Formal Languages Formal Languages D.1.7 [Software] Programming Techniques Visual Programmin
中国计算机学会推荐国际学术会议和期刊目录AB
IFIP International Conferences on Networking
International Conference on Network Protocols International Conference on Pervasive Computing and Communications Internet Measurement Conference International Symposium on Mobile Ad Hoc Networking and Computing International Workshop on Quality of Service
3 4 5 6
Eurocrypt
ESORICS CSFW RAID
7 8 9 10 11
NDSS DSN
ISOC Network and Distributed System Security Symposium The International Conference on Dependable Systems and Networks Theory of Cryptography Conference USENIX Security Symposium Workshop on Information Hiding
Annual Computer Security Applications Conference
CRYPTO 会议简称
ACSAC
B类
序号 1
2
ASIACRYPT
Annual International Conference on the Theory and Application of Cryptology and Information Security Annual International Conference on the Theory and Applications of Cryptographic Techniques European Symposium on Research in Computer Security IEEE Computer Security Foundations Workshop International Symposium on Recent Advances in Intrusion Detection
软件工程第八版(英文)机械工业出版社 课后习题

Part 1 OverviewChapter 1 Introduction1.1 FAQs about software engineering1.2 Professional and ethical responsibility Chapter 2 Socio-technical systems2.1 Emergent system properties2.2 Systems engineering2.3 Organisations, people and computer systems 2.4 legacy systemsChapter 3 Critical systems3.1 A simple safety-critical system 463.2 System dependability 473.3 Availability and reliability 513.4 Safety 553.5 Security 58Chapter 4 Software processes4.1 Software process models 654.2 Process iteration 714.3 Process activities 744.4 The Rational Unified Process 824.5 Computer-Aided Software Engineering 85 Chapter 5 Project management 925.1 Management activities 945.2 Project planning 965.3 Project scheduling 995.4 Risk management 104 RequirementsChapter 6 Software requirements 6.1 Functional and non-functional requirements6.2 User requirements6.3 System requirements6.4 Interface specification6.5 The software requirements document Chapter 7 Requirements engineering processes7.1 Feasibility studies7.2 Requirements elicitation and analysis7.3 Requirements validation7.4 Requirements managementChapter 8 System models 8.1 Context models8.2 Behavioural models8.3 Data models8.4 Object models8.5 Structured methodsChapter 9 Critical systems specification9.1 Risk-driven specification9.2 Safety specification9.3 Security specification9.4 Software reliability specificationChapter 10 Formal specification 10.1 Formal specification in the software process 10.2 Sub-system interface specification10.3 Behavioural specificationPart 3 DesignChapter 11 Architectural design 11.1 Architectural design decisions11.2 System organisation11.3 Modular decomposition styles11.4 Control styles11.5 Reference architecturesChapter 12 Distributed systems architectures12.1 Multiprocessor architectures12.2 Client-server architectures12.3 Distributed object architectures12.4 Inter-organisational distributed computing Chapter 13 Application architectures13.1 Data processing systems13.2 Transaction processing systems13.3 Event processing systems13.4 Language processing systems Chapter 14 Object-oriented design14.1 Objects and object classes14.2 An object-oriented design process14.3 Design evolutionKey PointsFurther ReadingExercisesChapter 15 Real-time software design15.1 System design15.2 Real-time operating systems15.3 Monitoring and control systems15.4 Data acquisition systemsChapter 16 User interface design 36216.1 Design issues 36616.2 The UI design process 37616.3 User analysis 37816.4 User interface prototyping 38116.5 Interface evaluation 383Part 4 Development 389 Chapter 17 Rapid software development 39117.1 Agile methods 39617.2 Extreme programming 39817.3 Rapid application development 40517.4 Software prototyping 409Chapter 18 Software reuse 415 18.1 The reuse landscape 41818.2 Design patterns 42118.3 Generator-based reuse 42318.4 Application frameworks 42618.5 Application system reuse 428 Chapter 19 Component-based software engineering19.1 Components and component models 19.2 The CBSE process19.3 Component compositionChapter 20 Critical systems development20.1 Dependable processes20.2 Dependable programming20.3 Fault tolerance20.4 Fault-tolerant architecturesChapter 21 Software evolution 21.1 Program evolution dynamics21.2 Software maintenance21.3 Evolution processes21.4 Legacy system evolutionPart 5 Verification and ValidationChapter 22 Verification and validation22.1 Planning verification and validation 22.2 Software inspections22.3 Automated static analysis22.4 Verification and formal methods Chapter 23 Software testing23.1 System testing23.2 Component testing23.3 Tes1 case design23.4 Tes1 automationChapter 24 Critical systems validation24.1 Reliability validation24.2 Safety assurance24.3 Security assessment24.4 Safety and dependability case's ManagementChapter 25 Managing people25.1 Selecting staff25.2 Motivating people25.3 Managing groups25.4 The People Capability Maturity Model Chapter 26 Software cost estimation 61226.1 Software productivity 61426.2 Estimation techniques 62026.3 Algorithmic cost modelling 62326.4 Project duration and staffing 637 Chapter 27 Quality management 64127.1 Process and product quality 64427.2 Quality assurance and standards 645 27.3 Quality planning 65227.4 Quality control 65327.5 Software measurement and metrics 655 Chapter 28 Process improvement 66528.1 Process and product quality 66728.2 Process classification 66928.3 Process measurement 67228.4 Process analysis and modelling 67328.5· Process change 67828.6 The CMMI process improvement framework 680Chapter 29 Configuration management29.1 Configuration management plclnning 29.2 Change management29.3 Version and release management 29.4 System building29.5 CASE tools for configuration managementEmerging TechnologiesSecurity engineering30.1 Security concepts30.2 Security risk management 30.3 Design for security 30.4 System survivabilityService-oriented software e:ngineering31.1 Services as reusable components 31.2 Service engineering31.3 Software development with servicesAspect-oriented software development32.1 The separation of concerns 32.2 Aspects, join points and pointcuts 32.3 Software engineering with aspectsChapter 1 ' IntroductionChapter 2 Socio-technical systemsChapter 3 iii Critical systemsChapter 6 • Software requirementsChapter 7 Requirements engineering processesChapter 8 System modelsChapter 9 Critical systems specificationChapter 10 Formal specificationChapter 11 Architectural designChapter 12 Distributed systems architecturesChapter 13 Application architecturesChapter 14 Object-oriented designChapter 15 Real-time software designChapter 16 User interface designChapter 17 Rapid software developmentChapter 18 Software reuseChapter 19 Component-based software engineeringChapter 20 Critical systems developmentChapter 21 Software evolutionChapter 22 Verification and validationChapter 23 Software testingChapter 24 Critical systems validationChapter 25 Managing people。
大学各专业名称英文翻译(一)——工学_ENGINEERING

大学各专业名称英文翻译(一)——工学ENGINEERING课程中文名称课程英文名称高等数理方法Advanced Mathematical Method弹塑性力学Elastic-Plastic Mechanics板壳理论Theory of Plate and Shell高等工程力学Advanced Engineering Mechanics板壳非线性力学Nonlinear Mechanics of Plate and Shell复合材料结构力学Structural Mechanics of Composite Material弹性元件的理论及设计Theory and Design of Elastic Element非线性振动Nonlinear Vibration高等土力学Advanced Soil Mechanics分析力学Analytic Mechanics随机振动Random Vibration数值分析Numerical Analysis基础工程计算与分析Calculation and Analysis of Founda tion Engineering结构动力学Structural Dynamics实验力学Laboratory Mechanics损伤与断裂Damage and Fracture小波分析Wavelet Analysis有限元与边界元分析方法Analytical Method of Finite Element and Boundary Element最优化设计方法Optimal Design Method弹性力学Elastic Mechanics高层建筑基础Tall Building Foundation动力学Dynanics土的本构关系Soil Constitutive Relation数学建模Mathematical Modeling现代通信理论与技术Emerging Communications Theory and Technology数字信号处理Digital Signal Processing网络理论与多媒体技术Multi-media and Network Technology医用电子学Electronics for Medicine计算微电子学Computational Microelectronics集成电路材料和系统电子学Material and System Electronics for In tegrated Circuits网络集成与大型数据库Computer Network Integrating Technology and Large scale Database 现代数字系统Modern Digital System微机应用系统设计Microcomputer Application Design计算机网络新技术Modern Computer Network Technologies网络信息系统Network Information System图像传输与处理Image Transmission and Processing图像编码理论Theory of Image Coding遥感技术Remote Sensing Techniques虚拟仪器系统设计Design of Virtual Instrument System生物医学信号处理技术Signal Processing for Biology and Medicine光纤光学Fiber OpticsVLSI的EDA技术EDA Techniques for VLSI电子系统的ASIC技术ASIC Design TechnologiesVLSI技术与检测方法VLSI Techniques & Its Examination专题阅读或专题研究The Special Subject Study信息论Information Theory半导体物理学Semiconductor Physics通信原理Principle of Communication现代数理逻辑Modern Mathematical Logic算法分析与设计Analysis and Design of Algorithms高级计算机网络Advanced Computer Networks高级软件工程Advanced Software Engineering数字图像处理Digital Image Processing知识工程原理Principles of Knowledge Engineering面向对象程序设计Object-Oriented Programming形式语言与自动机Formal Languages and Automata人工智能程序设计Artificial Intelligence Programming软件质量与测试Software Quality and Testing大型数据库原理与高级开发技术Principles of Large-Scale Data-Bas e and Advanced Development Technology自然智能与人工智能Natural Intelligence and Artificial Intelligence Unix操作系统分析Analysis of Unix System计算机图形学Computer GraphicsInternet与Intranet技术Internet and Intranet Technology多媒体技术Multimedia Technology数据仓库技术与联机分析处理Data Warehouse and OLAP程序设计方法学Methodology of Programming计算机信息保密与安全Secrecy and Security of Computer Information电子商务Electronic Commerce分布式系统与分布式处理Distributed Systems and Distributed Processing并行处理与并行程序设计Parallel Processing and Parallel Programming模糊信息处理技术Fuzzy Information Processing Technology人工神经网络及应用Artificial Intelligence and Its Applications Unix编程环境Unix Programming Environment计算机视觉Computer Vision高级管理信息系统Advanced Management Information Systems信息系统综合集成理论及方法Theory and Methodology of Information n System Integration计算机科学研究新进展Advances in Computer Science离散数学Discrete Mathematics操作系统Operating System数据库原理Principles of Database编译原理Principles of