Abstract
abstract例子

abstract例子
摘要是指对文章、论文或报告等内容进行简洁、概括性的描述,以
便于读者了解全文的主要内容和结论。
下面是一个摘要的例子:
本文旨在研究大气污染对人类健康的影响,并探讨减少氮氧化物排
放对改善空气质量的重要性。
研究采用了大样本量的数据,通过对污
染物浓度和健康指标的相关性分析,发现大气中高浓度的氮氧化物污
染与呼吸系统疾病、心血管疾病等健康问题之间存在显著关联。
此外,我们还调查了某市的氮氧化物排放情况,并使用模型模拟了减少排放
量的效果。
结果表明,减少氮氧化物排放量可以显著降低空气中的污
染物浓度,从而改善人类的健康状况。
综上所述,本研究强调了减少
氮氧化物排放对于保护人类健康和改善空气质量的重要性,为政府制
定环境保护政策和公众健康管理提供了科学依据。
abstract方法

abstract方法Abstract方法。
在面向对象的编程中,抽象方法是一种非常重要的概念。
它是一种在抽象类或者接口中声明但不实现的方法,需要由子类去实现具体的逻辑。
本文将对抽象方法进行详细的介绍,包括其定义、特点、使用方法以及示例等内容。
首先,抽象方法是指在抽象类或者接口中声明但不实现的方法。
它只有方法的声明,没有方法体。
抽象方法的存在是为了让子类去实现具体的逻辑,从而达到代码的灵活性和可扩展性。
在Java中,使用关键字“abstract”来声明抽象方法,而在C#中,则使用关键字“abstract”来修饰方法。
其次,抽象方法的特点是必须在抽象类或者接口中声明,而且不能包含方法体。
另外,包含抽象方法的类必须被声明为抽象类,而包含抽象方法的接口则必须被实现。
在使用抽象方法时,需要注意的是子类必须实现父类中的所有抽象方法,否则子类也必须声明为抽象类。
使用抽象方法的好处在于可以定义一套规范,让子类去实现具体的逻辑。
这样一来,可以在不同的子类中实现不同的逻辑,从而提高代码的复用性和可维护性。
此外,抽象方法还可以降低代码的耦合度,使得程序更加灵活和易于扩展。
下面通过一个简单的示例来说明抽象方法的使用方法。
假设有一个图形类Shape,其中包含一个抽象方法calculateArea()用于计算图形的面积。
然后有两个子类Circle和Rectangle分别继承Shape类,并实现calculateArea()方法来计算圆形和矩形的面积。
这样一来,就可以通过多态的方式来调用不同子类的calculateArea()方法,而不需要关心具体是哪个子类。
总之,抽象方法是面向对象编程中非常重要的概念,它可以提高代码的灵活性和可扩展性,降低代码的耦合度,使得程序更加易于维护和扩展。
通过本文的介绍,相信读者对抽象方法有了更深入的理解,可以在实际的项目中更加灵活地运用抽象方法来设计和实现代码。
4个步骤教你如何写好abstract部分

4个步骤教你如何写好abstract部分A b s t r a c t,就是对英文论文的一个简短总结,目的是为了告诉读者论文研究的是什么课题,以此来吸引读者。
一个好的a b s t r a c t,对英文论文的作用是非常大的,是论文的核心部分,所以一定得写好。
下面就给大家讲解一下如何写好a b s t r a c t部分。
1.无论任何学科,a b s t rac t需要包括以下几个重要组成部分和重要元素1)动机或问题的陈述:为什么我们对这个研究问题这么关心?你的研究针对的是实践性的,科学性的,理论性的还是艺术性的?有些a b s t r a c t 写作的时候,在写作动机之前要简要介绍相关的背景信息。
2)措施/流程/解决方法以及调查范围:为了得到相关的结果,你做了什么?3)结果/发现/产品:在上述的调查研究完成后,你学会了什么?发现了什么?创造了什么?4)结论/影响:你得出的哪些结论会产生更大的影响?然而,需要注意的是,根据不同的学科,要注意相关的可变性因素。
2.a b s t rac t中的语法特点和要求1)注意到细微的变化在陈述主要目标和调查范围的时候,多采用陈述性语言。
2)采用合适的方法描述方法的时候多使用过去时态。
要注意时态的一致性。
如果有必要,要按照时间的顺序进行排列。
3)注意结果的呈现方式只需要呈现结果即可。
以过去时态呈现出来。
4)注意结论的可靠性陈述个人观点。
在陈述主要结论的时候要使用现在时。
不要表现出试探性的倾向。
3.a b s t rac t s的类型a b s t r a c t s分为两种类型,i n f o r m a t i o n a l a b s t r a c t s和d e s c r i p t i v ea b s t r a c t s。
I n f o r m a t i o n a l A b s t r a c t s--针对r e p o r t s的相关内容进行沟通。
Abstract写作常用句型及句式

Abstract写作常⽤句型及句式Abstract⼀、在摘要中直接提出论⽂主题的句型和句式1、In this paper, we present a … approach to …本⽂提出了⼀种针对…的…⽅法。
2、In this paper, we describe improved … models for …本⽂介绍⼏种针对…的改进的…模型。
3、We propose a new … model and … algorithm that enables us to …我们提出⼀种新的…模型和…算法,它让我们能够…4、We present a … model that enables …我们提出了⼀种…模型,它使我们能够…5、This paper demonstrates the ability of … to perform robust and accurate …本⽂证明了…进⾏…可靠准确的…的能⼒。
6、In this paper we report results of a … approach to …本⽂报导了…的…⽅法的实验结果。
