Andriod平台下手机防盗软件的设计与实现
libtersafe.so原理

文章标题:深度解析libtersafe.so原理:保护您的应用安全一、引言在当今信息爆炸的时代,随着移动互联网的快速发展,移动应用程序在人们日常生活中扮演着日益重要的角色。
然而,随之而来的安全问题也变得日益严峻,给用户和开发者带来了不小的困扰。
为了保障移动应用程序的安全性,libtersafe.so应运而生。
本文将深入探讨libtersafe.so的原理,帮助读者全面理解并应用于实际开发中。
二、libtersafe.so的概述libtersafe.so是一种用于加固Android应用程序的安全库。
它通过多种技术手段对应用程序进行保护,防止被破解、篡改和盗用。
其原理主要包括代码加密、反调试、完整性校验和动态加载等方面。
1. 代码加密在应用程序编译打包完成后,libtersafe.so会对其中的关键代码进行加密处理,使得黑客无法直接获取到敏感信息。
还会对加密后的代码进行混淆处理,增加破解的难度。
2. 反调试libtersafe.so还会对应用程序进行反调试处理,防止黑客通过动态调试工具对应用程序进行逆向分析和破解。
这一技术可以有效防止黑客窃取应用程序中的关键算法和逻辑。
3. 完整性校验为了确保应用程序的完整性,libtersafe.so会在应用程序启动时对其进行完整性校验。
如果发现应用程序被篡改或修改,将立即触发安全机制,阻止应用程序继续执行,保护用户数据不被泄露。
4. 动态加载为了防止黑客对应用程序进行静态分析破解,libtersafe.so还会采用动态加载技术,动态加载一些关键代码,使得应用程序的逻辑更加复杂,增加破解的难度。
三、个人观点和理解在我看来,libtersafe.so的原理非常巧妙,通过多种技术手段全方位地保护了应用程序的安全性。
它不仅可以有效防止黑客对应用程序进行破解和盗用,还可以为开发者提供一种安全可靠的开发环境。
在移动应用程序开发中,我认为广泛应用libtersafe.so是非常必要的,可以大大提升应用程序的安全性和可靠性。
智能车载导航与防盗系统设计

智能车载导航与防盗系统设计殷贤华;王强;姜燕【摘要】According to the dual demand of vehicle navigation and anti-theft,an intelligent vehicle navigation and anti-theft system was designed based on Android and embedded platform. The vehicle can be navigated based on GPS. A signal that is caused by an illegal intrusion or movement of the vehicle can be detected by the gravitational acceleration sensor and the vibration sensor. The control of vehicle fuel supply and power supply can be simulated by the relay. The 3G module was used to alarm the car owner and send the information of the vehicle in real time.The controller can communicate with each terminal module via Zig-Bee technology. Experiments show that the system can realize the dual function of navigation and anti-theft.%根据车辆导航与防盗双重需求,设计了一种基于Android平台的嵌入式智能车载导航与防盗系统.该系统利用GPS实现导航功能,利用重力加速度传感器和振动传感器检测车辆被非法入侵或移动的信号,利用断油断电继电器模拟车辆熄火控制,利用3G模块向车主手机报警并实时发送车辆行踪信息.中央控制器和各个终端模块之间通过ZigBee技术通信.实验表明,该系统能够实现导航和防盗双重功能.【期刊名称】《仪表技术与传感器》【年(卷),期】2018(000)002【总页数】4页(P89-92)【关键词】导航;防盗;嵌入式系统;ZigBee技术;电源管理【作者】殷贤华;王强;姜燕【作者单位】桂林电子科技大学电子工程与自动化学院,广西桂林 541004;广西自动检测技术与仪器重点实验室,广西桂林 541004;桂林电子科技大学电子工程与自动化学院,广西桂林 541004;广西自动检测技术与仪器重点实验室,广西桂林541004;桂林电子科技大学电子工程与自动化学院,广西桂林 541004;广西自动检测技术与仪器重点实验室,广西桂林 541004【正文语种】中文【中图分类】TP277;TP3110 引言近年来,我国汽车数量日益增多,汽车的行车导航问题较多[1]。
第九届“挑战杯”湖南省大学生课外学术科技作品竞赛获奖作品名单

附件1:第九届“挑战杯”湖南省大学生课外学术科技作品竞赛获奖作品名单特等奖(共10件)国防科学技术大学(1件)基于射频技术的涉密U盘监控系统张博汉于龙飞赵衰吴珊邹杰中南大学(2件)“祥龙”高适应性多功能蛇形机器人曹玉杨文璟李璟兮巩宇鹏王杨森核苷(酸)类似物对慢性乙型肝炎治疗效果的系统评价赵树山唐兰花丁翌湖南师范大学(1件)散居型农村社区公共服务设施建设的问题与对策——基于湘中25个行政村的实证研究吴博张荣锋长沙理工大学(1件)多功能电气参数测试仪李维李旻炫张修鹏张雯邓凯符奥宛璐中南林业科技大学(1件)不霉不蛀黑竹改性技术吴凤娟薛秋王淑文湖南商学院(1件)电子政务成效评价模型的构建与实证研究——以湖南省地级市为例朱金赤彭珂然潘红梅刘建广黄文艳李涛黄敏何军湖南工学院(1件)仿生越障探测车黄锦李杰宸郭秋霞张桐张芳礼湘潭大学(1件)动力电池钢壳的单体喷镀方法及装置潘俊安朱经涛曹丰文湖南科技大学(1件)纳米碳酸钙基耐水浸型特种合成纸岳坤亮寻金锭曾俊长吴磊黄昆戴绿英一等奖(共35件)国防科学技术大学(4件)基于轮腿复合结构的多适应性作战平台设计程子龙马磊朱效洲王奇黄安琪防失密笔记本电脑李清江王义楠田晓波邢金岭陈虎生红外智能交互系统李胜利常振林凌艳香一种新型超高频(UHF)射频识别(RFID)系统中读写器天线的分形设计王银坤侯申茂孔祥进中南大学(5件)湖南省湘江流域水污染现状的调研报告——基于环境管理的视角程海威李亚萍彭婉丽曹曦文曹渝吴玥邓文凯大规格超高强镁合金材料成型制备技术万迎春舒心曾新喜赵广迪邵帅方捷王星湖南省永兴县有色金属循环产业发展现状调查与研究报告李晓静袁廷刚曹承铖刘冰冰袁超钱宇轩两型社会建设背景下湘绣文化产业现状与发展模式探究韩宇奇王典王一苇郭璐庞珊珊黄琨农业科技园:推动城乡统筹发展的试验田——基于湖南望城国家农业科技园区的调研报告陈恒智李依瑶邓汉威郑姗姗周孔凝王志旭葛燕春湖南大学(3件)基于碳基金视角的我国低碳发展模式研究张玓林珊赵颖婕基于经济资本模型的银行业信用风险的宏观压力测试研究黄彦琳邓可欣煤矿开发诱发地质灾害对矿区居民的影响及班服对策研究潘然栾之珑湖南师范大学(2件)农民合作经济组织发展中的金融支持研究——基于长沙市地区个案分析邱浩宇李济东余鑫琳周婕但迁顾辉沐浴民生建设的阳光——民办孤儿院孤儿发展及其模式的实践探索冀曼雯曾威长沙理工大学(2件)新型聚苯硫醚/聚醚砜基耐磨复合材料的研制粟洋莫雪华龚建彬刘磊刘莫北基于网络管理的新时代家居智能控制系统王斌刘倞肖晖陈琦贺滢朱肖琼邱麒朱许丽丽湖南农业大学(2件)太阳能智能无线液位控制器胡文武艾卫中谢昌盛张广志谢艳群廖敦军熊中刚童艳利p14多肽——新型黄科病毒解螺旋酶抑制剂的克隆表达系统构建及抗病毒研究简熠丁婧谢雪花陈晓燕黄鹤中南林业科技大学(1件)木结构桥梁模型试验研究贺茜丁文宋佩超陈焱王超陈伟湖南中医药大学(1件)对王氏脊椎疗法治疗颈椎病机理的研究王旭武征张宏江龙家乐长沙学院(2件)新型全方位水剂喷射灭火器邓毅何习达罗映宇柏敬袁泽峰基于USB通信技术的电容触摸式无限多媒体控制器杨云峰刘兵胡久松包蕾长沙医学院(1件)人体科技馆异型样本的科学考察李乙许波龙伶方栋钟巍邓思敏衡阳师范学院(1件)基于地学信息图谱的坡耕地水土流失研究——以常宁市为例朱飞胡婷艳罗艳青王文军湖南工业大学(1件)视频监控中人体跟踪温向兵刘波谢成剑龚颖菊湘潭大学(2件)全自动莲子去芯机凌斗钟敏王凌川周银镔李仕成郑军辉湖南省洞庭湖上岸渔民可持续发展问题调查研究倪凌毛星芝马一源黎明奇涂义美李葡阳杨远立湖南科技大学(2件)巷道围岩变形自动监控与预警系统张庆伦张建庄昆瑜张磊张彬漆灿农村留守儿童心灵呵护志愿机制的研究与实践刘柯资威李颖彭林游恋湖南理工学院(1件)电梯及升降机生命保障机构童梓桂周韧肖成军瞿进周纯李茜铭湖南城市学院(1件)钢筒套筋内灌浆加固立柱试验研究蒋培湘许国胜孙秋萍邓亚丽周志伟胡幸湘南学院(1件)关于某高校准医务人员对AIDS的歧视羞辱和相关职业暴露知识现况研究及干预探讨陈运平湖南人文科技学院(1件)公平与效益的博弈——关于中部地区农村中小学撤点并校的调查与反思李盼强喻树林曾尔琴王强李维吉首大学(1件)土家族传统药用植物彩色图典肖艳刘云娇周光凤湖南电气职业技术学院(1件)合动力大巴运行数据采集系统邹明智二等奖(共121件)国防科学技术大学(8件)模块化轮式移动机器人廖波刘海波于乃辉基于头盔显示器何体感技术的单兵虚拟训练系统徐龙龙夏博保金桢陈东张见杨静基于ZigBee及GSM网络电器管理平台罗延金崔婧周云峰朱梦宇机敏战士——无人化侦查武器平台伍惟俊陈海涛潘瑶陈廷斌张慧博ATM数键分离密码防窃取装置唐璜杨大川俞晓海丁钰利用太阳能等热能的温差发电系统曾旸任广森郭良朱亚东邱晓天仿水黾四足复合材料水面滑行器朱宝军黄俊刘勇何玲张章刍议文化对中国实现伟大民族复兴的作用张子伟赵泽洋张晓宇冈敦殿刘俊林中南大学(8件)基于智能视觉技术医用药剂中可见异物自动化检测系统苏雨阳谢伟涛张瑞楷桑延奇肖亮两型社会要求下土地流转市场机制设计——以实现规模经济为目的陈宇王灏李学东许棋吴菲雅郑思维宁文博湖南农业信息化调查与对策研究——湖南与新疆农业信息化对比的视角刘明敏周小平包尔罗乐文铭马洪烈低碳农业视角下的区域产业循环模式探究——以祁阳县为例谢婧柳唐楚楚陈铭波方闻千共享发展成果,构建和谐社会——最低工资制度在长株潭地区实施情况的调查毛蓝米雪黄梓钊田放张伟蒋浩识湖南省非标准劳动关系发展状况调查及对策思考——以湖南省长株潭地区为例夏冰杜鹃马德帅夏梦阳余悦欧阳竟成许栗山降钙素基因相关肽对脂多糖诱导的巨噬细胞表达髓样细胞触发受体-1的影响李云超周漾施萌李文杰Synthesis of ZrSiO4Cd(S1–xSex) inclusion pigments by micro-emulsion method[微乳液法合成ZrSiO4Cd(S1–xSex)包裹色料)]丁意张开春李媚王顺葵湖南大学(4件)TrackerNerv道路车辆识别跟踪系统刘升高晗肖潇彭群基于移相控制的臭氧软开关电源司超许亮中国南方小型农田水利设施建设的机制创新张润泽李骅谭萃杨子毅黄旭东农民工返乡创业受益影响因素调查报告蔡婕萍何知吴超辉湖南师范大学(9件)基于博世——力士乐数控系统的凸轮轴磨床控制软件开发王东昱蔡文申彬彬往复式高层火灾逃生缓降器李密陈能立龙芬李辉英徐桂花基于新型三网模式下的智能家居并发控制系统黄端袁纯张玲苏美滋农村劳动力外流与我国粮食安全——基于全国粮食产销百强县衡南县的调查报告李婉婷姜雨含刘霞B2C网络慈善平台的建设与应用创新——以长沙市为例王鹏郑培娟于宪何璇芳冀曼雯李季李尚鹏潘多拉的魔盒:3G时代手机不良信息在青少年群体中的传播与影响—基于全国5省10市实证研究廖晶晶侯娟王丹枫李丫张磊流水线上的守望——民营企业流水线工人心理健康影响因素探究廖珂刘芳周莎莎白晓玉周瑾敏社会政策视阈下新生代女农民工城市适应性研究——以长沙永州张家界三市为例陈伟舒梦王玲芳周彦增谢倩农民工子女心理健康问题的干预研究吴文何金波李俊康曾志佳周彩萍杨文韬刘伟长沙理工大学(7件)货车尾部防撞新装置杨兰雷沐羲雷泽湘魏书彬刘一衡智能配电网接地故障有源消弧与保护系统王阳李健郭浩潘慧卓超李臻奇袁宇波魏梦阳基于相变控温设计的梯度功能混凝土路面结构及模型贺敬李柯潘明江孙淼李成家用多功能光伏并网发电系统孟庆辉谭富民曾立军吕鹏唐振国刘湘龙段美婕废弃氟石膏改性及做绿色建材和工业原料刘义姚艳杨纯任振兴张悦肖博黄中斯智能防坠安全装置童柏云伍奇宋奎甘航宇曾彦汪衡梁昶长沙橘子洲景区规划建设问题探析及对策研究贺建隆张典帅樊迪彭杰湖南农业大学(2件)一株虎杖糖苷水解酶产生菌筛选鉴定及其酶学特性的研究庞一林贺潜杨祖佑多孔混凝土连通孔隙率与抗压强度影响因素的试验研究杨加欧正蜂陈蛟刘行海周松中南林业科技大学(5件)废旧报纸回收纤维/聚乳酸生物可降解复合新材料的研制程芳童茁陈卫民卢璐莎田翠花贺霞陆生木本水培花卉韩志强王城顺胡召波邢怡祺刘彩霞湖南省集体林权制度改革配套服务体系调查报告王佩兰李长龙谭坚峰冯晨西洞庭生物多样性绿地图李芳刘祎炜阙胜峰时潘潘肖勇朱江华罗艳青王溶螺旋藻保健牛奶及牛乳饮料的研制刘莎莎陈业霖任洪浩徐洁湖南中医药大学(1件)局部间断应用VEGF对跟腱内源性愈合的影响研究蔡伟良汤明春毛锐