5 ADTs and Haskell
湛江2024年09版小学四年级下册第5次英语第四单元真题(含答案)

湛江2024年09版小学四年级下册英语第四单元真题(含答案)考试时间:100分钟(总分:120)A卷考试人:_________题号一二三四五总分得分一、综合题(共计100题)1、听力题:He is very ___. (talented)2、What do you need to write on paper?A. EraserB. PencilC. ScissorsD. Tape答案:B3、填空题:I have a strong bond with my ____.4、听力题:She is _______ (running) in the race.5、听力题:__________ are used in lubricants for machinery.6、What do you call a person who repairs computers?A. TechnicianB. EngineerC. BuilderD. Designer答案:A7、What is the name of the vast region containing thousands of galaxies?A. SuperclusterB. Galaxy ClusterC. NebulaD. Cosmic Web8、Which fruit is yellow and curved?A. AppleB. BananaC. OrangeD. Grape9、填空题:My grandpa loves to watch ____.10、填空题:This ________ (玩具) helps improve my skills.11、Which shape has four equal sides?A. RectangleB. TriangleC. SquareD. Circle12、What is the name of the famous detective created by Arthur Conan Doyle?A. Hercule PoirotB. Sherlock HolmesC. Miss MarpleD. Sam Spade13、填空题:My ___ (小马) loves to run fast.14、填空题:The _______ (小蟋蟀) chirps at night to attract a mate.15、填空题:My cousin loves to __________ (唱歌) at family gatherings.16、填空题:Certain flowers require ______ (特别的护理).17、What is the opposite of "fast"?A. QuickB. SlowC. SpeedyD. Hasty答案:B18、听力题:My brother is very ________.I enjoy cooking dinner with my ______ (家人). We try new recipes and enjoy delicious meals together.20、填空题:The _____ (小羊) loves to run and play.21、听力题:The teacher gives us ______ to study. (papers)22、填空题:A _____ (金丝雀) sings beautifully.23、听力题:Water is a ______ solvent.24、听力题:Animals that live in the Arctic are adapted to ______ weather.25、选择题:What do you call the person who helps you learn in school?A. DoctorB. TeacherC. CookD. Driver26、 Panther Party was founded to combat ________ (种族不平等). 填空题:The Bost27、What is the name of the popular animated series about a family of superheroes?A. The IncrediblesB. The SimpsonsC. Family GuyD. Avatar答案: A28、听力题:A catalyst lowers the ______ of a reaction.29、What is the name of the famous American actress known for "Legally Blonde"?A. Reese WitherspoonB. Jennifer AnistonC. Cameron DiazD. Kate Hudson答案:AI like to explore the ______.31、听力题:I want to _______ (travel) the world.32、听力题:A ____ is known for its hopping and is often found in gardens.33、填空题:Let’s build a __________ (名词) with our __________ (玩具名)!34、听力题:The chemical process that breaks down food in our bodies is called ______.35、填空题:The _____ (果树) is full of apples.36、What is the name of the famous bear in children's literature?A. Winnie the PoohB. Paddington BearC. Yogi BearD. Baloo37、填空题:I enjoy going ________ (滑冰) during winter.38、填空题:My uncle, ______ (我的叔叔), is a skilled carpenter.39、What do we call the bright display of lights seen in the northern sky?A. Aurora BorealisB. Northern LightsC. Southern LightsD. Star Shower答案: A. Aurora Borealis40、What is the name of the first artificial satellite?A. Vanguard 1B. Explorer 1C. Sputnik 1D. Luna 141、Which planet is known as the blue planet?A. MarsB. JupiterC. EarthD. Saturn答案: C42、听力题:My birthday is in ______ (July).43、填空题:The rabbit hops around the _________. (花园)44、填空题:The kangaroo can jump over _______ (障碍物).45、听力题:Chemical reactions often require a change in ________ to occur.46、What is the name of the famous giant structure in Egypt?A. ColosseumB. Great WallC. PyramidsD. Parthenon答案: C47、听力题:The __________ is the solid outer section of the earth.48、听力题:I love to ________ my family.49、What is the name of the famous clock tower in London?A. Big BenB. Eiffel TowerC. Leaning TowerD. Statue of Liberty答案:A50、What is the capital of the Seychelles?a. Victoriab. Mahéc. Praslind. La Digue答案:a51、听力题:My dad is a ________.52、听力题:The process of removing electrons from an atom is called ______.53、填空题:The _____ (可食用植物) are often sought after in markets.54、Which day comes after Monday?A. SundayB. TuesdayC. WednesdayD. Thursday55、听力题:Some stars are much _____ than the sun.56、听力题:A process that absorbs heat is called an ______ process.57、填空题:We have a ______ (丰富的) resource center.58、填空题:The ________ (树林) is home to many animals and plants.59、填空题:My friends and I often joke with each other and call each other __.(我的朋友和我常常开玩笑,相互称呼为。
小学下册第1次英语第二单元寒假试卷[含答案]
![小学下册第1次英语第二单元寒假试卷[含答案]](https://img.taocdn.com/s3/m/53fba1929f3143323968011ca300a6c30c22f1be.png)
小学下册英语第二单元寒假试卷[含答案]英语试题一、综合题(本题有100小题,每小题1分,共100分.每小题不选、错误,均不给分)1.What is the largest land animal?A. RhinoB. HippoC. GiraffeD. Elephant答案:D2.My favorite sport is ________.3.I enjoy playing ________ (运动) with my teammates.4.What do we call a person who performs surgeries?A. NurseB. SurgeonC. DoctorD. Physician5.I saw a _______ (小虫子) on the ground.6.The __________ is a famous area known for its historical significance.7.The _____ (mountain) is snowy.8.The stars twinkle _______ (在夜空中).9.The Pacific Plate is the largest ______ plate on Earth.10.The ________ was a notable figure in the fight against discrimination.11.The ______ (青蛙) can change color depending on its environment.12.The ______ is a type of fish that lives in coral reefs.13.My aunt is like a kind _______ who cares for me.14.The __________ is a famous river in China.15.What do we call a person who studies climate?A. ClimatologistB. MeteorologistC. Environmental ScientistD. Ecologist答案:A16. A ____ is a small animal that loves to scamper around.17.What is the opposite of "day"?A. NightB. NoonC. AfternoonD. Morning18.What kind of animal is a dolphin?A. FishB. MammalC. ReptileD. Amphibian答案:B19.The _____ (zookeeper) cares for the animals.20.Planting _____ (景观植物) enhances outdoor aesthetics.21.The crab has a hard _________. (外壳)22.__________ are used in the production of pharmaceuticals.23.What do we call the natural satellite that orbits the Earth?A. SunB. MoonC. StarD. Planet答案:B24._____ (天然植物) have various uses in everyday life.25. A _____ (小狼) howls at the moon.26.What is the opposite of ‘hard’?A. SolidB. RoughC. SoftD. Tough27.I enjoy _______ in the park.28.I enjoy hiking to see beautiful ______ (风景) and wildlife.29.I enjoy going ________ (跑步) in the morning.30.What do you call the first book in the Bible?A. ExodusB. GenesisC. RevelationD. Psalms答案:B31. A hedgehog rolls into a ______ (球) for protection.32.What do we call the act of telling a story?A. NarrationB. RecitationC. PerformanceD. Presentation33.What do you use to listen to music?A. RadioB. TVC. ComputerD. All of the above答案:D34.My sister sings like a ________.35.The _____ (遥控飞机) flies high in the sky.36.I like to listen to audiobooks while I ________ (散步) in the park.37.I want to ______ a new toy. (buy)38.What do we call a place where you can see wild animals?A. ZooB. AquariumC. FarmD. Circus答案:A39.The antelope runs very _________. (快)40.The chemical formula for strontium chloride is _____.41.What is the process of changing from a liquid to a solid called?A. FreezingB. BoilingC. MeltingD. Evaporating答案:A42.What is the name of the famous artist who painted the Mona Lisa?A. PicassoB. Van GoghC. Da VinciD. Michelangelo43.What is the main ingredient in guacamole?A. TomatoB. AvocadoC. OnionD. Pepper答案:B44.What color do you get by mixing red and white?A. PinkB. PurpleC. OrangeD. Brown答案:A45. A chemical bond that involves sharing electrons is a _____ bond.46.Space is a vacuum, which means it has no ______.47.My dad is known for his __________ (智慧).48.My favorite color for my toy is _____.49.I can ______ (保持) a positive outlook.50.What is the tallest mountain in the world?A. K2B. Mount EverestC. KilimanjaroD. Denali答案:B51.The store opens _____ (early/late) in the morning.52.What is the name of the tool used to measure temperature?A. BarometerB. ThermometerC. SpeedometerD. Altimeter答案:B53.The rabbit has sharp _______ (牙齿) for chewing.54.He is a good _______ (学生).55.I enjoy _______ my favorite songs.56.I enjoy _______ (看电视) with my family.57.What do we call the process of converting food into energy in living organisms?A. DigestionB. MetabolismC. AbsorptionD. Respiration58.The _____ (orchids) are known for their beauty.59.I like to ______ after school. (relax)60.Which fruit is yellow and curved?A. AppleB. BananaC. OrangeD. Grape61.We have a ______ (有趣的) discussion in class.62.My friend is very _______ (形容词) when it comes to math. 她总是 _______ (动词).63.My dad is a __________ (商业顾问).64.My favorite sport is _____. (soccer)65.The __________ (历史的启发) ignites curiosity.66.biome) of the tundra is characterized by permafrost. The ____67.Lizards like to bask in the ______ (阳光).68.My aunt enjoys baking ____ (pies).69.The __________ (植物的习性) is fascinating to study.70.What is the term for a baby dog?A. KittenB. PuppyC. CalfD. Cub答案:B71.The _______ can survive in extreme conditions.72.What do we call a series of steps to solve a problem?A. StrategyB. PlanC. MethodD. Equation答案:A73.What is the opposite of ‘happy’?A. SadB. ExcitedC. AngryD. Joyful74. A __________ is a narrow body of water between two landmasses.75.The country of Kenya is famous for its ________ (肯尼亚以其________而闻名).76.The ______ helps maintain the balance of nature.77.My friend has a __________ (宠物) cat that loves to play.78.What do you call a small animal that has a shell?A. SnailB. FrogC. MouseD. Lizard答案:A79.What is the hottest planet in our solar system?A. MercuryB. VenusC. MarsD. Jupiter80.The _____ (咖啡) is brewed fresh.81.What is the name of the region of space that contains the asteroid belt?A. Kuiper BeltB. Oort CloudC. Asteroid BeltD. Heliosphere82.The chemical symbol for titanium is ______.83.What is the capital of Zambia?A. LusakaB. HarareC. NairobiD. Kampala答案:A84.Reptiles lay ______.85.What do you call a group of lions?A. PackB. PodC. PrideD. Flock86.__________ are used in the production of explosives.87.The chemical formula for iron (III) oxide is _______.88.How many hours are in a day?A. 24B. 12C. 36D. 48答案:A89.What color is a typical school bus?A. BlueB. RedC. YellowD. Green答案:C90.I want to learn how to ________ (弹钢琴).91.Which insect makes a web?A. AntB. BeeC. SpiderD. Fly答案:C92.My best friend's dad is a _______ (职业). 他在 _______ (地点)工作.93.My birthday is in ___. (July, cold, happy)94.What is the opposite of ‘full’?A. EmptyB. PackedC. CompleteD. Whole95.What do we call a shape with four equal sides?A. RectangleB. SquareC. TriangleD. Pentagon96. A _______ is a visual representation of a chemical reaction.97.The _______ can provide shelter for many animals.98.She is _____ (coloring/drawing) a picture.99.I enjoy writing poetry because it’s a unique way to convey my __________. 100.I want to _____ (visit) historical sites.。
Honeywell STT850智能温度传感器选型指南说明书
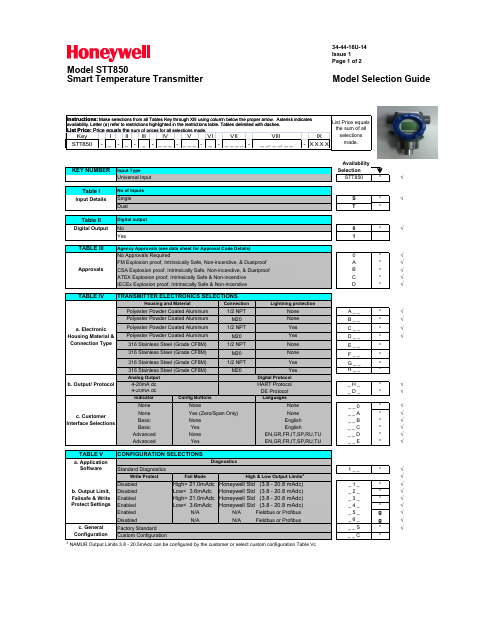
