Exploiting Logic Simulation to Improve Simulation-based Sequential ATPG
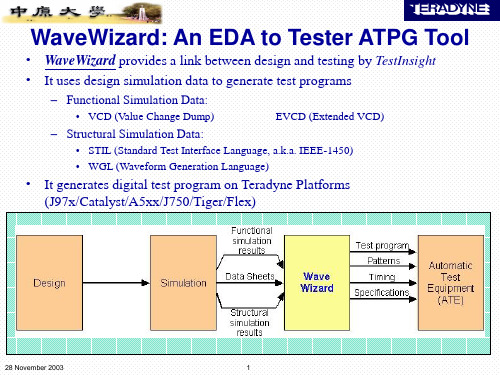
wavewizard
RTL_specset (tCYC 10ns) (clkout_tpd 0ns) (ts_data 0ns) (th_data 6ns) (data_valid 5.5ns)
9
Example Timings
WaveWizard (TestInsight):
(I_CLK100_L ro time_src: c0 (lvm_data_eset ( d0 "per_lvm_data_z*0.0000”) ( d1 "per_lvm_data_z*0.0000") ( d2 "per_lvm_data_z*0.2500") ( d3 mask) ( r1 mask) ( r2 mask) )) (O_LVM_CLK50 nrz (lvm_data_eset ( d0 mask) ( d1 mask) ( d2 mask) ( d3 mask) ( r1 "I_CLK100_H.d1+tpd_lvm_clk50") ( r2 "per_lvm_data*0.7250") ))
2
.vcd .evcd
Cyclizer
.vec file
.wgl .stil
Sampler
.sam file
A5/Catalyst/ Tiger Generator J971/J973 Generator Integra Flex/ J750 Generator
Sampling:
• • • • • • • •
clkout nrz r1 = 0ns Data nrz d0,d1 = 0ns r1 = 0ns
clkout nrz r1 = 0ns Data nrz d0,d1 = 2ns
基于强化学习的智能车间调度策略研究综述

收稿日期:2021 12 08;修回日期:2022 02 07 基金项目:浙江理工大学基本科研业务费专项资金资助项目(2021Q026)作者简介:王无双(1997 ),女,浙江绍兴人,硕士研究生,主要研究方向为强化学习、车间调度(wangwushuang_zstu@163.com);骆淑云(1986 ),女,浙江金华人,讲师,硕导,博士,主要研究方向为工业互联网.基于强化学习的智能车间调度策略研究综述王无双,骆淑云(浙江理工大学信息学院,杭州310000)摘 要:智能制造是我国制造业发展的必然趋势,而智能车间调度是制造业升级和深化“两化融合”的关键技术。
主要研究强化学习算法在车间调度问题中的应用,为后续的研究奠定基础。
其中车间调度主要包括静态调度和动态调度;强化学习算法主要包括基于值函数和AC(Actor Critic)网络。
首先,从总体上阐述了强化学习方法在作业车间调度和流水车间调度这两大问题上的研究现状;其次,对车间调度问题的数学模型以及强化学习算法中最关键的马尔可夫模型建立规则进行分类讨论;最后,根据研究现状和当前工业数字化转型需求,对智能车间调度技术的未来研究方向进行了展望。
关键词:强化学习;动态调度;静态调度;作业车间调度;流水车间调度中图分类号:TP181 文献标志码:A 文章编号:1001 3695(2022)06 002 1608 07doi:10.19734/j.issn.1001 3695.2021.12.0637ResearchonintelligentshopschedulingstrategiesbasedonreinforcementlearningWangWushuang,LuoShuyun(SchoolofInformationScience&Technology,ZhejiangSci TechUniversity,Hangzhou310000,China)Abstract:Intelligentmanufacturingisaninevitabletrendinthedevelopmentofourcountry’smanufacturingindustry,andin telligentshopschedulingisakeytechnologyfortheintegrationofmanufacturingupgradesanddeepening.Thispapermainlystudiedtheapplicationofreinforcementlearningalgorithmsinshopschedulingproblems,whichlayedthefoundationforsubse quentresearch.Shopschedulingmainlyincludedstaticschedulinganddynamicscheduling,reinforcementlearningalgorithmsmainlyincludedvalue basedfunctionsandActor Critic(AC)networks.Firstofall,thisarticledescribedtheresearchstatusofreinforcementlearningmethodsonthetwomajorissuesofJob ShopschedulingandFlow Shopschedulingingeneral.Secondly,itclassifiedtheestablishmentrulesofmathematicalmodeloftheshopschedulingproblemandthemostcriticalMarkovmodelinreinforcementlearningalgorithms.Finally,accordingtotheresearchstatusandthecurrentneedsofindustrialdigitaltransformation,itprospectedthefutureresearchdirectionofintelligentworkshopschedulingtechnology.Keywords:reinforcementlearning;dynamicscheduling;staticscheduling;Job Shopscheduling;Flow Shopscheduling0 引言车间调度问题是指如何在机器等资源有限的情况下,合理调度生产资源来安排车间生产任务,以满足一至多个优化目标的过程[1]。
Dftba

Design-For-Test Seminar
Design-For-Test
Basics
Slide
1
Design-for-Test Basics
Outline
• Meaning and importance of Design-for-Test
• DFT terminology
Has been proven effective in finding many types of faults, through years of research
Requires a test pattern to detect the stuck-at voltage and propagate the difference to the primary output
(1-t) The graphical plot follows DL=1 -Y
where t is fault coverage (Williams, IBM (1980))
t = # of faults detected / total # of faults
Defect Level
1.0 Y = 0.1
A design methodology that combines design and test to achieve maximum design testability Part of the design synthesis process Necessary due to reduced product time-tomarket and advanced technology such as:
Y = 0.01
POJ题目分类

1000 A+B Problem 送分题1001 Exponentiation 高精度1003 Hangover 送分题1004 Financial Management 送分题1005 I Think I Need a Houseboat 几何1006 Biorhythms 送分题1007 DNA Sorting 送分题1008 Maya Calendar 日期处理1010 STAMPS 搜索+DP1011 Sticks 搜索1012 Joseph 模拟/数学方法1014 Dividing 数论/DP?/组合数学->母函数?1015 Jury Compromise DP1016 Numbers That Count 送分题1017 Packets 贪心1018 Communication System 贪心1019 Number Sequence 送分题1020 Anniversary Cake 搜索1023 The Fun Number System 数论1025 Department 模拟1026 Cipher 组合数学1027 The Same Game 模拟1028 Web Navigation 送分题1031 Fence 计算几何1034 The dog task 计算几何1037 A decorative fence DP/组合数学1039 Pipe 几何1042 Gone Fishing 贪心/DP1045 Bode Plot 送分题(用物理知识)1046 Color Me Less 送分题1047 Round and Round We Go 高精度1048 Follow My Logic 模拟1049 Microprocessor Simulation 模拟1050 To the Max DP1053 Set Me 送分题1054 The Troublesome Frog 搜索1060 Modular multiplication of polynomials 高精度1061 青蛙的约会数论1062 昂贵的聘礼DP1064 Cable master DP/二分查找1065 Wooden Sticks DP1067 取石子游戏博弈论1068 Parencodings 送分题1069 The Bermuda Triangle 搜索1070 Deformed Wheel 几何1071 Illusive Chase 送分题1072 Puzzle Out 搜索1073 The Willy Memorial Program 模拟1074 Parallel Expectations DP1075 University Entrance Examination 模拟1080 Human Gene Functions DP->LCS变形1082 Calendar Game 博弈论1084 Square Destroyer 搜索?1085 Triangle War 博弈论1086 Unscrambling Images 模拟?1087 A Plug for UNIX 图论->最大流1088 滑雪DFS/DP1090 Chain ->格雷码和二进制码的转换1091 跳蚤数论1092 Farmland 几何1093 Formatting Text DP1094 Sorting It All Out 图论->拓扑排序1095 Trees Made to Order 组合数学1096 Space Station Shielding 送分题1097 Roads Scholar 图论1098 Robots 模拟1099 Square Ice 送分题1100 Dreisam Equations 搜索1101 The Game 搜索->BFS1102 LC-Display 送分题1103 Maze 模拟1104 Robbery 递推1106 Transmitters 几何1107 W's Cipher 送分题1110 Double Vision 搜索1111 Image Perimeters 搜索1112 Team Them Up! DP1113 Wall 计算几何->convex hull1119 Start Up the Startup 送分题1120 A New Growth Industry 模拟1122 FDNY to the Rescue! 图论->Dijkstra 1125 Stockbroker Grapevine 图论->Dijkstra 1128 Frame Stacking 搜索1129 Channel Allocation 搜索(图的最大独立集)1131 Octal Fractions 高精度1135 Domino Effect 图论->Dijkstra1137 The New Villa 搜索->BFS1141 Brackets Sequence DP1142 Smith Numbers 搜索1143 Number Game 博弈论1147 Binary codes 构造1148 Utopia Divided 构造1149 PIGS 图论->网络流1151 Atlantis 计算几何->同等安置矩形的并的面积->离散化1152 An Easy Problem! 数论1157 LITTLE SHOP OF FLOWERS DP1158 TRAFFIC LIGHTS 图论->Dijkstra变形1159 Palindrome DP->LCS1160 Post Office DP1161 Walls 图论1162 Building with Blocks 搜索1163 The Triangle DP1170 Shopping Offers DP1177 Picture 计算几何->同等安置矩形的并的周长->线段树1179 Polygon DP1180 Batch Scheduling DP1182 食物链数据结构->并查集1183 反正切函数的应用搜索1184 聪明的打字员搜索1185 炮兵阵地DP->数据压缩1187 陨石的秘密DP(BalkanOI99 Par的拓展)1189 钉子和小球递推?1190 生日蛋糕搜索/DP1191 棋盘分割DP1192 最优连通子集图论->无负权回路的有向图的最长路->BellmanFord 1193 内存分配模拟1194 HIDDEN CODES 搜索+DP1197 Depot 数据结构->Young T ableau1201 Intervals 贪心/图论->最长路->差分约束系统1202 Family 高精度1209 Calendar 日期处理1217 FOUR QUARTERS 递推1218 THE DRUNK JAILER 送分题1233 Street Crossing 搜索->BFS1245 Programmer, Rank Thyself 送分题1247 Magnificent Meatballs 送分题1248 Safecracker 搜索1250 T anning Salon 送分题1251 Jungle Roads 图论->最小生成树1271 Nice Milk 计算几何1273 Drainage Ditches 图论->最大流1274 The Perfect Stall 图论->二分图的最大匹配1275 Cashier Employment 图论->差分约束系统->无负权回路的有向图的最长路->Bellman-Ford1280 Game 递推1281 MANAGER 模拟1286 Necklace of Beads 组合数学->Polya定理1288 Sly Number 数论->解模线性方程组1293 Duty Free Shop DP1298 The Hardest Problem Ever 送分题1316 Self Numbers 递推同Humble Number一样1322 Chocolate 递推/组合数学1323 Game Prediction 贪心1324 Holedox Moving BFS+压缩储存1325 Machine Schedule 图论->二分图的最大匹配1326 Mileage Bank 送分题1327 Moving Object Recognition 模拟?1328 Radar Installation 贪心(差分约束系统的特例)1338 Ugly Numbers 递推(有O(n)算法)1364 King 图论->无负权回路的有向图的最长路->BellmanFord1370 Gossiping (数论->模线性方程有无解的判断)+(图论->DFS)2184 Cow Exhibition DP2190 ISBN 送分题2191 Mersenne Composite Numbers 数论2192 Zipper DP->LCS变形2193 Lenny's Lucky Lotto Lists DP2194 Stacking Cylinders 几何2195 Going Home 图论->二分图的最大权匹配2196 Specialized Four-Digit Numbers 送分题2197 Jill's Tour Paths 图论->2199 Rate of