Chapter 16 Using Queueing Network Modelling Software
容器技术智慧树知到期末考试章节课后题库2024年山东劳动职业技术学院

容器技术智慧树知到期末考试答案章节题库2024年山东劳动职业技术学院1.Docker Swarm需要网络的支持,但不依赖于特定的网络组件。
()答案:错2.Rancher的用户可以利用“应用商店”来部署各种应用,并可以在应用有新版本时实现自动升级。
()答案:对3.在Kubernetes配置文件中,可以使用nodeSelector来指定容器运行在特定的节点上。
()答案:对4.在Kubernetes配置文件中,可以使用securityContext来设置容器的安全策略。
()答案:对5.使用kubectl get命令可以获取集群中所有资源的信息。
()答案:对6.虚拟化技术是基于系统的隔离,容器技术是基于程序的隔离。
()答案:对7.Kubernetes配置文件只支持YAML格式。
()答案:错8.在docker swarm中,节点分为管理节点和工作节点两种类型。
()答案:对9.使用kubectl describe命令可以获取资源的详细信息,包括资源的历史、事件等。
()答案:对10.使用docker-compose stop命令只会停止应用,但不会删除容器。
()答案:对11.使用docker-compose up命令可以在后台启动应用。
()答案:对12.Docker镜像只能包含一个应用。
()答案:错13.使用docker node rm命令可以从docker swarm中删除一个节点,但该节点必须先离开swarm。
()答案:对14.Docker Compose文件可以用于部署到生产环境。
()答案:对15.Docker镜像的层可以合并成一个单独的镜像。
()答案:对16.docker CE是社区版Docker。
()答案:对17.在docker swarm中,一个节点只能同时担任管理节点和工作节点的角色。
()答案:错18.Rancher的组成主要包括基础设施编排、容器编排与调度、应用商店和企业级权限管理。
()答案:对19.使用docker-compose rm命令可以删除已停止的Compose应用,包括容器和网络,但不会删除卷和镜像。
博世 D7212 使用说明书
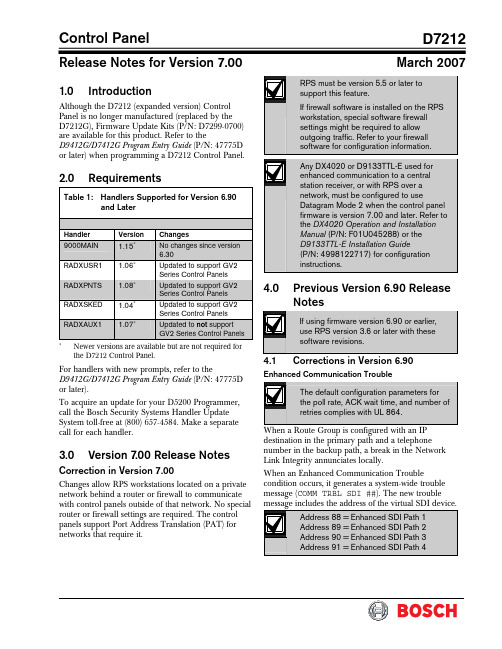
Control PanelD7212Release Notes for Version 7.00March 20071.0 IntroductionAlthough the D7212 (expanded version) Control Panel is no longer manufactured (replaced by the D7212G), Firmware Update Kits (P/N: D7299-0700) are available for this product. Refer to theD9412G/D7412G Program Entry Guide (P/N: 47775D or later) when programming a D7212 Control Panel.2.0 RequirementsTable 1: Handlers Supported for Version 6.90and LaterHandler Version Changes 9000MAIN 1.15∗No changes since version 6.30RADXUSR1 1.06∗Updated to support GV2 Series Control PanelsRADXPNTS 1.08∗Updated to support GV2 Series Control PanelsRADXSKED 1.04∗Updated to support GV2 Series Control PanelsRADXAUX1 1.07∗Updated to not support GV2 Series Control Panels∗Newer versions are available but are not required for the D7212 Control Panel.For handlers with new prompts, refer to theD9412G/D7412G Program Entry Guide (P/N: 47775D or later).To acquire an update for your D5200 Programmer, call the Bosch Security Systems Handler Update System toll-free at (800) 657-4584. Make a separate call for each handler.3.0 Version 7.00 Release NotesCorrection in Version 7.00Changes allow RPS workstations located on a private network behind a router or firewall to communicate with control panels outside of that network. No special router or firewall settings are required. The control panels support Port Address Translation (PAT) for networks that require it.4.0 Previous Version 6.90 ReleaseNotes4.1 Corrections in Version 6.90Enhanced Communication TroubleWhen a Route Group is configured with an IP destination in the primary path and a telephone number in the backup path, a break in the Network Link Integrity annunciates locally.When an Enhanced Communication Troublecondition occurs, it generates a system-wide trouble message (COMM TRBL SDI ##). The new troubleD7212The trouble condition is also sent through a backup path to the central station as Communication Trouble SDI ##, using the same virtual address numbers as the trouble messages. The communication trouble event also creates new Modem IIIa 2 messages that thecentral station might need to add to their automation software. Refer to Events 157 to 160 in the D6600 Computer Interface Manual (P/N: 4998122703) for the details of central station data changes. Unsupported Point TypePreviously, if the value of 11 was used with RADXPNTS version 1.06 or later when configuring the Point Index parameters, the control panel might not operate as expected. This condition is corrected so that the control panel responds to a P# Type value of 11 as a disabled point.5.0 Previous Version6.80 ReleaseNotes5.1Corrections in Version 6.805.1.1Local Event ReportingSeveral changes in this release prevent the controlpanel from sending local alarm events intermittently to the central stations. All local alarm events now remain local. 5.1.2Ethernet Link IntegrityFor UL 1610 Line Security (formerly Grade AA) Intrusion System installations and for UL 864 Commercial Fire installations, use the parametersshown in Table 2 when configuring the Heartbeat Poll. For additional details, refer to Programming PathNumbers and IP Addresses for Enhanced Communications in the D9412G/D7412G Program Entry GuideTable 2: Parameters for Heartbeat PollConfiguration in Version 6.801Number of IP Paths Poll Rate (sec) ACK Wait Time (sec)Number of Retries1 30 62 to 19 1 30 8 2 to 12 1 30 10 2 to 8 1 30 12 2 to 5 1 30 14 2 to3 1 60 6 2 to 14 1 60 8 2 to 8 1 60 10 2 to5 1 60 12 2 1 752 102 32 1 906 2 to 9 1 90 8 2 to 4 1 90 10 2 1 120 6 2 to 4 1 145 522 752 82 323 752 62 324 75252321 The parameters in this table are for Version 6.80 only . 