34-44-16U-14Issue 1Page 1 of 2Model STT850Smart Temperature TransmitterModel Selection GuideAvailability KEY NUMBERInput TypeSelection Universal InputSTT850*√Table IInput DetailsS *√T *Table IIDigital outputDigital OutputNo 0*√Yes1TABLE III0*√FM Explosion proof, Intrinsically Safe, Non-incendive, & Dustproof A *√CSA Explosion proof, Intrinsically Safe, Non-incendive, & Dustproof B *√ATEX Explosion proof, Intrinsically Safe & Non-incendive C *√IECEx Explosion proof, Intrinsically Safe & Non-incendive D *√TABLE IV Connection1/2 NPT A _ _*√M20 B _ _*√1/2 NPT C _ _*√M20 D _ _*√1/2 NPT E _ _*M20 F _ _*1/2 NPT G _ _*M20H _ _*Analog Output4-20mA dc _ H _*√4-20mA dc_ D _*√IndicatorExt Zero, Span & Config ButtonsLanguagesNone None_ _ 0*√None _ _ A *√Basic None _ _ B *√Basic Yes _ _ C *√Advanced None _ _ D *√Advanced Yes _ _ E*√TABLE V1 _ _*√Write ProtectFail Mode√Disabled High> 21.0mAdc Honeywell Std (3.8 - 20.8 mAdc)_ 1 _*√Disabled Low< 3.6mAdc Honeywell Std (3.8 - 20.8 mAdc)_ 2 _*√Enabled High> 21.0mAdc Honeywell Std (3.8 - 20.8 mAdc)_ 3 _*√Enabled Low< 3.6mAdcHoneywell Std (3.8 - 20.8 mAdc)_ 4 _*√Enabled N/A N/A _ 5 _g √DisabledN/AN/A_ 6 _g√Factory Standard _ _ S *√_ _ C*3NAMUR Output Limits 3.8 - 20.5mAdc can be configured by the customer or select custom configuration Table Vcc. General ConfigurationCustom ConfigurationCONFIGURATION SELECTIONSa. Application SoftwareDiagnosticsStandard Diagnosticsb. Output Limit, Failsafe & Write Protect SettingsHigh & Low Output Limits3Fieldbus or Profibus Fieldbus or Profibus EnglishEN,GR,FR,IT,SP,RU,TU EN,GR,FR,IT,SP,RU,TUb. Output/ ProtocolDigital ProtocolHART Protocol DE Protocolc. Customer Interface SelectionsNone Yes (Zero/Span Only)None English 316 Stainless Steel (Grade CF8M)None 316 Stainless Steel (Grade CF8M)Yes 316 Stainless Steel (Grade CF8M)YesNone Polyester Powder Coated Aluminum Yes Polyester Powder Coated Aluminum Yes 316 Stainless Steel (Grade CF8M)None Agency Approvals (see data sheet for Approval Code Details)ApprovalsNo Approvals RequiredTRANSMITTER ELECTRONICS SELECTIONSa. Electronic Housing Material & Connection TypeHousing and MaterialLightning protectionPolyester Powder Coated Aluminum None Polyester Powder Coated AluminumList Price equalsthe sum of all selections made. No of InputsSingle Dualavailability. Letter (a) refer to restrictions highlighted in the restrictions table. Tables delimited with dashes. Instructions: Make selections from all Tables Key through XIII using column below the proper arrow. Asterisk indicatesList Price: Price equals the s um of prices for all selections made.Key I II III IV V VI VII VIII IXSTT850-_ -_-_-_ _ _-_ _ _-_-_ _ _ _-_ _, _ _, _ _-X X X X34-44-16U-14Issue 1Page 2 of 2√√√√√√√√√√√√√√√。
track and trace

track and traceTrack and Trace: An Overview of the System and Its ImportanceIntroductionThe track and trace system is an essential tool used in various industries, including healthcare, logistics, and supply chain management. Its primary purpose is to monitor and manage the movement of goods, services, and personnel. This article provides an overview of the track and trace system, its components, and its importance in today's interconnected world.What is Track and Trace?Track and trace, also known as T&T, is a method used to identify and track the movement of a product or person throughout its journey. This system utilizes various technologies such as barcodes, RFID (Radio Frequency Identification), GPS (Global Positioning System), and IoT (Internet of Things) to track and monitor the item or individual in real-time.Components of Track and Trace System1. Identification: The first step in the track and trace system is to assign a unique identification code to the product or person. This code can be in the form of a barcode, QR code, or RFID tag. This code allows for easy identification and tracking throughout the supply chain.2. Data Capturing Devices: These devices are used to collect data at different stages of the product's journey. For example, in the healthcare industry, medication packaging may have a QR code that can be scanned by a healthcare professional to record the administration of the medication.3. Communication Networks: The collected data is transmitted through communication networks such as the internet, mobile networks, or radio waves. This allows for real-time tracking and monitoring.4. Data Management Systems: The collected data is stored and managed in databases or cloud-based systems. These systems enable easy access to information and facilitate data analysis for decision-making purposes.5. Tracking Applications: These applications allow authorized personnel to access real-time information about the location, status, and other relevant details of the tracked item. This helps in improving efficiency and reducing errors in various processes.Importance of Track and Trace System1. Supply Chain Management: The track and trace system plays a crucial role in supply chain management. It allows businesses to keep track of inventory levels, monitor the movement of goods, and identify bottlenecks in the supply chain. This helps in improving efficiency, reducing costs, and ensuring timely deliveries.2. Consumer Safety: In industries such as pharmaceuticals and food, the track and trace system ensures the safety of consumers. It allows for the rapid identification and recall of products in case of quality issues or safety concerns. This helps in protecting consumers and maintaining trust in the brand.3. Counterfeit Prevention: The track and trace system can help in the prevention of counterfeit products. By assigning unique identification codes and tracking their movement, businesses can ensure the authenticity of their products. This protects the brand's reputation and safeguards consumer interests.4. Regulatory Compliance: Many industries have regulatory requirements for tracking and tracing products. For example, in the healthcare sector, pharmaceutical companies need to comply with regulations that mandate the traceability of medications from manufacturing to distribution. The track and trace system enables businesses to meet these regulatory requirements efficiently.5. Supply Chain Visibility: The track and trace system provides visibility into the supply chain, allowing businesses to identify inefficiencies, optimize processes, and make data-driven decisions. This leads to improved overall performance and customer satisfaction.Use Cases of Track and Trace System1. Healthcare: In the healthcare sector, the track and trace system is crucial for medication management, medical devicetracking, and patient safety. It helps in reducing errors, ensuring compliance with regulations, and enhancing patient care.2. Logistics and Transportation: The track and trace system is widely used in logistics and transportation to monitor the movement of goods, manage delivery schedules, and optimize routes. This improves operational efficiency and customer satisfaction.3. E-commerce: In the e-commerce industry, the track and trace system allows customers to track their packages in real-time, providing transparency and peace of mind. It also enables businesses to streamline their fulfillment processes and manage inventory effectively.ConclusionThe track and trace system is a vital tool for industries worldwide. It enables efficient supply chain management, ensures consumer safety, prevents counterfeiting, ensures regulatory compliance, and provides supply chain visibility. With advancements in technology, the track and trace system is continuously evolving, offering more precise and real-time tracking capabilities. Embracing this system can bringsignificant benefits to businesses and enhance customer satisfaction in today's globalized and interconnected world.。
Hand-outNo.2[Sevenstandardsoftextuality]
![Hand-outNo.2[Sevenstandardsoftextuality]](https://img.taocdn.com/s3/m/9c5c201653ea551810a6f524ccbff121dd36c50b.png)
King Saud UniversityCollege of languages and TranslationText-linguistics for students of translationThe English ProgramHand-out No.2The Seven Standards of TextualityText has been defined as a communicative occurrence/event which meets seven standards of textuality (cohesion, coherence, intentionality, acceptability, informativity, situationality, and intertextuality). Linguists confirm that if any of these standards of textuality is not to have been satisfied, the text will not be communicative.1. CohesionThe first standard of textuality is called cohesion. Cohesion is the network of lexical, grammatical, and other relations that provide links between various parts of a text. These relations or ties organise a text by requiring the reader to interpret words and expressions by reference to other words and expressions in the surrounding sentences and paragraphs. Moreover, cohesion is seen as a non-structural semantic relation, as for example, between a pronoun and its antecedent in a preceding sentence, expressing at each stage in the discourse the point of context with what has gone before. A cohesive device is the interpretative link between, for example, a pronoun and its antecedent, or two lexically linked NPs, and a series of such ties (having the same referent) is referred to as a ‘cohesive chain’.Halliday and Hasan (1976) establish five cohesion categories: reference, substitution, ellipsis, conjunctions, and lexical cohesion. In clarifying the notion of‘cohesion’ and ‘cohesive device’, Halliday and Hasan (1976: 1) present the following examples:a. Wash and core six cooking apples. Put them into afireproof dish.b. My axe is blunt. I have to get a sharper one.c. Did you see John? - Yes Ø.d. They fought a battle. Afterwards, it snowed.Here, the two sentences, in each example, are linked to each other by a cohesive link; in each instance a different cohesive item is implemented. In example (a), the two sentences are linked by the pronoun ‘them’, in the second sentence, which refers anaphorically to the noun phrase ‘six cooking apples’, in the first sentence. In (b) this relation is established bythe presence of the substitute ‘one’ in the second sentence, which is a counter of the noun‘axe’ in the first sentence of the same example; in (c) the cohesive relation is achieved by the omission of some element in the second sentence that presupposes the first sentence. In example (d) none of the above relations exist; the conjunction or conjunctive adjunct‘afterwards’ is not an anaphoric relation like the previous ones; it does not instruct the reader to search for the meaning of the element to interpret it as in reference, or the replacement of some linguistic element by a counter or by a blank, as are substitution and ellipsis, “but a specification of the way in which what is to follow is systematically connected to what has gone before” (Halliday and Hasan, 1976: 227).As for the main cohesion category called lexical cohesion, Halliday and Hasan present the following examples:“There is a boy climbing the tree”a. The boy’s going to fall if he does not take care.b. The lad’s going to fall if he does not take care.c. The child’s going to fall if he does not take care.d. The idiot’s going to fall if he does not take care.In example (a), there is a repetition of the same lexical item: ‘boy’, in (b), the reiteration takes the form of a synonym or nearsynonym ‘lad’; in (c), of the superordinate the term ‘child’; and in (d), of a general word ‘idiot’.All these instances have in common the fact that one lexical item refers back to another, to which it is related by having a common referent.2. CoherenceLike cohesion, coherence