GUET计算机网络习题课2
计算机网络教程知识点和习题

计算机网络教程知识点和习题B类和C类地址都是单播地址,D类地址用于多播,E类地址保留为以后用。
划分子网:1个C类地址空间仅能容纳254台主机,划分子网的编址方法大大减小了对A、B类地址空间的浪费。
截图3.CIDR:无分类域间选择(CIDR)无分类编址:1.网络地址=子网掩码ANDIP地址2.同样的IP地址和不同的子网掩码可以得出相同的网络地址,但不同的子网掩码的效果是不同的,最大地址是一样的,各自容纳的最大主机数是不一样的。
3.斜线记法(CIDR记法)中,斜线后面的数字就是地址掩码中1的个数。
CIDR记法提供了IP地址,子网掩码,能分配几个IP地址,也就是地址空间大小,并能计算最大,最小地址。
看书4.ARP协议:1.IP地址放在IP数据报的首部,而物理地址则放在MAC帧的首部。
在网络层和网络层以上使用的是IP地址,而数据链路层及以下使用的是物理地址。
2.地址解析协议ARP解决知道IP地址求物理地址,逆地址解析协议RARP解决知道物理地址求IP地址的。
3.每一个主机都设有一个ARP高速缓存,里面有所在的局域网上的各主机和路由器的IP地址到硬件地址的映射表。
4.ARP是解决同一个局域网上的主机或路由器的IP地址和硬件地址的映射问题。
否则只能通过路由器了。
5.RARP协议:第六章DHCP协议中介绍6.IP首部:1.一个IP数据报由首部和数据两部分组成。
首部的前一部分是固定长度,共20字节,是所有IP数据报必须具有的。
2.片偏移是起始位数除以8,IP数据报结构,截图7.路由表:看书8.默认路由:看书9.ICMP协议的应用:1.ICMP报文作为IP层数据报的数据,加上数据报的首部,组成IP数据报发送出去。
ICMP协议是IP层的协议。
2.ICMP 差错报告报文:终点不可达,源点抑制,超时,参数问题,改变路由(重定向),ICMP询问报文:回送请求和回答,时间戳请求和回答。
10.RIP协议:1.因特网把路由选择协议划分为内部网关协议(RIP和OSPF等)和外部网关协议(BGP)。
2.计算机网络原理第二章课后习题及答案

第二章1. (Q2)For a communication session between a pair of processes, which process is the client and which is the server?Answer:The process which initiates the communication is the client; the process that waits to be contacted is the server..2. (Q3) What is the difference between network architecture and application architecture?Answer:Network architecture refers to the organization of the communication processintolayers (e.g., the five-layer Internet architecture). Application architecture, on the other hand, is designed by an application developer and dictates the broadstructure of the application (e.g., client-server or P2P)3. (Q4) What information is used by a process running on one host to identify a process running on another host?Answer: The IP address of the destination host and the port number of the destinationsocket.4. (Q6) Referring to Figure 2.4, we see that none of the application listed in Figure 2.4 requires both no data loss and timing. Can you conceive of an application that requires no data loss and that is also highly time-sensitive?Answer: There are no good example of an application that requires no data loss and timing.If you know of one, send an e-mail to the authors5. (Q9) Why do HTTP, FTP, SMTP, and POP3 run on top of TCP rather than on UDP?Answer: The applications associated with those protocols require that all application databe received in the correct order and without gaps. TCP provides this servicewhereas UDP does not.6. (Q11) What is meant by a handshaking protocol?Answer: A protocol uses handshaking if the two communicating entities first exchangecontrol packets before sending data to each other. SMTP uses handshaking at theapplication layer whereas HTTP does not.7. (Q13) Telnet into a Web server and send a multiline request message. Include in the request message the If-modified-since: header line to force a response message with the 304 Not Modified status code.Answer: Issued the following command (in Windows command prompt) followed by theHTTP GET message to the “” web server:> telnet 80Since the index.html page in this web server was not modified since Fri, 18 May2007 09:23:34 GMT, the following output was displayed when the abovecommands were issued on Sat, 19 May 2007. Note that the first 4 lines are theGET message and header lines input by the user and the next 4 lines (startingfrom HTTP/1.1 304 Not Modified) is the response from the web server.8. (Q14) Consider an e-commerce site that wants to keep a purchase record for each of its customers. Describe how this can be done with cookies.Answer: When the user first visits the site, the site