Towards Programmable Networks
从大规模生产到智能网络企业(英文)

From mass production to Intelligent Cyber-enterpriseIoan Dumitrache, Simona Iuliana Caramihai, Aurelian StanescuAutomatic Control and Computer Science Faculty,University POLITEHNICA of BucharestBucharest, Romaniaioan.dumitrache@acse.pub.ro; simona.caramihai@aii.pub.roAbstract—The paper proposes a new paradigm for the enterprise of the future, with respect to the requirements and the constraints it will be forced to face in order to progress and evolve. It is a paradigm which will take into account not only the complex relations between enterprise components - hu man, material and informational, bu t also the integration enterprise-society will all its aspects. There are presented some of the main trends in the control and management of manufacturing systems, in order to enlighten the evolution of the concepts towards that of Cyber-Physical Systems, which is the core of the proposed paradigm. A generic model of the next generation of Man fact ring Systems will be introd ced, based on the paradigm of Intelligent Cyber-Enterprise.Key words—Intelligent Manufacturing Sy stem, Cy ber-Phy sical System, enterprise modelI.G ENERAL F RAMEWORKGlobal economy and high-level technological support have created a real framework to change the manufacturing and industrial production to respond more quickly and efficiently with innovative products and processes.Next generation of manufacturing systems must accommodate with new requirements to continually adapt to changes and challenges of economy, society and environment. In the framework of global sustainable economy, the Manufacturing Systems will play an important role, with a real impact on society evolution.The new, innovative and technology-intensive products and processes require intelligent manufacturing equipment, specially designed for customization with respect to customer specific needs.Rapidly increasing product and process innovation, high quality, shorter time to market, better performing customized products increasing productivity and reducing costs are only few drivers to change the manufacturing paradigms to provide a competitive edge in the future. New generation of manufacturing systems need design models, standards, large sensor networks in order to increase yield and reduce material waste in micro-nano-fabrication. By advanced measurement systems is possible to evaluate fundamental process characteristics and to specify optional process parameters for improving the performance of next generation manufacturing equipments and quality of complex products of agile manufacturing.The complexity of manufacturing systems considering materials of tools, the machining equipments, large diversity of measurement of control methods and rigorous characterization of these systems interconnected with manufacturing equipment needs precisely and robust predictive models for optimization of all manufacturing operations.On the other hand, society itself, by its – sometimes manufacturing-driven – evolution is challenging the new manufacturing enterprise with: [1]−Globalization – Technology development as well as the subsequent organizational paradigm resulted in the social paradigm of the “global village” – with the unprecedentedly vast pool of resources, untapped skills, knowledge and abilities throughout the world and important clusters of customers in various parts of it.−Increased degree of networking/ connectionism (Internet of Things) – Internet has already modified the social framework by the effect of globally widespread information exchange. At manufacturing level, its beneficial effects could reside in the increased capacity of adaptation not only of the manufacturing shop-floor, but also of the manufacturing enterprise at the environment. Information about every item – human, machine, sensor, product – can be provided, practically instantaneous, at every monitoring/ decision point.−Scarce resources - Environmental pressures. This factor will put pressure on the efficient use of assets and supplies as well as on the medium and long term environmental impact of every enterprise, especially manufacturing. Factors as transport route, use of recycling materials/ re-use of parts, duration of functioning a.s.o. will have an increased importance in the estimated cost of a product.−High dynamics in technology development – This challenge is both a factor that acts on society – in general - and manufacturing – in particular – development (by generating means as well as pressure) and an effect of manufacturing development. Subjected to increased market pressure (in itself a factor generated by the increasing offer of products and services), manufacturing has favored/ encouraged technology2013 19th International Conference on Control Systems and Computer Sciencedevelopment as a mean to become more efficient and as a value added part of its production.One of the approaches of answering to challenges of this new knowledge and innovative economy at the beginning of the third millennium is to develop smart machines and processes, where most critical decisions and optimization is carried out by machines without operator intervention.Such smart machines and processes should have capabilities like: self awareness, self diagnosed and dynamic configuration in adaptive and optimal way.The new type of autonomous smart machines (ASM) needs to create and provide broad access to next-generation sensing technologies and the digital infrastructure for the enterprise application of manufacturing intelligence, considering data fusion, wired and wireless network which combine data and knowledge from different sources. This allows developing virtual factory and supply chain tools for real-time planning and point in time tracking/ traceability of materials and products.On the other hand, there exists already an experience concerning the entirely automated manufacturing, which proved its limitations as the dynamics of the socio-economical environment increased.Human operators could prove less reliable that automated control systems, but they are certainly more flexible and can adapt faster to new situations. It could then be envisaged an approach based on the close interaction of man and machines, raising the enterprise intelligence to a new qualitative stage.The following sections will present a short overview on manufacturing enterprise paradigm evolution with a special emphasis on factors as technological research and organizational paradigms impact.This overview aims to introduce finally the concept of Intelligent Cyber-Enterprise as an emerging structure based on Smart Factory, Cognitive Enterprise, Knowledge Management and Cyber-Physical Systems.II.E VOLUTION OF ENTERPRISE PARADIGM In [2] is presented an evolution of manufacturing enterprises paradigm taking into account external pressure factors and technological support. It underlines three main phases:-Mass production: it responded primarily to the need of population to acquire new products, with a specialorientation on their functionality. Mass productionrelied on (supposedly) unlimited number ofcustomers, though focusing on optimization ofmanufacturing processes and low cost/ product. Itgenerated and benefited from new control concepts:Numerical Control Machines, Industrial Robots, and,later on, whole Automated Manufacturing Systems.Repetitive tasks were more and more assigned tomachines, though increasing the speed and thereliability of the production. Human resource,especially at shop-floor level, was considered ratheras a source of errors than an important asset.Productivity and low cost/ product were consideredthe most important performance indicators of anenterprise. Hierarchical organization was the mostsuccessful managerial approach.But the success of the mass production created a new societal requirement: customization. As competition and production optimization resulted in a large supply of goods with comparable functionalities and costs, customers required new choice criteria: color, shape, differentiation from other similar products a.s.o. This tendency created the first shift, towards the second phase:-Flexible Manufacturing: In years ’70 the paradigm of “Flexible Manufacturing System” was defined, as amachining system configuration with fixed hardwareand programmable software, capable to handlechanges in work orders, production schedules,machining programs and tooling, so as to cost-effective manufacture several types of parts, withshortened changeover time, on the same system, atrequired (and variable) volume and given quality.The exchange from mass production to customization has given to the customer a new position in the product life-cycle, and required new views of human resources and their management. Interaction among people and machines became crucial for the rapid changes at shop-floor level, so, human resources gained importance in fast error recovery. Human resource became more creative at the design level and more skilled in order to operate at the shop floor level, as a result of training and instruction, and thus becoming a valuable asset for the enterprise. Moreover, with the increasing importance of computer-aided techniques, high qualified personnel needed complementary training in computer use.Several level of flexibility defined at the level of products and processes needed new organizational approaches – on product-oriented teams rather than on competence pools. Matrix organizations started their evolution.The capability of storing and retrieving information and data proved to be one of the key factors for the efficiency of those new (and expensive) systems. First difficulties appeared in the transfer of information between software applications, as CAD and CAM, that had different approaches to integrate the same data.The new shift in manufacturing had to solve this problem and developed a new era in the use of information technologies.-Computer Integrated Manufacturing and Virtual Organizations: are only two of the enterpriseparadigms that evolved in this phase, which is stillunder development and which is mostly focusing ondifferent use of Computing, Control, Communicationand Cognition for obtaining maximum of flexibilityand adaptivity for enterprises.CIM-OSA [3] defines a model-based enterprise engineering method which categorizes manufacturing operations into Generic and Specific (Partial and Particular)functions. These may then be combined to create a model which can be used for process simulation and analysis. The same model can also be used on line in the manufacturing enterprise for scheduling, dispatching, monitoring and providing process information.The CIM-OSA approach and the paradigms derived from the integrationist theory in manufacturing insisted on very precise and detailed organization of the enterprise as a key factor of success.However, research proved that organization and flexibility should be appropriately balanced in order for the enterprise to successfully compete on dynamic environments.The paradigm of Virtual Organization was one of several (from Concurrent Engineering to Intelligent Manufacturing Systems, and networked enterprises) which tried to obtained the above-mentioned balance. The made use of collaborative autonomous structures, simple enoughto be versatile, but connected by ellaborated protocols of communications, ready to ensure efficient behavior.A Virtual Organization (VO) is, according to a widely accepted definition: “a flexible network of independent entities linked by information technology to share skills, knowledge and access to others' expertise in non-traditional ways”. It may include companies, institutions and/or individuals delivering a product or service on the basis of a common business understanding. [4]Oragnization aspects shifted from matrix to networked enterprises. The enterprise is regarded as a network integrating advanced technologies, computers, communication