature,such as the details of a consensus protocol or an RPC system.2Design2.1RationaleOne might argue that we should have built a library em-bodying Paxos,rather than a library that accesses a cen-tralized lock service,even a highly reliable one.A client Paxos library would depend on no other servers(besides the name service),and would provide a standard frame-work for programmers,assuming their services can be implemented as state machines.Indeed,we provide such a client library that is independent of Chubby. Nevertheless,a lock service has some advantages over a client library.First,our developers sometimes do not plan for high availability in the way one would wish.Of-ten their systems start as prototypes with little load and loose availability guarantees;invariably the code has not been specially structured for use with a consensus proto-col.As the service matures and gains clients,availability becomes more important;replication and primary elec-tion are then added to an existing design.While this could be done with a library that provides distributed consensus,a lock server makes it easier to maintain exist-ing program structure and communication patterns.For example,to elect a master which then writes to an ex-istingfile server requires adding just two statements and one RPC parameter to an existing system:One would acquire a lock to become master,pass an additional inte-ger(the lock acquisition count)with the write RPC,and add an if-statement to thefile server to reject the write if the acquisition count is lower than the current value(to guard against delayed packets).We have found this tech-nique easier than making existing servers participate in a consensus protocol,and especially so if compatibility must be maintained during a transition period. Second,many of our services that elect a primary or that partition data between their components need a mechanism for advertising the results.This suggests that we should allow clients to store and fetch small quanti-ties of data—that is,to read and write smallfiles.This could be done with a name service,but our experience has been that the lock service itself is well-suited for this task,both because this reduces the number of servers on which a client depends,and because the consistency fea-tures of the protocol are shared.Chubby’s success as a name server owes much to its use of consistent client caching,rather than time-based caching.In particular, we found that developers greatly appreciated not having to choose a cache timeout such as the DNS time-to-live value,which if chosen poorly can lead to high DNS load, or long client fail-over times.Third,a lock-based interface is more familiar to our programmers.Both the replicated state machine of Paxos and the critical sections associated with exclusive locks can provide the programmer with the illusion of sequen-tial programming.However,many programmers have come across locks before,and think they know to use them.Ironically,such programmers are usually wrong, especially when they use locks in a distributed system; few consider the effects of independent machine fail-ures on locks in a system with asynchronous communi-cations.Nevertheless,the apparent familiarity of locks overcomes a hurdle in persuading programmers to use a reliable mechanism for distributed decision making. Last,distributed-consensus algorithms use quorums to make decisions,so they use several replicas to achieve high availability.For example,Chubby itself usually has five replicas in each cell,of which three must be run-ning for the cell to be up.In contrast,if a client system uses a lock service,even a single client can obtain a lock and make progress safely.Thus,a lock service reduces the number of servers needed for a reliable client system to make progress.In a loose sense,one can view the lock service as a way of providing a generic electorate that allows a client system to make decisions correctly when less than a majority of its own members are up. One might imagine solving this last problem in a dif-ferent way:by providing a“consensus service”,using a number of servers to provide the“acceptors”in the Paxos protocol.Like a lock service,a consensus service would allow clients to make progress safely even with only one active client process;a similar technique has been used to reduce the number of state machines needed for Byzan-tine fault tolerance[24].However,assuming a consensus service