7、This paper demonstrates that … can effectively … with very high accuracy.本⽂证明,…能够有效地准确地…8、The purpose/goal/intention/objective/object/emphasis/aim of this paper is …本⽂的⽬的是…9、The primary/chief/overall/main object of this study is to survey …本研究的⾸要⽬标是考察…10、The chief aim of this paper/research/study/experiment/the present work is …本⽂的主要⽬标是…11、 The emphasis of this study lies in …我们的研究重点是…12、The work presented in this paper focuses on …本⽂所述⼯作重点放在…13、Our goal has been to provide …我们的⽬标是提供…14、The main objective of our investigation has been to obtain some knowledge of …我们的研究⽬标是获取有关…的知识。
考研英语:词汇abstract的中文翻译解析

考研英语:词汇abstract的中文翻译解析考研英语有许多题目组成,方便大家及时了解,下面为你精心准备了“考研英语:词汇abstract的中文翻译解析”,持续关注本站将可以持续获取的考试资讯!考研英语:词汇abstract的中文翻译解析abstract是什么意思及用法adj.1. 抽象的2. 抽象派的n.1. 抽象,抽象概念,抽象性2. 抽象派艺术作品3. 摘要,梗概及物动词:1. 提取,抽取2. 做…的摘要词形变化副词abstractly名称abstractness时态abstracted,abstracting,abstracts英语解释not representing or imitating external reality or the objects of naturemake off with belongings of othersdealing with a subject in the abstract without practical purpose or intentionconsider a concept without thinking of a specific example consider abstractly or theoreticallyconsider apart from a particular case or instancegive an abstract (of)a concept or idea not associated with any specific instancea sketchy summary of the main points of an argument or theoryexisting only in the mind separated from embodiment 例句She beheaded me, and flung my head into abstract space 她切下了我的头颅,把它扔进抽象的空间。
abstract 的写法
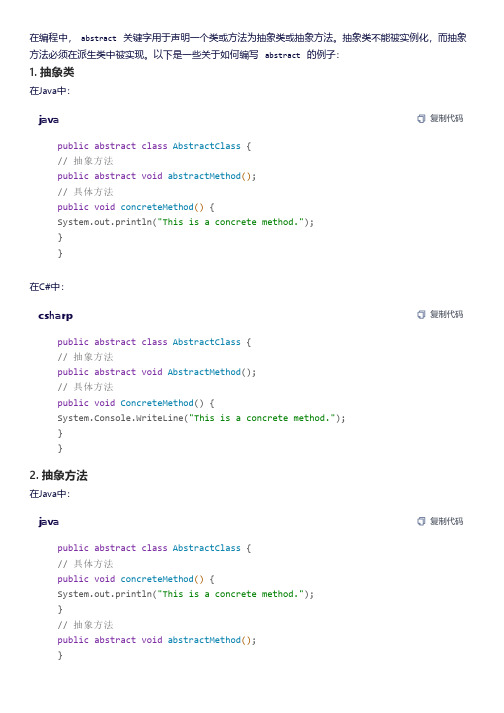
在编程中,abstract关键字用于声明一个类或方法为抽象类或抽象方法。
抽象类不能被实例化,而抽象方法必须在派生类中被实现。
以下是一些关于如何编写abstract的例子:1. 抽象类在Java中:java复制代码public abstract class AbstractClass {// 抽象方法public abstract void abstractMethod();// 具体方法public void concreteMethod() {System.out.println("This is a concrete method.");}}在C#中:csharp复制代码public abstract class AbstractClass {// 抽象方法public abstract void AbstractMethod();// 具体方法public void ConcreteMethod() {System.Console.WriteLine("This is a concrete method.");}}2. 抽象方法在Java中:java复制代码public abstract class AbstractClass {// 具体方法public void concreteMethod() {System.out.println("This is a concrete method.");}// 抽象方法public abstract void abstractMethod();}在C#中:csharp复制代码public abstract class AbstractClass {// 具体方法public void ConcreteMethod() {System.Console.WriteLine("This is a concrete method.");}// 抽象方法public abstract void AbstractMethod();}注意点:抽象类不能被实例化。
abstract 造句
abstract造句1、consider an abstract concept to be real.把一个抽象的概念作具体的考虑。
2、The choice of the data structure often begins from the choice of an abstract data type.所选择的数据结构往往首先从选择一个抽象的数据类型。
3、Abstract expressionism was at its peak in the 1940s and 1950s.20世纪45十时期是抽象体现主义艺术发展和进步的顶峰时期。