systems, control strategies as well as cognitive agents (both humans and/or advanced intelligent systems) able not only to manage processes and products, but also to generate new behaviours for adapting themselves to a dynamic market. The study of the emergent behaviour of those cognitive agents imposes new theories,as the theory of complexity.Collaborative networked organizations (CNO) representa new dynamic world, based on cooperation, competitiveness, world-excellence and agility. They are complex production structures – scaling from machine tools, robots, conveyors, etc., to knowledge networks, including humans – and should normally be designed as hives of autonomous but cooperative/ collaborative entities.Human resource is seen, from this shift on, as one of the most important asset of an enterprise, a knowledge stakeholder, and a special attention is given to a new area, specially designed: knowledge management.Next section will present some of the most important evolutions of this phase, enabling the enterprise to evolve towards an intelligent behavior.III.I NTELLIGENT C YBER-E NTERPRISETo increase flexibility, “future management systems shallfocus on the integration of the human in a real interconnection with intelligent agents”.People working together with a defined purpose, people interacting with specialized machines in order to increase their flexibility by a new dimension of intelligence, people interacting with complex IT structures, improving their communication and learning capabilities - will allow the creation of self-optimizing joint cognitive systems, whose complete structure will generate intricate behaviors.Smart manufacturing is one of the most prominent directions of development, as it has as declared objective (/) to transform “traditional factories from cost centers into profit centers that progressive businesses will strategically invest in to increase sales”.There are already prestigious promoters of programs in Smart Manufacturing, as the National Institute of Standards and Technology and the Smart Manufacturing Leadership Coalition (https:///about), focusing on topics as “Smart Manufacturing Processes and Equipment” and “Smart Manufacturing and Construction Systems”.Main objectives of this new generation of autonomous smart manufacturing could be:-Development of innovative pathways to competitively manufacture existing and novel materials and productsin response to growing local and global market -Agile processes in highly optimized manufacturing plants and supply networks with rapid response tofluctuations or new trends in customer demands -Efficiency of resources-Safety and confidence – products and processes will be generated safely and reliable through comprehensivetracking of sustainable production-Sustainability – minimize impact on the environment and climate changesAn Intelligent Manufacturing Enterprise could be based on the Smart Factory and will include the overall operation workflow system allowing a remote and distributed control approach, by using virtual monitoring and RFID capabilities. (Fig.1)Such enterprises could extend themselves by interconnections with suppliers and customers, fusions, and networking with other temporary partner business systems for creating an optimized and competitive global structure.A smart factory is a macro-system for manufacturing purposes, whose shop-floor activities are supported by smart machines and networked sensors, with RFID-based monitoring and intelligent automation. An important component in ensuring the proper balance between flexibility and cost-efficiency is the human resource that operates it and which is a basic subset of enterprise knowledge stakeholders.Smart processes are designed on the basis of multi-scale dynamic modeling and simulation and their adequacy to the actual state of the enterprise is permanently checked out via the integrative workflow management system.IT infrastructure integration at enterprise level provides business intelligence and adequate knowledge management systems offers support for adaptation and innovation, generating an intelligent overall behavior at the enterprise level.Intricate inputs from suppliers, marketing research, technological research a.s.o. are permanently modifying enterprise state whereas the socio-environmental factors as well as new paradigms in enterprise management could necessitate dynamic reconfiguration of enterprise structure, organization and objectives.Enterprise itself could, in subtle ways, via its customer’s reactions, contribute to the dynamics of its environment.In order to better understand and thoroughly react in such a scenario it is necessary to use a new approach both in modeling and in control implementation – as those that actually exist seem to attain certain saturation with regard performance.Cyber-Physical Systems constitute a very promising research direction in this area.The entire architecture of a manufacturing system as a Cyber-Physical System by measurement methods, instruments, algorithms as well as knowledge and data exchange protocols and standards will allow self awareness, self diagnosis and optimization of processes and equipments. A new vision on manufacturing processes will take into consideration some new areas like: smart machining and micro- and nano-manufacturing. The impact on smart machining area will be observed in widespread use of modeling and simulation of machines and processes and products to enable realization of autonomous smart machines.Such systems will allow cognitive planning and control activities for production with characteristics as: perception, reasoning, remembering, decision making, learning – without necessitating a fixed programming approach. (/el/smartcyber.cfm)The Cognitive Factory is a new level of Smart Factory, including machines and processes with cognitive capabilities in order to allow them to asses and increase their scope of operation autonomously.The main capabilities of the technical cognitive systems like perception, reasoning, planning, decision-making, learning and action allow to the Cognitive Factory to have an autonomous behavior in a turbulent and competitive environment.By integrating human capabilities with addressed and intelligent control systems into next cognitive factory will increase the flexibility, adaptivity, autonomy and intelligenceof production systems. The reconfigurability of manufacturing systems could be achieved at the overall system structure level and on the functional level of production.A large intelligent multi-agent architecture should be created for the Cognitive Factory, where coordination and control, cooperative execution of complex tasks, effective operation in concrete competitive scenarios implies the participation of all agents, sharing semantic models and ontologies.Figure 1: Intelligent, smart manufacturing-based Enterprise approachThe system reacts to disturbances autonomously, based both on the reaction of each agent and on the cooperation among them. The manufacturing system should be considered as a swarm of cognitive agents controlling work-pieces, machines, robots, transport systems, software applications and representing human resources implied in the process.In the Intelligent Cyber-Enterprise that will have to face the challenges of this century all resources are modeled by autonomous entities with specific functionalities and physical structure, various degrees of intrinsic intelligence, geographically distributed and controlled, but whose cooperation will emerge into a globally intelligent behavior.Another approach which should be considered for the behavior generation and networking of agents is that of Biological Manufacturing Systems, where machine tools, transport systems, robots, a.s.o. should be considered as biological organisms able to adapt themselves to environmental changes.Figure 2 is representing the way in which the IntelligentCyber-Enterprise integrates all the above-presented paradigms Figure 2. Intelligent Cyber-EnterpriseIV.K NOWLEDGE M ANAGEMENT IN THE I NTELLIGENTC YBER-E NTERPRISEIn one form or another, knowledge management, as the discipline who deals with procedures concerning storing, retrieving and updating manufacturing process data, information and knowledge, was always implied in manufacturing enterprise.Modern mass manufacturing has started by using data, as the primary level of knowledge, with the purpose of ensuring a constant quality of products and processes optimization. Sometimes referred as raw intelligence or evidence [5], data result from observation and measurement and can be retrievedin primitive messages of low level automation. In order to properly use data for analysis and optimization, they have to be organized: sorted, classified, indexed a.s.o. and this contextualization transform data in information.Information needs understanding and information management implies primarily filtering and correlation of data, but also association and extrapolation of new obtained information.As manufacturing paradigms evolved through Flexible Manufacturing Systems to CIM-OSA, procedures of information management were improved until, from models that synthesized static and dynamic relationships between information, a new level of intelligence arise: knowledge.Knowledge is, for data and information, what is integrated enterprise for flexible manufacturing. This notion, together with standardization supported by the Integrated Infrastructure, has marked a shift in knowledge management – a discipline that started to be recognized and developed. Knowledge engineering and data mining, supporting first generation of knowledge management, brought their support in developing new types of manufacturing systems.Actually, all new paradigms from the third stage of evolution presented above are using knowledge management in order to improve productivity and tried to find out means for knowledge modeling so as to generate new cycles of transformation of tacit in explicit knowledge (Dalkir).The Intelligent Cyber-Enterprise is intended to use knowledge management in order to link together all its components.In its representation as a Cyber-Physical System, the Intelligent Manufacturing Enterprise is composed by modules with very different physical structure, functionality, dimension a.s.o., having in common some features as ():•computation/information processing and physical processes are tightly integrated and non-separablefrom the behavioral point of view;•functionality and salient system characteristics are emerging through the interaction of physical andcomputational objects;•computers, networks, devices and their environments in which they are embedded have interacting physicalproperties, consume resources, and contribute to theoverall system behavior.These systems which are so different and which have usually competing local and immediate goals will need a different way of interaction and communication in order to achieve their global responsibility.As all of them will embed knowledge in different ways, it is for knowledge management to be the driver for finding ways of representing and connecting the individual pieces.It seems actually that software interoperability is not able to solve inter-organizational knowledge transfer problems, neither to deal appropriately, into a flexible, adaptive and open fashion with heterogeneous systems.As the Intelligent Cyber-Physical Enterprise is extending furthermore the concepts of human-machine cooperation introduced by Smart and Cognitive manufacturing paradigms, it could be foreseen that a communication platform supporting both biological and non-biological cognitive agents’ interactions should use some bio-inspired novel approach.V.C ONCLUSIONManufacturing is one of the most important human activities, shaping the evolution of societies and generating both challenges and solutions. It is only natural that its future development should be carefully anticipated in order to ensure sustainability. The classical manufacturing enterprise concept can no more offer ways of evolution into a world that is continuously changing. A new way of development should be found, which is the purpose of this paper.The paper synthesizes ideas, paradigms and trends in manufacturing, technological and organizational areas which are considered important in the evolution of manufacturing enterprise structure, with the purpose to propose, on their basis a new concept for the enterprise of the future.The Intelligent Cyber-Enterprise will combine the newest developments in engineering and control, with advanced concepts of knowledge management and human-machine interaction, challenging with the finding of new ways of communication and cooperation with the purpose of generating an intelligent behavior.R EFERENCES[1]Ioan Dumitrache, Simona Caramihai, The Enterprise of Future as aCyber-Physical System in Procs. Of MIM2012, ifacpaperplaza, 2012 [2]Ioan Dumitrache, Simona Caramihai, The Intelligent ManufacturingParadigm in Knowledge Society Knowledge Management. In Virtanen,P. and Helander, N. (ed.), InTech, ISBN: 978-953-7619-94-7, 2010[3]CIMOSA: Open System Architecture for CIM Research Reports Esprit /Project 688/5288. AMICE Ed. Springer;, ISBN-10: 3540562567 ISBN-13: 978-3540562566, 1993[4]Luis Camarinha-Matos , Afsarmanesh, H., Collaborative Networks: anew scientific discipline, Journal of Intelligent Manofacturing , No.16 ,Springer Science, pp 439-452, 2005[5]Kimiz Dalkir, Knowledge Management in Theory and Practice. Elsevier,ISBN-13: 978-0-7506-7864-3, ISBN-10: 0-7506-7864-X, 2005。