2Recommended settings for the corresponding number of IP paths.5.2 Enhancements in Version6.80Summary Fire Relay SustainWhen the Silent Alarm Relay for Area 2 isprogrammed with 24, the Summary Fire Alarm Relay remains active until all Fire Alarms are cleared from the keypad display. The default operation is consistent with the Summary Fire Relay operation in Version 6.60 and older. This feature provides a method of maintaining fire strobes after the alarm bells are silenced.5.3 Known Issue in Version6.80When a Route Group is configured with an IP destination in the primary path and a telephone number in the backup path, a break in the Network Link Integrity does not annunciate locally.D72126.0 Previous Version 6.70 ReleaseNotesEnhancement in Version 6.70Arming Scope RestrictionsWhen the Silent Alarm Relay for Area 3 isprogrammed with 59, some prompts in the FunctionTable 3: Arming Scope RestrictionsMenu Function Function NumberDisabled Prompt Disarm Menu 1 DISARM ALL?Master Arm Delay 2 MASTER ARM ALL? Master Arm Instant3ARM INSTANT ALL?7.0Previous Version 6.60 Release Notes7.1Corrections in Version 6.60The changes made to the version 6.60 firmware affect only control panels with the ground fault detection circuit: the G-model control panels. Because the D7212 Control Panel does not have the ground fault detection circuit, this firmware upgrade does not change the control panel’s function.7.2Known Issues in Version 6.60•When a faulted local point is force armed, the central station should receive a Forced Close report for that point. The control panel does not send Forced Close reports for faulted local points. •If a local and a non-local point are faulted and force armed, the control panel does not send Forced Armed, Forced Point, or Forced Close Reports for the non-local point. A point is a local point if configured as follows: • Local While Armed : Yes •Local While Disarmed : Yes8.0 Previous Version 6.50 ReleaseNotesCorrections in Version 6.50Intermittent RF Low Battery eventsIn versions 6.30 and 6.40, Points 1 through 8 generate intermittent RF Low Battery events when devices connected to the on-board points change very quickly from normal to off-normal conditions. Firmware version 6.50 corrects this issue.When an RF Low Battery condition occurs on atransmitter, RF Low Battery appears on the D1255 or D1260 Keypad’s display. To determine whichtransmitter has the low battery condition, select one of the following: •View Log? function from the Service Menu (99 + ENT) on the keyboard, or•Diagnostics function, using the D8125INV. Refer to the D8125INV Operation and Installation Guide (P/N: 49690) for details.If the event is transmitted to the central station, the point number is included in the transmission.D72129.0 Previous Version 6.40 ReleaseNotes9.1Enhancements in Version 6.40Enabling the D1260 in a D7212 Control Panel 1. To enable D1260 Keypads, set the commandcenter menu item to Yes for the command center addresses where the D1260s reside.• In the Command Center Assignments section, the prompt is CC#EnhanceCmdCtr . •In the COMMAND CENTER (9000MAIN) section in RPS, the prompt is EnhancedCommand Center .Figure 1: Enhanced Command Center Prompt inRPS2. When power is applied, each D1260 checks thefirmware revision number that resides in the control panel. For each D1260 to work, theDisplay Revision (Command 59) must be enabled and not passcode protected. Refer to Figure 2 on page 4.•In the D5200, this function is located at: 9000MAIN USER INTERFACE Cmd Center FunctionsDisplay Rev •In RPS (Figure 2), this function is located at: USER INTERFACE Command Center FunctionsFigure 2: Enable Display Revision Prompt in RPS3. Before exiting RPS, reset the control panel aftercompleting an RPS programming session:A.Click the Reset Panel checkbox B. Click OK .Refer to Figure 3.Figure 3: End Session Dialog BoxFigure 4: Keypad DisplayD72129.2Corrections in Version 6.40Duplicate Events Do Not Report under Comm Fail ConditionsVersion 6.40 corrects the following problem:When a Comm Fail condition occurs in Route Group 1, Route Group 2, or both, D7212 does not send duplicate events to Route Groups 3 and 4 whenduplicate events are programmed for Route Groups 2, 3, 4, or all groups.Support for D1260 Not in Version 6.30 as Stated in LiteratureThe D9412G/D7412G Program Entry Guide(P/N: 47775D) and the D7212 Release Notes for v6.30 (P/N: 34699N) state incorrectly that Alpha V Command Center (keypad) support is available in version 6.30.Only version 6.40 or higher can support the D1260 Alpha V Command Center (keypad) Watchdog Reset EventsVersion 6.40 corrects Watchdog Reset eventsgenerated when a SKED is used to arm a disabled area or a Closing Window and Auto Close prompt is set to Yes (in Area Wide Open/Close ). BFSK FormatBefore version 6.40, the control panel did not send Burglary Restoral reports when using the BFSK communication format. Version 6.40 corrects this issue.Fail to Execute EventsBefore version 6.40, Fail To Execute events incorrectly identified the serial device interface (SDI) device associated with the event. Version 6.40 corrects this issue.Programming Point Indexes for Points 240 – 247 In version 6.30 for the D7412G and D7212 Control Panels, if you use a D5200 to assign point