is a network of relations which organise and create a text: cohesion is the network of surface relations which link words and expressions to other words and expressions in a text, and coherence is the network of conceptual relations which underlie the surface text. Both concern the way stretches of language are connected to each other. In the case of cohesion, stretches of language are connected to each other by virtueof lexical and grammatical dependencies. In the case of coherence, they are connected by virtue of conceptual or meaning dependencies as perceived by language users. Hoey (1991: 12) sums up the difference between cohesion and coherence as follows:"We will assume that cohesion is a property of the text andthat coherence is a facet [i.e. side] of the reader's evaluationof a text. In other words, cohesion is objective, capable inprinciple of automatic recognition, while coherence issubjective and judgements concerning it may vary fromreader to reader."We could say that cohesion is the surface expression of coherence relations, that it is a device for making conceptual relations explicit. For example, a conjunction such as'therefore' may express a conceptual notion of 'reason' or 'consequence'. However, if the reader cannot perceive an underlying semantic relation of 'reason' or 'consequence' between the propositions connected by 'therefore', he will not be able to make sense of the text in question; in other words, the text will not 'cohere' for this particular reader. Generally speaking, the mere presence of cohesive markers cannot create a coherent text; cohesive markers have to reflect conceptual relations which make sense. Enkvist (1978b: 110-11) gives an example of a highly cohesive text which is nevertheless incoherent:I bought a Ford. The car in which President Wilson rode down the Champs Elysees was black. Black English has been widely discussed. The discussions between the presidents ended last week. A week has seven days. Every day I feed my cat. Cats have four legs.The fact that we cannot make sense of stretches of language like the one quoted above, in spite of the presence of a number of cohesive markers, suggests that what actually gives texture to a stretch of language is not the presence of cohesive markers but our ability to recognise underlying semantic relations which establish continuity of sense. The main value of cohesive markers seems to be that they can be used to facilitate and possibly control the interpretation of underlying semantic relations.The coherence of a text is a result of the interaction between knowledge presented in the text and the reader's own knowledge and experience of the world, the latter being influenced by a variety of factors such as age, sex, race, nationality, education, occupation, and political and religious affiliations. Even a simple cohesive relation of co-reference cannot be recognised, and therefore cannot be said to contribute to the coherence of a text.Coherence can be illustrated by causality, as in: (A) Jack fell down and (B) he broke his crown. Here, (A) is the cause of (B).Coherence can be illustrated by enablement or reason, as in: Jack (A) spent two days working on the problem and he (B) found the solution. (A) enabled (B) or (A) is the reason that led to (B).While cohesion and coherence are to a large extent text-centred, intentionality is user-centred. A text-producer normally seeks to achieve a purpose or goal (e.g. persuasion, instruction, request, information, etc.) based on a given plan. Obviously, cohesion and coherence are taken into consideration while planning and executing one's plan. Speakers or writers vary in the degree of success in planning and achieving their purposes.4. AcceptabilityThe receiver's attitude is that a text is cohesive and coherent. The reader usually supplies information that is missing or unstated. Acceptability is very much sensitive to the social activity the text is fulfilling. A legal contract does not leave much room for inference. It contains what, otherwise, is called redundancies. Poetic language will be viewed as such because it calls on for inferences.Acceptability is very much affected by the reader's social and cultural background. The joke of the priest who, on shaving his beard in the morning cut his chin because he was thinking of the sermon he was about to give, and the advice his fellow priest gave him, "Cut your sermon and concentrate on your beard", was not very much appreciated by some students belonging to different culture.5. InformativityA text has to contain some new information. A text is informative if it transfers new information, or information that was unknown before. Informativity should be seen as a gradable phenomenon. The degree of informativity varies from participant to participant in the communicative event. Situationality contributes to the informativity of the text. A book written in 1950 has an informativity that was high appropriate then.6. SituationalityA text is relevant to a particular social or pragmatic context. Situationality is related to real time and place. Communicative partners as well as their attitudinal state are important for the text's meaning, purpose and intended effect. Scientific texts share a common situationality, while ideological texts have different situationalities across languages and cultures.The seventh standard of textuality is called intertextuality. A text is related to other texts. Intertextuality refers "to the relationship between a given text and other relevant texts encountered in prior experience." (Neubert and Shreve, 1992: 117). These include textual conventions and textual expectations. Some text features have become more and more international, e.g. medical texts. They exhibit many features that are English-like, even they are written in Arabic. There is a fine line between plagiarism and intertextuality.。
新外研版高中英语选择性必修第三册Unit 5课文翻译

Nature in Architecture建筑中的自然元素Trees, plants and flowers are all around us and we enjoy their beauty every day. In fact, we are so used to them that we even take them for granted without realising how much inspiration they have given us. When we look at a pine cone, we might think how much it looks like the tiles on a roof. An open flower might make us think how closely it resembles an umbrella. It is natural to think in this way, but of course it wasn't the umbrella that inspired the flower or the roof that inspired the pine cone.我们身边都有花、草、树木,并且每天都能欣赏到它们的美。
事实上,我们已经习惯了它们的存在,甚至可能把它们视为理所当然,却没有意识到它们给了我们多少灵感。
看到一个松果,我们可能会想它看起来多么像屋顶上的瓦片;看到一朵绽开的花,我们可能会觉得它和雨伞是多么相似。
以这种方式思考是很自然的,但当然不是雨伞给了花朵灵感,也不是屋顶给了松果灵感。
Nature has inspired many of the most fascinating designs around us, including those in architecture. From Barcelona’s forest-like Sagrada Familia to the modern style of Beijing’s Water Cube,nature is presented in various architectural designs. Today,architects continue to explore ways to capture the beauty of natural forms to mimic the way nature works or even to make natural organisms part of a building.我们身边许多最迷人的设计,包括建筑设计,它们的灵感都来自大自然。
Cats(1)- 从Free开始,Free cats
Cats(1)-从Free开始,Free catscats是scala的一个新的函数式编程工具库,其设计原理基本继承了scalaz:大家都是haskell typeclass的scala版实现。
当然,cats在scalaz的基础上从实现细节、库组织结构和调用方式上进行了一些优化,所以对用户来说:cats的基础数据类型、数据结构在功能上与scalaz是大致相同的,可能有一些语法上的变化。
与scalaz著名抽象、复杂的语法表现形式相比,cats的语法可能更形象、简单直白。
在scalaz的学习过程中,我们了解到所谓函数式编程就是monadic Programming:即用monad这样的数据类型来构建程序。
而实际可行的monadic programming就是用Free-Monad编程了。
因为Free-Monad程序是真正可运行的,或者说是可以实现安全运行的,因为它可以保证在固定的堆栈内实现无限运算。
我们知道:函数式编程模式的运行方式以递归算法为主,flatMap函数本身就是一种递归算法。
这就预示着monadic programming很容易造成堆栈溢出问题(StackOverflowError)。
当我们把普通的泛函类型F[A]升格成Free-Monad后就能充分利用Free-Monad安全运算能力来构建实际可运行的程序了。
由于我们在前面已经详细的了解了scalaz的大部分typeclass,包括Free,对cats的讨论就从Free开始,聚焦在cats.Free 编程模式方面。
同时,我们可以在使用cats.Free的过程中对cats的其它数据类型进行补充了解。
cats.Free的类型款式如下:sealed abstract class Free[S[_], A] extends Product with Serializable {...}S是个高阶类,就是一种函数式运算。
值得注意的是:现在S不需要是个Functor了。
the history of haskell
A History of Haskell: Being Lazy With ClassApril16,2007Paul HudakYale University paul.hudak@John HughesChalmers Universityrjmh@cs.chalmers.seSimon Peyton JonesMicrosoft Researchsimonpj@ Philip WadlerUniversity of Edinburghwadler@AbstractThis paper describes the history of Haskell,including its genesis and principles,technical contributions,implementations and tools, and applications and impact.1.IntroductionIn September of1987a meeting was held at the confer-ence on Functional Programming Languages and ComputerArchitecture in Portland,Oregon,to discuss an unfortunatesituation in the functional programming community:therehad come into being more than a dozen non-strict,purelyfunctional programming languages,all similar in expressivepower and semantic underpinnings.There was a strong con-sensus at this meeting that more widespread use of this classof functional languages was being hampered by the lack ofa common language.It was decided that a committee shouldbe formed to design such a language,providing faster com-munication of new ideas,a stable foundation for real ap-plications development,and a vehicle through which otherswould be encouraged to use functional languages.These opening words in the Preface of thefirst Haskell Report, Version1.0dated1April1990,say quite a bit about the history of Haskell.They establish the motivation for designing Haskell(the need for a common language),the nature of the language to be designed(non-strict,purely functional),and the process by which it was to be designed(by committee).Part I of this paper describes genesis and principles:how Haskell came to be.We describe the developments leading up to Haskell and its early history(Section2)and the processes and principles that guided its evolution(Section3).Part II describes Haskell’s technical contributions:what Haskell is. We pay particular attention to aspects of the language and its evo-Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on thefirst page.To copy otherwise,to republish,to post on servers or to redistribute to lists,requires prior specific permission and/or a fee.Third ACM SIGPLAN History of Programming Languages Conference(HOPL-III) San Diego,CACopyright c 2007ACM...