智慧新飞跃的英语作文

In the era of rapid technological advancement,the concept of smart has become increasingly prevalent in our daily lives.From smart homes to smart cities,the integration of technology into our surroundings is reshaping the way we live,work,and interact with the world.The leap in intelligence is not just about making things more convenient its about enhancing our quality of life and pushing the boundaries of whats possible.The Evolution of Smart TechnologyThe journey towards smarter living began with the advent of the internet and the proliferation of digital devices.The first wave of smart technology included simple automations like programmable thermostats and remotecontrolled lights.However,it was the introduction of smartphones and the subsequent development of the Internet of Things IoT that truly revolutionized the concept of smart living.Smart HomesAt the heart of the smart revolution is the smart home.These homes are equipped with devices that can be controlled remotely,learn from user behavior,and automate tasks to increase comfort and efficiency.Smart thermostats,for instance,can adjust the temperature based on the time of day or the occupants preferences.Smart lighting systems can mimic natural light patterns to enhance mood and productivity.Smart CitiesThe concept of smart homes extends to the broader environment with the idea of smart cities.These urban spaces use data collected from IoT devices to manage resources more effectively.Traffic management systems can optimize routes to reduce congestion,while smart grids can balance energy consumption and production for greater sustainability.Artificial Intelligence and Machine LearningThe real power behind the leap in smart technology lies in artificial intelligence AI and machine learning.These technologies enable devices to learn from data,make predictions, and improve over time.For example,AI can analyze traffic patterns to predict congestion and suggest alternative routes,or it can monitor energy usage to optimize power distribution.Challenges and Ethical ConsiderationsWhile the benefits of smart technology are numerous,there are also challenges to consider.Data privacy is a significant concern,as smart devices collect vast amounts of personal information.Additionally,the reliance on technology raises questions about security and the potential for misuse.Ethical considerations also come into play,particularly with AI.As machines become more intelligent,there is a need to ensure that they are programmed to make decisions that align with human values and promote fairness and equality.The Future of Smart TechnologyLooking ahead,the future of smart technology is likely to be even more integrated and sophisticated.We can expect to see more personalized experiences,where technology not only responds to our needs but anticipates them.The development of5G networks will enable faster data transfer,supporting more complex and responsive smart systems. Moreover,the integration of virtual and augmented reality into smart environments will create new dimensions for interaction,blurring the lines between the digital and physical worlds.ConclusionThe leap in smart technology represents a significant shift in how we interact with our surroundings.As we continue to develop and integrate these technologies,it is crucial to address the challenges and ethical considerations that arise.By doing so,we can ensure that the benefits of smart technology are realized in a way that enhances our lives while respecting our values and protecting our privacy.。
自动化专业英语原文和翻译

自动化专业英语原文和翻译引言概述:自动化是现代工程技术领域中的重要学科,它涉及到自动控制系统、机器人技术、传感器技术等多个领域。
在自动化专业中,学习和掌握英语是必不可少的,因为英语是国际通用语言,也是自动化领域中的重要交流工具。
本文将介绍一些常见的自动化专业英语原文和翻译,以帮助学习者更好地理解和运用这些术语。
一、自动化概念及应用1.1 自动化定义英文原文:Automation refers to the use of technology to control and operate processes or systems without human intervention.翻译:自动化是指利用技术来控制和操作过程或系统,无需人为干预。
1.2 自动化应用领域英文原文:Automation is widely applied in manufacturing, transportation, healthcare, and many other industries.翻译:自动化广泛应用于制造业、交通运输、医疗保健等许多行业。
1.3 自动化优势英文原文:Automation offers advantages such as increased productivity, improved efficiency, and enhanced safety.翻译:自动化提供了增加生产力、提高效率和增强安全性等优势。
二、自动控制系统2.1 自动控制系统定义英文原文:An automatic control system is a set of devices that manage and regulate the behavior of a system or process automatically.翻译:自动控制系统是一组设备,能够自动管理和调节系统或过程的行为。
2.2 自动控制系统组成英文原文:An automatic control system consists of sensors, actuators, controllers, and communication networks.翻译:自动控制系统由传感器、执行器、控制器和通信网络组成。
基于FPGA的稀疏化卷积神经网络加速器

190
计算机工程
2021 年 7 月 15 日
作 。 如 果 在 计 算 系 统 中 只 运 行 非“0”元 素 参 与 的 有 效 操 作 ,那 么 算 法 模 型 的 计 算 量 就 能 大 幅 减 少 。 然 而 ,传 统 针 对 CNN 的 并 行 加 速 器 或 [3-5] 数 据 流 优 化[6] 通 常 只 适 用 于 稠 密 矩 阵 运 算 ,并 不 能 在 实 际 意 义 上 减 少 操 作 数 。 因 此 ,需 要 针 对 稀 疏 性 做 优 化 处 理 ,以 探索稀疏神经网络硬件加速器。
运 算 的 权 重 。 式(1)的 基 本 变 量 和 参 数 在 表 1 中 做
详细说明。
"{bnuv}Î[1B]*[1N ]*[1V ]*[1U ],
Y CONV [bnuv]=
CJK
∑∑∑(X CONV [bcv + ju + k]* F [ncjk])+ βCONV [n] c=1 j=1 k=1
1 卷积神经网络及其稀疏性分析
1.1 卷积神经网络 卷 积 神 经 网 络 是 一 种 前 馈 网 络 ,包 含 由 卷 积 层
和子采样层构成的特征抽取器以及由全连接层组成 的 分 类 器 。 在 卷 积 层 中 ,有 多 个 卷 积 滤 波 器(卷 积 核)扫 过 该 层 的 特 征 图 像 做 卷 积 操 作 得 到 下 一 级 特 征 图 ,如 式(1)所 示 ,卷 积 滤 波 器 中 的 参 数 即 为 参 与
基于 FPGA 的稀疏化卷积神经网络加速器
狄 新 凯 1,2,杨 海 钢 1,2
(1. 中国科学院空天信息创新研究院,北京 100094;2. 中国科学院大学,北京 100049)
交换机sdn原理

交换机sdn原理English:Software-Defined Networking (SDN) is a network architecture approach that enables the network to be intelligently and centrally controlled, or programmed, using software applications. In a traditional network, the control plane (which makes decisions about where traffic should be sent) and the data plane (which actually forwards the traffic) are tightly coupled within network devices like switches and routers. In an SDN environment, these planes are decoupled, and the control plane is moved to a centralized controller, which communicates with the network devices to program and manage their behavior. This allows for more agile, flexible, and programmable networks, as administrators can directly and dynamically control network traffic using software. This makes it easier to implement network-wide policies, automate network configuration, and optimize network performance. SDN switches play a key role in this architecture by allowing the centralized controller to make decisions and define the forwarding behavior of the switch, leading to more efficient and cost-effective network operations.中文翻译:软件定义网络(SDN)是一种网络架构方法,它使网络能够通过软件应用程序进行智能和集中控制或编程。
计算机专业英语多选题

1.A user interface we said here is __ABC________A.a text-based user interface or GUIB.an interface between a computer and its peripheral deviceC.an interaction between an operating system and a userD.an interaction between an application program and a user2.___A___provides transparent transfer of data between end users, providing reliable data transfer services to the upper layers.A.The Transport LayerB. Session LayerC. Network LayerE.Application Layer E. Presentation Layer3.Many viruses do harmful things such as (ABCD ).A.deleting filesB. slowing your PC downB.simulating typos D. changing random data on your disk4.We can classify programming languages under two types:(AB ) languages and ( )languages.A.high-levelB. low-levelC. advanced-levelD. basic-level5.With an Internet connection you can get some of the basic services available are:___ABCD_______A.E-mailB. TelnetC. FTPD. Usenet news6. A general purpose computer has four main sections: ( ABCE).A.the control unitB. the memoryC. the input and output devicesD. the cpuE. the arithmetic and logic unit (ALU),7.Windows 2000 has the key technologies, they are (ABCD ).A.securityB. active directoryC. flat directoryD. enterprise management8.The register file is___ACD_______A.addressed by much shorter addressesB. physically largeC.physically smallD. one the same chip as the CPU9. A stack protocol can be used for (A ).A.removing the latest element ins( )ertedB. removing the earliest element ins( )ertedC. subroutine callsD. operation of arithmetic expressions10.The end equipment in a communication system includes (ABCD ).A.printersB. computersC. CRTsD. keyboards11.Microsoft Office Professional 2000 include____ABCD______.A.Excel 2000B. PowerPoint 2000C. Word 2000D. Outlook 200012. A general purpose computer has four main sections: ______ABCE______A.the input and output devicesB. the memoryC. the arithmetic and logic unit (ALU),D. the cpuE. the control unit13.The two most common types of scanners are (BC ) and ( )A. hand-held scannersB. flatbed scannersC. auto scannersD. handler scanners14.Some viruses use (CD ) and ( ) techniques to hide their existence.A.quickly spreadB. replace a part of system softwareC. stealthD. polymorphic15.The Windows 2000 product line includes____ABCD______.A.Windows 2000 Datacenter ServerB. Windows 2000 ProfessionalC. Windows 2000 ServerD. Windows 2000 Advanced Server16.Similar to viruses, you can also find malicious code in (ABC ).A.Trojan HorsesB. logic bombsC. wormsD. Microsoft Word Documents17.Viruses all have two phases to their execution, the ( ) and the ( BD).A.create phaseB. attack phaseC. del( )ete phaseD. infection phase18.Active Directory can help you (ACD ).A.get off the limits of down level networksB. deliver complete enterprise security by itselfC. build a complex international networkD. manage every resource with a single logon19.High-level languages are commonly classified as (ACDE ).A.object-orientedB. automaticC. functionalD. logic languagesE. procedure-oriented20.(CD )is a type of executable file .A.TXT fileB. JPG fileC. EXE fileD. COM file21.( ABCD) maybe a certain cause that some viruses infect upon.A.an external event on your PCB. a dayC. a counter within the virusD. a time22.