Return 高精度2200 A Card Trick 模拟2210 Metric Time 日期处理2239 Selecting Courses 图论->二分图的最大匹配2243 Knight Moves 搜索->BFS2247 Humble Numbers 递推(最优O(n)算法)2253 Frogger 图论->Dijkstra变形(和1295是一样的)2254 Globetrotter 几何2261 France '98 递推2275 Flipping Pancake 构造2284 That Nice Euler Circuit 计算几何2289 Jamie's Contact Groups 图论->网络流?2291 Rotten Ropes 送分题2292 Optimal Keypad DP2299 Ultra-QuickSort 排序->归并排序2304 Combination Lock 送分题2309 BST 送分题2311 Cutting Game 博弈论2312 Battle City 搜索->BFS2314 POJ language 模拟2315 Football Game 几何2346 Lucky tickets 组合数学2351 Time Zones 时间处理2379 ACM Rank T able 模拟+排序2381 Random Gap 数论2385 Apple Catching DP(像NOI98“免费馅饼”)2388 Who's in the Middle 送分题(排序)2390 Bank Interest 送分题2395 Out of Hay 图论->Dijkstra变形2400 Supervisor, Supervisee 图论->二分图的最大权匹配?2403 Hay Points 送分题2409 Let it Bead 组合数学->Polya定理2416 Return of the Jedi 图论->2417 Discrete Logging 数论2418 Hardwood Species 二分查找2419 Forests 枚举2421 Constructing Roads 图论->最小生成树2423 The Parallel Challenge Ballgame 几何2424 Flo's Restaurant 数据结构->堆2425 A Chess Game 博弈论2426 Remainder BFS2430 Lazy Cows DP->数据压缩1375 Intervals 几何1379 Run Away 计算几何->1380 Equipment Box 几何1383 Labyrinth 图论->树的最长路1394 Railroad 图论->Dijkstra1395 Cog-Wheels 数学->解正系数的线性方程组1408 Fishnet 几何1411 Calling Extraterrestrial Intelligence Again 送分题1430 Binary Stirling Numbers 日期处理1431 Calendar of Maya 模拟1432 Decoding Morse Sequences DP1434 Fill the Cisterns! 计算几何->离散化/1445 Random number 数据结构->碓1447 Ambiguous Dates 日期处理1450 Gridland 图论(本来TSP问题是NP难的,但这个图比较特殊,由现成的构造方法)1458 Common Subsequence DP->LCS1459 Power Network 图论->最大流1462 Random Walk 模拟+解线性方程组1463 Strategic game 贪心1466 Girls and Boys 图论->n/a1469 COURSES 贪心1475 Pushing Boxes DP1476 Always On the Run 搜索->BFS1480 Optimal Programs 搜索->BFS1481 The Die Is Cast 送分题1482 It's not a Bug, It's a Feature! 搜索->BFS1483 Going in Circles on Alpha Centauri 模拟1484 Blowing Fuses 送分题1485 Fast Food DP(似乎就是ioi2000的postoffice)1486 Sorting Slides 图论->拓扑排序1505 Copying Books DP+二分查找1510 Hares and Foxes 数论1512 Keeps Going and Going and ... 模拟1513 Scheduling Lectures DP1514 Metal Cutting 几何1515 Street Directions 图论->把一个无向连通图改造成为有向强连通图1517 u Calculate e 送分题1518 Problem Bee 几何1519 Digital Roots 送分题(位数可能很大)1520 Scramble Sort 排序1547 Clay Bully 送分题1555 Polynomial Showdown 送分题(非常阴险)1563 The Snail 送分题1601 Pizza Anyone? 搜索1604 Just the Facts 送分题1605 Horse Shoe Scoring 几何1606 Jugs 数论/搜索1631 Bridging signals DP+二分查找1632 Vase collection 图论->最大完全图1633 Gladiators DP1634 Who's the boss? 排序1635 Subway tree systems 图论->不同表示法的二叉树判同1637 Sightseeing tour 图论->欧拉回路1638 A number game 博弈论1639 Picnic Planning 图论->1641 Rational Approximation 数论1646 Double Trouble 高精度1654 Area 几何1657 Distance on Chessboard 送分题1658 Eva's Problem 送分题1660 Princess FroG 构造1661 Help Jimmy DP1663 Number Steps 送分题1664 放苹果组合数学->递推1677 Girls' Day 送分题1688 Dolphin Pool 计算几何1690 (Your)((Term)((Project))) 送分题1691 Painting A Board 搜索/DP1692 Crossed Matchings DP1693 Counting Rectangles 几何1694 An Old Stone Game 博弈论?1695 Magazine Delivery 图论->1712 Flying Stars DP1713 Divide et unita 搜索1714 The Cave 搜索/DP1717 Dominoes DP1718 River Crossing DP1719 Shooting Contest 贪心1729 Jack and Jill 图论->1730 Perfect Pth Powers 数论1732 Phone numbers DP1734 Sightseeing trip 图论->Euler回路1738 An old Stone Game 博弈论?1741 Tree 博弈论?1745 Divisibility DP1751 Highways 图论->1752 Advertisement 贪心/图论->差分约束系统1753 Flip Game 搜索->BFS1755 Triathlon 计算几何?1770 Special Experiment 树形DP1771 Elevator Stopping Plan DP1772 New Go Game 构造?1773 Outernet 模拟1774 Fold Paper Strips 几何1775 Sum of Factorials 送分题1776 T ask Sequences DP1777 Vivian's Problem 数论1870 Bee Breeding 送分题1871 Bullet Hole 几何1872 A Dicey Problem BFS1873 The Fortified Forest 几何+回溯1874 Trade on Verweggistan DP1875 Robot 几何1876 The Letter Carrier's Rounds 模拟1877 Flooded! 数据结构->堆1879 Tempus et mobilius Time and motion 模拟+组合数学->Polya定理1882 Stamps 搜索+DP1883 Theseus and the Minotaur 模拟1887 Testing the CATCHER DP1889 Package Pricing DP1893 Monitoring Wheelchair Patients 模拟+几何1915 Knight Moves 搜索->BFS1916 Rat Attack 数据结构->?1936 All in All DP?1946 Cow Cycling DP1947 Rebuilding Roads 二分1985 Cow Marathon 图论->有向无环图的最长路1995 Raising Modulo Numbers 数论->大数的幂求余2049 Finding Nemo 图论->最短路2050 Searching the Web 模拟(需要高效实现)2051 Argus 送分题(最好用堆,不用也可以过)2054 Color a Tree 贪心2061 Pseudo-random Numbers 数论2080 Calendar 日期处理2082 Terrible Sets 分治/2083 Fractal 递归2084 Game of Connections 递推(不必高精度)2105 IP Address 送分题2115 C Looooops 数论->解模线性方程2136 Vertical Histogram 送分题2165 Gunman 计算几何2179 Inlay Cutters 枚举2181 Jumping Cows 递推2182 Lost Cows ->线段树/=============================================1370 Gossiping (数论->模线性方程有无解的判断)+(图论->DFS)1090 Chain ->格雷码和二进制码的转换2182 Lost Cows ->线段树/2426 Remainder BFS1872 A Dicey Problem BFS1324 Holedox Moving BFS+压缩储存1088 滑雪DFS/DP1015 Jury Compromise DP1050 To the Max DP1062 昂贵的聘礼DP1065 Wooden Sticks DP1074 Parallel Expectations DP1093 Formatting Text DP1112 Team Them Up! DP1141 Brackets Sequence DP1157 LITTLE SHOP OF FLOWERS DP1160 Post Office DP1163 The Triangle DP1170 Shopping Offers DP1179 Polygon DP1180 Batch Scheduling DP1191 棋盘分割DP1293 Duty Free Shop DP2184 Cow Exhibition DP2193 Lenny's Lucky Lotto Lists DP2292 Optimal Keypad DP1432 Decoding Morse Sequences DP1475 Pushing Boxes DP1513 Scheduling Lectures DP1633 Gladiators DP1661 Help Jimmy DP1692 Crossed Matchings DP1712 Flying Stars DP1717 Dominoes DP1718 River Crossing DP1732 Phone numbers DP1745 Divisibility DP1771 Elevator Stopping Plan DP1776 T ask Sequences DP1874 Trade on Verweggistan DP1887 Testing the CATCHER DP1889 Package Pricing DP1946 Cow Cycling DP1187 陨石的秘密DP(BalkanOI99 Par的拓展)1485 Fast Food DP(似乎就是ioi2000的postoffice) 2385 Apple Catching DP(像NOI98“免费馅饼”) 1064 Cable master DP/二分查找1037 A decorative fence DP/组合数学1936 All in All DP?1505 Copying Books DP+二分查找1631 Bridging signals DP+二分查找1159 Palindrome DP->LCS1458 Common Subsequence DP->LCS1080 Human Gene Functions DP->LCS变形2192 Zipper DP->LCS变形1185 炮兵阵地DP->数据压缩2430 Lazy Cows DP->数据压缩1067 取石子游戏博弈论1082 Calendar Game 博弈论1085 Triangle War 博弈论1143 Number Game 博弈论2311 Cutting Game 博弈论2425 A Chess Game 博弈论1638 A number game 博弈论1694 An Old Stone Game 博弈论?1738 An old Stone Game 博弈论?1741 Tree 博弈论?2083 Fractal 递归1104 Robbery 递推1217 FOUR QUARTERS 递推1280 Game 递推2261 France '98 递推2181 Jumping Cows 递推1316 Self Numbers 递推同Humble Number一样2084 Game of Connections 递推(不必高精度) 1338 Ugly Numbers 递推(有O(n)算法)2247 Humble Numbers 递推(最优O(n)算法)1322 Chocolate 递推/组合数学1189 钉子和小球递推?1947 Rebuilding Roads 二分2418 Hardwood Species 二分查找2082 Terrible Sets 分治/1001 Exponentiation 高精度1047 Round and Round We Go 高精度1060 Modular multiplication of polynomials 高精度1131 Octal Fractions 高精度1202 Family 高精度2199 Rate of Return 高精度1646 Double Trouble 高精度1147 Binary codes 构造1148 Utopia Divided 构造2275 Flipping Pancake 构造1660 Princess FroG 构造1772 New Go Game 构造?1005 I Think I Need a Houseboat 几何1039 Pipe 几何1070 Deformed Wheel 几何1092 Farmland 几何1106 Transmitters 几何2194 Stacking Cylinders 几何2254 Globetrotter 几何2315 Football Game 几何2423 The Parallel Challenge Ballgame 几何1375 Intervals 几何1380 Equipment Box 几何1408 Fishnet 几何1514 Metal Cutting 几何1518 Problem Bee 几何1605 Horse Shoe Scoring 几何1654 Area 几何1693 Counting Rectangles 几何1774 Fold Paper Strips 几何1871 Bullet Hole 几何1875 Robot 几何1873 The Fortified Forest 几何+回溯1031 Fence 计算几何1034 The dog task 计算几何1271 Nice Milk 计算几何2284 That Nice Euler Circuit 计算几何1688 Dolphin Pool 计算几何2165 Gunman 计算几何1755 Triathlon 计算几何?1379 Run Away 计算几何->1113 Wall 计算几何->convex hull1434 Fill the Cisterns! 