$5.00lution that are distinctive in themselves,or that developed in un-expected or surprising ways.We reflect onfive areas:syntax(Sec-tion4);algebraic data types(Section5);the type system,and type classes in particular(Section6);monads and input/output(Sec-tion7);and support for programming in the large,such as modules and packages,and the foreign-function interface(Section8).Part III describes implementations and tools:what has been built for the users of Haskell.We describe the various implementations of Haskell,including GHC,hbc,hugs,nhc,and Yale Haskell(Sec-tion9),and tools for profiling and debugging(Section10).Part IV describes applications and impact:what has been built by the users of Haskell.The language has been used for a bewildering variety of applications,and in Section11we reflect on the distinc-tive aspects of some of these applications,so far as we can dis-cern them.We conclude with a section that assesses the impact of Haskell on various communities of users,such as education,open-source,companies,and other language designers(Section12). Our goal throughout is to tell the story,including who was involved and what inspired them:the paper is supposed to be a history rather than a technical description or a tutorial.We have tried to describe the evolution of Haskell in an even-handed way,but we have also sought to convey some of the ex-citement and enthusiasm of the process by including anecdotes and personal reflections.Inevitably,this desire for vividness means that our account will be skewed towards the meetings and conversations in which we personally participated.However,we are conscious that many,many people have contributed to Haskell.The size and quality of the Haskell community,its breadth and its depth,are both the indicator of Haskell’s success and its cause.One inevitable shortcoming is a lack of comprehensiveness.Haskell is now more than15years old and has been a seedbed for an im-mense amount of creative energy.We cannot hope to do justice to all of it here,but we take this opportunity to salute all those who have contributed to what has turned out to be a wild ride.Part IGenesis and Principles2.The genesis of HaskellIn1978John Backus delivered his Turing Award lecture,“Can pro-gramming be liberated from the von Neumann style?”(Backus, 1978a),which positioned functional programming as a radical at-tack on the whole programming enterprise,from hardware archi-tecture upwards.This prominent endorsement from a giant in the field—Backus led the team that developed Fortran,and invented Backus Naur Form(BNF)—put functional programming on the map in a new way,as a practical programming tool rather than a mathematical curiosity.Even at that stage,functional programming languages had a long history,beginning with John McCarthy’s invention of Lisp in the late1950s(McCarthy,1960).In the1960s,Peter Landin and Christopher Strachey identified the fundamental importance of the lambda calculus for modelling programming languages and laid the foundations of both operational semantics,through abstract machines(Landin,1964),and denotational semantics(Strachey, 1964).A few years later Strachey’s collaboration with Dana Scott put denotational semantics onfirm mathematical foundations un-derpinned by Scott’s domain theory(Scott and Strachey,1971; Scott,1976).In the early’70s,Rod Burstall and John Darling-ton were doing program transformation in afirst-order functional language with function definition by pattern matching(Burstall and Darlington,1977).Over the same period David Turner,a for-mer student of Strachey,developed SASL(Turner,1976),a pure higher-order functional language with lexically scoped variables—a sugared lambda calculus derived from the applicative subset of Landin’s ISWIM(Landin,1966)—that incorporated Burstall and Darlington’s ideas on pattern matching into an executable program-ming language.In the late’70s,Gerry Sussman and Guy Steele developed Scheme, a dialect of Lisp that adhered more closely to the lambda calcu-lus by implementing lexical scoping(Sussman and Steele,1975; Steele,1978).At more or less the same time,Robin Milner in-vented ML as a meta-language for the theorem prover LCF at Ed-inburgh(Gordon et al.,1979).Milner’s polymorphic type system for ML would prove to be particularly influential(Milner,1978; Damas and Milner,1982).Both Scheme and ML were strict(call-by-value)languages and,although they contained imperative fea-tures,they did much to promote the functional programming style and in particular the use of higher-order functions.2.1The call of lazinessThen,in the late’70s and early’80s,something new happened.A series of seminal publications ignited an explosion of interest in the idea of lazy(or non-strict,or call-by-need)functional languages as a vehicle for writing serious zy evaluation appears to have been invented independently three times.•Dan Friedman and David Wise(both at Indiana)published “Cons should not evaluate its arguments”(Friedman and Wise, 1976),which took on lazy evaluation from a Lisp perspective.•Peter Henderson(at Newcastle)and James H.Morris Jr.(at Xerox PARC)published“A lazy evaluator”(Henderson and Morris,1976).They cite Vuillemin(Vuillemin,1974)and Wadsworth(Wadsworth,1971)as responsible for the origins of the idea,but popularised the idea in POPL and made one other important contribution,the name.They also used a variant ofLisp,and showed soundness of their evaluator with respect to a denotational semantics.•David Turner(at St.Andrews and Kent)introduced a series of influential languages:SASL(St Andrews Static Language) (Turner,1976),which was initially designed as a strict lan-guage in1972but became lazy in1976,and KRC(Kent Re-cursive Calculator)(Turner,1982).Turner showed the elegance of programming with lazy evaluation,and in particular the use of lazy lists to emulate many kinds of behaviours(Turner,1981;Turner,1982).SASL was even used at Burroughs to develop an entire operating system—almost certainly thefirst exercise of pure,lazy,functional programming“in the large”.At the same time,there was a symbiotic effort on exciting new ways to implement lazy languages.In particular:•In software,a variety of techniques based on graph reduction were being explored,and in particular Turner’s inspirationally elegant use of SK combinators(Turner,1979b;Turner,1979a).(Turner’s work was based on Haskell Curry’s combinatory cal-culus(Curry and Feys,1958),a variable-less version of Alonzo Church’s lambda calculus(Church,1941).)•Another potent ingredient was the possibility that all this would lead to a radically different non-von Neumann hardware archi-tectures.Several serious projects were underway(or were get-ting underway)to build dataflow and graph reduction machines of various sorts,including the Id project at MIT(Arvind and Nikhil,1987),the Rediflow project at Utah(Keller et al.,1979), the SK combinator machine SKIM at Cambridge(Stoye et al., 1984),the Manchester dataflow machine(Watson and Gurd, 1982),the ALICE parallel reduction machine at Imperial(Dar-lington and Reeve,1981),the Burroughs NORMA combinator machine(Scheevel,1986),and the DDM dataflow machine at Utah(Davis,1977).Much(but not all)of this architecturally oriented work turned out to be a dead end,when it was later dis-covered that good compilers for stock architecture could outper-form specialised architecture.But at the time it was all radical and exciting.Several significant meetings took place in the early’80s that lent additional impetus to thefield.In August1980,thefirst Lisp conference took place in Stanford, California.Presentations included Rod Burstall,Dave MacQueen, and Don Sannella on Hope,the language that introduced algebraic data types(Burstall et al.,1980).In July1981,Peter Henderson,John Darlington,and David Turner ran an Advanced Course on Functional Programming and its Appli-cations,in Newcastle(Darlington et al.,1982).All the big names were there:attendees included Gerry Sussman,Gary Lindstrom, David Park,Manfred Broy,Joe Stoy,and Edsger Dijkstra.(Hughes and Peyton Jones attended as students.)Dijkstra was characteris-tically unimpressed—he wrote“On the whole I could not avoid some feelings of deep disappointment.I still believe that the topic deserves a much more adequate treatment;quite a lot we were ex-posed to was definitely not up to par.”(Dijkstra,1981)—but for many attendees it was a watershed.In September1981,thefirst conference on Functional Program-ming Languages and Computer Architecture(FPCA)—note the title!—took place in Portsmouth,New Hampshire.Here Turner gave his influential paper on“The semantic elegance of applicative languages”(Turner,1981).(Wadler also presented hisfirst confer-ence paper.)FPCA became a key biennial conference in thefield. In September1982,the second Lisp conference,now renamed Lisp and Functional Programming(LFP),took place in Pittsburgh,Pennsylvania.Presentations included Peter Henderson on func-tional geometry(Henderson,1982)and an invited talk by Turner on programming with infinite data structures.(It also saw thefirst pub-lished papers of Hudak,Hughes,and Peyton Jones.)Special guests at this conference included Church and Curry.The after-dinner talk was given by Barkley Rosser,and received two ovations in the mid-dle,once when he presented the proof of Curry’s paradox,relating it to the Y combinator,and once when he presented a new proof of the Church-Rosser theorem.LFP became the other key biennial conference.(In1996,FPCA merged with LFP to become the annual Interna-tional Conference on Functional Programming,ICFP,which re-mains the key conference in thefield to the present day.)In August1987,Ham Richards of the University of Texas and David Turner organised an international school on Declarative Programming in Austin,Texas,as part of the UT“Year of Pro-gramming”.Speakers included:Samson Abramsky,John Backus, Richard Bird,Peter Buneman,Robert Cartwright,Simon Thomp-son,David Turner,and Hughes.A major part of the school was a course in lazy functional programming,with practical classes using Miranda.All of this led to a tremendous sense of excitement.The simplic-ity and elegance of functional programming captivated the present authors,and many other researchers with zy evaluation—with its direct connection to the pure,call-by-name lambda cal-culus,the remarkable possibility of representing and manipulating infinite data structures,and addictively simple and beautiful imple-mentation techniques—was like a drug.(An anonymous reviewer supplied the following:“An interesting sidelight is that the Friedman and Wise paper inspired Sussman and Steele to examine lazy evaluation in Scheme,and for a time they weighed whether to make the revised version of Scheme call-by-name or call-by-value.They eventually chose to retain the original call-by-value design,reasoning that it seemed to be much easier to simulate call-by-name in a call-by-value language(using lambda-expressions as thunks)than to simulate call-by-value in a call-by-name language(which requires a separate evaluation-forcing mech-anism).Whatever we might think of that reasoning,we can only speculate on how different the academic programming-language landscape might be today had they made the opposite decision.”)2.2A tower of BabelAs a result of all this activity,by the mid-1980s there were a num-ber of researchers,including the authors,who were keenly inter-ested in both design and implementation techniques for pure,lazy languages.In fact,many of us had independently designed our own lazy languages and were busily building our own implementations for them.We were each writing papers about our efforts,in which wefirst had to describe our languages before we could describe our implementation nguages that contributed to this lazy Tower of Babel include:•Miranda,a successor to SASL and KRC,designed and imple-mented by David Turner using SK combinator reduction.While SASL and KRC were untyped,Miranda added strong polymor-phic typing and type inference,ideas that had proven very suc-cessful in ML.