4、The param elements provide a value for each parameter reference used in the abstract pattern.param元素提供了抽象范式中每个参数引用的值。
5、For those of us living in China, there's nothing abstract about it.对于我们这些生活在中国的人来说,它一点也不抽象。
6、This is because you cannot create tooling for abstract types.这是因为您不能为抽象类型创建工具。
7、Many topological spaces with abstract convexity structure are all FC-spaces.许多具有抽象凸结构的拓扑空间都是FC-空间。
8、Platonism began the West’s pursuit of abstract truth from the times of ancient Greece.从古希腊时代起,柏拉图主义便开始了西方式的对抽象真理的追求。
9、It used abstract art and often childish language to ridicule the absurdity of the modern world.它使用抽象的艺术和幼稚的语言嘲弄了现代世界的荒谬。
abstract方法
用关键字abstract修饰的方法称为abstract方法(抽象方法)。
abstract int min (int x, int y );
对于abstract方法,只允许声明,不允许实现(没有方法体),而且不允许使用final和abstract同时修饰一个方法或类,也不允许使用static修饰abstract方法,即abstract方法必须是实例方法
1.abstract类中可以有abstract方法
和普通类(非abstract类)相比,abstract类中可以有abstract方法,
也可以有非abstract方法(非abstract类中不可以有abstract方法)。
注意:abstract类里也可以没有abstract方法。
2.abstract类不能用new运算符创建该类的对象。
3.abstract类的子类
如果一个非abstract类是abstract的子类,他必须重写父类的abstract
方法,即去掉abstract方法的abstract修饰,并给出方法体。
如果一个abstract 类是abstract类的子类,它可以重写父类的abstract方法,也可以继承父类的abstract方法。
4.abstract类的对象可以作为上转型对象
可以使用abstract类声明对象,尽管不能使用new运算符创建该对象,但该对象可以成为其子对象的上转型对象,那么该对象就可以调用子类重写的方法。
abstract是什么意思
abstract是什么意思abstract,他有几种词性?有形容词之外,还有哪些呢?下面店铺为大家带来abstract是什么意思,欢迎大家一起学习!abstract的英语音标英 [ˈæbstrækt] 美 [ˈæbˌstrækt]abstract的时态过去分词: abstracted 复数: abstracts 过去式: abstracted 现在分词: abstractingabstract的意思adj. 抽象的,理论上的; 难解的; 抽象派的; 茫然的;n. 抽象概念; 抽象派艺术作品; 摘要; [化]萃取物;vt. 提取,分离; 转移(注意等); 概括,摘录; <婉辞>剽窃; abstract的近义词n. [图情]摘要;抽象;抽象的概念brief , summary , resumeadj. 抽象的;深奥的deep , nonobjectivevt. [图情]摘要;提取;使……抽象化extract , briefabstract的同根词词根: abstractadj.abstracted 心不在焉的;出神的;分离出来的;抽出的abstractionist 抽象派艺术的abstractive 摘要式的;具有抽象能力的adv.abstractly 抽象地;理论上地abstractedly 茫然地;抽象地;心不在焉地n.abstraction 抽象;提取;抽象概念;空想;心不在焉abstractionism 抽象派艺术;抽象主义理论abstractionist 抽象派艺术家;理想主义者abstractor 萃取器;[图情] 摘录者abstract的词语辨析abstract, summary, resume, digest, outline这组词都有“摘要、概要、概括”的意思,其区别是:abstract 指论文、书籍等正文前的内容摘要,尤指学术论文或法律文件的研究提要。
学术英语写作Unit-5----Abstract
A descriptive abstract—a summary of someone else’s paper or book—is often required by professors to give you practice in summarizing and responding to sources.
Descriptive Abstracts
• tell readers what information the report, article, or paper contains.
• include the purpose, methods, and scope of the report, article, or paper.
Types of abstracts
1. descriptive abstracts: mainly direct to the original document and simply identifies basic subject of article.
