H3C_S7500E_AAA典型配置举例
H3C华三交换机基本配置命令大全,弱电人用的到!

H3C华三交换机基本配置命令大全,弱电人用的到!本期我们一起来了解下H3C最详细的基础命令。
一、不知道密码,如何恢复出厂设置1、开机启动,Ctrl+B进入bootrom菜单,选择恢复出厂设置。
2、用com线连上电脑,用超级终端进入,然后重启电脑,看提示按ctrl+b进入bootrom模式,然后按照菜单提示删除flash中的.cfg文件,然后重启就可以了。
二、将Trunk端口添加到vlan中Trunk端口可以允许多个VLAN通过,也就是可以加入多个VLAN,所以Trunk 端口的VLAN加入不可能是一个一个地加,而是采取批量添加的方式进行。
但只能在以太网端口视图下进行配置,配置步骤如表7-11所示。
【示例1】使用port trunk permit vlan命令将中继端口Ethernet2/0/1加入到2、6、10、50~100 VLAN中。
1. <H3C> system-view2. System View: return to User View with Ctrl+Z.3. [H3C] interface Ethernet2/0/14. [H3C-Ethernet2/0/1] port trunk permit vlan 2 6 10 50 to 1005. Please wait...6. Done.表7-11 把Trunk端口添加到VLAN中的步骤s命令把该链路转换成Access链路,然后再使用本步命令转换成Trunk链路4port trunk permit vlan { vlan-id-list | all }例如:[sysname-GigabitEthernet1/0/1] port trunkpermit vlan 2 to 10将以上Trunk端口加入到一个或多个VLAN,以实现允许来自指定VLAN的数据包通过(也就是Cisco IOS中所说的VLAN修剪)二选一参数vlan-id-list = [ vlan-id1 [ to vlan-id2 ] ]&<1-10>用于指定Trunk端口允许加入的VLAN的范围,vlan-id取值范围为1~4094。
H3C配置案例大全(内部分享)
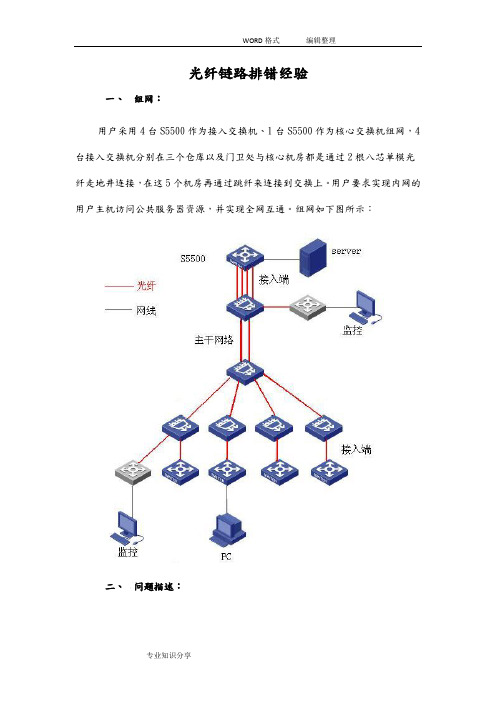
光纤链路排错经验一、组网:用户采用4台S5500作为接入交换机、1台S5500作为核心交换机组网,4台接入交换机分别在三个仓库以及门卫处与核心机房都是通过2根八芯单模光纤走地井连接,在这5个机房再通过跳纤来连接到交换上。
用户要求实现内网的用户主机访问公共服务器资源,并实现全网互通。
组网如下图所示:二、问题描述:PC现无法访问server服务器,进一步发现S5500光纤端口灯不亮,端口信息显示down状态。
在核心交换机端通过自环测试发现该端口以及光模块正常,接入交换机端也同样测试发现正常。
监控网络正常使用,再将网络接口转接到监控主干链路上,发现网络同样无法正常使用。
三、过程分析:想要恢复链路,首先要排查出故障点,根据故障点情况结合实际恢复链路通畅。
在这里主要分析光纤通路,光信号从接入交换机光口出来通过跳线,转接到主干光纤,然后再通过核心跳线转接到核心交换上。
由于该链路不通,首先要排除两端接口以及光模块问题,这里使用自环检测(如果是超远距离传输光纤线缆需要接光衰然后在自环,防止烧坏光模块)。
当检测完成发现无问题,再测试接入端的光纤跳纤:如果是多模光纤可以将一端接到多模光纤模块的tx口,检测对端是否有光;单模光纤如果没有光功率计可以使用光电笔检测(该方法只能检测出中间无断路,并不能检测出线路光衰较大的情况)。
最后再检测主线路部分,检测方式同跳线一样。
光路走向流程如图所示:四、解决方法:从上述的分析可以看出,只要保证了光信号一出一收两条路径都能正常就可以解决用户无法访问服务器的问题。
为了保证光路正常通路,最好的解决方法就是,通过使用光功率计来检测对端发射光在本端的光功率是否在光口可接受范围内。
由于用户组网使用了一些监控设备来接入该主干光缆,并且该光路现正常使用,通过将网络光纤转接到该监控主干光缆,发现网络光路仍然不通;并且两端端口自环检测正常。
由此可以判断出主要问题在两端的跳纤上。
如图所示:在没有光功率计并且客户业务又比较着急恢复的情况,可以先将两端的接入跳纤更换。
H3C_S7500E_SNMP典型配置举例

H3C S7500E SNMP典型配置举例Copyright © 2015 杭州华三通信技术有限公司版权所有,保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本文档内容的部分或全部,并不得以任何形式传播。
本文档中的信息可能变动,恕不另行通知。
目录1 简介 (1)2 配置前提 (1)3 SNMPv1/SNMPv2c配置举例 (1)3.1 组网需求 (1)3.2 使用版本 (1)3.3 配置注意事项 (1)3.4 配置步骤 (2)3.4.1 设备的配置 (2)3.4.2 NMS的配置 (2)3.5 验证配置 (4)3.6 配置文件 (5)4 SNMPv3配置举例 (6)4.1 组网需求 (6)4.2 使用版本 (6)4.3 配置注意事项 (6)4.4 配置步骤 (6)4.4.1 设备的配置 (6)4.4.2 NMS的配置 (7)4.4.3 验证配置 (9)4.5 配置文件 (10)5 相关资料 (11)1 简介本文档介绍了SNMP功能典型配置举例。
2 配置前提本文档不严格与具体软、硬件版本对应,如果使用过程中与产品实际情况有差异,请参考相关产品手册,或以设备实际情况为准。
本文档中的配置均是在实验室环境下进行的配置和验证,配置前设备的所有参数均采用出厂时的缺省配置。
如果您已经对设备进行了配置,为了保证配置效果,请确认现有配置和以下举例中的配置不冲突。
本文档假设您已了解SNMP特性。
3 SNMPv1/SNMPv2c配置举例3.1 组网需求如图1所示,服务器作为NMS通过SNMPv1/SNMPv2c协议对设备进行配置文件备份,并且当设备出现故障时能够主动向NMS发送告警信息。
图1SNMPv1/v2c功能典型配置组网图3.2 使用版本本举例是在S7500E-CMW710-R7150版本上进行配置和验证的。
3.3 配置注意事项•SNMPv2c与SNMPv1配置方法完全一致,本举例中以配置SNMPv2c为例进行介绍。
[史上最详细]H3C路由器NAT典型配置案例
![[史上最详细]H3C路由器NAT典型配置案例](https://img.taocdn.com/s3/m/882e4d6942323968011ca300a6c30c225801f060.png)
H3C路由器NAT典型配置案列(史上最详细)神马CCIE,H3CIE,HCIE等网络工程师日常实施运维必备,你懂的。
1.11 NAT典型配置举例1.11.1 内网用户通过NAT地址访问外网(静态地址转换)1. 组网需求内部网络用户10.110.10.8/24使用外网地址202.38.1.100访问Internet。
2. 组网图图1-5 静态地址转换典型配置组网图3. 配置步骤# 按照组网图配置各接口的IP地址,具体配置过程略。
# 配置内网IP地址10.110.10.8到外网地址202.38.1.100之间的一对一静态地址转换映射。
<Router> system-view[Router] nat static outbound 10.110.10.8 202.38.1.100# 使配置的静态地址转换在接口GigabitEthernet1/2上生效。
[Router] interface gigabitethernet 1/2[Router-GigabitEthernet1/2] nat static enable[Router-GigabitEthernet1/2] quit4. 验证配置# 以上配置完成后,内网主机可以访问外网服务器。
通过查看如下显示信息,可以验证以上配置成功。
[Router] display nat staticStatic NAT mappings:There are 1 outbound static NAT mappings.IP-to-IP:Local IP : 10.110.10.8Global IP : 202.38.1.100Interfaces enabled with static NAT:There are 1 interfaces enabled with static NAT.Interface: GigabitEthernet1/2# 通过以下显示命令,可以看到Host访问某外网服务器时生成NAT会话信息。
