密码学第五版部分课后答案
密码编码学和网络安全(第五版)答案解析

Access control: The prevention of unauthorized use of a resource (i.e., this service controls who can have access to a resource, under what conditions access can occur, and what those accessing the resource are allowed to do).Data confidentiality: The protection of data from unauthorized disclosure.Data integrity: The assurance that data received are exactly as sent by an authorized entity (i.e., contain no modification, insertion, deletion, or replay).Nonrepudiation: Provides protection against denial by one of the entities involved in a communication of having participated in all or part of the communication.Availability service: The property of a system or a system resource being accessible and usable upon demand by an authorized system entity, according to performance specifications for the system (i.e., a system is available if it provides services according to the system design whenever users request them).1.5 See Table 1.3.2.1 Plaintext, encryption algorithm, secret key, ciphertext, decryptionalgorithm.2.2 Permutation and substitution.2.3 One key for symmetric ciphers, two keys for asymmetric ciphers.2.4 A stream cipher is one that encrypts a digital data stream one bit or one byteat a time. A block cipher is one in which a block of plaintext is treated as a whole and used to produce a ciphertext block of equal length.2.5 Cryptanalysis and brute force.2.6 Ciphertext only . One possible attack under these circumstances is thebrute-force approach of trying all possible keys. If the key space is very large, this becomes impractical. Thus, the opponent must rely on an analysis of the ciphertext itself, generally applying various statistical tests to it. Known plaintext. The analyst may be able to capture one or more plaintext messages as well as their encryptions. With this knowledge, the analyst may be able to deduce the key on the basis of the way in which the known plaintext is transformed. Chosen plaintext. If the analyst is able to choose the messages to encrypt, the analyst may deliberately pick patterns that can be expected to reveal the structure of the key.2.7 An encryption scheme is unconditionally secure if the ciphertext generatedby the scheme does not contain enough information to determine uniquely the corresponding plaintext, no matter how much ciphertext is available. An encryption scheme is said to be computationally secure if: (1) the cost of breaking the cipher exceeds the value of the encrypted information, and (2) the time required to break