IBM Tivoli Access Manager and Sun OpenSSO- Combining the best of both worlds -
TIAM简介

概要1.IBM Tivoli安全体系结构2.IBM安全解决方案产品列表1.IBM Directory Server:一个遵循LDAP V3标准的,可以支持上亿用户的目录服务器。
2.IBM Directory Integrator:元目录整合系统,可以支持多达几十种的用户数据源,并且提供了整合的逻辑处理机制。
3.IBM Tivoli Identity Manager:用户身份生命周期管理系统,完善的用户管理流程和对其他系统的支持能力被其被Gartnerranking为第一的产品。
4.IBM Tivoli Access Manager:完整的访问控制家族,支持从B/S结构应用到UNIX/Linux操作系统,到消息中间件,是业界最为流行的访问控制系统,高踞Gartner产品象限的右上角。
5.IBM Tivoli Risk Manager:作为受到大奖的安全事件管理系统现在日益成为企业的安全总控中心,对第三方安全产品的支持和强大的分析引擎成为制胜的两大法宝。
6.IBM Tivoli Security Compliance Manager:在成为Tivoli产品之前,已经在IBM Global Service部门工作超过十年,现在更加入了和Cisco安全系统的集成能力和Tivoli Provision Manager 的协同工作能力,能量日将强大。
7.IBM Tivoli Federated Identity Manager:Tivoli安全家族的新成员,专以解决跨企业的联邦身份管理而著称。
3.IBM的安全解决方案的特点:1.集中管理:IBM认为安全管理必须采用集中的方式,这样才能保证安全策略的一致性。
2.遵循标准:IBM一直是标准的倡导者,在安全领域管理标准还不完善的情况下,IBM一方面积极参与标准的创建工作,另一方面则使自己的产品支持最为广泛标准以满足各种规模企业的需要。
3.灵活可扩展:IBM一直认为安全管理管理在每个企业都有其特定性和特殊性,是随着每个企业的业务系统的需求来确定的。
国内外IT运维平台对比
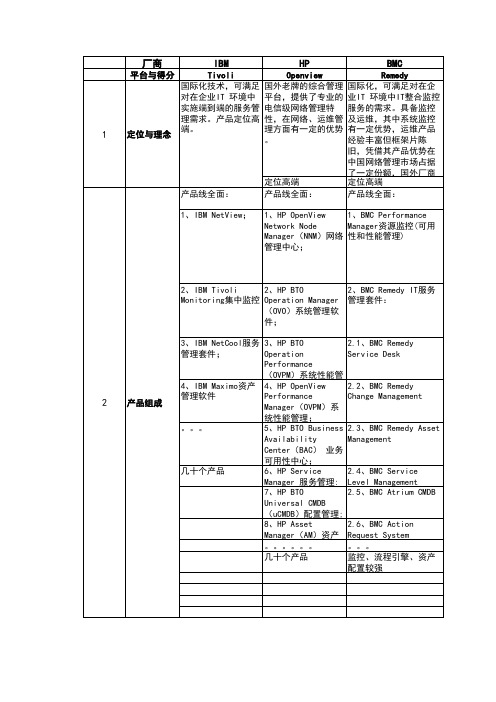
度非常高。
理
ITIL的运维服务流程管理,理念站位较高,流程自定义方面很强,但是其基础流程平台类似念。
通过Netcool提供服务流程,通过Maximo提供资产管理功能,提供了流程的
Ultra-NMS为核心,衍生周边运维产品,
供服务流程与CMDB 。
部分功能齐全
、系统及运维服务管理,较为全面,但是监测深度和广度还相对落后,也没有成型务管理功能。
以网络故障和性能为核心平台,拓展系统、业务、运维管理等几个方
维管理和IT服务管理三位一体的产品体注重实际网络管理系统,在网络管理产品
理功能,只是单纯的ITIL平台。
支持ITIL 标准流程(包括服务支持和服务交付),提供工具进行流程的自定义,支持表单的动态定制(通过独立的工具),但一个流程只能有一个表单。
持,同时提供传统的OA功能,在工作流方面效果不错,但是对底层监控的集成效果Array
中IT资产与综合,上
可实时查询,资源监测信息的历史数据的分析功能比较强,具体动态的调节功能;。
单点登录技术文档

单点登录技术文档张昀* 2006.12说明:本文档在我们最大努力范围之内确保其正确性、实效性和可观性,但并不代表所有的观点都是正确的,而仅代表个人看法。
如发现不当之处,请多指教,谢谢!另外,本文并不是给初学者看的。
虽然我们尽可能把每个概念和操作步骤都说得比较明白,但是如果您对于Linux系统不是很熟的话,很多操作仍然可能存在困难。
这种情况下我们建议您直接下载虚拟机安装试用,边实践边学习。
联系邮件:************************。
1、单点登录概述单点登录的英文名称为Single Sign-On,简写为SSO,它是一个用户认证的过程,允许用户一次性进行认证之后,就访问系统中不同的应用;而不需要访问每个应用时,都重新输入密码。
IBM对SSO有一个形象的解释“单点登录、全网漫游”。
SSO将一个企业内部所有域中的用户登录和用户帐号管理集中到一起,SSO的好处显而易见:1. 减少用户在不同系统中登录耗费的时间,减少用户登录出错的可能性2. 实现安全的同时避免了处理和保存多套系统用户的认证信息3. 减少了系统管理员增加、删除用户和修改用户权限的时间4. 增加了安全性:系统管理员有了更好的方法管理用户,包括可以通过直接禁止和删除用户来取消该用户对所有系统资源的访问权限对于内部有多种应用系统的企业来说,单点登录的效果是十分明显的。
很多国际上的企业已经将单点登录作为系统设计的基本功能之一。
1.1单点登录产品商业SSO软件●专门的SSO商业软件⏹主要有:Netgrity的Siteminder,已经被CA收购。
Novell 公司的iChain。
RSA公司的ClearTrust等。
●门户产品供应商自己的SSO产品,⏹如:BEA的WLES,IBM 的Tivoli Access Manager,Sun 公司的identity Server,Oracle公司的OID等。
上述商业软件一般适用于客户对SSO的需求很高,并且企业内部采用Domino、SAP、Sieble等系统比较多的情况下。
单点登录技术文档

单点登录技术文档何伟民* 2010.61、单点登录概述单点登录的英文名称为Single Sign-On,简写为SSO,它是一个用户认证的过程,允许用户一次性进行认证之后,就访问系统中不同的应用;而不需要访问每个应用时,都重新输入密码。
IBM对SSO有一个形象的解释“单点登录、全网漫游”。
SSO将一个企业内部所有域中的用户登录和用户帐号管理集中到一起,SSO的好处显而易见:1. 减少用户在不同系统中登录耗费的时间,减少用户登录出错的可能性2. 实现安全的同时避免了处理和保存多套系统用户的认证信息3. 减少了系统管理员增加、删除用户和修改用户权限的时间4. 增加了安全性:系统管理员有了更好的方法管理用户,包括可以通过直接禁止和删除用户来取消该用户对所有系统资源的访问权限对于内部有多种应用系统的企业来说,单点登录的效果是十分明显的。
很多国际上的企业已经将单点登录作为系统设计的基本功能之一。