H3C交换机优先级重标记和队列调度典型配置指导

H3C交换机优先级重标记和队列调度典型配置指导5.2 优先级重标记和队列调度典型配置指导5.2.1 组网图5.2.2 应用要求公司企业网通过交换机(以 S5500-EI 为例)实现互连。
网络环境描述如下: Host A 和 Host B 通过端口 GigabitEthernet 1/0/1 接入交换机; Host C 通过端口 GigabitEthernet 1/0/2 接入交换机;数据库服务器、邮件服务器和文件服务器通过端口GigabitEthernet 1/0/3 接入交换机。
配置优先级重标记和队列调度,实现如下需求:当 Host A 和 Host B 访问服务器时,交换机优先处理 Host A 和Host B 访问数据库服务器的报文,其次处理 Host A 和 Host B 访问邮件服务器的报文,最后处理 Host A 和 Host B 访问文件服务器的报文;无论Host C 访问Internet 或访问服务器,交换机都优先处理Host C 发出的报文。
5.2.3 配置过程和解释针对 Host A 和 Host B 的配置# 定义高级 ACL 3000,对目的 IP 地址为 192.168.0.1 的报文进行分类。
system-view[Switch] acl number 3000[Switch-acl-adv-3000] rule permit ip destination 192.168.0.1 0 [Switch-acl-adv-3000] quit# 定义高级 ACL 3001,对目的 IP 地址为 192.168.0.2 的报文进行分类。
system-view[Switch] acl number 3001[Switch-acl-adv-3001] rule permit ip destination 192.168.0.2 0 [Switch-acl-adv-3001] quit# 定义高级 ACL 3002,对目的 IP 地址为 192.168.0.3 的报文进行分类。
H3C S7500E系列以太网交换机操作手册

1.7 VLAN显示和维护
.............................................................................................................. 1-13
1.8 VLAN典型配置举例
3.2 配置Voice VLAN ................................................................................................................ 3-3
3.2.1 配置准备
........................................................................................... 2-3
第
3章 Voice VLAN配置
.........................................................................................................3-1
2.3 Isolate-user-vlan显示和维护
.............................................................................................. 2-2
2.4 Isolate-user-vlan典型配置举例
1.1 VLAN简介
.......................................................................................................................... 1-1
H3C交换机_典型配置举例-6W100-以太网链路聚合典型配置举例

1 链路聚合典型配置举例······················································································································· 1-1 1.1 简介 ···················································································································································1-1 1.2 二层链路聚合配置举例 ······················································································································1-1 1.2.1 适用产品和版本 ······················································································································1-1 1.2.2 组网需求 ·································································································································1-1 1.2.3 配置思路 ·································································································································1-1 1.2.4 配置注意事项 ··························································································································1-2 1.2.5 配置步骤 ·································································································································1-2 1.2.6 验证配置 ································································································································1-3 1.2.7 配置文件 ·································································································································1-4 1.3 二层聚合负载分担配置举例···············································································································1-5 1.3.1 适用产品和版本 ······················································································································1-5 1.3.2 组网需求 ·································································································································1-5 