is not used exclusively to provide locks(which reduces it to a lock service),this approach solves none of the other problems described above.These arguments suggest two key design decisions:•We chose a lock service,as opposed to a library or service for consensus,and•we chose to serve small-files to permit elected pri-maries to advertise themselves and their parameters, rather than build and maintain a second service. Some decisions follow from our expected use and from our environment:•A service advertising its primary via a Chubbyfile may have thousands of clients.Therefore,we must allow thousands of clients to observe thisfile,prefer-ably without needing many servers.•Clients and replicas of a replicated service may wish to know when the service’s primary changes.Thissuggests that an event notification mechanism would be useful to avoid polling.•Even if clients need not pollfiles periodically,many will;this is a consequence of supporting many devel-opers.Thus,caching offiles is desirable.•Our developers are confused by non-intuitive caching semantics,so we prefer consistent caching.•To avoid bothfinancial loss and jail time,we provide security mechanisms,including access control.A choice that may surprise some readers is that we do not expect lock use to befine-grained,in which they might be held only for a short duration(seconds or less); instead,we expect coarse-grained use.For example,an application might use a lock to elect a primary,which would then handle all access to that data for a consider-able time,perhaps hours or days.These two styles of use suggest different requirements from a lock server. Coarse-grained locks impose far less load on the lock server.In particular,the lock-acquisition rate is usu-ally only weakly related to the transaction rate of the client applications.Coarse-grained locks are acquired only rarely,so temporary lock server unavailability de-lays clients less.On the other hand,the transfer of a lock from client to client may require costly recovery proce-dures,so one would not wish a fail-over of a lock server to cause locks to be lost.Thus,it is good for coarse-grained locks to survive lock server failures,there is little concern about the overhead of doing so,and such locks allow many clients to be adequately served by a modest number of lock servers with somewhat lower availability. Fine-grained locks lead to different conclusions.Even brief unavailability of the lock server may cause many clients to stall.Performance and the ability to add new servers at will are of great concern because the trans-action rate at the lock service grows with the combined transaction rate of clients.It can be advantageous to re-duce the overhead of locking by not maintaining locks across lock server failure,and the time penalty for drop-ping locks every so often is not severe because locks are held for short periods.(Clients must be prepared to lose locks during network partitions,so the loss of locks on lock server fail-over introduces no new recovery paths.) Chubby is intended to provide only coarse-grained locking.Fortunately,it is straightforward for clients to implement their ownfine-grained locks tailored to their application.An application might partition its locks into groups and use Chubby’s coarse-grained locks to allocate these lock groups to application-specific lock servers. Little state is needed to maintain thesefine-grain locks; the servers need only keep a non-volatile,monotonically-increasing acquisition counter that is rarely updated. Clients can learn of lost locks at unlock time,and if a simplefixed-length lease is used,the protocol can be simple and efficient.The most important benefits of thisclient processes5servers of a Chubby cellclientapplicationchubbylibraryclientapplicationchubbylibrary...mRPCs m mastermmmqIFigure1:System structurescheme are that our client developers become responsible for the provisioning of the servers needed to support their load,yet are relieved of the complexity of implementing consensus themselves.2.2System structureChubby has two main components that communicate via RPC:a server,and a library that client applications link against;see Figure1.All communication between Chubby clients and the servers is mediated by the client library.An optional third component,a proxy server,is discussed in Section3.1.A Chubby cell consists of a small set of servers(typi-callyfive)known as replicas,placed so as