【工业制造】2018年全球增材制造市场价值93亿美元,增长率为18%
2018年6月英语六级真题及答案(三套全)

2018年6月英语六级真题和答案听力Passage 1At some 2300 miles in length, the Mississippi is the longest river in the United States. At some1000 miles, the Mackenzie is the longest river in Canada. But these waterways seem minute ingthiest rivers: the Nile and the Amazon.comparison to the world’s 2 lenThe Nile which begins in central Africa and flows over 4100 miles north into the Mediterraneanhosted one of the world’s great ancient civilizations along its shores. Calm and peaceful for mostof the year, the Nile used to flood annually, thereby creating, irrigating and carrying new topsoil tothe nearby farmland on which ancient Egypt depended for livelihood. As a means of transportation,the river carried various vessels up and down its length.A journey through the unobstructed part of this waterway today would pass by the splendidvalley of the Kings, where the tombs of many of these ancient monarchs have stood for over 3000years. Great civilizations and intensive settlement are hardly associated with the Amazon, yet this4000 mile-long south American river carries about 20% of the world’s fresh water more than the Mississippi, Nile and Yangtze combined. Other statistics are equally astonishing. The Amazon isso wide at some points that from its center neither shore can be seen. Each second, the Amazonpours some 55 million gallons of water into the Atlantic. There, at its mouth stands one islandlarger than Switzerland. Most important of all, the Amazon irrigates the largest tropical rain foreston earth.Passage 19. What can be found in the valley of the Kings?10. In what way is the Amazon different from other big rivers?11. What does the speaker say about the Amazon?Recording 2Good morning, ladies and gentlemen, and welcome to the third in our cities of business seminarsin the program “Doing Business Abroad”. (Q19) Today, we are going to look at the intercultural awareness, that is the fact that not everyone is British, not everyone speaks English and noteveryone does business in a British way. And, why should they? (Q19) If overseas business peopleare selling to us, then they will make every effort to speak English and to respect our traditionsand methods. It is only polite for us to do the same when we visit them. It is not only polite, it is acentral, if we want to sell British products overseas. First, a short quiz. Let’s see howinterculturally-aware you are. Question 1: where must you not drink alcohol on the first andseventh of every month. Question 2: where should you never admire your host’spossessions.Question 3: how should you attract the waiter during a business lunch in Bangkok. Question 4:where should you try to make all your appointments either before 2 or after 5:30 pm. OK,everyone had a chance to make some notes. Right! Here are the answers. Although I am sure thatthe information could equally well apply to countries other than those I have chosen. No.1: (Q20)you must not drink alcohol on the first and seventh of the month in India. In international hotels,you may find it served, but if you are having a meal with an India colleague, remember to avoidasking for a beer. If you are an arrival, coincide with one of those tips. No.2: in Arab countries, thepoliteness and generosity of the people is without parallel. If you admire your colleague’sbeautiful belt and bowls, you may well find yourself being presented with them as a present. Thisis not a cheap way to do your shopping, however, as your host will quite correctly expect you torespond by presenting him with a gift of equal worth and beauty. In Thailand, clicking the fingers,clapping your hands or just shouting “Waiter” will embarrass your hosts, fellow diners, the waiter himself and, most of all, you. Place your palm downward and make an inconspicuous wavinggesture, which will produce instant and satisfying results. And finally, (Q21) in Spain, somebusinesses maintain the pattern of working until about 2 o’clock and then returning to the office from 5:30 to 8, 9 or 10 in the evening.Q19: What should you do when doing business with foreigners?Q20: What must you avoid doing with your Indian colleague?Q21: What do we learn about some Spanish people?选词填空儿歌Did Sarah Josepha Hale write “Mary’s Little Lamb,” the eternal nursery rhyme(儿歌)about girlnamed Mary with a stubborn lamb? This is still disputed, but it’s clear that the woman 26 repute for writing it was one of America’s most fascinating 27 characters. In honor of the poempublication on May 24,1830, here’s more about the 28 supposed author’s life.Hale wasn’t just a writer, she was also a 29 fierce social advocate, and she was particularly 30obsessed with an ideal New England, which she associated with abundant Thanksgivinx xg mealsshe began a nationwide 31 campaign to have athat she claimed had “a deep moral influence,” national holiday declared that would bring families together while celebrating the 32 traditionalfestivals. In 1863, after 17 years of advocacy including letters to five presidents, Hale got it.President Abraham Lincoln during the Civil War, issued a 33 proclamation setting aside the lastThursday in November for the holiday.The true authorship of “Mary’s Little Lamb” is disputed. According to New England Historical Society, Hale wrote only one part of the poem, but claimed authorship. Regardless of the author, itseems that the poem was 34 inspired by a real event. When young Mary Sawyer was followed toschool by a lamb in 1816, it caused some problems. A bystander named John Roulstone wrote apoem about the event, then, at some point, Hale herself seems to have helped write it. However, ifa 1916 piece by her great-niece is to be trusted, Hale claimed for the 35 rest of her life thatother people pretended that someone else wrote the poem”.A)campaignB)careerC)charactersD)featuresE)fierceF)inspiredG)latterH)obsessedI)proclamationJ)rectifiedK)reputedL)restM)supposedN)traditionalO)versatile金字塔Scientists scanning and mapping the Giza pyramids say they've discovered that the Great Pyramid of Giza is not exactly even. But really not by much. This pyramid is the oldest of theexact size has 26 puzzled experts for centuries, as the Seven Wonders. The pyramid’sworld’s"more than 21 acres of hard, white casing stones" that originally covered it were 27 removed long ago.Reporting in the most recent issue of the newsletter "AERAGRAM," which 28 chronicles thework of the Ancient Egypt Research Associates, engineer Glen Dash says that by using a new measuring approach that involved finding any surviving 29 remnants of the casing in order to determine where the original edge was. They found the east side of the pyramid to be a 30 maximum of 5.55 inches shorter than the west side.The question that most 31 fascinates him, however, isn't how the Egyptians who designed and built the pyramid got it wrong 4,500 years ago, but how they got it so close to 32 perfect. "We can only speculate as to how the Egyptians could have laid out these lines with such 33 precision using only the tools they had," Dash writes. He says his 34 hypothesis is that the Egyptians laidout their design on a grid, noting that the great pyramid is oriented only 35 slightly away from the cardinal directions (its north-south axis runs 3 minutes 54 seconds west of due north, while its east-west axis runs 3 minutes 51 seconds north of due east)—an amount that's "tiny, but similar," Atlas Obscura points out.chroniclesestablishedfascinateshypothesismaximummomentummysteriouslyperfectprecisionpuzzledremnantsremovedrevelationsslightly家用机器人When Elon Musk says, as he did this week, that his new priority is using artificial intelligence tobuild domestic robots, we should not only take note, but look forward to the day we can put ourlegs up in admiration.Mr. M usk is a guy who gets things done. The founder of two “moonshot” tech companies, Tesla Motors and SpaceX, is bringing electric vehicles to mass market and 26 humans to live onother planets. Lest this strike the amateur techie—not that readers of The Independent would ever8.8bn) fortunecount among them—as so much hot air, you can be reassured that the near $13bn (£this entrepreneur has 27 comes from practical achievements rather than hypothetical ones.A lot of clever people are 28 about artificial intelligence, fearing that robots will one daybecome so 29 they’ll murder all of us. These fears are mostly30 : as with hysteria aboutgenetic modification, we humans are generally wise enough to manage these problems withalacrity and care.And just think of how wonderful it would be if you had a live-in robot. It could —31 — belike having a babysitter and masseuse rolled into one —or, if that required 32 intelligenceone to chop the carrots, wash thebeyond the ken of Mr. Musk’s imagined machine, at least somecar and mow the lawn. Once purchased and trained, this would allow the 33 user to savemoney and time, freeing up 34 space in our busy lives to, for instance, read The Independent.That is why we welcome Mr. Mu sk’s latest35 , and wish him well. As long as robots add tothe sum of human happiness, reduce suffering or cumbersome activity, and create time to readworld-class journalism, The Independent will be their fans. Especially since journalism is one jobrobots will never do.B) casualC) emotionalD) enablingE) eventuallyF) exaggeratedG) extravagantH) generouslyI) misleadingJ) preciousK) rewardL) smartM) sphereN) terrifiedO) venture答案:26. D enabling27. A amassed28. N terrified29. L smart30. F exaggerated31. E eventually32. C emotional33. B casual34. J precious35. O venture阅读Passage OneQuestions 46 to 50 are based on the following passage.The Ebro Delta, in Spain, famous as a battleground during the Spanish Civil War, is now the setting for a different contest, one that is pitting rice farmers against two enemies: the rice-eating giant apple snail, and rising sea levels. What happens here will have a bearing on the future of European rice production and the overall health of southern European wetlands.Located on the Mediterranean just two hours south of Barcelona, the Ebro Delta produces 120 million kilograms of rice a year, making it one of the continent’smost important rice-growing areas. As the sea creeps into these fresh-water marshes, however, rising salinity(盐分)is hampering rice production. At the same time, this sea-water also kills off the greedy giant applesnail, an introduced pest that feeds on young rice plants. The most promising strategy has becometo harness one foe against the other.The battle is currently being waged on land, in greenhouses at the University of Barcelona.are seeking varieties of rice that can Scientists working under the banner “Project N eurice” withstand the increasing salinity without losing the absorbency that makes European rice ideal fortraditional Spanish and Italian dishes.“The project has two sides,” says Xavier Serrat, Neurice project manager and researcher at the University of Barcelona. “the short-term fight against the snail, and a mid- to long-term fightagainst climate change. But the snail has given the project greater urgency.”Originally from South America, the snails were accidentally introduced into the Ebro Delta byGlobal Aquatic Tecnologies, a company that raised the snails for fresh-water aquariums(水族馆),s presence in Europe is limited tobut failed to prevent their escape. For now, the giant apple snail’the Ebro Delta. But the snail continues its march to new territory, says Serrat. “The question is notif it will reach other rice-growing areas of Europe, but when.”Over the next year and a half investigators will test the various strains of salt-tolerant ricethey’ve bred. In 2018, farmers will plant the varieties with the most promise in the Ebro Delta andRh?ne. A Europe’s other two main rice-growing regions—along the Po in Italy, and France’sseason in the field will help determine which, if any, of the varieties are ready for commercialization.As an EU-funded effort, the search for salt-tolerant varieties of rice is taking place in all threecountries. Each team is crossbreeding a local European short-grain rice with a long-grain Asianvariety that carries the salt-resistant gene. The scientists are breeding successive generations toarrive at varieties that incorporate salt tolerance but retain about 97 percent of the European ricegenome(基因组).46.Why does the author mention the Spanish Civil War at the beginning of the passage?A. It had great impact on the life of Spanish rice farmers.B. It is of great significance in the records of Spanish history.C. Rice farmers in the Ebro Delta are waging a battle of similar importance.D. Rice farmers in the Ebro Delta are experiencing as hard a time as in the war.47.What may be the most effective strategy for rice farmers to employ in fighting their enemies?A. Striking the weaker enemy firstB. Killing two birds with one stoneC. Eliminating the enemy one by oneD. Using one evil to combat the other48. What do we learn about “Project Neurice”?A. Its goals will have to be realized at a cost.B. It aims to increase the yield of