1.3.3 配置思路 ·································································································································1-6 1.3.4 配置注意事项 ··························································································································1-6 1.3.5 配置步骤 ·································································································································1-6 1.3.6 验证配置 ·································································································································1-7 1.3.7 配置文件 ·································································································································1-8 1.4 三层链路聚合配置举例 ······················································································································1-9 1.4.1 适用产品和版本 ······················································································································1-9 1.4.2 组网需求 ·······························································································································1-10 1.4.3 配置思路 ·······························································································································1-10 1.4.4 配置注意事项 ························································································································1-10 1.4.5 配置步骤 ·······························································································································1-10 1.4.6 验证配置 ·······························································································································1-11 1.4.7 配置文件 ·······························································································································1-12
H3C静态链路聚合的典型配置

H3C静态链路聚合的典型配置一、组网需求:两台H3C S3500-EA A,B之间做静态链路聚合。
这里假设e1/0/1,e1/0/2,e1/0/3端口都是trunk端口,允许vlan 10,20,30通过。
二、组网图:三、配置步骤:(1)设备A上的配置#创建二层聚合端口[switch-A] interface Bridge-Aggregation 1[switch-A-Bridge-Aggregation1] port link-type trunk[switch-A-Bridge-Aggregation1] port trunk permit vlan 10 20 30 #分别将设备A上端口e1/0/1,e1/0/2,e1/0/3加入到聚合组中[switch-A] interface Ethernet 1/0/1[switch-A-Ethernet1/0/1] port link-type trunk[switch-A-Ethernet1/0/1] port trunk permit vlan 10 20 30[switch-A-Ethernet1/0/1]port link-aggregation group 1[switch-A] interface Ethernet 1/0/2[switch-A-Ethernet1/0/2] port link-type trunk[switch-A-Ethernet1/0/2] port trunk permit vlan 10 20 30[switch-A-Ethernet1/0/2]port link-aggregation group 1[switch-A] interface Ethernet 1/0/3[switch-A-Ethernet1/0/3] port link-type trunk[switch-A-Ethernet1/0/3] port trunk permit vlan 10 20 30[switch-A-Ethernet1/0/3]port link-aggregation group 1(2)设备B上的配置设备B上的配置和A类似,这里从略。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
3.1 组网需求
如 图 1 所示,通过在作为NAS的Device上配置远程HWTACACS认证、授权功能,实现Telnet用户 的安全登录。要求在Device上配置实现: • HWTACACS 服务器对登录 Device 的 Telnet 用户进行认证和授权,登录用户名为 user@bbb,
1
• 由于本例中用户登录 Device 要通过 AAA 处理,因此 Telnet 用户登录的用户界面认证方式配 置为 scheme。
• 为了实现通过 HWTACACS 来进行认证和授权,需要在 Device 上配置 HWTACACS 方案并 指定相应的认证和授权服务器,并将其应用于 Telnet 用户所属的 ISP 域。
密码为 aabbcc; • 用户通过认证后可执行系统所有功能和资源的相关 display 命令。 图1 Telnet 用户的远端 HWTACACS 认证和授权配置组网图
HWTACACS server 10.1.1.1/24
Vlan-int2 192.168.57.12/24
Vlan-int3 10.1.1.2/24
3.4 配置步骤
3.4.1 配置HWTACACS
本文以 HWTACACS 服务器 ACS 4.0 为例,说明该例中 HWTACACS 的基本配置。 1. 增加设备管理用户 # 登录进入 HWTACACS 管理平台,点击左侧导航栏“User-Setup”增加设备管理用户。 • 在界面上输入用户名“user@bbb”; • 点击按钮“Add/Edit”进入用户编辑页面。
i
1 简介
本文档介绍了 Telnet、SSH 用户通过 AAA 服务器进行登录认证和授权的配置举例。
2 配置前提