to reduce the likelihood of correlated failure(for example,in different racks).The replicas use a distributed consensus protocol to elect a master;the master must obtain votes from a majority of the replicas,plus promises that those replicas will not elect a different master for an interval of a few seconds known as the master lease.The master lease is periodically renewed by the replicas provided the master continues to win a majority of the vote.The replicas maintain copies of a simple database,but only the master initiates reads and writes of this database. All other replicas simply copy updates from the master, sent using the consensus protocol.Clientsfind the master by sending master location requests to the replicas listed in the DNS.Non-master replicas respond to such requests by returning the iden-tity of the master.Once a client has located the master, the client directs all requests to it either until it ceases to respond,or until it indicates that it is no longer the master.Write requests are propagated via the consensus protocol to all replicas;such requests are acknowledged when the write has reached a majority of the replicas in the cell.Read requests are satisfied by the master alone; this is safe provided the master lease has not expired,as no other master can possibly exist.If a master fails,the other replicas run the election protocol when their master leases expire;a new master will typically be elected in a few seconds.For example,two recent elections took6s and4s,but we see values as high as30s(§4.1).If a replica fails and does not recover for a few hours,a simple replacement system selects a fresh machine from a free pool and starts the lock server binary on it.It then updates the DNS tables,replacing the IP address of the failed replica with that of the new one.The current mas-ter polls the DNS periodically and eventually notices the change.It then updates the list of the cell’s members in the cell’s database;this list is kept consistent across all the members via the normal replication protocol.In the meantime,the new replica obtains a recent copy of the database from a combination of backups stored onfile servers and updates from active replicas.Once the new replica has processed a request that the current master is waiting to commit,the replica is permitted to vote in the elections for new master.2.3Files,directories,and handlesChubby exports afile system interface similar to,but simpler than that of UNIX[22].It consists of a strict tree offiles and directories in the usual way,with name components separated by slashes.A typical name is:/ls/foo/wombat/pouchThe ls prefix is common to all Chubby names,and stands for lock service.The second component(foo)is the name of a Chubby cell;it is resolved to one or more Chubby servers via DNS lookup.A special cell name local indicates that the client’s local Chubby cell should be used;this is usually one in the same building and thus the one most likely to be accessible.The remain-der of the name,/wombat/pouch,is interpreted within the named Chubby cell.Again following UNIX,each di-rectory contains a list of childfiles and directories,while eachfile contains a sequence of uninterpreted bytes. Because Chubby’s naming structure resembles afile system,we were able to make it available to applications both with its own specialized API,and via interfaces used by our otherfile systems,such as the Google File System.This significantly reduced the effort needed to write basic browsing and name space manipulation tools, and reduced the need to educate casual Chubby users. The design differs from UNIX in a ways that ease dis-tribution.To allow thefiles in different directories to be served from different Chubby masters,we do not expose operations that can movefiles from one directory to an-other,we do not maintain directory modified times,and we avoid path-dependent permission semantics(that is, access to afile is controlled by the permissions on the file itself rather than on directories on the path leading to thefile).To make it easier to cachefile meta-data,the system does not reveal last-access times.The name space contains onlyfiles and directories, collectively called nodes.Every such node has only one name within its cell;there are no symbolic or hard links.Nodes may be either permanent or ephemeral.Any node may be deleted explicitly,but ephemeral nodes are also deleted if no client has them open(and,for