计算几何->离散化/1151 Atlantis 计算几何->同等安置矩形的并的面积->离散化1177 Picture 计算几何->同等安置矩形的并的周长->线段树2419 Forests 枚举2179 Inlay Cutters 枚举1025 Department 模拟1027 The Same Game 模拟1048 Follow My Logic 模拟1049 Microprocessor Simulation 模拟1073 The Willy Memorial Program 模拟1075 University Entrance Examination 模拟1098 Robots 模拟1103 Maze 模拟1120 A New Growth Industry 模拟1193 内存分配模拟1281 MANAGER 模拟2200 A Card Trick 模拟2314 POJ language 模拟1431 Calendar of Maya 模拟1483 Going in Circles on Alpha Centauri 模拟1512 Keeps Going and Going and ... 模拟1773 Outernet 模拟1876 The Letter Carrier's Rounds 模拟1883 Theseus and the Minotaur 模拟2050 Searching the Web 模拟(需要高效实现)1012 Joseph 模拟/数学方法1086 Unscrambling Images 模拟?1327 Moving Object Recognition 模拟?1893 Monitoring Wheelchair Patients 模拟+几何1462 Random Walk 模拟+解线性方程组2379 ACM Rank T able 模拟+排序1879 Tempus et mobilius Time and motion 模拟+组合数学->Polya定理1520 Scramble Sort 排序1634 Who's the boss? 排序2299 Ultra-QuickSort 排序->归并排序1008 Maya Calendar 日期处理1209 Calendar 日期处理2210 Metric Time 日期处理1430 Binary Stirling Numbers 日期处理1447 Ambiguous Dates 日期处理2080 Calendar 日期处理2351 Time Zones 时间处理1770 Special Experiment 树形DP1916 Rat Attack 数据结构->?1197 Depot 数据结构->Young T ableau1182 食物链数据结构->并查集2424 Flo's Restaurant 数据结构->堆1877 Flooded! 数据结构->堆1445 Random number 数据结构->碓1023 The Fun Number System 数论1061 青蛙的约会数论1091 跳蚤数论1152 An Easy Problem! 数论2191 Mersenne Composite Numbers 数论2381 Random Gap 数论2417 Discrete Logging 数论1510 Hares and Foxes 数论1641 Rational Approximation 数论1730 Perfect Pth Powers 数论1777 Vivian's Problem 数论2061 Pseudo-random Numbers 数论1014 Dividing 数论/DP?/组合数学->母函数?1606 Jugs 数论/搜索1995 Raising Modulo Numbers 数论->大数的幂求余2115 C Looooops 数论->解模线性方程1288 Sly Number 数论->解模线性方程组1395 Cog-Wheels 数学->解正系数的线性方程组1000 A+B Problem 送分题1003 Hangover 送分题1004 Financial Management 送分题1006 Biorhythms 送分题1007 DNA Sorting 送分题1016 Numbers That Count 送分题1019 Number Sequence 送分题1028 Web Navigation 送分题1046 Color Me Less 送分题1053 Set Me 送分题1068 Parencodings 送分题1071 Illusive Chase 送分题1096 Space Station Shielding 送分题1099 Square Ice 送分题1102 LC-Display 送分题1107 W's Cipher 送分题1119 Start Up the Startup 送分题1218 THE DRUNK JAILER 送分题1245 Programmer, Rank Thyself 送分题1247 Magnificent Meatballs 送分题1250 T anning Salon 送分题1298 The Hardest Problem Ever 送分题1326 Mileage Bank 送分题2190 ISBN 送分题2196 Specialized Four-Digit Numbers 送分题2291 Rotten Ropes 送分题2304 Combination Lock 送分题2309 BST 送分题2390 Bank Interest 送分题2403 Hay Points 送分题1411 Calling Extraterrestrial Intelligence Again 送分题1481 The Die Is Cast 送分题1484 Blowing Fuses 送分题1517 u Calculate e 送分题1547 Clay Bully 送分题1563 The Snail 送分题1604 Just the Facts 送分题1657 Distance on Chessboard 送分题1658 Eva's Problem 送分题1663 Number Steps 送分题1677 Girls' Day 送分题1690 (Your)((Term)((Project))) 送分题1775 Sum of Factorials 送分题1870 Bee Breeding 送分题2105 IP Address 送分题2136 Vertical Histogram 送分题1555 Polynomial Showdown 送分题(非常阴险) 2388 Who's in the Middle 送分题(排序)1519 Digital Roots 送分题(位数可能很大)1045 Bode Plot 送分题(用物理知识)2051 Argus 送分题(最好用堆,不用也可以过) 1011 Sticks 搜索1020 Anniversary Cake 搜索1054 The Troublesome Frog 搜索1069 The Bermuda Triangle 搜索1072 Puzzle Out 搜索1100 Dreisam Equations 搜索1110 Double Vision 搜索1111 Image Perimeters 搜索1128 Frame Stacking 搜索1142 Smith Numbers 搜索1162 Building with Blocks 搜索1183 反正切函数的应用搜索1184 聪明的打字员搜索1248 Safecracker 搜索1601 Pizza Anyone? 搜索1713 Divide et unita 搜索1129 Channel Allocation 搜索(图的最大独立集)1190 生日蛋糕搜索/DP1691 Painting A Board 搜索/DP1714 The Cave 搜索/DP1084 Square Destroyer 搜索?1010 STAMPS 搜索+DP1194 HIDDEN CODES 搜索+DP1882 Stamps 搜索+DP1101 The Game 搜索->BFS1137 The New Villa 搜索->BFS1233 Street Crossing 搜索->BFS2243 Knight Moves 搜索->BFS2312 Battle City 搜索->BFS1476 Always On the Run 搜索->BFS1480 Optimal Programs 搜索->BFS1482 It's not a Bug, It's a Feature! 搜索->BFS 1753 Flip Game 搜索->BFS1915 Knight Moves 搜索->BFS1017 Packets 贪心1018 Communication System 贪心1323 Game Prediction 贪心1463 Strategic game 贪心1469 COURSES 贪心1719 Shooting Contest 贪心2054 Color a Tree 贪心1328 Radar Installation 贪心(差分约束系统的特例)1042 Gone Fishing 贪心/DP1752 Advertisement 贪心/图论->差分约束系统1201 Intervals 贪心/图论->最长路->差分约束系统1097 Roads Scholar 图论1161 Walls 图论1450 Gridland 图论(本来TSP问题是NP难的,但这个图比较特殊,由现成的构造方法)2197 Jill's Tour Paths 图论->2416 Return of the Jedi 图论->1639 Picnic Planning 图论->1695 Magazine Delivery 图论->1729 Jack and Jill 图论->1751 Highways 图论->1122 FDNY to the Rescue! 图论->Dijkstra1125 Stockbroker Grapevine 图论->Dijkstra1135 Domino Effect 图论->Dijkstra1394 Railroad 图论->Dijkstra1158 TRAFFIC LIGHTS 图论->Dijkstra变形2395 Out of Hay 图论->Dijkstra变形2253 Frogger 图论->Dijkstra变形(和1295是一样的)1734 Sightseeing trip 图论->Euler回路1466 Girls and Boys 图论->n/a1515 Street Directions 图论->把一个无向连通图改造成为有向强连通图1635 Subway tree systems 图论->不同表示法的二叉树判同1275 Cashier Employment 图论->差分约束系统->无负权回路的有向图的最长路->Bellman-Ford1274 The Perfect Stall 图论->二分图的最大匹配1325 Machine Schedule 图论->二分图的最大匹配2239 Selecting Courses 图论->二分图的最大匹配2195 Going Home 图论->二分图的最大权匹配2400 Supervisor, Supervisee 图论->二分图的最大权匹配?1637 Sightseeing tour 图论->欧拉回路1383 Labyrinth 图论->树的最长路1094 Sorting It All Out 图论->拓扑排序1486 Sorting Slides 图论->拓扑排序1149 PIGS 图论->网络流2289 Jamie's Contact Groups 图论->网络流?1192 最优连通子集图论->无负权回路的有向图的最长路->BellmanFord 1364 King 图论->无负权回路的有向图的最长路->BellmanFord1985 Cow Marathon 图论->有向无环图的最长路1087 A Plug for UNIX 图论->最大流1273 Drainage Ditches 图论->最大流1459 Power Network 图论->最大流1632 Vase collection 图论->最大完全图2049 Finding Nemo 图论->最短路1251 Jungle Roads 图论->最小生成树2421 Constructing Roads 图论->最小生成树1026 Cipher 组合数学1095 Trees Made to Order 组合数学2346 Lucky tickets 组合数学1286 Necklace of Beads 组合数学->Polya定理2409 Let it Bead 组合数学->Polya定理1664 放苹果组合数学->递推。
四大安全会议论文题目

2009and2010Papers:Big-4Security ConferencespvoOctober13,2010NDSS20091.Document Structure Integrity:A Robust Basis for Cross-site Scripting Defense.Y.Nadji,P.Saxena,D.Song2.An Efficient Black-box Technique for Defeating Web Application Attacks.R.Sekar3.Noncespaces:Using Randomization to Enforce Information Flow Tracking and Thwart Cross-Site Scripting Attacks.M.Van Gundy,H.Chen4.The Blind Stone Tablet:Outsourcing Durability to Untrusted Parties.P.Williams,R.Sion,D.Shasha5.Two-Party Computation Model for Privacy-Preserving Queries over Distributed Databases.S.S.M.Chow,J.-H.Lee,L.Subramanian6.SybilInfer:Detecting Sybil Nodes using Social Networks.G.Danezis,P.Mittal7.Spectrogram:A Mixture-of-Markov-Chains Model for Anomaly Detection in Web Traffic.Yingbo Song,Angelos D.Keromytis,Salvatore J.Stolfo8.Detecting Forged TCP Reset Packets.Nicholas Weaver,Robin Sommer,Vern Paxson9.Coordinated Scan Detection.Carrie Gates10.RB-Seeker:Auto-detection of Redirection Botnets.Xin Hu,Matthew Knysz,Kang G.Shin11.Scalable,Behavior-Based Malware Clustering.Ulrich Bayer,Paolo Milani Comparetti,Clemens Hlauschek,Christopher Kruegel,Engin Kirda12.K-Tracer:A System for Extracting Kernel Malware Behavior.Andrea Lanzi,Monirul I.Sharif,Wenke Lee13.RAINBOW:A Robust And Invisible Non-Blind Watermark for Network Flows.Amir Houmansadr,Negar Kiyavash,Nikita Borisov14.Traffic Morphing:An Efficient Defense Against Statistical Traffic Analysis.Charles V.Wright,Scott E.Coull,Fabian Monrose15.Recursive DNS Architectures and Vulnerability Implications.David Dagon,Manos Antonakakis,Kevin Day,Xiapu Luo,Christopher P.Lee,Wenke Lee16.Analyzing and Comparing the Protection Quality of Security Enhanced Operating Systems.Hong Chen,Ninghui Li,Ziqing Mao17.IntScope:Automatically Detecting Integer Overflow Vulnerability in X86Binary Using Symbolic Execution.Tielei Wang,Tao Wei,Zhiqiang Lin,Wei Zou18.Safe Passage for Passwords and Other Sensitive Data.Jonathan M.McCune,Adrian Perrig,Michael K.Reiter19.Conditioned-safe Ceremonies and a User Study of an Application to Web Authentication.Chris Karlof,J.Doug Tygar,David Wagner20.CSAR:A Practical and Provable Technique to Make Randomized Systems Accountable.Michael Backes,Peter Druschel,Andreas Haeberlen,Dominique UnruhOakland20091.Wirelessly Pickpocketing a Mifare Classic Card.