Compiler程序设计语言Programming Language数据结构Data Structure计算机科学中的逻辑学Logic in Computer Science面向对象系统分析与设计Object-Oriented System Analysis and Design高等数值分析Advanced Numeric Analysis人工智能技术Artificial Intelligence Technology软计算理论及应用Theory and Application of Soft-Computing逻辑程序设计与专家系统Logic Programming and Expert Systems模式识别Pattern Recognition软件测试技术Software Testing Technology高级计算机网络与集成技术Advanced Computer Networks and Integration Technology 语音信号处理Speech Signal Processing系统分析与软件工具System Analysis and Software Tools计算机仿真Computer Simulation计算机控制Computer Control图像通信技术Image Communication Technology人工神经网络及应用Artificial Intelligence and Its Applications计算机技术研究新进展Advances in Computer Technology环境生物学Environmental Biology水环境生态学模型Models of Water Quality环境化学Environmental Chemistry环境生物技术Environmental Biotechnology水域生态学Aquatic Ecology环境工程Environmental Engineering环境科学研究方法Study Methodology of Environmental Science藻类生理生态学Ecological Physiology in Algae水生动物生理生态学Physiological Ecology of Aquatic Animal专业文献综述Review on Special Information废水处理与回用Sewage Disposal and Re-use生物医学材料学及实验Biomaterials and Experiments现代测试分析Modern Testing Technology and Methods生物材料结构与性能Structures and Properties of Biomaterials计算机基础Computer Basis医学信息学Medical Informatics计算机汇编语言Computer Assembly Language学科前沿讲座Lectures on Frontiers of the Discipline组织工程学Tissue Engineering生物医学工程概论Introduction to Biomedical Engineering高等生物化学Advanced Biochemistry光学与统计物理Optics and Statistical Physics图像分析Image Treatment数据处理分析与建模Data Analysis and Constituting Model高级数据库Advanced Database计算机网络Computer Network多媒体技术Technology of Multimedia软件工程Software Engineering药物化学Pharmaceutical Chemistry功能高分子Functional Polymer InternetIntranet程序设计方法学Methods of Programming InternetIntranet高分子化学与物理Polymeric Chemistry and Physics医学电子学Medical Electronics现代仪器分析Modern Instrumental Analysis仪器分析实验Instrumental Analysis Experiment食品添加剂Food Additives Technology高级食品化学Advanced Food Chemistry食品酶学Food Enzymology现代科学前沿选论Literature on Advances of Modern Science波谱学Spectroscopy波谱学实验Spectroscopic Experiment食品贮运与包装Food Packaging液晶化学Liquid Crystal Chemistry高等有机化学Advanced organic Chemistry功能性食品Function Foods食品营养与卫生学Food Nutrition and Hygiene食品生物技术Food Biotechnology食品研究与开发Food Research and Development有机合成化学Synthetic organic Chemistry食品分离技术Food Separation Technique精细化工装备Refinery Chemical Equipment食品包装原理Principle of Food Packaging表面活性剂化学及应用Chemistry and Application of Surfactant天然产物研究与开发Research and Development of Natural Products 食品工艺学Food Technology生物化学Biochemistry食品分析Food Analysis食品机械与设备Food Machinery and Equipment。
PA-chapter01-What is Software

Pfleeger and Atlee, Software Engineering: Theory and Practice
Chapter 1.9
1.2 How Successful Have We Been?
• Perform tasks more quickly and effectively
– Word processing, spreadsheets, e-mail
Pfleeger and Atlee, Software Engineering: Theory and Practice Chapter 1.13
1.3 What is Good Software?
• Good software engineering must always include a strategy for producing quality software • Three ways of considering quality
• Method: refers to a formal procedure; a formal “recipe” for accomplishing a goal that is typically independent of the tools used • Tool: an instrument or automated system for accomplishing something in a better way • Procedure: a combination of tools and techniques to produce a product • Paradigm: philosophy or approach for building a product (e.g., OO vs structured approaches)
Under consideration for publication in Formal Aspects of Computing A Formal Relationship Be

Under consideration for publication in Formal Aspects of ComputingA Formal Relationship Between Program Slicing and Partial EvaluationDavid W.Binkley1,Sebastian Danicic2,Mark Harman3and Lahcen Ouarbya21Department of Computer Science,Loyola College,4501N.Charles Street,Baltimore,Maryland21210-2699,USA;2Department of Computing,Goldsmiths College,University of London,New Cross,London SE146NW,UK.3Department of Computer Science,King’s College London,Strand,London WC2R2LS,UK.Keywords:Conditioned Program Slicing;Partial EvaluationAbstract.A formal relationship between program slicing and partial evaluation is established.It is proved that for terminating programs,a residual program produced by partial evaluation is semantically equivalent to a conditioned slice.1.IntroductionPartial evaluation and slicing are both program specialisation techniques that attempt to simplify a program. Partial evaluation[JGS93]involves the evaluation of static computation,while slicing[BH04,Tip95]involves the removal of parts of the program which do not affect the values of selected variables at execution points of interest.Both techniques have common applications including optimisation,program comprehension,dependence analysis and testing[BF98,CHM+98a,Das98,DFM96,DHN98,Ers78,JR94,HD97].It may be productive, in the future,therefore,to explore the similarities and differences between partial evaluation and slicing and to investigate hybrid approaches that combine the two.In spite of this,research on partial evaluation and slicing has largely been conducted by two disjoint communities and so there has been relatively little work on the similarities and differences between the two techniques and none which establishes any formal relationship between the two.This paper explores these similarities and differences,establishing a formal relationship between the residual program of partial evaluation and a form of slice known as a conditioned slice[CCD98,DFHH00, DDH+02,DDH04,FDHH04,DDF+04,HHD+01,FHHD01,HHF+02].The paper uses a program projection2 D.Binkley,S.Danicic,M.Harman,L.Ouarbyaframework[HBD03,HD97]that allows for the definition of various forms of program projection,which preserve only a projection of the original program’s semantics.The rest of this paper is organised as follows:Sections2and3briefly review partial evaluation and slicing respectively.A semantics that is preserved by slicing is given in Section4.Section5introduces the theoretical framework of program projection which allows different transformation methodologies to be compared.It is shown how different slicing techniques can be expressed using the framework of Section5and the semantics of Section4.Section6expresses partial evaluation in terms of the framework in order to formally compare it with slicing.It is established that a residual program of a terminating program is semantically equivalent to a conditioned slice.Section7describes some applications of the theoretical results of the paper,showing how partial evaluation and amorphous slicing can be combined to produce amorphous conditioned slices and how the precision of syntax preserving conditioned slicing could be improved using information from partial evaluation.Section8presents related work and Section9summarises the paper.2.Partial EvaluationMany programs contain computations that can be performed at compile time.Optimising compilers exploit such computations by pre-computing their values.Partial evaluation(also known as mixed computation) takes this process one step further by allowing some of the inputs to a program to be statically determined(or statically‘bound’).By propagating that binding-time information‘forward’through the program,additional static computations can be identified.Static computations can be performed at compile time,often reducing the program’s size and run time.Partial evaluation was originally considered as an extension of compiler theory,used as a means of im-proving efficiency[Ers78]and of creating compilers and compiler generators from interpreters[Fut71,Fut99a, Fut99b,JSS89].Initial work concerned declarative languages,for which the semantics were comparatively ‘clean’[BHO+76,GJ89,JSS85,Har78,Ste75].Consequently,the propagation of binding time information was definable in terms of the formal semantics of the programming language concerned.More recently, partial evaluation-based approaches to software engineering[CHM+98a],program comprehension[BF98], state-based testing[DHN98]and multimedia computing[Dra98]have been explored.The initial work on declarative language partial evaluation has also been extended to the imperative programming paradigm, most notably by the early work on[And92,GJ91,KKZG95]and by more recent work on partial evaluation using dependence graphs by Das[Das98]and the Tempo partial evaluation system for a large subset of the C programming language[CHM+98b].Algorithms for partial evaluation typically consist of two phases:an initial Binding Time Analysis(BTA) followed by a manipulation phase(called‘specialisation’).The result of this specialisation is a program, called the residual program.Some authors[RT96,SGJ94]use the term‘specialisation’to describe the more general concept of tailoring a program to a specific task.This nomenclature includes both partial evaluation and slicing as special cases of specialisation.Example.Consider the power program in Figure1(in order to simplify the following example,it will be assumed that the input to a program is taken from those variables that are referenced before being defined. This will allow program fragments and whole programs to be considered in a similar way).Suppose the value of n is determined to be4.The results of BTA for this program are shown in the right-hand sections of thefigure(S indicates that a variable is determined to be static at the associated point,D indicates that it is determined to be dynamic).Using the results of BTA,it can be seen that the variable n remains static throughout the computation and therefore it will be safe to specialise the program by unfolding the loop controlled by n.This specialisation phase leads to the construction of the residual program in Figure2.As originally formulated[BHO+76,Ers78,Fut71,Har78,JSS85,Ste75],the residual program was con-structed with respect to the instantiation of selected inputs withfixed values.Futamura and Nogi[FN87] introduced a more generalised form of partial evaluation,in which residual programs are constructed with respect to a set of initial states characterised by afirst order predicate logic expression on input variables. Gl¨u ck and Sørensen[GS96]cite four varieties of partial evaluator.These are•Monovariant,where each function of the original program results in at most one function in the residual program.