•Lazy ML(LML),pioneered at Chalmers by Augustsson and Johnsson,and taken up at University College London by Peyton Jones.This effort included the influential development of the G-machine,which showed that one could compile lazy functional programs to rather efficient code(Johnsson,1984;Augustsson, 1984).(Although it is obvious in retrospect,we had becomeused to the idea that laziness meant graph reduction,and graph reduction meant interpretation.)•Orwell,a lazy language developed by Wadler,influenced by KRC and Miranda,and OL,a later variant of Orwell.Bird and Wadler co-authored an influential book on functional program-ming(Bird and Wadler,1988),which avoided the“Tower of Babel”by using a more mathematical notation close to both Miranda and Orwell.•Alfl,designed by Hudak,whose group at Yale developed a combinator-based interpreter for Alflas well as a compiler based on techniques developed for Scheme and for T(a dialect of Scheme)(Hudak,1984b;Hudak,1984a).•Id,a non-strict dataflow language developed at MIT by Arvind and Nikhil,whose target was a dataflow machine that they were building.•Clean,a lazy language based explicitly on graph reduction, developed at Nijmegen by Rinus Plasmeijer and his colleagues (Brus et al.,1987).•Ponder,a language designed by Jon Fairbairn,with an impred-icative higher-rank type system and lexically scoped type vari-ables that was used to write an operating system for SKIM (Fairbairn,1985;Fairbairn,1982).•Daisy,a lazy dialect of Lisp,developed at Indiana by Cordelia Hall,John O’Donnell,and their colleagues(Hall and O’Donnell, 1985).With the notable exception of Miranda(see Section3.8),all of these were essentially single-site languages,and each individually lacked critical mass in terms of language-design effort,implementations, and users.Furthermore,although each had lots of interesting ideas, there were few reasons to claim that one language was demonstra-bly superior to any of the others.On the contrary,we felt that they were all roughly the same,bar the syntax,and we started to wonder why we didn’t have a single,common language that we could all benefit from.At this time,both the Scheme and ML communities had developed their own standards.The Scheme community had major loci in MIT,Indiana,and Yale,and had just issued its‘revised revised’report(Rees and Clinger,1986)(subsequent revisions would lead to the‘revised5’report(Kelsey et al.,1998)).Robin Milner had issued a‘proposal for Standard ML’(Milner,1984)(which would later evolve into the definitive Definition of Standard ML(Milner and Tofte,1990;Milner et al.,1997)),and Appel and MacQueen had released a new high-quality compiler for it(Appel and MacQueen, 1987).2.3The birth of HaskellBy1987,the situation was akin to a supercooled solution—all that was needed was a random event to precipitate crystallisation.That event happened in the fall of’87,when Peyton Jones stopped at Yale to see Hudak on his way to the1987Functional Program-ming and Computer Architecture Conference(FPCA)in Portland, Oregon.After discussing the situation,Peyton Jones and Hudak decided to initiate a meeting during FPCA,to garner interest in de-signing a new,common functional language.Wadler also stopped at Yale on the way to FPCA,and also endorsed the idea of a meet-ing.The FPCA meeting thus marked the beginning of the Haskell de-sign process,although we had no name for the language and very few technical discussions or design decisions occurred.In fact,a key point that came out of that meeting was that the easiest way to move forward was to begin with an existing language,and evolveit in whatever direction suited us.Of all the lazy languages under development,David Turner’s Miranda was by far the most mature. It was pure,well designed,fulfilled many of our goals,had a ro-bust implementation as a product of Turner’s company,Research Software Ltd,and was running at120sites.Turner was not present at the meeting,so we concluded that thefirst action item of the committee would be to ask Turner if he would allow us to adopt Miranda as the starting point for our new language.After a brief and cordial interchange,Turner declined.His goals were different from ours.We wanted a language that could be used, among other purposes,for research into language features;in par-ticular,we sought the freedom for anyone to extend or modify the language,and to build and distribute an implementation.Turner, by contrast,was strongly committed to maintaining a single lan-guage standard,with complete portability of programs within the Miranda community.He did not want there to be multiple dialects of Miranda in circulation and asked that we make our new lan-guage sufficiently distinct from Miranda that the two would not be confused.Turner also declined an invitation to join the new design committee.For better or worse,this was an important fork in the road.Al-though it meant that we had to work through all the minutiae of a new language design,rather than starting from an already well-developed basis,it allowed us the freedom to contemplate more radical approaches to many aspects of the language design.For ex-ample,if we had started from Miranda it seems unlikely that we would have developed type classes(see Section6.1).Neverthe-less,Haskell owes a considerable debt to Miranda,both for general inspiration and specific language elements that we freely adopted where theyfitted into our emerging design.We discuss the relation-ship between Haskell and Miranda further in Section3.8.Once we knew for sure that Turner would not allow us to use Mi-randa,an insanely active email discussion quickly ensued,using the mailing list fplangc@,hosted at the Univer-sity College London,where Peyton Jones was a faculty member. The email list name came from the fact that originally we called ourselves the“FPLang Committee,”since we had no name for the language.It wasn’t until after we named the language(Section2.4) that we started calling ourselves the“Haskell Committee.”2.4Thefirst meetingsThe Yale Meeting Thefirst physical meeting(after the im-promptu FPCA meeting)was held at Yale,January9–12,1988, where Hudak was an Associate Professor.Thefirst order of busi-ness was to establish the following goals for the language:1.It should be suitable for teaching,research,and applications,including building large systems.2.It should be completely described via the publication of a for-mal syntax and semantics.3.It should be freely available.Anyone should be permitted toimplement the language and distribute it to whomever they please.4.It should be usable as a basis for further language research.5.It should be based on ideas that enjoy a wide consensus.6.It should reduce unnecessary diversity in functional program-ming languages.More specifically,we initially agreed to base it on an existing language,namely OL.The last two goals reflected the fact that we intended the language to be quite conservative,rather than to break new ground.Although matters turned out rather differently,we intended to do little more than embody the current consensus of ideas and to unite our dis-parate groups behind a single design.As we shall see,not all of these goals were realised.We abandoned the idea of basing Haskell explicitly on OL very early;we violated the goal of embodying only well-tried ideas,notably by the inclu-sion of type classes;and we never developed a formal semantics. We discuss the way in which these changes took place in Section3. Directly from the minutes of the meeting,here is the committee process that we agreed upon:1.Decide topics we want to discuss,and assign“lead person”toeach topic.2.Lead person begins discussion by summarising the issues forhis topic.•In particular,begin with a description of how OL does it.•OL will be the default if no clearly better solution exists.3.We should encourage breaks,side discussions,and literatureresearch if necessary.4.Some issues will not be resolved!But in such cases we shouldestablish action items for their eventual resolution.5.It may seem silly,but we should not adjourn this meeting untilat least one thing is resolved:a name for the language!6.Attitude will be important:a spirit of cooperation and compro-mise.We return later to further discussion of the committee design pro-cess,in Section3.5.A list of all people who served on the Haskell Committee appears in Section14.Choosing a Name Thefifth item above was important,since a small but important moment in any language’s evolution is the moment it is named.At the Yale meeting we used the following process(suggested by Wadler)for choosing the name.Anyone could propose one or more names for the language,which were all written on a blackboard.At the end of this process,the following names appeared:Semla,Haskell,Vivaldi,Mozart,CFL (Common Functional Language),Funl88,Semlor,Candle(Com-mon Applicative Notation for Denoting Lambda Expressions),Fun, David,Nice,Light,ML Nouveau(or Miranda Nouveau,or LML Nouveau,or...),Mirabelle,Concord,LL,Slim,Meet,Leval,Curry, Frege,Peano,Ease,Portland,and Haskell B Curry.After consider-able discussion about the various names,each person was then free to cross out a name that he disliked.When we were done,there was one name left.That name was“Curry,”in honour of the mathematician and lo-gician Haskell B.Curry,whose work had led,variously and indi-rectly,to our presence in that room.That night,two of us realised that we would be left with a lot of curry puns(aside from the spice, and the thought of currying favour,the one that truly horrified us was Tim Curry—TIM was Jon Fairbairn’s abstract machine,and Tim Curry was famous for playing the lead in the Rocky Horror Picture Show).So the next day,after some further discussion,we settled on“Haskell”as the name for the new language.Only later did we realise that this was too easily confused with Pascal or Has-sle!Hudak and Wise were asked to write to Curry’s widow,Virginia Curry,to ask if she would mind our naming the language after her husband.Hudak later visited Mrs.Curry at her home and listened to stories about people who had stayed there(such as Church and Kleene).Mrs.Curry came to his talk(which was about Haskell,of course)at Penn State,and although she didn’t understand a wordof what he was saying,she was very gracious.Her parting remark was“You know,Haskell actually never liked the name Haskell.”The Glasgow Meeting Email discussions continued fervently af-ter the Yale Meeting,but it took a second meeting to resolve many of the open issues.That meeting was held April6–9,1988at the University of Glasgow,whose functional programming group was beginning a period of rapid growth.It was at this meeting that many key decisions were made.It was also agreed at this meeting that Hudak and Wadler would be the editors of thefirst Haskell Report.The name of the report,“Re-port on the Programming Language Haskell,A Non-strict,Purely Functional Language,”was inspired in part by the“Report on the Algorithmic Language Scheme,”which in turn was modelled after the“Report on the Algorithmic Language Algol.”IFIP WG2.8Meetings