(Best Practical Paper Award)Flavio D.Garcia,Peter van Rossum,Roel Verdult,Ronny Wichers Schreur2.Plaintext Recovery Attacks Against SSH.Martin R.Albrecht,Kenneth G.Paterson,Gaven J.Watson3.Exploiting Unix File-System Races via Algorithmic Complexity Attacks.Xiang Cai,Yuwei Gui,Rob Johnson4.Practical Mitigations for Timing-Based Side-Channel Attacks on Modern x86Processors.Bart Coppens,Ingrid Verbauwhede,Bjorn De Sutter,Koen De Bosschere5.Non-Interference for a Practical DIFC-Based Operating System.Maxwell Krohn,Eran Tromer6.Native Client:A Sandbox for Portable,Untrusted x86Native Code.(Best Paper Award)B.Yee,D.Sehr,G.Dardyk,B.Chen,R.Muth,T.Ormandy,S.Okasaka,N.Narula,N.Fullagar7.Automatic Reverse Engineering of Malware Emulators.(Best Student Paper Award)Monirul Sharif,Andrea Lanzi,Jonathon Giffin,Wenke Lee8.Prospex:Protocol Specification Extraction.Paolo Milani Comparetti,Gilbert Wondracek,Christopher Kruegel,Engin Kirda9.Quantifying Information Leaks in Outbound Web Traffic.Kevin Borders,Atul Prakash10.Automatic Discovery and Quantification of Information Leaks.Michael Backes,Boris Kopf,Andrey Rybalchenko11.CLAMP:Practical Prevention of Large-Scale Data Leaks.Bryan Parno,Jonathan M.McCune,Dan Wendlandt,David G.Andersen,Adrian Perrig12.De-anonymizing Social Networks.Arvind Narayanan,Vitaly Shmatikov13.Privacy Weaknesses in Biometric Sketches.Koen Simoens,Pim Tuyls,Bart Preneel14.The Mastermind Attack on Genomic Data.Michael T.Goodrich15.A Logic of Secure Systems and its Application to Trusted Computing.Anupam Datta,Jason Franklin,Deepak Garg,Dilsun Kaynar16.Formally Certifying the Security of Digital Signature Schemes.Santiago Zanella-Beguelin,Gilles Barthe,Benjamin Gregoire,Federico Olmedo17.An Epistemic Approach to Coercion-Resistance for Electronic Voting Protocols.Ralf Kuesters,Tomasz Truderung18.Sphinx:A Compact and Provably Secure Mix Format.George Danezis,Ian Goldberg19.DSybil:Optimal Sybil-Resistance for Recommendation Systems.Haifeng Yu,Chenwei Shi,Michael Kaminsky,Phillip B.Gibbons,Feng Xiao20.Fingerprinting Blank Paper Using Commodity Scanners.William Clarkson,Tim Weyrich,Adam Finkelstein,Nadia Heninger,Alex Halderman,Ed Felten 21.Tempest in a Teapot:Compromising Reflections Revisited.Michael Backes,Tongbo Chen,Markus Duermuth,Hendrik P.A.Lensch,Martin Welk22.Blueprint:Robust Prevention of Cross-site Scripting Attacks for Existing Browsers.Mike Ter Louw,V.N.Venkatakrishnan23.Pretty-Bad-Proxy:An Overlooked Adversary in Browsers’HTTPS Deployments.Shuo Chen,Ziqing Mao,Yi-Min Wang,Ming Zhang24.Secure Content Sniffing for Web Browsers,or How to Stop Papers from Reviewing Themselves.Adam Barth,Juan Caballero,Dawn Song25.It’s No Secret:Measuring the Security and Reliability of Authentication via’Secret’Questions.Stuart Schechter,A.J.Bernheim Brush,Serge Egelman26.Password Cracking Using Probabilistic Context-Free Grammars.Matt Weir,Sudhir Aggarwal,Bill Glodek,Breno de MedeirosUSENIX Security2009promising Electromagnetic Emanations of Wired and Wireless Keyboards.(Outstanding Student Paper)Martin Vuagnoux,Sylvain Pasini2.Peeping Tom in the Neighborhood:Keystroke Eavesdropping on Multi-User Systems.Kehuan Zhang,XiaoFeng Wang3.A Practical Congestion Attack on Tor Using Long Paths,Nathan S.Evans,Roger Dingledine,Christian Grothoff4.Baggy Bounds Checking:An Efficient and Backwards-Compatible Defense against Out-of-Bounds Errors.Periklis Akritidis,Manuel Costa,Miguel Castro,Steven Hand5.Dynamic Test Generation to Find Integer Bugs in x86Binary Linux Programs.David Molnar,Xue Cong Li,David A.Wagner6.NOZZLE:A Defense Against Heap-spraying Code Injection Attacks.Paruj Ratanaworabhan,Benjamin Livshits,Benjamin Zorn7.Detecting Spammers with SNARE:Spatio-temporal Network-level Automatic Reputation Engine.Shuang Hao,Nadeem Ahmed Syed,Nick Feamster,Alexander G.Gray,Sven Krasser8.Improving Tor using a TCP-over-DTLS Tunnel.Joel Reardon,Ian Goldberg9.Locating Prefix Hijackers using LOCK.Tongqing Qiu,Lusheng Ji,Dan Pei,Jia Wang,Jun(Jim)Xu,Hitesh Ballani10.GATEKEEPER:Mostly Static Enforcement of Security and Reliability Policies for JavaScript Code.Salvatore Guarnieri,Benjamin Livshits11.Cross-Origin JavaScript Capability Leaks:Detection,Exploitation,and Defense.Adam Barth,Joel Weinberger,Dawn Song12.Memory Safety for Low-Level Software/Hardware Interactions.John Criswell,Nicolas Geoffray,Vikram Adve13.Physical-layer Identification of RFID Devices.Boris Danev,Thomas S.Heydt-Benjamin,Srdjan CapkunCP:Secure Remote Storage for Computational RFIDs.Mastooreh Salajegheh,Shane Clark,Benjamin Ransford,Kevin Fu,Ari Juels15.Jamming-resistant Broadcast Communication without Shared Keys.Christina Popper,Mario Strasser,Srdjan Capkun16.xBook:Redesigning Privacy Control in Social Networking Platforms.Kapil Singh,Sumeer Bhola,Wenke Lee17.Nemesis:Preventing Authentication and Access Control Vulnerabilities in Web Applications.Michael Dalton,Christos Kozyrakis,Nickolai Zeldovich18.Static Enforcement of Web Application Integrity Through Strong Typing.William Robertson,Giovanni Vigna19.Vanish:Increasing Data Privacy with Self-Destructing Data.(Outstanding Student Paper)Roxana Geambasu,Tadayoshi Kohno,Amit A.Levy,Henry M.Levy20.Efficient Data Structures for Tamper-Evident Logging.Scott A.Crosby,Dan S.Wallach21.VPriv:Protecting Privacy in Location-Based Vehicular Services.Raluca Ada Popa,Hari Balakrishnan,Andrew J.Blumberg22.Effective and Efficient Malware Detection at the End Host.Clemens Kolbitsch,Paolo Milani Comparetti,Christopher Kruegel,Engin Kirda,Xiaoyong Zhou,XiaoFeng Wang 23.Protecting Confidential Data on Personal Computers with Storage Capsules.Kevin Borders,Eric Vander Weele,Billy Lau,Atul Prakash24.Return-Oriented Rootkits:Bypassing Kernel Code Integrity Protection Mechanisms.Ralf Hund,Thorsten Holz,Felix C.Freiling25.Crying Wolf:An Empirical Study of SSL Warning Effectiveness.Joshua Sunshine,Serge Egelman,Hazim Almuhimedi,Neha Atri,Lorrie Faith Cranor26.The Multi-Principal OS Construction of the Gazelle Web Browser.Helen J.Wang,Chris Grier,Alex Moshchuk,Samuel T.King,Piali Choudhury,Herman VenterACM CCS20091.Attacking cryptographic schemes based on”perturbation polynomials”.Martin Albrecht,Craig Gentry,Shai Halevi,Jonathan Katz2.Filter-resistant code injection on ARM.Yves Younan,Pieter Philippaerts,Frank Piessens,Wouter Joosen,Sven Lachmund,Thomas Walter3.False data injection attacks against state estimation in electric power grids.Yao Liu,Michael K.Reiter,Peng Ning4.EPC RFID tag security weaknesses and defenses:passport cards,enhanced drivers licenses,and beyond.Karl Koscher,Ari Juels,Vjekoslav Brajkovic,Tadayoshi Kohno5.An efficient forward private RFID protocol.Come Berbain,Olivier Billet,Jonathan Etrog,Henri Gilbert6.RFID privacy:relation between two notions,minimal condition,and efficient construction.Changshe Ma,Yingjiu Li,Robert H.Deng,Tieyan Li7.CoSP:a general framework for computational soundness proofs.Michael Backes,Dennis Hofheinz,Dominique Unruh8.Reactive noninterference.Aaron Bohannon,Benjamin C.Pierce,Vilhelm