the cipher exceeds the useful lifetime of the information.C HAPTER 2C LASSICAL E NCRYPTION T ECHNIQUESR2.8 The Caesar cipher involves replacing each letter of the alphabet with theletter standing k places further down the alphabet, for k in the range 1 through25.2.9 A monoalphabetic substitution cipher maps a plaintext alphabet to a ciphertextalphabet, so that each letter of the plaintext alphabet maps to a single unique letter of the ciphertext alphabet.2.10 The Playfair algorithm is based on the use of a 5 5 matrix of lettersconstructed using a keyword. Plaintext is encrypted two letters at a time using this matrix.2.11 A polyalphabetic substitution cipher uses a separate monoalphabeticsubstitution cipher for each successive letter of plaintext, depending on a key.2.12 1. There is the practical problem of making large quantities of random keys.Any heavily used system might require millions of random characters on a regular basis. Supplying truly random characters in this volume is asignificant task.2. Even more daunting is the problem of key distribution and protection. Forevery message to be sent, a key of equal length is needed by both sender and receiver. Thus, a mammoth key distribution problem exists.2.13 A transposition cipher involves a permutation of the plaintext letters.2.14 Steganography involves concealing the existence of a message.A NSWERS TO P ROBLEMS2.1 a. No. A change in the value of b shifts the relationship between plaintextletters and ciphertext letters to the left or right uniformly, so that if the mapping is one-to-one it remains one-to-one.b. 2, 4, 6, 8, 10, 12, 13, 14, 16, 18, 20, 22, 24. Any value of a larger than25 is equivalent to a mod 26.c. The values of a and 26 must have no common positive integer factor otherthan 1. This is equivalent to saying that a and 26 are relatively prime, or that the greatest common divisor of a and 26 is 1. To see this, first note that E(a, p) = E(a, q) (0 ≤ p≤ q< 26) if and only if a(p–q) is divisible by 26. 1. Suppose that a and 26 are relatively prime. Then, a(p–q) is not divisible by 26, because there is no way to reduce the fractiona/26 and (p–q) is less than 26. 