1.1单点登录产品商业SSO软件●专门的SSO商业软件⏹主要有:Netgrity的Siteminder,已经被CA收购。
Novell 公司的iChain。
RSA公司的ClearTrust等。
●门户产品供应商自己的SSO产品,⏹如:BEA的WLES,IBM 的Tivoli Access Manager,Sun 公司的identity Server,Oracle公司的OID等。
上述商业软件一般适用于客户对SSO的需求很高,并且企业内部采用Domino、SAP、Sieble等系统比较多的情况下。
单点登录产品通常需要在应用软件中增加代理模块,而商业SSO产品主要针对大型软件制作了代码模块。
因此,商业SSO软件除了价格问题外,另一个重要问题就是对客户自己的应用系统支持未必十分完善。
开源SSO软件●Opensso⏹https:///⏹OpenSSO基于Sun Java System Access Manager,是Sun公司支持的一个开源的SSO项目。
IBM跨域认证简单解决方案

跨域认证简单解决方案-使用第三方Cookie概述跨域认证,意味着用户在一个入口登录后可以无障碍的漫游到其它信任域。
也就是所谓的单点登录(SSO)。
对于大型的服务提供着,常用的方法有:使用安全断言标记语言(SAML)、基于公开密钥技术(PKI-Pubic Key Infrastructure)的Kerberos网络认证协议或者使用Windows采用的认证方案LanManager认证(称为LM协议-对于NT 安装Service Pack4以后采用NTLM v2版本)。
这些认证方式需要单独的认证服务器,对于普通的使用者来说,既难已实现,也不太可能搭建单独的服务器。
有没有一种简单又安全的认证方式呢?本文的目标使用Cookie和SHA1结合实现简单又安全的认证,如用户在中登录后,无需再次登录就可以直接使用中提供的服务。
Cookie是什么Cookie 是由Web 站点创建的小文本文件,存储在您的计算机上。
这样,当您下一次访问该站点时,它可以自动获取有关您的信息,例如浏览喜好,或您的姓名、地址及电话号码。
关键词SSO(Single Sign-On)-单点登录SAML(Security Assertions Markup Language)-安全断言标记语言Cross-Realm Authentication -跨域认证PKI(Pubic Key Infrastructure)-公开密钥技术SHA1(Secure Hash Algorithm 1)-安全哈希算法1P3P(The Platform for Privacy Preferences)隐私参数选择平台单一认证模型1、用户使用a_logon.aspx登录服务器2、在a_logon.aspx中自动嵌入iframe其src指向的b_auth.php3、认证成功后在客户端写入Cookie,通过iframe调用b_auth.php 传递认证参数(经过SHA1后)4、b_auth.php认证成功后在客户端写入认证Cookie5、完成和的统一认证问题:上面提到的过程如果使用FireFox浏览器b_auth.php能够成功写入Cookie,如果使用IE6.0及以上版本b_auth.php写入Cookie失败。
SSO的简单实现

SSO的简单实现在门户项目中,经常会遇到如何实现单点登录的问题,下面就本人的经验做个总结。
欢迎大家进行补充讨论。
单点登录的具体实现有很多种选择,包括:1.采用专门的SSO商业软件:主要有:Netgrity的Siteminder,已经被CA收购。
Novell公司的iChain。
RSA公司的ClearTrust等。
2.采用门户产品供应商自己的SSO产品,如:BEA的WLES,IBM 的Tivoli AccessManager,Sun 公司的identity Server,Oracle公司的OID等。
3.这些商业软件一般适用于客户对SSO的需求很高,并且企业内部采用COTS软件如:Domino,SAP,Sieble的系统比较多的情况下采用。
并结合身份管理。
统一认证等项目采用。
采用这些软件一般都要对要集成的系统做些改造,如在要集成的系统上安装AGENT。
现在一般只提供常见软件如:Domino,SAP,Sieble,常见应用服务器:weblogic,websphere等的AGENT。
要先统一这些系统的认证。
一般采用LDAP或数据库。
然后才能实现SSO。
比较麻烦。
4.另外,如果不想掏银子,也有OPEN SOURCE的SSO软件可选:主要有:/https:////等。
具体怎么样就不清楚了。
如果项目对SSO的要求比较低,又不想对要被集成的系统做任何改动,可采用下面介绍的方式简单实现:下面我们通过一个例子来说明。
假如一个门户项目要对下面的几个系统做SSO。
用户在这些系统中的用户名,密码各不相同,如:员工号为001的员工在这些系统中的用户名,密码分别如下:用户系统用户名密码001 Portal系统 A 1234001 邮件系统 B 2345001 DOMINO系统 C AAAA001 报销系统 D CCCC001 工资系统 E BBBB首先,建立员工在PORTAL系统中的用户名和其他系统中的用户名之间的对应关系首先,要建立员工在PORTAL系统中的用户名和其他系统中的用户名之间的对应关系并保存。
H3SE存储培训教材-第四部分 1 数据保护技术2.0

数据保护实现方法对比
适用场合 家庭用户,无BC要求 RTO、RPO 长 备份 介质 磁盘 增量机制 不能做增量拷贝,每 次都要拷贝所有文件 有归档需求的用户, 备份 BC要求较低。 长 磁带机、 支持增量,文件级增 磁带库、 量或数据库表级增量 磁盘 为主,支持裸设备增 量备份的软件较少且 价格昂贵, 企业重要应用,BC要 求高,距离远。 复制技术 短 磁盘 支持增量,可精确到 物理块级 远近皆可 复制过程在磁盘阵列或 者存储网络层进行,不 会占用应用服务器资源 和应用网络带宽 近,以本地 备份为主 备份距离 近 对业务系统的影响 拷贝过程占用大量服务 器资源 需要配置备份服务器、 客户端软件及大量的 License,占用服务器资 源和网络带宽 管理 手工执行占用人 力资源。 备份软件对使用 者要求较高,需要 掌握裸设备、文件 系统、数据库等综 合知识。 设定策略后无需人 工干预,复制与恢 复的过程都很简单。