The’80s were an exciting time to be do-ing functional programming research.One indication of that ex-citement was the establishment,due largely to the effort of John Williams(long-time collaborator with John Backus at IBM Al-maden),of IFIP Working Group2.8on Functional Programming. This not only helped to bring legitimacy to thefield,it also provided a convenient venue for talking about Haskell and for piggy-backing Haskell Committee meetings before or after WG2.8meetings.The first two WG2.8meetings were held in Glasgow,Scotland,July11–15,1988,and in Mystic,CT,USA,May1–5,1989(Mystic is about 30minutes from Yale).Figure1was taken at the1992meeting of WG2.8in Oxford.2.5Refining the designAfter the initialflurry of face-to-face meetings,there followedfif-teen years of detailed language design and development,coordi-nated entirely by electronic mail.Here is a brief time-line of how Haskell developed:September1987.Initial meeting at FPCA,Portland,Oregon. December1987.Subgroup meeting at University College London. January1988.A multi-day meeting at Yale University.April1988.A multi-day meeting at the University of Glasgow. July1988.Thefirst IFIP WG2.8meeting,in Glasgow.May1989.The second IFIP WG2.8meeting,in Mystic,CT.1April1990.The Haskell version1.0Report was published(125 pages),edited by Hudak and Wadler.At the same time,the Haskell mailing list was started,open to all.The closed fplangc mailing list continued for committee dis-cussions,but increasingly debate took place on the public Haskell mailing list.Members of the committee became in-creasingly uncomfortable with the“us-and-them”overtones of having both public and private mailing lists,and by April1991 the fplangc list fell into disuse.All further discussion about Haskell took place in public,but decisions were still made by the committee.August1991.The Haskell version1.1Report was published(153 pages),edited by Hudak,Peyton Jones,and Wadler.This was mainly a“tidy-up”release,but it included let expressions and operator sections for thefirst time.March1992.The Haskell version1.2Report was published(164 pages),edited by Hudak,Peyton Jones,and Wadler,introduc-ing only minor changes to Haskell1.1.Two months later,in May1992,it appeared in SIGPLAN Notices,accompanied by a“Gentle introduction to Haskell”written by Hudak and Fasel.We are very grateful to the SIGPLAN chair Stu Feldman,andthe Notices editor Dick Wexelblat,for their willingness to pub-lish such an enormous document.It gave Haskell both visibility and credibility.1994.Haskell gained Internet presence when John Peterson regis-tered the domain name and set up a server and web-site at Yale.(Hudak’s group at Yale continues to maintain the server to this day.)May1996.The Haskell version1.3Report was published,edited by Hammond and Peterson.In terms of technical changes, Haskell1.3was the most significant release of Haskell after1.0.In particular:•A Library Report was added,reflecting the fact that pro-grams can hardly be portable unless they can rely on stan-dard libraries.•Monadic I/O made itsfirst appearance,including“do”syn-tax(Section7),and the I/O semantics in the Appendix wasdropped.•Type classes were generalised to higher kinds—so-called“constructor classes”(see Section6).•Algebraic data types were extended in several ways:new-types,strictness annotations,and namedfields.April1997.The Haskell version1.4report was published(139 +73pages),edited by Peterson and Hammond.This was a tidy-up of the1.3report;the only significant change is that list comprehensions were generalised to arbitrary monads,a decision that was reversed two years later.February1999The Haskell98Report:Language and Libraries was published(150+89pages),edited by Peyton Jones and Hughes.As we describe in Section3.7,this was a very signifi-cant moment because it represented a commitment to stability.List comprehensions reverted to just lists.1999–2002In1999the Haskell Committee per se ceased to exist.Peyton Jones took on sole editorship,with the intention of collecting andfixing typographical errors.Decisions were no longer limited to a small committee;now anyone reading the Haskell mailing list could participate.However,as Haskell became more widely used(partly because of the existence of the Haskell98standard),many smallflaws emerged in the language design,and many ambiguities in the Report were discovered.Peyton Jones’s role evolved to that of Benign Dictator of Linguistic Minutiae.December2002The Revised Haskell98Report:Language and Libraries was published(260pages),edited by Peyton Jones.Cambridge University Press generously published the Report asa book,while agreeing that the entire text could still be availableonline and be freely usable in that form by anyone.Theirflex-ibility in agreeing to publish a book under such unusual terms was extraordinarily helpful to the Haskell community,and de-fused a tricky debate about freedom and intellectual property.It is remarkable that it took four years from thefirst publication of Haskell98to“shake down”the specification,even though Haskell was already at least eight years old when Haskell98 came nguage design is a slow process!Figure2gives the Haskell time-line in graphical form1.Many of the implementations,libraries,and tools mentioned in thefigure are discussed later in the paper.。
剑桥国际少儿英语3第五单元lock and key
剑桥国际少儿英语3第五单元lock and keyThe intricate dance between locks and keys has been a captivating part of human history for centuries. These seemingly simple mechanisms have played a vital role in securing our most prized possessions, safeguarding our privacy, and shaping the way we interact with the world around us. In this essay, we will delve into the fascinating world of locks and keys, exploring their evolution, their significance, and the myriad ways in which they have become woven into the fabric of our lives.Locks and keys have a long and storied history, dating back to ancient civilizations. The earliest known lock and key system was discovered in the ruins of the ancient Egyptian city of Nineveh, dating back to around 4000 BC. These primitive devices were made of wood and consisted of a bolt that could be secured by a wooden pin tumbler lock. As civilizations advanced, so too did the complexity and sophistication of lock and key systems.Throughout the ages, locks have been crafted from a variety of materials, each with its own unique properties and applications. Fromthe sturdy iron locks of medieval castles to the delicate pin tumbler locks of modern-day homes, the evolution of these devices has been a testament to human ingenuity and the constant drive to create more secure and reliable means of protection.One of the most significant advancements in lock technology came with the invention of the pin tumbler lock, attributed to the ancient Egyptians. This design, which utilizes a series of pins of varying lengths to prevent the bolt from opening without the correct key, has remained a fundamental component of many modern lock systems. As technology has progressed, lock designs have become increasingly complex, incorporating features such as electronic sensors, biometric identification, and even wireless connectivity.Alongside the development of locks, the creation of keys has also been a crucial aspect of this enduring story. Keys, too, have evolved from their humble beginnings as simple wooden or metal devices to the sophisticated, high-tech tools we use today. From the intricate warding and bitting patterns of traditional keys to the advanced radio-frequency identification (RFID) chips found in modern keyless entry systems, the key has become a symbol of access, control, and trust.The significance of locks and keys extends far beyond their practical applications. These humble devices have become cultural icons,representing themes of security, privacy, and personal identity. In literature and art, locks and keys have been used as metaphors for the human condition, exploring themes of trust, vulnerability, and the search for personal fulfillment.One particularly poignant example can be found in the works of renowned author Ernest Hemingway. In his novel "The Sun Also Rises," Hemingway uses the imagery of a locked suitcase to symbolize the emotional barriers and personal struggles faced by the characters. The suitcase, with its key held by a distant lover, becomes a tangible representation of the characters' inability to fully connect with one another, highlighting the universal human desire for intimacy and understanding.Similarly, in the realm of art, locks and keys have been the subject of countless works, from the intricate etchings of Albrecht Dürer to the surreal sculptures of Salvador Dalí. These artistic interpretations have further cemented the symbolic significance of these everyday objects, inviting viewers to explore the deeper meanings and emotional resonances that they evoke.Beyond their cultural significance, locks and keys have also played a crucial role in the practical aspects of our lives. From the simple padlocks securing our bicycles to the high-security systems safeguarding our most valuable assets, these devices have becomean integral part of our daily routines and the infrastructure that supports our modern world.In the realm of security, the importance of locks and keys cannot be overstated. They have become essential tools in protecting our homes, businesses, and vital information from the prying eyes of those who seek to do us harm. The continuous advancements in lock technology have led to the creation of increasingly sophisticated systems that utilize biometric data, encrypted codes, and even cloud-based access management to ensure the safety and privacy of our most sensitive belongings.Furthermore, the use of locks and keys extends beyond the realm of personal and commercial security. In the world of transportation, these devices have become vital components in securing everything from vehicles to shipping containers, ensuring the safe and efficient movement of people and goods around the globe. The development of advanced key technologies, such as keyless entry systems and remote-controlled locks, has revolutionized the way we interact with our modes of transportation, providing greater convenience and security.Looking to the future, the role of locks and keys is poised to evolve even further. As the world becomes increasingly connected through the Internet of Things (IoT), the integration of smart locks and digitalkeys is expected to transform the way we access and secure our homes, workplaces, and even entire cities. Imagine a world where a single digital key, stored securely on your smartphone, could grant you access to your front door, your office, and your car, all with a simple tap or voice command.This vision of a seamlessly connected future is not merely a fanciful dream, but rather a tangible reality that is rapidly taking shape. As technology continues to advance, the humble lock and key are set to play an even more vital role in shaping the way we live, work, and interact with the world around us.In conclusion, the story of locks and keys is a testament to the enduring ingenuity and adaptability of the human spirit. From their ancient origins to their modern-day applications, these unassuming devices have become a fundamental part of our lives, safeguarding our most prized possessions, securing our personal and collective safety, and serving as powerful symbols of trust, privacy, and personal identity. As we look to the future, the continued evolution of locks and keys will undoubtedly continue to shape the way we navigate the world, opening doors to new possibilities and forging ever-stronger connections between ourselves and the spaces we inhabit.。