Spanish rice.C. Its immediate priority is to bring the pest under control.D. It tries to kill the snails with the help of climate change.49. What does Neurice project manager say about the giant apple snail?A. It can survive only on southern European wetlands.B. It will invade other rice-growing regions of Europe.C. It multiplies at a speed beyond human imagination.D. It was introduced into the rice fields on purpose.50. What is the ultimate goal of the EU-funded program?A. Cultivating ideal salt-resistant rice varieties.B. Increasing the absorbency of the Spanish rice.C. Introducing Spanish rice to the rest of Europe.D. Popularizing the rice crossbreeding technology.Passage TwoQuestions 51 to 55 are based on the following passage.Photography was once an expensive, laborious ordeal reserved for life's greatest milestones. Now, the only apparent cost to taking infinite photos of something as common as a meal is the space on your hard drive and your dining companion's patience.But is there another cost, a deeper cost, to documenting a life experience instead of simply enjoying it? "You hear that you shouldn't take all these photos and interrupt the experience, and it's bad for you, and we're not living in the present moment," says Kristin Diehl, associate professor of marketing at the University of Southern California Marshall School of Business.Diehl and her fellow researchers wanted to find out if that was true, so they embarked on a series of nine experiments in the lab and in the field testing people's enjoyment in the presence or absence of a camera. The results, published in the Journal of Personality and Social Psychology, surprised them. Taking photos actually makes people enjoy what they're doing more, not less."What we find is you actually look at the world slightly differently, because you're looking for things you want to capture, that you may want to hang onto," Diehl explains. "That gets peoplemore engaged in the experience, and they tend to enjoy it more."Take sightseeing. In one experiment, nearly 200 participants boarded a double-decker bus for a tour of Philadelphia. Both bus tours forbade the use of cell phones but one tour provided digital cameras and encouraged people to take photos. The people who took photos enjoyed the experience significantly more, and said they were more engaged, than those who didn't.Snapping a photo directs attention, which heightens the pleasure you get from whatever you're looking at, Diehl says. It works for things as boring as archaeological(考古的)museums, wherepeople were given eye-tracking glasses and instructed either to take photos or not. "People look longer at things they want to photograph," Diehl says. They report liking the exhibits more, too.To the relief of Instagrammers(Instagram用户)everywhere, it can even makes meals more enjoyable. When people were encouraged to take at least three photos while they ate lunch, they were more immersed in their meals than those who weren't told to take photos.Was it the satisfying click of the camera? The physical act of the snap? No, they found; just the act of planning to take a photo—and not actually taking it—had the same joy-boosting effect. "If you want to take mental photos, that works the same way," Diehl says. "Thinking about what you would want to photograph also gets you more engaged."51.What does the author say about photo-taking in the past?A. It was a painstaking effort for recording life’s major events.B. It was a luxury that only a few wealthy people could enjoy.C. It was a good way to preserve one’s precious images.D. It was a skill that required lots of practice to master.52.Kristin Diehl conducted a series of experiments on photo-taking to find out __________.A. what kind of pleasure it would actually bring to photo-takersB. whether people enjoyed it when they did sightseeingC. how it could help to enrich people’s life experiencesD. Whether it prevented people enjoying what they were doing53.What do the results of Diehl’s experiments show that people taking photos?A. They are distracted from what they are doing.B. They can better remember what they see or do.C. They are more absorbed in what catches their eye.D. They can have a better understanding of the world.54.What is found about museum visitors with the aid of eye-tracking glasses?A. They come out with better photographs of the exhibits.B. They focus more on the exhibits when taking pictures.C. They have a better view of what are on display.D. They follow the historical events more easily.55.What do we learn from the last paragraph?A. It is better to make plans before taking photos.B. Mental photos can be as beautiful as snapshots.C. Photographers can derive great joy from the click of the camera.D. Even the very thought of taking a photo can have a positive effect.翻译自行车自行车曾经是中国城乡最主要的交通工具,中国一度被称为“自行车王国”。
Native Instruments MASCHINE MK3 用户手册说明书

The information in this document is subject to change without notice and does not represent a commitment on the part of Native Instruments GmbH. The software described by this docu-ment is subject to a License Agreement and may not be copied to other media. No part of this publication may be copied, reproduced or otherwise transmitted or recorded, for any purpose, without prior written permission by Native Instruments GmbH, hereinafter referred to as Native Instruments.“Native Instruments”, “NI” and associated logos are (registered) trademarks of Native Instru-ments GmbH.ASIO, VST, HALion and Cubase are registered trademarks of Steinberg Media Technologies GmbH.All other product and company names are trademarks™ or registered® trademarks of their re-spective holders. Use of them does not imply any affiliation with or endorsement by them.Document authored by: David Gover and Nico Sidi.Software version: 2.8 (02/2019)Hardware version: MASCHINE MK3Special thanks to the Beta Test Team, who were invaluable not just in tracking down bugs, but in making this a better product.NATIVE INSTRUMENTS GmbH Schlesische Str. 29-30D-10997 Berlin Germanywww.native-instruments.de NATIVE INSTRUMENTS North America, Inc. 6725 Sunset Boulevard5th FloorLos Angeles, CA 90028USANATIVE INSTRUMENTS K.K.YO Building 3FJingumae 6-7-15, Shibuya-ku, Tokyo 150-0001Japanwww.native-instruments.co.jp NATIVE INSTRUMENTS UK Limited 18 Phipp StreetLondon EC2A 4NUUKNATIVE INSTRUMENTS FRANCE SARL 113 Rue Saint-Maur75011 ParisFrance SHENZHEN NATIVE INSTRUMENTS COMPANY Limited 5F, Shenzhen Zimao Center111 Taizi Road, Nanshan District, Shenzhen, GuangdongChina© NATIVE INSTRUMENTS GmbH, 2019. All rights reserved.Table of Contents1Welcome to MASCHINE (25)1.1MASCHINE Documentation (26)1.2Document Conventions (27)1.3New Features in MASCHINE 2.8 (29)1.4New Features in MASCHINE 2.7.10 (31)1.5New Features in MASCHINE 2.7.8 (31)1.6New Features in MASCHINE 2.7.7 (32)1.7New Features in MASCHINE 2.7.4 (33)1.8New Features in MASCHINE 2.7.3 (36)2Quick Reference (38)2.1Using Your Controller (38)2.1.1Controller Modes and Mode Pinning (38)2.1.2Controlling the Software Views from Your Controller (40)2.2MASCHINE Project Overview (43)2.2.1Sound Content (44)2.2.2Arrangement (45)2.3MASCHINE Hardware Overview (48)2.3.1MASCHINE Hardware Overview (48)2.3.1.1Control Section (50)2.3.1.2Edit Section (53)2.3.1.3Performance Section (54)2.3.1.4Group Section (56)2.3.1.5Transport Section (56)2.3.1.6Pad Section (58)2.3.1.7Rear Panel (63)2.4MASCHINE Software Overview (65)2.4.1Header (66)2.4.2Browser (68)2.4.3Arranger (70)2.4.4Control Area (73)2.4.5Pattern Editor (74)3Basic Concepts (76)3.1Important Names and Concepts (76)3.2Adjusting the MASCHINE User Interface (79)3.2.1Adjusting the Size of the Interface (79)3.2.2Switching between Ideas View and Song View (80)3.2.3Showing/Hiding the Browser (81)3.2.4Showing/Hiding the Control Lane (81)3.3Common Operations (82)3.3.1Using the 4-Directional Push Encoder (82)3.3.2Pinning a Mode on the Controller (83)3.3.3Adjusting Volume, Swing, and Tempo (84)3.3.4Undo/Redo (87)3.3.5List Overlay for Selectors (89)3.3.6Zoom and Scroll Overlays (90)3.3.7Focusing on a Group or a Sound (91)3.3.8Switching Between the Master, Group, and Sound Level (96)3.3.9Navigating Channel Properties, Plug-ins, and Parameter Pages in the Control Area.973.3.9.1Extended Navigate Mode on Your Controller (102)3.3.10Navigating the Software Using the Controller (105)3.3.11Using Two or More Hardware Controllers (106)3.3.12Touch Auto-Write Option (108)3.4Native Kontrol Standard (110)3.5Stand-Alone and Plug-in Mode (111)3.5.1Differences between Stand-Alone and Plug-in Mode (112)3.5.2Switching Instances (113)3.5.3Controlling Various Instances with Different Controllers (114)3.6Host Integration (114)3.6.1Setting up Host Integration (115)3.6.1.1Setting up Ableton Live (macOS) (115)3.6.1.2Setting up Ableton Live (Windows) (116)3.6.1.3Setting up Apple Logic Pro X (116)3.6.2Integration with Ableton Live (117)3.6.3Integration with Apple Logic Pro X (119)3.7Preferences (120)3.7.1Preferences – General Page (121)3.7.2Preferences – Audio Page (126)3.7.3Preferences – MIDI Page (130)3.7.4Preferences – Default Page (133)3.7.5Preferences – Library Page (137)3.7.6Preferences – Plug-ins Page (145)3.7.7Preferences – Hardware Page (150)3.7.8Preferences – Colors Page (154)3.8Integrating MASCHINE into a MIDI Setup (156)3.8.1Connecting External MIDI Equipment (156)3.8.2Sync to External MIDI Clock (157)3.8.3Send MIDI Clock (158)3.9Syncing MASCHINE using Ableton Link (159)3.9.1Connecting to a Network (159)3.9.2Joining and Leaving a Link Session (159)3.10Using a Pedal with the MASCHINE Controller (160)3.11File Management on the MASCHINE Controller (161)4Browser (163)4.1Browser Basics (163)4.1.1The MASCHINE Library (163)4.1.2Browsing the Library vs. Browsing Your Hard Disks (164)4.2Searching and Loading Files from the Library (165)4.2.1Overview of the Library Pane (165)4.2.2Selecting or Loading a Product and Selecting a Bank from the Browser (170)4.2.2.1[MK3] Browsing by Product Category Using the Controller (174)4.2.2.2[MK3] Browsing by Product Vendor Using the Controller (174)4.2.3Selecting a Product Category, a Product, a Bank, and a Sub-Bank (175)4.2.3.1Selecting a Product Category, a Product, a Bank, and a Sub-Bank on theController (179)4.2.4Selecting a File Type (180)4.2.5Choosing Between Factory and User Content (181)4.2.6Selecting Type and Character Tags (182)4.2.7List and Tag Overlays in the Browser (186)4.2.8Performing a Text Search (188)4.2.9Loading a File from the Result List (188)4.3Additional Browsing Tools (193)4.3.1Loading the Selected Files Automatically (193)4.3.2Auditioning Instrument Presets (195)4.3.3Auditioning Samples (196)4.3.4Loading Groups with Patterns (197)4.3.5Loading Groups with Routing (198)4.3.6Displaying File Information (198)4.4Using Favorites in the Browser (199)4.5Editing the Files’ Tags and Properties (203)4.5.1Attribute Editor Basics (203)4.5.2The Bank Page (205)4.5.3The Types and Characters Pages (205)4.5.4The Properties Page (208)4.6Loading and Importing Files from Your File System (209)4.6.1Overview of the FILES Pane (209)4.6.2Using Favorites (211)4.6.3Using the Location Bar (212)4.6.4Navigating to Recent Locations (213)4.6.5Using the Result List (214)4.6.6Importing Files to the MASCHINE Library (217)4.7Locating Missing Samples (219)4.8Using Quick Browse (221)5Managing Sounds, Groups, and Your Project (225)5.1Overview of the Sounds, Groups, and Master (225)5.1.1The Sound, Group, and Master Channels (226)5.1.2Similarities and Differences in Handling Sounds and Groups (227)5.1.3Selecting Multiple Sounds or Groups (228)5.2Managing Sounds (233)5.2.1Loading Sounds (235)5.2.2Pre-listening to Sounds (236)5.2.3Renaming Sound Slots (237)5.2.4Changing the Sound’s Color (237)5.2.5Saving Sounds (239)5.2.6Copying and Pasting Sounds (241)5.2.7Moving Sounds (244)5.2.8Resetting Sound Slots (245)5.3Managing Groups (247)5.3.1Creating Groups (248)5.3.2Loading Groups (249)5.3.3Renaming Groups (251)5.3.4Changing the Group’s Color (251)5.3.5Saving Groups (253)5.3.6Copying and Pasting Groups (255)5.3.7Reordering Groups (258)5.3.8Deleting Groups (259)5.4Exporting MASCHINE Objects and Audio (260)5.4.1Saving a Group with its Samples (261)5.4.2Saving a Project with its Samples (262)5.4.3Exporting Audio (264)5.5Importing Third-Party File Formats (270)5.5.1Loading REX Files into Sound Slots (270)5.5.2Importing MPC Programs to Groups (271)6Playing on the Controller (275)6.1Adjusting the Pads (275)6.1.1The Pad View in the Software (275)6.1.2Choosing a Pad Input Mode (277)6.1.3Adjusting the Base Key (280)6.1.4Using Choke Groups (282)6.1.5Using Link Groups (284)6.2Adjusting the Key, Choke, and Link Parameters for Multiple Sounds (286)6.3Playing Tools (287)6.3.1Mute and Solo (288)6.3.2Choke All Notes (292)6.3.3Groove (293)6.3.4Level, Tempo, Tune, and Groove Shortcuts on Your Controller (295)6.3.5Tap Tempo (299)6.4Performance Features (300)6.4.1Overview of the Perform Features (300)6.4.2Selecting a Scale and Creating Chords (303)6.4.3Scale and Chord Parameters (303)6.4.4Creating Arpeggios and Repeated Notes (316)6.4.5Swing on Note Repeat / Arp Output (321)6.5Using Lock Snapshots (322)6.5.1Creating a Lock Snapshot (322)6.5.2Using Extended Lock (323)6.5.3Updating a Lock Snapshot (323)6.5.4Recalling a Lock Snapshot (324)6.5.5Morphing Between Lock Snapshots (324)6.5.6Deleting a Lock Snapshot (325)6.5.7Triggering Lock Snapshots via MIDI (326)6.6Using the Smart Strip (327)6.6.1Pitch Mode (328)6.6.2Modulation Mode (328)6.6.3Perform Mode (328)6.6.4Notes Mode (329)7Working with Plug-ins (330)7.1Plug-in Overview (330)7.1.1Plug-in Basics (330)7.1.2First Plug-in Slot of Sounds: Choosing the Sound’s Role (334)7.1.3Loading, Removing, and Replacing a Plug-in (335)7.1.3.1Browser Plug-in Slot Selection (341)7.1.4Adjusting the Plug-in Parameters (344)7.1.5Bypassing Plug-in Slots (344)7.1.6Using Side-Chain (346)7.1.7Moving Plug-ins (346)7.1.8Alternative: the Plug-in Strip (348)7.1.9Saving and Recalling Plug-in Presets (348)7.1.9.1Saving Plug-in Presets (349)7.1.9.2Recalling Plug-in Presets (350)7.1.9.3Removing a Default Plug-in Preset (351)7.2The Sampler Plug-in (352)7.2.1Page 1: Voice Settings / Engine (354)7.2.2Page 2: Pitch / Envelope (356)7.2.3Page 3: FX / Filter (359)7.2.4Page 4: Modulation (361)7.2.5Page 5: LFO (363)7.2.6Page 6: Velocity / Modwheel (365)7.3Using Native Instruments and External Plug-ins (367)7.3.1Opening/Closing Plug-in Windows (367)7.3.2Using the VST/AU Plug-in Parameters (370)7.3.3Setting Up Your Own Parameter Pages (371)7.3.4Using VST/AU Plug-in Presets (376)7.3.5Multiple-Output Plug-ins and Multitimbral Plug-ins (378)8Using the Audio Plug-in (380)8.1Loading a Loop into the Audio Plug-in (384)8.2Editing Audio in the Audio Plug-in (385)8.3Using Loop Mode (386)8.4Using Gate Mode (388)9Using the Drumsynths (390)9.1Drumsynths – General Handling (391)9.1.1Engines: Many Different Drums per Drumsynth (391)9.1.2Common Parameter Organization (391)9.1.3Shared Parameters (394)9.1.4Various Velocity Responses (394)9.1.5Pitch Range, Tuning, and MIDI Notes (394)9.2The Kicks (395)9.2.1Kick – Sub (397)9.2.2Kick – Tronic (399)9.2.3Kick – Dusty (402)9.2.4Kick – Grit (403)9.2.5Kick – Rasper (406)9.2.6Kick – Snappy (407)9.2.7Kick – Bold (409)9.2.8Kick – Maple (411)9.2.9Kick – Push (412)9.3The Snares (414)9.3.1Snare – Volt (416)9.3.2Snare – Bit (418)9.3.3Snare – Pow (420)9.3.4Snare – Sharp (421)9.3.5Snare – Airy (423)9.3.6Snare – Vintage (425)9.3.7Snare – Chrome (427)9.3.8Snare – Iron (429)9.3.9Snare – Clap (431)9.3.10Snare – Breaker (433)9.4The Hi-hats (435)9.4.1Hi-hat – Silver (436)9.4.2Hi-hat – Circuit (438)9.4.3Hi-hat – Memory (440)9.4.4Hi-hat – Hybrid (442)9.4.5Creating a Pattern with Closed and Open Hi-hats (444)9.5The Toms (445)9.5.1Tom – Tronic (447)9.5.2Tom – Fractal (449)9.5.3Tom – Floor (453)9.5.4Tom – High (455)9.6The Percussions (456)9.6.1Percussion – Fractal (458)9.6.2Percussion – Kettle (461)9.6.3Percussion – Shaker (463)9.7The Cymbals (467)9.7.1Cymbal – Crash (469)9.7.2Cymbal – Ride (471)10Using the Bass Synth (474)10.1Bass Synth – General Handling (475)10.1.1Parameter Organization (475)10.1.2Bass Synth Parameters (477)11Working with Patterns (479)11.1Pattern Basics (479)11.1.1Pattern Editor Overview (480)11.1.2Navigating the Event Area (486)11.1.3Following the Playback Position in the Pattern (488)11.1.4Jumping to Another Playback Position in the Pattern (489)11.1.5Group View and Keyboard View (491)11.1.6Adjusting the Arrange Grid and the Pattern Length (493)11.1.7Adjusting the Step Grid and the Nudge Grid (497)11.2Recording Patterns in Real Time (501)11.2.1Recording Your Patterns Live (501)11.2.2The Record Prepare Mode (504)11.2.3Using the Metronome (505)11.2.4Recording with Count-in (506)11.2.5Quantizing while Recording (508)11.3Recording Patterns with the Step Sequencer (508)11.3.1Step Mode Basics (508)11.3.2Editing Events in Step Mode (511)11.3.3Recording Modulation in Step Mode (513)11.4Editing Events (514)11.4.1Editing Events with the Mouse: an Overview (514)11.4.2Creating Events/Notes (517)11.4.3Selecting Events/Notes (518)11.4.4Editing Selected Events/Notes (526)11.4.5Deleting Events/Notes (532)11.4.6Cut, Copy, and Paste Events/Notes (535)11.4.7Quantizing Events/Notes (538)11.4.8Quantization While Playing (540)11.4.9Doubling a Pattern (541)11.4.10Adding Variation to Patterns (541)11.5Recording and Editing Modulation (546)11.5.1Which Parameters Are Modulatable? (547)11.5.2Recording Modulation (548)11.5.3Creating and Editing Modulation in the Control Lane (550)11.6Creating MIDI Tracks from Scratch in MASCHINE (555)11.7Managing Patterns (557)11.7.1The Pattern Manager and Pattern Mode (558)11.7.2Selecting Patterns and Pattern Banks (560)11.7.3Creating Patterns (563)11.7.4Deleting Patterns (565)11.7.5Creating and Deleting Pattern Banks (566)11.7.6Naming Patterns (568)11.7.7Changing the Pattern’s Color (570)11.7.8Duplicating, Copying, and Pasting Patterns (571)11.7.9Moving Patterns (574)11.7.10Adjusting Pattern Length in Fine Increments (575)11.8Importing/Exporting Audio and MIDI to/from Patterns (576)11.8.1Exporting Audio from Patterns (576)11.8.2Exporting MIDI from Patterns (577)11.8.3Importing MIDI to Patterns (580)12Audio Routing, Remote Control, and Macro Controls (589)12.1Audio Routing in MASCHINE (590)12.1.1Sending External Audio to Sounds (591)12.1.2Configuring the Main Output of Sounds and Groups (596)12.1.3Setting Up Auxiliary Outputs for Sounds and Groups (601)12.1.4Configuring the Master and Cue Outputs of MASCHINE (605)12.1.5Mono Audio Inputs (610)12.1.5.1Configuring External Inputs for Sounds in Mix View (611)12.2Using MIDI Control and Host Automation (614)12.2.1Triggering Sounds via MIDI Notes (615)12.2.2Triggering Scenes via MIDI (622)12.2.3Controlling Parameters via MIDI and Host Automation (623)12.2.4Selecting VST/AU Plug-in Presets via MIDI Program Change (631)12.2.5Sending MIDI from Sounds (632)12.3Creating Custom Sets of Parameters with the Macro Controls (636)12.3.1Macro Control Overview (637)12.3.2Assigning Macro Controls Using the Software (638)12.3.3Assigning Macro Controls Using the Controller (644)13Controlling Your Mix (646)13.1Mix View Basics (646)13.1.1Switching between Arrange View and Mix View (646)13.1.2Mix View Elements (647)13.2The Mixer (649)13.2.1Displaying Groups vs. Displaying Sounds (650)13.2.2Adjusting the Mixer Layout (652)13.2.3Selecting Channel Strips (653)13.2.4Managing Your Channels in the Mixer (654)13.2.5Adjusting Settings in the Channel Strips (656)13.2.6Using the Cue Bus (660)13.3The Plug-in Chain (662)13.4The Plug-in Strip (663)13.4.1The Plug-in Header (665)13.4.2Panels for Drumsynths and Internal Effects (667)13.4.3Panel for the Sampler (668)13.4.4Custom Panels for Native Instruments Plug-ins (671)13.4.5Undocking a Plug-in Panel (Native Instruments and External Plug-ins Only) (675)13.5Controlling Your Mix from the Controller (677)13.5.1Navigating Your Channels in Mix Mode (678)13.5.2Adjusting the Level and Pan in Mix Mode (679)13.5.3Mute and Solo in Mix Mode (680)13.5.4Plug-in Icons in Mix Mode (680)14Using Effects (681)14.1Applying Effects to a Sound, a Group or the Master (681)14.1.1Adding an Effect (681)14.1.2Other Operations on Effects (690)14.1.3Using the Side-Chain Input (692)14.2Applying Effects to External Audio (695)14.2.1Step 1: Configure MASCHINE Audio Inputs (695)14.2.2Step 2: Set up a Sound to Receive the External Input (698)14.2.3Step 3: Load an Effect to Process an Input (700)14.3Creating a Send Effect (701)14.3.1Step 1: Set Up a Sound or Group as Send Effect (702)14.3.2Step 2: Route Audio to the Send Effect (706)14.3.3 A Few Notes on Send Effects (708)14.4Creating Multi-Effects (709)15Effect Reference (712)15.1Dynamics (713)15.1.1Compressor (713)15.1.2Gate (717)15.1.3Transient Master (721)15.1.4Limiter (723)15.1.5Maximizer (727)15.2Filtering Effects (730)15.2.1EQ (730)15.2.2Filter (733)15.2.3Cabinet (737)15.3Modulation Effects (738)15.3.1Chorus (738)15.3.2Flanger (740)15.3.3FM (742)15.3.4Freq Shifter (743)15.3.5Phaser (745)15.4Spatial and Reverb Effects (747)15.4.1Ice (747)15.4.2Metaverb (749)15.4.3Reflex (750)15.4.4Reverb (Legacy) (752)15.4.5Reverb (754)15.4.5.1Reverb Room (754)15.4.5.2Reverb Hall (757)15.4.5.3Plate Reverb (760)15.5Delays (762)15.5.1Beat Delay (762)15.5.2Grain Delay (765)15.5.3Grain Stretch (767)15.5.4Resochord (769)15.6Distortion Effects (771)15.6.1Distortion (771)15.6.2Lofi (774)15.6.3Saturator (775)15.7Perform FX (779)15.7.1Filter (780)15.7.2Flanger (782)15.7.3Burst Echo (785)15.7.4Reso Echo (787)15.7.5Ring (790)15.7.6Stutter (792)15.7.7Tremolo (795)15.7.8Scratcher (798)16Working with the Arranger (801)16.1Arranger Basics (801)16.1.1Navigating Song View (804)16.1.2Following the Playback Position in Your Project (806)16.1.3Performing with Scenes and Sections using the Pads (807)16.2Using Ideas View (811)16.2.1Scene Overview (811)16.2.2Creating Scenes (813)16.2.3Assigning and Removing Patterns (813)16.2.4Selecting Scenes (817)16.2.5Deleting Scenes (818)16.2.6Creating and Deleting Scene Banks (820)16.2.7Clearing Scenes (820)16.2.8Duplicating Scenes (821)16.2.9Reordering Scenes (822)16.2.10Making Scenes Unique (824)16.2.11Appending Scenes to Arrangement (825)16.2.12Naming Scenes (826)16.2.13Changing the Color of a Scene (827)16.3Using Song View (828)16.3.1Section Management Overview (828)16.3.2Creating Sections (833)16.3.3Assigning a Scene to a Section (834)16.3.4Selecting Sections and Section Banks (835)16.3.5Reorganizing Sections (839)16.3.6Adjusting the Length of a Section (840)16.3.6.1Adjusting the Length of a Section Using the Software (841)16.3.6.2Adjusting the Length of a Section Using the Controller (843)16.3.7Clearing a Pattern in Song View (843)16.3.8Duplicating Sections (844)16.3.8.1Making Sections Unique (845)16.3.9Removing Sections (846)16.3.10Renaming Scenes (848)16.3.11Clearing Sections (849)16.3.12Creating and Deleting Section Banks (850)16.3.13Working with Patterns in Song view (850)16.3.13.1Creating a Pattern in Song View (850)16.3.13.2Selecting a Pattern in Song View (850)16.3.13.3Clearing a Pattern in Song View (851)16.3.13.4Renaming a Pattern in Song View (851)16.3.13.5Coloring a Pattern in Song View (851)16.3.13.6Removing a Pattern in Song View (852)16.3.13.7Duplicating a Pattern in Song View (852)16.3.14Enabling Auto Length (852)16.3.15Looping (853)16.3.15.1Setting the Loop Range in the Software (854)16.4Playing with Sections (855)16.4.1Jumping to another Playback Position in Your Project (855)16.5Triggering Sections or Scenes via MIDI (856)16.6The Arrange Grid (858)16.7Quick Grid (860)17Sampling and Sample Mapping (862)17.1Opening the Sample Editor (862)17.2Recording Audio (863)17.2.1Opening the Record Page (863)17.2.2Selecting the Source and the Recording Mode (865)17.2.3Arming, Starting, and Stopping the Recording (868)17.2.5Using the Footswitch for Recording Audio (871)17.2.6Checking Your Recordings (872)17.2.7Location and Name of Your Recorded Samples (876)17.3Editing a Sample (876)17.3.1Using the Edit Page (877)17.3.2Audio Editing Functions (882)17.4Slicing a Sample (890)17.4.1Opening the Slice Page (891)17.4.2Adjusting the Slicing Settings (893)17.4.3Live Slicing (898)17.4.3.1Live Slicing Using the Controller (898)17.4.3.2Delete All Slices (899)17.4.4Manually Adjusting Your Slices (899)17.4.5Applying the Slicing (906)17.5Mapping Samples to Zones (912)17.5.1Opening the Zone Page (912)17.5.2Zone Page Overview (913)17.5.3Selecting and Managing Zones in the Zone List (915)17.5.4Selecting and Editing Zones in the Map View (920)17.5.5Editing Zones in the Sample View (924)17.5.6Adjusting the Zone Settings (927)17.5.7Adding Samples to the Sample Map (934)18Appendix: Tips for Playing Live (937)18.1Preparations (937)18.1.1Focus on the Hardware (937)18.1.2Customize the Pads of the Hardware (937)18.1.3Check Your CPU Power Before Playing (937)18.1.4Name and Color Your Groups, Patterns, Sounds and Scenes (938)18.1.5Consider Using a Limiter on Your Master (938)18.1.6Hook Up Your Other Gear and Sync It with MIDI Clock (938)18.1.7Improvise (938)18.2Basic Techniques (938)18.2.1Use Mute and Solo (938)18.2.2Use Scene Mode and Tweak the Loop Range (939)18.2.3Create Variations of Your Drum Patterns in the Step Sequencer (939)18.2.4Use Note Repeat (939)18.2.5Set Up Your Own Multi-effect Groups and Automate Them (939)18.3Special Tricks (940)18.3.1Changing Pattern Length for Variation (940)18.3.2Using Loops to Cycle Through Samples (940)18.3.3Using Loops to Cycle Through Samples (940)18.3.4Load Long Audio Files and Play with the Start Point (940)19Troubleshooting (941)19.1Knowledge Base (941)19.2Technical Support (941)19.3Registration Support (942)19.4User Forum (942)20Glossary (943)Index (951)1Welcome to MASCHINEThank you for buying MASCHINE!MASCHINE is a groove production studio that implements the familiar working style of classi-cal groove boxes along with the advantages of a computer based system. MASCHINE is ideal for making music live, as well as in the studio. It’s the hands-on aspect of a dedicated instru-ment, the MASCHINE hardware controller, united with the advanced editing features of the MASCHINE software.Creating beats is often not very intuitive with a computer, but using the MASCHINE hardware controller to do it makes it easy and fun. You can tap in freely with the pads or use Note Re-peat to jam along. Alternatively, build your beats using the step sequencer just as in classic drum machines.Patterns can be intuitively combined and rearranged on the fly to form larger ideas. You can try out several different versions of a song without ever having to stop the music.Since you can integrate it into any sequencer that supports VST, AU, or AAX plug-ins, you can reap the benefits in almost any software setup, or use it as a stand-alone application. You can sample your own material, slice loops and rearrange them easily.However, MASCHINE is a lot more than an ordinary groovebox or sampler: it comes with an inspiring 7-gigabyte library, and a sophisticated, yet easy to use tag-based Browser to give you instant access to the sounds you are looking for.What’s more, MASCHINE provides lots of options for manipulating your sounds via internal ef-fects and other sound-shaping possibilities. You can also control external MIDI hardware and 3rd-party software with the MASCHINE hardware controller, while customizing the functions of the pads, knobs and buttons according to your needs utilizing the included Controller Editor application. We hope you enjoy this fantastic instrument as much as we do. Now let’s get go-ing!