(BC )is a type of executable file .A.TXT fileB. EXE fileC. COM fileD. JPG file23.The web browsers which is normal used, such as(ABCE ).A.FirefoxB. Internet ExplorerC. OpraD. ICQE. Apple Safari24.Newer ideas in computing such as(ABDE ) have radically altered the traditional concepts that once determined program form and functionA.artificial intelligenceB. distributed computingC. software engineeringD. parallel computingE. data mining25.Microsoft Windows currently supports __AC___and _____file systemsA.NTFSB. OCFSC. FATD. ext2E. NILFS26.Modem is ____ACD______.A.a modulator/demodulatorB. a data setC. a demodulatorD. a modulator27.The equipment _AB_____.A.transfers the number of bits in serial formB.manipulates digital information internally in word unitsC.transfers the number of bits in parallelD. manipulates digital information internally in serial form28.Electronic commerce that is conducted between businesses is referred to as business-to-business or DA. C2CB. C2BC. e-commerceD. B2B29.The World Wide Web also subsumes previous Internet information systems such as (AC ).A.GopherB. FtpC. FTPD. Telnet relies on the services of .NET data providers.There are ABCDA.ConnectionB. Data AdapterC. DataReaderD. Command31.The development process in the software life cycle involves four phases: analysis, design, implementation, and ___ACDE_____.A.analysisB. auditC. implementationD. designE. testing32.The end equipment in a communication system includes __ABCD____.A.printersB. CRTsC. computersD. keyboards33.In electronic commerce ,information search and discovery services include (ABCDE ).A.search enginesB. information filtersC. software agentsD. directoriesE. electronic catalogs34.GIS work with two fundamentally different types of geographic models.They are the (BD ).A.geography modelB. vector modelC. mathematic modelD. raster modelE. data model35.The two most common types of scanners are ____AC___and _____A.flatbed scannersB. hand-held scannersC. auto scannersD. handler scanners36.Windows 2000 has the key technologies, they are ( ABCD).A.active directoryB. flat directoryC. enterprise managementD. securityputer software, or just software is a general term used to describe a collection of computer programs, procedures and documentation that perform some tasks on a computer system.The term includes: ABCA.Firmware which is software programmed resident to electrically programmable memorydevices on board mainboards or other types of integrated hardware carriers.B.Application software such as word processors which perform productive tasks for users.C.Middleware which controls and co-ordinates distributed systems.38.Software engineering is related to the disciplines of ___ADE_____A.project managementB. natural languageC. netural networkD. systems engineeringE. computer science39.What make it is difficult to agree on how to count viruses? ABCDA.some viruses can create different versions when they infect other programsB.just a trivial change may create a new virusC.some viruses can use polymorphic techniqueD.new virus arise from an existing virus40. A virus is a program that reproduces its own code by (ABC ).A.ins_erting into the middle of a fileB. simply placing a pointerC. adding to the end of a fileD. replacing another program41.Input devices include: ____ABCD______.A.the keyboardB. microphoneC. touch screenD. the mouse42.Viruses all have two phases to their execution, the ( ) and the ( AD).A.attack phaseB. create phaseC. del_ete phaseD. infection phase43.The equipment (BC ).A.manipulates digital information internally in serial formB.manipulates digital information internally in word unitsC.transfers the number of bits in serial formD.transfers the number of bits in parallel44.Office automation is___CD_______.A.. the computerB. communications technologyC. the application of computerD. used to improve the productivity of people45.The types (classes, structs, enums, and so on) associated with each .NET data provider are located in their own namespaces are: ABCDEA.System.Data.SqlClient. Contains the SQL Server .NET Data Provider types.B.System.Data.Odbc. Contains the ODBC .NET Data Provider types.C.System.Data. Contains provider-independent types such as the DataSet and DataTable.D.System.Data.OracleClient. Contains the Oracle .NET Data ProviderE.System.Data.OleDb. Contains the OLE DB .NET Data Provider types.46.C++ is __ACD________.A.extended from CB. a superset of CC. object-orientedD. procedure-oriented47.Some viruses, with no attack phase, often damage the programs or disks they infect because they (AD ).A.have bugs in themB. show messages on your screenC. steal storageD. contain poor quality code48.Windows 2000 is ( A).A.an inventive technologyB. used for building a scalable networkB.the same as Windows NT D. new lease of Windows49.Some common applications related to electronic commerce are the following:A.TeleconferencingB. Online bankingC. EmailD. Instant messagingE. Enterprise content managementF. NewsgroupsG. Shopping cart software50. A program is a sequence of ( ) that can be executed by a computer.It can either be built into the hardware or exist independently in the form of (BC ).A.hardwareB. softwareC. instructionsD. data51.Electronic payments include ___ABCD______.A.credit card paymentsB. electronic checksC. digital currenciesD. cash payment52.The web browsers which is normal used, such as____ABCD_____.A.OpraB. Internet ExplorerC. FirefoxD. Apple SafariE. ICQputer programs fall into two major classes: __AC____and ____.A.application programsB. application suiteC. operating systemsD. database application54.Database connection ( B) allows an application to reuse an existing connection from a pool instead of repeatedly establishing a new connection with the database.A.pondB. poolingC. linkD. connection55.The development process in the software life cycle involves four phases: analysis, design, implementation, and (ABCE ).A.implementationB. designC. analysisD. auditE. testing56.Hypermedia include ( ABCDEF)A.video clipsB. imagesC. textD. flashE. vidoeF. sounds57.An asleep state is_____ABD_____ed to lessen wear-and tear on the computerB. used for saving energyC. indicated by the indicator light putting outD. a low power standby mode58.Electronic payments include (ABCD ).A.digital currenciesB. electronic checksC. credit card paymentsD. cash payment59.You want to (BCD ) maybe wake up a virus that has residented in memory.A.del( )ete a fileB. access a disketteC. execute a programD. copy a file60.Before you turn the power on with a new computer, you should make sure_____ABCD_____A.the computer system has been set upB. the computer is already out of the boxB.appropriate software have been installed D. appropriate cables are correctly connected61.Security is usually enforced through ___ABE________.A.access controlB. encryptionC. data retrievingD. data storingE. auditingputer programming is the process of ABCD__the source code of computer programs.A. testingB. maintainingC. debuggingD. writing63.Queues that occur everyday life can be seen ( ABCD).A.as automobiles waiting for a traffic lightB. as people waiting for service at a bankC. in certain societies lacking equalityD. in an emergency room of a hospital64.Static graphics include____AB______.A.animatorsB. photographsC. moviesD. pictures66.which is the threat to computer security in the following choices ? ABCDA. Computer CriminalsB. Human ErrorsC. Computer CrimeD. earthquake65.The attributes of the stack are______A____.A.queueB. FIFOC. built into their circuitryD. LIFO66.If a virus simply reproduce and have no cause for an attack phase, but it will still ( ) without your permission. BDA.play musicB. stealing storageC. del( )ete filesD. pilfer CPU cycles67.According to the text,modern digital computers can be divided into four major categories on the basis of cost and performance.They are _______ABDE___________. A.minicomputers B. mainframes C. note book D. workstation E. microcomputers F. lenovo68.The Application layer in TCP/IP Model is correspond to (ABD ) in OSI ModelA.Presentation LayerB. Session LayerC. Transport LayerD. Application LayerE. Network Layer69. A computer system user generally more cares for___ABD_______A.speed of computationB. storage sizeC. physical size of the computerD. efficiency of the computer71.Cache is____ABC______A. slowB. high costC. fastD. relatively small72.We can say a bus is simply_____ABC_____ .A. a wireB. a 16-bit busC. a group of wiresD. a 8-bit bus73.Viruses can delay their attack for (ABCD ).A.yearsB. monthsC. weeksD. days74.In order to increase our computer’s performance we need to____BCD______A.buy a L1 cacheB. have a much larger main memoryC. have a L2 cacheD. buy a L2 cache75.The software that controls the interaction between the input and output hardware is called BIOS,which stands of __A________A.Basic Input Output SystemB. Classic Input Output SystemB.Advanced Input Output System D. Junior Input Output System76.To enhance performance of a computer system we should____ACD______A.improve the pattern of referencing operandB. optimize the simple movement of dataC. optimize the basic sequence control mechanismD. use IF and LOOP instructions as many as possible77.Their company used international lawyers to prosecute a crime ring involving software ____A____in Thailand.A.piracyB. copyingC. duplicationD. cloning78.The software that controls the interaction between the input and output hardware is called BIOS,which stands of (B)A.Advanced Input Output SystemB. Basic Input Output SystemC. Classic Input Output SystemD. Junior Input Output System79.Some viruses use ( AC) and ( ) techniques to hide their existence.A.stealthB. quickly spreadC. polymorphicD. replace a part of system software80.Middleware lies in______ACD____A.the middle of interactions between different application programsB.the top of the layering vertical stackC.the top of an operating systemD.the middle of the layering vertical stack81.Software includes ( ACDE) etcA.video gamesB. all kinds of filesC. programsD. websitesE. mobile application82.The major functional components of an office automation system include: ___ABCD__A.electronic mailB. personal assistance featuresC. information storage and retrievalD. text processing83.The Internet carries various information resources and services, such as (ACDEF ) and the inter-linked hypertext documentsA.online chatB. talkingC. electronic mailD. file transferE. online gamingF. file sharing84. A processor is composed of:____ABCD______.A.an arithmeticB. a control unitC. RegistersD. logic unit85.Functions of the compiler used in RISC are ___ABC_______A.to optimize register usageB.to maximize register usageC.to allocate registers to those variables that will be used the most in a given time periodD.to compile a high level language program86. A digital computer is generally made up of five dstinct elements: a central processing unit,(ABCD).A.a busB. input devicesC. memeory storage devicesD. output devicesE. crt screen87.There are AB (CD)_between the DTEs.A.digital-to-analog converterB. the modemC. communications equipmentD. will be replaced by an upd_ated standard88.What make it is difficult to agree on how to count viruses? ABCDA.just a trivial change may create a new virusB.some viruses can use polymorphic techniqueC.some viruses can create different versions when they infect other programsD.new virus arise from an existing virus89.which aspect have to be considered in the design of a piece of software. ABCDEFGA.Fault-toleranceB. ExtensibilityC. ModularityD. CompatibilityE.MarketabilityF. PackagingG. Maintainability90.Active Directory can help you (ACD ).A.build a complex international networkB. deliver complete enterprise security by itselfC.manage every resource with a single logonD. get off the limits of down level networks91.Early computer solved_____CD_____ problems.A.controlB. engineeringC. mathematicalD. business applications92.The tools which Programming software usually provides include: ABCDEA.debuggersB. text editorsC. linkersD. compilersE. interpreters93.DTE is ( AB).A.data terminal equipmentB.the last piece of equipment that belonged to the subscriber in a data link systemC.satelliteD. Digital T-carrier94.According to the text,modern digital computers can be divided into four major categories on the basis of cost and performance.They are ( BDEF).A.note bookB. microcomputersC. lenovoD. minicomputersE. workstationF. mainframes95.which is the type of electronic commerce in the following choice ACA.B2BB. C2CC. B2C96.The operations of a structured data type might act on (ABCD ).A.a stackB. the values of the data typeC. component elements of the data structureD. a