directo-ries,they are empty).Ephemeralfiles are used as tempo-raryfiles,and as indicators to others that a client is alive. Any node can act as an advisory reader/writer lock;these locks are described in more detail in Section2.4.Each node has various meta-data,including three names of access control lists(ACLs)used to control reading,writing and changing the ACL names for the node.Unless overridden,a node inherits the ACL names of its parent directory on creation.ACLs are themselves files located in an ACL directory,which is a well-known part of the cell’s local name space.These ACLfiles con-sist of simple lists of names of principals;readers may be reminded of Plan9’s groups[21].Thus,iffile F’s write ACL name is foo,and the ACL directory contains afile foo that contains an entry bar,then user bar is permit-ted to write ers are authenticated by a mechanism built into the RPC system.Because Chubby’s ACLs are simplyfiles,they are automatically available to other ser-vices that wish to use similar access control mechanisms. The per-node meta-data includes four monotonically-increasing64-bit numbers that allow clients to detect changes easily:•an instance number;greater than the instance number of any previous node with the same name.•a content generation number(files only);this in-creases when thefile’s contents are written.•a lock generation number;this increases when the node’s lock transitions from free to held.•an ACL generation number;this increases when the node’s ACL names are written.Chubby also exposes a64-bitfile-content checksum so clients may tell whetherfiles differ.Clients open nodes to obtain handles that are analo-gous to UNIXfile descriptors.Handles include:•check digits that prevent clients from creating or guessing handles,so full access control checks need be performed only when handles are created(com-pare with UNIX,which checks its permissions bits at open time,but not at each read/write becausefile de-scriptors cannot be forged).•a sequence number that allows a master to tell whethera handle was generated by it or by a previous master.•mode information provided at open time to allow the master to recreate its state if an old handle is presented to a newly restarted master.2.4Locks and sequencersEach Chubbyfile and directory can act as a reader-writer lock:either one client handle may hold the lock in exclu-sive(writer)mode,or any number of client handles mayhold the lock in shared(reader)mode.Like the mutexes known to most programmers,locks are advisory.That is,they conflict only with other attempts to acquire the same lock:holding a lock called F neither is necessary to access thefile F,nor prevents other clients from do-ing so.We rejected mandatory locks,which make locked objects inaccessible to clients not holding their locks:•Chubby locks often protect resources implemented by other services,rather than just thefile associated with the lock.To enforce mandatory locking in a meaning-ful way would have required us to make more exten-sive modification of these services.•We did not wish to force users to shut down appli-cations when they needed to access lockedfiles for debugging or administrative purposes.In a complex system,it is harder to use the approach employed on most personal computers,where administrative soft-ware can break mandatory locks simply by instructing the user to shut down his applications or to reboot.•Our developers perform error checking in the conven-tional way,by writing assertions such as“lock X is held”,so they benefit little from mandatory checks.Buggy or malicious processes have many opportuni-ties to corrupt data when locks are not held,so wefind the extra guards provided by mandatory locking to be of no significant value.In Chubby,acquiring a lock in either mode requires write permission so that an unprivileged reader cannot prevent a writer from making progress.Locking is complex in distributed systems because communication is typically uncertain,and processes may fail independently.Thus,a process holding a lock L may issue a request R,but then fail.Another process may ac-quire L and perform some action before R arrives at its destination.If R later arrives,it may be acted on without the protection of L,and potentially on inconsistent data. The problem of receiving messages out of order has been well studied;solutions include virtual time[11],and vir-tual synchrony[1],which avoids the problem by ensuring that