2. informative abstracts: give much information about the original, summarizing the principal arguments and giving the principal arguments and summarizing the principal data.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Optimistic Fair Exchange in a Multi-user SettingYevgeniy Dodis New York University dodis@Pil Joong LeePOSTECHpjl@postech.ac.krDae Hyun YumPOSTECHdhyum@postech.ac.kr May10,2007AbstractThis paper addresses the security of optimistic fair exchange in a multi-user setting.While the security of public key encryption and public key signature schemes in a single-user setting guaranteesthe security in a multi-user setting,we show that the situation is different in the optimistic fairexchange.First,we show how to break,in the multi-user setting,an optimistic fair exchange schemeprovably secure in the single-user setting.This example separates the security of optimistic fairexchange between the single-user setting and the multi-user setting.We then define the formalsecurity model of optimistic fair exchange in the multi-user setting,which is thefirst completesecurity model of optimistic fair exchange in the multi-user setting.We prove the existence of ageneric construction meeting our multi-user security based on one-way functions in the randomoracle model and trapdoor one-way permutations in the standard model.Finally,we revisit twowell-known methodologies of optimistic fair exchange,which are based on the verifiably encryptedsignature and the sequential two-party multisignature,respectively.Our result shows that theseparadigms remain valid in the multi-user setting.1IntroductionMulti-user Security.In the early stage of modern cryptography,public key cryptography was usually studied in the single-user setting and the security model assumed only one public key[23,24]; one receiver in the public key encryption and one signer in the public key signature.However,there are many users in the real world and the security in the single-user setting does not guard against the attacks by colluding dishonest users.Even though the threats under multiple public keys were already pointed out in the1980’s(e.g.,see [38,26]),the security in the multi-user setting was formally studied only recently[4,21].Fortunately, these researches show that the security of encryption schemes in the single-user setting is preserved in the multi-user setting[4]and the same result holds good for signature schemes1[21].Therefore, we only have to deal with the single-user security and need not consider the multi-user security in the public key encryption and signature schemes.21A slightly different result is presented in[27],where authors argue that the existential unforgeability against chosen message attacks in the single-user setting is not enough for the multi-user setting.However,their duplicate-signature key selection attack is not aflaw from the view of standard security notions and can be thwarted with ease.2Sometimes,separate security analysis in the multi-user setting shows tighter security reduction[4],which is irrelevant to the subject of our paper.While the security of public key encryption and public key signature schemes in the single-user setting guarantees the security in the multi-user setting,there are other cryptosystems where the single-user security is not enough.For example,identity-based encryption schemes[37,10],by nature, must be analyzed in the multi-user setting and the security proof in the single-user setting is almost meaningless.Optimistic Fair Exchange.A fair exchange scheme is a protocol by which two parties Alice and Bob swap items or services without allowing either party to gain an advantage by quitting prematurely or otherwise misbehaving.For instance,Alice signs some statement(e.g.,e-cash)and Bob fulfills some obligation(e.g.,delivery of goods).However,each party will play the role only if he(or she)is sure that the other party will keep the appointment.Of course,one could use an online trusted third party in every transaction to act as a mediator;each party sends the item to the trusted third party,who upon verifying the correctness of both items,forwards each item to the other party.A drawback of this approach is that the trusted third party is always involved in the exchange even if both parties are honest and no fault was occurred.In practice,sending messages via a trusted third party can lead to performance problems as it becomes a bottleneck.A more desirable approach is that a semi-trusted arbitrator involves only in cases where one party attempts to cheat or simply crashes.We call such a fair exchange protocol optimistic.In this model, Alicefirst issues a verifiable“partial signature”σ to Bob.Bob verifies the validity of the partial signature and fulfills his obligation,after which Alice sends her“full signature”σto complete the transaction.Thus,if no problem occurs,the arbitrator does not participate in the protocol.However, if Alice refuses to send her full signatureσat the end,Bob will sendσ (and proof of fulfilling his obligation)to the arbitrator who will convertσ intoσ,sendingσto Bob.Optimistic fair exchange was introduced by Asokan et al.[1]and formally studied in[2,3]where several solutions were presented based on verifiably encrypted signatures.The approach of[2,3]was later generalized by[12],but all these schemes involve expensive and highly interactive zero-knowledge proofs in the exchange phase.Thefirst non-interactive verifiably encrypted signature was built by Boneh et al.[11]under a form of the computational Diffie-Hellman assumption over special elliptic curve groups.A different approach for building non-interactive optimistic fair exchange based on sequential two-party multisignatures was proposed by Park et al.