Sjoberg,Stephanie Weirich,Steve Zdancewicputational soundness for key exchange protocols with symmetric encryption.Ralf Kusters,Max Tuengerthal10.A probabilistic approach to hybrid role mining.Mario Frank,Andreas P.Streich,David A.Basin,Joachim M.Buhmann11.Efficient pseudorandom functions from the decisional linear assumption and weaker variants.Allison B.Lewko,Brent Waters12.Improving privacy and security in multi-authority attribute-based encryption.Melissa Chase,Sherman S.M.Chow13.Oblivious transfer with access control.Jan Camenisch,Maria Dubovitskaya,Gregory Neven14.NISAN:network information service for anonymization networks.Andriy Panchenko,Stefan Richter,Arne Rache15.Certificateless onion routing.Dario Catalano,Dario Fiore,Rosario Gennaro16.ShadowWalker:peer-to-peer anonymous communication using redundant structured topologies.Prateek Mittal,Nikita Borisov17.Ripley:automatically securing web2.0applications through replicated execution.K.Vikram,Abhishek Prateek,V.Benjamin Livshits18.HAIL:a high-availability and integrity layer for cloud storage.Kevin D.Bowers,Ari Juels,Alina Oprea19.Hey,you,get offof my cloud:exploring information leakage in third-party compute clouds.Thomas Ristenpart,Eran Tromer,Hovav Shacham,Stefan Savage20.Dynamic provable data possession.C.Christopher Erway,Alptekin Kupcu,Charalampos Papamanthou,Roberto Tamassia21.On cellular botnets:measuring the impact of malicious devices on a cellular network core.Patrick Traynor,Michael Lin,Machigar Ongtang,Vikhyath Rao,Trent Jaeger,Patrick Drew McDaniel,Thomas Porta 22.On lightweight mobile phone application certification.William Enck,Machigar Ongtang,Patrick Drew McDaniel23.SMILE:encounter-based trust for mobile social services.Justin Manweiler,Ryan Scudellari,Landon P.Cox24.Battle of Botcraft:fighting bots in online games with human observational proofs.Steven Gianvecchio,Zhenyu Wu,Mengjun Xie,Haining Wang25.Fides:remote anomaly-based cheat detection using client emulation.Edward C.Kaiser,Wu-chang Feng,Travis Schluessler26.Behavior based software theft detection.Xinran Wang,Yoon-chan Jhi,Sencun Zhu,Peng Liu27.The fable of the bees:incentivizing robust revocation decision making in ad hoc networks.Steffen Reidt,Mudhakar Srivatsa,Shane Balfe28.Effective implementation of the cell broadband engineTM isolation loader.Masana Murase,Kanna Shimizu,Wilfred Plouffe,Masaharu Sakamoto29.On achieving good operating points on an ROC plane using stochastic anomaly score prediction.Muhammad Qasim Ali,Hassan Khan,Ali Sajjad,Syed Ali Khayam30.On non-cooperative location privacy:a game-theoretic analysis.Julien Freudiger,Mohammad Hossein Manshaei,Jean-Pierre Hubaux,David C.Parkes31.Privacy-preserving genomic computation through program specialization.Rui Wang,XiaoFeng Wang,Zhou Li,Haixu Tang,Michael K.Reiter,Zheng Dong32.Feeling-based location privacy protection for location-based services.Toby Xu,Ying Cai33.Multi-party off-the-record messaging.Ian Goldberg,Berkant Ustaoglu,Matthew Van Gundy,Hao Chen34.The bayesian traffic analysis of mix networks.Carmela Troncoso,George Danezis35.As-awareness in Tor path selection.Matthew Edman,Paul F.Syverson36.Membership-concealing overlay networks.Eugene Y.Vasserman,Rob Jansen,James Tyra,Nicholas Hopper,Yongdae Kim37.On the difficulty of software-based attestation of embedded devices.Claude Castelluccia,Aurelien Francillon,Daniele Perito,Claudio Soriente38.Proximity-based access control for implantable medical devices.Kasper Bonne Rasmussen,Claude Castelluccia,Thomas S.Heydt-Benjamin,Srdjan Capkun39.XCS:cross channel scripting and its impact on web applications.Hristo Bojinov,Elie Bursztein,Dan Boneh40.A security-preserving compiler for distributed programs:from information-flow policies to cryptographic mechanisms.Cedric Fournet,Gurvan Le Guernic,Tamara Rezk41.Finding bugs in exceptional situations of JNI programs.Siliang Li,Gang Tan42.Secure open source collaboration:an empirical study of Linus’law.Andrew Meneely,Laurie A.Williams43.On voting machine design for verification and testability.Cynthia Sturton,Susmit Jha,Sanjit A.Seshia,David Wagner44.Secure in-VM monitoring using hardware virtualization.Monirul I.Sharif,Wenke Lee,Weidong Cui,Andrea Lanzi45.A metadata calculus for secure information sharing.Mudhakar Srivatsa,Dakshi Agrawal,Steffen Reidt46.Multiple password interference in text passwords and click-based graphical passwords.Sonia Chiasson,Alain Forget,Elizabeth Stobert,Paul C.van Oorschot,Robert Biddle47.Can they hear me now?:a security analysis of law enforcement wiretaps.Micah Sherr,Gaurav Shah,Eric Cronin,Sandy Clark,Matt Blaze48.English shellcode.Joshua Mason,Sam Small,Fabian Monrose,Greg MacManus49.Learning your identity and disease from research papers:information leaks in genome wide association study.Rui Wang,Yong Fuga Li,XiaoFeng Wang,Haixu Tang,Xiao-yong Zhou50.Countering kernel rootkits with lightweight hook protection.Zhi Wang,Xuxian Jiang,Weidong Cui,Peng Ning51.Mapping kernel objects to enable systematic integrity checking.Martim Carbone,Weidong Cui,Long Lu,Wenke Lee,Marcus Peinado,Xuxian Jiang52.Robust signatures for kernel data structures.Brendan Dolan-Gavitt,Abhinav Srivastava,Patrick Traynor,Jonathon T.Giffin53.A new cell counter based attack against tor.Zhen Ling,Junzhou Luo,Wei Yu,Xinwen Fu,Dong Xuan,Weijia Jia54.Scalable onion routing with torsk.Jon McLachlan,Andrew Tran,Nicholas Hopper,Yongdae Kim55.Anonymous credentials on a standard java card.Patrik Bichsel,Jan Camenisch,Thomas Gros,Victor Shouprge-scale malware indexing using function-call graphs.Xin Hu,Tzi-cker Chiueh,Kang G.Shin57.Dispatcher:enabling active botnet infiltration using automatic protocol reverse-engineering.Juan Caballero,Pongsin Poosankam,Christian Kreibich,Dawn Xiaodong Song58.Your botnet is my botnet:analysis of a botnet takeover.Brett Stone-Gross,Marco Cova,Lorenzo Cavallaro,Bob Gilbert,MartinSzydlowski,Richard A.Kemmerer,Christopher Kruegel,Giovanni VignaNDSS20101.Server-side Verification of Client Behavior in Online Games.Darrell Bethea,Robert Cochran and Michael Reiter2.Defeating Vanish with Low-Cost Sybil Attacks Against Large DHTs.S.Wolchok,O.S.Hofmann,N.Heninger,E.W.Felten,J.A.Halderman,C.J.Rossbach,B.Waters,E.Witchel3.Stealth DoS Attacks on Secure Channels.Amir Herzberg and Haya Shulman4.Protecting Browsers from Extension Vulnerabilities.Adam Barth,Adrienne Porter Felt,Prateek Saxena,and Aaron Boodman5.Adnostic:Privacy Preserving Targeted Advertising.Vincent Toubiana,Arvind Narayanan,Dan Boneh,Helen Nissenbaum and Solon Barocas6.FLAX:Systematic Discovery of Client-side Validation Vulnerabilities in Rich Web Applications.Prateek Saxena,Steve Hanna,Pongsin Poosankam and Dawn Song7.Effective Anomaly Detection with Scarce Training Data.William Robertson,Federico Maggi,Christopher Kruegel and Giovanni Vignarge-Scale Automatic Classification of Phishing Pages.Colin Whittaker,Brian Ryner and Marria Nazif9.A Systematic Characterization of IM Threats using Honeypots.Iasonas Polakis,Thanasis Petsas,Evangelos P.Markatos and Spiros Antonatos10.On Network-level Clusters for Spam Detection.Zhiyun Qian,Zhuoqing Mao,Yinglian Xie and Fang Yu11.Improving Spam Blacklisting Through Dynamic Thresholding and Speculative Aggregation.Sushant Sinha,Michael Bailey and Farnam Jahanian12.Botnet Judo:Fighting Spam with Itself.A.Pitsillidis,K.Levchenko,C.Kreibich,C.Kanich,G.M.Voelker,V.Paxson,N.Weaver,S.Savage13.Contractual