queue97.Types of media include__ACD________.A.textB. animationC. audioD. full-motion video98. A virus is a program that reproduces its own code by (ABC ).A.simply placing a pointerB. adding to the end of a fileC. ins( )erting into the middle of a fileD. replacing another program99.According to the text,the author mentions three of the most commonly used types of printer.They are (BDE ).A.belt printerB. dot-matrix printers;C. array printerD. laser printerE. inkjet printers100.The end equipment in a communication system includes ___ABD_______A.keyboardsB. DCEC. CRTsD. computers101.Software includes _____ACDE________etcA.programsB. all kinds of filesC. video gamesD. websitesE. mobile application102.With .NET, Microsoft is opening up a channel both to ( ) in other programming languages and to ( BC). (developers; components)A.coderB. developersC. componentsD. architecturemon contemporary operating systems include (ABCD ).A.LinuxB. Microsoft WindowsC. SolarisD. Mac OS104.A mechanism for translating Internet hostnames into IP addresses is___BCD_______A.equipped into the general-purpose operating systemB.typically inside of operating system kernelC.as a middleware by author’s definitionD.typically outside of operating system kernel105.RISC is____ABC______ed for many computer manufacturers nowadaysB.guided to be built from studying the execution behavior of high-level language programsC.abbreviation of reduced instruction set computerD.abbreviation of complex instruction set computer106.With .NET, Microsoft is opening up a channel both to _BC_______in other programming languages and to ________. (developers; components)A.coderB. componentsC. developersD. architecture107.The tools which Programming software usually provides include: ABCDEpilersB. interpretersC. text editorsD. linkersE. debuggers108.The following products of software are belong to middleware____BCD______A.OracleB. IBM’s Web Sphere MQC. Java 2 PlatformD. J2EE109.The system manager used by a fast processor can____BCD______A.connect a networkB. monitor processor’s core temperatureC. monitor processor’s supply voltagesD. reset a system110.Queues that occur everyday life can be seen (ABCD ).A.as automobiles waiting for a traffic lightB. as people waiting for service at a bankC. in an emergency room of a hospitalD. in certain societies lacking equality111.C++ include the following pillars: ____ABCD______.A.data hidingB. polymorphismC. encapsulationD. inheritance112.Windows 2000 is____ACD______A.new lease of WindowsB. an inventive technologyC. the same as Windows NTD. used for building a scalable network113.We use paged virtual memory to___ABCD_______A.extend the size of memoryB. reduce latency of the diskC. store large program and data setD. increase bandwidth of the disk114.According to the physical size of computers we can classify the __ABCD____ computers into A. supercomputer B. minicomputer C. microcomputer D. mainframe115.Some common applications related to electronic commerce are the following: ABCDEFGA.EmailB. TeleconferencingC. Instant messagingD. Shopping cart softwareE.NewsgroupsF. Enterprise content managementG. Online banking116.One machine cycle in RISC has _B_________A.two machine instructionsB. one machine instructionC. four machine instructionsD. three machine instructions117.The function of computer hardware is typically divided into three main categories.They are____ADE_____.A.inputB. motherboardC. cpuD. storageE. output118.Active Directory supports ( ABCD).A.granular access controlB. inheritanceC. encapsulationD. delegation of administrative task119.The core of SQL is formed by a command language that allows the (ACDE ) and performing management and administrative functions.A.deletion of dataB. process of dataC. updating of dataD. retrieval of dataE. ins( )ertion of data120.Some commentators say the outcome of the information revolution is likely to be as profound as the shift in (ABCD )A.industrialB. agriculturalC. Service IndustryD. handicraft industry。
通信常用缩略语
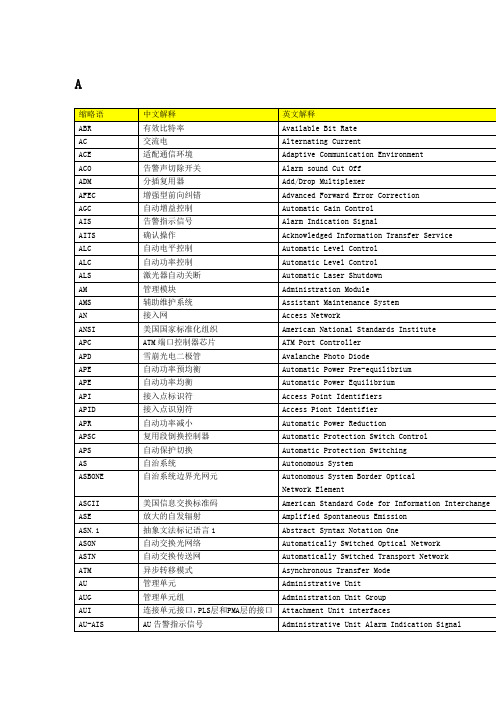
异步转移模式
Asynchronous Transfer Mode
AU
管理单元
Administrative Unit
AUG
管理单元组
Administration Unit Group
AUI
连接单元接口,PLS层和PMA层的接口
Attachment Unit interfaces
AU-AIS
AU告警指示信号
DCF
色散补偿光纤
Dispersion Compensation Fiber
DCG
色散补偿光栅
Dispersion Compensation Grating
DCM
色散补偿模块
Dispersion Compensation Module
DCN
数据通信网
Data Communication Network
ALC
自动电平控制
Automatic Level Control
ALC
自动功率控制
Automatic Level Control
ALS
激光器自动关断
Automatic Laser Shutdown
AM
管理模块
Administration Module
AMS
辅助维护系统
Assistant Maintenance System
AU Pointer Positive Justification
AUG
管理单元组
Administration Unit Group
AUP
管理单元指针
Administration Unit Pointer
AWG
阵列波导光栅
Arrayed Waveguide Grating
OpenFlow Enabling Innovation in Campus Network以及中文翻译

附录A 外文原文OpenFlow: Enabling Innovation in Campus NetworksNick McKeown Stanford University Guru Parulkar Stanford UniversityTom AndersonUniversity of WashingtonLarry PetersonPrinceton UniversityHari BalakrishnanMITJennifer RexfordPrinceton UniversityScott Shenker University of California,BerkeleyJonathan Turner Washington University inSt. LouisThis article is an editorial note submitted to CCR. It has NOT been peer reviewed.Authors take full responsibility for this article’s technical ments can be posted through CCR Online.ABSTRACTThis whitepaper proposes OpenFlow: a way for researchers to run experimental protocols in the networks they use every day. OpenFlow is based on an Ethernet switch, with an internal flow-table, and a standardized interface to add and remove flow entries. Our goal is to encourage networking vendors to add OpenFlow to their switch products for deployment in college campus backbones and wiring closets. We believe that OpenFlow is a pragmatic compromise: on one hand, it allows researchers to run experiments on heterogeneous switches in a uniform way at line-rate and with high port-density; while on the other hand, vendors do not need to expose the internal workings of their switches. In addition to allowing researchers to evaluate their ideas in real-world traffic settings, OpenFlow could serve as a useful campus component in proposed large-scale testbeds like GENI. Two buildingsat Stanford University will soon run OpenFlow networks, using commercial Ethernet switches and routers. We will work to encourage deployment at other schools; and we encourage you to consider deploying OpenFlow in your university network too.Categories and Subject DescriptorsC.2 [Internetworking]: RoutersGeneral TermsExperimentation, DesignKeywordsEthernet switch, virtualization, flow-based1. THE NEED FOR PROGRAMMABLE NETWORKSNetworks have become part of the critical infrastructure of our businesses, homes and schools. This success has been both a blessing and a curse for networking researchers; their work is more relevant, but their chance of making an impact is more remote. The reduction in real-world impact of any given network innovation is because the enormous installed base of equipment and protocols, and the reluctance to experiment with production traffic, which have created an exceedingly high barrier to entry for new ideas. Today, there is almost no practical way to experiment with new network protocols (e.g., new routing protocols, or alternatives to IP) in sufficiently realistic settings (e.g., at scale carrying real traffi c) to gain the confidence needed for their widespread deployment. The result is that most new ideas from the networking research community go untried and untested; hence the commonly held belief that the network infrastructure has “ossified”.Having recognized the problem, the networking community is hard at work developing programmable networks, such as GENI [1] a proposed nationwide research facility for experimenting with new network architectures and distributed systems. These programmable networks call for programmable switches and routers that (using virtualization) can process packets for multiple isolated experimental networks simultaneously. For example, in GENI it is envisaged that a researcher will be allocated a slice of resources across the whole network, consisting of a portion of network links, packet processing elements (e.g. routers) and end-hosts; researchers program their slices to behave as they wish. A slice could extend across the backbone, into access networks, into college campuses, industrial research labs, and include wiring closets, wireless networks, and sensor networks.Virtualized programmable networks could lower the barrier to entry for new ideas, increasing the rate of innovation in the network infrastructure. But the plans for nationwide facilities are ambitious (and costly), and it will take years for them to be deployed.This whitepaper focuses on a shorter-term question closer to home: As researchers, how can we run experiments in our campus networks? If we can figure out how, we can start soon and extend the technique to other campuses to benefit the whole community.To meet this challenge, several questions need answering, including: In the early days, how will college network administrators get comfortable putting experimental equipment (switches, routers, access points, etc.) into their network? How will researchers control a portion of their local network in a way that does not disrupt others who depend on it? And exactly whatfunctionality is needed in network switches to enable experiments? Our goal here is to propose a new switch feature that can help extend programmability into the wiring closet of college campuses.One approach -that we do not take -is to persuade commercial “name-brand” equipment vendors to provide an open, programmable, virtualized platform on their switches and routers so that researchers can deploy new protocols, while network administrators can take comfort that the equipment is well supported. This outcome is very unlikely in the short-term. Commercial switches and routers do not typically provide an open software platform, let alone provide a means to virtualize either their hardware or software. The practice of commercial networking is that the standardized external interfaces are narrow (i.e., just packet forward ing), and all of the switch’s internalflexibility is hidde n. The internals differ from vendor to vendor, with no standard platform for researchers to experiment with new ideas. Further, network equipment vendors are understandably nervous about opening up interfaces inside their boxes: they have spent years deploying and tuning fragile distributed protocols and algorithms, and they fear that new experiments will bring networks crashing down. And, of course, open platforms lower the barrier-to-entry for new competitors.A few open software platforms already exist, but do not have the performance or port-density we need. The simplest example is a PC with several network interfaces and an operating system. All well-known operating systems support routing of packets between interfaces, and open-source implementations of routing protocols exist (e.g., as part of the Linux distribution, or from XORP [2]); and in most cases it is possible to modify theoperating system to process packets in almost any manner (e.g., using Click [3]). The problem, of course, is performance: A PC can neither support the number of ports needed for a college wiring closet (a fan out of 100+ ports is needed per box), nor the packet-processing performance (wiring closet switches process over 100Gbits/s of data, whereas a typical PC struggles to exceed 1Gbit/s; and the gap between the two is widening).Existing platforms with specialized hardware for line-rate processing are not quite suitable for college wiring closets either. For example, an ATCA-based virtualized programmable router called the Supercharged Planet Lab Platform [4] is under development at Washington University, and can use network processors to process packets from many interfaces simultaneously at line-rate. This approach is promising in the long-term, but for the time being is targeted at large switching centers and is too expensive for widespread deployment in college wiring closets. At the other extreme is NetFPGA [5] targeted for use in teaching and research labs. NetFPGA is a low-cost PCI card with a user-programmable FPGA for processing packets, and 4 ports of Gigabit Ethernet. NetFPGA is limited to just four network interfaces—insufficient for use in a wiring closet.Thus, the commercial solutio ns are too closed and inflex ible and the research solutions either have insufficient performance or fan out, or are too expensive. It seems unlikely that the research solutions, with their complete generality, can overcome their performance or cost limitations. A more promising approach is to compromise on generality and to seek a degree of switch flexibility that is:Figure 1 Idealized OpenFlow Switch. The Flow Table is controlled by a remote controllervia the Secure Channel.