messages are processed in an order consistent with the observations of every participant.It is costly to introduce sequence numbers into all the interactions in an existing complex system.Instead, Chubby provides a means by which sequence numbers can be introduced into only those interactions that make use of locks.At any time,a lock holder may request a se-quencer,an opaque byte-string that describes the state of the lock immediately after acquisition.It contains the name of the lock,the mode in which it was acquired (exclusive or shared),and the lock generation number. The client passes the sequencer to servers(such asfile servers)if it expects the operation to be protected by the lock.The recipient server is expected to test whether the sequencer is still valid and has the appropriate mode;if not,it should reject the request.The validity of a sequencer can be checked against the server’s Chubby cache or,if the server does not wish to maintain a ses-sion with Chubby,against the most recent sequencer that the server has observed.The sequencer mechanism re-quires only the addition of a string to affected messages, and is easily explained to our developers.Although wefind sequencers simple to use,important protocols evolve slowly.Chubby therefore provides an imperfect but easier mechanism to reduce the risk of de-layed or re-ordered requests to servers that do not sup-port sequencers.If a client releases a lock in the normal way,it is immediately available for other clients to claim, as one would expect.However,if a lock becomes free because the holder has failed or become inaccessible, the lock server will prevent other clients from claiming the lock for a period called the lock-delay.Clients may specify any lock-delay up to some bound,currently one minute;this limit prevents a faulty client from making a lock(and thus some resource)unavailable for an arbitrar-ily long time.While imperfect,the lock-delay protects unmodified servers and clients from everyday problems caused by message delays and restarts.2.5EventsChubby clients may subscribe to a range of events when they create a handle.These events are delivered to the client asynchronously via an up-call from the Chubby li-brary.Events include:•file contents modified—often used to monitor the lo-cation of a service advertised via thefile.•child node added,removed,or modified—used to im-plement mirroring(§2.12).(In addition to allowing newfiles to be discovered,returning events for child nodes makes it possible to monitor ephemeralfiles without affecting their reference counts.)•Chubby master failed over—warns clients that other events may have been lost,so data must be rescanned.•a handle(and its lock)has become invalid—this typi-cally suggests a communications problem.•lock acquired—can be used to determine when a pri-mary has been elected.•conflicting lock request from another client—allows the caching of locks.Events are delivered after the corresponding action has taken place.Thus,if a client is informed thatfile contents have changed,it is guaranteed to see the new data(or data that is yet more recent)if it subsequently reads thefile. The last two events mentioned are rarely used,and with hindsight could have been omitted.After primary election for example,clients typically need to commu-nicate with the new primary,rather than simply know that a primary exists;thus,they wait for afile modifi-cation event indicating that the new primary has written its address in afile.The conflicting lock event in theory permits clients to cache data held on other servers,using Chubby locks to maintain cache consistency.A notifi-cation of a conflicting lock request would tell a client to finish using data associated with the lock:it wouldfinish pending operations,flush modifications to a home loca-tion,discard cached data,and release.So far,no one has adopted this style of use.2.6APIClients see a Chubby handle as a pointer to an opaque structure that supports various operations.Handles are created only by Open(),and destroyed with Close(). Open()opens a namedfile or directory to produce a handle,analogous to a UNIXfile descriptor.Only this call takes a node name;all others operate on handles. The name is evaluated relative to an existing directory handle;the library provides a handle on”/”that is always valid.Directory handles avoid the difficulties of using a program-wide current directory in a multi-threaded pro-gram that contains many layers of abstraction[18].The client indicates various options:•how the handle will be used(reading;writing and locking;changing the ACL);the handle is created only if the client has the appropriate permissions.