湖南商学院(3件)湖南省农村老年人幸福指数实证研究徐艳慧蒋妤婷姜春桃刘剑彭佳颖刘慧杨霄曹姝和谐社会视角下精神病人救助模式研究——以长沙市为例颜帅黄丹珺潘婷王蒙杨阳李鼎刘安琪向江洲大学生误入传销陷阱的调查研究——以长沙地区高校为例曾文珏周建平李静潘蕾谭菲易陈强邹骞唐光宇长沙学院(3件)全自动玉米脱粒机刘文建高熙鸿尹华根黄果果黄政远程视频监控作业小车尚添陈浩郝乾啸自助无线点餐系统刘兵胡久松谭星杨云峰湖南第一师范学院(1件)简易式音响王文莉南华大学(3件)破冰除雪车满文成郑羽陈毅敏刘勇张海艳刘东赵嘉东机械扩大的桩尖与两次扩大头管桩的施工方法单智李瑞倾许岩剑大学生精神文化消费现状的调查分析与对策研究杨权琳孟文黄东荣何余黄启聪曹宇帆陈丹衡阳师范学院(2件)南岳古镇文化景观基因特征分析李冻陈坤华郭小杰夏琳唐娥荧光法研究三氮烯衍生物与阴离子表面活性剂的相互作用及水样中痕量阴离子表面活性剂的检测王雪新曾慧婷雷依超吴贞祥方淑英邢静湖南工学院(2件)仿生扑翼飞行器刘宇郭扬赵俊邹健雄王其车载驾驶员疲劳驾驶智能监控制系统研究熊兑韬湖南工业大学(5件)基于Android平台及J2EE的手机防盗与跟踪系统刘鑫标过志刚曹贵芝杜鹏伦智能逃生门向旺杨志荣关于株洲市农村土地流转情况的调查单龙军吴朝煌陈亮林洵婷敬琳流浪儿童受教育权现状及完善途径廖凌敏邹学平伍肖谕刘蓓苏婧过氧化氢生产过程中废氧化铝微球的高资源化利用技术的研究李加加石文莹李玉停龙志华刘佩佩湘潭大学(4件)3D虚拟校园微观网络平台龙辉刘戈张微罗浩毕伟祥杜康华黄震袁伟华一种FLV高清视频网站系统设计周泉刘洋谢谦长株潭地区重点装备制造企业知识产权现状调研报告李宇彭艳消费者商场“手机钱包”初始信任影响因素的实证研究:基于长株潭试点区域张军校廖柔静李艳刘澎辉戴忆奇湖南科技大学(3件)基于等离子体辉光放电技术的电子黑板研究与实现唐伟东刘孟龙罗克华黄彦宋盼湘江流域污染企业的治理与补偿机制研究刘成胡莹龙志群姜博莫毓黎唐扶祥秦华长株潭“两型社会”建设中新型行政管理体制初探朱旭峰刘娟湖南工程学院(3件)螃蟹机械手谭鸣胡滔张桓翊曾夏衡李辉带过载保护定时插座李胜文刘纯亮段博杨继新锥栗原淀粉及其分离组分的热力学特性胡蝶吴平湖南理工学院(6件)基于视觉动视质量的移频监控系统刘春龙骆志辉熊斌罗晓成我国现阶段社会群体性事件的特征成因及防治策略——基于岳阳市出租车停运事件的调查分析郑茜彭西妍许一清易龙飞张东方易桂芝基于劳动合同法视角下的大学生兼职纠纷情况调查——以岳阳市为例陈友云蒋伊琳胡美玲张文倩卢纯瞿伟光纤 DWDM系统中非线性效应数值仿真研究凌龙辉李乔谭伟敏汤备子频带的优化划分与带限信号的重构自适应算法蒋宏弼黄一休欧阳强雷林肖海洋三聚氰胺对草酸钙结石形成机理的影响李龙李红亮黄义华寻中华王伟陈鹏飞湖南文理学院(1件)“镇村同治理念”下革命老区村镇建设规划调查与研究报告冯丕成刘杰姜祺源邱献议湖南城市学院(2件)益阳市高中生职业生涯规划研究伍凤刘银燕王敏陈运农村太阳能沼气联合供热创新研究李文强廖琪张卿鲁蓉蓉湘南学院(3件)杜仲降压口香糖李遐郝凤周慧佳陈娇张丽君叶辉刘静基于GPRS彩信模块的远程监控多功能家庭安防系统刘海斌廖梦林李浪宋寒屈波涛具有Hybrid边值条件的分数阶微分包含解存在的一个新结果李国栋湖南科技学院(2件)嵌入式智能晾衣架龙剑肖雄彭灿杜杰李相钊微波促进磺化炭催化合成月桂酸甲酯毛兰兰肖军杨检刘望陈艳红怀化学院(4件)资源枯竭型城市经济转型研究——以湘中地区城市为例刘艳萍雪峰“断颈龙”灯舞的美学内涵和社会价值向娅玲孙乐平段悦琴郭霞袁灿储油罐的变位识别与罐容表标定研究曾光刘传星王玮姚湾湾石毅辰溪石煤矿中提取钒的研究朱文雅蔡峰谢利红何庭满沛志湖南人文科技学院(2件)一种用甘蔗渣制备保水剂的方法万富新生代农民工生存与发展调查报告谢志群韩周王欢聂小为吉首大学(6件)暑期实践——花垣县经济转型调研报告高萍肖和纪杨瑾陈娜杜卫国守望者说——寻访吉首与凤凰国家级非物质文化遗产传承人张旺张静丁渝珈陈德夫杨大智徐佳朱勇丁维联湘西土家族毛古斯文化调查报告田甜陈诗毛元媛贾杰向超张程侯森耀邓梦莹湘渝黔“锰三角”地带环境治理的机制与模式研究谢丽玲刘涛刘师师李颜韩轩湖南德夯风景区藤本植物多样性研究周建军钱凯歌响应面优化超声波辅助水酶法提取茶叶籽油工艺王敬敬曾巧辉逯与运怀化医学高等专科学校(1件)流动食品摊点卫生状况调查及监管对策研究曹乙芳廖菁卿邱玲梁高兰王秀梅湖南中医药高等专科学校(1件)大学生寻常性痤疮发病与情志关系的调查黄听听陈露娟梁双梅黄洁琼罗金平陈伟丹长沙民政职业技术学院(1件)“同片蓝天”关注农民工子女玫瑰义卖实践报告陈美蓉湖南信息职业技术学院(1件)多功能智能小车刘彬傅翔湖南科技职业学院(2件)简便螺旋式轴承压入机的创新设计与制造彭雪辉曹丹曾国泽大学生村官现状调查报告——以湖南省科技职业学院大学生村官肖志龙为例尹理敏朱海波朱伍阳湖南生物机电职业技术学院(1件)低温火腿肠保水性与生产工艺研究樊鹏勃刘永兰邓春雪杨燕欧小娟长沙环境保护职业技术学院(1件)“永州血鸭”冷冻调理食品的研制王敏林小妹张俐俐湖南司法警官职业学院(1件)法律援助之关于家庭暴力社会调查报告徐安全黄振易苗陈一琼石明月罗乾坤严跃文钦文星湖南软件职业学院(2件)多媒体视力训练系统邓超群吴冠环境保护公益系列动画片项目策划书——《湘江鱼鱼船队》彭嗣芬李颖硕王曦湖南现代物流职业技术学院(1件)贵州省遵义县辣椒产业链存在的问题与对策分析杨钰湖南化工职业技术学院(1件)白象方便面市场调研报告肖兵杨梦林陈康雄颜霖唐建兴湘潭职业技术学院(2件)防长流水自关断自动控制阀李文杨林江陈奎湖南省留守儿童成长发展研究调查报告周美王瑜方亚郭品帅许哲王京湖南电气职业技术学院(1件)太阳能热水器优化系统罗佳俊湖南环境生物职业技术学院(2件)以自办报刊开辟高职学生就业新渠道谌理泉谢丽丽李兰青王佳乐潘彦求用AMS-V型动物血细胞定量分析法监测犬瘟热治疗效果的研究周密密湖南高速铁路职业技术学院(2件)班级公司化系统林沛平基于对村官理想的大学生农村社会实践调查报告周贤兵张建庭陈俊杨柳邹毅刘小龙岳阳职业技术学院(1件)“病理取材健康记录系统”产品开发赵亚丽赵小玲卢婷沈文刘书甜邱雨张家界航空工业职业技术学院(1件)K14B发动机缸气门锁片快速压装夹具吴志广三等奖(共231件)国防科学技术大学(2件)单桨自消旋涵道风扇飞行器单上求吴岸平张国鹏刘俊林郭天豪应急救灾物资资金运行管理模式研究黄长云陈林湖南大学(6件)多功能垃圾桶胡方义戴芳芳吴彦霏赵嘉熊施权速滑水橇徐新生杨嘉崔杰节能赛车电控离合系统的设计与优化刘李盼周全明智能电网家庭用电监控系统熊海涛李建闽康力张玲清风系列新型室内空气处理器张水平黄芬芬宋媛媛许瑞张进文经济实力外化与文化软实力增长:基于改革开放以来的实证数据分析唐怡欧阳昕戴旖旎柳梦娜湖南师范大学(3件)以非物质文化遗产伟依托的文化创意产业与大学生创业的前景性研究——以隆回滩头木版年画调研为例谢魁璋魏仁珍杨紫晖饶敏罗宇美阳永锋陈起航面向体感游戏的人体运动生成方法李季刘念李亚平宋翔飞染料敏化太阳能电池的性能改进研究何荣李杨欧阳睿张玉凤长沙理工大学(5件)出租车合乘路径选择与费用优化肖尧刘天增赵翘楚夏西汤承芳激光遥控烟花点火装置李聪李春艳肖爽刘雅儒膜片式流体滤波器谭文成王守兵王雪芝复合导电聚合物涂层改性的质子交换膜燃料电池不锈钢双极板的制备左成刚李宜峰霍霖霖赵志飞唐诗姜春颖任亚黄璟瑜竹炭负载纳米铁系催化剂光电降解有机废水装置的研究刘军余熙艳孟秋节朱锦涛陈敏左丹龙婷焦晓翠湖南农业大学(6件)氟苯尼考混悬型微乳剂的制备及药效学研究杨昆杨亚刘晗罗璋朱鑫利用餐厅回收物生产微生物饲料添加剂刘振唐湘薇杨冠史艳云王婧周超宜晨亮林秋枫外来物种福寿螺入侵湘江的危害及防治邓杰李梦芸詹学武李虹辉戴富全张明轩杜娇RFC3对拟南芥抗性生长和花器官发育的调控作用研究倪金魁崔看赵一夫向志敏魏芳肖植升戴菁博落回提取物防治断奶仔猪腹泻效果研究方成堃空间结构对抗病毒肽活性的影响:p14肽及转导蛋白的氨基酸改造及其活性影响丁婧简熠黄子裕郑慧欣贺洁琼中南林业科技大学(8件)单元式移动立体停车系统李禹龙谷园油茶粕固态发酵饲料条件的研究朱培丁彦鹏大泉村土地集约利用评价王钰亮郑晓丽刘生张金农民收入与农村物流发展水平动态关系研究——以湖南省为例伍婷王丽丽沈淑莲黄奇峰康健新农村家具市场调研何婧卢维佳盛春亮王敏璐吴珺胡薇残疾人旅游障碍分析杨慧周丹李春霞基于能量转移的稀土和锰共掺单一基质白光发射LED用荧光粉的合成和发光性质研究余涛肖骐谢灿盐酸美金刚胺的合成李辉齐帆湖南中医药大学(8件)实用腰椎骨折复位床马笃军刘庆国向剑锋蔡青张楠阳晶晶多功能步态康复训练机辛蔚贺薪伊刘佳苑真毓肖开心黄鹤朱重政长沙市大学生寝室矛盾调查报告——基于五级化解机制的研究邓蓉卿蓓蕾关于留守家庭男性犯罪青少年的攻击性特点及影响因素的研究黎亚易丽娟王娜破血逐瘀中药对肝癌HepG2细胞增殖及生长影响研究谭茜陈园薏米黄酒对机体免疫及肠道功能的调节作用研究赵雨橙邓红洁补肾化瘀方对PCOS大鼠血脂水平的影响鲁璨颜斌清肝宁肺汤治疗咳嗽变异性哮喘疗效与机理的实验研究童骄朱文雄曾逸笛葛资宇湖南商学院(6件)新型工业化道路建设背景下湘阴县水产品供应链一体化研究许钟远陈璐程恒楚琬琰蒋世意向云肖智雄湖南省少数民族聚居区商贸发展研究徐石磊周维瓯玉香龚叶梨杨相刘康新型农村社会养老保险制度创新研究——基于“BSI”机构在长株潭试点的可行性探析李巧喻炼张勇戴珍冯敏何刚成常德市城市扩建中城市边缘地区耕地保护问题研究徐倩章辉邓鹏黄春兰黄靖邓芝华龙霞罗正旅游景区社区参与中的利益协调机制研究蒋国国徐塔周卓杜娟周娅扶熙詹雨栖黄丹珺“两型社会”背景下农地流转推进模式探索——基于长沙大河西先导区农户意愿的调查魏来胡项连宋剑刘妤曹雅琴新型多功能花炮卷筒机的设计黎俊王强李颖熊涛李杰基于Wildfire的彩纸拉炮纸片自动安装设备的设计及简单模型制作段想平姚亮王炼曾一心汽车智能防超载系统龙洁滕艳丽全方位万能充电器张楷黎俊李靖周观发王强基于单片机恶性负载智能识别控制器的设计胡久松刘兵谭星包蕾湖南第一师范学院(9件)关于当代大学生理想信念的调查报告及论文王雪娇关于湖南大一新生大学适度及个人预期的调查王成李盼从隐喻学角度赏析《一个推销员的生活》胡莎湖南省常德市桃源县偏远山区基础教育现状调查报告——以常德市桃源县西安镇中心小学为例曾志远罗正康师范生的社会支持与生涯社会支持状况的调查研究贺泽霖“国贫县”:实现义务教育“脱贫”,还要走多久——关于江华瑶族自治县义务教育现状的调查报告左重元基础教育发展如何继续“深加工”——关于对中部地区农村基础教育现状的继续再调查研究报告(以湖南省桂东县新坊乡为例)彭涛“授爱于教”:关注贫困村小基础教育——关于邵东朋山村水口小学教育现状调查报告李珂李静景李欢有趣的幻方张园园湖南涉外经济学院(2件)80MHz调频发射机傅文卫温柔背后的苦涩王靓易杰。
基于Android4.0的蓝牙防丢失报警功能实现

DOI:10.19392/j.cnki.1671-7341.201912065基于Android4.0的蓝牙防丢失报警功能实现李雨航蒋玮杰刘元刘毅文怀化学院湖南怀化418000摘要:文章首先分析了以Android4.0为基础的蓝牙防丢失警报系统的运行原理,随后介绍了以Android4.0为基础的蓝牙防丢失警报功能的实现,包括设计思想、结构设计、定位代码设计等,希望能给相关人士提供一些参考。
关键词:Android4.0;蓝牙防丢失;报警功能一、以Android4.0为基础的蓝牙防丢失警报系统的运行原理Android4.0系统也被称作是冰淇淋三明治,简称ICS,是谷歌推出的一种操作系统,其拥有十大特征,运行速度有所提高。
Android4.0中还拥有新型设计的人性化UI界面,UI设计也将更加成熟。
随着众多生产厂商开始研制双核智能手机,Android4.0也将对双核或是多核处理器进行优化设计,将手机中的双核性能全面发挥出来。
以Android4.0为基础的蓝牙防丢失警报系统主要包括设备元件与手机等两部分内容,其中手机主要发挥的功能是寻找信号和接收信号等,设备主要功能就是报警系统与信息接收,尽管一部手机可以同时配对多种设备,但是在相同的时间里只能和一项设备进行连接,手机和设备之间的距离也不可以大于设备接收限制,不然两者之间的联系就是立刻中断,具体运行流程如下,首先是将手机中的APP软件打开,和相应的设备进行连接,在功率抵达范围之内,在这种条件下手机中的APP软件就不会自动报警或是弹出各种消息。
其次手机与设备之间处于一种断开或是没有连接的状态。
手机中的APP软件就会自动给予提示,需要将振动与定位打开,将设备所处位置准确显示出来,设备能够自动闪光,出现蜂鸣和振动。
再次,设备应该附带与随身装置的物品当中,因此应该对设备进行科学设计,从而保证设备的随身携带性,比如可以将设备设计成一种书签的形式或是锁扣的形式,只能应用小型的电池,保证设备的附着力。
毕业论文(设计)备选题目一览表(电子电气工程系--电子信息工程专业20151229)
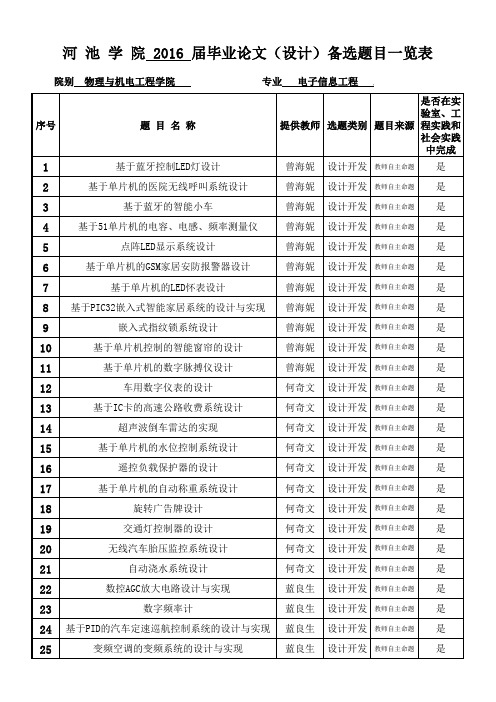
河 池 学 院 2016 届毕业论文(设计)备选题目一览表 院别 物理与机电工程学院 专业 电子信息工程注:1.选题类别:理论研究、应用研究、设计开发、其他;2.题目来源分为教师自主命题、教师课题;3.“是否在实验室、工程实践和社会实践中完成”填“是”或“否”;4.本表分专业填写,一式两份,一份由二级学院存档,一份上交教务处。