•Polyvariant where each function of the original program may result in more than one function in the residual program.A Formal Relationship Between Program Slicing and Partial Evaluation3r=1;D S Swhile(n>0)D S D{n=n-1;D S Dr=r*x;}D S Dprintf("%d",r);D S Dr=1;r=r*x;r=r*x;r=r*x;r=r*x;printf("%d",r);base=2;count=0;for(i=0;i<N;i++)for(i=0;i<N;i++){if(A[i]%base==0){count++;R[N-i-1]=A[i];R[N-i-1]=A[i];}}b=(A[0]==R[0]);b=(A[0]==R[0]);b=(A[0]==A[N-1]);Fig.3.Amorphous and Syntax-preserving Slices4 D.Binkley,S.Danicic,M.Harman,L.Ouarbyamaintenance[GL91],testing[Bin98,Bin97,GHS92,HD95,HHD99,HHF+02],program integration[HPR89, BHR95]and software conformance certification[KS98].There are several surveys of slicing,techniques and applications[BG96,HH01,De01,Tip95].In addition to capturing a projection of a program’s semantics,the original application of slicing required a syntactic property:a slice must preserve a projection of the original program’s syntax.Traditionally,slicing has used a‘statement deletion’for this projection largely for historical reasons.This derives from the original application of slicing[Wei79]to debugging,where the motivation for slicing was to remove statements and associated control structures that could not have been responsible for an error.The importance of this syntactic requirement varies from application to application.For re-engineering,program comprehension and testing it is primarily the semantic property of a slice that is of interest.Conditioned slicing[CCD98]is the act of simplifying a program assuming that the states of the program at certain chosen points in its execution satisfy certain properties.What distinguishes conditioned slicing from other forms of slicing is mainly its implementation[DFHH00,DDH+02,FDHH04,DDF+04].Conditioned slicing combines the standard techniques of slicing with symbolic execution and theorem proving.Conditioned slicers are required to reason about the validity of paths under certain conditions using symbolic execution and automated theorem proving.The simplifying power of the conditioned slicer depends on two things:1.The precision of the symbolic executor which handles propagation of state and path information.2.The precision of the underlying theorem prover which determines the truth of propositions about statesand paths.By using an approximation to a program’s semantics using a form of symbolic execution,and by being willing to accept approximate results from the theorem proving itself,conditioning allows us to adopt reasoning that does not require the full force of inductive proofs.The theorem proving used in programming conditioning is lightweight when compared to the theorem proving required for a complete formal analysis of a program. As in the case of traditional slicing,conditioned slicing only simplifies programs by deletion.Semantically,as will be seen later,conditioned slicing is very closely related to both traditional slicing and partial evaluation.Amorphous slicing[HBD03]is a variation of slicing,in which simplification is not limited to statement deletion.For this reason it is clearly closer to partial evaluation than the other forms.To illustrate,consider the example in Figure3.The original program reverses the array A,keeping a count(in the variable count) of the number of array elements which are exactly divisible by base.The program also records whether or not thefirst and last element of the array are identical(in the variable b).The integer N(the size of the array A),is a compile-time constant.The array A is an input parameter to the program fragment.The original program is in the leftmost column of thefigure.The syntax-preserving end-slice for the value of the variable b is in the central column and the amorphous slice is in the rightmost column of thefigure.Figure3makes it clear that amorphous slices can be smaller than their syntactically constrained counter-parts.Of course,it is a more challenging problem to compute amorphous slices.Recently proposed algorithms [Bin99,HHZM01]represent initial attempts at addressing this problem.Notice also that the variable base is statically determined,and so it could be‘partially evaluated away’in the original program and in its syntax-preserving end-slice.Since N is also statically determined,the loop can also be replaced by a sequence of N assignments.The combination of these partial evaluation steps together with syntax-preserving end-slicing,could almost produce the amorphous slice,as shown in Figure4. This suggests that amorphous slicing might be achievable as a combination of syntax-preserving end-slicing and partial evaluation.However,the program produced by mixing partial evaluation and syntax-preserving end-slicing,is only valid slice because the computation was static for the unwanted array elements,R[i]for (i<N)and the unwanted variables base and count.Had the value of N or base been inputs,then partial evaluation would have had no effect.However,this example shows that there is a connection between the residual program of partial evaluation and amorphous forms of program slicing.This observation motivates the formal examination of this connection which follows.4.Semantics of SlicingOriginally,program slicing was defined in terms of an algorithm[Wei79].Informally,this algorithm simplified programs both syntactically,and semantically.Given a program P and a set of variables J,Weiser’s algorithm produces a program P′smaller than P which‘behaves the same’with respect to J.Weiser,in fact proved that in all states where P terminates,P′also terminates and agrees with P on all the variables in J.A Formal Relationship Between Program Slicing and Partial Evaluation5 Original Partially Evaluated Syntax-Preserving end-slice for b1Other authors have produced semantics which they claim to be preserved by slicing.These include the lazy semantics of Cartwright and Felleisen[CF89]and the transfinite semantics of Giacobazzi and Mastroeni[GM03].6 D.Binkley,S.Danicic,M.Harman,L.OuarbyaM:P→Σ⊥→Σ⊥s kip statementM[[abort]]σ ⊥Assignment statementsM[[S1;S2]]σ M[[S2]](M[[S1]]σ)i f statementsM[[w hile(b)S]] fix(λf·λσ·E[[b]]σ→f(M[[S]]σ),σ)Fig.5.Standard Semantics for a Simple Procedural language.Definition1(det:E→P(V)).Given an expression e,det(e)is defined as follows:1.For all x∈det(e),there exists two statesσ1,σ2differing only on x such that:E[[e]]σ1=E[[e]]σ2.2.For all x∈det(e),and for all statesσ1,σ2differing only on x,E[[e]]σ1=E[[e]]σ2.If det(e)contains a variable which has⊥as a value inσ,then the whole expression is evaluated to⊥inσ. Otherwise the lazy value,E L,of an expression is the same as its strict value,E.The meaning of an expression in our lazy semantics is the function,E L:E→Σ⊥−→V⊥.given by E L eσ ⊥if∃v∈det(e)withσv=⊥.E eσotherwise.The lazy meaning of a program is given by the function M L,which,as in the case of standard semantics, is a state to state function:M L:P−→Σ⊥−→Σ⊥.Lazy semantics of the s kip statementM L[[abort]]σ σUnlike in standard semantics,the lazy meaning of the abort statement is the same as lazy meaning ofA Formal Relationship Between Program Slicing and Partial Evaluation7Program p Program q Program r Program sM L[[x=e]]σ σ[x←E L[[e]]σ]As in standard semantics,the meaning of an assignment is obtained by updating the state with the new value of the variable assigned to it.In the case of lazy semantics,this value is the lazy value of the corre-sponding expression.Since in lazy semantics,there are states which map some variables to proper values and other variables to⊥,the assignment rule implies that a variable can‘recover’from being undefined as demonstrated by program p in Figure6,where after the loop x has the value⊥but it recovers to5 after the assignment x=5.Lazy semantics of the statement sequencesM L[[i f(B)S1e lse S2]]σ E L[[B]]σ→M L[[S1]]σ,M L[[S2]]σ,M L[[S1]]σ⊓M L[[S2]]σwhereσ1⊓σ2,the meet ofσ1andσ2,is defined asλi·σ1(i)=σ2(i)→σ1(i),⊥and the notation a→b,c,d is shorthand for if a is true return b otherwise if a is false return c otherwise if a is⊥return d and the notation a→b,c is shorthand for if a is true return b otherwise return c.The difference between this and standard semantics is when the guard evaluates to⊥.If a variable x is assigned different values in the t hen and e lse parts its lazy value will be⊥.On the other hand,if the value of x is the same in the t hen and e lse parts then this should be itsfinal value even if the guard is ⊥,as,in this case,the value of x does not depend on the guard.Consider,for example,program q in Figure6.Given an initial stateσ={x→1,y→1,z→⊥},the value i f predicate,z>0inσis⊥.However,thefinal value of the variable x is1whichever branch of the conditional is executed.For this reason,the lazy value of the variable x after executing program q in σis deemed to be1.8 D.Binkley,S.Danicic,M.Harman,L.OuarbyaThe value of the variable y has different values after executing the t hen branch from when executing e lse branch,and hence,thefinal value of the variable y is⊥2.Before the lazy meaning of a w hile loops can be given,loop unfoldings,W n(B,S)for each n∈I N are defined:W0(B,S) abortW n+1(B,S) i f(B){S;W n(B,S)}e lse s kipLazy semantics of w hile loops2Unlike this semantics,the value of the variable x after executing program q in Figure6in the stateσwhen using the lazy semantics by Cartwright and Felleisen[CF89]or the transfinite semantics by Giacobazzi and Mastroeni[GM03]is⊥.This is a result of the fact that their semantics loses all information about the variables defined in the t hen or e lse parts of an i f statement in states where its predicate is undefined.A Formal Relationship Between Program Slicing and Partial Evaluation 9That is,the syntax must not ‘get worse’as a result of projection of a program,while the semantics of the projected program must remain equivalent to the original.Definition 3(A program transformation satisfies a projection).A program transformation f satisfies a (<∼,≈)–projection if and only