本文档中的配置均是在实验室环境下进行的配置和验证,配置前设备的所有参数均采用出厂时的 缺省配置。如果您已经对设备进行了配置,为了保证配置效果,请确认现有配置和以下举例中的 配置不冲突。 本文假设您已了解 AAA 特性。
• 为了在 Device 和 HWTACACS 服务器之间安全地传输用户密码,并且能在 Device 上验证服 务器响应报文未被篡改,在 Device 和 HWTACACS 服务器上都要设置交互报文时所使用的 共享密钥。
3.3 使用版本
本举例是在 S7500E-CMW710-R7150 版本上进行配置和验证的。
3.4.1 配置HWTACACS······················································································································· 2 3.4.2 配置Device ································································································································ 6 3.5 验证配置 ··············································································································································· 7 3.6 配置文件 ··············································································································································· 7 4 SSH用户的RADIUS认证和授权配置举例······························································································ 8 4.1 组网需求 ··············································································································································· 8 4.2 配置思路 ··············································································································································· 9 4.3 使用版本 ··············································································································································· 9 4.4 配置步骤 ··············································································································································· 9 4.4.1 配置RADIUS服务器 ··················································································································· 9 4.4.2 配置Device ······························································································································ 11 4.5 验证配置 ············································································································································· 13 4.6 配置文件 ············································································································································· 15 5 相关资料 ············································································································································· 15
“10.1.1.2”。 • “Key”一栏填写 HWTACACS 服务器和设备通信时的共享密钥“expert”,必须和 Device
上 HWTACACS 方案里配置的认证、授权和计费共享密钥相同。 • 在“Authenticate Using”的下拉框里选择“TACACS+ (Cisco IOS)”。 • 单击“Submit+Apply”按钮完成配置。
2
图2 用户创建界面
2. 配置设备管理用户 # 在用户编辑页面上配置设备管理用户。 • 配置用户密码“aabbcc”; • 为用户选择组“Group 1”; • 单击“Submit”完成操作。
3Leabharlann 图3 用户密码配置界面3. 配置网络 # 点击左侧导航栏“Network Configuration”,在“AAA Client Hostname”处任意命名(本例为 “Device”)后开始配置网络。 • “AAA Client IP Address”一栏填写 Device 与 HWTACACS 服务器相连的接口的 IP 地址
H3C S7500E AAA 典型配置举例
Copyright © 2015 杭州华三通信技术有限公司 版权所有,保留一切权利。 非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本文档内容的部分或全部, 并不得以任何形式传播。本文档中的信息可能变动,恕不另行通知。
目录
1 简介 ······················································································································································ 1 2 配置前提 ··············································································································································· 1 3 Telnet用户的HWTACACS认证和授权配置举例 ···················································································· 1
4
图4 网络配置界面
4. 设置组 # 单击左侧导航栏“Group Setup”,选取“Group 1”(与配置设备管理用户时为用户选择的组一 致),单击“Edit Settings”进入编辑区。 • 在多选框中选择“Shell”(用户可以执行命令); • 在多选框中选择“Custom attributes”,并在文本框中输入:roles=\”network-operator\”; • 单击“Submit”后完成操作。 图5 选择组界面