难度(偏难、适中、偏易)分量(充足、一般、不足)选题学生姓名适中充足适中充足适中充足适中充足适中充足适中充足适中充足适中充足适中充足适中充足适中充足适中充足谢杰锋偏难充足适中充足适中充足宋子阳适中充足适中充足李吉星适中充足容贤木适中充足雷远明适中充足适中充足适中充足适中充足适中充足适中充足适中充足偏难充足偏难充足偏难充足偏难充足适中充足适中充足适中充足偏难充足适中充足适中充足适中充足偏难充足偏难充足适中充足偏难充足适中充足偏难充足适中充足适中充足朱乾华适中充足适中充足黄业安适中充足谢佳权适中充足偏难充足偏难充足阮联波偏难充足王思适中一般偏难充足段军明偏难充足潘冬利适中一般梁家玉适中一般万锡敏适中一般杨水兰适中一般黄柳荣适中一般李丽君偏难充足柏国宏适中充足适中充足偏难充足适中充足适中充足适中充足适中充足偏难充足适中充足适中充足适中充足适中一般适中一般适中一般适中一般适中一般适中一般适中适中孟方娜适中适中尤业和适中适中廖家隆适中李健玲适中叶桂材适中劳忠灿适中高震偏难偏难偏难黄华漩适中黄创观适中适中偏难曾海明偏难王亚彬适中冯焕开偏易适中黄泽富适中适中适中适中适中适中适中李涛涛适中朱建林适中韦少娟适中覃文适中一般适中充足适中充足适中充足适中充足适中充足适中充足饶志鹏适中充足韦少青适中充足韦达侯适中充足陈俊适中充足适中充足黄冠诚适中充足适中充足陈胜桓偏难充足适中充足适中充足严志凡偏难充足适中充足李丽智偏难充足适中充足汤祖荣适中充足偏难充足适中充足偏难充足石权勇适中充足适中充足顾金虹适中充足张申杰适中充足甘秋香适中充足刘家辉。
基于Android的手机防盗软件的研究与实现

基金项 目: 国家 自然 科 学基 金 面 上项 目( 6 1 3 7 0 2 2 3 ) ; 湖 北 省 自然 科 学 基 金 面 上 项 目( 2 0 1 4 C F B 5 7 7 )
作者简介 : 李纪平( 1 9 7 2 一 ) , 男, 湖北汉川人 , 湖 北 工 程 学 院 计 算 机 与信 息 科 学 学 院 副教 授 , 博士。 丁 么明( 1 9 6 3 - ) , 男, 湖 北 孝 昌人 , 湖 北 工 程 学 院 计 算 机 与信 息科 学 学 院教 授 , 博士 。
录 Us e r n a me 和 P a s s wo r d , 以及 要 绑 定 的 S e c u r i —
t y Nu mb e r 和S I M 卡信 息等 。
警告 、 手机 定 位 跟 踪 、 手机锁屏、 隐私 数 据 清 除 及 手机 语音 警告 等功 能 。
1 . 2 系统功 能 当手 机开 机 时 , 系统 首 先 检 测 该 安全 软件 是
第 3 6卷 第 6 期
2 0 1 6年 1 1月
湖 北 工 程 学 院 学 报
J OURNAL OF HU B EI ENGI NEERI NG
V0 L . 3 6 N0. 6 N0V. 2 0 1 6
基 于 An d r o i d的 手机 防 盗 软 件 的 研 究 与 实 现
否是 首 次在此 手机 上运 行 , 若是 , 就 进行 初 始 化设
置, 完成 登 录用户 名和 登 录密码 , 以及 安全 号 码 的 设 置 。当初 始 化 设 置 完 成 后 , 系统将 S I M 卡 信
的 总体 设 计 方 案 和 流 程 , 详 细 给 出 了各模 块 的具 体 实 现 方 法 和 相 应 的关 键 代 码 。该 软 件 采 用 后 台监 听 技 术 , 以
手机防盗追踪系统的设计与实现
手机防盗追踪系统的设计与实现古发辉;赖路燕;井福荣【期刊名称】《电脑知识与技术》【年(卷),期】2015(011)031【摘要】In modern life, people have been separated from the mobile phone, many important information is stored in the mobile phone. Mobile security has become an urgent need to solve the problem of modern society. This paper the design and implementa-tion of a mobile phone anti-theft tracking system is to effectively solve real-time monitoring of mobile phone status and data backup function based on GPS positioning, base station location, sensor technology, data backup and other technology.%现代生活中人们已经离不开手机,许多重要信息都存储在手机中,手机防盗已成为现代社会迫切需要解决的问题.该文基于GPS定位、基站定位、传感器技术、数据备份等技术设计了一款手机防盗追踪系统,实现了实时监听手机状态和数据备份功能,有效解决了手机防盗问题.【总页数】3页(P56-58)【作者】古发辉;赖路燕;井福荣【作者单位】江西应用技术职业学院信息工程学院,江西赣州341000;江西环境工程职业学院商学院,江西赣州341000;江西理工大学信息工程学院,江西赣州341000【正文语种】中文【中图分类】TP393【相关文献】1.智能手机的防盗系统设计与实现 [J], 朱鹏;陈瑞斌2.一种利用IMSI检测和人脸识别的手机防盗追踪系统研究 [J], 周非;叶超龙;张贵棕3.基于Android的手机防盗软件设计与实现 [J], 陈博;张伟;刘丽君4.基于Android平台手机防盗软件的设计与实现 [J], 罗永宏;王剑;冯超5.探析安卓系统的手机防盗设计与实现 [J], 李俊因版权原因,仅展示原文概要,查看原文内容请购买。
基于Android平台的手机防盗与数据保护系统
( 高级加密准则1 算法加密数据 , 最大程度保证数据传输
的安全。 另外 , 在 定 位遗 失 设 备 过 程 中 , 实 现 自动拍 照 , 获取当前环境 , 让用户准确知道手机所在地址 . 同 时 在 其他功能 上也有所改进 , 运用 A n d r o i d编 程 , 实 现 了 此
系统。
人关注 .特别是人们愈发依赖 以智能手机为代 表的智 能终端来保存重要信息资料 . 手机 的丢失 . 将会 造成严
重的损失 , 由此可 见 。 其 安 全 性 至关 重 要 。
如今 . 市.
1 系统设 计 与 实现
★基金 项 目 : 重 庆 市 大 学 生创 新创 业训 练 计 划 ( No . 2 0 1 2 1 0 6 1 7 0 1 5 )
收 稿 日期 : 2 0 1 3 — 0 8 —0 2 修 稿 日期 : 2 0 1 3 — 0 8 —0 8
作 者 简介 : 王颖( 1 9 9 3 一) , 女, 重庆人 , 本科 , 研 究 方 向 为信 息安 全
加 密 传 输 等 安 全 措施 。 针对这一现状 , 该 系统 运 用 基 于 E c h F l s e 平 台的 A n d r o i d编 程 , 实现 集
S I M 监控 、 地理位置获取、 图像 采 集 、 隐私 数 据 远 程 备 份 等 功 能 于一 体 的手 机 防盗 与数 据 保
远程备份数据 , 但是 . 数据在传输过程 中的安全性无法
保证 。 另 一方 面 , Wa v e S e c u r e 能 在 地 图上 标 出 遗 失设 备 的位置 , 但 地 图本 身 的 缺 陷 可 能 导 致 定 位 [ 6 1 范 围过大 . 使 此 功 能缺 乏 实 际 的意 义
联网防盗报警方案
(3)烟雾火警探测器:检测火警烟雾,预防火灾事故。
(4)紧急求助按钮:方便用户在紧急情况下求助。
3.数据传输层
采用有线与无线相结合的传输方式,确保报警数据稳定传输。
(1)有线传输:利用现有宽带网络资源,实现报警数据的高速传输。
(2)无线传输:采用GPRS、4G、NB-IoT等无线通信技术,实现报警数据的远程传输。
联网防盗报警方案
第1篇
联网防盗报警方案
一、项目背景
随着我国社会经济的快速发展,人民生活水平的不断提高,安全问题日益受到关注。尤其是在居民住宅、商业场所、企事业单位等领域,防盗安全需求日益迫切。为了保护人民群众的生命财产安全,减少犯罪事件发生,构建和谐社会,本项目旨在制定一套合法合规的联网防盗报警方案。
二、方案目标
1.提高防盗报警系统的实时性、准确性和可靠性。
2.实现远程监控和报警信息推送,提高应急响应速度。
3.降低系统建设和运维成本,提高投资回报率。
4.符合国家法律法规,确保系统合法合规运行。
三、方案设计
1.系统架构
本方案采用分布式架构,包括前端报警设备、传输网络、报警中心和管理平台四个部分。
2.前端报警设备
2.建立健全内部管理制度,加强对系统用户的管理和培训。
3.加强对前端报警设备的质量把控,确保设备符合国家标准。
4.采取加密措施,保护用户隐私和数据安全。
五、项目实施与验收
1.项目实施
(1)制定详细的实施计划,明确责任分工和进度安排。
(2)按照设计方案,进行前端报警设备的安装和调试。
(3)搭建传输网络,确保报警信号的实时传输。
第2篇
联网防盗报警方案
基于Android的手机安全软件设计与实现
本课题的目的是开发一款实用的手机安全软件,对手机的安全进行管理,非
常有益于保障人们生活少受干扰,并且能在一定程度上保护人们的隐私,让用户能放心地使用手机。同时,该软件的设计与实现也是对Android应用程序开发知识的综合应用,可在设计和实现的过程中学习掌握Android应用开发的基础知识和开发技术,锻炼自主学习能力,积累开发经验,增强发现问题、解决问题的能力。
(1)软件系统流程图,如图3-1所示。
图3-1系统流程图
(2)软件系统用例图,如图3-2所示。
图3-2系统用例图
(3)软件模块顺序图
1)软件管理模块顺序图,如图3-3所示。
2)手机杀毒模块顺序图:如图3-4所示。
图3-3软件管理模块顺序图
图3-4手机杀毒模块顺序图
(4)活动图
1)软件管理模块活动图:如图3-5所示。
本应用软件采用安卓开源系统技术,利用利用java语言和eclipse工具进行代码编写和设计,通过搭建开发环境、需求分析以及详细的系统设计,展示了本应用的六大主要功能模块:手机防盗、软件管理、任务管理、流量管理、手机杀毒、系统优化。最后集成各个模块运行,总体运行正常。
本文第一章是绪论,简要地概括课题研究的背景、目的及其意义,简述Android的发展情况以及所需的软硬件环境。第二章介绍Android系统架构,主要阐述该架构的操作系统层、各种库和运行环境、应用程序框架和应用程序层。第三章是软件系统分析,介绍需求分析、可行性分析,还有一些UML图。第四章是软件系统设计与实现,包括布局设计实现和功能设计实现。第五章是软件测试,主要包括测试结果截图及其分析。最后是对本文的总结。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Low-complexity and energy efficient image compression scheme for wireless sensor networksQin Lu a,*,Wusheng Luo a ,Jidong Wang a ,Bo Chen baDepartment of Instrument Science and Technology,College of Mechatronics Engineering and Automation,National University of Defense Technology,Changsha 410073,China bDepartment of Mathematic and System Science,College of Science,National University of Defense Technology,Changsha 410073,Chinaa r t i c l e i n f o Available online 29May 2008Keywords:Image compressionComputational complexity Energy consumption WSNsa b s t r a c tCurrently most energy-constrained wireless sensor networks are designed with the object of minimizing the communication power at the cost of more computation.To achieve high com-pression efficiency,the main image compression algorithms used in wireless sensor net-works are the high-complexity,state-of-the-art image compression standards,such as JPEG2000.These algorithms require complex hardware and make the