2. Suppose that a and 26 have a common factor k> 1. Then E(a, p) = E(a, q), if q = p + m/k≠ p.2.2 There are 12 allowable values of a (1, 3, 5, 7, 9, 11, 15, 17, 19, 21, 23,25). There are 26 allowable values of b, from 0 through 25). Thus the totalnumber of distinct affine Caesar ciphers is 12 26 = 312.2.3 Assume that the most frequent plaintext letter is e and the second most frequentletter is t. Note that the numerical values are e = 4; B = 1; t = 19; U = 20.Then we have the following equations:1 = (4a + b) mod 2620 = (19a + b) mod 26Thus, 19 = 15a mod 26. By trial and error, we solve: a = 3.Then 1 = (12 + b) mod 26. By observation, b = 15.2.4 A good glass in the Bishop's hostel in the Devil's seat—twenty-one degreesand thirteen minutes—northeast and by north—main branch seventh limb east side—shoot from the left eye of the death's head— a bee line from the tree through the shot fifty feet out. (from The Gold Bug, by Edgar Allan Poe)2.5 a. The first letter t corresponds to A, the second letter h corresponds toB, e is C, s is D, and so on. Second and subsequent occurrences of a letter in the key sentence are ignored. The resultciphertext: SIDKHKDM AF HCRKIABIE SHIMC KD LFEAILAplaintext: basilisk to leviathan blake is contactb. It is a monalphabetic cipher and so easily breakable.c. The last sentence may not contain all the letters of the alphabet. If thefirst sentence is used, the second and subsequent sentences may also be used until all 26 letters are encountered.2.6The cipher refers to the words in the page of a book. The first entry, 534,refers to page 534. The second entry, C2, refers to column two. The remaining numbers are words in that column. The names DOUGLAS and BIRLSTONE are simply words that do not appear on that page. Elementary! (from The Valley of Fear, by Sir Arthur Conan Doyle)2.7 a.2 8 10 7 9 63 14 5C R Y P T O G A H I4 2 8 1056 37 1 9ISRNG BUTLF RRAFR LIDLP FTIYO NVSEE TBEHI HTETAEYHAT TUCME HRGTA IOENT TUSRU IEADR FOETO LHMETNTEDS IFWRO HUTEL EITDSb. The two matrices are used in reverse order. First, the ciphertext is laidout in columns in the second matrix, taking into account the order dictated by the second memory word. Then, the contents of the second matrix are read left to right, top to bottom and laid out in columns in the first matrix, taking into account the order dictated by the first memory word. Theplaintext is then read left to right, top to bottom.c. Although this is a weak method, it may have use with time-sensitiveinformation and an adversary without immediate access to good cryptanalysis(e.g., tactical use). Plus it doesn't require anything more than paper andpencil, and can be easily remembered.2.8 SPUTNIK2.9 PT BOAT ONE OWE NINE LOST IN ACTION IN BLACKETT STRAIT TWO MILES SW MERESU COVEX CREW OF TWELVE X REQUEST ANY INFORMATION。
密码学-课后习题
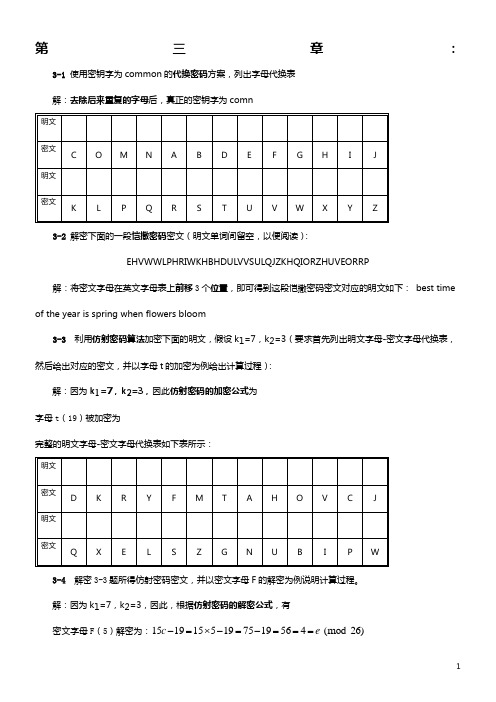
解:置乱密码的格纸表如下表所示:
列
行
0
1
2
3
4
0
c
r
y
p
t
1
o
g
r
a
p
2