—The MASCHINE team at Native Instruments.MASCHINE Documentation1.1MASCHINE DocumentationNative Instruments provide many information sources regarding MASCHINE. The main docu-ments should be read in the following sequence:1.MASCHINE Getting Started: This document provides a practical approach to MASCHINE viaa set of tutorials covering easy and more advanced tasks in order to help you familiarizeyourself with MASCHINE.2.MASCHINE Manual (this document): The MASCHINE Manual provides you with a compre-hensive description of all MASCHINE software and hardware features.Additional documentation sources provide you with details on more specific topics:▪Controller Editor Manual: Besides using your MASCHINE hardware controller together withits dedicated MASCHINE software, you can also use it as a powerful and highly versatileMIDI controller to pilot any other MIDI-capable application or device. This is made possibleby the Controller Editor software, an application that allows you to precisely define all MIDIassignments for your MASCHINE controller. The Controller Editor was installed during theMASCHINE installation procedure. For more information on this, please refer to the Con-troller Editor Manual available as a PDF file via the Help menu of Controller Editor.▪Online Support Videos: You can find a number of support videos on The Official Native In-struments Support Channel under the following URL: https:///NIsupport-EN. We recommend that you follow along with these instructions while the respective ap-plication is running on your computer.Other Online Resources:If you are experiencing problems related to your Native Instruments product that the supplied documentation does not cover, there are several ways of getting help:▪Knowledge Base▪User Forum▪Technical Support▪Registration SupportYou will find more information on these subjects in the chapter Troubleshooting.1.2Document ConventionsThis section introduces you to the signage and text highlighting used in this manual. This man-ual uses particular formatting to point out special facts and to warn you of potential issues. The icons introducing these notes let you see what kind of information is to be expected:This document uses particular formatting to point out special facts and to warn you of poten-tial issues. The icons introducing the following notes let you see what kind of information can be expected:Furthermore, the following formatting is used:▪Text appearing in (drop-down) menus (such as Open…, Save as… etc.) in the software and paths to locations on your hard disk or other storage devices is printed in italics.▪Text appearing elsewhere (labels of buttons, controls, text next to checkboxes etc.) in the software is printed in blue. Whenever you see this formatting applied, you will find the same text appearing somewhere on the screen.▪Text appearing on the displays of the controller is printed in light grey. Whenever you see this formatting applied, you will find the same text on a controller display.▪Text appearing on labels of the hardware controller is printed in orange. Whenever you see this formatting applied, you will find the same text on the controller.▪Important names and concepts are printed in bold.▪References to keys on your computer’s keyboard you’ll find put in square brackets (e.g.,“Press [Shift] + [Enter]”).►Single instructions are introduced by this play button type arrow.→Results of actions are introduced by this smaller arrow.Naming ConventionThroughout the documentation we will refer to MASCHINE controller (or just controller) as the hardware controller and MASCHINE software as the software installed on your computer.The term “effect” will sometimes be abbreviated as “FX” when referring to elements in the MA-SCHINE software and hardware. These terms have the same meaning.Button Combinations and Shortcuts on Your ControllerMost instructions will use the “+” sign to indicate buttons (or buttons and pads) that must be pressed simultaneously, starting with the button indicated first. E.g., an instruction such as:“Press SHIFT + PLAY”means:1.Press and hold SHIFT.2.While holding SHIFT, press PLAY and release it.3.Release SHIFT.Unlabeled Buttons on the ControllerThe buttons and knobs above and below the displays on your MASCHINE controller do not have labels.。
六级英语真题2018年6月(第三套)试卷及答案详解

—1—
Section B
Directions: In this section, you are going to read a passage with ten statements attached to it. Each statement contains 叫ormation given in one of the paragraphs. Identify the paragraph from咖ch the information is derived. You may choose a paragraph more than once. Each paragraph is marked with a letter. Answer the questions by marking the corresponding letter on Answer Sheet 2. In the real world, nobody cares that you went to an Ivy League school
And just think of how wonderful it would be if you had a live-in robot. It could, 31 , be likehaving a babysitter and a nurse rolled into one—or, if that required 32 intelligence beyond thepower of Mr. Musk's imagined machine, at least someone to chop the carrots, wash the car andmow the lawn. Once purchased and trained, this would allow the 33 user to save money andtime, freeing up 34 space in our busy lives to read a good book.
2018年6月大学英语三级考试B真题及答案解析

2018年6月B 级考试全真试题Par t I Listening Comprehension [25 minutes]Directions: This part is to test your listening ability. It consists of 4 sections.Sect ion ADirections: 兀is section is to test your ability to give proper responses. There are 7 recorded questionsin it. After each question, t加·e is a pause. 吓e questions will be spoken two times. When you hear a question, you slwuld decide on the co rrect answer from the 4 choices markedA ), B), C) and D) given in your test pap 砑;Then you should mark the corresponding letter on the Answer . Sheet with a single line through tlie center.Exam ple: You wil l hear:You will read: A) I'm not sure.�) Yo u'r e rig htC) Yes, certainly .., D) That's interesting. From the question we learn that t加speaker is asking . the listener ·to leave a message. Therefore, C) Yes, certai11ly is the cor r ect answe r . You should mark CJ on the Answe r Sheet with a single line through the center.[A][BJ图[D JNow the test will begin.1. A ) Fine. And you?B)I like it very much.2.A) Take care.B)It's great.3.A) See you tomorrow. :)B)Ok, it doesn't matter.4.A) Yes, please.B)Have a nice day.5.A) H urry up .B)So long.6.A ) Coffe e, please .B)Yes. Here you are.7.A) Don't worry.B )G ood luck!C)Sit down please.C)My ple asu re.D)Oh, yes. Please.D)Th is w ay , please.C)Here is the room ·key.D)Sorry, all our rooms are booked.C)Don't do it.D)Let's go.C)Certainly. Is Friday OK?D)Mind ·your steps.C)Your telephone number, please.D)I'm fine, thank you.C)Al l rig _扯·\D)Never . mind./,1; I ,, ,Sect ion BD irections: This s ec tion势tq ... t est::. y qur: a bility . to . understa叫S加7i�(l.ialpgues.There ar e 7 1-e co讨ed ,. , . , , ·dialogues i n 札A 府r .,e cu;fi 1,ialo匹e,.there is a戏co,;<f,.f!<t.q'H�stion,1,B o t h t he dialogues and1;ques t io 邓W�f t �e SP.Q妇印o times .. :Whe?i you he a:r,..;a ,.!J'µe sfi,o 叫\ur u should q.ecide •. Q肛妒corr ect a 吩w er from the 4 choices ma rk ed A ), BJ_,:.(;) a叫\;J)入航ven in . your t est pa p织The n you shou ld,_1;11迈忱,加,,p orres p on <!,in g .. l etter叨:,加l!心叩红;;Sheet叭th ,a, 戏ngle line;, lfrt, ,,,,. t h r p四h t he C 叩陌;o N.o 初l 树邻1.t o f h f:l ; di 咄妞兀{:!S,I 儿)1;'i<, 小沁,r !、l '. '.', I'' I 、8.A ) By bus. 9.A ) A repo rt.10.A) H. e IS an engm eer.B) By taxi . B)A design.C) On foot.D)By bicycle.,.0)-A p )皿·旧叩)Jo•, lH .'/O D,),�p � 担��,..,,., C)He is a manager.B)He is a doctor.11.A) Writing work reports.B)Working on weekends.12.A) To do business.B)To see a doctor.13.A) It had a flat tire.B)It was out of fuel.14.A) Read newspapers.B)Attend a job fair.D)He is a programmer.C)Giving presentations.D)Dealing with angry customers.C)To take a holiday.D)To visit friends.C)Its front window was broken.D)The engine didn't work C)Visit the website.D)Ask her friends for help.Section CDirections: In this section, ther e are 2 recorded co1ive1·sations. After each conversation, t加噜e are somerecorded questio 邓.Both t加conve1·sations and questions will be spoken two times. W酝youhear a question, you slwuld decide on the co 订ect answe1·from the 4 choices marked A), B.入CJ a叫D)given in your test paper. 吓en you slwu囚mark the c01Tesponding letter on theAnswer S. 如et with a single l!ne through the center. Now listen to the conversations.C onversation 115.A) To report a case.B)To book a hotel room.16.A) Her srnartphone .B)Her passport.C o nversatmn 217.A) She has coughed a lot.B)She has a high fever.18.A) This morning.B)This afternoon19.A) Take her blood pressure.B)Give her some m edicine .C)To ask for sick leave.D)To order a meal.C)Her watch.D)Her computer.C)She has got a bad cold.D)She has got a pain in the stomach.C)Last night.D)Yesterday.C)Send her to the emerge ncy room.D)Perfor m an operat ion on her at once.S e ction DDirections: In this section you will hea1j ; a ·recorded short passage. The passage is printed in the testpa p er , but with some words or phrases mi ssing. The passage will be read three times.Durin g the second reading , you are required to put the missing words or phrases on the Answer Sheet in or如of .the numbered blanks according to what you hear. The thirdreading is for you to check your writing. Now the passage will be g in.,,.,,,pV o lwite e rs are our heart and . soul.'lease come an d he ip us b叫d homes for 20 low-inc ome famili es. There is no experience needed and w e supply the 21 . Jus t v olunt eer for a day. It's fun,rewarding and you can learn some '·122·-'!I ! . :',!. , ;, !)If building isn't your !ihfn g ,·:c o m e ·· 的d 1·voluntee r for 1 o ne of '如r even 区面�'i 23•'''' ,;': I i'You must be 24·:i 14·years of 'a ge ··to vol unteer ·antl those'15 y e 邮邸d under 11\llS t'come .,• with .aparent.l" . ; .·; j ..'', •• ll 1l. ,,, C o m e and sign up now I t.o : ,vo lunte e r : 1y our tim e . .. •;.•'I 'I . I •.Part II Vocabulary & Struct ure [10 minute s] Directions: 77iis par t is to test yoiir ability t o conslntct correct and meaningful s切阮ces.It consist,s of2 secti01岱.Section ADirections: In thi.s section勺there a re 10 incomplete sentences. You are required to complete e砒hone by deciding on the most appropriate word or words from the 4 choices marked A), BJ, CJ andDJ. 77砌i you should mark the con-esponding letter on the Answer Sheet with a single linethrough the center.25.Employees would like to work m1der·team leaders wh o good examples.A)tum B)p ut C)do _D)set26.Turn to us for legal advice at any tin1e you need it.A)whe n'B) how·C) where27.Your pay raise w ll in part your work e x perience and skills.A)ca ny on B)take on C)depend on D)wh y D)put on28.You are required to enter the name of the city in which your company.A)locates B)located C)is locating D)is located29.Tourists can get the latest information of our city the help of our local tour gui妇A)on B)with C)under.D) for30.Let's find people with computer skills to_ a team for the project.A)look up B) rin g u p C) g iv e up . D) m ake up31.If I were you, I·the company's website for more detailed information.A)would visit,. B) will visit C)visit D)h a ve visited32.No company can afford to bear the of customer confidence.A)stress B)loss C)worry D)h u rry33.she has been working in China for only two years, she speaks fluent Chinese.A)W h en B)I f C)Althou g h D)Until34.We have read this instruction many times and we are with all the ste p s we shouldtake.A)similar··, ·B) u s e ful -·C) hel pful· D)familiarSec tion BDirections: There are 5 incomplete statements here. You s h ould ill in each blank wi th th e严per Jo n 。
PLX SDK User Manual

User’s Manual
Version 4.40 March 2006
© 2006, PLX Technology, Inc. All rights reserved.
