计算机网络的问题英文
计算机网络(第四版)课后习题(英文)+习题答案(中英文)

计算机网络(第四版)英文原版1.1 Uses of Computer Networks

1.1.1 Business Applications
Many companies have a substantial number of computers. For example, a company may have separate computers to monitor production, keep track of inventories, and do the payroll. Initially, each of these computers may have worked in isolation from the others, but at some point, management may have decided to connect them to be able to extract and correlate information about the entire company.
(完整版)计算机网络课后作业以及答案(中英文对照)

Chapter11-11.What are two reasons for using layered protocols?(请说出使用分层协议的两个理由)答:通过协议分层可以把设计问题划分成较小的易于处理的片段。
分层意味着某一层的协议的改变不会影响高层或低层的协议。
1-13. What is the principal difference between connectionless communication and connection-oriented communication?(在无连接通信和面向连接的通信两者之间,最主要的区别是什么?)答:主要的区别有两条。
其一:面向连接通信分为三个阶段,第一是建立连接,在此阶段,发出一个建立连接的请求。
只有在连接成功建立之后,才能开始数据传输,这是第二阶段。
接着,当数据传输完毕,必须释放连接。
而无连接通信没有这么多阶段,它直接进行数据传输。
其二:面向连接的通信具有数据的保序性,而无连接的通信不能保证接收数据的顺序与发送数据的顺序一致。
1-20. A system has an n-layer protocol hierarchy. Applications generate messages of length M bytes. At each of the layers, an h-byte header is added. What fraction of the network bandwidth is filled with headers?(一个系统有n层协议的层次结构。
应用程序产生的消息的长度为M字节。
在每一层上需要加上一个h字节的头。
请问,这些头需要占用多少比例的网络带宽)答:hn/(hn+m)*100%1-28. An image is 1024 x 768 pixels with 3 bytes/pixel. Assume the image is uncompressed. How long does it take to transmit it over a 56-kbps modem channel? Over a 1-Mbps cable modem? Over a 10-Mbps Ethernet? Over 100-Mbps Ethernet?(一幅图像的分辨率为1024 x 768像素,每个像素用3字节来表示。
关于计算机优点缺点的英语作文

关于计算机优点缺点的英语作文英文回答:Advantages of Computers:Increased productivity and efficiency: Computers enable tasks to be completed faster and more accurately, freeing up time for other activities.Improved communication: Computers facilitate seamless communication across vast distances through email, instant messaging, and video conferencing.Access to vast information: The internet provides access to an ocean of knowledge, allowing individuals to research, learn, and stay informed.Enhanced learning and education: Computers offer interactive multimedia platforms that make learning more engaging and accessible.Entertainment and recreation: Computers provide a wide range of entertainment options, including gaming, streaming videos, and social media platforms.Increased connectivity and socialization: Social media and online communication tools enable people to stay connected with friends, family, and colleagues worldwide.Scientific advancements and innovation: Supercomputers and simulations accelerate scientific research and technological breakthroughs.Disadvantages of Computers:Addiction and excessive use: Excessive computer use can lead to physical and mental health issues such as obesity, eye strain, and social isolation.Privacy concerns: Personal information stored on computers is vulnerable to hacking and data breaches.Environmental impact: Computers and their manufacturing contribute to electronic waste and environmental pollution.Job displacement: Automation and artificial intelligence powered by computers can replace certain jobs, leading to job loss in some sectors.Reduced human interaction: Over-reliance on computers can diminish face-to-face communication and social interactions.Digital divide: Unequal access to computers and technology perpetuates economic and social disparities.Security risks: Computers and networks are susceptible to cyber attacks, viruses, and malware that can compromise data and systems.中文回答:计算机的优点:提高生产力和效率,计算机使任务能够更快、更准确地完成,从而腾出时间进行其他活动。