h
y
i
s
t
3
h
e
s
c
i
4
e
n
c
e
a
5
n
d
s
t
u
6
d
y
o
f
s
7
e
c
r
e
t
8
w
r
i
t
i
9
n
g
a
b
c
根据密钥字money,得到读出列的顺序为1、3、2、0、4。按照此顺序读出各列,得到置乱密文如下:RGYENDYCRG PASCETFETB YRISCSORIA COHHENDEWN TPTIAUSTIC
4-7分别用多项式乘法、移位相加法和表操作法计算下列字节乘法运算:
(1) (2)
解(1) , 。
①多项式乘法计算字节乘法运算
②移位相加法计算字节乘法运算
由于 ,且
因此,有
③表操作法计算字节乘法运算
查表4-2的对数表,有: , 。因此,
查表4-3的反对数表,有: 。因此, 。
4-9利用 的已知结果,证明 域上的元素 。
解:该4级序列产生器的全状态图如题4-20图2所示。由图可见,从最小的非0状态开始,一个周期的输出序列为100011110101100,其周期为15,因此它是m序列产生器。
密码学第五版部分课后答案

2.4 已知下面的密文由单表代换算法产生:请将它破译。
提示:1、正如你所知,英文中最常见的字母是e。
因此,密文第一个或第二个(或许第三个)出现频率最高的字符应该代表e。
此外,e经常成对出现(如meet,fleet,speed,seen,been,agree,等等)。
找出代表e的字符,并首先将它译出来。
2、英文中最常见的单词是“the”。
利用这个事实猜出什么字母t和h。
3、根据已经得到的结果破译其他部分。
解:由题意分析:“8”出现次数最多,对应明文为“e”,“;48”代表的明文为“the”,“)”、“*”、“5”出现频率都比较高,分别对应“s”、“n”、“a”,由此破译出密文对应的明文为: A good glass in the Bishop’s hostel in the Devil’s seat-twenty-one degrees and thirteen minutes-northeast and by north-main branch seventh limb east side-shoot from the left eye of the death’s head-a bee line from the tree through the shot fifty feet out.2.20 在多罗的怪诞小说中,有一个故事是这样的:地主彼得遇到了下图所示的消息,他找到了密钥,是一段整数:7876565434321123434565678788787656543432112343456567878878765654343211234a.破译这段消息。
提示:最大的整数是什么?b.如果只知道算法而不知道密钥,这种加密方案的安全性怎么样?c.如果只知道密钥而不知道算法,这种加密方案的安全性又怎么样?解:A.根据提示,将密文排成每行8字母的矩阵,密钥代表矩阵中每行应取的字母,依次取相应字母即可得明文。
密码学作业解答

下面的密文是用模26下的仿射密码加密的:CRWWZ 明文以ha 开头,试解密消息。
解一: h -> 7 , a ->0 , C -> 2 ,R -> 17设解密函数为 βα+≡x y (mod 26)则有 ⎩⎨⎧+≡+≡βαβα17027 (mod 26) => ⎩⎨⎧==13βα=> 13+≡x y (mod 26)W -> 22 ,有151223≡+⨯≡y (mod 26) ,对应字母为pZ -> 25 ,有241253≡+⨯≡y (mod 26) ,对应字母为y所以该信息解密为happy解二: h -> 7 , a ->0 , C -> 2 ,R -> 17设加密函数为 βα+≡x y (mod 26)则有 ⎩⎨⎧+≡+≡βαβα01772 (mod 26)=> ⎩⎨⎧==179βα => 179+≡x y (mod 26)所以解密函数为 )17(91-≡-y x (mod 26)∵ 326mod 91≡-∴ 13)17(3+≡-≡y y x (mod 26)W -> 22 ,有151223≡+⨯≡x (mod 26) ,对应字母为pZ -> 25 ,有241253≡+⨯≡x (mod 26) ,对应字母为y所以该信息解密为happy以appletalk 为密钥,加密明文bookstore解:密钥方阵为明文bookstore预处理为:bo ok st or ex密文为:KQ VG UE QS LY作业三:密文IOTWSH 是通过矩阵 的希尔密码加密得到的,求明文。
解:I:8, O:14, T:19, W:22, S:18, H:7∵ 52139=9*5-2*13=19, gcd(19,26)=1 ∴26mod 2141339213511921351919213526451521391⎪⎪⎭⎫ ⎝⎛≡⎪⎪⎭⎫ ⎝⎛--≡⎪⎪⎭⎫⎝⎛--≡⎪⎪⎭⎫⎝⎛---≡⎪⎪⎭⎫ ⎝⎛-由解密公式得明文为26mod 1747158226mod 2141337182219148⎪⎪⎪⎭⎫⎝⎛≡⎪⎪⎭⎫ ⎝⎛⎪⎪⎪⎭⎫⎝⎛故明文为cipher⎪⎪⎭⎫⎝⎛52139作业四:选择p=7,q=17,e=5,试用RSA 算法对明文m=19进行加密,再对密文解密。
外文版第五版作业_zhang