Points 240 through 247, the control panel ignores these points and mistakenly shows missing conditions. Version 6.40 corrects this issue.9.3Known Issues in Version 6.40Disconnecting Battery during Walk Test Causes D1260 to Stop RespondingWhen the control panel’s battery is disconnected and then reconnected during a Walk Test, the D1260 stops responding and displays Retrieving panel info . The control panel must be restarted to clear the keypad.Areas Armed to “All on instant” Do Not Show Area Text in D1260 View Area StatusWhen arming areas to All on Instant, area text does not appear when using the View Area Status menu function on the D1260. BFSK FormatSupervisory and Fire Supervisory events cannot be29.4 Programming TipsNetCom CommunicationsIn applications where both the primary and backup paths are programmed to send an IP address, the Path # Poll Rate value for the backup IP address should be set to 0. In the D9412G/D7412G Program Entry Guide (P/N: 47775), refer to: •Routing and Enhanced Routing for information about primary and backup paths.•Enhanced Communications in the RADXAUX1Handler section for information about Path # Poll Rate .D7212NotesD7212 NotesD7212© 2007 Bosch Security Systems, Inc.130 Perinton Parkway, Fairport, NY 14450-9199 USACustomer Service: (800) 289-0096; Technical Support: (888) 886-6189 F01U034872-02Release Notes for Version 7.003/07D7212Page 8 of 8。
操作系统第九版部分课后作业习题答案分析解析

CHAPTER 9 Virtual Memory Practice Exercises9.1 Under what circumstances do page faults occur? Describe the actions taken by the operating system when a page fault occurs.Answer:A page fault occurs when an access to a page that has not beenbrought into main memory takes place. The operating system veri?esthe memory access, aborting the program if it is invalid. If it is valid, a free frame is located and I/O is requested to read the needed page into the free frame. Upon completion of I/O, the process table and page table are updated and the instruction is restarted.9.2 Assume that you have a page-reference string for a process with m frames (initially all empty). The page-reference string has length p;n distinct page numbers occur in it. Answer these questions for anypage-replacement algorithms:a. What is a lower bound on the number of page faults?b. What is an upper bound on the number of page faults?Answer:a. nb. p9.3 Consider the page table shown in Figure 9.30 for a system with 12-bit virtual and physical addresses and with 256-byte pages. The list of freepage frames is D, E, F (that is, D is at the head of the list, E is second,and F is last).Convert the following virtual addresses to their equivalent physicaladdresses in hexadecimal. All numbers are given in hexadecimal. (Adash for a page frame indicates that the page is not in memory.)? 9EF? 1112930 Chapter 9 Virtual Memory? 700? 0FFAnswer:? 9E F - 0E F? 111 - 211? 700 - D00? 0F F - EFF9.4 Consider the following page-replacement algorithms. Rank thesealgorithms on a ?ve-point scale from “bad” to “perfect” according to the page-fault rate. Separate those algorithms that suffer from Belady’sanomaly from those that do not.a. LRU replacementb. FIFO replacementc. Optimal replacementd. Second-chance replacementAnswer:Rank Algorithm Suffer from Belady’s anomaly1 Optimal no2 LRU no3 Second-chance yes4 FIFO yes9.5 Discuss the hardware support required to support demand paging. Answer:For every memory-access operation, the page table needs to be consulted to check whether the corresponding page is resident or not and whetherthe program has read or write privileges for accessing the page. These checks have to be performed in hardware. A TLB could serve as a cache and improve the performance of the lookup operation.9.6 An operating system supports a paged virtual memory, using a central processor with a cycle time of 1 microsecond. It costs an additional 1 microsecond to access a page other than the current one. Pages have 1000 words, and the paging device is a drum that rotates at 3000 revolutionsper minute and transfers 1 million words per second. The following statistical measurements were obtained from the system:page other than the? 1 percent of all instructions executed accessed acurrent page.?Of the instructions that accessed another page, 80 percent accesseda page already in memory.Practice Exercises 31?When a new page was required, the replaced page was modi?ed 50 percent of the time.Calculate the effective instruction time on this system, assuming that the system is running one process only and that the processor is idle during drum transfers.Answer:(2 sec)(1sec + 0.008 ×effective access time = 0.99 ×(10,000 sec + 1,000 sec)+ 0.002 ×(10,000 sec + 1,000 sec)+ 0.001 ×9.7 Consider the two-dimensional array A:int A[][] = new int[100][100];where A[0][0] is at location 200 in a paged memory system with pages of size 200. A small process that manipulates the matrix resides in page 0 (locations 0 to 199). Thus, every instruction fetch will