计算机网络习题(有答案)

一、填空题1.计算机网络是现代通信技术和计算机技术密切结合的产物。
2.计算机网络的定义为一个互连的自主的计算机集合。
3.计算机网络按规模分为局域网,城域网,广域网。
4.按带宽分为窄带网和宽带网。
5.局域网的英文缩写为 LAN ,城域网的英文缩写为 MAN ,广域网的英文缩写为 WAN 。
6.在某层上进行通信所使用的规则的集合称为该层的协议。
网络各层协议按层次顺序排列而成的协议称为网络的协议栈。
7.对一个网络进行层次结构的划分时应做到:各层功能明确、相互独立;层间接口清晰、穿越接口的信息量尽可能少。
8.两个最重要的网络参考模型是__OSI/RM______模型和_TCP/IP_______。
9.OSI参考模型分为__7___层,从低到高依次是物理层、数据链路层、网络层、传输层、会话层、表示层和应用层。
10.ISO的全称是___国际标准化组织 ______,在1984年正式颁布了一个称为__开放系统互联参考模型___。
该模型包含七个层次。
11.计算机网络采用___分层结构 _____。
每层完成一定的___功能 _____,每层都向它的上层提供一定的____服务 ____,而将如何实现服务的细节对上层屏蔽,即低层协议对高层而言是透明的。
相邻两层之间为___层间接口 _____。
对等层用户通话时所必须遵守的规则称为___对等层协议_____。
12.协议由_语义,语法,时序等三部分组成。
13.TCP/IP协议分为___4__层,从低到高依次是___网络接口层_______,___网间网层_____________, __传输层________,___应用层________________。
14.数据通信的几个主要指标有___信号传输速率、数据传输速率、信道容量、误码率。
15.RS-232C机械特性规定了使用一个__25_____芯或__9_____芯接头。
16.RS-232C机械特性规定了使用一个__25_____芯标准连接器,电气特性规定逻辑“1”的电平为___-15____至__5_____,即采用正负15V的__负_____逻辑电平。
计算机网络自顶向下方法答案(英文第六版)

All material © copyright 1996-2012 by J.F. Kurose and K.W. Ross. All rights reserved
Chapter 1 Review ons
1. There is no difference. Throughout this text, the words “host” and “end system” are used interchangeably. End systems include PCs, workstations, Web servers, mail servers, PDAs, Internet-connected game consoles, etc. 2. From Wikipedia: Diplomatic protocol is commonly described as a set of international courtesy rules. These well-established and time-honored rules have made it easier for nations and people to live and work together. Part of protocol has always been the acknowledgment of the hierarchical standing of all present. Protocol rules are based on the principles of civility. 3. Standards are important for protocols so that people can create networking systems and products that interoperate. 4. 1. Dial-up modem over telephone line: home; 2. DSL over telephone line: home or small office; 3. Cable to HFC: home; 4. 100 Mbps switched Ethernet: enterprise; 5. Wifi (802.11): home and enterprise: 6. 3G and 4G: wide-area wireless. 5. HFC bandwidth is shared among the users. On the downstream channel, all packets emanate from a single source, namely, the head end. Thus, there are no collisions in the downstream channel. 6. In most American cities, the current possibilities include: dial-up; DSL; cable modem; fiber-to-the-home. 7. Ethernet LANs have transmission rates of 10 Mbps, 100 Mbps, 1 Gbps and 10 Gbps. 8. Today, Ethernet most commonly runs over twisted-pair copper wire. It also can run over fibers optic links. 9. Dial up modems: up to 56 Kbps, bandwidth is dedicated; ADSL: up to 24 Mbps downstream and 2.5 Mbps upstream, bandwidth is dedicated; HFC, rates up to 42.8 Mbps and upstream rates of up to 30.7 Mbps, bandwidth is shared. FTTH: 2-10Mbps upload; 10-20 Mbps download; bandwidth is not shared. 10. There are two popular wireless Internet access technologies today: a) Wifi (802.11) In a wireless LAN, wireless users transmit/receive packets to/from an base station (i.e., wireless access point) within a radius of few tens of meters. The base station is typically connected to the wired Internet and thus serves to connect wireless users to the wired network. b) 3G and 4G wide-area wireless access networks. In these systems, packets are transmitted over the same wireless infrastructure used for cellular telephony, with the base station thus being managed by a telecommunications provider. This provides wireless access to users within a radius of tens of kilometers of the base station.