•events that should be delivered(see§2.5).•the lock-delay(§2.4).•whether a newfile or directory should(or must)be created.If afile is created,the caller may supply ini-tial contents and initial ACL names.The return value indicates whether thefile was in fact created.Close()closes an open handle.Further use of the han-dle is not permitted.This call never fails.A related call Poison()causes outstanding and subsequent operations on the handle to fail without closing it;this allows a client to cancel Chubby calls made by other threads without fear of deallocating the memory being accessed by them. The main calls that act on a handle are: GetContentsAndStat()returns both the contents and meta-data of afile.The contents of afile are read atom-ically and in their entirety.We avoided partial reads and writes to discourage largefiles.A related call GetStat() returns just the meta-data,while ReadDir()returns the names and meta-data for the children of a directory. SetContents()writes the contents of afile.Option-ally,the client may provide a content generation number to allow the client to simulate compare-and-swap on a file;the contents are changed only if the generation num-ber is current.The contents of afile are always written atomically and in their entirety.A related call SetACL() performs a similar operation on the ACL names associ-ated with the node.Delete()deletes the node if it has no children. Acquire(),TryAcquire(),Release()acquire and release locks.GetSequencer()returns a sequencer(§2.4)that de-scribes any lock held by this handle.SetSequencer()associates a sequencer with a handle. Subsequent operations on the handle fail if the sequencer is no longer valid.CheckSequencer()checks whether a sequencer is valid(see§2.4).Calls fail if the node has been deleted since the han-dle was created,even if thefile has been subsequently recreated.That is,a handle is associated with an instance of afile,rather than with afile name.Chubby may ap-ply access control checks on any call,but always checks Open()calls(see§2.3).All the calls above take an operation parameter in ad-dition to any others needed by the call itself.The oper-ation parameter holds data and control information that may be associated with any call.In particular,via the operation parameter the client may:•supply a callback to make the call asynchronous,•wait for the completion of such a call,and/or •obtain extended error and diagnostic information. Clients can use this API to perform primary election as follows:All potential primaries open the lockfile and attempt to acquire the lock.One succeeds and becomes the primary,while the others act as replicas.The primary writes its identity into the lockfile with SetContents() so that it can be found by clients and replicas,which read thefile with GetContentsAndStat(),perhaps in response to afile-modification event(§2.5).Ideally, the primary obtains a sequencer with GetSequencer(), which it then passes to servers it communicates with; they should confirm with CheckSequencer()that it is still the primary.A lock-delay may be used with services that cannot check sequencers(§2.4).2.7CachingTo reduce read traffic,Chubby clients cachefile data and node meta-data(includingfile absence)in a consis-tent,write-through cache held in memory.The cache is maintained by a lease mechanism described below,and kept consistent by invalidations sent by the master,which keeps a list of what each client may be caching.The pro-tocol ensures that clients see either a consistent view of Chubby state,or an error.Whenfile data or meta-data is to be changed,the mod-ification is blocked while the master sends invalidations for the data to every client that may have cached it;this mechanism sits on top of KeepAlive RPCs,discussed more fully in the next section.On receipt of an invali-dation,a clientflushes the invalidated state and acknowl-。
绿盾信息安全管理软件使用手册100305