energy consumption for computation comparable to communication energy dissipation.To reduce the hardware cost and the energy consumption of the sensor network,a low-complexity and energy effi-cient image compression scheme is proposed.The compression algorithm in the proposed scheme greatly lowers the computational complexity and reduces the required memory,while it still achieves required PSNR.The proposed implementation scheme of the image compression algorithm overcomes the computation and energy limitation of individual nodes by sharing the processing of tasks.And,it applies transmission range adjustment to save communication energy dissipation.Performance of the proposed scheme is investigated with respect to image quality and energy consumption.Simulation results show that it greatly prolongs the lifetime of the network under a specific image quality requirement.Ó2008Elsevier B.V.All rights reserved.1.IntroductionMany of the potential WSN applications such as target tracking,process control,source localization,discovering and following rare animal species,controlling the vehicle traffic on highways and railways necessitate efficient im-age communication in sensor networks.Since in these im-age-based applications,resources-constrained sensor nodes need to capture,compress and transmit a large amount of data,processing and communication efficiency of the compression algorithms is clearly a design con-straint,which needs to be carefully addressed [1].Recently a number of research efforts are under way to address the issue of image compression and transmissionin sensor networks.Pradhan et al.proposed a distributed coding framework to realize the coding gain of correlated data from the Slepian–Wolf coding theorem in informa-tion theory [2].Wagner et al.proposed another distrib-uted image compression scheme [3]by sending the low-resolution overlapped areas to the receiver and using super-resolution recovery techniques to reconstruct them.Min Wu et al.proposed a novel collaborative image trans-mission scheme [4].This scheme firstly employs a shape matching method along the route to find out the maximal overlap between images.Then the original image and the difference between another image and it are coded to transmit instead of transmitting two individual images independently.These works are designed with the object of minimizing the communication power at the cost of more computation.Except the distributed image compression for multiple correlated images based on1389-1286/$-see front matter Ó2008Elsevier B.V.All rights reserved.doi:10.1016/net.2008.05.006*Corresponding author.E-mail address:freda0126@ (Q.Lu).Computer Networks 52(2008)2594–2603Contents lists available at ScienceDirectComputer Networksj o u r n a l h o m e p a g e :w w w.e l s e v i e r.c o m /l o c a t e /c om n e tthe Slepian–Wolf coding theorem,few schemes consider the computational complexity of the image compression algorithms.The high-complexity state-of-the-art image compression standards,such as JPEG2000,are still the main methods they used.However,these image compres-sion algorithms are not suitable for resource-constrained wireless sensor networks because they require complex hardware and make the energy consumption for compu-tation comparable to communication energy dissipation. Therefore,a low-complexity and high efficient image compression algorithm should be designed in order to re-duce the hardware cost and the energy consumption of the sensor network.To prolong the lifetime of the network,the implementa-tion scheme of image compression algorithm should also be considered in the design.Traditionally,source coding is implemented at the source in order to reduce the num-ber of bits transmitted thus reducing the communication energy dissipation.However,this approach is not always energy efficient for image-based applications.Centralized image compression which is used at the source nodes may sometimes limit the lifetime of the network.In this paper,we present a low-complexity and energy efficient image compression scheme that is suitable for re-source-constrained wireless sensor networks.The key fea-tures of this proposed scheme are:Lapped biorthogonal transform(LBT)is used in image compression instead of discrete cosine transform(DCT) or discrete wavelet transform(DWT).Compared with the DCT-based methods,the proposed algorithm improves coding efficiency by taking into account inter-block spatial correlation and solves the problem of block-ing pared with the DWT-based ones,the proposed algorithm greatly lowers the complexity of computation and reduces the required memory,while it still achieves required peak signal-to-noise ratio (PSNR).What is more,it is very suitable for distributed implementation in the sensor network.Golomb+Multiple Quantization(MQ)coders are used in image compression instead of Huffman coding or arithmetic coding,so the computational complexity is significantly reduced.Further,the memory requirement is minimized because the proposed algorithm doses not require any statistical table or list when coding.A distributed implementation scheme of the LBT-basedimage compression algorithm is proposed based on a clustering architecture.It overcomes the computation and energy limitation of individual nodes by sharing the processing of tasks.Both computational and com-munication energy consumption are considered.This greatly prolongs the lifetime of the wireless sensor net-work under a specific image quality requirement.The rest of the paper is organized as follows.In Section 2,we briefly review related work.The algorithm of LBT and its corresponding encoding method is introduced in