计算机网络试卷及答案-英文版
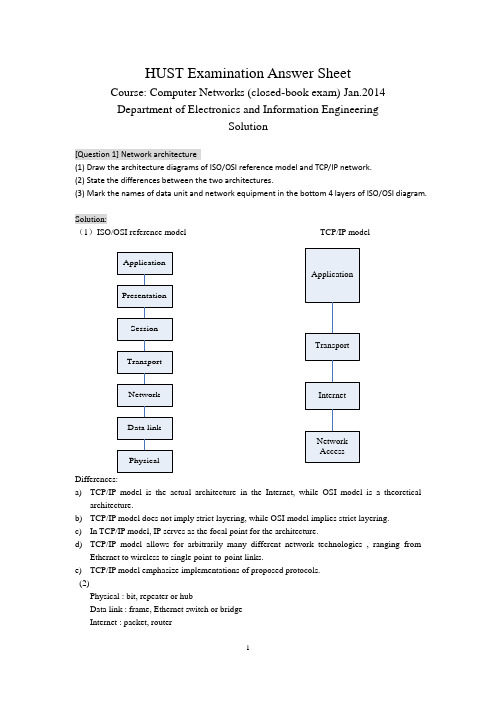
HUST Examination Answer SheetCourse: Computer Networks (closed-book exam) Jan.2014 Department of Electronics and Information EngineeringSolution[Question 1] Network architecture(1) Draw the architecture diagrams of ISO/OSI reference model and TCP/IP network. (2) State the differences between the two architectures.(3) Mark the names of data unit and network equipment in the bottom 4 layers of ISO/OSI diagram.Solution:(1)ISO/OSI reference model TCP/IP modelDifferences:a) TCP/IP model is the actual architecture in the Internet, while OSI model is a theoreticalarchitecture.b) TCP/IP model does not imply strict layering, while OSI model implies strict layering. c) In TCP/IP model, IP serves as the focal point for the architecture.d) TCP/IP model allows for arbitrarily many different network technologies , ranging fromEthernet to wireless to single point-to-point links.e) TCP/IP model emphasize implementations of proposed protocols. (2)Physical : bit, repeater or hubData link : frame, Ethernet switch or bridge Internet : packet, routerTransport : message, gateway[Question 2] Principles of network designSelect ONE of the following principles, tell its main ideas and provide an example. (1) Keep it simple and stupid(2) Complex edge and simple core (3) Smart sender and dumb receiverSolution:(1) KISS: Keep It Simple and StupidIt means that you should make things simple in the designing. One example following it : Ethernet(2) Complex edge and simple coreIt means that the hosts are very complex and have many functions while the nodes are very simple and have few functions.One example following it : The design of router, or the functions of TCP and IP(3) Smart sender and dumb receiverIt means that the function of sender is more complex than that of the receiver, which is help to improve the robustness and performance of communication protocol. One example following it: The flow control of TCP protocol[Question 3] Error detection(1) Tell the main idea of error detection and error correction in communication.(2) Given the CRC polynomial x 4 + x 3 + 1, if the original message is 10110011010, what is the CRC message to send?(3) Suppose the first bit of the message in (2) is inverted due to the noise in transmission. How can the receiver detect it via CRC verification?Solution:(1)1087431()M x x x x x x x =+++++, 43()1C x x x =++. So k=4.a) Multiply M(x) by 2kto get 141211875()T x x x x x x x =+++++,b) Then divide T(x) by C(x) to get the remainder 0000.c) The message that should be transmitted is 101100110100000.(2)The message received is 001100110100000.Divide it by C(x), then the remainder is 1100.So it is not divisible by C(x).So the receiver knows that an error has occurred.(1) What are the essential components to realize reliable transmission?(2) Suppose two computers are communicated via Stop-and-wait protocol. The link bandwidth is 5kbps, and the one-way propagation delay is 20ms. To reach 80% or higher link utilization, what is the minimal frame size for this communication?(3) If it is upgraded to Sliding-Window protocol. To reach the same goal with (2), what is the minimal window size, how many bits are required to describe the frame sequence in window? (Suppose the frame size is 1 or 100Byte)Solution:(1)ACK, and timerActual_throughput = Data / Total_DelayTotal_Delay = RTT + Data / BWLink_Utilization = 100 * Actual_throughput / BWSo: Data/throughput = RTT + Data/BW(BW/throughput - 1) Data = BW*RTTData = BW*RTT/(1/Utilization -1)For the stop-and-wait protocol, for each RTT only one frame is sent,Thus Frame_size = Data = BW*RTT/(1/Utilization - 1) = 5kbps * 40ms / (1/0.8 - 1)= 200 bit / 0.25 = 800 bit = 100 ByteIf the students ignore the data transmission delay, their answer isframe_size = BW*RTT*Utilization = 5000 bit/sec * 40 / 1000 sec * 0.8 = 160 bit = 20 ByteIn this case, at least -2 score.