[29],which was broken and repaired by Dodis and Reyzin[17].While the schemes in[17]are very efficient,one important drawback of the approach based on the sequential two-party multisignature is that it is setup-driven[39];the registration is required between the user and the arbitrator.Our Contribution.There have been attempts to formally define the security of optimistic fair exchange.Thefirst formal security model was proposed by Asokan et al.[2,3]but was not complete as their model did not consider a dishonest third party.3A more generalized and unified model for non-interactive optimistic fair exchange was suggested by Dodis and Reyzin[17].Their model,called verifiably committed signatures,incorporates all aspects of non-interactive optimistic fair exchange but was defined in a single-user setting.If the security of optimistic fair exchange in the single-user setting guarantees the multi-user security,the model of[17]is satisfactory.Otherwise,we should extend the 3In the construction based on verifiably encrypted signatures,each user has a signing key and the third party has a decryption key[2,3].Therefore,the dishonest third party,who does not know the signing keys,cannot compromise the signature schemes of users.However,we can devise other constructions which are secure in the model of[2,3]but they can be broken by a dishonest third party.For example,think of the optimistic fair exchange scheme where the third party simply holds the private keys of all users.model to the multi-user setting.In this paper,we show that the single-user security of optimistic fair exchange does not guarantee multi-user security.We present a simple counterexample based on a signature scheme and a trapdoor permutation.We then define the multi-user security model of optimistic fair exchange,extending the model of[17].While the single-user model of[17]is setup-driven,our multi-user model is setup-free [39],which we feel is a more natural and advantageous realization of“optimistic”fair exchange in the multi-user setting;(1)If every fair exchange is performed normally(i.e.,every user behaves honestly), it is desirable that users need not contact the arbitrator even for the registration purpose.(2)The arbitrator in setup-driven schemes should be semi-online to respond to registration requests,even when no dispute between users occurs.(3)If there are several arbitrators,the user in setup-free schemes can decide on a particular arbitrator in run-time.After defining security notions,we address our attention to the basic theoretical question,namely whether or not a scheme satisfying the security notions exists,and,if so,what are the minimal computational complexity assumptions under which this existence can be proven.We answer this by providing a generic setup-free construction which relies on one-way functions in the random oracle model and trapdoor one-way permutations in the standard model.While the construction in the standard model is of theoretic interest,some specific instantiations in the random oracle model are efficient enough for practical use.Finally,we revisit two well-known techniques of optimistic fair exchange;the verifiably encrypted signature and the sequential two-party signature.Fortunately,our result shows that these paradigms remain valid in the multi-user setting if the underlying primitives satisfy some security properties.Furthermore,the construction based on the verifiably encrypted signature shows that trapdoor permutations imply optimistic fair exchange schemes that are stand-alone as well as setup-free;a fair exchange scheme is stand-alone if the full signature is the same as it were produced by an ordinary signature scheme only[39].2Preliminaries2.1NotationIf k∈N,then1k denotes the string of k ones.If x is a string,then|x|denotes its length,while if X is afinite set then|X|denotes its size.If x and y are strings,then x y denotes the concatenation of x and y.A function f(n)is negligible if for all polynomials p(n),f(n)<1/p(n)hold for all sufficiently large n.An efficient algorithm A(·)is a probabilistic polynomial-time(PPT)Turing machine.If A(·) is an efficient algorithm and x is an input for A,then A(x)denotes the probability space that assigns to a string s the probability that A,on input x,outputs s.For a probability space P,x←P denotes the algorithm that samples a random element according to P.For afinite set X,x←X denotes the algorithm that samples an element uniformly at random from X.If p(·,·,···)is a boolean function, then Pr[p(x1,x2,...)|x1←P1,x2←P2,...]denotes the probability that p(x1,x2,...)is true after executing the algorithms x1←P1,x2←P2,....2.2NP-Relations andΣ-ProtocolsAn NP-relation R is a subset of{0,1}∗×{0,1}∗for which there is an efficient algorithm to decide whether(α,β)∈R or not in time polynomial in|α|.The NP-language L R associated with R is the set ofαfor which there existsβsuch that(α,β)∈R,i.e.,L R={α|∃β[(α,β)∈R]}.AΣ-protocol[16]for an NP-relation R is an efficient3-move two-party protocol between the proverand the verifier on a common inputα∈L R.Besidesα,a valid NP-witnessβforα,meaning(α,β)∈R, is also given to the prover as a private input.The proverfirst sends a commitment message c to the receiver.After receiving the commitment message c,the verifier sends a challenge message e to the prover.Finally,the prover sends a response message s to the verifier who decides to output1(accept) or0(reject)based on the inputαand the transcriptπ={c,e,s}.The transcriptπis valid if the verifier outputs1(accept).AΣ-protocol should satisfy three properties:correctness,special soundness,and special(honest-verifier)zero-knowledge.Correctness property states