七年级英语词汇联想记忆练习题30题(带答案)
七年级英语词汇联想记忆练习题30题(带答案)1. My father's father is my ____.A.grandfatherB.grandmotherC.fatherD.mother答案:A。
解析:爸爸的爸爸是爷爷,grandfather表示爷爷。
2. The color of the sky is usually ____.A.redB.blueC.greenD.yellow答案:B。
解析:天空的颜色通常是蓝色,blue表示蓝色。
3. A baby cat is called a ____.A.puppyB.kittenC.ducklingmb答案:B。
解析:小猫的英文是kitten,puppy是小狗,duckling 是小鸭子,lamb是小羊。
4. The opposite of "big" is ____.A.smallB.tallC.longD.short答案:A。
解析:big的意思是大的,它的反义词是小的,small表示小的。
5. There are ____ days in a week.A.fiveB.sixC.sevenD.eight答案:C。
解析:一周有七天。
6. The color of the grass is ____.A.blackB.whiteC.greenD.purple答案:C。
解析:草的颜色是绿色,green表示绿色。
7. My mother's sister is my ____.A.auntB.uncleC.cousinD.sister答案:A。
解析:妈妈的姐妹是阿姨,aunt表示阿姨。
8. A group of three is called ____.A.singleB.doubleC.tripleD.quadruple答案:C。
解析:三个一组被称为triple,single是单个的,double 是双的,quadruple是四个一组的。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Chapter5ADTs and Haskell5.1Implementing an ADTIn this section,we consider the practical side of implementing an ADT.•Once we've constructed a complete de nition of a stack,how do we turn it into code?•How do we actually program an abstract data type?•The answer will depend on the language you decide to use;we'll be using Haskell.In general,however,the principles are the same no matter what language you use.•First you need to identify which types in the language will correspond to the ADT's auxiliary types,and then you need to implement each of the ADT's operations. 5.1.1An aside:Haskell's module systemOne way to program an ADT in Haskell is to use the module system(covered last semester).The use of module s to program ADTs is explained,with examples,in Si-mon Thompson's book.Regardless of whether you use module s or some other technique, you will still need to address the questions raised below.5.2Either a bThe biggest problem we face is how to represent`either a or b'.There are many solutions (including avoid the problem).The Either type is de ned in the Haskell Prelude:1data Either a b=Left a|Right bderiving(Eq,Ord,Read,Show)Either de nes a whole family of data types,one for each choice of a and b.Some examples of types constructed using Either are•Either Integer CharThis is the Haskell type corresponding to(Integer∪Char).Typical values include Left5Right'x'Left16•Either Bool FloatThis is the Haskell type corresponding to(Bool∪Float).Typical values includeLeft TrueRight5.0Left FalseIf we substitute for just one of Either's type variables,we get a family of one-parameter data types.For example,other instances of Either include•Either a MsgThis is the Haskell type corresponding to(a∪Msg).Of course,we need to de ne the Msg type in Haskell as well,or this won't be properly de ned.Typical values of type Either a Msg includeLeft x,for any x of type aRight"the stack is empty"Finally,there's no reason we can't substitute types that are themselves parametric.•Either(Stack a)MsgThis is the Haskell type corresponding to(Stack a∪Msg).Typical values include Left createStackRight"the stack is empty"Left(push x s)•Either(Either Bool Integer)CharThis is the Haskell type corresponding to((Bool∪Integer)∪Char).Typical values include2Left(Left True)Left(Right5)Right'x'As these examples show,however,if we decide to use an Either type,the values we write down are going to look fairly unintuitive.Ultimately this is once again a matter of personal choice are we happy to put up with slightly more complicated values in exchange for having a standard way of representing types of the form`either a or b'?5.3Implementation using EitherNow that we know about Either,we can start to implement Stack a.5.3.1TypesThe rst thing to notice is that Haskell allows us to leave a unde ned.This is unusual,and re ects the fact that Haskell is a functional language equipped with the means to represent type nguages like Java and C++don't support type variables(except as speci c parameters in template s),so if we were implementing Stack a in one of those languages we would have to decide precisely what type to use to represent entries.As always,the nal choice as to which type is which is up to you as the ADT's designer.I choose the following types:Msg StringBool Bool(Stack a∪Msg)Either(Stack a)String(a∪Msg)Either a String5.3.2ConstructorsWe've identi ed two of the operations de ned in Stack a's syntax as constructors.We can re ect this directly using Haskell's data construction.data Stack a=EmptyStack|Push a(Stack a)This de nition says that,for any type a,Stack a is a data type whose elements come in two forms.Either a stack is an EmptyStack,or else it can be written in the form Push x s for some entry x and some existing stack s.The constructors themselves can now be de ned directly:3--definition of createStack:->Stack acreateStack::Stack acreateStack=EmptyStack--definition of push:a->Stack a->Stack apush::a->Stack a->Stack apush x s=Push x s5.3.3Non-constructorsThe other three operations can be de ned just as easily.Notice that the Haskell de nitions for these functions are just the rules we worked out for the semantics!Having worked out the ADT de nition of a Stack a,there's nothing left to do;all the equations are already de ned for us.--definition of emptyStack:Stack a->BoolemptyStack::Stack a->BoolemptyStack EmptyStack=TrueemptyStack(Push__)=False--definition of top:Stack a->Either a Stringtop::Stack a->Either a Stringtop EmptyStack=Right"the stack is empty"top(Push x_)=Left x--definition of pop:Stack a->Either(Stack a)Stringpop::Stack a->Either(Stack a)Stringpop EmptyStack=Right"the stack is empty"pop(Push_s)=Left sTyping these de nitions into Haskell environment shows the following evaluations: push5createStack-->Push5EmptyStack::Stack Integerpop(push5createStack)-->Left EmptyStack::Either(Stack Integer)String5.3.4Problems with this approachAlthough it looks like we've simply copied out the rules that occurred in the ADT's seman-tics,this isn't quite true;we've had to add various instances of Left and Right.These4cause very de nite problems,as becomes obvious is we try to evaluatepop(pop(push5(push6EmptyStack))).Consider what the result ought to be:starting with the empty stack,we rst push two integers onto the stack and then pop them o again.The result ought to be the empty stack again.In fact,however,the Haskell environment gives the evaluationMain>pop(pop(push5(push6EmptyStack)))ERROR-Type error in application***Expression:pop(pop(push5(push6EmptyStack)))***Term:pop(push5(push6EmptyStack))***Type:Either(Stack b)String***Does not match:Stack aThe problem lies in the return type of the rst pop,which is Either(Stack a)String.In order to apply pop a second time,we need the argument to be of type Stack a.Somehow, we need to get rid of the Either types in our de nitions.But how can we do this?5.4Using an invariant assertionIt looks like using Either is causing unnecessary problems,but in fact it's much worse than this.The problem lies in the ADT de nition itself.There's no obvious reason why we should rule out applying pop twice in a row(as long as the stack contains at least two entries),and yet our syntax won't let us do this.The types simply don't match up:1st pop:Stack a→(Stack a∪Msg)2nd pop:Stack a→(Stack a∪Msg)Applying pop once generates a result of type(Stack a∪Msg),but the second pop requires an argument of type Stack a.How can we avoid this problem?A standard solution is to give what's called an invariant assertion.We simply state, for example,that whenever a function is applied to a Msg,it simply returns its argument unchanged.In other words,all values of type Msg are left invariant by every operation that acts on them.So,if applying pop the rst time generates a stack as its result,the second pop operates on this stack as usual;if the rst pop generates the message the stack is empty,then the second pop also generates this result;it passes the message on unchanged.Unfortunately,while this tells us how to evaluate what happens when we apply pop twice in row,it doesn't actually solve our typing problem!5Clearly,we need the argument type and the return type of pop to essentially the same type.So either we need to change pop so it can explicitly be applied to arguments of type (Stack a∪Msg),or else we need to remove the need for Msg in the return type.Both approaches are viable.5.4.1Changing pop's argument typeThis solution simply means that pop's signature has to be changed topop:(Stack a∪Msg)→(Stack a∪Msg)but,of course,that's not the only change that's needed.We have to check what happens when each of the operations is combined with each of the others.Worse still,as we change the argument types of each operation,we will need to re-address these mismatches,so the entire process is iterative.We keep going until all the signatures are consistent with one another.Starting again with`pop then pop',the process might begin:•pop then pop.Got:pop returns(Stack a∪Msg)Got:pop requires Stack aChange to:pop:(Stack a∪Msg)→(Stack a∪Msg)•pop then push.Got:pop returns(Stack a∪Msg)Got:push requires a and Stack aChange to:push:a→(Stack a∪Msg)→(Stack a∪Msg)and so on...In some ways this is the best solution available to us.Although there are neater answers, they typically rely on making speci c compromises or design decisions,whereas the current solutionrem ains truly general.The overall solution isn't particularly complicated,just a little messy:•Typesa,Bool,Msg(a∪Msg),(Stack a∪Msg)•SyntaxcreateStack:→(Stack a∪Msg)6push:(a∪Msg)→(Stack a∪Msg)→(Stack a∪Msg)emptyStack:(Stack a∪Msg)→(Bool∪Msg)top:(Stack a∪Msg)→(a∪Msg)pop:(Stack a∪Msg)→(Stack a∪Msg)•Semantics[push.1]:push msg s==msg if msg::Msg,s::Stack a[push.2]:push x msg==msg if x::a,msg::Msg[push.3]:push msg msg'==joinMsg(msg,msg')if msg,msg'::Msg,where joinMsg denotes some form of message combination[empty.1]:emptyStack(createStack)==True[empty.2]:emptyStack(push x s)==False if x::a,s::Stack a[empty.3]:emptyStack msg==msg if msg::Msg[top.1]:top(createStack)=="the stack is empty"[top.2]:top(push x s)==x if x::a,s::Stack a[top.3]:top msg==msg if msg::Msg[pop.1]:pop(createStack)=="the stack is empty"[pop.2]:pop(push x s)==s if x::a,s::Stack a[pop.3]:pop msg==msg if msg::MsgGiven this new ADT de nition,we can construct a Haskell implementation using Either, much as before.The important thing to note is that we can't do tests to nd out what type the various arguments are,so we need to use care when converting the semantics into implementation rules.type Msg=StringjoinMsg::Msg->Msg->MsgjoinMsg msg_=msg--Keep it simple.