(3)For the sliding-window protocol, in each RTT the data window can be transmitted at most.Thus Window_size = Data = BW*RTT/(1/Utilization - 1) = 5kbps * 40ms / (1/0.8 - 1)= 200 bit / 0.25 = 800 bit = 100 ByteIf the frame size is 100Byte, 1 frames are allowed.To indicate the frames in both sides of sender and receiver, the sequence number should describe 2 frames, thus the [log2(2) ]=1 bitIf the students ignore the data transmission delay, their answer iswindow_size = BW*RTT*Utilization = 5000 bit/sec * 40 / 1000 sec * 0.8 = 160 bit = 20 ByteIf the frame size is 100Byte, 1 frames are allowed.To indicate the frames in both sides of sender and receiver, the sequence number should describe 2 frames, thus the [log2(2) ]=1 bitIn this case, at least -2 score.(1) What is the main idea of CSMA/CD (Carrier Sense Multiple Access/Collision Detection) in traditional Ethernet? Can it be deployed for wireless local network, why?(2) Suppose one traditional Ethernet has 1km cable, the signal propagation speed is 2*105km/s, and the transmission rate is designed to be 100Mbps. What is the minimal frame size to support carrier sensing?Solution:(1) the main idea of CSMA/CD include two parts. One is carrier sensing, which means the node should detect the channel before sending any data. If the node finds the channel is idle, it begins to transmit. Otherwise, the node stop for next round. The second issues is collision detection, which means the node should detect the channel in the duration of its data transmission. If the node finds the channel become busy, or in other word, there is a collision, it should stop transmitting immediately.CSMA/CD cannot be deployed in wireless LAN, because the wireless radio transmitter and receiver can not work in dual mode. The wireless node cannot detect collision when it is transmitting data.(2)the minimal frame should be transmitted throughout the whole traditional Ethernet.Thus t = frame_size / transmit_rate = 2 * cable_length / prop_speed.Frame_size = 100 * 106 bits/sec * 2 * 103 m / (2 * 108)m/sec = 1000 bits = 125 Byte[Question 6] Switched network(1) What are the differences between circuit switching and packet switching?(2) For the following linear topology network, each link has 2ms propagation delay and 4 Mbps bandwidth.A B C DIf we use circuit switching, circuit setup requires a 1KB message to make one round-trip on the path, which incurs a 1ms delay at each switch after the message has been completely received. Then we can send the file as one contiguous bit stream. What is the delay for circuit switching to transmit n-byte from A to D?(3) If we use packet switching in the network of (2), we can break the file into 1KB packets, which has 24byte header and 1000byte payload. The switch takes 1ms process delay after receiving the packet, and then sent it continuously. What is the condition for packet switching to have less delay performance than circuit switching?Solution:(1)(2)T pkt = Packet_Size / Bandwidth = 1 KB / 4Mbps = 1024 *8 / (4 * 106) = 2.048 ms T p = 2 ms, T s = 1 ms,T t = n B / 4MbpsIn circuit switching, Total time duration:D = Singling_Delay + Transmission_Delay = 2 * Packet_Duration + Transmission_Delay = 2 * (T pkt * 2 + T p * 3 + T s * 2 + T pkt ) + (T p * 3 + T t ) = T pkt * 6 + T p * 9 + T s * 4 + T tThus, D = 2.048 * 6 + 2 * 9 + 1 * 4 + n * 8 bits / 4Mbps = 34.288 (ms) + 2n (us)(3)Main ideaThe reliability provided by endhost The reliability provided by thenetwork Information in packet Every packet has its dest-addrin header Every packet has its temp VCIlocally Forwarding action inswitch Every packet was treatedindependentlyThe packets are processed inthe manner of VCPackets received indestinationNot in sequenceIn sequenceT pkt = Packet_Size / Bandwidth = 1 KB / 4Mbps = 1024 *8 / (4 * 106) = 2.048 msT p = 2 ms,T s = 1 ms,T t = 1.024 * n B / 4MbpsIn packet switching, Total time duration:D = Delay_at_Switch * Switch_Num + Delay_at_last_hop= (T p + T pkt +T s)*2 + (T p + T t )= T pkt * 2 + T p * 3 + T s * 2 + T tThus, D = 2.048 * 2 + 2 * 3 + 1 * 2 + 1.024 * n B / 4Mbps= 12.096 (ms) + 2.048 n (us)In order to make34.288 (ms) + 2n (us) > 12.096 (ms) + 2.048 n (us)Thus 22.192(ms) > 0.048 n(us)n < 22.192 * 1000 / 0.048 = 462333 Byte = 451.5 KB[Question 7] Ethernet Switch(1) What are the differences between hub and switch in Ethernet?(2) Suppose one server and nine clients are connected via hub in 10Mbps Ethernet, what is the maximal bandwidth for the client-server connection?