returns a cookie number. This cookie number is stored on the user’s host and is managed by the browser. During each subsequent visit (and purchase), the browser sends the cookie number back to the site. Thus the site knows when this user (more precisely, this browser) is visiting the site.9. (Q15) Suppose Alice, with a Web-based e-mail account (such as Hotmail or gmail), sends a message to Bob, who accesses his mail from his mail server using POP3. Discuss how the message gets from Alice’s host to Bob’s host. Be sure to list the series of application-layer protocols that are used to move the message between the two hosts.Answer: Message is sent from Alice’s host to her mail server over HTTP. Alice’s mail server then sends the message to Bob’s mail server over SMTP. Bob then transfers the message from his mail server to his host over POP3.10. (Q10) Recall that TCP can be enhanced with SSL to provide process-to-process securityservices, including encryption. Does SSL operate at the transport layer or the application layer? If the application developer wants TCP to be enhanced with SSL, what does the developer have to do?Answer: SSL operates at the application layer. The SSL socket takes unencrypted data fromthe application layer, encrypts it and then passes it to the TCP socket. If theapplication developer wants TCP to be enhanced with SSL, she has to include theSSL code in the application.11. (Q16) Print out the header of an e-mail message you have recently received. How manyReceived: header lines are there? Analyze each of the header lines in the message.Answer: from 65.54.246.203 (EHLO )Received:(65.54.246.203) by with SMTP; Sat, 19 May 2007 16:53:51 -0700from ([65.55.135.106]) by Received: with Microsoft SMTPSVC(6.0.3790.2668); Sat, 19 May 2007 16:52:42 -0700 Received: from mail pickup service by with Microsoft SMTPSVC; Sat,19 May 2007 16:52:41 -0700Message-ID: <*******************************************>Received: from 65.55.135.123 by with HTTP; Sat, 19 May 2007 23:52:36 GMTFrom: "prithuladhungel"<***************************>To: ******************Bcc:Subject: Test mailDate: Sat, 19 May 2007 23:52:36 +0000Mime-Version:1.0Content-Type: Text/html; format=flowedReturn-Path: ***************************Figure: A sample mail message headerReceived: This header field indicates the sequence in which the SMTP serverssend and receive the mail message including the respective timestamps.In this example there are 4 “Received:” header lines. This means the mailmessage passed through 5 different SMTP servers before being delivered to thereceiver’s mail box. The la st (forth) “Received:” header indicates the mailmessage flow from the SMTP server of the sender to the second SMTP server inthe chain of servers. The sender’s SMTP server is at address 65.55.135.123 andthe second SMTP server in the chain is .The third “Received:” header indicates the mail message flow from the secondSMTP server in the chain to the third server, and so on.Finally, the first “Received:” header indicates the flow of the mail message fromthe forth SMTP server to t he last SMTP server (i.e. the receiver’s mail server) inthe chain.Message-id: The message has been given this*************************************************(bybay0-omc3-s3.bay0.hotmail.com. Message-id is a unique string assigned by the mail systemwhen the message is first created.From: This indicates the email address of the sender of the mail. In the givenexample,**************************************To: This field indicates the email address of the receiver