that for allα∈L R and all valid witnessesβforα, if the prover and the verifier follow the protocol honestly,the verifier must output1(accept).Special soundness property states that there is an efficient extraction algorithm(called a knowledge extractor) that on inputα∈L R and two valid transcriptsπ1,π2with the same commitment message c outputs βsuch that(α,β)∈R.Special zero-knowledge property states that there is an efficient simulation algorithm(called a simulator)that on inputα∈L R and any challenge message e,outputs a valid transcriptπ ={c ,e,s }.Moreover,the distribution of(c ,s )is computationally indistinguishable from the corresponding distribution on(c,s)produced by the prover knowing a valid witnessβforαand the verifier.A function f:{0,1}∗→{0,1}∗is a one-way function,if there exists a polynomial time algorithm which computes f(x)correctly for all x and the following probability is negligible for all PPT algorithm A:Pr[f(x )=y|x←{0,1}k;y=f(x);x ←A(y,1k)].A one-way function f is called a trapdoor (one-way)permutation,if f is a permutation(that is,every f(x)has a unique pre-image x)and there exists a polynomial-length trapdoor td such that the inverse of f can efficiently be computed with td. For simplicity,we let f−1be an inverse algorithm of f with the trapdoor td.It is known that any language in NP has aΣ-protocol if one-way functions exist.Theorem1([18,22])AΣ-protocol for any NP-relation can be constructed if one-way functions exist.While theΣ-protocol for any NP-relation can be constructed in generic ways[18,22],there exist very efficientΣ-protocols for specific cases;for example,GQ protocol[25]and Schnorr protocol[36].AΣ-protocol can be transformed into a signature scheme by using the Fiat-Shamir heuristic[20]. To sign a message m,the legal signer produces a valid transcriptπ={c,e,s}of theΣ-protocol, where e=H(c,m)and H(·)is a cryptographic hash function modeled as a random function.The signature scheme obtained by applying the Fiat-Shamir heuristic to theΣ-protocol is secure in the random oracle model[6,31].It is also known that the Fiat-Shamir heuristic provides a non-interactive proof of knowledge in the random oracle model(i.e.,the witness can be extracted by rewinding the adversary).If there are twoΣ-protocols,i.e.,Σ1for R1andΣ2for R2,we can construct anotherΣ-protocol ΣOR(called OR-proof)[16]which allows the prover to show that given two inputs x1,x2,he knows w such that either(x1,w)∈R1or(x2,w)∈R2without revealing which is the case(called the witness indistinguishability property[19]).By applying the Fiat-Shamir heuristic to the OR-proofΣOR,we obtain a signature scheme S OR(called the OR-signature)secure in the random oracle model such that a valid signature can be generated by the signer who knows a valid witness w corresponding to either of the two inputs x1,x2.It is known that the Fiat-Shamir heuristic does not affect the witness indistinguishability property of theΣ-protocol.2.3SignaturesSyntax.A signature scheme S consists of three efficient algorithms:S=(Sig-Gen,Sign,Vrfy).The key generation algorithm Sig-Gen takes as input a security parameter1k and outputs a signing key sk and a verification key vk.The signing algorithm Sign takes as input a signing key sk and a message m from the associated message space M,and outputs a signatureσ.The verification algorithm Vrfy takes as input a verification key vk,a message m,and a signatureσ;it outputs1if the signature is valid and0otherwise.We require that Vrfy vk(m,Sign sk(m))=1,for any m∈M.Security.We consider existential unforgeability under adaptive chosen message attacks,denoted by UF-CMA[24].The adversary A is given oracle access to the signing oracle O Sign,i.e.,A is allowed to query the signing oracle O Sign to obtain valid signaturesσ1,...,σn of arbitrary message m1,...,m n adaptively chosen by A.Naturally,A is considered successful only if it forges a valid signatureσof a message m which has not been queried to O Sign:m∈{m1,...,m n}.Quantitatively,we defineAdv S A(k)=Pr[Vrfy vk(m,σ)=1|(sk,vk)←Sig-Gen(1k),(m,σ)←A O Sign(vk)]where m should not be queried to the signing oracle O Sign.Let S=(Sig-Gen,Sign,Vrfy)be a signature scheme.An adversary A is said to(t,q s,ε)-break S,if A runs in time at most t,makes at most q s signing queries to O Sign,and succeeds in forgery with probability at leastε.S is said to be(t,q s,ε)-secure,if no adversary can(t,q s,ε)-break it. Asymptotically,S is UF-CMA-secure if Adv S A(k)is negligible for any PPT adversary A.2.4EncryptionSyntax.An encryption scheme E consists of three algorithms:E=(Enc-Gen,Enc,Dec).The key generation algorithm Enc-Gen takes a security parameter1k as input and outputs an encryption key ek and a decryption key dk.The encryption algorithm Enc takes as input an encryption key ek and a message m from the associated message space M,and outputs a ciphertext c.The decryption algorithm Dec takes a decryption key dk and a ciphertext c as input;it outputs some message m∈M if the ciphertext is valid and⊥otherwise.We require that Dec dk(Enc ek(m))=m,for any m∈M. Security.We consider indistinguishability against adaptive chosen ciphertext attacks,denoted by IND-CCA[32,5].Intuitively,no efficient adversary A can distinguish encryptions of any two equal-length messages m0,m1for a randomly selected public key,even though A is given oracle access to the decryption oracle O Dec.For an efficient algorithm A,which runs in two stages offind and guess, we define the adversary’s advantage asCCA-Adv E A(k)=Prb= b(ek,dk)←Enc-Gen(1k),(m0,m1,α)←A O Dec(ek,find),b←{0,1},c b←Enc ek(m b), b←A O Dec(c b,α,guess)−12where the challenge ciphertext c b should not be queried to the decryption oracle in the guess stage andαis