所以有 :(A B)' = A' B 同时有:A B = A' B' 考虑在图 3.5 中的两个 XOR 运算。一次在 f 函数中 S 盒之前;一次在 f 函数输出之后。 在第一个 XOR 运算的两个输入都是原来的逆,根据 A B = A' B' 所以输出和不取逆的情况相同。 在第二个 XOR 运算的输入中一个是原来的逆,一个是本身,根据(A B)' = A' B 所以输出结果是原来的逆。这样 Ri 是原来的逆,同时 Li = Ri-1 也是原来的逆 所以结论成立。即如果 Y = E[K, X] 则 Y' = E[K', X']。 b.密钥搜索空间为 255 分析:选择明文攻击,给定一个 X,得到:Y = E[K, X] and Y = E[K, X'] 1 2 现在进行穷举攻击,给定一个密钥 T,计算 E[T, X],如果结果是 Y1 ,T 就是密钥。 否则计算 E[K, X'],如果结果是(Y2)',则 这样搜索空间减少了一倍。 第四章 有限域 习题: 1–1 = 1, 2–1 = 3, 3–1 = 2, 4–1 = 4 a. gcd(24140, 16762) = gcd(16762, 7378) = gcd(7378, 2006) = gcd(2006, 1360) = gcd(1360, 646) = gcd (646, 68) = gcd(68, 34) = gcd(34, 0) = 34 b. 35 4.19 a. 3239 b. gcd(40902, 24240) = 34 ≠ 1, 因而没有乘法逆元 c. 550 4.13 4.15 第五章 高级加密标准
桂林电子科技大学计算机科学与工程学院――张瑞霞
密码习题及部分参考答案

密码习题及部分参考答案第一篇:密码习题及部分参考答案一、密码学概述部分:1、什么是密码体制的五元组。
五元组(M,C,K,E,D)构成密码体制模型,M代表明文空间;C代表密文空间;K代表密钥空间;E代表加密算法;D 代表解密算法2、简述口令和密码的区别。
密码:按特定法则编成,用以对通信双方的信息进行明、密变换的符号。
换而言之,密码是隐蔽了真实内容的符号序列。
就是把用公开的、标准的信息编码表示的信息通过一种变换手段,将其变为除通信双方以外其他人所不能读懂的信息编码,这种独特的信息编码就是密码。
口令:是与用户名对应的,用来验证是否拥有该用户名对应的权限。
密码是指为了保护某种文本或口令,采用特定的加密算法,产生新的文本或字符串。
区别:从它们的定义上容易看出;当前,无论是计算机用户,还是一个银行的户头,都是用口令保护的,通过口令来验证用户的身份。
在网络上,使用户口令来验证用户的身份成了一种基本的手段。
3、密码学的分类标准:ν按操作方式可分为:替代、置换、复合操作ν按使用密钥的数量可分为:对称密钥(单密钥)、公开密钥(双秘钥)ν按对明文的处理方法可分为:流密码、分组密码4、简述柯克霍夫斯原则(及其特点和意义。
?)即使密码系统中的算法为密码分析者所知,也难以从截获的密文推导出明文或密钥。
也就是说,密码体制的安全性仅应依赖于对密钥的保密,而不应依赖于对算法的保密。
只有在假设攻击者对密码算法有充分的研究,并且拥有足够的计算资源的情况下仍然安全的密码才是安全的密码系统。
一句话:“一切秘密寓于密钥之中” Kerckhoffs原则的意义:ν知道算法的人可能不再可靠ν设计者有个人爱好ν频繁更换密钥是可能的,但无法频繁更换密码算法(设计安全的密码算法困难)5、密码攻击者攻击密码体制的方法有三种分别是:ν穷举:尝试所有密钥进行破译。
(增大密钥的数量)ν统计分析:分析密文和明文的统计规律进行破译。
(使明文和密文的统计规律不一样)ν解密变换:针对加密变换的数学基础,通过数学求解找到解密变换。
密码学参考答案(精品)

三、名词解释18. 答:被动攻击即窃听,是对系统的保密性进行攻击,通过截获密文,进行业务流分析,如搭线窃听、对文件或程序的非法拷贝等,以获取他人的信息。
18.答:主动攻击是对数据流的篡改或产生假的数据流,包括中断可用性、篡改完整性、伪造真实性。
18. 答:研究如何从密文推演出明文、密钥或解密算法的学问称为密码分析学。
18.答:自同步流密码是密钥流的产生与明文有关的流密码。
18.答:杂凑函数H是一公开函数,用于将任意长的消息M映射为较短的、固定长度的一个杂凑值H(M),作为认证符或消息摘要。
18.答:若n次不可约多项式p(x)的阶为2n-1,则称p(x)是n次本原多项式。
18. 答:称c是两个整数a、b的最大公因子,如果①c是a的因子也是b的因子,即c是a、b的公因子。
②a和b的任一公因子,也是c的因子。
表示为c=gcd(a, b)。
18.答:对x,若有y,使得x×y≡1 mod n,则称y为x的倒数,也称为模乘逆元。
19.答:从一个文本中随机选择两个字符,两个字符相同的概率称为重合指数。
20.答:序列密码算法或称流密码算法,通过将明(密)文同密码流逐位相异或进行加(解)密。
19. 答:汉明距离w(x)表示x中所有非0元素的个数。
20. 答:将明文加密成密文时所采用的一组规则称为加密算法。
19.答:设p是素数,a<p,如果方程x2≡a (mod p)无解,称a是p的非平方剩余。
20.答:消息认证码是指消息被一密钥控制的公开函数作用后产生的、用作认证符的、固定长度的数值,也称为密码校验和。
19.答:(Fermat)若p是素数,a是正整数且gcd(a, p)=1,则a p - 1≡1 mod p。
20.答:设p是素数,a<p,如果方程x2≡a (mod p)有解,称a是p的平方剩余。
19.答:如果移位寄存器的反馈函数f(a1,a2,…,a n)是a1,a2,…,a n的线性函数,则称之为线性反馈移位寄存器(LFSR)。
密码学第五版部分课后答案 (1)

2.4 已知下面的密文由单表代换算法产生:请将它破译。
提示:1、正如你所知,英文中最常见的字母是e。
因此,密文第一个或第二个(或许第三个)出现频率最高的字符应该代表e。
此外,e经常成对出现(如meet,fleet,speed,seen,been,agree,等等)。
找出代表e的字符,并首先将它译出来。
2、英文中最常见的单词是“the”。
利用这个事实猜出什么字母t和h。
3、根据已经得到的结果破译其他部分。