PLX Technology, Inc. retains the right to make changes to this product at any time, without notice. Products may have minor variations to this publication. PLX assumes no liability whatsoever, including infringement of any patent or copyright, for sale and use of PLX products.
PLX Technology and the PLX logo are registered trademarks of PLX Technology, Inc.
Other brands and names are the property of their respective owners.
PLX SOFTWARE LICENSE AGREEMENT
LICENSE Copyright © 2006 PLX Technology,
Inc.
This PLX Software License agreement is a legal agreement between you and PLX Technology, Inc. for the PLX Software, which is provided on the enclosed PLX CD-ROM. PLX Technology owns this PLX Software. The PLX Software is protected by copyright laws and international copyright treaties, as well as other intellectual property laws and treaties, and is licensed, not sold. If you are a rightful possessor of the PLX Software, PLX grants you a license to use the PLX Software as part of or in conjunction with a PLX chip on a per project basis. PLX grants this permission provided that the above copyright notice appears in all copies and derivatives of the PLX Software. Use of any supplied runtime object modules or derivatives from the included source code in any product without a PLX Technology, Inc. chip is strictly prohibited. You obtain no rights other than those granted to you under this license. You may copy the PLX Software for backup or archival purposes. You are not authorized to use, merge, copy, display, adapt, modify, execute, distribute or transfer, reverse assemble, reverse compile, decode, or translate the PLX Software except to the extent permitted by law.
TAS3xxx and TAS55xx & 3RD-PARTY Algorithms
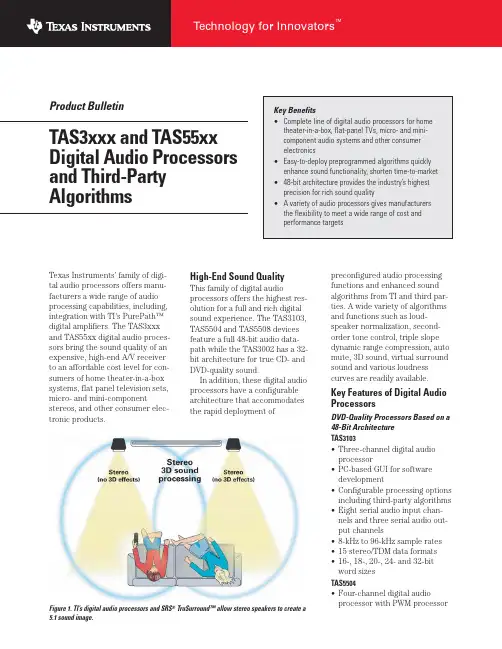
Product BulletinTAS3xxx and TAS55xx Digital Audio Processors and Third-Party AlgorithmsTexas Instruments’ family of digi-tal audio processors offers manu-facturers a wide range of audio processing capabilities, including, integration with TI's PurePath™digital amplifiers. The TAS3xxx and TAS55xx digital audio proces-sors bring the sound quality of an expensive, high-end A/V receiver to an affordable cost level for con-sumers of home theater-in-a-box systems, flat panel television sets, micro- and mini-component stereos, and other consumer elec-tronic products.High-End Sound QualityThis family of digital audioprocessors offers the highest res-olution for a full and rich digitalsound experience. The TAS3103,TAS5504 and TAS5508 devicesfeature a full 48-bit audio data-path while the TAS3002 has a 32-bit architecture for true CD- andDVD-quality sound.In addition, these digital audioprocessors have a configurablearchitecture that accommodatesthe rapid deployment ofpreconfigured audio processingfunctions and enhanced soundalgorithms from TI and third par-ties. A wide variety of algorithmsand functions such as loud-speaker normalization, second-order tone control, triple slopedynamic range compression, automute, 3D sound, virtual surroundsound and various loudnesscurves are readily available.Key Features of Digital AudioProcessorsDVD-Quality Processors Based on a48-Bit ArchitectureTAS3103•Three-channel digital audioprocessor•PC-based GUI for softwaredevelopment•Configurable processing optionsincluding third-party algorithms•Eight serial audio input chan-nels and three serial audio out-put channels•8-kHz to 96-kHz sample rates•15 stereo/TDM data formats•16-, 18-, 20-, 24- and 32-bitword sizesTAS5504•Four-channel digital audioprocessor with PWM processor Technology for InnovatorsTM Figure 1. TI’s digital audio processors and SRS®TruSurround™ allow stereo speakers to create a5.1 sound image.•Interfaces seamlessly to audio DSPs•Very low noise•Wide dynamic range from 20 Hz to 20 kHz•Extends dynamic range with power supply volume control •Stores three coefficient sets on-device•Intelligent AM interference avoidanceTAS5508•Eight-channel digital audio processor with PWM processor •Interfaces seamlessly to audio DSP and MPEG chips•High efficiency reduces the size of power supplies and heat sinks•Ultra-low noise•Stores a variety of bassmanagement algorithms •Extends dynamic range with power supply volume control •Intelligent AM interference avoidanceCD-Quality Processor Based on a 32-Bit ArchitectureTAS3002•Digital equalization•Dynamic range compression/expansion (DRCE)•Loudness contour algorithm •Integrated 24-bit, 100-dB stereo CODEC•Two single-ended inputs per channel•Six configurable general-purpose inputs for controlling volume, bass, treble and equalizationWhen the Market Won’t WaitThe configurable architecture of TI’s digital audio processors sup-port the demands of consumer electronics (CE) manufacturers who must bring products to mar-ket very quickly. With pre-programmed sound-processing algorithms from third parties and TI, CE manufacturers are able to rapidly respond to changing demands or new preferences as they emerge in the marketplace.For example, one major manu-facturer of consumer electronics products and audio systems,recently brought a new audio product to the marketplace in the record-setting time of just three months. The system featured TI’sSelected Third-Party Audio Processing and Sound Enhancement Algorithms for the TASxxxx Audio ProcessorsNOTE: Not all algorithms are available on all TASxxxx audio processors. Contact TI for the availability of specific algorithms. The following list of algorithms represents a sample of those that are available on TI's TASxxxx audio processors at any one time.TAS5508 digital audio processor/ PWM processor in an innovative bundling with third-party sound enhancement algorithms from SRS®Labs, Inc. The licensing bundle was put together to streamline the typical develop-ment cycle and shorten the sys-tem’s time-to-market. TI’s digital audio support personnel worked closely with SRS Labs to meet the project’s three-month timeframe.“We’re accustomed to fast turnaround times in the consumer electronics space,” said Joanna Skrdlant, director of emerging markets and platform develop-ment of SRS®Labs, “but this par-ticular project with TI was exceptionally fast. The project demonstrated the value of prepro-grammed, TruSurround XT™ vir-tual surround sound functionality and a compatible hardware archi-tecture capable of outstanding sound quality. In the end, all of the pieces fell into place and the parties involved benefited fromthe project.”TI has earned a reputation forthe extensive resources that sup-port manufacturers’ customdesign projects. The company hasimplemented a focused designand support model comprised ofengineering, production, manu-facturing and sales personnel.Many OEMs like Panasonic, JVC,Kenwood, Harman/Kardon, Jamo,LG Electronics, Pioneer, RCA,Koss, Samsung and others havetaken advantage of TI’s extensivesupport for its portfolio of digitalaudio technology to deliver theirproducts to a consumer electron-ics marketplace that changeseveryday.Comprehensive Digital AudioComponentsTI offers a complete suite of digi-tal audio technology which givesmanufacturers the freedom todesign a broad range of systemsthat meet a variety of cost andperformance targets. Many func-tions previously unrealizable oravailable only through analogcomponents are now performedin the digital domain with a newlevel of ease and flexibility.TI’s audio components offermanufacturers the widest dynamicrange and exceptional soundfidelity along with highest degreeof integration to simplify systemdesign. TI’s comprehensive port-folio of audio technology includesdigital audio processors devel-oped specifically for audio signalprocessing functions as well as itsindustry-leading line of DSPs fordecoding specific algorithms andthe audio industry’s most exten-sive selection of digital audioamplifiers.For more information aboutTI’s digital audio processors or TIPurePath™ Technology, go to/homeaudio.TI Worldwide Technical Support InternetTI Semiconductor Product Information Center Home PageTI Semiconductor KnowledgeBase Home Page/sc/knowledgebaseProduct Information CentersAmericasPhone +1(972) 644-5580Fax+1(972) 927-6377Internet/Email/sc/pic/americas.htmEurope, Middle East, and AfricaPhoneBelgium (English)+32 (0) 27 45 54 32Finland (English)+358 (0) 9 25173948France +33 (0) 1 30 70 11 64Germany+49 (0) 8161 80 33 11Israel (English)1800 949 0107Italy800 79 11 37Netherlands (English)+31 (0) 546 87 95 45Russia +7 (0) 95 363 4824Spain+34 902 35 40 28Sweden (English)+46 (0) 8587 555 22United Kingdom +44 (0) 1604 66 33 99Fax +(49) (0) 8161 80 2045Internet/sc/pic/euro.htmJapanFaxInternational +81-3-3344-5317Domestic0120-81-0036Internet/Email International /sc/pic/japan.htmDomestic www.tij.co.jp/picAsiaPhoneInternational +886-2-23786800Domestic Toll-Free Number Australia 1-800-999-084China 800-820-8682Hong Kong 800-96-5941Indonesia 001-803-8861-1006Korea 080-551-2804Malaysia 1-800-80-3973New Zealand 0800-446-934Philippines 1-800-765-7404Singapore 800-886-1028Taiwan 0800-006800Thailand 001-800-886-0010Fax 886-2-2378-6808Email tiasia@ti-china@Internet /sc/pic/asia.htmA042605Important Notice:The products and services of Texas Instruments Incorporated and its subsidiaries described herein are sold subject to TI’s standard terms and conditions of sale. Customers are advised to obtain the most current and complete information about TI products and services before placing orders. TI assumes no liability for applications assistance,customer’s applications or product designs, software performance, orinfringement of patents. The publication of information regarding any other company’s products or services does not constitute TI’s approval, warranty or endorsement thereof.© 2005 Texas Instruments IncorporatedPrinted in U.S.A. by Shas Graphics, Stafford, TXSPRT366Technology for Innovators, the black/red banner and PurePath are trademarks of TexasInstruments. SRS and SRS 3D are registered trademarks and Wow, TruBass, TruSurround,TruSurround XT and Focus are trademarks of SRS Labs, Inc. QSound and QSurround areregistered trademarks and QMSS and QXpander are trademarks of QSound Labs, Inc. BBE is a registered trademark of BBE Sound, Inc.All other trademarks are the property of their respective owners.。
2018年6月英语六级第一套听力原文翻译
Conversation 1M: What’s all that? Are you going to make a salad?男:这都是什么?你要做沙拉吗?W: No, I’m going to make a gazpacho.女:不是,是西班牙冷菜汤。
M: What’s that?男:是个啥?W: (1) Gazpacho is a cold soup from Spain. It’s mostly vegetables. I guess you can call it a liquid salad.女:是西班牙的一种冷汤。
有很多种蔬菜。
你可以叫它液体沙拉。
M: Cold soup? Sounds weird.男:冷菜汤?听起来有些怪。
W: It’s delicious. Trust me! I tried it for the first time during my summer vacation in Spain. You see, in the south of Spain, it gets very hot and summer, up to 42 degrees Celsius, so a cold gazpacho is very refreshing. The main ingredients are tomato, cucumber, bell peppers, olive oil and stale bread.女:很好吃呢,相信我!我在西班牙的暑假第一次尝试做。
在西班牙南部,夏天很热,有42度,所以冷菜汤很带劲哦~主要的成分有西红柿,黄瓜,灯笼椒,橄榄油和陈面包。
M: Stale bread? Surely you mean bread for dipping into the soup?男:陈面包?是把面包浸泡在汤里吗?W: (2) No. bread is crushed and blended in, like everything else. It adds texture and thickness to the soup.女:不是,面包会被压碎然后混合进去,和其它的材料一样。
synthmaster player用户手册说明书