绿盾信息安全管理软件使用说明(版本号:绿盾使用说明_V2.00.100305)目录1前言 (5)2安装配置说明 (6)2.1 系统要求 (6)2.2 安装配置步骤 (6)2.2.1 安装服务端、控制台程序 (6)2.2.2 安装终端程序 (8)2.2.2.1 安装过程有界面提示 (9)2.2.2.2 安装过程无界面提示 (10)2.3 系统初始化配置 (13)2.3.1 登录控制台 (14)2.3.2 设置企业密钥 (15)2.3.3 创建终端操作员 (16)3使用手册 (20)3.1 终端管理 (20)3.1.1 分组管理 (20)3.1.1.1 创建分组 (21)3.1.1.2 分组改名 (22)3.1.1.3 分组删除 (23)3.1.2 终端管理 (24)3.1.2.1 更改终端所属分组 (24)3.1.2.2 更改终端的名称 (24)3.1.2.3 如何删除终端用户 (25)3.1.2.4 如何远程升级终端程序 (27)3.1.2.5 如何设置终端的数据缓存时间 (28)3.2 文件加密模块 (28)3.2.1 前提条件 (28)3.2.2 企业密钥 (28)3.2.2.1 企业密钥的作用 (28)3.2.2.2 如何修改企业密钥 (29)3.2.2.3 如何导入导出企业密钥 (29)3.2.3 终端类型 (30)3.2.3.1 终端类型的作用 (30)3.2.3.2 终端类型的添加、修改、删除操作 (33)3.2.4 终端操作员 (35)3.2.4.1 为什么需要终端操作员 (35)3.2.4.2 终端操作员的添加、修改、删除 (38)3.2.5 如何查看文件操作记录 (40)3.2.6 如何过滤部分文件操作记录 (41)3.2.7 如何去除文件加密功能 (42)3.2.8 离线策略 (43)3.2.8.2 离线策略的生成和导入 (44)3.2.9 外发终端 (45)3.2.9.1 外发终端的作用 (45)3.2.9.2 如何添加外发终端 (46)3.2.10 文件备份记录 (47)3.2.10.1 文件备份记录的作用 (47)3.2.10.2 如何查看文件备份记录 (47)3.2.10.3 如何查看备份文件内容 (48)3.2.11 文件解密记录 (49)3.2.11.1 如何查看文件解密和文件外发记录 (49)3.2.11.2 如何查看文件批量加密和批量解密记录 (49)3.2.11.3 如何查看解密文件、外发文件内容 (50)3.2.12 打印内容监控 (51)3.2.13 全盘加密 (52)3.2.13.1 全盘加密的作用 (52)3.2.13.2 如何全盘加密 (52)3.2.14 如何查看离线申请日志 (53)3.2.15 文件外发策略 (54)3.2.16 特殊目录设置 (55)3.3 外网管理模块 (57)3.3.1 网页浏览监控 (57)3.3.2 显示语言的切换 (58)3.3.3 上网规则 (59)3.3.4 流量统计 (60)3.3.5 邮件监控 (61)3.4 内网管理模块 (62)3.4.1 现场观察 (62)3.4.1.1 实时日志 (62)3.4.1.2 远程进程,远程服务管理器,软件清单 (63)3.4.2 屏幕监控模块 (65)3.4.2.1 屏幕连续追踪 (65)3.4.2.2 屏幕回放 (65)3.4.2.3 屏幕监控的相关设置 (66)3.4.2.4 如何过滤屏幕录像 (67)3.4.2.5 注意事项 (67)3.4.3 应用程序模块 (68)3.4.3.1 程序启动停止记录 (68)3.4.3.2 窗口标题日志 (69)3.4.3.3 应用程序统计 (69)3.4.3.4 应用程序限制 (70)3.4.4 聊天监控模块 (72)3.4.4.1 聊天监视 (72)3.4.4.2 如何导出聊天内容 (73)3.4.5 软硬件变更、打印机日志 (74)3.4.5.1 软硬件配置 (74)3.4.5.3 软件改变日志 (78)3.4.5.4 打印机日志 (78)3.4.5.5 设备限制 (79)3.4.6 远程协助、远程控制 (80)3.4.7 ARP防火墙 (81)3.4.8 报警模块 (81)3.4.9 清除临时文件 (82)3.5 管理员 (83)3.6 注册 (83)3.7 其他操作说明 (84)3.7.1 如何隐藏控制台界面 (84)3.7.2 如何修改密码 (84)3.7.3 如何获得帮助信息 (85)1前言绿盾信息安全管理软件(以下简称:绿盾)是一款信息安全管理软件,用来保护企业内部文档不外泄,规范员工的计算机操作行为。
常用工具软件试题库

《常用工具软件》考试题库一.判斷題(毎小題1分,共10分)1. Realone Player不支持多节目连续播笊。
(X)2. 网斤快车可以上传和下教文件o (V)3. Internet ± Hi有电子用户的地址都采用同样的格式:用户名Ittgo (V)4. Adobe Acrobat Reader 可以解压缩文件。
(X )5. ACDSee是目前最逍行的数字图像处理軟件,它能广泛应用于图片的菇加、管理、训览、优化,甚至和他人的分?o(V)6. 天网肪火晴的拦則能是指敷据包无法进入或出去。
(X)7.Symantec Ghost可以实规数据修复。
(X )8•用户可以向金山词8(词库中济ID没有收录的中、英文单词。
(V)9•系统长时间便用之后,会留下一堆堆垃圾文件,使系统变得柑当懈肿,isliiO大为下睡, 但是系貌不会颛繁出錯甚至死机。
(V)10.在使用FlashFXP «件下戟网络中的FTP资瀾时,只需拿握FTP ®务器的URL地址即可。
(V)11 •在安装18星肪火埼时,IF1版本的端星肪火墙无需HISo(X)12.压编文件管理工具WinRAR只能压缩文件,不能对文件2H亍解压。
(X)13•在便用Virtual CD H ,映像文件是不能祓Windows资瀾管理器直接读取的,必须从Virtual CD 中ISUJo (V)14•在用Nero-Burning Rom軟件制作CD时,可暮数襦文件从本堆资源管理器中拖入了刻录机虛扭贯源管理器中。
(X)15.趙级解閒3000能截取当甫视顔窗口中的图像存为图形文件。
(V)16 •用MSN W天时,可以憶身登录。
(V)17、ACDSee是目前最流行的数字图像处理軟件,它能广泛应用于图片的获取、管理、浏览、优化,甚至和他人的分?o(V)18、病毒不属于廿算机軟件(x)19、优化大师就是止系筑运行后段有垃圾文件(x)20、注册表頁接影响系统运行的稳定性(V)21、淸理注JI表就是删除注IB表中无用软件的注H信息(x)22、360杀毒不能对单f文件进行菊毒查杀(x)23、具軟件便用的領喷不同,但是一般都色含有标證栏、菜单栏、工具栏、狀态栏、工作Eo (V)24、在进行实验操作»,为了不破坏现有的操作系躱以及相关设置,Sif]可以使用虔抵机软fto (V)25、在便用虛抓柄的时侯,按址盘右边的ALT可£1在虚折机和惜主机之间幼换。
妙计破解WinRAR
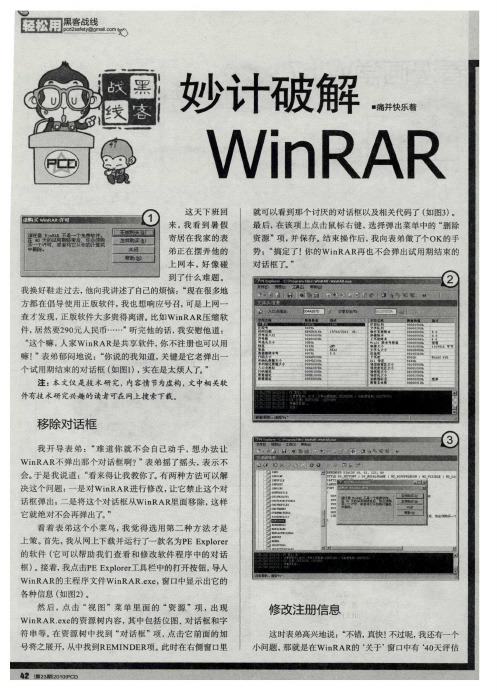
图4 ?” 点 开 看 ) 我
了一下 , 后 对 他 然
钮 , 在 弹 出窗 口中点击 “ ” 钮 , 结 束 了wiRAR 再 是 按 就 n 注
册 信息 的修 改 。
H Z ‘I . - u “J : 十 =; ・ V 爪 寺 怕这 些字 暴露 注册 情 况 , 你直 接用 刚才的 方法 把 ‘ ’ 口 关于 窗
谁 知表弟 马上 反对 道 :“ 不行 不行, 要你 把它们 改成 我 我 的名字 , 样开 学后我就 可 以找 同学 炫耀 了a 唉, 这 ” 瞧表 弟这虚
jt 古 甘 日 — 工 +卜 口 .、 r LI m 、 L —7 —r 喈 “^H 嗣
麻 ! 个 女孩 儿 , 还 真 敢 拿 给 同学 们 看 啊 ? 表 弟 委屈 地 像 你 回道 :“ 有 什么 办 法 , 妈 一直 这 样 叫我 , 想 改但 改 不 我 爸 我
J
" d JL . LJ L :、 , 1 lh “ n血 L ^ f l l :r , — n
— u '丹 , I 匕 ‘ 叮
,、 .
0
VL 7、思 勺 僧
J—
r'
坦
:
U示
. 援
你 非要 修改 , 方法 倒有一个 , 试试 吧 说 完 , 同样 在 前面P ” 我 E E p rr xl e中的WiR Ree o n A . 资源树 x 里 点 击 “ 话 框 ” , 中找 到 骚 嘲 戮 鹱 鹾 鳞 醚 对 项 从 搿 躐 鹈 = 巨 黑
来 , 看 到 暑 假 我 寄居 在 我 家 的表 弟正 在 摆 弄他 的
世界最强大的加密软件PGP中文版7页word文档

世界最强大的加密软件PGP中文版7页word文档世界最强大的加密软件PGP中文版世界最强大的加密软件PGP中文版2019-05-17 19:15PGP软件简介:你的公司可能有许多方法来保护信息。
例如说,可能利用上锁的门,在建筑物里隔出一个封闭的空间,然后只允许被授权的人出入;公司也可以要求员工必须使用个人账号以及密码来登录网络,同时架设防火墙服务器来监控所有公司内部与外部间的信息传输。
这些机制都是为了要加强信息的保密。
PGP能够提供独立计算机上的信息保护功能,使得这个保密系统更加完备。
它提供了这些功能:数据加密,包括电子邮件、任何储存起来的文件、还有即时通讯(例如ICQ之类)。
数据加密功能让使用者可以保护他们发送的信息─像是电子邮件─还有他们储存在计算机上的信息。
文件和信息通过使用者的密钥,通过复杂的算法运算后编码,只有它们的接收人才能把这些文件和信息解码。
现在你应该对PGP已经有个大概的了解了,现在让我们看看PGP实际上具有哪些功能:PGP使用加密以及效验的方式,提供了多种的功能和工具,帮助你保证你的电子邮件、文件、磁盘、以及网络通讯的安全。
你可以通过PGP做这些事:1、在任何软件中进行加密/签名以及解密/效验。
通过PGP选项和电子邮件插件,你可以在任何软件当中使用PGP的功能。
2、创建以及管理密钥。
使用PGPkeys来创建、查看、和维护你自己的PGP 密钥对;以及把任何人的公钥加入你的公钥库中。
3、创建自解密压缩文档(self-decrypting archives,SDA)。
你可以建立一个自动解密的可执行文件。
任何人不需要事先安装PGP,只要得知该文件的加密密码,就可以把这个文件解密。
这个功能尤其在需要把文件发送给没有安装PGP 的人的时候特别好用。
并且,此功能还能对内嵌其中的文件进行压缩,压缩率与ZIP 相似,比RAR略低(某些时候略高,比如含有大量文本)。
总的来说,该功能是相当出色的。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
固如金汤将RAR文件保卫起来
经常使用WinRAR的朋友都知道,WinRAR除了用来压缩或解压缩文件外,还可以当作加密软件来使用。
除了平时大家简单地将RAR文件加上密码之外,我们还有很多关于RAR密码的小技巧,可以帮你更好地把RAR保存起来。
01 中文口令更安全
一般情况下我们都是输入英文字母、数字或其他特殊符号为密码,不知道你是否想过使用汉字作为密码?那样保密性无疑会更好!不过该如何在RAR中输入汉字密码呢?