BUSY!!!!! 应用服务器 应用服务器
备份服务器
磁带库
存储系统
备份模式-LAN Free备份
LAN
应用服务器 介质服务器
应用服务器 备份服务器
Storage network
生产卷
指令流 数据流
备份模式-Server Free备份
LAN
应用服务器 应用服务器 备份服务器 介质服务器
效果评估
RTO/RPO
总体成本
1. 软硬件投入成本较低;
2. 人力和维护成本较高;
适用业务
1.无连续性要求; 2.简单小数据量备份,个人不定期的文件保护;
数据保护技术-备份
LAN 传统的备份是指利用备份软件把数据 从磁盘备份到磁带进行离线保存; 1.与拷贝相比,备份方式支持每次针对 增量数据进行保护、可以制定策略自动 完成,并且可以对正在使用的数据(如 注册表)进行保护; 2.备份数据是磁带格式,不能被应用系 统直接访问;在源数据被破坏或丢失时 ,备份数据必须由备份软件恢复成可用 数据,才可让数据处理系统访问; 3.备份过程中,应用系统的性能、带宽 等都会受影响,有可能需要应用停机或 者在业务量较小的时候进行。与业务连 续性矛盾突出!
IBM Tivoli Storage Manager 数据保护方案说明书

Keeping Your Options Open:The Smart Strategy for Data ProtectionData protection shouldn’t lock you in. Get data protection for today that scales for tomorrow. Take a look at three options you need to consider:1. On-premise appliances2. Cloud services3. Hybrid on-premise appliances with cloud services1. How can a PBBA help me simplify backup and recovery?An enterprise-class PBBA can help automate backups with a simple, self-service solution soyou don’t have to worry about integrating and managing different devices or deal with the frustrations of tape backup.2. Why is a PBBA better than tape backup?If you have tape backup, you know its shortcomings: mechanical failures, incomplete restores,lots of manual work and long backup times. Your staff has to physically mount and unmount tapesand transport them offsite for storage. Then, when you need to restore data fast, your staff has to retrieve the tapes from storage.3. How fast can I restore in the event of a data failure?With an on-prem backup appliance, there’s no need to retrieve tapes from storage to get yourdata back. Plus, you don’t need to waste time physically mounting tapes. You can usually restore from your appliance in minutes—rather than hours or even days!4. What features should I look for in an enterprise-class PBBA?The first thing to consider is security. An enterprise-class appliance needs to provide dataencryption. You’ll also want a PBBA that minimizes power consumption, floor space and coolingrequirements to save energy, space and money. If you want to add cloud backup in the future,choose a PBBA that offers deduplication so only changed data is sent to the cloud—decreasingbackup time, freeing up bandwidth during replication, and reducing the cloud storage capacity needed and its associated costs.Seagate Technology | 1-800-SEAGATE | To simplify backups and restore data fast, consider on-prem appliances.On-prem enterprise-class purpose-built backup appliances (PBBAs) PBBAs can automate backups and speed restores. What features should you look for?Seagate Technology | 1-800-SEAGATE | | Seagate Technology LLC, 10200 South De Anza Boulevard, Cupertino CA 95014 