SynthMaster Player User ManualVersion 2.6.16Written ByBülent BıyıkoğluCreditsProgramming, Concept,Design & Documentation : Bulent BiyikogluUser Interface Development: Salvatore ZummoBülent BıyıkoğluFactory Wavetables: GalbanumUser wavetables: Compiled with permission from public archiveFactory Presets (v2.5/2.6): BigToneFrank “Xenox” NeumannNori UbukataRob LeeSami RabiaTeoman PasinliogluUmit “Insigna” UyXenos SoundworksUfuk KevserBeta Testing: Sound designers, , forum users AU Version of SynthMaster is built using Symbiosis by NuEdge Development.XML processing is done by using TinyXMLHTTP/FTP processing is done by using LibCurlCopyright © 2007-2014 KV331 Audio. All rights reserved.This guide may not be duplicated in whole or in partwithout the express written consent of KV331 Audio.SynthMaster is a trademark of KV331 Audio.ASIO, VST, VSTGUI are trademarks of Steinberg.AU is a trademark of Apple Corporation.RTAS, AAX are trademarks of Avid CorporationAll other trademarks contained herein are theproperty of their respective owners.Product features, specifications, system requirements,and availability are subject to change without notice.TABLE OF CONTENTSSynthMaster Player User Manual (1)Introduction (4)System Requirements (4)Download Links for SynthMaster Player FREE (4)Download Links for SynthMaster Player (4)Forgot Your Serial Number? (5)Installing Latest Version (5)Changing Data Folder (6)Getting Started with SynthMaster Player (7)Browsing Presets (8)Controlling the Browser from your MIDI Controller (9)Adding Presets to Your Favorites List (10)Assigning the “Default” Preset (10)Loading a Preset from Your Favorites List (10)Importing Preset Banks Into SynthMaster (10)Assigning Easy Knobs to MIDI Controllers (MIDI Learn) (12)Editing Preset Parameters (12)Easy Parameters (12)Layer Insert Effects (13)Global Insert Effects (13)Preset Polyphony (13)Global/Preset Engine Buffer Size (13)Global/Preset Engine Quality (13)Global/Preset Scale (14)Global/Preset Skin (14)Changing Current Skin Globally (15)Changing Current Skin for the Current Preset (16)IntroductionSystem RequirementsSynthMaster Player comes in the following formats:Format System Requirements DAW RequirementsVST Instrument Windows 7 and aboveMacOSX 10.6 and above2 GB RAM, 2 GHz CPUVST Host supporting VST 2.4pluginsAU Instrument MacOSX 10.6 and above2 GB RAM, 2 GHz CPUAU Host applicationRTAS Instrument Windows 7 and aboveMacOSX 10.6 and above2 GB RAM, 2 GHz CPUProTools 9ProTools 10AAX Instrument Windows 7 and aboveMacOSX 10.6 and above2 GB RAM, 2 GHz CPU32bit: ProTools 10.3.6 and above64bit: ProTools 11 and aboveDownload Links for SynthMaster Player FREESynthMaster 2.6 Player FREE installer can be downloaded at:Windows-32 bits: /DownloadFile.aspx?fileID=83Windows-64 bits: /DownloadFile.aspx?fileID=84Mac OSX (32/64bits): /DownloadFile.aspx?fileID=85This installer contains the latest binaries and all the data files necessary to install SynthMaster 2.6 Player FREEDownload Links for SynthMaster PlayerSynthMaster 2.6 Player FREE installer can be downloaded at:Windows-32 bits: /DownloadFile.aspx?fileID=81Windows-64 bits: /DownloadFile.aspx?fileID=82Mac OSX (32/64bits): /DownloadFile.aspx?fileID=86This installer contains the latest binaries and all the data files necessary to install SynthMaster 2.6 Player. To start your download for SynthMaster Player you should enter your registered email address and serial number:Forgot Your Serial Number?If you forgot your serial number, it is very easy to retrieve it. Just go to/requestlicensefile.aspxenter your registered email address, and that’s it. You’ll receive your serial number plus the above download links in a couple of minutes!Installing Latest VersionOnce you download the zip archive containing SynthMaster 2.6 Player setup files, simply extract its contents to a temporary location and run the setup application: (SynthMaster26PlayerSetup.exe on Windows, SynthMaster26PlayerSetup.pkg on MacOSX)By default, SynthMaster will be installed under the following directories:Windows: C:\Program Files\Vstplugins\SynthMaster PlayerMacOSX: /Library/Application Support/KV331 Audio/SynthMaster PlayerOn MacOSX, you might get the following warning message after you install SynthMaster Player, and run your DAW application:In that case, please copy the following files manually:SynthMasterLicenseKey.txt to -> /Library/Application Support/KV331 Audio/SynthMaster Playerponent to -> /Library/Audio/Plug-Ins/ComponentsSynthMasterPlayer.vst to -> /Library/Audio/Plug-Ins/VSTSynthMasterPlayer.dpm to -> /Library/Application Support/Digidesign/DAE/Plug-InsChanging Data FolderIf you want to place SynthMaster Player data files in a different folder, there is an easy way to do that:Copy all SynthMaster folder/files except SynthMaster2.dll, SynthMaster2FX.dll and SynthMasterPlayerFolders.txt into the new folderOpen up the SythMasterPlayerFolders.txt file using a text editor, and change the following line:RootFolder=<new folder path goes here>Then save the SynthMasterPlayerFolder.txt file and you’re done!Getting Started with SynthMaster PlayerNow that we you’ve installed SynthMaster Player, it’s time to explore it!Let’s start by instantiating a SynthMaster Player instance in our DAW application:SynthMaster Player opens up with its default “Player Skin”. One of the unique features of SynthMaster is that it support multiple skins. You can even edit the skins that come with SynthMaster Player and customize your own skins, with the Interface Editor that comes with SynthMaster (just download and install SynthMaster DEMO for that:Browsing PresetsSynthMaster Player comes with a comprehensive preset library, with 800 presets to start with (the free version has only 200):When you select a preset from the list, it is loaded from disk, and its 12 easy parameters and insert effects are displayed. You can tweak the easy parameters right from the browser or using you MIDI controller’s knob/sliders that are globally linked to the easy parameters.The presets can be filtered byInstrument TypeAttributesMusic StylePreset AuthorBank NameFor instance, if you want to see all Mono Bass Factory presets for Electro music style created by Aiyn Zahev, click on Bass, Mono, Electro, Aiyn Zahev and then Factory Presets:To load a preset on the list: click on it:To go to the next preset on the list: click on the arrow, or press the “Down” key on your keyboard. To go to the previous preset on the list: click on the arrow, or press the “Up” key on your keyboard. To scroll down the list: move your mouse wheel down (when mouse is over the presets list)To scroll up the list: move your mouse wheel up (when mouse is over the presets list)To search for a preset by name: type the text into the search textbox and press enter or click on the Search button. The matching presets will be displayed on the list:Controlling the Browser from your MIDI ControllerIt is possible in SynthMaster Player to control the preset browser from your MIDI controller, by sending MIDI CC messages. You can assign buttons on your controller for scrolling up/down Instrument typeMusic stylePreset AuthorPresetsTo link a button to a list, move your mouse over the list, and then click on the right mouse button. The popup menu will show up with 2 selections: Prev and NextAfter you select one of the menu items, press the button on your MIDI controller to send the MIDI CC message, SynthMaster Player will learn the button and establish the link between the button and the browser function. SynthMaster Player saves this link in its configuration file, so you have to do this linking only once.Adding Presets to Your Favorites ListIt is possible to mark the presets you like as ‘favourites’ so that you can easily load them again in your sessions. To add a preset to your ‘favourites’ list:Click on the presetname to choosethe presetRight click on thepreset name tobring up thedropdown menuChoose “Add toFavourites”Assigning the “Default” Preset“Default” preset is the preset that is loaded when a new instance of SynthMaster Player is created. To assign a preset as the “default” preset:Click on the presetname to choosethe presetRight click on thepreset name tobring up thedropdown menuChoose “Set AsDefault Preset”Loading a Preset from Your Favorites ListOnce you assign your favourite presets, you canload them back by right clicking on the currentpreset name (displayed on the top header) andthen choosing a preset listed under the “LoadFavourite: “ category.Importing Preset Banks Into SynthMasterSynthMaster Player and Player FREE allows you to use the preset banks released by KV331 Audio. If you purchase preset banks from our website , you will notice that most of them require manual installation (expect the ones that come with their own installers).Starting with version 2.6.15, we’ve made it very easy to import those banks into SynthMaster Player:1. Move your mouse under the Bank list and right click. Popup menu will show up. Select Importpreset bank(s) menu item:2. Directory browser dialog will open up. Browse to the folder where you extracted the zip file thatcontains the preset bank files (that end with .smpb / .smar) and click OK to import the files:3. If import is successful, the preset browser will be refreshed and you’ll see the imported banks : In case importing fails (due to write permission error), you can manually copy the preset bank file(s) (andthe archive file(s) if the preset bank uses any custom samples/waveforms) to the following locations: Windows: C:\Program Files\Vstplugins\SynthMaster Player\PresetsMacOSX: /Library/Application Support/KV331 Audio/SynthMaster Player/PresetsAssigning Easy Knobs to MIDI Controllers (MIDI Learn)In SynthMaster Player, easy parameters (knobs and XY Pads) can be assigned to MIDI controllers. This assignment is achieved by the MIDI Learn feature in SynthMaster Player. The easy parameter assignments are saved in the configuration file so the assignments are global, not per preset.parameter (knob), and then right click to bring upthe content menu.Click on the MIDI Learn menu item, and then startmoving the corresponding knob/slider/etc on yourMIDI controller device to send MIDI ControlChange (CC) messages. As soon as SynthMasterreceives a CC message, it will assign thatcontroller to the parameter.your mouse over the parameter (knob) that’s linkedto a MIDI controller, and then right click to bring upthe content menu.Click on the Remove MIDI CC Link menu item, andthe assignment will be removed.Editing Preset ParametersSynthMaster Player has limited editing capabilities compared to SynthMaster. For each preset, the following parameters can be edited by the user:Easy ParametersEasy parameters are assigned by the sound designer to enable tweaking most important parameters in the preset’s design. Each preset has 8 easy knobs and 2 XY Pads.Layer Insert EffectsFor each of the 2 layers there are 5 insert effects that are assigned by the sound designer. To turn on/off an assigned effect click on the effect name ,its state will toggle.Global Insert EffectsThere are 2 global effect buses with 5 insert effect slots for each. To turn on/off an assigned effect click on the effect name, its state will toggle.Preset PolyphonyPolyphony is used to limit the maximum number of voices that thesynth can play at a time. By lowering polyphony, you can reduce theCPU usage of the synth. Its value can be