of the mail. In theexample, the ****************************Subject: This gives the subject of the mail (if any specified by the sender). In theexample, the subject specified by the sender is “Test mail”Date: The date and time when the mail was sent by the sender. In the example,the sender sent the mail on 19th May 2007, at time 23:52:36 GMT.Mime-version: MIME version used for the mail. In the example, it is 1.0.Content-type: The type of content in the body of the mail message. In theexample, it is “text/html”.Return-Path: This specifies the email address to which the mail will be sent if thereceiver of this mail wants t o reply to the sender. This is also used by the sender’smail server for bouncing back undeliverable mail messages of mailer-daemonerror messages. In the example, the return path is“***************************”.12. (Q18) Is it possible for an organizat ion’s Web server and mail server to have exactly thesame alias for a hostname (for example, )? What would be the type for the RR that contains the hostname of the mail server?Answer: Yes an organization’s mail server and Web server can have the sa me alias for ahost name. The MX record is used to map the mail server’s host name to its IPaddress.13. (Q19) Why is it said that FTP sends control information “out-of-band”?Answer:FTP uses two parallel TCP connections, one connection for sending controlinformation (such as a request to transfer a file) and another connection foractually transferring the file. Because the control information is not sent over thesame connection that the file is sent over, FTP sends control information out ofband.14. (P6) Consider an HTTP client that wants to retrieve a Web document at a given URL. The IPaddress of the HTTP server is initially unknown. What transport and application-layer protocols besides HTTP are needed in this scenario?Answer:Application layer protocols: DNS and HTTPTransport layer protocols: UDP for DNS; TCP for HTTP15. (P9) Consider Figure2.12, for which there is an institutional network connected to theInternet. Suppose that the average object size is 900,000 bits and that the average request rate from the institution’s browsers to the origin servers is 10 requests per second. Also suppose that the amount of time it takes from when the router on the Internet side of the access link forwards an HTTP request until it receives the response is two seconds on average (see Section 2.2.5).Model the total average response times as the sum of the average access delay (that is, the delay from Internet router to institution router) and the average Internet delay. For the average access delay, use △/(1-△β), where △is the average time required to send an object over the access link and βis the arrival rate of objects to the access link.a. Find the total average response time.b. Now suppose a cache is installed in the institutional LAN. Suppose the hit rate is 0.6. Findthe total response time.Answer:a.The time to transmit an object of size L over a link or rate R is L/R. The average timeisthe average size of the object divided by R:Δ= (900,000 bits)/(1,500,000 bits/sec) = 0.6 secThe traffic intensity on the link is (1.5 requests/sec)(0.6 sec/request) = 0.9. Thus, theaverage access delay is (0.6 sec)/(1 - 0.9) = 6 seconds. The total average response timeis therefore 6 sec + 2 sec = 8 sec.b.The traffic intensity on the access link is reduced by 40% since the 40% of therequestsare satisfied within the institutional network. Thus the average access delayis(0.6 sec)/[1–(0.6)(0.9)] = 