be from page 0. For three page frames, how many page faults are generated bythe following array-initialization loops, using LRU replacement andassuming that page frame 1 contains the process and the other two are initially empty?a. for (int j = 0; j < 100; j++)for (int i = 0; i < 100; i++)A[i][j] = 0;b. for (int i = 0; i < 100; i++)for (int j = 0; j < 100; j++)A[i][j] = 0;Answer:a. 5,000b. 509.8 Consider the following page reference string:1, 2, 3, 4, 2, 1, 5, 6, 2, 1, 2, 3, 7, 6, 3, 2, 1, 2, 3, 6.How many page faults would occur for the following replacement algorithms, assuming one, two, three, four, ?ve, six, or seven frames? Remember all frames are initially empty, so your ?rst unique pages will all cost one fault each.?LRU replacement? FIFO replacement?Optimal replacement32 Chapter 9 Virtual MemoryAnswer:Number of frames LRU FIFO Optimal1 20 20 202 18 18 153 15 16 114 10 14 85 8 10 76 7 10 77 77 79.9 Suppose that you want to use a paging algorithm that requires a referencebit (such as second-chance replacement or working-set model), butthe hardware does not provide one. Sketch how you could simulate a reference bit even if one were not provided by the hardware, or explain why it is not possible to do so. If it is possible, calculate what the cost would be.Answer:You can use the valid/invalid bit supported in hardware to simulate the reference bit. Initially set the bit to invalid. On ?rst reference a trap to the operating system is generated. The operating system will set a software bit to 1 and reset the valid/invalid bit to valid.9.10 You have devised a new page-replacement algorithm that you thinkmaybe optimal. In some contorte d test cases, Belady’s anomaly occurs. Is thenew algorithm optimal? Explain your answer.Answer:No. An optimal algorithm will not suffer from Belady’s anomaly beca an optimal algorithm replaces the page that will not—by de?nition—be used for the longest time. Belady’s anomaly occurs when a pagereplacement a lgorithm evicts a page that will be needed in theimmediatefuture. An optimal algorithm would not have selected such a page.9.11 Segmentation is similar to paging but usesnevariable-sized“pages.”De?two segment-replacement algorithms based on FIFO and LRU pagereplacement s chemes. Remember that since segments are not thesamesize, the segment that is chosen to be replaced may not be big enoughto leave enough consecutive locations for the needed segment. Considerstrategies for systems where segments cannot be relocated, and thosefor systems where they can.Answer:a. FIFO. Find the ?rst segment large enough to accommodate theincoming segment. If relocation is not possible and no one segmentis large enough, select a combination of segments whose memoriesare contiguous, which are “closest to the ?rst of the list” and which can accommodate the new segment. If relocation is possible,rearrange the memory so that the ?rstNsegments large enough forthe incoming segment are contiguous in memory. Add any leftoverspace to the free-space list in both cases.Practice Exercises 33b. LRU. Select the segment that has not been used for the longestperiod of time and that is large enough, adding any leftover spaceto the free space list. If no one segment is large enough, selecta combination of the “oldest” segments that are contiguous inmemory (if relocation is not available) and that are large enough.If relocation is available, rearrange the oldest N segments to becontiguous in memory and replace those with the new segment.9.12 Consider a demand-paged computer system where the degree of multiprogramming is currently ?xed at four. The system was recentlymeasured to determine utilization of CPU and the paging disk. The resultsare one of the following alternatives. For each case, what is happening?Can the degree of multiprogramming be increased to increase the CPU utilization? Is the paging helping?a. CPU utilization 13 percent; disk utilization 97 percentb. CPU utilization 87 percent; disk utilization 3 percentc. CPU utilization 13 percent; disk utilization 3 percentAnswer:a. Thrashing is occurring.b. CPU utilization is suf?ciently high to leave things alone, andincrease degree of multiprogramming.c. Increase the degree of multiprogramming.9.13 We have an operating system for a machine that uses base and limit registers, but we have modi?ed the ma chine to provide a page table.Can the page tables be set up to simulate base and limit registers? How can they be, or why can they not be?Answer:The page table can be set up to simulate base and limit registers provided that the memory is allocated in ?xed-size segments. In this way, the base of a segment can be entered into the page table and the valid/invalid bit used to indicate that portion of the segment as resident in the memory. There will be some problem with internal fragmentation.9.27.Consider a demand-paging system with the following time-measured utilizations:CPU utilization 20%Paging disk 97.7%Other I/O devices 5%Which (if any) of the following will (probably) improve CPU utilization? Explain your answer.a. Install a faster CPU.b. Install a bigger paging disk.c. Increase the degree of multiprogramming.d. Decrease the degree of multiprogramming.e. Install more main memory.f. Install a faster hard disk or multiple controllers with multiple hard disks.g. Add prepaging to the page fetch algorithms.h. Increase the page size.Answer: The system obviously is spending most of its time paging, indicating over-allocationof memory. If the level of multiprogramming is reduced resident processeswould page fault less frequently and the CPU utilization would improve. Another way toimprove performance would be to get more physical memory or a faster paging drum.a. Get a faster CPU—No.b. Get a bigger paging drum—No.c. Increase the degree of multiprogramming—No.d. Decrease the degree of multiprogramming—Yes.e. Install more main memory—Likely to improve CPU utilization as more pages canremain resident and not require paging to or from the disks.f. Install a faster hard disk, or multiple controllers with multiple hard disks—Also animprovement, for as the disk bottleneck is removed by faster response and morethroughput to the disks, the CPU will get more data more quickly.g. Add prepaging to the page fetch algorithms—Again, the CPU will get more datafaster, so it will be more in use. This is only the case if the paging actionis amenableto prefetching (i.e., some of the access is sequential).h. Increase the page size—Increasing the page size will result in fewer page faults ifdata is being accessed sequentially. If data access is more or less random, morepaging action could ensue because f ewer pages c an be kept in memory and moredata is transferred per page fault. So this change is as likely to decrease utilizationas it is to increase it.10.1、Is disk scheduling, other than FCFS scheduling, useful in a single-userenvironment? Explain your answer.Answer: In a single-user environment, the I/O queue usually is empty. Requests g enerally arrive from a single process for one block or for a sequence of consecutive blocks. In these cases, FCFS is an economical method of disk scheduling. But LOOK is nearly as easy to program and will give much better performance when multiple processes are performing concurrent I/O, such as when aWeb browser retrieves data in the background while the operating system is paging and another application is active in the foreground.10.2.Explain why SSTF scheduling tends to favor middle cylindersover theinnermost and outermost cylinders.The center of the disk is the location having the smallest average distance to all other tracks.Thus the disk head tends to move away from the edges of the disk.Here is another way to think of it.The current location of the head divides the cylinders into two groups.If the head is not in the center of the disk and a new request arrives,the new request is more likely to be in the group that includes the center of the disk;thus,the head is more likely to move in that direction.10.11、Suppose that a disk drive has 5000 cylinders, numbered 0 to 4999. The drive is currently serving a request at cylinder 143, and the previous request was at cylinder 125. The queue of pending requests, in FIFO order, is86, 1470, 913, 1774, 948, 1509, 1022, 1750, 130Starting from the current head position, what is the total distance (in cylinders) that the disk arm moves to satisfy all the pending requests, for each of the following disk-scheduling algorithms?a. FCFSb. SSTFc. SCANd. LOOKe. C-SCANAnswer:a. The FCFS schedule is 143, 86, 1470, 913, 1774, 948, 1509, 1022, 1750, 130. The total seek distance is 7081.b. The SSTF schedule is 143, 130, 86, 913, 948, 1022, 1470, 1509, 1750, 1774. The total seek distance is 1745.c. The SCAN schedule is 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 4999, 130, 86. The total seek distance is 9769.d. The LOOK schedule is 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 130, 86. The total seek distance is 3319.e. The C-SCAN schedule is 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 4999, 86, 130. The total seek distance is 9813.f. (Bonus.) The C-LOOK schedule is 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 86, 130. The total seek distance is 3363.12CHAPTERFile-SystemImplementationPractice Exercises12.1 Consider a ?le currently consisting of 100 blocks. Assume that the?lecontrol block (and the index block, in the case of indexed allocation)is already in memory. Calculate how many disk I/O operations are required for contiguous, linked, and indexed (single-level) allocation strategies, if, for one block, the following conditions hold. In the contiguous-allocation case, assume that there is no room to grow atthe beginning but there is room to grow at the end. Also assume thatthe block information to be added is stored in memory.a. The block is added at the beginning.b. The block is added in the middle.c. The block is added at the end.d. The block is removed from the beginning.e. The block is removed from the middle.f. The block is removed from the end.Answer:The results are:Contiguous Linked Indexeda. 