if for all programs p ,f (p )is a (<∼,≈)–projection of p .Clearly,every program transformation satisfies the weakest (<∼A ,≈A )–projection where p <∼A q and p ≈A qfor all programs p and q .Trivially,if a technique satisfies a particular (<∼,≈)–projection then it satisfies all weaker projections.The weakest projection is useless as it tells us nothing.Clearly the stronger projection that we find,the more precisely we capture behaviour.The purpose of the projection framework is to capture the behaviour of each technique or algorithm sufficiently strongly to at least distinguish it from other techniques.Alternatively,the projection framework can be used in the inverse manner for not categorising but defining classes of algorithms.We may define,say,a ζ–transformation to be any transformation which satisfies (<∼ζ,≈ζ)–projection where <∼ζis a given ordering and ≈ζis a given equivalence as defined above.ing the Framework to Express SlicingThe projection framework has successfully been used to categorise a variety of slicing techniques.As an introduction to the projection framework it is shown how three kinds of slices:(traditional)syntax-preserving slices,amorphous slices,and conditioned slices are categorised using it.This subsection describes the syntactic and semantic relations for these three kinds of slices.It is then shown how partial evaluation can also be expressed using the framework.5.1.1.Syntax-Preserving SlicingIt is helpful in discussing slicing to think of each line of a program as a single (labelled or numbered)node of a program’s Control Flow Graph (CFG).The following definition formalises the oft-quoted remark:“a slice is a subset of the program from which it is constructed.”It defines Syntax-Preserving Ordering ,the ordering for syntax-preserving slicing,denoted <∼SP .(In the sequel,subscripts are added to <∼and ≈to distinguish different instantiations of the respective relations.)Definition 4(Syntax-Preserving Ordering).Let F be a partial function which takes a program and returns a function from line numbers to statements,such that the function F (p )maps l to c iffprogram p contains the statement c at line number l .Syntax-preserving syntactic ordering is defined as follows:p <∼SP q ⇔F (p )⊆F (q ).Definition 5(End-Slice Equivalence).Given two programs p and q ,and a set of variables V ,p is end-slice semantically equivalent to q ,written p ≈V SPq ,if and only if for all states σ,for all variables v ∈V ,M L [[p ]]σv =M L [[q ]]σv.Instantiating Definitions 4and 5into Definition 2,the following definition of an end-slice is obtained:Definition 6(Syntax-Preserving End-Slice).Program q is a Syntax-Preserving End-slice of program p with respect to set of variables V if and only if qis a (<∼SP ,≈V SP )–projection of p .5.1.2.Amorphous SlicingTo define amorphous slicing,only the syntactic relation needs to be altered;the semantic relation remains the same.For amorphous slicing,a natural choice for a syntactic relation is that p is less than q if it contains10 D.Binkley,S.Danicic,M.Harman,L.Ouarbya fewer statements.Such a definition of the syntactic relation naturally depends upon how statements are to be counted.The approach adopted in this paper,in keeping with the spirit of slicing,is to count the nodes in the CFG [HRB88,OO84].Definition 7(Amorphous Syntactic Ordering).Let F (p )be the number of nodes in the CFG of program p .The amorphous syntactic relation,<∼AS ,is defined as follows:p <∼AS q ⇔F (p )≤F (q )Definition 8(Amorphous Semantic Equivalence).≈AS =≈SPDefinition 9(Amorphous Static Slicing).Program q is an amorphous static slice of program p with respect to the set of variables V if and only if qis a (<∼AS ,≈V SP )–projection of p .Amorphous slicing subsumes (i.e.,it is weaker than)syntax-preserving end-slicing because <∼SP ⊆<∼AS and ≈AS =≈SP .As a consequence of this,any implementation of syntax-preserving slicing is also an implementation of amorphous slicing,albeit a rather sub-optimal implementation.Therefore,there will always be an amorphous slice which contains no more CFG nodes than the syntax-preserving end-slice constructed for the same set of variables.Of course,there will often be an amorphous slice which contains fewer nodes than the corresponding syntax-preserving end-slice.This makes amorphous slicing attractive when preservation of syntax is unimportant.5.1.3.Conditioned SlicingFinally,conditional slicing is defined in the projection framework.As will be seen,the residual program produced by partial evaluation is most closely related to a conditioned slice [CCD98].Traditionally [CCD98,DFHH00]conditioned slices have been constructed by statement deletion.Thus,the definition of the con-ditioned slice syntactic ordering is the same as the syntax-preserving ordering used for syntax-preserving end-slicing.Definition 10(Conditioned Syntactic Ordering).The conditioned syntactic relation,<∼CS ,is defined as follows:<∼CS =<∼SPFor example,the conditioned program in Figure 7is ‘lower’than the original program according to <∼CS ,because the conditioned program contains a subset of the statements of the original.The semantic equivalence preserved by conditioned slicing is defined as follows:Definition 11(Conditioned Semantic Equivalence).Program p ′is conditioned equivalent to program p with respect to (V,Σ),written p ≈(V,Σ)CSp ′if and only if ∀σ∈Σ,∀v ∈V,M L [[p ]]σv =M L [[p ′]]σvThat is,for a set of states Σand variables V conditioned slicing preserves the values of variables in V when the program is executed in a state in Σ.For example,the conditioned program in Figure 7is conditioned equivalent to the original with respect to (x,y )when x is the set of all program variables and y is the set of all possible states,since the conditioned program and the original produce identical answers for all variables in all states.Combining these two definitions into the framework yields:Definition 12(Conditioned Slice).Program q is a conditioned slice of program p with respect to the slicing criterion (V,i )if and only if q is a (<∼CS ,≈(V,Σ)CS )–projection of p .Original program Conditioned programThe syntactic ordering used in partial evaluation also differs from that used in both syntax-preserving and amorphous slicing.There are situations where the two relations will agree,for example,both would allow3the transformation[[x=x+2;x=x-1;]]⇒[[x++;]]However,there are also situations where the two relations disagree.This occurs,for example,when a transformation reduces the number of CFG nodes,but increases the execution time.In this case amorphous slicing allows the transformation,but residualisation does not.The preceding discussion indicates that partial evaluation is both semantically and syntactically different from slicing(though bothfit the projection framework defined in Section5).However,there are similarities between the two approaches to program specialisation.Specifically,setting aside the differences between the syntactic ordering for slicing and partial evaluation,we will prove the following statement can be made about the relationship between partial evaluation and conditioned slicing.Theorem6.1.Let q be a residual program constructed from a program p,with respect to a set of statesΣIf q terminates in all statesσinΣthen q is semantically equivalent to a conditioned slice of p constructed with respect to the slicing criterion I−(SV(p,Σ),Σ).Since partial evaluation is defined in terms of strict semantics,M,and conditioned slicing in terms of lazy semantics M L,wefirst need a result which says that a terminating program’s lazy and strict meanings are identical:Proposition1.Let P be a program andσbe a state inΣ,then M[[P]]σ=⊥=⇒M L[[P]]σ=M[[P]]σ. Proof.This is proved by structural induction over the language being considered.s kip statementThe result is vacuously true as,M[[abort]]σ=⊥for allσinΣ.Assignment statementsLetσbe a state inΣwith M[[i f(B)S1e lse S2]]σ=⊥.Then it follows that E L[[B]]σ=E[[B]]σ=⊥asσis a state inΣ.If E L[[B]]σ=True,then M[[i f(B)S1e lse S2]]σis reduced to just M[[S1]]σand M L[[i f(B)S1e lse S2]]σis reduced to just M L[[S1]]σand the result follows immediately from the induc-tion hypothesis.Similarly,if E L[[B]]σ=False as M[[i f(B)S1e lse S2]]σis reduced to just M[[S2]]σand M L[[i f(B)S1e lse S2]]σis reduced to just M L[[S2]]σ.Sequences3This transformation is allowed by the definition of partial evaluation,but is not typically exploited in partial evaluation systems.Letσ∈Σwith M[[S1;S2]]σ=⊥.Hence,M[[S2]]M[[S1]]σ=⊥and M[[S1]]σ=⊥.The result follows immediately by application of the semantics rule for sequences and the induction hypothesis:M L[[S1;S2]]σ=M L[[S2]]M L[[S1]]σ(by definition)=M[[S2]]M[[S1]]σ(induction hypothesis)=M[[S1;S2]]σ.While loops7.ApplicationsThe correspondence between partial evaluation and conditioned slicing has potential practical applications in program slicing.This section illustrates some of these potential applications,by showing how existing partial evaluation and slicing techniques could be combined in order to improve slicing.Consider the example in Figure8.In this example,there are four program fragments.These will be referred to by points of the compass.The original program is the northerly program fragment.Previous work on conditioned slicing could be applied to this program fragment in an attempt to reduce the program, using knowledge gleaned from the symbolic states of the program as it is symbolically executed.For the purpose of this discussion,it will be supposed that the set of states with respect to which the conditioning takes places is the set of all possible states.Applying the existing approaches to conditioning[DDF+04,FDHH04]the program would not be sim-plified,because current approaches to conditioning have no ability to explore multiple loop executions.For example,using the tool ConSUS[DDF+04],the conditioned slice obtained is the entire program.ConSUS combines symbolic execution with theorem proving to obtain conditioned slices.The symbolic executor works out path conditions,while the theorem prover is used to determine which statements must