(3) If the hub is upgraded to switch, can the client-server connection obtain more bandwidth? if can, how much is it?Solution:(1)hub works in Layer2, it works as the shared media and relays the frames to all the nodes connecting to hub. Switch works in Layer2, it forwards the frames to the specific node according to the destination address embedded in the frame header.(2)the max bandwidth in client-server connection is 10Mbps/(1+9)= 1Mbps(3)the max bandwidth in client-server connection is 10Mbps/9 = 1.1111MbpsAdditional 0.1111 Mbps is obtained for each connection.[Question 8] Router(1) Somebody says that, ``the only difference between switch and router is that they do switch function based on the address in different layers.’’ Is it correct? Why?(2) If we obtain the following information from one router. What kind of routing protocol does itSolution:(1)it is not fully correct. The part talking about the forwarding function is correct, while it is not the only difference. Another but not the last difference is that, router has more functions on control plane, which do routing and find the paths for packets.(2)The routing protocol is RIP.The routing table is:Destination Next hop Interface192.168.1.0/24 * Fa 0/4192.168.2.0/24 * Fa 0/6192.168.10.0/24 192.168.1.1 Fa 0/4192.168.30.0/24 192.168.2.2 Fa 0/6[Question 9] Routing algorithm(1) State the main differences between distance vector routing and link state routing.(2) For the network given in the following figure, provide the steps of forward search in Dijkstra algorithm for node A finding the shortest path to node ESolution:(1) The idea of distance vector routing is to tell the neighbors about the learned topology to all the nodes in the network. The idea of link state routing is to tell all the nodes in network about the neighborhood topology.Step 1 2 3 4 5 6 7 8 9Confirmed (A,0,-) (A,0,-) (A,0,-)(D,2,D)(A,0,-)(D,2,D)(A,0,-)(D,2,D)(B,4,D)(A,0,-)(D,2,D)(B,4,D)(A,0,-)(D,2,D)(B,4,D)(E,6,D)(A,0,-)(D,2,D)(B,4,D)(E,6,D)(A,0,-)(D,2,D)(B,4,D)(E,6,D)(C,7,D)Tentative (B,5,B)(D,2,D)(B,5,B) (B,4,D)(E,7,D)(E,7,D)(E,6,D)(C,8,D)(C,8,D) (C,7,D)A→E A→D→EA→D→B→EA→D→B→E[Question 10] IP address allocationA company has one C class IP address of 200.1.1.*. It has four departments.(1) If each department has less than 25 computers. Provide a kind of IP address allocation. Give the network address, subnet mask, and the available IP address range for each department. (2) If the four departments have 72, 35, 34, 20 computers respectively. Provide the IP address allocation scheme again.Solution:(1)Since each department has less than 25 computers, even considering the additional two more IP address for gateway and broadcast, the 64-computer subnet is enough for them.One IP address allocation scheme is to even divide the 256 IP addresses into 4 subnets, each subnet allows 64 hosts.Another IP address allocation scheme is to even divide the 256 IP addresses into 4 subnets, each subnet allows 32 hosts.(2) Since one of the department has more requirements than 64, then the even distribution scheme[Question 11] TCP protocol(1) Somebody says that, ``because of the reliable transmission service in layer 2, there is no need to provide such service again within TCP protocol in layer 4’’. Is it correct? Why?(2) State the main rules of TCP connection setup according to the following figure. Explain every word and number in the figure.Solution:(1) It is wrong. TCP is based on the un-reliable IP layer, which only provides best effort service. If TCP wants to provide reliable transmission service, it has to realize this by itself.(2)TCP use three hand-shakes to setup the connection.According to the figure, there are two nodes. The sender is with IP address of 192.168.1.163 and the receiver 192.168.1.165 respectively.●At first, the sender send a request ``SYN’’to the receiver to setup the connection. Thismessage is with the sequence number of 424CF1DC;●Secondly, the receiver reply an acknowledgment message ``SYN/ACK’’ to the sender. Thismessage has two sequence numbers. The seq in the ACK is 424CF1DD, which is to confirm the last ``SYN’’ from sender. The seq in the SYN is 30318555, which is a new message from the receiver.