201 1 1b. 101 52 1c. 1 3 1d. 198 1 0e. 98 52 0f. 0 100 012.2 What problems could occur if a system allowed a ?le system to be mounted simultaneously at more than one location?Answer:4344 Chapter 12 File-System ImplementationThere would be multiple paths to the same ?le, which could confuse users or encourage mistakes (deleting a ?le with one path deletes the?le in all the other paths).12.3 Why must the bit map for ?le allocation be kept on mass storage, ratherthan in main memory?Answer:In case of system crash (memory failure) the free-space list would not be lost as it would be if the bit map had been stored in main memory.12.4 Consider a system that supports the strategies of contiguous, linked, and indexed allocation. What criteria should be used in deciding which strategy is best utilized for a particular ?le?Answer:?Contiguous—if ?le is usually accessed sequentially, if ?le isrelatively small.?Linked—if ?le is large and usually accessed sequentially.? Indexed—if ?le is large and usually accessed randomly.12.5 One problem with contiguous allocation is that the user must preallocate enough space for each ?le. If the ?le grows to be larger than thespace allocated for it, special actions must be taken. One solution to this problem is to de?ne a ?le structure consisting of an initial contiguousarea (of a speci?ed size). If this area is ?lled, the operating system automatically de?nes an over?ow area that is linked to the initial contiguous area. If the over?ow area is ?lled, another over?ow areais allocated. Compare this implementation of a ?le with the standard contiguous and linked implementations.Answer:This method requires more overhead then the standard contiguousallocation. It requires less overheadthan the standard linked allocation.12.6 How do caches help improve performance? Why do systems not use more or larger caches if they are so useful?Answer:Caches allow components of differing speeds to communicate moreef?ciently by storing data from the slower device, temporarily, ina faster device (the cache). Caches are, almost by de?nition, moreexpensive than the device they are caching for, so increasing the numberor size of caches would increase system cost.12.7 Why is it advantageous for the user for an operating system to dynamically allocate its internal tables? What are the penalties to the operating system for doing so?Answer:tablesDynamic tables allow more ?exibility in system use growth —are never exceeded, avoiding arti?cial use limits. Unfortunately, kernel structures and code are more complicated, so there is more potentialfor bugs. The use of one resource can take away more system resources (by growing to accommodate the requests) than with static tables.Practice Exercises 4512.8 Explain how the VFS layer allows an operating system to support multiple types of ?le systems easily.Answer:VFS introduces a layer of indirection in the ?le system implementation. In many ways, it is similar to object-oriented programming techniques. System calls can be made generically (independent of ?le system type). Each ?le system type provides its function calls and data structuresto the VFS layer. A system call is translated into the proper speci?c functions for the target ?le system at the VFS layer. The calling program has no ?le-system-speci?c code, and the upper levels of the system call structures likewise are ?le system-independent. The translation at the VFS layer turns these generic calls into ?le-system-speci?c operations.。
PTN简答题库

在删除了 startrun.dat 和 startrun.old 之后 cfg 文件夹里没有相关文件,此时使用reload 命令重启设备,当设备重启后是否会自动生成 startrun.dat?不会。
接上题,怎样才能使 startrun.dat 再次生成?在特权模式即#模式下进行 write 保存后会产生 startrun.dat 文件。
目前在初始化 6100 和 6300 时,串口线和网线分别连接什么接口?为什么?6100:串口线—OUT 告警输出及设备调试接口(做为设备调试接口时仅供工程人员在设备开局时使用) 网线— Qx 网管接口6300:串口线— CON 网线—业务电口单板运行指示灯即 RUN 灯在正常工作状态时闪烁频率是多少?0.5 次/秒闪烁即指示灯 1 秒亮, 1 秒灭。
接上题,如果 1 次/秒闪烁、5 次/秒闪烁呢?1 次/秒闪烁表示指示灯 0.5 秒亮, 0.5 秒灭; 5 次/秒闪烁表示 0.1 秒亮, 0.1 秒灭。
Q:为什么在设备初始化之前要删除设备已有的 startrun.dat 和 startrun.old?A: startrun.dat 是每次开机加载的配置文件,设备每次重启时首先会查找 startrun.dat。
设备加载脚本时只根据文件名是 startrun 即开始加载,如果没有 startrun.dat 则查找 startrun.old ,如果二者都没有重启设备之后方可配置脚本。
脚本运行完之后执行的 write 命令只是刚配置的脚本保存至 flash 中并生成 startrun.dat 文件,所以还要重启设备才能使设备工作在新配置的脚本下。
使用 show ip route 命令的作用是什么?路由表 OWNER 类型中的 direct、static、address 分别表示什么路由类型?结果中能否查看到动态路由?该命令可以显示路由器的全局路由表,查看路由表中是否有配置的静态路由。
(完整word版)《Linux网络操作系统项目教程(RHEL7.4 CentOS 7.4)(第3版))》习题及答案

《Linux网络操作系统项目教程(RHEL7.4/CentOS 7.4)(第3版)》课后习题答案1.11 练习题一、填空题1.GNU的含义是。
2.Linux一般有3个主要部分:、、。
3.目前被称为纯种的UNIX指的就是以及这两套操作系统。
4.Linux是基于的软件模式进行发布的,它是GNU项目制定的通用公共许可证,英文是。
5.史托曼成立了自由软件基金会,它的英文是。
6.POSIX是的缩写,重点在规范核心与应用程序之间的接口,这是由美国电气与电子工程师学会(IEEE)所发布的一项标准。
7.当前的Linux常见的应用可分为与两个方面。
8.Linux的版本分为和两种。
9.安装Linux最少需要两个分区,分别是。
10.Linux默认的系统管理员账号是。