some internal state information that A saves and uses in the two stages.Let E=(Enc-Gen,Enc,Dec)be an encryption scheme.An adversary A is said to(t,q d,ε)-break E,if A runs in time at most t,makes at most q d decryption queries to O Dec,and succeeds in distinguishing the challenge ciphertext with advantage at leastε.The encryption scheme E is said to be(t,q d,ε)-secure,if no adversary can(t,q d,ε)-break it.Asymptotically,E is CCA-secure if CCA-Adv E A(k)is negligible for any efficient adversary A.3Optimistic Fair Exchange in a Single-user Setting3.1DefinitionWe review the single-user model of optimistic fair exchange[17].Definition1A non-interactive optimistic fair exchange involves the signer Alice,the verifier Bob and the arbitrator Charlie,and is given by the following efficient algorithms:•Setup.This is a registration protocol between Alice and Charlie,by the end of which Alice learns her secret signing key SK,Charlie learns his secret arbitration key ASK,and they publish Alice’s public verification key PK and Charlie’s partial verification key APK.•Sig and Ver.These are similar to conventional signing and verification algorithms of an ordinary digital signature scheme.Sig(m,SK,APK)—run by Alice—outputs a signatureσon m,while Ver(m,σ,PK,APK)—run by Bob(or any verifier)—outputs1(accept)or0(reject).•PSig and PVer.These are partial signing and verification algorithms.PSig together with Res is functionally equivalent to Sig.PSig(m,SK,APK)—run by Alice—outputs a partial signature σ ,while PVer(m,σ ,PK,APK)—run by Bob(or any verifier)—outputs1(accept)or0 (reject).•Res.This is a resolution algorithm run by Charlie in case Alice refuses to open her signatureσto Bob,who in turn possesses a valid partial signatureσ on m(and a proof that he fulfilled his obligation to Alice).In this case,Res(m,σ ,ASK,PK)should output a legal signatureσon m. Correctness property states that•Ver(m,Sig(m,SK,APK),PK,APK)=1,PVer(m,PSig(m,SK,APK),PK,APK)=1,and Ver(m,Res(m,PSig(m,SK,APK),ASK,PK),PK,APK)=1.Ambiguity property states that•Any“resolved signature”Res(m,PSig(m,SK,APK),ASK,PK)is computationally indistinguish-able from the“actual signature”Sig(m,SK,APK).In a meaningful application,Charlie runs Res to produce a full signatureσfromσ only if Bob’s obligation to Alice has been fulfilled.The definition does not deal with the application-specific question of how Bob proves to Charlie that he fulfilled his obligation to Alice.The definition assumes the authenticity of public keys.The security of non-interactive optimistic fair exchange consists of ensuring three aspects:security against the signer,security against the verifier,and security against the arbitrator.In the following, we denote by O PSig an oracle simulating the partial signing procedure PSig,and by O Res an oracle simulating the resolution procedure Res.Security against Alice.We require that any PPT adversary A succeeds with at most negligible probability in the following experiment.Setup∗(1k)→(SK∗,PK,ASK,APK)(m,σ )←A O Res(SK∗,PK,APK)σ←Res(m,σ ,ASK,PK)success of A=[PVer(m,σ ,PK,APK)?=1∧Ver(m,σ,PK,APK)?=0]where Setup∗denotes the run of Setup with dishonest Alice(run by A)and SK∗is A’s state after this run.In other words,Alice should not be able to produce partial signatureσ ,which looks good to Bob but cannot be transformed into her full signature by honest Charlie.Security against Bob.We require that any PPT adversary B succeeds with at most negligible probability in the following experiment.Setup(1k)→(SK,PK,ASK,APK)(m,σ)←B O PSig,O Res(PK,APK)success of B=[Ver(m,σ,PK,APK)?=1∧(m,·)∈Query(B,O Res)]where Query(B,O Res)is the set of valid queries of B has asked to the resolution oracle O Res(i.e., (m,σ )such that PVer(m,σ ,PK,APK)=1).In other words,Bob should not be able to complete any partial signatureσ that he received from Alice into a complete signatureσ,without explicitly asking Charlie to do so.Note that there is no need to provide B with access to the signing oracle O Sig,since it could be simulated by O PSig and O Res.Finally,we remark that we also want Bob to be unable to generate a valid partial signatureσ which was not produced by Alice(via a query to O PSig).However,this guarantee will follow from a stronger security against Charlie,which is defined below.Indeed,we will ensure that even Charlie,who knows more than Bob(i.e.,ASK),cannot succeed in this attack. Security against Charlie.We require that any PPT adversary C succeeds with at most negligible probability in the following experiment.Setup∗(1k)→(SK,PK,ASK∗,APK)(m,σ)←C O PSig(ASK∗,PK,APK)success of C=[Ver(m,σ,PK,APK)?=1∧m∈Query(C,O PSig)]where Setup∗denotes the run of Setup with dishonest Charlie(run by C),ASK∗is C’s state after this run,and Query(C,O PSig)is the set of queries of C asked to the partial signing oracle O PSig.In other words,Charlie should not be able to produce a valid signature on m without explicitly asking Alice to produce a partial signature on m(which Charlie can complete into a full signature by himself using ASK).3.2Single-user Security Multi-user SecurityWe show that the single-user security of optimistic fair exchange does not imply the multi-user security by presenting a counter-example.Scheme.Let f(·)be a trapdoor permutation and S=(Sig-Gen,Sign,Vrfy)be a signature scheme.•Setup.Charlie generates a trapdoor permutation(f,f−1)and publishes APK=f,while he keeps ASK=f−1secret.Alice generates(sk,vk)←Sig-Gen(1k)and publishes PK A=vk and keeps SK A=sk secret.•Sig and Ver.To sign a message m,Alice chooses a random number r A,and computes y A=f(r A) andδA=Sign sk(m y A).The signature of m isσA=(r A,δA).To verify Alice’s signature σA=(r A,δA)of m,Bob computes y A=f(r A)and checks Vrfy vk(m y A,δA)?