1.2 seconds. The response time is approximately zero iftherequest is satisfied by the cache (which happens with probability 0.4); the averageresponse time is 1.2 sec + 2 sec = 3.2 sec for cache misses (which happens 60% of thetime). So the average response time is (0.4)(0 sec) + (0.6)(3.2 sec) = 1.92 seconds.Thusthe average response time is reduced from 8 sec to 1.92 sec.16. (P12) What is the difference between MAIL FROM: in SMTP and From: in the mail messageitself?Answer: The MAIL FROM: in SMTP is a message from the SMTP client that identifies the senderof the mail message to the SMTP server. TheFrom: on the mail message itself is NOTanSMTP message, but rather is just a line in the body of the mail message.17. (P16) Consider distributing a file of F = 5 Gbits to N peers. The server has an upload rate ofu s = 20 Mbps, and each peer has a download rate of d i =1 Mbps and an upload rate of u. For N = 10, 100, and 1,000 and u = 100 Kbps, 250 Kbps, and 500 Kbps, prepare a chart giving the minimum distribution time for each of the combinations of N and u for both client-server distribution and P2P distribution.Answer:For calculating the minimum distribution time for client-server distribution, we use thefollowing formula:D cs = max {NF/u s , F/d min }Similarly, for calculating the minimum distribution time for P2P distribution, we use thefollowing formula:D P 2P = max {F /u s ,F /d min ,NF /( u s + u i n i =1 )} Where,F = 5 Gbits = 5 * 1024 Mbits u s = 20 Mbps d min = d i = 1 MbpsClient Server:N 10 100 1000 200 Kbps10240 51200 512000 u 600 Kbps10240 51200 512000 1Mbps10240 51200 512000Peer to Peer:N 10 100 1000 200 Kbps10240 25904.3 47559.33 U 600 Kbps10240 13029.6 16899.64 1 Mbps10240 10240 10240。
计算机网络技术习题及答案

计算机网络技术习题及答案一、选择题1、在 OSI 参考模型中,物理层的主要功能是()A 数据链路的建立、维护和拆除B 在物理媒体上传输比特流C 确定进程之间通信的性质,以满足用户的需要D 提供可靠的端到端服务答案:B解释:物理层主要负责在物理媒体上传输比特流,也就是将数字信号转换为物理信号进行传输。
2、以下哪种拓扑结构的网络中,任意两个节点之间的通信都需要通过中心节点进行转发()A 星型拓扑B 总线型拓扑C 环型拓扑D 网状拓扑答案:A解释:在星型拓扑结构中,所有节点都连接到一个中心节点,任意两个节点之间的通信都要通过中心节点进行转发。
3、 TCP/IP 模型中,()层负责将数据分组从源主机传输到目的主机。
A 网络接口层B 网际层C 传输层D 应用层答案:B解释:网际层(也称为网络层)的主要功能是将数据分组从源主机通过网络路由到目的主机。
4、在以太网中,使用()协议来解决冲突。
A CSMA/CDB CSMA/CAC PPPD HDLC答案:A解释:CSMA/CD(载波监听多路访问/冲突检测)是以太网中用于解决冲突的协议。
5、 IP 地址 1921681100 属于()类 IP 地址。
A A 类B B 类C C 类D D 类答案:C解释:C 类 IP 地址的范围是 192000 至 223255255255,1921681100 属于 C 类 IP 地址。
二、填空题1、计算机网络按覆盖范围可以分为_____、_____和_____。
答案:局域网、城域网、广域网2、网络协议的三要素是_____、_____和_____。
答案:语法、语义、同步3、在 TCP/IP 体系结构中,HTTP 协议工作在_____层。
答案:应用4、常用的有线传输介质有_____、_____和_____。
答案:双绞线、同轴电缆、光纤5、网络地址 1721600,子网掩码为 255255255192,该子网的可用IP 地址范围是_____至_____。
【精品】计算机网络习题集及答案

第一章概述习题1.什么叫计算机网络?计算机网络主要有哪几类?答:计算网络是一个将分散在各地的计算机、工作站、终端和外部设备等,通过通信线路(或称通信媒体)互相连接在一起,并按照有关协议实现相互通信,资源共享和进行分布处理的综合系统。
计算网络是一些互相连接的、自治的计算机的集合。
计算机网络从不同的角度来看计算机网络分类如下:2.计算机网络经历了哪几个发展阶段?答:计算机网络经历了:1.面向终端的计算机通信网2.分组交换网3.计算机网络体系结构的形成4.Internet等几个阶段。
3.试从多个方面比较电路交换、报文交换和分组交换的主要优缺点。
解:若要连续传送大量的数据,且其传送时间远大于呼叫建立时间,则采用数据通信前预先分配传输带宽的电路交换较为合适。
报文交换和分组交换不需要预先分配传输带宽,在传送实发数据时可提高整个网络的信道利用率。
分组交换比报交换的时延小,但其结点交换机必须具有更强的处理能力。
在电路交换中,只要整个通路中有一段链路不能使用,通信就会中止,而分组交换可选择另一条路由转发分组。
但是电路交换是完全透明的,发送方和接收方可以使用任何比特速率、格式或分帧方法,电信公司不知道也不用关心这些;而分组交换,电信公司决定基本参数。
此外,电路交换基于时间和距离收费,而分组交换基于所传分组的字节数及连接时间收费。
3.试从多个方面比较电路交换、报文交换和分组交换的主要优缺点。
解:若要连续传送大量的数据,且其传送时间远大于呼叫建立时间,则采用数据通信前预先分配传输带宽的电路交换较为合适。
报文交换和分组交换不需要预先分配传输带宽,在传送实发数据时可提高整个网络的信道利用率。
分组交换比报交换的时延小,但其结点交换机必须具有更强的处理能力。
在电路交换中,只要整个通路中有一段链路不能使用,通信就会中止,而分组交换可选择另一条路由转发分组。
但是电路交换是完全透明的,发送方和接收方可以使用任何比特速率、格式或分帧方法,电信公司不知道也不用关心这些;而分组交换,电信公司决定基本参数。
计算机网络课后习题答案中文版
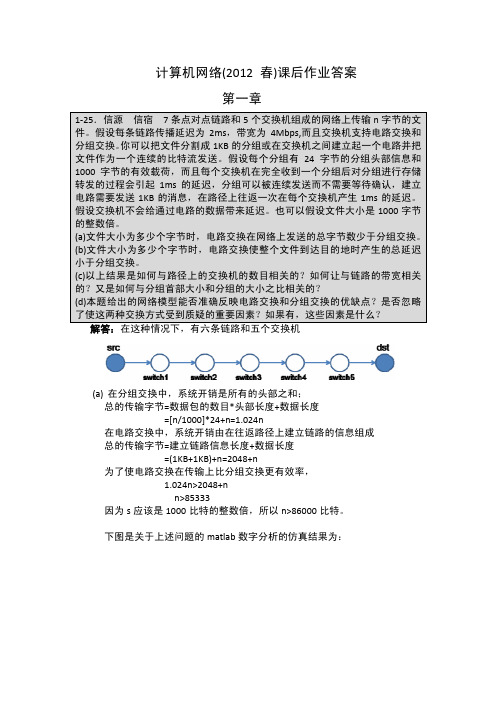
因为没有无序的到达方式,所以 DATA[0] 将永远不会到达。.