set between 4-64 voices.Global/Preset Engine Buffer SizeEngine buffer size determines the smallest buffer size at which internalLFOs, envelopes, etc. are recalculated. Increasing engine buffer sizewill lower CPU usage. It takes the following values:Short (16 samples)Normal (32 samples)Large (64 samples)XLarge (128 samples)XXLarge (256 samples).TIP: If Global Engine Buffer Size is not set to “Preset” it will override Preset Engine Buffer Size parameter. TIP: For best performance set buffer size to Normal/Large during tracking, and set it to Short when bouncing to audio.Global/Preset Engine QualityEngine quality determines the internal oversampling rate.Oversampling helps reduce aliasing noise that’s generated especiallyat high pitches. The more oversampling used, the more CPU cycleswill be consumed. The engine quality parameter takes the followingvalues:Draft (no oversampling)Good (2 times oversampling)Better (3 times oversampling)Best (4 times oversampling)TIP: If Global Engine Quality is not set to “Preset” it will override Preset Engine Quality parameter.TIP: For best performance set engine quality to Draft during tracking, and set it to Good/Better/Best when bouncing to audio.Global/Preset Scaleeach preset separately. By default, it comes with only 1 scaledefinition: EqualTempered scale. The scale definitions, which are inScala format, are stored under:Windows : C:\Program Files\VstPlugIns\SynthMasterPlayer\ScalesMacOSX: /Library/Application Support/KV331Audio/SynthMaster/ScalesTIP: If Global Scale is not set to “Preset” it will override Preset Scale parameter.TIP: If you want to use different tunings, please copy the scale files (in Scala format) into the above folders.Global/Preset SkinSynthMaster Player comes with 2 different skins (which will be 3 quitesoon!). By changing the Preset Skin parameter, you can use adifferent skin for the current preset. For the skin change to take effect,you have to close and reopen the plug-in window.TIP: If Global Skin is not set to “Preset” it will override Preset Skin parameter.Changing Current Skin GloballyTo change the current skin globally (for all SynthMaster Player instances), you should1. Click on the left/right arrows (next to the parameter name) on the header to display the currentvalue of the Global Skin parameter:2. Click on the left/right arrows (next to the parameter value) on the header to change Global Skinparameter’s value:3. Close and then reopen the skin:Changing Current Skin for the Current PresetRather than using a global skin for all SynthMaster Player instances, you can have a different skin for each instance. The skin name is saved inside preset settings. To change the current skin for the current instance, you should1. Click on the left/right arrows (next to theparameter name) on the header to displaythe current value of the Global Skinparameter2. Click on the left/right arrows (next to theparameter value) on the header to changeGlobal Skin parameter’s value to Preset3. Click on the left/right arrows (next to theparameter name) on the header to displaythe current value of the Preset Skinparameter4. Click on the left/right arrows (next to theparameter value) on the header to changePreset Skin parameter’s value to the skinyou want to switch to5. Close and then reopen the skin。
2018年6月大学英语六级真题试卷及答案(三套全)
2018年6月大学英语六级真题试卷及答案(三套全)目录2018年6月大学英语六级真题试卷及答案(一) (1)快速对答案 (16)2018年6月大学英语六级真题试卷及答案(二) (17)快速对答案 (32)2018年6月大学英语六级真题试卷及答案(三) (32)快速对答案 (42)2018年6月大学英语六级真题试卷及答案(一)Part I Writing(30minutes) (请于正式开考后半小时内完成该部分,之后将进行听力考试)Directions:For this part,you are allowed30minutes to write an essay on the importance of building trust between employers and employees.You can cite examples to illustrate your views.you should write at least150words but no more than200words.Part II Listening Comprehension(30minutes) Section ADirections:In this section,you will hear two long conversations.At the end of each conversation,you will hear four questions.Both the conversation and the questions will be spoken only once.After you hear a question,you must choose the best answer from the four choices marked A),B),C)and D).Then mark the corresponding letter on Answer Sheet1with a single line through the centre.注意:此部分试题请在答题卡1上作答。
Practical Information Security - 说明书
309© Springer International Publishing AG 2018 I. Alsmadi et al., Practical Information Security , https:///10.1007/978-3-319-72119-4AAccess controldatabase security mechanisms, 145multilevel, 146query modification, 146stored procedures, 146views, 146mobile and wireless security, 174Access Control Lists (ACLs), 56, 59, 63Address resolution protocol (ARP), 129Advanced Encryption Standard (AES), 99, 174Adwarefreeware/shareware, 22infected websites, 22infinite pop-ups, 21man-in-the-middle attacks, 21pop-up ads, 20slow down device’s, 21spying, 21users, 22Alternate Data Stream (ADS)ADSCheck, 217ADSSpy, 217, 218CAT tool, Nix Utilities, 217feature, 216hiding data, 217StreamArmor, 218Anti-Malware detection techniques, 196, 197Apple iOS security, 170Apple IPhones ™ cloud locks, 164Apple Mac’s FileVault, 109Applications sectionanti-virus software application, 13vulnerability scanning, 13–15ARP Spoofing attacks, 127–129Asset value, 9AttackerMalware, 140Network, 140notice, 144Attribute-based access control (ABAC), 66Authentication, Access control andAccountability (AAA), 64BBackdoors, 31BlowFish, 100Bootkits, 23Boot-sector viruses, 38Browser Hijacking, 41CCarriage return line feeds (CRLF) Injectionattacks, 42Certificate Authorities (CA), 104, 113Cipher Block Chaining (CBC), 97Cipher FeedBack (CFB), 97Code injection, 41–43Confidential information, 4Counter (CTR), 97Crimeware, 35–37Cross site request forgery (CSRF), 143, 144Cross-site Scripting (XSS), 42Crypto ransomware, 24Cyber-attacks, 121Index310DData encryption standard (DES), 62Data modification attacks, 126, 127 Database securityaccess control (see Access control,database security)applications, 155attack, SQL injection (see SQL injectionattack)management system, 144measures, 145privacyadding/deleting records, 147data perturbation/anonymization, 148output perturbation, 148query restriction, 148statistical database, 146, 147Denial of Service (DoS) attack, 5–6Digital Encryption Standard (DES), 96 Disaster Recovery Plan (DRP), 80, 85, 89 Discretionary Access Control (DAC), 56 Disk and computer forensicsADS, 216–218analysis, 208, 209applicationsKali Linux, 241Linux Logs, 241Linux Rootkit Checker, 242memory analysis with volatility, 240Windows registry, 241data recovery, 207, 208digital investigations, 204event viewers, 232, 233ext systems (see Extended file system (Ext)) factors, 204FAT system, 209, 210, 212, 213HFS+ systems, 221–222HFS+ volume headers, 222image acquisition, 205–207Internet usage and traces (see Internettraces)investigationsLinux (see Linux operating systems)MAC operating systems, 236, 237Windows operating systems, 227–229 memory (see Memory forensics)NTFS systems, 214–216operating system, 205skillsBinwalk disk forensic tool, 238file carving, 238–240foremost forensic tool, 237hex-editor program, 238raw format image acquisition, 238 unallocated disk, 214web logs, 233Windows registry, 229Distributed denial of service (DDoS) attack, 30 Distribution, Crimewareaffiliate marketing, 37attachment, 36hacking, 37Internet Worm, 36Piggybacking, 36Web Browser Exploit, 36Dynamic link library (DLL) file, 33EEICAR test files, 13Electronic Code Book (ECB), 97Electronic mail (email) virus, 38Email (Mail command/SMTP) injection, 42 Encrypted salt-sector initialization vector(ESSIV), 110Encrypting File System (EFS), 108 Ethernet Network cards (NIC), 251 Extended file system (Ext)file recovery, 220, 221high level layout, 218inode, 219journal process, 219Linux, 218Minix, 219eXtensible Access Control Markup Language (XACML), 70FFile allocation table (FAT) systemcorrupted data, 213data area, 210deleted data, 212DOS and Windows operating systems, 209 extensions, 213FAT12 disk sizes, 209, 210FAT16, FAT32 and NTFS, 210floppy, 209fsstat tool, 211hidden data, 212mmls tool, 211primary and backup FAT structures, 210reserved area, 210unallocated/formatted data, 213File infectors, 38File-sharing/peer-to-peer (P2P) worm, 28Index311Firmware, 24Flash worm, 28Foremost tool, 259, 260GGlobal Navigation Satellite Systems (GNSS), 301GNU Privacy Guard (GnuPG), 105HHardware, 24Hardware/network security issues in mobile/smart devices, 173Hardware-based keyloggersacoustic keyloggers, 34electromagnetic emissions, 34firmware-based, 34keyboard hardware, 34keyboard overlays, 34optical surveillance, 34physical evidence, 34smartphone sensors, 34wireless sniffers, 34Hierarchical file systems (HFS), 221, 222 Host header injection, 42HTML-Proxies, 29IInformation hiding and protectionasymmetric encryptionalgorithms, 100–104commitment schemes, 114cryptography applicationsApple OS/X, 109–111browsers, 105–107e-commerce, 104, 105email communication, 105Internet/online communications ande-commerce, 104operating systems and disks, 107–109telecommunication/networks, 107 digital time-stamping, 115encryption, 92experience/ability section, 119, 120hashing/steganography, 92information authentication, 113information concealment, 91, 92information concealment/authenticitytechniques, 115–117information integrity, 91information integrity and authenticationtechniques, 111–113information system/website, 92, 93knowledge sectionsciphering/encryption algorithms, 95cryptography/encryption, 93–95key-based encryption techniques, 95methods, 95message authentication, 113password storageand verification, 114, 115skills sectionencryption algorithms, 117encryption applications, 118information concealmentapplications, 119information integrity algorithms, 118information integrity applications, 118 symmetric encryption algorithmsblock ciphers, 95–100BlowFish, 100stream ciphers, 100Information locationdescription, 3hard and flash drives, 4in motion, 4Information security, 10–12Information security cases, 12, 13 Information sensitivitycategories, 4confidential information, 4private information, 5public information, 5Information statecreation, 2description, 2processing, 3storage, 3transition, 3Information taxonomy, 2Internet Bot, 31Internet DOS, 29Internet of Things (IoT), 11Internet Protocol Security (IPSec), 107 Internet Relay Chat (IRC) worm, 28 Internet tracesapplications, 229Google Chrome, 230, 232Mozilla Firefox, 231MS Internet explorer, 230OSI layers’ perspective, 230Intrusion Detection/Protection Systems (IDS/ IPS), 267–269Index312JJail-breaking, mobile devices, 172KKeyloggers, 32–35Knowledge sections, 1–12, 17–44LLightweight Directory Access Protocol(LDAP) injection attacks, 42 Linux operating systemsdirectories, 234disk forensics, 233forensic investigation, 234forensic investigator, 235forensic tools, 234Linux logon log files, 235tools, 235versions/flavors, 233web browsers, 235Linux Rootkit Checker, 242Linux Unified Key Setup (LUKS), 110 Locker ransomware, 24Logic bombs, 41MMAC flooding attack, 131, 132MAC operating systems, 236, 237 Macro viruses, 38Malware analysis, Software code security anti-malware detection techniques, 195 manual, 197NSRL server, 198software applications, 194Malware attacker, 140Malware threatsaccess or intrusion method, 164Android platform, 166Brain Test, 167Dendroid, 166Hiddad, 167hiding methods, 