fail to be executed due to the values of these path conditions.ConSUS can recognise some situations where a loop fails to exe-cute and can exploit limited information about the symbolic execution of the loop,but it fails to detect that the test if total>10is redundant.This is because the symbolic execution does not symbolically execute the unfolded body of the loop.However,if the program were to have beenfirst partially evaluated,then the loop body would have been ing this unfolded loop body,the symbolic executor would be able to provide more information about the terminating state of the loop to the theorem prover,allowing it to determine that the test if total>10is redundant.This would lead to the improved syntax preserving conditioned slice in the easterly quadrant.This conditioned slice is thinner than that produced by any existing tool for conditioned slicing, showing that the combination of partial evaluation and conditioned slicing can produce improvements in existing conditioned slicing approaches.A more dramatic improvement in slicing technology is obtained by exploiting the combination of amor-phous slicing and partial evaluation.Amorphous slicing is known to reduce the size of slices because it allows transformation to be applied[De01,DDF+04,HBD03,War02].This is to be contrasted with syntax–preserving slicing which allows only statement deletion.It would be desirable to construct a tool for amorphous conditioned slicing.Such a tool would im-prove the simplification power of static syntax–preserving slicing,both because it would be amorphous(not syntax–preserving)and because it would be conditioned(not static).Hitherto,no such slicing tool has been constructed;it has proved hard tofind effective algorithms for syntax–preserving conditioned slicing,so amorphous conditioned slicing would seem to be an even harder problem.Ward[War03]has shown how a form of amorphous conditioned slicing(called a semantic slice)could be produce by combining the transfor-mations of FermaT[War99]with slicing,but he gives no general algorithm for semantic slicing.The existence of effective algorithms for amorphous conditioned slicing therefore remains an open problem.The combination of amorphous static slicing and partial evaluation may yield algorithms for amor-phous conditioned slicing.Consider the program in the southerly quadrant of Figure8.This program is an amorphous conditioned slice of the original program in the northerly quadrant.Currently,no slicing tool is available which can produce this program and there are no algorithms in the literature for amorphous conditioned slicing.Applying partial evaluation(using a tools like tempo[CHM+98b]),to the original program in the northerly quadrant,the residual program in the westerly quadrant is obtained.By applying amorphous slicing to this residual program(using a tool like LinIAS[HHM+04])the desired amorphous conditioned slice in the southerly quadrant is obtained.The primary role of this paper is theoretical;it demonstrates the correspondence between slicing and partial evaluation.However,the importance of this result is likely to be the application of the connection between the two,in work on practical techniques for computing slices.The tantalising observations in this section show that it is possible to combine existing techniques for amorphous slicing and partial evaluation to produce amorphous conditioned slices;a form of slicing for which there are no currently existing techniques.。
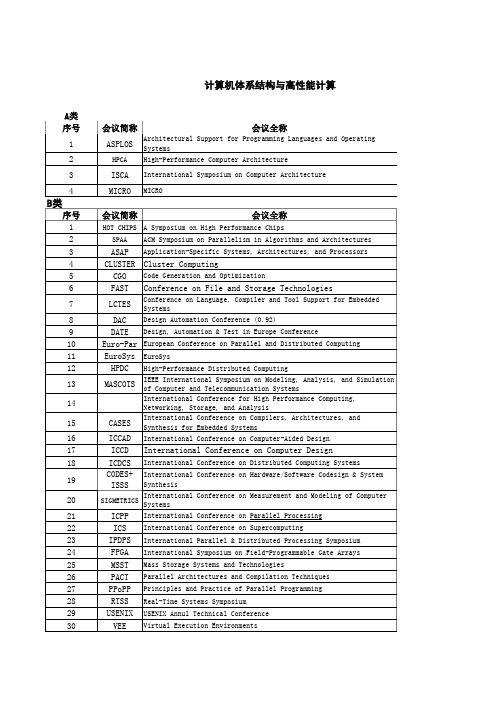
计算机科学ABC类会议分类表

Applications and MediaI3DG: ACM-SIGRAPH Interactive 3D GraphicsSIGGRAPH: ACM SIGGRAPH ConferenceACM-MM: ACM Multimedia ConferenceDCC: Data Compression ConfSIGMETRICS: ACM Conf on Meas. & Modelling of Comp SysSIGIR: ACM SIGIR Conf on Information RetrievalPECCS: IFIP Intl Conf on Perf Eval of Comp \& Comm SysWWW: World-Wide Web ConferenceIEEE VisualizationEUROGRAPH: European Graphics ConferenceCGI: Computer Graphics InternationalCANIM: Computer AnimationPG: Pacific GraphicsNOSSDAV: Network and OS Support for Digital A/VPADS: ACM/IEEE/SCS Workshop on Parallel \& Dist SimulationWSC: Winter Simulation ConferenceASS: IEEE Annual Simulation SymposiumMASCOTS: Symp Model Analysis \& Sim of Comp \& Telecom SysPT: Perf Tools - Intl Conf on Model Tech \& Tools for CPENetStore: Network Storage SymposiumMMCN: ACM/SPIE Multimedia Computing and NetworkingJCDL: Joint Conference on Digital Librariese-Science: IEEE International Conference on e-science and Grid Computing ICGC: International Conference on Grid ComputingACM-HPC: ACM Hypertext ConfMMM: Multimedia ModellingICME: Intl Conf on MMedia & ExpoAPweb: Asia Pacific Web ConferenceDSS: Distributed Simulation SymposiumSCSC: Summer Computer Simulation ConferenceWCSS: World Congress on Systems SimulationESS: European Simulation SymposiumESM: European Simulation MulticonferenceHPCN: High-Performance Computing and NetworkingGeometry Modeling and ProcessingWISE: Intl Conf on Web Information Systems EngineeringDS-RT: Distributed Simulation and Real-time ApplicationsIEEE Intl Wshop on Dist Int Simul and Real-Time ApplicationsECIR: European Colloquium on Information RetrievalEd-MediaIMSA: Intl Conf on Internet and MMedia SysData BasesSIGMOD: ACM SIGMOD Conf on Management of DataPODS: ACM SIGMOD Conf on Principles of DB SystemsVLDB: Very Large Data BasesICDE: Intl Conf on Data EngineeringICDT: Intl Conf on Database TheorySSD: Intl Symp on Large Spatial DatabasesDEXA: Database and Expert System ApplicationsFODO: Intl Conf on Foundation on Data OrganizationEDBT: Extending DB TechnologyDOOD: Deductive and Object-Oriented DatabasesDASFAA: Database Systems for Advanced ApplicationsCIKM: Intl. Conf on Information and Knowledge ManagementSSDBM: Intl Conf on Scientific and Statistical DB MgmtCoopIS - Conference on Cooperative Information SystemsER - Intl Conf on Conceptual Modeling (ER)COMAD: Intl Conf on Management of DataBNCOD: British National Conference on DatabasesADC: Australasian Database ConferenceADBIS: Symposium on Advances in DB and Information SystemsDaWaK - Data Warehousing and Knowledge DiscoveryRIDE WorkshopIFIP-DS: IFIP-DS ConferenceIFIP-DBSEC - IFIP Workshop on Database SecurityNGDB: Intl Symp on Next Generation DB Systems and AppsADTI: Intl Symp on Advanced DB Technologies and IntegrationFEWFDB: Far East Workshop on Future DB SystemsMDM - Int. Conf. on Mobile Data Access/Management (MDA/MDM)ICDM - IEEE International Conference on Data MiningVDB - Visual Database SystemsIDEAS - International Database Engineering and Application Symposium MiscellaneousRECOMB: Annual Intl Conf on Comp Molecular BiologyAMIA: American Medical Informatics Annual Fall SymposiumDNA: Meeting on DNA Based ComputersCSCW: Conference on Computer Supported Cooperative WorkMEDINFO: World Congress on Medical InformaticsInternational Conference on Sequences and their ApplicationsECAIM: European Conf on AI in MedicineAPAMI: Asia Pacific Assoc for Medical Informatics ConfINBS: IEEE Intl Symp on Intell. in Neural & Bio SystemsSAC: ACM/SIGAPP Symposium on Applied ComputingICSC: Internal Computer Science ConferenceISCIS: Intl Symp on Computer and Information SciencesICSC2: International Computer Symposium ConferenceICCE: Intl Conf on Comps in EduWCC: World Computing CongressPATAT: Practice and Theory of Automated TimetablingSystem Technology (Including networking and security) SIGCOMM: ACM Conf on Comm Architectures, Protocols & AppsSPAA: Symp on Parallel Algms and ArchitecturePODC: ACM Symp on Principles of Distributed ComputingPPoPP: Principles and Practice of Parallel ProgrammingMassPar: Symp on Frontiers of Massively Parallel ProcRTSS: Real Time Systems SympSOSP: ACM SIGOPS Symp on OS PrinciplesOSDI: Usenix Symp on OS Design and ImplementationCCS: ACM Conf on Comp and Communications SecurityS&P: IEEE Symposium on Security and PrivacyMOBICOM: ACM Intl Conf on Mobile Computing and NetworkingMOBIHOC: ACM International Symposium on Mobile Ad Hoc Networking and Computing ICNP: Intl Conf on Network ProtocolsOPENARCH: IEEE Conf on Open Arch and Network ProgPACT: Intl Conf on Parallel Arch and Compil TechINFOCOM: Annual Joint Conf IEEE Comp & Comm SocUSENIX Symp on Internet Tech and SysRTAS: IEEE Real-Time and Embedded Technology and Applications SymposiumPercom: IEEE International Conference on Pervasive Computing and CommunicationsUbiComp: Uniquitous ComputingCC: International Conference Compiler ConstructionIPDPS: Intl Parallel and Dist Processing SympMOBISYS: International Conference on Mobile Systems, Applications, and ServicesSenSys: ACM Conference on Embedded Networked Sensor SystemsICPP: Intl Conf on Parallel ProcessingICDCS: IEEE Intl Conf on Distributed Comp SystemsSRDS: Symp on Reliable Distributed SystemsMPPOI: Massively Par Proc Using Opt InterconnsASAP: Intl Conf on Apps for Specific Array ProcessorsEuro-Par: European Conf. on Parallel ComputingUsenix Security SymposiumNDSS: ISOC Network and Distributed System Security SymposiumESORICS: European Symposium on Research in Computer SecurityRAID: International Symposium on Recent Advances in Intrusion DetectionDSN: The International Conference on Dependable Systems and NetworksACSAC: Annual Computer Security Applications ConferenceWCW: Web Caching WorkshopLCN: IEEE Annual Conference on Local Computer NetworksIPCCC: IEEE Intl Phoenix Conf on Comp & CommunicationsCCC: Cluster Computing ConferenceICC: Intl Conf on CommWCNC: IEEE Wireless Communications and Networking ConferenceIPSN: International Conference on Information Processing in Sensor NetworksIPTPS: Annual International Workshop on Peer-To-Peer SystemsCSFW: IEEE Computer Security Foundations WorkshopMPCS: Intl. Conf. on Massively Parallel Computing SystemsGLOBECOM: Global CommIMC: Internet Measurement ConferenceIC3N: Intl Conf on Comp Comm and NetworksICCC: Intl Conf on Comp CommunicationNOMS: IEEE Network Operations and Management SympCONPAR: Intl Conf on Vector and Parallel ProcessingVAPP: Vector and Parallel ProcessingICPADS: Intl Conf. on Parallel and Distributed SystemsPublic Key CryptosystemsFast Software EncryptionSecureComm: Int. Conf on Security and Privacy for Emerging Areas in Communication Networks AsiaCCS: ACM Symposium on Information, Computer and Communications SecurityACNS: International Conference on Applied Cryptography and Network SecurityAnnual Workshop on Selected Areas in CryptographyAustralasia Conference on Information Security and PrivacyInt. Conf on Inofrm and Comm. SecurityFinancial CryptographyWorkshop on Information HidingSmart Card Research and Advanced Application ConferenceICON: Intl Conf on NetworksIMSA: Intl Conf on Internet and MMedia SysNCC: Nat Conf CommIN: IEEE Intell Network WorkshopSoftcomm: Conf on Software in Tcomms and Comp NetworksINET: Internet Society ConfWorkshop on Security and Privacy in E-commerceEEE: IEEE Conference on e-Technology, e-Commerce and e-Service Programming Languages and Software EngineeringPOPL: ACM-SIGACT Symp on Principles of Prog LangsPLDI: ACM-SIGPLAN Symp on Prog Lang Design & ImplOOPSLA: OO Prog Systems, Langs and ApplicationsICFP: Intl Conf on Function ProgrammingJICSLP/ICLP/ILPS: (Joint) Intl Conf/Symp on Logic ProgICSE: Intl Conf on Software EngineeringFSE: ACM Conference on the Foundations of Software EngineeringFM/FME: Formal Methods, World Congress/EuropeCAV: Computer Aided VerificationCP: Intl Conf on Principles & Practice of Constraint ProgTACAS: Tools and Algos for the Const and An of SystemsESOP: European Conf on ProgrammingICCL: IEEE Intl Conf on Computer LanguagesPEPM: Symp on Partial Evalutation and Prog ManipulationSAS: Static Analysis SymposiumRTA: Rewriting Techniques and ApplicationsESEC: European Software Engineering ConfIWSSD: Intl Workshop on S/W Spec & DesignCAiSE: Intl Conf on Advanced Info System EngineeringITC: IEEE Intl Test ConfIWCASE: Intl Workshop on Cumpter-Aided Software EngSSR: ACM SIGSOFT Working Conf on Software ReusabilitySEKE: Intl Conf on S/E and Knowledge EngineeringICSR: IEEE Intl Conf on Software ReuseASE: Automated Software Engineering ConferencePADL: Practical Aspects of Declarative LanguagesISRE: Requirements EngineeringICECCS: IEEE Intl Conf on Eng. of Complex Computer SystemsIEEE Intl Conf on Formal Engineering MethodsIntl Conf on Integrated Formal MethodsFOSSACS: Foundations of Software Science and Comp StructAPLAS: Asian Symposium on Programming Languages and SystemsMPC: Mathematics of Program ConstructionECOOP: European Conference on Object-Oriented ProgrammingFASE: Fund Appr to Soft EngAPSEC: Asia-Pacific S/E ConfPAP/PACT: Practical Aspects of PROLOG/Constraint TechALP: Intl Conf on Algebraic and Logic ProgrammingPLILP: Prog, Lang Implentation & Logic ProgrammingLOPSTR: Intl Workshop on Logic Prog Synthesis & TransfICCC: Intl Conf on Compiler ConstructionCOMPSAC: Intl. Computer S/W and Applications ConfICSM: Int. Conf on Software MaintenanceTAPSOFT: Intl Joint Conf on Theory & Pract of S/W DevWCRE: SIGSOFT Working Conf on Reverse EngineeringAQSDT: Symp on Assessment of Quality S/W Dev ToolsIFIP Intl Conf on Open Distributed ProcessingIntl Conf of Z UsersIFIP Joint Int'l Conference on Formal Description Techniques and Protocol Specification, Testing, And VerificatiPSI (Ershov conference)UML: International Conference on the Unified Modeling Language EDOC: IEEE Conference on Enterprise Computing Algorithms and TheorySTOC: ACM Symp on Theory of ComputingFOCS: IEEE Symp on Foundations of Computer ScienceCOLT: Computational Learning TheoryLICS: IEEE Symp on Logic in Computer ScienceSCG: ACM Symp on Computational GeometrySODA: ACM/SIAM Symp on Discrete AlgorithmsSPAA: ACM Symp on Parallel Algorithms and ArchitecturesPODC: ACM Symp on Principles of Distributed ComputingISSAC: Intl. Symp on Symbolic and Algebraic ComputationCRYPTO: Advances in CryptologyEUROCRYPT: European Conf on CryptographyCONCUR: International Conference on Concurrency TheoryICALP: Intl Colloquium on Automata, Languages and ProgSTACS: Symp on Theoretical Aspects of Computer ScienceCC: IEEE Symp on Computational ComplexityWADS: Workshop on Algorithms and Data StructuresMFCS: Mathematical Foundations of Computer ScienceSWAT: Scandinavian Workshop on Algorithm TheoryESA: European Symp on AlgorithmsIPCO: MPS Conf on integer programming & comb optimizationLFCS: Logical Foundations of Computer ScienceALT: Algorithmic Learning TheoryEUROCOLT: European Conf on Learning TheoryDSIC: Int'l Symp om Distributed Computing (old: WDAG)ISTCS: Israel Symp on Theory of Computing and SystemsISAAC: Intl Symp on Algorithms and ComputationFST&TCS: Foundations of S/W Tech & Theoretical CSLATIN: Intl Symp on Latin American Theoretical InformaticsRECOMB: Annual Intl Conf on Comp Molecular BiologyCADE: Conf on Automated DeductionIEEEIT: IEEE Symposium on Information TheoryAsiacryptMEGA: Methods Effectives en Geometrie AlgebriqueASIAN: Asian Computing Science ConfCCCG: Canadian Conf on Computational GeometryFCT: Fundamentals of Computation TheoryWG: Workshop on Graph TheoryCIAC: Italian Conf on Algorithms and ComplexityICCI: Advances in Computing and InformationAWTI: Argentine Workshop on Theoretical InformaticsCATS: The Australian Theory SympCOCOON: Annual Intl Computing and Combinatorics ConfUMC: Unconventional Models of ComputationMCU: Universal Machines and ComputationsGD: Graph DrawingSIROCCO: Structural Info & Communication ComplexityALEX: Algorithms and ExperimentsALG: ENGG Workshop on Algorithm EngineeringLPMA: Intl Workshop on Logic Programming and Multi-AgentsEWLR: European Workshop on Learning RobotsCITB: Complexity & info-theoretic approaches to biologyFTP: Intl Workshop on First-Order Theorem Proving (FTP)CSL: Annual Conf on Computer Science Logic (CSL)AAAAECC: Conf On Applied Algebra, Algebraic Algms & ECCDMTCS: Intl Conf on Disc Math and TCSJCDCG: Japan Conference on Discrete and Computational Geometry Data BasesSIGMOD: ACM SIGMOD Conf on Management of DataPODS: ACM SIGMOD Conf on Principles of DB SystemsVLDB: Very Large Data BasesICDE: Intl Conf on Data EngineeringICDT: Intl Conf on Database TheorySSD: Intl Symp on Large Spatial DatabasesDEXA: Database and Expert System ApplicationsFODO: Intl Conf on Foundation on Data OrganizationEDBT: Extending DB TechnologyDOOD: Deductive and Object-Oriented DatabasesDASFAA: Database Systems for Advanced ApplicationsCIKM: Intl. Conf on Information and Knowledge ManagementSSDBM: Intl Conf on Scientific and Statistical DB MgmtCoopIS - Conference on Cooperative Information SystemsER - Intl Conf on Conceptual Modeling (ER)COMAD: Intl Conf on Management of DataBNCOD: British National Conference on DatabasesADC: Australasian Database ConferenceADBIS: Symposium on Advances in DB and Information SystemsDaWaK - Data Warehousing and Knowledge DiscoveryRIDE WorkshopIFIP-DS: IFIP-DS ConferenceIFIP-DBSEC - IFIP Workshop on Database SecurityNGDB: Intl Symp on Next Generation DB Systems and AppsADTI: Intl Symp on Advanced DB Technologies and IntegrationFEWFDB: Far East Workshop on Future DB SystemsMDM - Int. Conf. on Mobile Data Access/Management (MDA/MDM)ICDM - IEEE International Conference on Data MiningVDB - Visual Database SystemsIDEAS - International Database Engineering and Application Symposium MiscellaneousRECOMB: Annual Intl Conf on Comp Molecular BiologyAMIA: American Medical Informatics Annual Fall SymposiumDNA: Meeting on DNA Based ComputersCSCW: Conference on Computer Supported Cooperative Work MEDINFO: World Congress on Medical InformaticsInternational Conference on Sequences and their ApplicationsECAIM: European Conf on AI in MedicineAPAMI: Asia Pacific Assoc for Medical Informatics ConfINBS: IEEE Intl Symp on Intell. in Neural & Bio SystemsSAC: ACM/SIGAPP Symposium on Applied ComputingICSC: Internal Computer Science ConferenceISCIS: Intl Symp on Computer and Information SciencesICSC2: International Computer Symposium ConferenceICCE: Intl Conf on Comps in EduWCC: World Computing CongressPATAT: Practice and Theory of Automated TimetablingArtificial Intelligence and Related SubjectsAAAI: American Association for AI National ConferenceCVPR: IEEE Conf on Comp Vision and Pattern RecognitionIJCAI: Intl Joint Conf on AIICCV: Intl Conf on Computer VisionICML: Intl Conf on Machine LearningSIGKDD: ACM Knowledge Discovery and Data MiningKR: Intl Conf on Principles of KR & ReasoningNIPS: Neural Information Processing SystemsUAI: Conference on Uncertainty in AIAAMAS: Intl Conf on Autonomous Agents and Multi-Agent Systems (past: ICAA)ACL: Annual Meeting of the ACL (Association of Computational Linguistics)ICDM - IEEE International Conference on Data MiningNAACL: North American Chapter of the ACLAID: Intl Conf on AI in DesignAI-ED: World Conference on AI in EducationCAIP: Inttl Conf on Comp. Analysis of Images and PatternsCSSAC: Cognitive Science Society Annual ConferenceECCV: European Conference on Computer VisionEAI: European Conf on AIEML: European Conf on Machine LearningGECCO: Genetic and Evolutionary Computation Conference (used to be GP)IAAI: Innovative Applications in AIICIP: Intl Conf on Image ProcessingICNN/IJCNN: Intl (Joint) Conference on Neural NetworksICPR: Intl Conf on Pattern RecognitionICDAR: International Conference on Document Analysis and RecognitionICTAI: IEEE conference on Tools with AIAMAI: Artificial Intelligence and MathsDAS: International Workshop on Document Analysis SystemsWACV: IEEE Workshop on Apps of Computer VisionCOLING: International Conference on Computational LiguisticsEMNLP: Empirical Methods in Natural Language ProcessingEACL: Annual Meeting of European Association Computational LingusticsCoNLL: Conference on Natural Language LearningDocEng: ACM Symposium on Document EngineeringIEEE/WIC International Joint Conf on Web Intelligence and Intelligent Agent Technology PRICAI: Pacific Rim Intl Conf on AIAAI: Australian National Conf on AIACCV: Asian Conference on Computer VisionAI*IA: Congress of the Italian Assoc for AIANNIE: Artificial Neural Networks in EngineeringANZIIS: Australian/NZ Conf on Intelligent Inf. SystemsCAIA: Conf on AI for ApplicationsCAAI: Canadian Artificial Intelligence ConferenceASADM: Chicago ASA Data Mining Conf: A Hard Look at DMEPIA: Portuguese Conference on Artificial IntelligenceFCKAML: French Conf on