Anonymity.Edward J.Schwartz,David Brumley and Jonathan M.McCune14.A3:An Extensible Platform for Application-Aware Anonymity.Micah Sherr,Andrew Mao,William R.Marczak,Wenchao Zhou,Boon Thau Loo,and Matt Blaze15.When Good Randomness Goes Bad:Virtual Machine Reset Vulnerabilities and Hedging Deployed Cryptography.Thomas Ristenpart and Scott Yilek16.InvisiType:Object-Oriented Security Policies.Jiwon Seo and Monica m17.A Security Evaluation of DNSSEC with NSEC3.Jason Bau and John Mitchell18.On the Safety of Enterprise Policy Deployment.Yudong Gao,Ni Pan,Xu Chen and Z.Morley Mao19.Where Do You Want to Go Today?Escalating Privileges by Pathname Manipulation.Suresh Chari,Shai Halevi and Wietse Venema20.Joe-E:A Security-Oriented Subset of Java.Adrian Mettler,David Wagner and Tyler Close21.Preventing Capability Leaks in Secure JavaScript Subsets.Matthew Finifter,Joel Weinberger and Adam Barth22.Binary Code Extraction and Interface Identification for Security Applications.Juan Caballero,Noah M.Johnson,Stephen McCamant,and Dawn Song23.Automatic Reverse Engineering of Data Structures from Binary Execution.Zhiqiang Lin,Xiangyu Zhang and Dongyan Xu24.Efficient Detection of Split Personalities in Malware.Davide Balzarotti,Marco Cova,Christoph Karlberger,Engin Kirda,Christopher Kruegel and Giovanni VignaOakland20101.Inspector Gadget:Automated Extraction of Proprietary Gadgets from Malware Binaries.Clemens Kolbitsch Thorsten Holz,Christopher Kruegel,Engin Kirda2.Synthesizing Near-Optimal Malware Specifications from Suspicious Behaviors.Matt Fredrikson,Mihai Christodorescu,Somesh Jha,Reiner Sailer,Xifeng Yan3.Identifying Dormant Functionality in Malware Programs.Paolo Milani Comparetti,Guido Salvaneschi,Clemens Kolbitsch,Engin Kirda,Christopher Kruegel,Stefano Zanero4.Reconciling Belief and Vulnerability in Information Flow.Sardaouna Hamadou,Vladimiro Sassone,Palamidessi5.Towards Static Flow-Based Declassification for Legacy and Untrusted Programs.Bruno P.S.Rocha,Sruthi Bandhakavi,Jerry I.den Hartog,William H.Winsborough,Sandro Etalle6.Non-Interference Through Secure Multi-Execution.Dominique Devriese,Frank Piessens7.Object Capabilities and Isolation of Untrusted Web Applications.Sergio Maffeis,John C.Mitchell,Ankur Taly8.TrustVisor:Efficient TCB Reduction and Attestation.Jonathan McCune,Yanlin Li,Ning Qu,Zongwei Zhou,Anupam Datta,Virgil Gligor,Adrian Perrig9.Overcoming an Untrusted Computing Base:Detecting and Removing Malicious Hardware Automatically.Matthew Hicks,Murph Finnicum,Samuel T.King,Milo M.K.Martin,Jonathan M.Smith10.Tamper Evident Microprocessors.Adam Waksman,Simha Sethumadhavan11.Side-Channel Leaks in Web Applications:a Reality Today,a Challenge Tomorrow.Shuo Chen,Rui Wang,XiaoFeng Wang Kehuan Zhang12.Investigation of Triangular Spamming:a Stealthy and Efficient Spamming Technique.Zhiyun Qian,Z.Morley Mao,Yinglian Xie,Fang Yu13.A Practical Attack to De-Anonymize Social Network Users.Gilbert Wondracek,Thorsten Holz,Engin Kirda,Christopher Kruegel14.SCiFI-A System for Secure Face Identification.(Best Paper)Margarita Osadchy,Benny Pinkas,Ayman Jarrous,Boaz Moskovich15.Round-Efficient Broadcast Authentication Protocols for Fixed Topology Classes.Haowen Chan,Adrian Perrig16.Revocation Systems with Very Small Private Keys.Allison Lewko,Amit Sahai,Brent Waters17.Authenticating Primary Users’Signals in Cognitive Radio Networks via Integrated Cryptographic and Wireless Link Signatures.Yao Liu,Peng Ning,Huaiyu Dai18.Outside the Closed World:On Using Machine Learning For Network Intrusion Detection.Robin Sommer,Vern Paxson19.All You Ever Wanted to Know about Dynamic Taint Analysis and Forward Symbolic Execution(but might have been afraid to ask).Thanassis Avgerinos,Edward Schwartz,David Brumley20.State of the Art:Automated Black-Box Web Application Vulnerability Testing.Jason Bau,Elie Bursztein,Divij Gupta,John Mitchell21.A Proof-Carrying File System.Deepak Garg,Frank Pfenning22.Scalable Parametric Verification of Secure Systems:How to Verify Ref.Monitors without Worrying about Data Structure Size.Jason Franklin,Sagar Chaki,Anupam Datta,Arvind Seshadri23.HyperSafe:A Lightweight Approach to Provide Lifetime Hypervisor Control-Flow Integrity.Zhi Wang,Xuxian Jiang24.How Good are Humans at Solving CAPTCHAs?A Large Scale Evaluation.Elie Bursztein,Steven Bethard,John C.Mitchell,Dan Jurafsky,Celine Fabry25.Bootstrapping Trust in Commodity Computers.Bryan Parno,Jonathan M.McCune,Adrian Perrig26.Chip and PIN is Broken.(Best Practical Paper)Steven J.Murdoch,Saar Drimer,Ross Anderson,Mike Bond27.Experimental Security Analysis of a Modern Automobile.K.Koscher,A.Czeskis,F.Roesner,S.Patel,T.Kohno,S.Checkoway,D.McCoy,B.Kantor,D.Anderson,H.Shacham,S.Savage 28.On the Incoherencies in Web Browser Access Control Policies.Kapil Singh,Alexander Moshchuk,Helen J.Wang,Wenke Lee29.ConScript:Specifying and Enforcing Fine-Grained Security Policies for JavaScript in the Browser.Leo Meyerovich,Benjamin Livshits30.TaintScope:A Checksum-Aware Directed Fuzzing Tool for Automatic Software Vulnerability Detection.(Best Student Paper)Tielei Wang,Tao Wei,Guofei Gu,Wei Zou31.A Symbolic Execution Framework for JavaScript.Prateek Saxena,Devdatta Akhawe,Steve Hanna,Stephen McCamant,Dawn Song,Feng MaoUSENIX Security20101.Adapting Software Fault Isolation to Contemporary CPU Architectures.David Sehr,Robert Muth,CliffBiffle,Victor Khimenko,Egor Pasko,Karl Schimpf,Bennet Yee,Brad Chen2.Making Linux Protection Mechanisms Egalitarian with UserFS.Taesoo Kim and Nickolai Zeldovich3.Capsicum:Practical Capabilities for UNIX.(Best Student Paper)Robert N.M.Watson,Jonathan Anderson,Ben Laurie,Kris Kennaway4.Structuring Protocol Implementations to Protect Sensitive Data.Petr Marchenko,Brad Karp5.PrETP:Privacy-Preserving Electronic Toll Pricing.Josep Balasch,Alfredo Rial,Carmela Troncoso,Bart Preneel,Ingrid Verbauwhede,Christophe Geuens6.An Analysis of Private Browsing Modes in Modern Browsers.Gaurav Aggarwal,Elie Bursztein,Collin Jackson,Dan Boneh7.BotGrep:Finding P2P Bots with Structured Graph Analysis.Shishir Nagaraja,Prateek Mittal,Chi-Yao Hong,Matthew Caesar,Nikita Borisov8.Fast Regular Expression Matching Using Small TCAMs for Network Intrusion Detection and Prevention Systems.Chad R.Meiners,Jignesh Patel,Eric Norige,Eric Torng,Alex X.Liu9.Searching the Searchers with SearchAudit.John P.John,Fang Yu,Yinglian Xie,Martin Abadi,Arvind Krishnamurthy10.Toward Automated Detection of Logic Vulnerabilities in Web Applications.Viktoria Felmetsger,Ludovico Cavedon,Christopher Kruegel,Giovanni Vigna11.Baaz:A System for Detecting Access Control Misconfigurations.Tathagata Das,Ranjita Bhagwan,Prasad Naldurg12.Cling:A Memory Allocator to Mitigate Dangling Pointers.Periklis Akritidis13.ZKPDL:A Language-Based System for Efficient Zero-Knowledge Proofs and Electronic Cash.Sarah Meiklejohn,C.Chris Erway,Alptekin Kupcu,Theodora Hinkle,Anna Lysyanskaya14.P4P:Practical Large-Scale Privacy-Preserving Distributed Computation Robust against Malicious Users.Yitao Duan,John Canny,Justin Zhan,15.SEPIA:Privacy-Preserving Aggregation of Multi-Domain Network Events and Statistics.Martin Burkhart,Mario Strasser,Dilip Many,Xenofontas Dimitropoulos16.Dude,Where’s That IP?Circumventing Measurement-based IP Geolocation.Phillipa Gill,Yashar Ganjali,Bernard Wong,David Lie17.Idle Port Scanning and Non-interference Analysis of Network Protocol Stacks Using Model Checking.Roya Ensafi,Jong Chun Park,Deepak Kapur,Jedidiah R.Crandall18.Building a Dynamic Reputation System for DNS.Manos Antonakakis,Roberto Perdisci,David Dagon,Wenke Lee,Nick Feamster19.Scantegrity II Municipal Election at Takoma Park:The First E2E Binding Governmental Election with Ballot Privacy.R.Carback,D.Chaum,J.Clark,J.Conway,A.Essex,P.S.Herrnson,T.Mayberry,S.Popoveniuc,R.L.Rivest,E.Shen,A.T.Sherman,P.L.Vora20.Acoustic Side-Channel Attacks on Printers.Michael Backes,Markus Durmuth,Sebastian Gerling,Manfred Pinkal,Caroline Sporleder21.Security and Privacy Vulnerabilities of In-Car Wireless Networks:A Tire Pressure Monitoring System Case Study.Ishtiaq Rouf,Rob Miller,Hossen Mustafa,Travis Taylor,Sangho Oh,Wenyuan Xu,Marco Gruteser,Wade Trappe,Ivan Seskar 22.VEX:Vetting Browser Extensions for Security Vulnerabilities.