Sec-tion3.Section4proposes the distributed implementation scheme of the LBT-based image compression algorithm. Simulations of proposed compression algorithm and implementation scheme are presented in Section5.We conclude the paper in Section6.2.Related workTo our knowledge,low-complexity and energy efficient compression schemes for single image in wireless sensor networks have not been studied in the literature.However, our work has been inspired by a variety of related research efforts.We describe some of the ideas and basic concepts below.Nowadays transform-based methods are still the most popular lossy image compression methods which mainly involve DCT-based methods and DWT-based ones.DCT-based methods have many fast algorithms with low-com-plexity and low-memory but often cause boring blocking artifacts in low bit rate.DWT overcomes this innately for its ability to keep track of time and frequency simulta-neously and represent local features better.JPEG2000is a representative DWT-based compression method.It is not appropriate for WSNs because its transform(CDF9/7)and coding process(EBCOT)are both of high computational complexity and need much memory.To overcome the problems of DWT,Chrysafis and Zhang presented line-based wavelet transform[5]and strip-based wavelet transform[6]separately.The memory needed in these two algorithms is only related with the level of transform and the width of the image but not the height.However, the wavelet coefficients used in[5,6]are stillfloating point numbers and the computation is not reduced.If we substi-tute CDF9/7with binary wavelet transform[7]which needs less computation,the PSNR of compressed image will decrease about1dB.In resourced-constrained WSNs,Huaming Wu et al.no-ticed the high energy consumption of JPEG2000first[7]. They distributed the workload of wavelet transform to sev-eral groups of nodes along the path from the source to the destination by using the concept of parallel distributed computing theory.Our work is inspired by this idea.How-ever,it is worth noting that JPEG2000is not suitable for distributed implementation in the sensor network because the processing of tiles independently leads to a rate-distor-tion loss and blocking artifacts as the number of tiles in-creases or bit rate lowers.Wefind that the lapped biorthogonal transform(LBT) [8]can solve the problems above.LBT is improved DCT, and costs about half of computation of CDF9/7wavelet and needs only1/15of the memory.Moreover,LBT has the following advantages.(1)In analysis process,the corre-lation between adjacent blocks is substantially reduced,so the energy of the image is concentrated better.(2)In the synthesis process,thefilter functions of LBT decay smoothly to zero at their boundaries,which can reduce the block effect efficiently.(3)It is suitable for the distrib-uted implementation in the WSN.In the quest for higher compression efficiency,arithme-tic coding has been applied to DCT and DWT.There are sev-eral representatives of such state-of-the-art coders,such as EZDCT[9],EZW[10],SPIHT[11]and EBCOT[12].These coders provide very high compression efficiency.TheQ.Lu et al./Computer Networks52(2008)2594–26032595disadvantage of these coders is higher computational com-plexity and additional memory requirement.The work in [13]proposed a low-complexity and low-memory entropy coder which combined zerotree coding with quantization. All quantization steps are completed before the zerotree coding and no list is needed.A Golomb codec is used when coding the quantized coefficients.As we know,the distri-bution of quantized coefficients of LBT is similar to DWTs. Therefore,the coder used in the proposed image compres-sion algorithm is similar to the coder in[13].Here,it should be pointed out that categorizing is performed after the zerotree coding,and the ability of coding the coeffi-cients of zerotree codec is neglected in[13].In practice, the signal put into the Golomb codec does not follow a geo-metric distribution well.Therefore,we apply an MQ codec after the Golomb codec for further coding.In our previous work,we have used this LBT-based algo-rithm in the image compression device for satellite which is also strictly restricted in space,CPU memory resources and energy consumption[14].The design of the algorithm and its implementation scheme in WSNs has not been studied before.3.Image compression algorithm based on LBTIn WSNs,we need an image compression method with low complexity as well as good image pped bior-thogonal transform(LBT)is a good candidate for this requirement.In this section,we present a lifting-based fast binary algorithm of LBT and a low-complexity zerotree coding method.3.1.Lifting-based fast binary algorithm of LBTThrough a series of elementary matrix manipulations,a large class of lapped transform(LT)can be constructed as the pre-processing of DCT inputs in the time domain or the post-processing of DCT coefficients in the frequency domain[15].Both classes of algorithms share one common goal:to eliminate or reduce the severity of coding artifacts in the reconstructed signal.By analyzing the structures of these two classes of algorithms,we use time-domain pre-processing of DCT in this paper which is attractive for the distributed implementation in WSNs.The structure is de-picted in Fig.1a.Fast LT can be constructed in polyphase form from com-ponents with a fast algorithm for DCT.The analysis poly-phase matrix of type-II fast lapped orthogonal transform (LOT)[16]can be written as:E IIðzÞ¼D M C IIMI00zI0II0P;ð1ÞwhereP¼1I JJÀII00VI JJÀIV¼JðC IIM=2ÞT C IVM=2JD M¼diag1;À1;1;À1;...f g:ð2ÞThe matrix V controls pre-filtering and contains all of the degrees of freedom in the structure.By inserting aninvertible diagonal matrix S betweenðC IIM=2ÞT and C IVM=2,V can be represented in the single-value decomposition form:V¼JC IIM=2T SC IVM=2J;ð3ÞS is limited to diag f s;1;...;1g,where s is a scaling factor.A good value of s for a smooth image model is8=5which yields good biothogonal solutions.It is well known that a plane rotation can be decom-posed into three lifting steps.This can be written in matrix formas:Fig.1.Implementationflow of one-dimension binary. 