●Thirdly, the sender reply an acknowledgment message ``ACK’’ to the receiver. The seq in theACK is 30318556, which is to confirm the last ``SYN’’ from receiver.In the end, both the sender and receiver knows that the other side is ready for this TCP connection.[Question 12] TCP congestion control(1) Both flow control and congestion control in TCP are realized by window based packet control. How can TCP get the window sizes in these two mechanisms?(2) Assume that TCP implements an extension that allows window sizes much larger than 64 KB. Suppose that you are using this extended TCP over a 1Gbps link with a latency of 150ms. TCP packet size is 1KB, and the max receive window is 1 MB. Suppose there is no real congestion and packet loss in transmission. How many RTTs does it take until slow start opens the send window to 1 MB? How long does it take to send the complete file? ( Suppose file size is 10MB )Solution:(1) In flow control, TCP sender knows the window size by the field of advertise-window replied from the receiver. In congestion control, TCP sender learns the window size adaptively by AIMD( Additive Increase and Multiplicative Decrease) mechanism responding to the packet lossevent.(2)When TCP realizes congestion control mechanism, its effective send window size will be min (CongestionWindow, AdvertizedWindow). In original design of TCP header, the field of AdvertizedWindow is 16 bit, which is 216=26*210=64 KB. So the maximum effective window of original TCP sender is 64KB. The assumption of the first sentence in this question relaxes such constraint for TCP.In slow start, the send window starts from w0=1 packet, which is 1 KB. For each RTT after a successful transmission, the window size will be doubled. After i RTT, it will be 2i * w0. Let 2i * 1KB = 1MB, soi = log2(1MB/1KB) = log2(210) = 10.It will take 10 RTTs to reach 1MB send window.Case 1: if the receiver window remains as 1MBIn the first 10 RTTs, total (1 + 2 + 4 + … + 210) * 1KB has been transmitted.Which is (211 - 1) * 1KB = 2 MB - 1 KB, the rest file is 10MB - (2MB - 1KB) = 8MB + 1KBIn the reset transmission, each RTT can only support 1MB transmission.Thus, additional 9 RTTs are required. Total 19 RTT = 19 * 150ms = 2.85 sCase 2: if the receiver window can be changed.Since there is no congestion and loss, the maximum send window will be the bandwidth * delay for this TCP connection.w max= 1G bps * 150ms = 109 * 150 * 10-3= 150 *106 bit = 18.75 * 106 byte = 17.88 MB.So, this 10 MB file can be transferred before reaching w max. In another word, it can be sent in its slow start phase. Assume x RTT is required to send this file, then:(1 + 2 + 4 + … + 2x) * 1KB ≥ 10 MB2 * 2x–1 ≥ 10 * 1024x ≥ log2(10241) – 1 = 12.3Thus x = 13, it will take 13 RTTs to transfer this file. 13RTT = = sTotal delay = 13RTT + Filesize/BW = 13 * 150ms+ 10MB / 1Gbps =1.95 + 0.08 * 1.024^2=2.03 s11。
计算机网络英文复习题

计算机⽹络英⽂复习题、英译汉(10分)1.TCP(Transmission Control Protocol) 传输控制协议2.IP(Internet Protocol) 互联⽹协议3.RFC(Requests for comments) 请求评议4.SMTP(Simple Mail Transfer Protocol) 简单邮件传输协议5.Congestion-control 拥塞控制6.Flow control 流控制7.UDP (User Datagram Protocol) ⽤户数据报协议8.FTP(File Transfer Protocol) ⽂件传输协议9.HTTP( Hyper-Text Transfer Protocol ) 超⽂本传输协议10.TDM 时分复⽤11.FDM 频分复⽤12.ISP(Internet Service Provider) 互联⽹服务提供商13.DSL(Digital Subscriber Line) 数字⽤户线路14.DNS(Domain Name System) 域名系统15.ARQ(Automatic Repeat Request) ⾃动重发请求16.ICMP(Internet Control Message Protocol) ⽹间控制报⽂协议17.AS(Autonomous Systems) ⾃制系统18.RIP(Routing Information Protocol)\ 路由信息协议19.OSPF(Open Shortest Path First) 开放最短路径优先20.BGP (Border Gateway Protocol) 边界⽹关协议21.HFC 光纤同轴电缆混合⽹22.CRC(Cyclic Redundancy Check) 循环冗余检验23.CSMA/CD 带冲突检测的载波侦听多路存取24.ARP 地址解析协议25.RARP 反向地址解析协议26.DHCP 动态主机配置协议27.RTT 循环时间28.IETF(P5)互联⽹⼯程任务组29.URL(P88)统⼀资源定位30.API应⽤程序编程接⼝31.MIME多⽤途互联⽹邮件扩展1. DSL divides the communication link between the home and the ISP into three nonoverlapping frequency bands, a upstream channel is in _A_________.A)50 kHz to 1MHz band B) 1MHz to 2MHz bandC)4 kHz to 50kHz band D) 0 to 4kHz band2. As a data packet moves from the upper to the lower layers, headers are A .A) Added; B) subtracted; C) rearranged; D) modified3. What is the main function of the network layer? DA) node-to-node delivery; B) process-to-process