(b) MaxSeqNum – 1 = 7 是不充分的 证明:(i) 我们假设发送方发送 { DATA[0] , DATA[1], …, DATA[4] },并且全部到达。
(ii) 接收方发送 ACK[5]作为反馈,接收方的窗口将会移动到{ DATA[5], …, DATA[7]}.
CS: 没有影响
关于上述关于时延的影响的 matlab 仿真结果如下图:
(d)本题给出的网络模型能够准确反映电路交换和分组交换的优缺点。这里也 有很多被忽略了的因素,例如:
(i)交换机的存储量和数据处理能力,这能产生很多的时延; (ii)复杂的网络拓扑结构,这可能带来分组交换的多路径传输。
第二章
2-6.假设一条链路上到达比特序列 1101011111010111110010111110110,给出去掉任
我们将五个 1 之后的 0 用红色表示。 接收的序列: 1101011111010111110010111110110 去掉填充物 0: 1101011111^1011111^01011111^110 在这里,没有连续的七个没有被填充物 0 阻断的 1,因此接收方不能检测出
任何差错。
2-18.假设我们想要传输消息 11001001,并用 CRC 多项式 x3 + 1 防止它出错. (a)使用多项式长除法确定应传输的消息。 (b)假设由于传输链路上的噪声使得消息最左端的比特发生发转。接收方的 CRC
2-44.令 A 和 B 是试图在一个以太网上传输的两个站。每个站有一个准备发送的 帧的稳定队列;A 的帧被编号为 A1、A2,等等,B 的帧类似。令 T=51.2µs 是指 数退避的基本单元 假设 A 和 B 同时想发送帧 1,导致冲突,并分别发生选择退避时间 0*T 和 1*T, 这意味着 A 在竞争中获胜并传输 A1 而 B 等待。在这次传输结束时,B 将试图重 传 B1 而 A 试图传输 A2,这种首次尝试又会冲突,但现在 A 退避 0*T 或 1*T,而 B 退避时间等于 0*T,1*T,2*T,3*T 中之一。 (a).给出第一个冲突后 A 立即在第二次退避竞争中获胜的概率;就是说,A 第一 次选择的退避时间 K*51.2 小于 B 的退避时间; (b) 假设 A 在第二次退避竞争中获胜,A 传输 A3,当传输结束时,在 A 试图传输 A4 而 B 试图再一次传输 B1 时,A 和 B 又一次产生了冲突,给出第一次冲突后 A 立即在第三次退避竞争中获胜的概率; (c) 为 A 在所有余下的退避竞争中获胜的概率给出一个合理的下界; (d) 然后对帧 B1 发生什么?
计算机网络习题册.

5.客户服务器方式与对等通信方式的主要区别是什么?有没有相同的地方?
6.计算机网络有哪些常用的性能指标?
7.收发两端之间的传输距离为1000km ,信号在媒体上的传播速率为2×108m/s。试计算以下两种情况的发送时延和传播时延:
(1每一个子网的网络前缀有多长?
(2每一个子网中有多少个地址?
(3每一个子网的地址是什么?
(4每一个子网可分配给主机使用的最小地址和最大地址是什么?
14.假定网络中的路由器B的路由表有如下的项目(这三列分别表示“目的网络”、“距离”和“下一跳路由器”
N1 7 A
N2 2 B
N6 8 F
N8 4 E
N9 4 F
8.设某路由器建立了如下路由表:
目的网络子网掩码下一跳
128.96.39.0 255.255.255.128接口m0
128.96.39.128 255.255.255.128接口m1
128.96.40.0 255.255.255.128 R2
192.4.153.0 255.255.255.192 R3
3. DHCP使用的运输层端口号是多少,客户端在成功获取地址的过程中使用了哪些DHCP报文?
4.什么是OSPF ,写出OSPF的五个分组类型,并解释每个分组类型的具体作用?
5.画出TCP协议“三次握手原则”的过程?
6.计算机网络拓扑结构有哪几种?并简述每种拓扑结构的特点。
7.在数据传输过程中,若接收方收到发送方送来的信息为10110011010,生成多项式为G (x =x4+x3+1,接收方收到的数据是否正确?