U.S.A 5. Why do I need cloud backup?The cloud provides cost-effective backup and DR, archive, query and other less critical dataoperations. You pay only for the capacity you need, adding more capacity as your data volume grows.6. Is my data really safe and secure in the cloud?Your data is safe. Data can be encrypted onsite, in transit and at rest in the cloud—while youcontrol the encryption keys. Next, insist on an SSAE 16-certified data center, the gold standardfor security. Finally, if your organization requires dedicated space, you can get it. If you don’t need that level of security, consider lower-cost colocation.7. Can I simplify upgrades as the data volumes grow?Make sure your solution scales painlessly as data expands. Look for a cloud provider thatprovides scale-up architecture to add capacity to the same unit or scale-out architecturedesigned to add devices without disruption. “Clustering” allows you to add an appliance to a cluster and manage the entire cluster as a single vault via one management console.8. What happens if a disaster takes out my onsite systems?If a major disaster takes out your local data center, your organization can operate from thecloud without significant downtime (less than an hour with a 1-hour SLA) until you get your local systems up again.For low-cost backup and fast reliable DR, choose the cloud.Cloud backup and disaster recovery (DR)When disaster strikes, your data is safe in the cloud. Keep your business running when everything around you crashes.Choose the best solution for your environment today, keeping an eye on the future. As your needs change and expand, make sure you have a vendor like Seagate EVault that can grow with you every step of the way.Seagate Technology | 1-800-SEAGATE | | Seagate Technology LLC, 10200 South De Anza Boulevard, Cupertino CA 95014 U.S.A © 2015 Seagate Technology LLC. Seagate, Seagate Technology, and the Wave logo are trademarks or registered trademarks of Seagate Technology LLC or one of its affiliated companies in the United States and/or other countries. All other trademarks or registered trademarks are the property of their respective owners. Complying with all applicable copyright laws is the responsibility of the user. Seagate may change, without notice, product offerings or specifications.1 Hybrid Cloud PBBAs Help to Manage and Secure Data Cost-Effectively. Phil Goodwin, IDC Research Director, Storage Systems and Software. August 2015.9. What exactly is hybrid cloud data protection?Hybrid cloud data protection means you get easy-to-manage, reliable local backup and fast restores combined with a cost-effective extra layer of protection in the cloud.10. What are some advantages