165payload, 164Pegasus spyware, 165Pretender Applications, 166propagation, 164RuMMS, 167Triada, 167ViperRAT, 166XcodeGhost, 167Malwaresapplications sectiondangerous website, 46–47Keylogger, 45, 46Microsoft safety scanner, 44, 45outlook account, 47, 48TDSSKiller, 48–50knowledge sectionsAdware, 20–22backdoors, 31browser Hijacking, 41classes, 18code injection, 41–43Crimeware, 35–37hardware-based keyloggers, 34, 35Internet Bot, 31, 32Keylogger, 32, 33logic bomb, 41pharming, 43phishing, 40Ransomware, 24–26Rogue security software, 31Rootkits, 22–24Scareware, 37software Bugs, 39software-based keyloggers, 33spamming, 40spyware, 18–20taxonomy of, 17Trojan horses, 29–31Viruses, 37–39Worms, 26, 28, 29skills section, 44Memory forensicsanalysis with volatility, 240BIOS, 223computing systems, 223data analysis, 223information, 223, 224ROM, 223size, 223toolsanalysis, 225Dumpit, 225FTK Imager memory capture, 226Linux, 227Redline, 226simple/generic, 225V olatilitux, 226volatility, 225, 226virtual, 223Mobile and wireless securityaccess control models, 174AES crypto-engine, 174age of using mobile phones, 161Index313anti-malware apps, 168application code signing, 162applications, 178booting process, 173bring your own device (BYOD), 162, 163 consumer reports, 161hardware/network, 173installation, unknown/un-trusted stores,167jail-breaking, 172location-based services and privacycontrol, 176malware threats (see Malware threats)operating systems, 170OSNs, 169physical thefts, 172remote wipe feature, 176Sandboxing, 171skillsSmart devices operating systems, 177Software security issues, 177theft and loss/unauthorized access, 163,164TLS/SSL, 175transmissions, 175unsecured network connection, 175updates, operating systems, 172usage, 161users/software, 162Mobile anti-malware systems, 168Mobile forensicscompany to seize, 307device folders, 305device information, installed apps, callhistory, contacts, and messaging,307device seize, 301device states, 300, 305GPS, 301, 306hardware and software, 299mobile device features, 298operating systems, 299, 300, 304SIM card, 300, 306tools, 301, 302Monte Carlo analysis, 79Multi-variant virus, 38NNAC, see Network access control (NAC) National Institute of Standards andTechnology (NIST), 99Near Field Communication (NFC), 299 Network access control (NAC), 125Network attacker, 140Network attacksaddress resolution protocol, 129countermeasures, 129data modification, 126, 127denial, service attack, 130eavesdropping, 125, 126MAC flooding, 131, 132Packet sniffers, 134SMURF, 133SpoofingARP, 127–129identification, 126TCP SYN flooding, 132Network forensicsARP spoofing, 273DHCP servers, 250Ethernet cards promiscuous mode, 251firewalls, 267Foremost, 259, 262, 273IDS/IPS, 267–269, 274, 275, 277, 279, 281 NIC Promisc Mode, 273packet filtering, 254–257, 261port mirroring, 264real time, analysis, 249routers, 265, 266SDN switches, 273static, analysis, 249switches, 261–264, 274traffic analysis, 247–249, 272wire tapping, 250wireless communication, 269, 270wireless tapping, 250, 251Wireshark, 252–255Network layer, 124Network securityapplication layer, 122applications, 137attacks (see Network attacks)cyber-attacks, 121network traffic analysis, 134–137OSI Model, 121–123transport Layer (see Transport layer)Non-resident viruses, 38NTFS systems, disk forensics, 214–216OObject-based access control (OBAC), 66, 67 Online Social Networks (OSNs), 169Open Systems Interconnection model (OSIModel)layers, 121, 122protocols, 123Index314Operating systems security issues, mobile/smart devices, 170 Organization’s risk tolerance, 73Output FeedBack (OFB), 97PPacket Sniffing attacks, 134Personal Information Manager (PIM), 299 Pharming, 43Phishing, 40Physical security, 126Physical thefts, mobile phones, 172 Physical-world DOS, 29Physical-world Reconnaissance, 29Policy Administration Point (PAP), 67 Policy Decision Point (PDP), 66Policy Enforcement Point (PEP), 66Private information, 5Public information, 5Public Key Encryption (PKE), 104RRadio frequency identification (RFID) virus, 38 Ransomware, 24, 26Remote wipe feature, 176Resident viruses, 38Riskdefinition, 73impact of, 73metrics, 74monitoring, 74response, 74security, 73tracking, 74Risk management and planningapplications’ sectionassessment/model, 89cyber security plan, 89–90knowledge sectionsapproaches, 76, 82, 83assessment and model, 79cyber security awareness, 81, 86disaster recovery, 80, 81, 85DRP sections, 85–86forensics resources, 81, 82incident response planning, 79, 80, 83, 84policies, 77, 78security, 75, 76self-assessment survey, 84, 85tolerance, 76, 77, 83skill’s sectiondevelopment process, 88disaster recovery plan, 89disaster recovery planning, 87–88incident response plan, 88metrics, 87security incident responses, 87tracking, 87Rivest-Shamir-Adleman (RSA), 101, 102 Rogue security software, 31Role-based access control (RBAC)and OBAC, 66, 67in MAC, 64permissions, 64policies/roles, 65policy-based security systems, 64 Rootkits, 22–24, 48–50RuMMS, 167SSandboxing, 171Scareware, 37Script virus, 38Secunia PSI software, 14Secure phone booting process, 173Secure shell (SSH), 107Secure Socket Tunneling Protocol (SSTP), 107 Secure Sockets Layer (SSL), 104Securitymobile and wireless (see Mobile andwireless security)web (see Web security)Security access controlsapplications sectionsOBAC systems, 70RBAC systems, 70websites and web-applications, 69 authentication, 55components, 55database management systems, 53different database management, 54different operating systems, 54different websites and web-applications, 54 knowledge sectionsdatabase management systems, 59, 60digital certificates, 62–63distributed and operating systems, 63, 64identity management, 61Kerberos, 62OBAC and RBAC, 56operating and file systems, 56–59permissions, 56session time-out, 62Index315SSO methods, 61websites and web-applications, 60–61 OBAC, 53, 54operating systems, 53RBAC, 53, 54 (see Role-based accesscontrol (RBAC))skills sectionsin Linux, 68, 69Windows SAM database, 67, 68 websites and web-applications, 53 Security awareness, 10Security countermeasurementdescription, 10human, 10legal, 10organizational, 10technical, 10Security education, 10Security goalsaccountability, 6authentication, 6authorization, 6a3vailability, 5confidentiality, 5description, 5identification, 6integrity, 5non-repudiation, 7privacy, 6Security risks, 7, 8Security threat, 8Security training, 10Single-Sign-On (SSO), 61Skills section, CIA triad - confidentiality,integrity and availability, 12, 13 Smart devices operating systems and security issues, 177SMURF attacks, 133Software Bugs, 39Software code securityevaluation, software programs, 198management and control of information, 183 perspectives, 199skillsMalwares, 198reviews, 198testing tools, 197and vulnerability issues (see Vulnerability, Software code security) Software Defined Networking (SDN)Controllers, 64Software security issues, smart devices, 177 Software-based keyloggers, 33API-based, 33grabbing based, 33hypervisor-based, 33Javascript-based, 33kernel-based, 33memory injection based, 33 Spamming, 40SpywareActiveX control, 19anti-spyware, 19browser add-ons, 19computer programs, 18devices, 19disable active-X, 20drive-by download, 19installation, 20piggybacked software installation, 19pop-up blocker, 20type of, 18"X" icon, 20SQL GRANT/REVOKE commands, 60 SQL injection (SQLi), 42SQL injection attackautomated, 149deleting, updating and inserting data, 154 initiation, 150input validation vulnerability, 150, 151mitigation, 152skills, 152, 153statements, 149steal data, 150, 152Web application, 154Yahoo V oices, 149Statistical database, 147Steal data, 150, 152Subscriber Identity Module (SIM) card, 300 Swarm worm, 28TTCP SYN flooding, 132TDSSKiller, 48, 49Theft and loss/unauthorized access, mobiledevices, 163, 164Time Stamping Authority (TSA), 115 Transmission Control Protocol (TCP), 122 Transport layerNetwork layer, 124routing and translation, addresses, 125types of addresses, Internet, 124, 125UDP, 123TCP, 122Transport Layer Security (TLS), 105Index316Transport Layer Security (TLS) or SecureSocket Layer (SSL), 175 Triada, 167Trojan horses, 29–31TrueCrypt, 110Trusted Third Party (TTP), 104UUbuntu shadow content, 114Unsecured wireless network connection, 175 User Datagram Protocol (UDP), 123User-mode/kernel-mode hybrid Rootkit, 23 Users/software security,mobile/smart devices, 162VVeraCrypt, 110Vetting, 162Virtual Private Networks (VPNs), 105 Virus detection pop-up window, 14Virus life cycledormant phase, 39execution phase, 39propagation phase, 39triggering phase, 39Viruses, 37–39Vulnerability, 9Vulnerability threats, 74Vulnerability, Software code securityanti-malware detectiontechniques, 195–197buffer and stack overflows, 184design flawschanges, 193control modules and APIs, 193encryption, 193sensitive data, 193validate user inputs, 192, 193design principlesand practices, 190–192exception handling, 194feedback exceptions, 194malware analysis, 195manual malware analysis, 197memory leak and violationissues, 185race conditions, 187, 188SQL injection and XSS, 185–187static and dynamic security analysis,188–190techniques and tools, 188WWarhol worm, 28Web application code, 140Web browser, 140Web forensicsartifacts for investigation, 294criminal and civil cases, 295criminal cases with web, 291emailand browsers information, 292clients, 285file reports, 291files, 289, 290forensics tools, 286, 287headers, 287–289headers review, 293mail servers, 285protocols, 285scan for archived files, 293software, 295steps, 284web browsers, 291, 292web browsing history, 294, 295Web logs, 233Web securityand database (see Database security)applications, 139, 155Cloud, 139online transactions, 139threat models, 140–144Web threat modelscross site scriptingCookie encryption, 143Cookies associated with a web page,142impacts, 143sever response, 142techniques, 141textbox and text area, 141, 142URL, 141CSRF, 143, 144malware attacker, 140network attacker, 140web attacker, 140Wide Area Networks (W AN), 265Windows operating systemsevent viewers, 232, 233forensic investigationsartifacts, 229backdoors/Rootkits, 228disk, 228keyword searches, 227malicious processes, 228Index317review, 227unauthorized user accounts/groups, 228versions of, 228Windows registry, 229, 241Wire tapping, 250Wireless security, see Mobile and wirelesssecurityWireless tapping, 250, 251Wormsactivation, 27malicious code, 26payloads, 28propagation techniques, 28scanning, 27types of, 27, 28XXcodeGhost, 167XML injection, 42XPath injection, 42Index。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
[键入文字]
2018年全球增材制造市场价值93亿美元,增长率为18%
marTechPublishing是一家专注于增材制造市场的领先行业分析公司,近日,该公司发布了年终AM市场评估报告,称2018年全球增材制造市场,包括硬件、软件、材料和服务,在增长了18%后,创造了93亿美元的收入。
该报告题为《2019年增材制造市场展望和机遇总结》,新报告还对2018年至2027年的总增材制造业进行了总结和预测,首次提供了一个包含关键市场规模和预测数据的全面数据库,跟踪整个增材制造业价值链和活动从2018年的硬件、材料、软件到零件生产服务,同时提供对未来的宝贵见解。
该分析侧重于为金属和聚合物增材制造领域提供细分市场数据和见解,同时突出AM市场中最具影响力的活动。
其中包括航空航天、医疗保健、汽车、服务机构以及消费品、能源和工业等新兴机遇等关键领域。
SmarTechPublishing的新报告旨在为希望跟踪整个价值链中增材制造业进展的公司和/或业务部门提供资源,这些公司还需要深入的市场数据来量化行业中的增长和关键指标,如打印技术和市场上的硬件安装、按材料类型分列的材料出货量、按行业分列的外包零部件生产价值等等。
随附的数据库包括X数据表,为用户提供无与伦比的现成市场数据,同时总结行业的关键驱动因素和趋势,并就2019年及以后的预期提出建议。
在2018年,增材制造市场似乎已经重新获得了其演变——均衡增长的重要因素。
所有细分市场现在似乎都在以类似的方式发展和增长,共享目标和解决方案跨越细分市场。
在3DSystems和Stratasys这样的实体中观察到这种积极的发展,面对比前几年更加复杂的竞争格局,看到更加一致的正增长结果,这两家公司在2018年来之不易的成功是帮助聚合物AM部门增长到估计近55亿美元。
1。