(Best Paper)Sruthi Bandhakavi,Samuel T.King,P.Madhusudan,Marianne Winslett23.Securing Script-Based Extensibility in Web Browsers.Vladan Djeric,Ashvin Goel24.AdJail:Practical Enforcement of Confidentiality and Integrity Policies on Web Advertisements.Mike Ter Louw,Karthik Thotta Ganesh,V.N.Venkatakrishnan25.Realization of RF Distance Bounding.Kasper Bonne Rasmussen,Srdjan Capkun26.The Case for Ubiquitous Transport-Level Encryption.Andrea Bittau,Michael Hamburg,Mark Handley,David Mazieres,Dan Boneh27.Automatic Generation of Remediation Procedures for Malware Infections.Roberto Paleari,Lorenzo Martignoni,Emanuele Passerini,Drew Davidson,Matt Fredrikson,Jon Giffin,Somesh Jha28.Re:CAPTCHAs-Understanding CAPTCHA-Solving Services in an Economic Context.Marti Motoyama,Kirill Levchenko,Chris Kanich,Damon McCoy,Geoffrey M.Voelker,Stefan Savage29.Chipping Away at Censorship Firewalls with User-Generated Content.Sam Burnett,Nick Feamster,Santosh Vempala30.Fighting Coercion Attacks in Key Generation using Skin Conductance.Payas Gupta,Debin GaoACM CCS20101.Security Analysis of India’s Electronic Voting Machines.Scott Wolchok,Erik Wustrow,J.Alex Halderman,Hari Prasad,Rop Gonggrijp2.Dissecting One Click Frauds.Nicolas Christin,Sally S.Yanagihara,Keisuke Kamataki3.@spam:The Underground on140Characters or Less.Chris Grier,Kurt Thomas,Vern Paxson,Michael Zhang4.HyperSentry:Enabling Stealthy In-context Measurement of Hypervisor Integrity.Ahmed M.Azab,Peng Ning,Zhi Wang,Xuxian Jiang,Xiaolan Zhang,Nathan C.Skalsky5.Trail of Bytes:Efficient Support for Forensic Analysis.Srinivas Krishnan,Kevin Z.Snow,Fabian Monrose6.Survivable Key Compromise in Software Update Systems.Justin Samuel,Nick Mathewson,Justin Cappos,Roger Dingledine7.A Methodology for Empirical Analysis of the Permission-Based Security Models and its Application to Android.David Barrera,H.Gunes Kayacik,Paul C.van Oorschot,Anil Somayaji8.Mobile Location Tracking in Metropolitan Areas:malnets and others.Nathanial Husted,Steve Myers9.On Pairing Constrained Wireless Devices Based on Secrecy of Auxiliary Channels:The Case of Acoustic Eavesdropping.Tzipora Halevi,Nitesh Saxena10.PinDr0p:Using Single-Ended Audio Features to Determine Call Provenance.Vijay A.Balasubramaniyan,Aamir Poonawalla,Mustaque Ahamad,Michael T.Hunter,Patrick Traynor11.Building Efficient Fully Collusion-Resilient Traitor Tracing and Revocation Schemes.Sanjam Garg,Abishek Kumarasubramanian,Amit Sahai,Brent Waters12.Algebraic Pseudorandom Functions with Improved Efficiency from the Augmented Cascade.Dan Boneh,Hart Montgomery,Ananth Raghunathan13.Practical Leakage-Resilient Pseudorandom Generators.Yu Yu,Francois-Xavier Standaert,Olivier Pereira,Moti Yung14.Practical Leakage-Resilient Identity-Based Encryption from Simple Assumptions.Sherman S.M.Chow,Yevgeniy Dodis,Yannis Rouselakis,Brent Waters15.Testing Metrics for Password Creation Policies by Attacking Large Sets of Revealed Passwords.Matt Weir,Sudhir Aggarwal,Michael Collins,Henry Stern16.The Security of Modern Password Expiration:An Algorithmic Framework and Empirical Analysis.Yinqian Zhang,Fabian Monrose,Michael K.Reiter17.Attacks and Design of Image Recognition CAPTCHAs.Bin Zhu,JeffYan,Chao Yang,Qiujie Li,Jiu Liu,Ning Xu,Meng Yi18.Robusta:Taming the Native Beast of the JVM.Joseph Siefers,Gang Tan,Greg Morrisett19.Retaining Sandbox Containment Despite Bugs in Privileged Memory-Safe Code.Justin Cappos,Armon Dadgar,JeffRasley,Justin Samuel,Ivan Beschastnikh,Cosmin Barsan,Arvind Krishnamurthy,Thomas Anderson20.A Control Point for Reducing Root Abuse of File-System Privileges.Glenn Wurster,Paul C.van Oorschot21.Modeling Attacks on Physical Unclonable Functions.Ulrich Ruehrmair,Frank Sehnke,Jan Soelter,Gideon Dror,Srinivas Devadas,Juergen Schmidhuber22.Dismantling SecureMemory,CryptoMemory and CryptoRF.Flavio D.Garcia,Peter van Rossum,Roel Verdult,Ronny Wichers Schreur23.Attacking and Fixing PKCS#11Security Tokens.Matteo Bortolozzo,Matteo Centenaro,Riccardo Focardi,Graham Steel24.An Empirical Study of Privacy-Violating Information Flows in JavaScript Web Applications.Dongseok Jang,Ranjit Jhala,Sorin Lerner,Hovav Shacham25.DIFC Programs by Automatic Instrumentation.William Harris,Somesh Jha,Thomas Reps26.Predictive Black-box Mitigation of Timing Channels.Aslan Askarov,Danfeng Zhang,Andrew Myers27.In Search of an Anonymous and Secure Lookup:Attacks on Structured Peer-to-peer Anonymous Communication Systems.Qiyan Wang,Prateek Mittal,Nikita Borisov28.Recruiting New Tor Relays with BRAIDS.Rob Jansen,Nicholas Hopper,Yongdae Kim29.An Improved Algorithm for Tor Circuit Scheduling.Can Tang,Ian Goldberg30.Dissent:Accountable Anonymous Group Messaging.Henry Corrigan-Gibbs,Bryan Ford31.Abstraction by Set-Membership—Verifying Security Protocols and Web Services with Databases.Sebastian Moedersheim。
基于改进DeepLabV3+的引导式道路提取方法及在震源点位优化中的应用

2024年3月第39卷第2期西安石油大学学报(自然科学版)JournalofXi’anShiyouUniversity(NaturalScienceEdition)Mar.2024Vol.39No.2收稿日期:2023 06 03基金项目:国家自然科学基金面上项目“基于频变信息的流体识别及流体可动性预测”(41774142);四川省重点研发项目“工业互联网安全与智能管理平台关键技术研究与应用”(2023YFG0112);四川省自然科学基金资助项目“基于超分辨感知方法的密集神经图像分割”(2022NSFSC0964)第一作者:曹凯奇(1998 ),男,硕士,研究方向:遥感图像标注。
E mail:819088338@qq.com通讯作者:文武(1979 ),男,博士,研究方向:人工智能在地球科学的应用、高性能计算。
E mail:wenwu@cuit.edu.cnDOI:10.3969/j.issn.1673 064X.2024.02.016中图分类号:TE19文章编号:1673 064X(2024)02 0128 15文献标识码:A基于改进DeepLabV3+的引导式道路提取方法及在震源点位优化中的应用曹凯奇1,张凌浩2,徐虹1,吴蔚3,文武1,周航1(1.成都信息工程大学计算机学院,四川成都610225;2.国网四川省电力公司电力科学研究院,四川成都610094;3.中国石油集团东方地球物理勘探有限责任公司采集技术中心,河北涿州072750)摘要:为解决自动识别方法在道路提取时存在漏提、错提现象,提出一种引导式道路提取方法提高修正效率。
在DeepLabV3+原有输入通道(3通道)的基础上添加额外输入通道(第4通道),将道路的4个极点转化为二维高斯热图后作为额外通道输入网络,网络以极点作为引导信号,使网络适用于引导式道路提取任务;设计并行多分支模块,提取上下文信息,增强网络特征提取能力;融合类均衡二值交叉熵和骰子系数组成新的复合损失函数进行训练缓解正负样本不均衡问题。
Best-design-practices-for-DFT