--Just use the first of the two messagesdata Stack a=EmptyStack|Push a(Stack a)deriving(Show,Eq)createStack::Either(Stack a)MsgcreateStack=Left EmptyStack7--[push.1]push msg s==msg if msg::Msg,s::Stack a--[push.2]push x msg==msg if x::a,msg::Msg--[push.3]push msg msg'==joinMsg(msg,msg')if msg,msg'::Msg push::Either a Msg->Either(Stack a)Msg->Either(Stack a)Msgpush(Left x)(Left s)=Left(Push x s)push(Right msg)(Left_)=Right msg--[push.1]push(Left_)(Right msg)=Right msg--[push.2]push(Right msg)(Right msg')=Right(joinMsg msg msg')--[push.3]--Easy version so I can just push values without having to"Left"-ify them pushEasy::a->Either(Stack a)Msg->Either(Stack a)MsgpushEasy x=push(Left x)--IMPLEMENT EMPTYSTACK--[empty.1]emptyStack(createStack)==True--[empty.2]emptyStack(push x s)==False if x::a,s::Stack a--[empty.3]emptyStack msg==msg if msg::MsgemptyStack::Either(Stack a)Msg->Either Bool MsgemptyStack(Left EmptyStack)=Left TrueemptyStack(Left_)=Left FalseemptyStack(Right msg)=Right msg--IMPLEMENT TOP--[top.1]top(createStack)=="the stack is empty"--[top.2]top(push x s)==x if x::a,s::Stack a--[top.3]top msg==msg if msg::Msgtop::Either(Stack a)Msg->Either a Msgtop(Left EmptyStack)=Right"the stack is empty"--[top.1]top(Left(Push x_))=Left x--[top.2]top(Right msg)=Right msg--[top.3]--IMPLEMENT POP--[pop.1]pop(createStack)=="the stack is empty"--[pop.2]pop(push x s)==s}if x::a,s::Stack a--[pop.3]pop msg==msg if msg::Msgpop::Either(Stack a)Msg->Either(Stack a)Msg8pop(Left EmptyStack)=Right"the stack is empty"--[pop.1]pop(Left(Push_s))=Left s--[pop.2]pop(Right msg)=Right msg--[pop.3]--Try out a double-pop to see what happenstest=pop(pop(pushEasy5(pushEasy6(createStack))))which causes test to evaluate,as expected,toLeft EmptyStack::Either(Stack Integer)Msg5.5Removing the need for MsgA simpler solution would be to remove the need for Msg altogether,but to do this we need to remember why Msg was introduced in the rst place.The problem was that sometimes it doesn't make sense to apply an operation;for example, it doesn't make sense to apply top to the empty stack.We included Msg as a way of letting the user know that they'd done something silly; rather than leaving them in the dark when they try applying top after createStack,we provide them with the feedback message,`the stack is empty'.But in fact there's no need for this.We could set aside a speci c value of type Stack a, which we return whenever we would previously have returned a message.•People do this all the time at the concrete(i.e.,programming)level;for example, you might de ne a function that returns integers,but with the understanding that negative results indicate error conditions of some sort.•Because top also returns`error'messages,we would also need to set aside a special value of type a.•Taking this approach would allow us to simplify the ADT de nition quite signi cantly in some ways,but complicates it in others.•In particular,we are making design decisions when we should be keeping things as abstract as possible.We should also remember that it's not always possible to set aside a special`error value'. For example,suppose we wanted to program a division operator for integers;we'd need to pick some value to represent division-by-zero,but there is no value we can choose that might not actually arise quite naturally as the result of a valid division.9•Typesa,Bool•SyntaxaErr:→astackErr:→Stack acreateStack:→Stack apush:a→Stack a→Stack aemptyStack:Stack a→Booltop:Stack a→apop:Stack a→Stack a•Semantics[empty.1]:emptyStack(createStack)==True[empty.2]:emptyStack(push x s)==False[empty.3]:emptyStack(stackErr)==False(it's up to us how we de nethis)[top.1]:top(createStack)==aErr[top.2]:top(push x s)==x[top.3]:top(stackErr)==aErr[pop.1]:pop(createStack)==stackErr[pop.2]:pop(push x s)==s[pop.3]:pop(stackErr)==stackErr[push.1]:push x stackErr==stackErr[push.2]:push aErr s==stackErrwhere aErr and stackErr are the speci c entities of types a and Stack a,respectively, used solely to indicate error conditions.Notice,however,that we now need to add several extra rules to the semantics,so we know what happens if people try to operate on these special values.In particular,we've had to add two new rules for push.105.6Exploiting side-e ects using errorThat's just about all we can do at the abstract level,but when we try to implement the ADT,we can take advantage of speci c language features,and in particular we can exploit side-e ects.In Haskell,we can do this using the error function.Recall that this is a hard-wired function,de ned in the Haskell Prelude aserror::String→aThe important point about error is that it allows us to generate a message to the user, without actually returning the message as a return value.•If we use the error mechanism,we can simplify things somewhat.•Wherever we previously returned a value of type(a∪Msg),we can now return one of type a instead,and•wherever we returned a value of type(Stack a∪Msg),we can return one of type Stack a•i.e.,wherever a message would have been required,we use error to generate it instead.•That is,we use Haskell's error system to simplify the syntax for Stack a.•We no longer need to consider the special error values aErr and stackErr,and so we no longer need to introduce extra rules into the semantics.•As before,we can use Haskell's data construction,and as before the function imple-mentations are simply the semantic rules written using Haskell syntax.data Stack a=EmptyStack|Push a(Stack a)--definition of createStack:->Stack acreateStack::Stack acreateStack=EmptyStack--definition of push:a->Stack a->Stack apush::a->Stack a->Stack apush x s=Push x s--definition of emptyStack:Stack a->BoolemptyStack::Stack a->BoolemptyStack EmptyStack=True--[empty.1]11emptyStack(Push__)=False--[empty.2]--definition of top:Stack a->atop::Stack a->atop EmptyStack=error"the stack is empty"--[top.1]top(Push x_)=x--[top.2]--definition of pop:Stack a->Stack apop::Stack a->Stack apop EmptyStack=error"the stack is empty"--[pop.1]pop(Push_s)=s--[pop.2]As expected,these new type signatures mean that we can apply as many operators as we like in sequence;if the result ought to be de ned,it will be.For example:pop(pop(push5(push6EmptyStack)))-->pop(pop(push5(Push6EmptyStack)))-->pop(pop(Push5(Push6EmptyStack)))-->pop(Push6EmptyStack)-->EmptyStack::Stack Integer5.7Using Haskell's class systemWe'll look at this in more detail later in the course,but for now it's worth noting that Haskell has a class system that can be used for implementing ADTs.Important:This has virtually nothing to do with object-oriented`classes'in languages like Java and C++.A type class is a set of types that share the same polymorphic functions.For example, the class Eq a comprises those types a for which the functions(==)and(/=)are de ned. Formally,the class is introduced in the Haskell Prelude by the declarationclass Eq a where(==),(/=)::a->a->BoolTo de ne a class you use the class keyword,give the name of the class,and then say precisely what functions have to be available if a type is to count as a member of the class. For example,we can say that an arbitrary type adt is a member of the Stack type class by writingclass Stack adt wherecreateStack::adt12push::adt->adt->adtemptyStack::adt->Booltop::adt->adtpop::adt->adtThis tells us that a data type adt can be used as a stack provided it has some way of representing each of the operators in question.There are many data types can be used in this way.For example,a common technique is to represent a stack as a list.In order to t in with the class de nition given above,we'd also need to represent individual entries as lists,and we can do this easily by representing the entry e as the singleton-list[e].Given this interpretation,we tell Haskell that lists can be used as stacks by using the instance keyword,and telling Haskell how to implement each of the ADT's operations.instance Stack[a]wherecreateStack=[]push[e]s=e:spush__=error"invalid entry pushed onto stack"emptyStack[]=TrueemptyStack_=Falsetop[]=error"the stack is empty"top(e:_)=[e]pop[]=error"the stack is empty"pop(_:s)=sThe rst line of this de nition says that`one instance of the class Stack is the type [a]',provided we de ne the required operations as shown in the list of implementations that appear within the scope of the where keyword.In this instance the empty stack is represented as the empty list[],and the top element of a list is the list[e]containing the top element.We don't have to use existing data types if we don't want to.If we prefer,we can de ne our own algebraic data types and declare them to be instance of the Stack class.For example, the following de nitions introduce a new algebraic data type StackADT a for storing entries of type a,in which the empty stack and the push constructor are de ned in the usual way.Because of the way I've de ned the Stack class'operations,entries also need to be expressed as elements of type StackADT,so we represent them as stacks containing just the one entry.So,for example,the rule`top(Push x)=Push x EmptyStack' says that the top element of a non-empty stack is represented as the one-element stack whose only entry is the top element in question.data StackADT a=EmptyStack|Push a(StackADT a)deriving(Show,Eq)makeEntry::a->StackADT a13makeEntry x=Push x EmptyStackinstance Stack(StackADT a)wherecreateStack=EmptyStackpush(Push x EmptyStack)s=Push x spush__=error"invalid entry pushed onto stack"emptyStack EmptyStack=TrueemptyStack_=Falsetop EmptyStack=error"the stack is empty"top(Push x_)=Push x EmptyStackpop EmptyStack=error"the stack is empty"pop(Push_s)=sAs these examples show,there can be many di erent instances of any given type class, and there's nothing intrinsically better about one instance rather than another.It is your job as a designer to choose the best instance for your own purposes-it is precisely this advantage,that ADTs give you this freedom to choose the best implementation for the task at hand,that justi es the decision to generate the ADT de nition in the rst place.5.8SummaryThere are many di erent ways to implement an ADT in Haskell.•If we use the data construct to declare the ADT as an algebraic data type,the rules we worked out for the ADT's semantics turn out to be exactly the formulae we need to de ne the ADT's operations.•An alternative solution is to use Haskell's class system.Rather than de ne new data structures to represent the ADT,the class system lets us tell Haskell how to use existing data types to represent the ADT.•Whichever approach we use,however,we need to check that the function signatures all make sense-it should be possible to apply the ADT's operations one after another without unexpected type-mismatches occurring.•This can be done in di erent ways.We we can examine all of the argument and return types for our operations,and change them wherever necessary to ensure that all the types are consistent with one another.•Another approach is to remove the need for things like error messages by exploiting Haskell's error function,which allows us to generate messages as side-e ects.14。