现在B收到从C发来的路由信息(这两列分别表示“目的网络”“距离” :
计算机网络第四版(课后练习+答案)

第 1 章概述1.假设你已经将你的狗Berníe 训练成可以携带一箱3 盒8mm 的磁带,而不是一小瓶内哇地. (当你的磁盘满了的时候,你可能会认为这是一次紧急事件。
)每盒磁带的窑最为7GB 字节;无论你在哪里,狗跑向你的速度是18km/h 。
请问,在什么距离范围内Berníe的数据传输速率会超过一条数据速率为150Mbps的传输线?答:狗能携带21千兆字节或者168千兆位的数据。
18 公里/小时的速度等于0.005 公里/秒,走过x公里的时间为x / 0.005 = 200x秒,产生的数据传输速度为168/200x Gbps或者840 /x Mbps。
因此,与通信线路相比较,若x<5.6 公里,狗有更高的速度。
6. 一个客户·服务器系统使用了卫星网络,卫星的高度为40 000km. 在对一个请求进行响应的时候,最佳情形下的延迟是什么?答:由于请求和应答都必须通过卫星,因此传输总路径长度为160,000千米。
在空气和真空中的光速为300,000 公里/秒,因此最佳的传播延迟为160,000/300,000秒,约533 msec。
9.在一个集中式的二叉树上,有2n -1 个路出器相互连接起来:每个树节点上都布一个路由器。
路由器i 为了与路由器j 进行通信,它要给树的根发送一条消息。
然后树根将消息送下来给j 。
假设所有的路由器对都是等概率出现的,请推导出当n很大时,每条消息的平均跳数的一个近似表达式。
答:这意味着,从路由器到路由器的路径长度相当于路由器到根的两倍。
若在树中,根深度为1,深度为n,从根到第n层需要n-1跳,在该层的路由器为0.50。
从根到n-1 层的路径有router的0.25和n-2跳步。
因此,路径长度l为:18.OSI 的哪一层分别处理以下问题?答:把传输的比特流划分为帧——数据链路层决定使用哪条路径通过子网——网络层.28.一幅图像的分辨率为1024X 768 像素,每个像素用3 字节来表示。
计算机网络习题课修订版

14
习题部分 一、单选题
1.通信子网的主要组成是 B
(A)主机系统和通信链路
(B)网络结点和通信链路
(D)计算机网络和终端
(C)网络体系结构和网络协议
C 2.OSI参考模型的意义是——。
(A)将整个网络功能划分成七个层次 (B)首次提出网络体系结构的概念
(c)建立了标准的网络体系结构
(D)首次提出了网络协议的概念
3. FDDI标准规定MAC帧的数据字段的最大长度为__。 B (B)4500字节 (D)没有上限
27
D 4.下面——网络使用光纤作为传输介质。 (A)10BASE-2 (B)10BASE-5
(C)10BASE-T
(D)10BASE-F
5. 与IEEE802.3(以太网)协议相比,IEEE802.4(令牌总 D 线)协议具有的优点——。 (A)站点都有公平的访问权 (B)几个站点都要发送数据帧之前必须等待时间的最 大值总是确定的 (c)没有最短帧长的限制 (D)以上皆是 D 6. 下面的———协议符合IEEE802.5标准。
D 10.下列说法错误的是——。
(A)电路交换技术在交换结点上无法进行代码转换
(B)虚电路能够保证报文分组的发送次序和接收次序一 致
(c)纠错码的编码效率低于检错码
(D)在同步传输中,收/发端需要保持同步;在异步传 输中,收/发端无需保持同步
18
二、填空题 1.按网络覆盖范围,计算机网络可分类为—— 、 ——和—— 2.电路交换方式在用户开始通信前,必须建立一 物理信道(或物理电路) 条从发送端到接收端的—— 3.计算机网络是——和——密切结合的产物。 4.在面向终端的计算机网络中,实施数字信号和 模拟信号之间的转换设备是_____ 5.Internet为用户提供的主要服务包括电子邮件、 信息浏览(或WWW) 文件传输、远程登录和_____
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
回答: OSI model has seven layers. From bottom to up these layers are: Physical layer, Data link layer, Network layer, Transport layer, Session layer, Presentation layer, Application layer. The physical layer is concerned with transmitting raw bits over a communication channel. The main task of the data link layer is to transform a raw transmission facility into a line that appears free of undetected transmission errors to the network layer. The network layer controls the operation of the subnet. The basic function of the transport layer is to accept data from above, split it up into smaller units if need be, pass these to the network layer, and ensure that the pieces all arrive correctly at the other end. Session layer allows users on different machines to establish sessions between them. Presentation layer is concerned with the syntax and semantics of the information transmitted. Application layer contains a variety of protocols that are commonly needed by users. 2015-1-18 1
2015-1-18
2
3 、 Consider the subnet of the following Figure. The routing table is built using shortest path routing algorithms. Please illustrate the process or list the working nodes (with its distance from the source node along the best known path) in order to building the sink tree using shortest path routing algorithms, assume the process starts out by the source node A.