2596Q.Lu et al./Computer Networks52(2008)2594–2603cos h Àsin h sin hcos h¼10tan h 21"#1Àsin h 0110tan h21"#:ð4ÞSo,we can replace each butterfly in the pre-filter P by theunnormalized Haar matrix asP ¼1I J 1J ÀI"#I 00VIJ 12J À12I "#:ð5ÞBecause the current consumption of the multiplyinstruction in DSPs is far greater than the current con-sumption of other instructions,a lifting scheme is used in the implementation of transform process.All coefficients are approximated by the fraction of integral numerator and dyadic denominator so only integer additions and shifts but no float multiplications are needed;this is called a binary transform and is quite suitable for hardware implementation.Fig.1b shows the structure of the binary LBT pre-processing.In our image compression algorithm,an eight-point type-II DCT [17]is used.The structure of the binary DCT-II is illustrated in Fig.1c.The computations needed by LBT,DCT and DWT (CDF9/7)are listed in Table 1.It is seen that the computation of binary LBT is 62%less than that of binary DWT,while its performance is better than that of binary DWT in the experiments,which will be shown in Section 5.3.2.Low-complexity zerotree codingSensor nodes in WSNs are limited in energy,memory and computational power.Therefore,besides high com-pression efficiency,the coders for image compression inwireless sensor networks should be of low complexity and low memory.The distribution of quantized coefficients of LBT is sim-ilar to DWT which has a zerotree structure.The zeortree structure of 8Â8LBT is illustrated in Fig.2.The element in every pane is a quantized coefficient of LBT.The energy of the coefficients,i.e.,the absolute value,decreases from top left corner to bottom right.Therefore,separating the entire block into 10sub bands by the solid lines,the LBT coefficients can be classified by the sub band that they be-long to and then coded separately.Denoting X as the quantized 8Â8blocks of coefficients,X ði ;j Þ;i ;j ¼0;...;7are the quantized coefficients.C ðX ði ;j ÞÞare the children of X ði ;j Þ,and D ðX ði ;j ÞÞare the descendants of X ði ;j Þexcept C ðX ði ;j ÞÞ.The detail steps of coding are given below:1.Code X ð0;0Þby Golomb +MQ codec;2.Code x ¼X ð0;0Þwith zerotree codec;2.1.If x has no children,end;2.2.If all the children of x is zero,output 0;Otherwise go to (2.3);2.3.Output 1,and code every children of x byGolomb +MQ codec;2.3.1.If all the coefficients in D ðx Þis 0,output 0;Otherwise go to (2.3.2);2.3.2.Output 1,and code the coefficients in C ðx Þwith zerotree codec separately.where the Golomb +MQ codec is Denote input as X ði ;j Þpute C ðX ði ;j ÞÞ¼N ;2N À1X ði ;j Þj j 2N ;2.Get the sub band B that X ði ;j Þbelongs to.Send ð0;B Þinto MQ codec N times and send ð1;B Þinto MQ codec one time;3.If X ði ;j Þis positive,output 1;Otherwise output 0;4.Output the lower C ðX ði ;j ÞÞÀ1bits of X ði ;j Þ.To reduce computation,the further compression of the position and sign information [18]is not considered here.In this improved zerotree coding algorithm,all quantizationisFig.2.Zerotree structure of 8Â8LBT quantized coefficients.Table 1Computation cost per bitFloat DCTFloat CDF9/7Binary DCT Binary CDF9/7Binary LBT Integer+007.7534.113Integer shift 00 3.523.6 6.7Float+7.2510.5000Float Â3.257.9Q.Lu et al./Computer Networks 52(2008)2594–26032597completed before zerotree coding and no list is needed.Thus it needs little memory and is straightforward for both soft-ware and hardware implementation.Here,we call it LZC. 4.Image compression schemeThe goal of presenting a low-complexity and low-mem-ory image compression algorithm based on LBT is to realize the image compression scheme in resource-constrained WSNs.We now propose a distributed implementation scheme of this image compression algorithm.4.1.System modelIn our study,we use the wireless communication en-ergy model proposed in[19].The energy consumed in transmission per bit isE TX¼E elecþe fs d2;d<d0E elecþe mp d4;d P d0(ð6Þand the energy consumed in reception per bit isE RX¼E elec;ð7Þwhere E elec is the energy consumed by the circuit per bit,d is the distance between the wireless transmitter and the receiver,and e fs d2or e mp d4is the amplifier energy that de-pends on the transmitter amplifier model.The energy consumed in image compression per bit is E cp¼2ðE preþE DCTÞþE code;ð8Þwhere E pre is the energy dissipated for one-dimensional bin-ary LBT pre-processing.E DCT is the energy dissipated for one-dimensional binary DCT.E code is the energy spent in coding.Noting r as the compression ratio,then if E cpþE TX= r>E TX,it’s better for the camera sensor to send the raw data directly than to compress it before sending.work structureAs each sensor node is power-constrained,the lifetime of WSNs is limited.Efficiently organizing sensor nodes into clusters is useful in reducing energy consumption.We con-sider the image compression scheme in the clustered wire-less sensor network because clustering allows for scalability of MAC and routing.What is more,cluster heads can serve as fusion points for the aggregation of data,so that the amount of data that is actually transmitted to the base station is reduced.Although data