解:由题意分析:“8”出现次数最多,对应明文为“e”,“;48”代表的明文为“the”,“)”、“*”、“5”出现频率都比较高,分别对应“s”、“n”、“a”,由此破译出密文对应的明文为: A good glass in the Bishop’s hostel in the Devil’s seat-twenty-one degrees and thirteen minutes-northeast and by north-main branch seventh limb east side-shoot from the left eye of the death’s head-a bee line from the tree through the shot fifty feet out.2.20 在多罗的怪诞小说中,有一个故事是这样的:地主彼得遇到了下图所示的消息,他找到了密钥,是一段整数:11234a.破译这段消息。
提示:最大的整数是什么?b.如果只知道算法而不知道密钥,这种加密方案的安全性怎么样?c.如果只知道密钥而不知道算法,这种加密方案的安全性又怎么样?解:A.根据提示,将密文排成每行8字母的矩阵,密钥代表矩阵中每行应取的字母,依次取相应字母即可得明文。
明文为:He sitteth between the cherubims.The isles may be glad thereof.As the rivers in the South.B.安全性很好。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
2.4 已知下面的密文由单表代换算法产生:请将它破译。
提示:1、正如你所知,英文中最常见的字母是e。
因此,密文第一个或第二个(或许第三个)出现频率最高的字符应该代表e。
此外,e经常成对出现(如meet,fleet,speed,seen,been,agree,等等)。
找出代表e的字符,并首先将它译出来。
2、英文中最常见的单词是“the”。
利用这个事实猜出什么字母t和h。
3、根据已经得到的结果破译其他部分。
解:由题意分析:“8”出现次数最多,对应明文为“e”,“;48”代表的明文为“the”,“)”、“*”、“5”出现频率都比较高,分别对应“s”、“n”、“a”,由此破译出密文对应的明文为: A good glass in the Bishop’s hostel in the Devil’s seat-twenty-one degrees and thirteen minutes-northeast and by north-main branch seventh limb east side-shoot from the left eye of the death’s head-a bee line from the tree through the shot fifty feet out.2.20 在多罗的怪诞小说中,有一个故事是这样的:地主彼得遇到了下图所示的消息,他找到了密钥,是一段整数:7876565434321123434565678788787656543432112343456567878878765654343211234a.破译这段消息。
提示:最大的整数是什么?b.如果只知道算法而不知道密钥,这种加密方案的安全性怎么样?c.如果只知道密钥而不知道算法,这种加密方案的安全性又怎么样?解:A.根据提示,将密文排成每行8字母的矩阵,密钥代表矩阵中每行应取的字母,依次取相应字母即可得明文。
明文为:He sitteth between the cherubims.The isles may be glad thereof.As the rivers in the South.B.安全性很好。
若密文的字母数为8n,则共有8n种可能的密钥,不易攻破。
C.安全性较差。
将字母总数与密钥总数相除,得每组8个字母,即可破译。
3.8 这个问题给出了用一轮DES加密的具体数字的例子。
假设明文和密钥K有相同的位模式,即:用十六进制表示:0 1 2 3 4 5 6 7 8 9 A B C D E F用二进制表示: 0000 0001 0010 0011 0100 0101 0110 01111000 1001 1010 1011 1100 1101 1110 1111a.推导第一轮的子密钥解:经过表3.4(b)PC-1置换,得:C0:1111000011001100101010100000D0:1010101011001100111100000000经过表3.4(d)左移,得:C1’:1010000110011001010101000001D1’:0101010110011001111000000001经过表3.4(c)置换选择,得:K1:0000 1011 0000 0010 0110 0111 1001 1011 0100 1001 1010 0101用十进制表示为:0 B 0 2 6 7 9 B 4 9 A 5b.推导L0,R0解:经过表3.2(a)置换,得L0:1100 1100 0000 0000 1100 1100 1111 1111R0:1111 0000 1010 1010 1111 0000 1010 1010c.扩展R0求E(R0)解:根据表3.2(C)扩充置换,得:E(R0) = 01110 100001 010101 010101 011110 100001 010101 010101d.计算A=E(R0) K1解:根据a、c可得A = 011100 010001 011100 110010 111000 010101 110011 110000e.把(d)的48位结果分成6位(数据)的集合并求对应S盒代换的值解:根据表3.3S盒代换得(1110) = (14) =0 (10进制) =0000 (2进制)(1000) = (8) = 12 (10进制)=1100 (2进制)(1110) = (14) =2 (10进制)=0010(2进制)(1001) = (9) = 1(10进制) =0001(2进制)(1100) = (12) =6 (10进制) =0110 (2进制)(1010) = (10) =13 (10进制)=1101(2进制)(1001) = (9) = 5 (10进制) =0101 (2进制)(1000) = (8) =0 (10进制) =0000 (2进制)f.利用(e)的结论来求32位的结果B解:B = 0000 1100 0010 0001 0110 1101 0101 0000g.利用置换求P(B)解:根据表3.2(d),得P(B) = 1001 0010 0001 1100 0010 0000 1001 1100h.计算R1=P(B) L0解:R1 = 0101 1110 0001 1100 1110 1100 0110 0011i.写出密文解:L1=R0,连接L1、R1可得密文为:MEYE823.12 16个密钥(K1、K2……K16)在DSE解密过程中是逆序使用的。