第一步:当我们右击要压缩的文件,然后选择弹出菜单中的“添加到档案文件”命令后,就会打开WinRAR的“压缩包名称和参数”窗口,选中“高级”选项卡,点击“设置口令”按钮。
第二步:在“带口令存档”窗口中勾选“显示口令”复选框之后,就可以很方便地在“输入口令”框内输入汉字密码了。
在解密的时候要在任意编辑器如记事本中输入作为口
令的汉字,然后粘贴到密码输入框内。
02 让密码固若金汤
现在,针对WinRAR密码的破解软件层出不穷,不管密码设置得再长、再复杂,也难免成为某些暴力破解软件的猎物。
那么究竟怎么做才能让我们的WinRAR加密文件固若金汤呢?
用破解软件破解加密文件时,一般都要先指定一个目标文件,接下来根据字典使用穷举法来破解设置好的密码。
如果我们把多个文件压缩在一起,然后分别给它们设置密码,破解软件就无能为力了。
具体操作步骤如下:
第一步:准备好要加密的重要文件和几个无关紧要的文件。
第二步:将重要文件按照平常的步骤压缩,并设置密码。
第三步:在WinRAR操作界面中,打开刚才已经压缩完成的加密文件,选择“命令→添加文件到档案文件”选项。
第四步:在“选择添加文件”窗体中点选准备好的其他文件,“确定”后回到“档案文件名字和参数”对话框。
第五步:在“高级”选项卡中设置一个不同的密码。
最后完成压缩即可。
试着打开压缩文件,是否每一个文件都有表示加密的星号存在?打开每个文件都需要输入先前设置的相应密码。
最重要的是,一般的解密软件根本对付不了按照这种方法加密
的文件。
这种方法对于Zip文件的加密同样有效。
03 避免反复输入密码
当我们用WinRAR对文件进行加密后,每次执行压缩包里的程序时,它都会让我们输入密码,当文件很多时会使人不胜其烦。
要想让WinRAR只在打开其中第一个文件时要求输入密码,只要第一次通过密码验证,以后就直接查看加密压缩包里面的其他文件,我们可以这样做:在打开加密的压缩包以后,用鼠标点击“文件”菜单里的“口令”命令,然后输入正确的密码,就可以一次解决问题。
04 给压缩文件自动加上密码
有时需要创建很多个加密压缩包,如果一个一个地来设置密码,那效率也太低了。
要是能够在生成压缩文件的同时自动加上一个自己设定的密码,那该多好!利用WinRAR的设置默认的压缩选项可达到这个目的。
第一步:点击菜单中的“选项→设置”,在弹出的设置窗口中选择“压缩选项”选项卡。
第二步:点击“创建默认配置”按钮,在“设置默认压缩选项”的窗口中选择“高级”选项卡。
第三步:单击“设置口令”按钮,输入自己的密码,你还可根据需要来选择是否加密文件名,连续按两次确定,出现询问是否保存密码时按“是”保存设置即可。
这样设置后,每次使用右键快捷菜单来创建压缩文件时,程序都会自动地添加你输入的默认密码,节省了不少时间。
第四步:所有压缩文件创建完成后,再按以上步骤,即单击“选项→设置→压缩→创建默认配置→高级→设置密码”,将密码保持为空,单击“确定”。
这样,无论别人在你的电脑还是其他电脑打开你的压缩文件时都必须输入你刚才的密码才能打开。