2015-1-18
5
回答:第20次时TCP拥塞窗口大小等于接收窗口。
2015-1-18
6
5、The data flow was captured and listed below in hexadecimal, context of the data includes ethernet frame header, IP header and transport layer segment, according to the information answer the following questions. 0x0000 E0 05 C5 9C 69 90 00 E0-4C 36 C8 2D 08 00 45 00 ?艤i?郘6?..E. 0x0010 00 53 10 98 00 00 40 11-E0 AD C0 A8 01 64 B7 3C .S.?.@.喹括.d? 0x0020 10 0C 0F A0 1F 40 00 3F-D1 DD 02 21 07 00 17 56 ...?@.?演.!...V 0x0030 F9 00 01 DF 2D 02 00 00-00 01 01 01 00 00 64 86 ?.?.........d? 0x0040 A9 B1 1F 21 EE B4 07 93-FF EF 55 E3 3C 69 5C 33 ┍.!畲.?颱?i\3 0x0050 BD 5B 3F 55 59 00 7E 18-57 65 FF 7C 92 AE 59 96 絒?UY.~.We |挳Y? 0x0060 03
2、Explain the procedure of TCP connection establishment.
回 答 : The TCP connection establishment is 3 way hand-shaking. The procedure is shown as follow:
2015-1-18
7
2015-1-18
8
问题: 1)What is the source address of Ethernet frame in decimal form? 2)What is the length of IP header? 3)What is the source IP address and destination IP address in the network layer? 4) Is this a TCP or UDP protocol in the transport layer? 5) What is the destination port? 回答: 1)00:E0:4C:36:C8:2D 2)0x05 = 20(bytes) 3)source IP address:192.168.1.100 destination IP address:183.60.16.12 4)0x11 -> UDP 5)8000
2015-1-18 12
回答: 1)20 bytes 2)Sequence number:50 5f a9 06 Acknowledgement number:00 00 00 00 3)Source port:0d 28 Destination port:00 15 4)FTP service 5)SYN=1 ACK=0 Means:the source machine initiates a FTP connection request to the destination machine.
2015-1-18 9
7、A router has the following entries in its routing table: Address Mask Next Hop 180.25.21.128 255.255.255.128 Interface 0 180.25.21.0 255.255.255.128 Interface 1 180.25.68.0 255.255.255.128 Router 2 192.25.121.0 255.255.255.192 Router 3 default Router 4 For each of the following IP addresses, what does the router do if a packet with that address arrives? 问题: 1)180.25.21.0 2)180.25.68.151 3)180.25.21.168 4)192.25.121.129 5)192.25.121.24
2015-1-18
10
回答: 1)Interface 1 2)Router 4 3)Interface 0 4)Router 4 5)Router 3
2015-1-18
11
8 、 According to the TCP header in Fig.1, analyze the following TCP header in hexadecimal(十六进制) form: 0d 28 00 15 50 5f a9 06 00 00 00 00 50 02 40 00 c0 29 00 00
2015-1-18
3
回答:
2015-1-18
4
4 、 Assume that the receive window is 16KB and the maximum segment size is 1KB. Initially, threshold is set to 12KB. Then a timeout occurs when the TCP congestion window is equal to 14KB. And suppose that next transmissions are successful, how many times (Started from the initialization) would it take when the TCP congestion window is equal to the receive window? Please illustrate it.
2015-1-18 13
问题: 1)How long is the header part of this TCP segment? 2)What are the sequence number and the acknowledgment number? 3)What are the source port and the destination port in decimal form? 4)What kind of service requested by the source machine from the destination machine? 5)Please describes the function of this TCP segment according the 6-bit symbol field.