aggregation is not discussed in this paper,it should be considered when we design the image compression scheme.A typical cluster-based method is LEACH[20].In LEACH, the entire network is divided into non-overlapping clus-ters.There is a cluster head among each cluster.Instead of transmitting the data to the base station directly,the sensors send their data to the cluster head which relays the data to the global base station.Many LEACH-like algo-rithms,such as DEEC[21]and LEACH-B[22],have recently been proposed to improve the performance of LEACH re-cently.In DEEC,the cluster heads are elected by a probabil-ity based on the radio between the residual energy of each node and the average of the network.Because we are not aiming at the performance of the clustering schemes,the proposed scheme is designed based on LEACH in this paper.Two types of nodes with different functionality are used.One is the camera node;the other is the scalar sen-sor.The nodes are assumed to have power control features so as to adjust their transmit power.By using LEACH,all the nodes commonly run in a single hop homogeneous network(Fig.3left).The cluster-head role is rotated ran-domly and periodically to distribute the energy consump-tion evenly among all sensors in the network.The camera nodes should adjust their transmit power to communicate with the cluster head.If the cluster head is far from the camera node,the communication energy consumption will be high.Hence,this architecture is not energy efficient for the camera nodes.To prolong the lifetime of the network,both computa-tional and communication energy consumption should be considered.To reduce communication energy of the cam-era nodes,we propose an architecture in which the camera node does not take part in the clustering process.It adjusts its transmission range only to keep its neighborsnearlyFig.3.(Left)all the nodes commonly run in a single hop homogeneous network;(right)the camera node does not take part in the cluster and adjusts transmission range only to keep its neighbors nearly constant.2598Q.Lu et al./Computer Networks52(2008)2594–2603constant during the cluster head selection phase and trans-mits data to the neighbors during the steady-state phase. Thus,the communication energy consumption of the cam-era node is minimized.4.3.Partition schemeThe purpose of distributed implementation of the image compression algorithm is to reduce the burden ofenergy Fig.4.(a)Normal row-to-column computing scheme;(b)proposed partition scheme for distributed implementation inWSNs.Fig.5.Distributed implementation of LBT-based image compression algorithm in a cluster.Q.Lu et al./Computer Networks52(2008)2594–26032599consumption in the camera sensor and maximize the net-work lifetime.Therefore,we propose a partition scheme of the image compression algorithm which is different from the row-to-column way in normal parallel distributed computing(Fig.4a).The scheme is illustrated in Fig.4b.First,12rows data are read into the buffer and the back8rows do the LBT pre-processing on all columns.Second,the former8rows do DCT on all columns.Third,the former8rows do the LBT pre-processing and DCT on all rows.Once the former 8rows complete their2D LBT,they can be coded in8Â8 blocks and sent out directly.Then the buffer reads the next 8rows in and repeats the same process with the4rows left.In this partition scheme,only12W(image width)pixels need to be buffered at one time.It can be seen that the processes4,2,and5all deal with the former8rows until the compression of the8rows data complete.So these tasks can be distributed to other nodes in the cluster.4.4.Distributed image compressionDistributed implementation of the LBT-based image compression algorithm in a cluster is shown in Fig.5.When the camera node takes a picture,it should send it to the cluster head.During the transmission,the image is com-pressed.The compression scheme follows the steps below: Step1:The camera node announces this message to one of its neighbors S.Step2:S sends a request to the head in its cluster.Step3:The cluster head chooses some idle nodes ðP1ÀP4Þin the cluster which have the energyabove a threshold and send an OK message backto S.Step4:S sends an OK message back to the camera node.Table2The PSNR of different algorithms(dB)Rate (bpp)BinaryLBT+LZCBinaryDCT+LZCBinaryDWT+LZCFloat CDF9/7+SPIHT138.7838.1538.6339.380.536.1335.4136.0536.200.2533.0832.2932.9633.12pression of Lena image.2600Q.Lu et al./Computer Networks52(2008)2594–2603Step5:The camera node sends8rows data(12rows data in thefirst time)to S.S does the process3andsends the former8rows to a chosen node P whichis now idle.Then S goes to Step4.Step6:Each chosennode P does the processes4,2,and5, and sends the compressed data to the Cluster head.The time of doing step6is much more than the time of doing step5,hence the compression scheme needs many Ps to compute at the same time.In this scheme,12W pixels need to be buffered in the processor of S and8W pixels need to be buffered at each processor P.While in5-level decomposition with CDF9/7, even if the line-based transform method is used,about ð25þ1þ2À5À3ÞÂ3W%183W pixels must be buffered. The buffer that LBT needs is only1/15of that of the DWT.5.Performance evaluationThis section compares the performance of the proposed image compression algorithm with other image compres-sion algorithms with respect to two metrics:image quality and the network lifetime.5.1.Image qualityIn this analysis we focus on the performance of not only the algorithm itself but also its distributed implementation in WSNs.The image Lena of size512Â512pixels with8 bits per pixel is used in this evaluation.To evaluate