message deliveryC) synchronization; D) updating and maintenance of routingtables4. Which of the following is the default mask for the address 168.0.46.201? BA) 255.0.0.0; B) 255.255.0.0; C) 255.255.255.0; D) 255.255.255.2555.A router reads theaddress on a packet to determine the next hop. AA) IP ; B) MAC; C) source; D)ARP6 .Which device can’t isolates the departme ntal collision domains. AA) Hub; B) switch; C) router; D) A and B7. Input port of a router don’t perform ____D____ functions.A) the physical layer functions B) the data link layer functionsC) lookup and forwarding function D) network management8. HTTP has a mechanism that allows a cache to verify that its objects are up to date. The mechanism is DA) persistent connections B) cookies C) Web Caching D) conditional GET9. A protocol layer can be implemented in ___D_____.A) software B) hardware C) a combination of the software and hardware D) All of the above10. A protocol has three important factors, they are_A______.A)syntax, semantics, order B) syntax, semantics, layerC)syntax, semantics, packet D) syntax , layer, packet11. There are two broad classes of packet-switched networks: datagram networks and virtual-circuit networks. The virtual-circuit networks forward packets in their switches use ___D___.A) MAC addresses B) IP addressesC) e-mail addresses D) virtual-circuit numbers12. TCP service model doesn’t provide ___D_______service.A) reliable transport service B) flow control serviceC) congestion-control service D) guarantee a minimum transmission rate service.13. Usually elastic applications don’t include____B______.A) Electronic mail B) Internet telephony14. A user who uses a user agent on his local PC receives his mail sited in a mail server by using _B___ protocol.A)SMTP B) POP3C)SNMP D) FTP15. Considering sliding-window protocol, if the size of the transmitted window is N and the size of the receiving window is 1,the protocol is BA) stop-and-wait protocol B) Go-Back-N protocolC) selective Repeat protocol D) alternating-bit protocol16. which IP address is effective___B______.A) 202,131,45,61 B) 126.0.0.1C) 192.268.0.2 D) 290.25.135.1217. if IP address is 202.130.191.33, subnet mask is 255.255.255.0,then subnet prefix is__D_____A) 202.130.0.0 B) 202.0.0.0C) 202.130.191.33 D)202.130.191.018.The command Ping s implemented with __B______messagesA) DNS B) ICMPC) IGMP D) RIP19. Which layer-function is mostly implemented in an adapter? __A________A) physical layer and link layer B) network layer and transport layerC)physical layer and network layer D) transport layer and application layer20. If a user brings his computer from Chengdu to Peking, and accesses Internet again. Now, __B_____ of his computer needs to be changed.A) MAC address B) IP addressC) e-mail address D) user address1. .traceroute is implemented with __B____messages.A) DNS B) ICMPC) ARP D) RIP2.A router reads the A address on a packet to determine the next hop.A. IP ;B. MAC;C. source;D.ARP3. There are two broad classes of packet-switched networks: datagram networks andvirtual-circuit networks. The virtual-circuit networks forward packets in their switches use ___D___.A) MAC addresses B) IP addressesC) e-mail addresses D) virtual-circuit numbersA) device interfaces with same subnet part of IP addressB) can’t physically reach each other without intervening a router.C)all of the devices on a given subnet having the same subnet address.D)A portion of an interface’s IP address must be determined by the subnet to which it is connected.5. if IP address is 102.100.100.32, subnet mask is 255.255.240.0,then subnet prefix is___A___A) 102.100.96.0 B) 102.100.0.0C) 102.100.48.0 D) 102.100.112.06 If a user brings his computer from chengdu to beijing, and accesses Internet again. Now,___B__ of his computer needs to be changed.A) MAC address B) IP addressC) e-mail address D) user address7.I nput port of a router don’t perform ____D___ functions.A) the physical layer functions B) the data link layer functionsC) lookup and forwarding function D) network management8.switching fabric is at the heart of a router, switching can be accomplished in a number of ways, donit include_D_A)Switching via memory B)Switching via crossbarC)Switching