•Amenable to high-performance and low-cost implementations.•Capable of supporting a broad range of research.•Assured to isolate experimental traffic from production traffic. •Consistent with vendors’ need for closed platforms.This paper describes the OpenFlow Switch—a specification that is an initial attempt to meet these four goals.2. THE OPENFLOW SWITCHThe basic idea is simple: we exploit the fact that most modern Ethernet switches and routers contain flow-tables (typically built from TCAMs) that run at line-rate to im plement firewalls, NAT, QoS, and to collect statistics. While each vendor’s flow-table is different, we’ve identified an interesting common set of functions that run in many switches and routers. OpenFlow exploits this common set of functions.OpenFlow provides an open protocol to program the flow-table in different switches and routers. A network administrator can partition traffic into production and research flows. Researchers can control their own flows -by choosing the routes their packets follow and the processing they receive. Inthis way, researchers can try new routing protocols, security models, addressing schemes, and even alternatives to IP. On the same network, the production traffic is isolated and processed in the same way as today.The datapath of an OpenFlow Switch consists of a Flow Table, and an action associated with each flow entry. The set of actions supported by an OpenFlow Switch is extensible, but below we describe a minimum requirement for all switches. For high-performance and low-cost the data-path must have a carefully prescribed degree of flexibility. This means forgoing the ability to specify arbitrary handling of each packet and seeking a more limited, but still useful, range of actions. Therefore, later in the pape r, define a basic required set of actions for all OpenFlow switches.An OpenFlow Switch consists of at least three parts: (1) A Flow Table, with an action associated with each flow entry, to tell the switch how to process the flow, (2) A Secure Channel that connects the switch to a remote control process (called the controller), allowing commands and packets to be sent between a controller and the switch using (3) The OpenFlow Protocol, which provides an open and standard way for a controller to communicate with a switch. By specifying a standard interface (the OpenFlow Protocol) through which entries in the Flow Table can be defined externally, the OpenFlow Switch avoids the need for researchers to program the switch.It is useful to categorize switches into dedicated OpenFlow switches that do not support normal Layer 2 and Layer 3 processing, and OpenFlow-enabled general purpose commercial Ethernet switches and routers, to which the Open-Flow Protocol and interfaces have been added as a new feature.Dedicated OpenFlow switches. A dedicated OpenFlow Switch is a dumb datapath element that forwards packets between ports, as defined b y a remote control process. Figure 1 shows an example of an OpenFlow Switch.In this context, flows are broadly defined, and are limit ed only by the capabilities of the particular implementation of the Flow Table. For example, a flow could be a TCP con nection, or all packets from a particular MAC address or IP address, or all packets with the same VLAN tag, or all packets from the same switch port. For experiments involving non-IPv4 packets, a flow could be defined as all packets matching a specific (but non-standard) header.Each flow-entry has a simple action associated with it; the three basic ones (that all dedicated OpenFlow switches must support) are:1 Forward this flow’s packets to a given port (or ports). This allows packets to be routed through the network. In most switches this is expected to take place at line-rate.2 Encapsulate and forw ard this flow’s packets to a con troller. Packet is delivered to Secure Channel, where it is encapsulated and sent to a controller. Typically used for the first packet in a new flow, so a controller can decide if the flow should be added to the Flow Table. Or in some experiments, it could be used to forward all packets to a controller for processing.3 Drop this flow’s packets. Can be used for security, to curb denial of service attacks, or to reduce spurious broadcast discovery traffic from end-hosts.An entry in the Flow-Table has three fields: (1) A packet header that defines the flow, (2) The action, which defines how the packets should be processed, and (3) Statistics, which keep track of the number of packets and bytes foreach flow, and the time since the last packet matched the flow (to help with the removal of inactive flows).In the first generation “Type 0” switches, the flow header is a 10-tuple shown in T able 1. A TCP flow could be specified by all ten fields, whereas an IP flow might not include the transport ports in its definition. Each header field can be a wildcard to allow for aggregation of flows, such as flows in which only the VLAN ID is defined would apply to all traffic on a particular VLAN.Table 1 The header fields matched in a “Type 0” OpenFlow switch.The detailed requirements of an OpenFlow Switch are defined by the OpenFlow Switch Specification [6].OpenFlow-enabled switches. Some commercial switches, routers and access points will be enhanced with the OpenFlow feature by adding the Flow Table, Secure Channel and OpenFlow Protocol (we list some examples in Section 5). Typically, the Flow Table will re-use existing hardware, such as a TCAM; the Secure Channel and Proto col will be ported to run on the switch’s operating system. Figure 2 shows a network of OpenFlow-enabled commercial switches and access points. In this example, all the Flow Tables are managed by the same controller; the OpenFlow Protocol allows a switch to be controlled by two or more controllers for increased performance or robustness. Our goal is to enable experiments to take place in an existing production network alongside regular traffic and applications. Therefore, to win theconfidence of network administrators, OpenFlow-enabled switches must isolate experimental traffic (processed by the Flow Table) from productiontraffic that is to be processed by the normal Layer 2 and Layer 3 pipeline of the switch. There are two ways to achieve this separation. One is to add a fourth action:4. Forward this flow’s packets through the switch’s nor mal processing pipeline.The other is to define separat e sets of VLANs for experimental and production traffic. Both approaches allow normal production traffic that isn’t part of an experiment to be processed in the usual way by the switch. All OpenFlow-enabled switches are required to support one approach or the other; some will support both.Additional features. If a switch supports the header formats and the four basic actions mentioned above (and detailed in the OpenFlow SwitchSpecification), then we call it a “Type 0” switch. We expect that many switches will support additional actions, for example to rewrite portions of the packet header (e.g., for NAT, or to obfuscate addresses on intermediate links), and to map packets to a priority class. Likewise, some Flow Tables will be able to match on arbitrary fields in the packet header, enabling experiments with new non-IP protocols. As a particular set of features emerges, we willdefine a “Type 1” switch.Controllers.A controller adds and removes flow-entries from the Flow Table on behalf of experiments. For example, a static controller might be a simple application running on a PC to statica lly establish flows to interconnect a set of test computers for the duration of an experiment. In this case the flows resemble VLANs in current networks— providing a simple mechanism toisolate experimental traffic from the production network. Viewed this way, OpenFlow is a generalization of VLANs.One can also imagine more sophisticated controllers that dynamicallyadd/remove flows as an experiment progresses. In one usage model, a researcher might control the complete network of OpenFlow Switches and be free to decide how all flows are processed.Figure 2 Example of a network of OpenFlow-enabled commercial switches and routers.A more sophisticated controller might support multiple researchers, each with different accounts and permissions, enabling them to run multiple independent experiments on different sets of flows. Flows identified as under the control of a particular researcher (e.g., by a policy table running in a controller) could be delivered to a researcher’s user-level control program which then decides if a new flow-entry should be added to the network of switches.3. USING OPENFLOWAs a simple example of how an OpenFlow Switch might be used imagine that Amy (a researcher) invented Amy-OSPF as a new routing protocol toreplace OSPF. She wants to try her protocol in a network of OpenFlow Switches, without changing any end-host software. Amy-OSPF will run in a controller; each time a new application flow starts Amy-OSPF picks a route through a series of OpenFlow Switches, and adds a flow-entry in each switch along the path. In her experiment, Amy decides to use Amy-OSPF for thetraffic entering the OpenFlow network from her own desktop PC— so she doesn’t disrupt the network for others. To do this, she defines one flow to be all the traffic entering the Open-Flow switch through the switch port her PC is connected to, and adds a flow-entry with the action “Enca psulate and forward all packets to a controller”. When her packets reach a controller, her new protocol chooses a route and adds a new flow-entry (for the application flow) to every switch along the chosen path. When subsequent packets arrive at a switch, they are processed quickly (and at line-rate) by the Flow Table. There are legitimate questions to ask about the performance, reliability and scalability of a controller that dynam ically adds and removes flows as an experiment progresses: Can such a centralized controller be fast enough to process new flows and program the Flow Switches? What happens when a controller fails? To some extent these questions were addressed in the context of the Ethane prototype, which used simple flow switches and a central controller [7]. Preliminary results suggested that an Ethane controller based on a low-cost desktop PC could process over 10,000 new flows per second —enough for a large college campus. Of course, the rate at which ne w flows can be processed will depend on the complexity of the processing required by the re searcher’s experiment. But it gives us confidence that mean ingful experiments can be run. Scalability and redundancy are possible by making acontroller (and the experiments) stateless, allowing simple load-balancing over multiple separate devices.3.1 Experiments in a Production NetworkChances are, Amy is testing her new protocol in a network used by lots of other people. We therefore want the network to have two additional properties:1 Packets belonging to users other than Amy should be routed using a standard and tested routing protocol running in the switch or router from a “name-brand” v endor.2 Amy should only be able to add flow entries for her traffic, or for any traffic her network administrator has allowed her to control.Property 1 is achieved by OpenFlow-enabled switches. In Amy’s experiment, the default action for all packets that don’t come from Amy’s PC could be to forward them through the normal processing pipeline. Amy’s own packets would be forwarded directly to the outgoing port, without being processed by the normal pipeline.Property 2 depends on the controller. The controller should be seen as a platform that enables researchers to implement various experiments, and the restrictions of Property 2 can be achieved with the appropriate use of permissions or other ways to limit the powers of individual researchers to control flow e ntries. The exact nature of these permission-like mechanisms will depend on how the controller is implemented. We expect that a variety of controllers will emerge. As an example of a concrete realization of a controller, some of the authors are working on a controller called NOX as a follow-on to the Ethane work [8]. A quite different controller might emerge by extending the GENI management software to OpenFlow networks.3.2 More ExamplesAs with any experimental platform, the set of experiments will exceed those we can think of up-front — most experiments in OpenFlow networks are yet to be thought of. Here, for illustration, we offer some examples of how OpenFlow-enabled networks could be used to experiment with new network applications and architectures.Example 1: Network Management and Access Con trol. We’ll use Ethane as our first example [7] as it was the research that inspired OpenFlow. In fact, an OpenFlow Switch can be thought of as a generalization of Ethane’s datapath switch. Ethane used a specific implementation of a controller, suited for network management and control, that manages the admittance and routing of flows. The basic idea of Ethane is to allow network managers to define a network-wide policy in the central controller, which is enforced directly by making admission control decisions for each new flow. A controller checks a new flow against a set of rules, such as “Guests can communicate using HTTP, but only via a web proxy” or “VoIP phones are not allowed to communicate with laptops.” A controller associates pack ets with their senders by managing all the bindings between names and addresses — it essentially takes over DNS, DHCP and authenticates all users when they join, keeping track of which switch port (or access point) they are connected to. One could envisage an extension to Ethane in which a policy dictates that particular flows are sent to a user’s process in a controller, hence allowing researcher-specific processing to be performed in the network.Example 2: VLANs. OpenFlow can easily provide users with their own isolated network, just as VLANs do. The simplest approach is to statically declare a set of flows which specify the ports accessible by traffic on a givenVLAN ID. Traffic identified as coming from a single user (for example, originating from specific switch ports or MAC addresses) is tagged by the switches (via an action) with the appropriate VLAN ID.A more dynamic approach might use a controller to manage authentication of users and use the knowledge of the users’ locations for tagging traffic at runtime.Example 3: Mobile wireless VOIP clients. For this example consider an experiment of a new call-handoff mechanism for WiFi-enabled phones. In the experiment VOIP clients establish a new connection over the OpenFlow-enabled network. A controller is implemented to track the location of clients, re-routing connections — by reprogramming the Flow Tables — as users move through the network, allowing seamless handoff from one access point to another.Example 4: A non-IP network. So far, our examples have assumed an IP network, but OpenFlow doesn’t require packets to be of any one format — so long as the Flow Table is able to match on the packet header. This would allow experiments using new naming, addressing and routing schemes. There are several ways an OpenFlow-enabled switch can support non-IP traffic. For example, flows could be identified using their Ethernet header (MAC src and dst addresses), a new EtherType value, or at the IP level, by a new IP Version number. More generally, we hope that future switches will allow a controller to create a generic mask (offset + value + mask), allowing packets to be processed in a researcher-specified way.Example 5: Processing packets rather than flows.The examples above are for experiments involving flows — where a controller makes decisions when the flow starts. There are, of course, interesting experiments to be performed that require every packet to be processed. For example, an intrusion detection system that inspects every packet, an explicit congestion control mechanism, or when modifying the contents of packets, such as when converting packets from one protocol format to another.Figure 3: Example of processing packets through anexternal line-rate packet-processing device, such as a programmable NetFPGA router.There are two basic ways to process packets in an OpenFlow-enabled network. First, and simplest, is to force all of a flow’s packets to pass t hrough a controller. To do this, a controller doesn’t add a new flow entry into the Flow Switch — it just allows the switch to default to forwarding every packet to a controller. This has the advantage of flexibility, at the cost of performance. It might provide a useful way to test the functionality of a new protocol, but is unlikely to be of much interest for deployment in a large network.The second way to process packets is to route them to a programmable switch that does packet processing — for example, a NetFPGA-based programmable router. The advantage is that the packets can be processed at line-rate in a user-definable way; Figure 3 shows an example of how this could be done, in which the OpenFlow-enabled switch operates essentially as a patch-panel to allow the packets to reach the NetFPGA. In some cases, the NetFPGA board (a PCI board that plugs into a Linux PC) might be placed in the wiring closet alongside the OpenFlow-enabled switch, or (more likely) in a laboratory.4. THE OPENFLOW CONSORTIUMThe OpenFlow Consortium aims to popularize OpenFlow and maintain the OpenFl ow Switch Specification. The Con sortium is a group of researchers and network administrators at universities and colleges who believe their research mission will be enhanced if OpenFlow-enabled switches are installed in their network.Membership is open and free for anyone at a school, college, university, or government agency worldwide. The OpenFlow Consortium welcomes individual members who are not employed by companies that manufacture or sell Ethernet switches, routers or wireless access points (because we want to keep the consortium free of vendor influence). To join, send email to***********************.The Consortium web-site contain s the OpenFlow Switch Specification, a list of consortium members, and reference implementations of OpenFlow switches.Licensing Model: The OpenFlow Switch Specification is free for all commercial and non-commercial use. (The exact wording is on the web-site.) Commercial switches and routers claiming to be “OpenFlow-enabled” must conform to the requirements of an OpenFlow Type 0 Switch, as defined in the OpenFlow Switch Specification. OpenFlow is a trademark of Stanford University, and will be protected on behalf of the Consortium.5. DEPLOYING OPENFLOW SWITCHESWe believe there is an interesting market opportunity for network equipment vendors to sell OpenFlow-enabled switches to the research community. Every building in thousands of colleges and universities contains wiring closets with Ethernet switches and routers, and with wireless access points spread across campus.We are actively working with several switch and router manufacturers who are adding the OpenFlow feature to their products by implementing a Flow Table in existing hardware; i.e. no hardware change is needed. The switches run the Secure Channel software on their existing processor.We have found network equipment vendors to be very open to the idea of adding the OpenFlow feature. Most vendors would like to support the research community without having to expose the internal workings of their products. We are deploying large OpenFlow networks in the Computer Science and Electrical Engineering departments at Stanford University. The networks in two buildings will be replaced by switches running OpenFlow. Eventually, all traffic will run over the OpenFlow network, with production traffic and experimental traffic being isolated on different VLANs under the control of。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
TOWARDS PROGRAMMABLE NETWORKSYechiam Yemini & Sushil da SilvaDepartment of Computer ScienceColumbia University{dasilva, yemini}@April 15, 1996AbstractIntermediate nodes (e.g., routers, switches) of current networks, in contrast with end nodes (e.g., PCs workstations), are vertically integrated closed systems. Their functions, mostly implemented by embedded software, are rigidly built-in by intermediate nodes vendors. Vendors must follow designs dictated by slow and intractable standard committees rather than pursue rapid introduction of innovative cost-effective technologies. There is thus a need for new technologies that would enable programming inter-mediate nodes with the same simplicity of programming end-nodes. This paper describes the NetScript project, pursuing agent-based middleware for programming functions of intermediate network nodes. Delegated agents are used to deploy functions in intermediate nodes. The NetScript programming lan-guage provides means to script processing of packet streams; it is particularly suitable to program routing, packet analyzers or signalling functions. This paper describes an architecture for programmable network nodes; middleware for agent-based programming of these nodes; the NetScript language to program node functions and applications of these technologies to create programmable SNMP agents, protocol analyz-ers, signalling and routing protocols and firewalls.1. INTRODUCTIONEnd nodes in a network--e.g., PC’s and workstations -- are organized as open systems whose functions can be programmed with ease. In contrast, intermediate nodes --e.g., routers and switches -- are closed vertically-integrated systems whose functions are determined through long and intractable standardization processes. These different paradigms have created an increasing gap between the functions and capabilities of end nodes in networks and those of intermediate nodes. For example, virtually every PC incorporates powerful multimedia capabilities. However, it may take a decade before the various standardization processes have been completed, imple-mented by vendors and deployed by end users to accomplish ubiquitous interactive multimedia networks. There is thus a need to reconsider the very paradigm of closed vertically-integrated intermediate nodes, underlying current networks.This paper provides a preliminary description of the NetScript project, for creating technologies to program intermediate network node functions. The idea underlying NetScript is simple. One should be able to deploy software in intermediate nodes dynamically with the same ease of launching an end-node application. This will enable software vendors to provide powerful soft-ware that programs intermediate nodes to support innovative applications. For example, a vendor of a multicast multimedia application could provide its users with applications software for end-nodes as well as routing software for intermediate nodes. End users will deploy and use this software in both end nodes as well as intermediate nodes with the same ease. Such programma-ble networks will enable and stimulate faster introduction of innovative