Best design practices for DFTGunjot KaurSidhant Goel,mayank parasrampuria, - October 14, 20151. IntroductionSoC sub-components (IPs) generally come from various sources – internal and external – and with that it has become necessary that designers ensure the RTL is testable. If the RTL has testability issues, test coverage goals can’t be met and the RTL needs to be modified, which means several iterations of synthesis, verification, and Automatic Test Pattern Generation (ATPG).Here we will discuss the basic design practices to ensure proper testability.2. Clock ControlFor ATPG tool to generate patterns, the clock and reset of a flop must be fully controllable; i.e., the tool can trigger the clock whenever required – it must not be gated by any other uncontrollable signal.2.1 Clocks gated by combinational logicIn case the clock is gated by a combinational logic then an override should be added using ashift/test mode signal for ensuring proper shift & capture clock propagation.Figure 1: SHIFT_MODE = 1 during shift2.2 Internally generated clocksFor all internally generated clocks a bypass should be provided. In case there is a requirement of this clock, say we need PLL clock for at-speed testing, then a clock control logic should be added on them.Figure 2: Bypassing all internally generated clockAn example for this would be clock generated by sequential logic:Here the clock is generated by the output of a flop, since this generated clock is not directly controllable by the ATPG tool, we need to add clock control logic.Figure 3: Bypass for clock generate from a flop2.3 Test clock selectionIt must be ensured that test clock frequency is always greater than or equal to the functional clock frequency, so that we never end up under-testing a logic.2.4 Using clock as dataWhen clock is used as data in a design, then it must always be ensured that we use test mode signal to gate this data path (i.e., clock to the data cone). Otherwise a race condition may result that produces an inaccurate simulation results.Figure 4: Eliminating race condition3. Un-clocked latchesStatic Timing Analysis (STA) team closes timing only on those sequential elements which are clocked. If the enable/clock of the latch comes from the output of a flop, STA team doesn’t check it for timing, which may lead to erroneous latching of the data. It will be caught either in simulation or on silicon. This can be prevented if the enable of the latch is a valid clock (gated or ungated).Figure 5: Un-clocked latchZero Delay (ATPG/Idle):ATPG tools while generating patterns works on a zero delay type simulation model. Data is sampled just before the clock edge, so from tool’s perspective, the output is always high during pattern generation in this case.Figure 6(a): Zero DelayData Skewed with respect to clock (Simulation):In simulation, due to skew in design between the data and clock we can have two scenarios, data coming either early or late and in both such cases we will start getting fails.Figure 6(b): Data EarlyFigure 6(c): Data Delayed4. Reset ControlAs discussed previously, clock and reset of a flop must be fully controllable. To achieve this, a multiplexer is placed in the reset path as shown below. The first input of the multiplexer is the functional reset as before. The second input is the DFT (test) controlled RESET and the select line (test mode) is used by DFT to switch to the controlled reset in test mode.Figure 7: Reset control using mux4.1 Cascading of switching logic in the reset pathThe select signal (Reset Override) is not timed by the timing team, so any random skew in this signalmust not affect the state of any of the flops. If two or more such switching logics are cascaded as shown, this may result in a glitch to the RESET pin of the flop which will corrupt its state.Figure 8(a): Cascaded reset control logicZero Delay (ATPG):Due to zero delay in ATPG, the select line M1 & M2 will toggle at the same time so the reset RST is always high.Figure 8(b): Zero Delay ATPGDelay between M1 & M2 (simulation)Due to interconnect delay, M2 makes a late transition than M1 resulting in a glitch at reset resetting the flop.Figure 8(c): Real simulation ScenarioIn order to solve the problem, only a single multiplexer should be used in the reset path.4.2 Synthesis of switching logic for controlling resetAs mentioned above, a multiplexer is added before the reset of a flop. During synthesis, this multiplexer may be converted to complex gates (AOI - AND OR INVERT) as shown in figure 9(a).Figure 9(a): Synthesized muxThis scenario may result in a glitch at the reset of the flop leading to the false output.Figure 9(b): A failing scenarioTo prevent the glitch, this multiplexer should be preserved using pragma in RTL so that the logic is synthesized as a glitch-free multiplexer instead of any random AOI combination working as a multiplexer.5. Common source of inputs of combinational logicA combinational logic (for example 2-input AND gate or a 2-input OR gate) having both its inputs driven from same source with one being inverted will maintain the same constant output value regardless of the state of the driving node, but the output will probably contain a glitch when the driving node changes state.Figure 10: Two input AND gate with common input sources6. Combinational LoopsWhen the output of a combination logic is fed back to one of its input, a combination loop is formed. ATPG tool simulates the design assuming zero delay in combinational elements which may result in undetermined output for one or more input combinations.Figure 11: Combinational LoopsAs shown above, the input combination (A, B, C) = (1, 0, 0) will create oscillations in the circuit. To prevent this, the tool breaks the loop and models it as a TIEX block in the feedback path which results in coverage loss. Therefore such loops should be avoided.7. Analog BlocksSpecial handling is required for all analog blocks during testing when working with ATPG tools. Many analog blocks can have embedded digital logic and we should ensure that all this logic is testable. The digital inputs/outputs of the analog block interface needs to fully controllable and observable. At the same time analog inputs/outputs should be wrapped or safe-stated. There can be requirements based on test cases to keep analog portion of the block in a low power state (power down or sleep), along with its analog outputs either in high impedance state or driving a constant value, so special care needs to be taken care in such cases via safe stating of the block.8. Voltage and Temperature Triggers MaskingSOC has voltage and temperature detection circuits built in them, to generate interrupts in case either goes beyond the defined specification. During testing these signals need to be disabled or masked, since there are multiple tests like Very Low Voltage (VLV) Test, High Voltage Stress Test, etc., which will start showing fails if these interrupt signals are not masked.Figure 12: Analog Wrapper9. ConclusionIt is very important to make our designs DFT-friendly. The simple practices above can save much design time, effort, and frustration. Hence, it is recommended that designers ensure that all of the above design practices are followed.Also see:Design planning for large SoC implementation at 40nm: Guaranteeing predictable schedule and qfirst-pass silicon successProduct How To: DFT strategy for ARM processor-based designsqSOC DFT verification with static analysis and formal methodsq。
一种用于技术融合与演化路径探测的新方法:技术群相似度时序分析法
2021 年 6 月
第 40 卷
第6期
Journal of the China Society for Scientific and Technical Information, Jun. 2021, 40(6): 565-574
DOI: 10.3772/j.issn.1000-0135.2021.06.002
情
566
报
学
报
第 40 卷
tervals. The results of the study show that the additive manufacturing technology is undergoing a stage of rapid develop‐
ment, wherein the technology integration capability and inheritance is gradually enhanced. Additionally, this technical field
制造领域的技术发展路径分析。首先,以增材制造技术专利数据为分析对象,从专利文献记录层面、技术层面和技术
域层面,依次对该技术领域整体变化趋势进行测度;再次,基于 IPC (International Patent Classification) 分类号共现
原理,利用社区探测算法识别技术群,并通过余弦相似度关联相邻时间区间的技术群;最后,通过可视化技术展示不
groups, and correlates the technology groups in adjacent time intervals through cosine similarity. Finally, visualization tech‐