1. GNU's Not Unix的递归缩写(GNU计划一个自由软件组织)2. 内核(kernel)、命令解释层(Shell或其他操作环境)、实用工具3. System V BSD4. Copyleft(无版权)General Public License,GPL)5. FSF,Free Software Foundation6. 便携式操作系统接口(Portable Operating System Interface)7. 企业应用个人应用8. 内核版本发行版本9. swap交换分区/(根)分区10. root二、选择题1.Linux最早是由计算机爱好者()开发的。
A.Richard Petersen B.Linus TorvaldsC.Rob Pick D.Linux Sarwar2.下列中()是自由软件。
A.Windows XP B.UNIX C.Linux D.Windows 2008 3.下列中()不是Linux的特点。
A.多任务B.单用户C.设备独立性D.开放性4.Linux的内核版本2.3.20是()的版本。
A.不稳定B.稳定的C.第三次修订D.第二次修订5.Linux安装过程中的硬盘分区工具是()。
《Linux操作系统及应用(第四版)》课后习题答案

国家十二五规划教材《Linux操作系统及应用(第四版)》课后习题答案Windows & Linux老师交流群:189934741 作者QQ:68433059 项目1 安装Red Hat Enterprise Linux1.6 练习题一、填空题1. GNU's Not Unix的递归缩写2. 内核(kernel)、命令解释层(Shell或其他操作环境)、实用工具3. System V BSD4. Copyleft(无版权)General Public License,GPL)5. FSF,Free Software Foundation6. 便携式操作系统接口(Portable Operating System Interface)7. 企业应用个人应用8. 内核版本发行版本9. swap交换分区/(根)分区10. root11. X Server、X Client和通信通道二、选择题1.B2.C3.B4.A5. D6. C项目2 管理文件系统2.5 练习题一、填空题1. 区分Tab2. 分号3. 反斜杠“\”“>”4. “&”5. 保存管理6. 扩展文件系统ext2/ext3/ext47. 级块索引节点表数据块8. 树状目录“/”9. umask umask 777 00010. . ..11. 隐藏文件12. chmod a+x filename二、选择题1. C2. C3. C4. C5. A6. A7. A8. B9. D10. D项目3 shell与vim编辑器3.5 练习题一、填空题1. shell2. /etc/shells3. /etc/passwd4. 命令编辑功能;命令与文件补全功能;命令别名设置功能;作业控制、前台与后台控制;程序化脚本;通配符等。
5. 全局变量局部变量6. set7. *、?、[]8. 行9. 查找、删除、替换10. 通配符(wild card)正则表示法项目4 shell编程-shell script4.5 练习题一、填空题1. shell shell 的语法与命令(含外部命令)正则表达式管道命令数据流重导向2. 上下左右3. r r 与x4. shell (#!/bin/bash) 程序用途版本作者5. read date6. 父程序7. test 中括号( [] )8. if...then case $var in ... esac9. 不定循环(while, until) 固定循环(for)10. sh -x script.sh三、实践习题1.请创建一个script ,当你运行该script 的时候,该script 可以显示:①你目前的身份(用whoami );②你目前所在的目录(用pwd)。
2024年电信5G基站建设理论考试题库(附答案)

2024年电信5G基站建设理论考试题库(附答案)一、单选题1.在赛事保障值守过程中,出现网络突发故障,需要启用红黄蓝应急预案进行应急保障,确保快速处理和恢复。
红黄蓝应急预案的应急逻辑顺序为()A、网络安全->用户感知->网络性能B、网络性能->用户感知->网络安全C、用户感知->网络安全->网络性能D、用户感知->网络性能->网络安全参考答案:D2.2.1G规划,通过制定三步走共享实施方案,降配置,省TCO不包含哪项工作?A、低业务小区并网B、低业务小区关小区C、低业务小区拆小区D、高业务小区覆盖增强参考答案:D3.Type2-PDCCHmonsearchspaceset是用于()。
A、A)OthersysteminformationB、B)PagingC、C)RARD、D)RMSI参考答案:B4.SRIOV与OVS谁的转发性能高A、OVSB、SRIOVC、一样D、分场景,不一定参考答案:B5.用NR覆盖高层楼宇时,NR广播波束场景化建议配置成以下哪项?A、SCENARTO_1B、SCENARIO_0C、SCENARIO_13D、SCENARIO_6参考答案:C6.NR的频域资源分配使用哪种方式?A、仅在低层配置(非RRC)B、使用k0、k1和k2参数以实现分配灵活性C、使用SLIV控制符号级别的分配D、使用与LTE非常相似的RIV或bitmap分配参考答案:D7.SDN控制器可以使用下列哪种协议来发现SDN交换机之间的链路?A、HTTPB、BGPC、OSPFD、LLDP参考答案:D8.NR协议规定,采用Min-slot调度时,支持符号长度不包括哪种A、2B、4C、7D、9参考答案:D9.5G控制信道采用预定义的权值会生成以下那种波束?A、动态波束B、静态波束C、半静态波束D、宽波束参考答案:B10.TS38.211ONNR是下面哪个协议()A、PhysicalchannelsandmodulationB、NRandNG-RANOverallDescriptionC、RadioResourceControl(RRC)ProtocolD、BaseStation(BS)radiotransmissionandreception参考答案:A11.在NFV架构中,哪个组件完成网络服务(NS)的生命周期管理?A、NFV-OB、VNF-MC、VIMD、PIM参考答案:A12.5G需要满足1000倍的传输容量,则需要在多个维度进行提升,不包括下面哪个()A、更高的频谱效率B、更多的站点C、更多的频谱资源D、更低的传输时延参考答案:D13.GW-C和GW-U之间采用Sx接口,采用下列哪种协议A、GTP-CB、HTTPC、DiameterD、PFCP参考答案:D14.NR的频域资源分配使用哪种方式?A、仅在低层配置(非RRC)B、使用k0、k1和k2参数以实现分配灵活性C、使用SLIV控制符号级别的分配D、使用与LTE非常相似的RIV或bitmap分配参考答案:D15.下列哪个开源项目旨在将电信中心机房改造为下一代数据中心?A、OPNFVB、ONFC、CORDD、OpenDaylight参考答案:C16.NR中LongTruncated/LongBSR的MACCE包含几个bit()A、4B、8C、2D、6参考答案:B17.对于SCS120kHz,一个子帧内包含几个SlotA、1B、2C、4D、8参考答案:D18.SA组网中,UE做小区搜索的第一步是以下哪项?A、获取小区其他信息B、获取小区信号质量C、帧同步,获取PCI组编号D、半帧同步,获取PCI组内ID参考答案:D19.SA组网时,5G终端接入时需要选择融合网关,融合网关在DNS域名的'app-protocol'name添加什么后缀?A、+nc-nrB、+nr-ncC、+nr-nrD、+nc-nc参考答案:A20.NSAOption3x组网时,语音业务适合承载以下哪个承载上A、MCGBearB、SCGBearC、MCGSplitBearD、SCGSplitBear参考答案:A21.5G需要满足1000倍的传输容量,则需要在多个维度进行提升,不包括下面哪个()A、更高的频谱效率B、更多的站点C、更多的频谱资源D、更低的传输时延参考答案:D22.以SCS30KHz,子帧配比7:3为例,1s内调度次数多少次,其中下行多少次。
计算机专业英语试题及答案

计算机专业英语试题及答案1. 选择题1. Which of the following is not a programming language?a) Javab) HTMLc) Pythond) CSS答案: b) HTML2. Which protocol is used for sending and receiving email?a) HTTPSb) FTPc) SMTPd) DNS答案: c) SMTP3. What does the acronym CPU stand for?a) Central Processing Unitb) Computer Processing Unitc) Control Processing Unitd) Central Power Unit答案: a) Central Processing Unit4. Which programming language is commonly used for web development?a) C++b) Javac) JavaScriptd) Swift答案: c) JavaScript5. What does HTML stand for?a) Hyperlinks and Text Markup Languageb) Hyper Text Markup Languagec) Home Tool Markup Languaged) Hyper Text Modeling Language答案: b) Hyper Text Markup Language2. 填空题1. The process of converting high-level programming code into machine code is called ___________.答案: compilation2. HTTP stands for ___________ Transfer Protocol.答案: Hyper Text3. The process of testing software by executing it is called ___________.答案: debugging4. Java is an object-_____________ programming language.答案: oriented5. DNS stands for Domain Name ___________.答案: System3. 简答题1. What is the difference between TCP and UDP?答案: TCP (Transmission Control Protocol) is a connection-oriented protocol, which means it establishes a connection between the sender and receiver before transferring data. It ensures that all packets are received in the correct order and provides error checking. UDP (User Datagram Protocol), on the other hand, is a connectionless protocol that does not establish a direct connection before transmitting data. It does not guarantee packet delivery or order but is faster and more efficient for time-sensitive applications.2. What is the purpose of an operating system?答案: An operating system (OS) is a software that manages computer hardware and software resources and provides common services forcomputer programs. Its primary purpose is to enable the user to interact with the computer and provide a platform for running applications. It manages memory, file systems, input/output devices, and multitasking. The OS also handles system security and resource allocation to ensure optimal performance.4. 解答题请参考下文并给出自己的解答。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