Know. Acquisition & Machine LearningICANN: International Conf on Artificial Neural NetworksICCB: International Conference on Case-Based ReasoningICGA: International Conference on Genetic AlgorithmsICONIP: Intl Conf on Neural Information ProcessingIEA/AIE: Intl Conf on Ind. & Eng. Apps of AI & Expert SysICMS: International Conference on Multiagent SystemsICPS: International conference on Planning SystemsIWANN: Intl Work-Conf on Art & Natural Neural NetworksPACES: Pacific Asian Conference on Expert SystemsSCAI: Scandinavian Conference on Artifical IntelligenceSPICIS: Singapore Intl Conf on Intelligent SystemPAKDD: Pacific-Asia Conf on Know. Discovery & Data MiningSMC: IEEE Intl Conf on Systems, Man and CyberneticsPAKDDM: Practical App of Knowledge Discovery & Data MiningWCNN: The World Congress on Neural NetworksWCES: World Congress on Expert SystemsINBS: IEEE Intl Symp on Intell. in Neural \& Bio SystemsASC: Intl Conf on AI and Soft ComputingPACLIC: Pacific Asia Conference on Language, Information and ComputationICCC: International Conference on Chinese ComputingICADL: International Conference on Asian Digital LibrariesRANLP: Recent Advances in Natural Language ProcessingNLPRS: Natural Language Pacific Rim SymposiumMeta-Heuristics International ConferenceHardware and ArchitectureASPLOS: Architectural Support for Prog Lang and OSISCA: ACM/IEEE Symp on Computer ArchitectureICCAD: Intl Conf on Computer-Aided DesignDAC: Design Automation ConfMICRO: Intl Symp on MicroarchitectureHPCA: IEEE Symp on High-Perf Comp ArchitectureFCCM: IEEE Symposium on Field Programmable Custom Computing MachinesSC(SUPER): ACM/IEEE Supercomputing ConferenceICS: Intl Conf on SupercomputingISSCC: IEEE Intl Solid-State Circuits ConfHCS: Hot Chips SympVLSI: IEEE Symp VLSI CircuitsCODES+ISSS: Intl Conf on Hardware/Software Codesign & System SynthesisDATE: IEEE/ACM Design, Automation & Test in Europe ConferenceFPL: Field-Programmable Logic and ApplicationsCASES: International Conference on Compilers, Architecture, and Synthesis for Embedded System ICA3PP: Algs and Archs for Parall ProcEuroMICRO: New Frontiers of Information TechnologyACS: Australian Supercomputing ConfISC: Information Security ConferenceHiPC:International Conference on High Performance ComputingClass A A A A A A A A B B B B B B B B B B B B B B B B C C C C C C C C C C C C C C C C C Class A A A A A B B B B BB B B B BC C C C C C C C C C C C C C C Class B B B B C C C C C C C C C C C C Class A A A A A A A A A A A A A A AB B A A B B B B B B B B B B B B B B B B B B B B B B B B BC C C C C C C C C C C C C C C C C C C C C C C C CC C Class A A A A A A A A A B B B B B B B B B B B B B B B B B B B B B B B B B C C C C C C C C C C C C C C CC C Class A A A A A A A A A A A B B B B B B B B B B B B B B B B B B B B B C C C C C C C C C C C C C C C C C CC C C C C Class A A A A A B B B B B B B B B B C C C C C C C C C C C C C C C Class B B B B C C C C C C C C C C CClassAAAAAAAAAAABBBBBBBBBBBBBBBBBBBBBBBBBCCCCCCCCCCCCCCCCC C C C C C C C C C C C C C C C C C Class A A A A A A B B B B B B B B B B C C C C C。
计算机学科中的12个核心概念英文版
Below is a list of twel v e core c onc epts that per v ade the discipline and are independent of any particul ar technolog y. Each of them▪Occurs throughout the discipline▪Has a variety of instanti ations▪Has a high degree of tec hnological independenc e In addition to the three characteristics giv en abov e, most c ore c onc epts▪H ave instanti ations at the levels of theor y, abs traction and design▪H ave instanti ations in eac h of the nine s ubj ect areas▪O ccur generall y i n mathematics, scienc e and engineering1. BindingBinding is the process of mak i ng an abstr action more concrete by associ ating additional properties with it.Examples i nclude assigning a proc ess with a process or, ass ociating a ty pe with a variable name,associati ng a librar y object program with a s y mbolic referenc e to a subprogram, instanti ation in logicprogrammi ng, ass ociating a method with a message i n an object-oriented language, cr eating c oncrete instanc es from abstr act descrīptions.2. Complex ity of Large ProblemsThe effec ts of the nonlinear incr ease in c omplex ity as the size of a problem grows. T his is an important factor in distinguis hing and sel ecting methods that sc ale to different data sizes, problem spaces, andprogram sizes. In large programming pr ojects, it is a factor in determining the org anizati on of animplementation team.3. Conceptual and F ormat ModelsVarious way s of for malizing, characterizing, v isualizing and think ing about an idea or problem. Examples include for mal models in logic, switc hing theor y and the theory of c omputation, pr ogramming language paradigms bas ed upon for mal models, c onc eptual models s uch as abstrac t data ty pes and semantic data models, and v isual languages us ed in specify ing and designing s y stems, s uch as data flow andentity-relati ons hip di agrams.4. Consistenc y and C ompletenessConcrete realizations of the concepts of consistenc y and c ompleteness in c omputing, including related concepts s uch as correctness, robus tness, and reliability. Consistenc y i ncludes the consistenc y of a s et of ax i oms that s erve as a formal specification, the consistenc y of theor y to obser v ed fact, and internal consistenc y of a language or interfac e design. Correctness c an be v iewed as the consistenc y of component or s y stem behavīor to stated specificati ons. Completeness includes the adequa c y of a gi v en set of ax ioms to c apture all desired behavīors, functional adequac y of software and hardware s y s tems, and the ability of a s y stem to behave well under error conditi ons and unanticipated situations.5. Efficienc yMeasures of c ost rel ati v e to res ources s uch as s pac e, ti me, money and people. Examples i nclude the theoretical assess ment of the s pac e and time compl ex ity of an algorithm, feasi bility, the efficienc y with which a c ertain desirable res ult (suc h as the completion of a project or the manu facture of a component) can be achieved, and the efficienc y of a given i mplementation relati v e to alternati ve implementati ons.6. EvolutionThe fac t of c hange and its implications. The impact of c hange at all levels and the resilienc y and adequac y of abstracti ons, tec hniques and s y stems in the fac e of change. Ex amples include the ability of formal models to repr esent as pec ts of s y stems that v ar y with time, and the ability of a design to withs tand changing env ironmental demands and changing requirements, tools and facilities for configuration management.7. Lev els of Abstrac tionThe nature and use of abs traction in c omputing; the use of abstrac tion i n managing complex ity, structuring s y stems, hiding details, and c apturing recurring patterns; the ability to r epres ent an entity orsy stem by abstrac tions hav ing different lev els of detail and s pecificity. Ex amples include levels of hardware descrīption, levels of specificity within an obj ect hierarchy, the notion of generics inprogrammi ng languages, and the levels of detail prov ided i n a problem s olution from specificati ons though code.8. Ordering in SpaceThe concepts of loc ality and prox imity in the discipline of computing. In addition to phy sical loc ation, as in networ k s or memor y, this includes organizati onal l ocation (e.g., of pr ocessors, process es, type defi nitions, and associ ated oper ations) and conceptual loc ation (e.g., s oftware scoping, coupling, and c ohesion).9. Ordering in TimeThe concept of ti me i n the ordering of events. This incl udes time as a parameter in formal models (e.g., i n temporal l ogic), time as a means of s y nc hronizing pr ocesses that are spr ead out ov er space, time as an essential element in the ex ec ution of algorithms.10. R euseThe ability of a particul ar tec hnique, conc ept or s y stems to respond appropriatel y to be reused in a new contex t or situation. Ex amples include probability, the reus e of software libr aries and hardware components, technologies that promote reuse of software components, and language abstractions that promote the dev el opment of reus abl e software modul es.11. Sec urityThe ability of software and hardware s y stems to respond appropriatel y to and defend thems el v es against inappropriate and unanticipated requests; the ability of a c omputer installation to withstand catastrophic events (e.g., natural dis asters and attempts at sabotage). Ex amples include ty pe-chec k i ng and other concepts in programming languages that prov i de protection against mis use of data objects and functi ons, data encryption, granti ng and rev ok i ng of priv ileges by a databas e management s y stem, features in user interfac es that mini mize user errors, phy sic al security measur es at computer facilities, and sec uritymec hanis ms at various levels in a s y stem.12. Tradeoff and ConsequencesThe phenomenon of trade-offs in c omputing and the c ons equences of s uch trade-offs. The tec hnical, economic, cultural and other effects of s electi ng one design alternati ve over another. Trade-offs are a fundamental fact of life at all lev els and in all subject areas. Examples incl ude space-time trade-offs in the study of algorithms, trade-offs inherent in c onflicting design objecti v es (e.g., eas e of us e v ersus completeness, flex ibility versus simplicity, low cost versus high reliability and s o forth), design trade-offs i n hardware, and trade-offs i mplied in attempts to opti mize c omputing power in the face of a variety of constraints.。
5ProgrammingandLanguages
4. Program testing
❖ desk-checking 手工检查
❖ debugging
调试
5. Program documentation and ❖musaeinr dteoncuamnecnetation
❖ operation documentation
❖ programmer documentation
code
code
executable file
assemble language
source assembler objective linker
code
code
executable file
5.4 Object-Oriented Programming(OOP)
[7] Object-Oriented programming is a programming method that combines data and instructions for processing that data into a self-sufficient “object” that can be used in other programs.