=1.•PSig and PVer.To generate a partial signature,Alice chooses a random number r A and computes y A=f(r A)andδA=Sign sk(m y A).The partial signature of m isσA=(y A,δA).Bob verifiesσA=(y A,δA)by checking Vrfy vk(m y A,δA)?=1.•Res.Given a partial signature(m,y A,δA),the arbitrator Charliefirst verifies its validity by checking Vrfy vk(m y A,δA)?=1.If valid,he computes r A=f−1(y A)and returnsσA=(r A,δA).The Single-user Security.The above scheme is secure in the single-user setting,which can easily be shown following the proofs in[17].For details,see appendix A.Attack Scenario.We observe that y A can be re-used by a dishonest user without knowing the corresponding r A,which causes the scheme to be insecure in the multi-user setting.Dishonest users Bob and Eve attack Alice as follows:1.Alice gives a partial signature(m A,y A,δA)to Bob,where y A=f(r A)andδA=Sign SKA(m A y A).2.Bob gives(m B,y B,δB)to his dishonest friend Eve,where m B=m A,y B=y A andδB=Sign SKB(m B y B).3.Eve comes to the arbitrator with(m B,y B,δB)and claims that Bob refuses to open his signature(and maybe gives a proof to the arbitrator that Eve fulfilled her obligation to Bob).4.The arbitrator does not suspect anything and completes this signature by giving r A=f−1(y B)to Eve.5.Eve gives r A to Bob,who now has completed the signature of Alice,(m A,r A,δA),although Alicenever intended to open this and Bob did not fulfill his duty to Alice.Therefore,the above optimistic fair exchange scheme is secure in the single-user setting but insecure in the multi-user setting.4This counterexample entails the following theorem.Theorem2The single-use security of optimistic fair exchange does not imply the multi-user security.Remark1(Disclaimer)Theorem2does not claim that all previous schemes(e.g.,[2,3,11,17]) are insecure in the multi-user setting.Even though the previous schemes were proved secure in the single-user models(or in the incomplete models),we believe that they are also secure in the multi-user model of Section4.4Optimistic Fair Exchange in a Multi-user Setting4.1DefinitionInstead of defining the syntax and security from scratch,we extend the model of[17]to the multi-user setting.Firstly,we separate the Setup algorithm of the single-user setting into two algorithms Setup TTP and Setup User to model the setup-free optimistic fair exchange.By running Setup User,eachuser U i generates his own key pair(SK Ui ,PK Ui).4A naive countermeasure such as including the signer’s public key in the message m does not defeat the collusion attacks.Definition2A non-interactive optimistic fair exchange involves the users(signers and verifiers)and the arbitrator,and is given by the following efficient algorithms:•Setup TTP.The arbitrator setup algorithm takes as input a security parameter and returns a secret arbitration key ASK and a public partial verification key APK.•Setup User.The user setup algorithm takes as input a security parameter and(optionally)APK.It returns a private signing key SK and a public verification key PK.•Sig and Ver.These are similar to conventional signing and verification algorithms of an ordinarydigital signature scheme.Sig(m,SK Ui ,APK)—run by a signer U i—outputs a signatureσUionm,while Ver(m,σUi ,PK Ui,APK)—run by a verifier—outputs1(accept)or0(reject).•PSig and PVer.These are partial signing and verification algorithms.PSig together with Res is functionally equivalent to Sig.PSig(m,SK Ui,APK)—run by a signer U i—outputs a partialsignatureσU i ,while PVer(m,σU i,PK Ui,APK)—run by a verifier—outputs1(accept)or0(reject).•Res.This is a resolution algorithm run by the arbitrator in case a signer U i refuses to open hissignatureσUi to a user U j,who in turn possesses a valid partial signatureσU ion m(and a proofthat U j fulfilled his obligation to U i).In this case,Res(m,σU i ,ASK,PK Ui)should output a legalsignatureσUion m. Correctness property states that•Ver(m,Sig(m,SK Ui ,APK),PK Ui,APK)=1,PVer(m,PSig(m,SK Ui,APK),PK Ui,APK)=1,and Ver(m,Res(m,PSig(m,SK Ui ,APK),ASK,PK Ui),PK Ui,APK)=1.Ambiguity property states that•Any“resolved signature”Res(m,PSig(m,SK Ui ,APK),ASK,PK Ui)is computationally indistin-guishable from the“actual signature”Sig(m,SK Ui,APK).We do not deal with the subtle issue of timely termination addressed by[2,3].We remark,however, that the technique of[2,3]can easily be added to our solutions to resolve this problem.The security of non-interactive optimistic fair exchange is composed of ensuring three aspects:security against signers,security against verifiers,and security against the arbitrator.To clarify the identity of the signer,we hereinafter assume that the message m(implicitly)includes the identity of the signer.One simple and trivial solution is to include the signer’s identity inside the message.If the included signer’s identity does not correspond to the subject of the alleged signer’s public key,we consider the signature (or the partial signature)is invalid.We also remark that it is a good practice to include an enforcing resolution policyκinside the message,as suggested in[3].In order to consider the collusion attack of dishonest users,we modify the resolution oracle O Res. In the single-user setting,the input to O Res is(m,σ ),assuming thatσ is the partial signature value of the single signer Alice and the oracle checks the validity ofσ by using Alice’s public key.In themulti-user setting,we define the input to O Res as(m,σ ,PK Ui )where PK Uiis the public key of thealleged signer U i.As usual,we assume that the authenticity of public keys can be verified and each user should show his knowledge of the legitimate private key in the public key registration stage to defend against key substitution attacks.。