the performance of the proposed image compression algorithm,we compare four algorithms:the proposed one,binary DCT+LZC,5-level binary DWT+ LZC and5-level Float CDF9/7+SPIHT.Table2gives the PSNR of these algorithms.It can be observed that binary LBT outperforms binary DCT.And the PSNR of recon-structed image compressed by the binary LBT-based algo-rithm is higher than the binary DWT-based one. Compared with Float CDF9/7+SPIHT,the binary LBT-based algorithm is also competitive.Because of using a binary transform and low-complexity coding algorithm,the PSNR decreased0.24dB on the average.In the case of distributed implementation in WSNs, nodes are extremely limited in memory.Therefore we compare the LBT-based distributed method with the dis-tributed JPEG2000method in[7]under the same memory requirement condition.In the proposed LBT-based distrib-uted method,8Â512pixels of the image is processed by the nodes at a time.In the distributed JPEG2000method, the image is partitioned into tiles,and then each tile is sent to a node to do JPEG2000algorithm independently.To let the image size processed by one node be equal for these two methods,here we consider the distributed JPEG2000 method with64Â64pixels tile.Fig.6shows the image quality with0.1bits per pixel(bpp)and0.25bpp bit rates. We can see that the image quality of the LBT-based method is much better than the distributed JPEG2000one when the bit rate is low.work lifetimeIn this section,we evaluate the performance of the pro-posed distributed image compression scheme using MAT-LAB.We consider seven sensor networks with N¼25;50; 100;250;400;625or900nodes randomly distributed over a500mÂ500mfield.We choose the node which is clos-est to the center of thefield as the camera node.The coor-dinate of the base station is(0,0).Each node is initially given10J of energy.LEACH is used in the simulation and here P opt¼0:1.Fig.7.System lifetime of the three schemes.Q.Lu et al./Computer Networks52(2008)2594–26032601The values of the energy model parameters are chosen as follows:the values of the parameters of the wireless com-munication energy model in (6)and (7)are the typical val-ues E elec ¼50nJ =bit,e fs ¼10pJ =bit =m 2,e mp ¼0:0013pJ =bit =m 4and d 0¼87m.The energy consumption of the pro-posed image compression algorithm is evaluated in a StrongARM SA1100processor.The experiment is done on the test image Lena of size 512Â512pixels with 8bits per pixel.The bit rate is 0.25bpp.From the experiment,the val-ues of the parameters of the computation energy model are E pre ¼15nJ =bit,E DCT ¼20nJ =bit and E code ¼90nJ =bit.To evaluate the performance of our proposed scheme,we compare the following three schemes:Scheme (A):The camera node acts as a member of the nearest cluster and compresses the images before send-ing them to the cluster head.Scheme (B):The camera node acts as a member of the nearest cluster and sends the raw images to the cluster head.Then the cluster head compresses the images and sends the compressed data to the base station.Scheme (C):The proposed distributed image compres-sion scheme in the proposed network architecture.We first let the camera node adjust its transmission range to keep one neighbor alive in its communication ra-dius at the beginning of each round.Five images are in-tended to be sent out during every steady-state phase.The simulation is stopped if the camera node depletes its energy.The system lifetime is measured by the number of images which are successfully received by the base sta-tion.Fig.7shows the system lifetime of the three schemes.It is observed that the proposed scheme results in a much longer lifetime since the camera node shares the computa-tional workload with other nodes and adjusts its transmis-sion range to save communication energy consumption.In the design of WSNs both energy efficiency and QoS support should be considered.In the proposed scheme,we can let the camera node adjust its transmission range to keep more than one neighbor alive in its communication radius.The cluster head is in charge of measuring the en-ergy and data loss probability of its cluster.And the camera node chooses the best cluster to process the distributed image compression scheme according to the message from the cluster head.Here,we let the camera node choose the cluster according to the residual energy of the cluster head.Fig.8shows the system lifetime of the proposed scheme when the camera node keeps M =1,2or 3neighbors with-in its communication radius.It is observed that in the net-work with a high node density the proposed scheme performs well when the camera node increases its trans-mission range to keep more neighbors alive in its commu-nication radius.6.ConclusionsWe have studied the problem of image compression algorithm and its implementation scheme in WSNs.The de-sign and evaluation of a low complexity and energy efficient image compression scheme is presented.A LBT-based low complexity and low memory image compression algorithm is used.It greatly reduces the hardware cost and the energy consumption of the sensor network.To prolong the lifetime of the network,both computational and communication energy consumption are considered in the implementation scheme.Our technique shares the task of image compres-sion algorithm with several nodes and applies transmis-sion range adjustment to save communication energy dissipation.The proposed scheme is simple to implement.Performance evaluation shows that our technique greatly prolongs the lifetime of the wireless sensor network under a specific image qualityrequirement.Fig.8.System lifetime of the proposed scheme.2602Q.Lu et al./Computer Networks 52(2008)2594–2603。