of a hybrid cloud solution?With on-prem appliance and cloud backup integration, the cloud provides secondary backupfor your data should your local systems go down. The cloud can also provide you with “burstoperations,” giving you additional capacity for a brief period without having to add permanent extra capacity on-prem.11. Is it possible to offload all our backup and DR to a managed service provider?A managed service provider (MSP) can take care of all your data backup and DR needs todayand eliminate complex and disruptive upgrades as you grow. Here are some things to look for:• Option to keep data in your own data center or in your service provider’s private cloud• Self-healing automated data dispersal technology that guarantees data is optimallydistributed within one or more geographically dispersed data centers with failover enablement • Separate data and metadata distribution and storage12. Is there an advantage to working with a single vendor for our hybrid cloud solution?A single vendor ensures that your on-prem and cloud solution is optimally integrated andmanagement is centralized through one console. In terms of security, when working with morethan one vendor “you get the least common denominator between them to provideinteroperability.”1 Even if both have good security, you may not be able to take advantage of it if the systems are incompatible.If you choose a hybrid cloud solution, choose one that gives you simple, centralized control andmanagement—no matter what kind of environment you have (physical-to-virtual, virtual-to-virtual,etc.). Insist on end-to-end encryption and physical data center security. Optimize your systems withdeduplication, compression and full support.Do you want more information? Visit our website or call us at 866-766-2186.PBBAs and cloud team up to give you the best of both worlds.Hybrid cloud data protectionAs businesses grow, they often find that fast local restores and low-cost secure cloud backup offer the perfect blend that grows with them.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Figure 1: CDAS
Using EAI, the authentication process can be made much more flexible. Another significant advantage is that development of the authentication procedure is not longer bound to the C-language. Figure 2 shows how EAI is implemented: 1. 2. 3. 4. 5. 6. A user tries to access a protected resource and is redirected to the EAI-application, the EAI-application gathers the necessary authentication data over HTTP, after verifying the users authentication data, the EAI-application returns a user identity, WebSEAL builds an internal credential for that user, the user is granted or denied access based on the security policy.