via a bus D) Switching via buffer9.if a host wants to emit a datagram to all hosts on the same subnet, then the datagram’s destination IP address is ___B__A)255.255.255.0 B) 255.255.255.255C)255.255.255.254 D) 127.0.0.110.The advantage of Circuit switching does not include________.A) small transmission delay B)small Processing costC) high link utilization D)no limited to format of message1.an ARP query sent to __A__A) local network B) all over the Internet.2. .packet-switching technologies that use virtual circuitsinclude__B___:A) X.25, ATM, IP B) X.25, ATM, frame relay.C) IPX, IP, ATM D) IPX, IP, TCP3. In Internet, _D_ protocol is used to report error and provide the information forun-normal cases.A) IP B) TCP C)UDP D) ICMP1.A is a Circuit-switched network.B. Datagram networkC. InternetD. virtual circuit network2.The store-and-forward delay is DA. processing delayB. queuing delayC. propagation delayD. transmission delay3.Which is not the function of connection-oriented service? DA. flow controlB. congestion controlC. error correctionD. reliabledata transfer4.The IP protocol lies in CA. application layerB. transport layerC. network layerD. link layer5.Which of the following is the PDU for application layer __B___A.datagram;B. message;C. frame;D.segment6.bandwidth is described in _B__A) Bytes per second B) Bits per secondC) megabits per millisecond D) centimeters7.A user who uses a user agent on his local PC receives his mail sited in a mail server by using __A__ protocol.A)SMTP B) POP3C)SNMP D) FTP8.As a data packet moves from the lower to the upper layers, headers are B.A)Added; B. subtracted; C. rearranged; D. modified三、填空题(每空1分,共22分 (注意:所有填空题不能写中⽂,否则中⽂答案对的情况1. link-layer address is variously called a LAN address, a MAC address, or a physical address.2 In the layered architecture of computer networking, n layer is the user of n-1 layer and the service provider of n+1 layer.A) n B) n+3 C) n+1 D) n-1四、判断题(每⼩题1分,共10分)1.√The services of TCP’s reliable data transfer founded on the services of theunreliable data transfer.2.√Any protocol that performs handshaking between the communication entitiesbefore transferring data is a connection-oriented service.3.× HOL blocking occur in output ports of router.4.√Socket is globally unique.5.√SMTP require multimedia data to be ASCII encoded before transfer.6.×The transmission delay is a function of the distance between the two routers.7.×IP address is associated with the host or router. SO one device only have one IPaddress.8. √In packet-switched networks, a session’s messages use the resources on demand, and Internet makes its best effort to deliver packets in a timely manner.9. ×UDP is a kind of unreliable transmission layer protocol, so there is not any checksum field in UDP datagram header.10.√Forwarding table is configured by both Intra and Inter-AS routing algorithmIP is a kind of reliable transmission protocol. F8.Forwarding table is configured by both Intra and Inter-AS routing algorithm.T9.Distance vector routing protocol use lsa to advertise the network which router10.RIP and OSPF are Intra-AS routing protocols T11.Packet switching is suitable for real-time services, and offers better sharing ofbandwidth than circuit switching F五、计算题(28 points)1.C onsider the following network. With the indicated link costs, use Dijkstra’s shortest-path algorithm to compute the shortest path from X to all network nodes.2 Given: an organization has been assigned the network number 198.1.1.0/24 and it needs todefine six subnets. The largest subnet is required to support 25 hosts. Please:●Defining the subnet mask; (2分) 27bits or 255.255.255.224●Defining each of the subnet numbers; which are starting from 0# (4分)198.1.1.0/27 198.1.1.32/27 198.1.1.64/27 198.1.1.96/27 198.1.1.128/27 198.1.1.160/27 198.1.1.192/27 198.1.1.224/27●Defining the subnet 2#’s broadcast address.(2分) 198.1.1.95/27Defining host addresses scope for subnet 2#. (2分) 198.1.1.65/27--198.1.1.94/273. Consider sending a 3,000-byte datagram into a link that has an MTU of 1500bytes.Suppose the original datagram is stamped with the identification number 422 .Assuming a 20-byte IP header,How many fragments are generated? What are their characteristics?(10分)。