355
LEVEL 4 High-level front ends for generating models (Section 16.2.4)
LEVEL 3 User interface with convenience features (Section 16.2.3)
Chapter 16 Using Queueing Network Modelling Software
16.1. Introduction
A variety of techniques for evaluating queueing network models have been described. The general techniques of bounding analysis, single and multiple class analysis, and hierarchical modelling were presented in Part II. Specific techniques for memory, disk I/O, and processor subsystems were discussed in Part III. This collection of techniques comes together for the computer system performance analyst in the form of queueing network modelling software. Such software frees the analyst from the algorithmic portion of the modelling process, allowing concentration on important issues such as model construction and validation, performance projection, and capacity planning. Most queueing network modelling software can be understood in terms of the structure illustrated in Figure 16.1. There is a sequence of software layers, each transforming input received from the layer above into output suitable for the layer below. In Section 16.2 we will refer to this structure in describing the major components of queueing network modelling software. In Section 16.3 we give an example of conducting a performance study using such software.
of 16.2. Components QueueingNetwork IviodellingSoftware
357
are made visible to the analyst with little intervention by the user interface layer. In other cases, the correspondence is not so direct. In particular, the user interface layer smoothes the analyst’s interaction with the transformation layer. As an example, when multipathing I/O is modelled, as described in Section 10.5, the user interface layer allows the analyst to describe the system in terms of channels, controllers, heads of string, disks, and logical channels (in the case of an IBM configuration) and translates this information into a form acceptable to the transformation layer. The transformation layer then uses this information to estimate effective service demands for the various disks, interacting iteratively with the core routine, which evaluates a sequence of separable models provided by the transformation layer. Finally, the transformation and user interface layers provide performance measures in a meaningful form. A related facility allows the analyst to associate a “type” with a dev-! ice, and to specify the relevant characteristics of this type to the software. This is useful during modification analysis. As a simple example, an existing system may have an IBM 3081-D CPU, and one of the contemplated modifications may be an upgrade to a 3081-K. If the relative speeds of these two processors are known to the software (in fact, they are roughly 4.0 and 5.51, then the following sequence of interactions would be possible: - analyst provides all inputs for baseline model - analyst identifies CPU as 3081-D - baseline model is validated - analyst specifies that CPU type should be changed to 3081-K - software adjusts CPU service demands based on internal information A similar approach can be applied to other devices. The user interface layer typically provides the ability to save, recall, and edit model definitions during an interactive session, since model modification is the major activity in interacting with queueing network modelling software. Output reports also need to be stored for postprocessing. A final example of a facility provided by the user interface layer is a means for the analyst to “program” the package using a simple language, similar to the “exec file” or “command file” facility provided by most contemporary timesharing systems. A simple application of this facility would be to perform automatically a parametric study (for example, on the effect of increasing the number of active terminals). Of course, an analyst could conduct such a study by interacting with the software directly, issuing separate commands to evaluate the model with each population of interest. A better approach, though, would be to write a
TransforFnations from non-separable QNMs to separable QNMs (Section 16.2.2)
Core algorithms for separable QNMs (Section 16.2.1)
Figure 16.1 - The Structure of Queueing Network Modelling Software