因此,图3.5的右半部分不再正确。
请模仿表3.4(d)为解密过程设计一个合适的密钥移位扩展方案。
解:选代轮数 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 移位次数0 1 2 2 2 2 2 2 1 2 2 2 2 2 2 13.10 (a)解:T16(L15 || R15) = L16 || R16T17(L16 || R16) = R16 || L16IP [IP–1 (R16 || L16)] = R16 || L16TD1(R16 || L16) = L16 || R16 f(L16, K16)=R15 || L15 f(R15, K16) f(R15, K16)= R15 ||L15(b)解:T16(L15 || R15) = L16 || R16IP [IP–1 (L16 || R16)] = L16 || R16TD1(R16 || L16) = R16|| L16 f(R16, K16)= L15 f(R15, K16)|| R15 f(R16, K16)≠L15 || R153.15For 1 ≤ i ≤ 128, take c i∈ {0, 1}128 to be the string containing a 1 in position i and then zeros elsewhere. Obtain the decryption of these 128 ciphertexts. Let m1, m2, . . . , m128 be the corresponding plaintexts. Now, given any ciphertext c which does not consist of all zeros, there is a unique nonempty subset of the c i’s which we can XOR together to obtain c. Let I(c) ⊆ {1, 2, . . . , 128} denote this subset. Observec=ÅiÎI c()ci=ÅiÎI c()E mi()=EÅiÎI c()miæèçöø÷Thus, we obtain the plaintext of c by computingiÎI c()mi. Let 0 be the all-zerostring. Note that 0 = 0 ⊕ 0. From this we obtain E(0) = E(0 ⊕ 0) = E(0) ⊕ E(0) = 0. Thus, the plaintext of c = 0 is m = 0. Hence we can decrypt everyc ∈ {0, 1}128.4.15 a. gcd(24140, 16762) = gcd(16762, 7378) = gcd(7378, 2006) = gcd(2006,1360) = gcd(1360, 646) = gcd (646, 68) = gcd(68, 34) = gcd(34, 0) = 34b. gcd(4655, 12075) = gcd(12075, 4655) = gcd(4655, 2765) = gcd(2765, 1890)= gcd(1890, 875) = gcd (875, 140) = gcd(140, 35) = gcd(35, 0) =354.17 a. Euclid: gcd(2152, 764) = gcd(764, 624) = gcd(624, 140) = gcd(140, 64)= gcd(64, 12) = gcd(12, 4) = gcd(4, 0) = 4Stein: A1 = 2152, B1 = 764, C1 = 1;A2 = 1076, B2 = 382, C2 = 2;A3 = 538, B3 = 191, C3 = 4;A4 = 269, B4 = 191, C4 = 4;A5 = 78, B5 = 191, C5 = 4;A6 = 39, B6= 191,C6 = 4;A7 = 152, B7 = 39, C7 = 4;A8 = 76, B8 = 39, C8 = 4;A9 = 38, B9 = 39, C9 = 4;A10 = 19, B10 = 39, C10 = 4;A11 = 20, B11 = 19, C11 = 4;A12 = 10, B12 = 19, C12 = 4;A13 = 5, B13 = 19, C13 = 4;A14 = 14, B14 = 5, C14 = 4;A15 = 7, B15 = 5, C15 = 4;A16 = 2, B16 = 5, C16 = 4;A17 = 1, B17 = 5, C17 = 4;A18 = 4, B18 = 1, C18 = 4;A19 = 2, B19 = 1, C19 = 4;A20 = 1, B20 = 1, C20 = 4;故gcd(2152, 764) = 1 ´ 4 = 4b. 在每一步算法中,Euclid算法所进行的除法运算比较复杂,而Stein算法只需完成除以2、相等、求差或取最小值的简单运算,减小了运算复杂度。