5.2 Development of Programming Languages
❖ machine language (platform-specific)
❖ assembly language backward compatible
❖ High-level language (platform-independent) procedural
❖ member variable 成员变量
❖ class variable
类变量
程序设计语言概念(ConceptsofProgrammingLanguages)英文第10版第7章P
Copyright © 2012 Addison-Wesley. All rights reserved.
1-12
Functional Side Effects
• Two possible solutions to the problem
1. Write the language definition to disallow functional side effects
• No two-way parameters in functions • No non-local references in functions • Advantage: it works! • Disadvantage: inflexibility of one-way parameters and
else average = sum /count
Copyright © 2012 Addison-Wesley. All rights reserved.
1-10
Arithmetic Expressions: Operand Evaluation Order
• Operand evaluation order
Copyright © 2012 Addison-Wesley. All rights reserved.
1-3
Arithmetic Expressions
• Arithmetic evaluation was one of the motivations for the development of the first programming languages
形式语义学Lambda演算PPT课件
用SUB (E)来表示E的子表达式集;
2020/7/27
13
表达式 (5)—作用域
表达式中变量的作用域:
x. E表达式中的变量x是被绑定的,它的作用域是体 表达式 E 中去掉所有形如x. E’子表达式后的表达 式部分;
x. E表达式中x.部分可以看作是变量x的定义点, 在 E 中x的定义域中出现变量x为其使用点;
= x1. x2. … xn. ( E1 E2 E3 … Em )
2020/7/27
12
表达式 (4)—子表达式
子表达式(针对不同的表达式形式)
设E是一个表达式,则E的子表达式可以定义为: E x ,x就是E的子表达式; E E1 E2 , E1和E2以及它们的子表达式都是E的
子表达式; E x. E’, x. E’以及E’的子表达式都是E的子
2020/7/27
15
表达式 (7)– 自由变量
自由变量:称x为表达式E的自由变量,如果E中至少
包含一个x的自由出现;
需要区分的概念:
变量:<变量名,含义>,定义点确定
变量名:标识符
变量的出现:<变量名,位置>
自由变量集合:用FV(E)表示E的自由变量集合,则其 具体定义为:
E x , FΒιβλιοθήκη (x) = {x} ;2020/7/2因7 此在描述某些算法的时候更精炼和严格;
5
引言
函数式语言不仅可用于程序设计,还可 用于算法、编译器、解释器的抽象描述 ,以及指称语义的定义等方面。
本课程将分两个部分介绍函数式语言
无类型的函数式语言 – Lambda演算( calculus) 有类型的函数式语言 – 类似ML, 通用描述方法
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
AVisualandInteractiveAutomataTheoryCoursewithJFLAP4.0
RyanCavalcante∗DeptofComputerScienceDukeUniversityDurham,NC27708-0129ThomasFinley†DeptofComputerScienceCornellUniversityIthaca,NY14853-7501SusanH.Rodger‡DeptofComputerScienceDukeUniversityDurham,NC27708-0129
rodger@cs.duke.edu
ABSTRACTWedescribetheinstructionalsoftwareJFLAP4.0andhowitcanbeusedtoprovideahands-onformallanguagesandautomatatheorycourse.JFLAP4.0doublesthenumberofchaptersworthofmaterialfromJFLAP3.1,nowcover-ingtopicsfromelevenofthirteenchaptersforasemestercourse.JFLAP4.0haseasierinteractiveapproachestopre-vioustopicsandcoversmanynewtopicsincludingthreeparsingalgorithms,multi-tapeTuringmachines,L-systems,andgrammartransformations.
CategoriesandSubjectDescriptorsF.4.3[TheoryofComputation]:MathematicalLogicandFormalLanguagesFormalLanguages;D.1.7[Software]:Pro-grammingTechniquesVisualProgramming
GeneralTermsTheory
KeywordsJFLAP,automata,pushdownautomata,Turingmachine,grammar,SLRparsing,LLparsing,L-system
1.INTRODUCTIONManycomputersciencestudentsobtainonlyasuperficialunderstandingoftheory,eventhoughtheoreticalconceptsprovidethefundamentalbasisformostareasofcomputerCh.1MathematicalPreliminariesCh.2FiniteAutomataCh.3RegularLanguagesandGrammarsCh.4PropertiesofRegularLanguagesCh.5Context-FreeLanguagesCh.6SimplificationofContext-FreeGrammarsCh.7PushdownAutomataCh.8PropertiesofContext-FreeLanguagesCh.9TuringMachinesCh.10OtherModelsofTuringMachinesCh.11AHierarchyofFormalLanguagesExtra1L-SystemsExtra2LLandSLRParsingThefollowingshowswhatpartofthechapter(where1ismostofthechapter)thatJFLAP4.0andJFLAP3.1canbeusedwith.ChapterJFLAP3.1JFLAP4.0
Figure4:TheequivalentregularexpressionspondingtolowleveloperandsoftheREandthenconnectedthesesubmachinesintolargerandlargersubmachinesuntilthefinalequivalentNFAwasconstructed.Forexample,toconverttheREab+(c+d)∗onefirstconstructedtwoNFAthatrecognizedthelanguagesabandc+d,thenreformedthec+dmachinetorecognize(c+d)∗,andthencombinedthetwomachinestorecognizeab+(c+d)∗.HowdidJFLAPknowtocreatetheabNFA,andthenthec+dNFA,andsoforth?ImplicitlyJFLAPparsedtheREdowntoitslowestleveloperands.JFLAP4.0nowmakesthisparsingmoreexplicitwithoutundulycomplicatingtheconversion.JFLAP4.0takesatop-downapproach.Theuserworksinthesamedirectiontheparserdoes,andobservesandin-teractswiththeparser.Thisservestomakethestepsofthealgorithmless“magical”bydividingthepreviouslywhollyimplicitparsingoftheREintomoreeasilycomprehensi-blesmallchunks.OnestartswithaGTGwithoneinitialstate,onefinalstate,andasingleREtransitionfromtheinitialtothefinalstateontheREtoconvert.Usingamod-ifiedautomatoneditor,theuserrepeatedlyreduceseachREtransitiononanRERintomanyREtransitionsconsistingofR’soperands,andtheuseraddslambdatransitionstoduplicatethefunctionalityofR’slostoperators.AteachstagetheGTGisequivalenttotheinitialRE.AfterenoughtransitionreductionstheGTGbecomesanNFA.
3.3LLandLRParsingInJFLAP4.0onecanstartwithaCFGandbuildanLL(1)parsetableoranSLR(1)parsetablethroughase-riesofsteps,andthensimulatetheparsingofinputstrings.ThesetoolsweremodeledaftertheLLandLRparsinginthetoolJeLLRap[2].WegiveanexampleofbuildingtheSLR(1)parsetableforthegrammarS→aSb,S→b.InJFLAP,theuserfirstenterstheCFGandselectstheoptiontobuildtheSLR(1)parsetable.ThewindowinFigure5appearswiththegram-mar(notshown)andthefieldsinthewindowwouldbeblank.TheuserwouldfirstenterintheFIRSTsetsforthevariables,followedbytheFOLLOWsetsforthevariables.ThentheuserwouldconstructtheDFAthatmodelstheparsingstack.Eachstatehasmarkedrulesoritemsasso-ciatedwithit.Theseitemscanbeeasilyselectedfromamenu;theywouldbetootedioustotypeinasusershadtodoinJeLLRap.JFLAPgiveshintsalongthewayintheconstructionoftheDFAsuchasanerrormessageifyoutrytoaddatransitionthatdoesn’texist,orifyouhavethewrongitemsforastate.OncetheDFAiscomplete,theuserentersintheentriesintheparsetable.Figure5showsthecompletedFirstandFollowsets,DFAandparsetable.Oncetheparsetableiscomplete,theusercanparseaninputstring.Theparsingwindowisdividedintofourviews:thegrammar,theparsetable,theparsetreeandtheinput.Theuserentersaninputstringandstepsthroughthepars-ing.Foreachstep,thestackisadjusted,thecurrentmoveintheparsetableishighlighted,thenewadditionstotheparsetreeareaddedandamessagesuchas“shiftinga”isdisplayed.Theusercanvieweitheraparsetree,aninvertedparsetreeorthederivationtable.IfthegrammarisnotLL(1)orSLR(1),theuserisallowedtocontinue,buildingaparsetablethatwillhaveconflicts.IfthereisaconflictintheSLR(1)parsetable,theusercanchooseoneoftheconflictsasvalidandproceedtoparseinputstrings.