IBM has introduced a new feature with the release 4 of TAMeb 6.0 , called External Authentication Interface (EAI).
Client certificate authentication cannot be done via EAI, IBM provides the “User Mapping Client Certificate CDAS” that allows to map a certificate to any TAM-user by using XSL mapping rules. The CDAS is included in the TAMlicense.
IBM Tivoli Access Manager and Sun OpenSSO
- Combining the best of both worlds -
In this fast evolving world where businesses need to make applications available online, business leaders ask themselves questions about how to secure both the applications and the transactions. That is where the demand for Web Application Management (WAM)-platforms is raised from. While multiple WAM-players are competing each other on the today’s market another competition is raging in all its dimensions, those of the strong security authentication solutions (token, biometric, certificate …). Authentication is the process of mapping a physical user to an electronic identity. Besides the authentication process is used to verify if one is really the user (s)he is claiming to be. Up until recently, this was done by using username and password. Because of the increasing CPU-power in modern machines, breaking today’s well-considered passwords becomes easier each day. Strong authentication, introduced to increase protection of sensitive information, is based on three pillars: Something you “know”: A passphrase or code that only the user knows. Something you “have”: A physical device you own (token). Something you “are”: A biometric property uniquely identifying the authenticating person (fingerprint, iris, finger vein pattern,…)
To put the above in practice, a wide range of proven technology can be used. Once a business has chosen the security solution that is compliant with the business needs, a final obstacle must be bypassed: “Is the selected strong authentication solution supported by the WAMplatform in place?”. This whitepaper explains how to extend the few outof-the-box authentication mechanisms provided by 1 IBM Tivoli Access Manager for e-business with the numerous ones that are available by default when 2 using SUN’s free OpenSSO -solution.
IBM Tivoli Access a leading authentication and authorization platform TAMeb provides a platform to centrally manage authentication and authorization to webenabled applications. Next to providing security at user level, TAMeb also works closely with IBM
4
3
also TAMeb 5.1 FP9
P age |2
Figure 2: EAI returning user identity
Figure 3: EAI returning PAC
WebSEAL is not longer responsible for gathering the logon information from the user. This directly indicates that the authentication process becomes more flexible than the CDAS because: EAI has complete access to the HTTPrequest (POST-data or additional HTTPheaders), EAI has the possibility to interact with the user during the authentication phase, which makes it possible to implement whatever authentication strategy, development of the EAI-solution is no longer limited to the C-language.
1 2
/software/tivoli/products/access-mgr-e-bus/ https:///
P age |1
Rational Appscan to address issues which may expose application vulnerabilities. TAMeb supports a number of authentication mechanisms out-of-the-box: 1. 2. 3. 4. Username/password RSA SecurID 3 Client Side X509-certificate HTTP-header based authentication
For other authentication mechanisms, IBM has created the Cross-Domain Authentication Service (CDAS) which allows replacing the default authentication mechanism with a custom one. CDAS is pretty powerful but needs a considerable amount of development. No additional information can be requested from the user during authentication. Even more important: because the TAMeb-reverse proxy (WebSEAL) does not pass all the data contained in a HTTP-request to the CDAS (such as POST-data or additional HTTP-headers), some useful information can be missing to perform the authentication. Figure 1 shows the working principle of the CDAS: 1. 2. 3. 4. 5. 6. 7. A user tries to access a protected resource, WebSEAL gathers the authentication data from the user, WebSEAL passes the gathered data to the custom CDAS-library via an API-call, the CDAS verifies the incoming data against an external resource, the CDAS returns a user identity, WebSEAL builds an internal credential for that user, the user is granted or denied access based on the security policy.