network technologies and functions than is possible today. They will also eliminate the need for intractable standardi-zation, replacing committees with market forces in establishing standards.While this may seem, at first, a radical transition it is indeed a very natural evolutionary step. Already today intermediate nodes contain a large variety of software to support a growing range of protocols and functions. A typical router incorporates software to support over 20 different routing protocols. This growing featurization of elements has given rise to ever-complex con-figuration management. Configuration management has become, in effect, a form of program-ming intermediate node functions. Often this is sufficiently complex, with elements MIBs al-ready incorporating thousands of configuration variables, that one develops specialized scripting languages to program configuration choices. Thus the problem is not whether networks should be programmable, but what is the right paradigm to program them efficiently.The situation described above is not dissimilar from the evolution of printing some 15 years ago. With rapid improvements in printing technologies vendors increased featurization of printers. To enable users to take advantage of these features they developed corresponding configuration ca-pabilities. Applications vendors had to include scripts to manage these configurations options to create output to different printers. The introduction of Postscript enabled a simpler, universal and more efficient paradigm for programming printing engines. It enabled rapid development and introduction of more powerful, innovative and cost-efficient printing technologies. It enabled applications to be designed to take advantage of and program these features of printing e ngines.A central feature that distinguishes programmable engines from a configurable ones is the pro-gramming model used. A configurable engine focuses on establishing a maximal set of high-level features that can be activated as single atomic actions. In contrast, a programmable enginefocuses on identifying a minimal set of primitives from which one can compose an indefinite spectrum of high-level features. The NetScript project seeks to create a model for programma-ble, rather than merely configurable, intermediate network node engine.We use the term agent to describe a program that can be dynamically dispatched to and executed at a remote system. NetScript uses agents to program management and control the functions of intermediate nodes. A NetScript agent glues primitive node functions to processing packet streams and allocate node resources. NetScript agents can be programmed to handle both stan-dardized as well non-standardized protocols. Packet streams arriving at intermediate nodes are processed by the appropriate agents to accomplish the desired functionality of these protocols. For example, consider the provisioning of a private virtual network and processing of packet streams transported over this networks. NetScript agents can be dispatched to intermediate nodes to allocate resources to the virtual network and to configure its processing functions to handle routing and flow control of packet streams over this network. In what follows we overview the various technologies pursued by the NetScript project towards accomplishing such programma-ble networks. The NetScript project consists of three components: a architecture for program-ming networks in the large, an architecture of a dynamically programmable networked device, and a language called NetScript for building networked software on a programmable network. Section 2 describes the NetScript architecture; Section 3 presents a conceptual overview of the NetScript language; Section 4 outlines a few NetScript applications to network management and control; Section 5 describes related work. We conclude with an overview of challenges that must be overcome if networks are to become programmable.2. AN ARCHITECTURE FOR PROGRAMMABLE NETWORKSHow can one program a large scale multi-domain network to provide communication services used by a large number of end-nodes? How can this be accomplished in networks that contain a mix of programmable and non-programmable nodes? This section outlines the answers pursued by NetScript.NetScript views a network as a collection of Virtual Network Engines (VNE) interconnected by Virtual Links (VL). The VNEs can be programmed by NetScript agents to process packet streams and relay these streams over VLs to other VNEs. The collection of VNEs and VLs de-fines a NetScript Virtual Network (NVN). NetScript provides a language to program a NVN. NVN may correspond only loosely to the underlying physical network. A physical network node may be responsible to execute multiple VNEs, and a VL may correspond to a collection of physi-cal links and nodes that interconnect VNEs. Furthermore, a VL can interconnect any number of VNEs; this is particularly useful to handle broadcast links.Consider now the architecture of a VNE, depicted in the figure below. The Agent Services layer provides a portable multi-threaded execution environment to support delegation, execution and control of agent programs. It supports, additionally, message communication services among agents. The Agent Services layer uses the SMARTS Operations Server (SOS) implementation [1] of the management by delegation agents [2]. It provides a library that enables NetScript pro-grams to delegate, execute and control agents at VNEs.Figure 1: Architecture of a Programmable Virtual Network EngineThe NVN Connectivity Services module is responsible to interact with the underlying physical environment to allocate and maintain VLs to neighboring VNEs. It provides a library of primi-tives used by NetScript programs to control the allocation of VL resources, scheduling and transmission of packets over VLs. The NetScript interpreter provides a multi-threaded execution environment for NetScript agents. It maintains local libraries of agents and provides access to a distributed global directory of agents executing at different VNEs.A NetScript program can be viewed as a collection of threads, distributed at the VNEs and proc-essing packet streams moving through the NVN. For example, a routing protocol programmed in NetScript consists of agents, executing at multiple VNEs, whose task is to relay packet streams belonging to this protocol. Routing agents are responsible to analyze packet headers and forward them accordingly to other routing agents. They are also responsible to maintain routing tables at these VNEs. Similarly, a virtual network programmed in NetScript consists of agents that configure and maintain the virtual network topology and resources; agents to provide routing and flow control functions along the virtual links of this network; and agents that support sig-nalling protocols for this virtual network. A firewall programmed in NetScript consists of agents who filter NetScript packet streams and remove packets that fail to meet the filter criteria.How do NetScript programs communicate? Packets contain a minimal NetScript encapsulation header that basically identifies the stream to which they belong. When a packet arrives at a VNE this header is used by the run-time environment to pass it to the respective programs which proc-ess this stream. This communication model is essentially similar to Milner’s CCS semantic model. The communication model permits a single stream to be processed by multiple programs. These programs may perform global routing, collect stream statistics for management purposes, monitor a stream to detect intrusion attacks or filter packets. It is important to note that the NVN does not have built-in global routing functions. Communication services provided by the VNE are entirely local and permit interactions with neighboring VNEs only. Global routing is left to programmable protocols. The NetScript run-time environment provides a default globalrouting protocol. This protocol is used by VNEs to access various global services such as topol-ogy and agent directory services.How does NetScript interoperate with other network protocols and technologies? Two possible models are used to accomplish interoperability. First, one can overlay the NetScript Virtual Net-work on top of other network architectures. For example, a VL of NetScript may be implemented on top of IP links or tunnels, or use an ATM virtual circuit. A second possibility is to overlay an existing protocol stack as a NetScript program. For example a NetScript program may implement IP routers in VNEs. IP packets will be encapsulated in NetScript header and routed by this pro-gram to neighboring VNEs, where they are processed again by the IP routers.How are NetScript programs deployed and executed in the NVN? This is accomplished through the use of the Agent Services layer. NetScript agents can be dispatched from any VNE to any other VNEs. The source VNE uses the local Agent Services layer to delegate and execute agents at remote VNEs. The default global routing program is used to support these agent serv-ices.3. THE NETSCRIPT LANGUAGEThis section presents a high-level overview of the NetScript language. Our goal here is to de-scribe the computational model and guiding design principles behind NetScript, not to provide a detailed description of the language; the NetScript Language Manual [3] gives such a description. NetScript is a small and simple dataflow language designed specifically for communications-based tasks. In particular, NetScript programs operate on streams of packets. The language pro-vides a set of standard primitives that simplify the construction of stream-based computations. These primitives include operations on messages -- parse, flatten, split, join -- and operations on streams of messages -- multiplex, demultiplex, etc. NetScript is based on simple object-oriented principles, so programmers can override the default operators with customized versions of their own.A NetScript program consists of a pool of communicating threads. These threads communicate through message streams that connect inputs to outputs of executing programs. Communicating NetScript programs need not reside on a single VNE; they can be geographically distributed on VNEs across a network. NetScript utilizes the services of a Virtual Link (VL) to provide stream communication between distributed NetScript programs. It is important to note that a program that runs on a VNE need not be written completely in NetScript. Resident programs, especially common-path, low-level protocols and drivers, can be written in any convenient programming language (e.g. C, C++). One can think of NetScript as the "glue" that ties together computations on a VNE.Figure 2 below shows a typical VNE configuration. Here a NetScript implementation of a hypo-thetical Multimedia Multicasting Protocol (MM) communicates with a UDP protocol through a pair of streams. The arrival of messages from the network successively activates the Ethernet, IP, UDP, and MM modules.Figure 2: Typical VNE ConfigurationWe now illustrate how one would use NetScript to deploy a new protocol across a network. We use the Multimedia Multicasting Protocol (MM) from Figure 2 as a guiding example. MM pro-vides multicasting services, jitter control and video synchronization for multi-conferencing appli-cations on an internetwork. MM must run on both the intermediate nodes (the routers) and the end nodes of the network. At the intermediate nodes, MM maintains multicast routing trees, and aids in jitter-control; at the end nodes, MM lets users enter and leave multi-conferencing ses-sions, and provides video data streams. A software vendor could code the intermediate and end node components of MM in NetScript and bundle both with a multi-conferencing application. When a user launches the application, the application first attempts to dispatch and execute MM on the intermediate nodes of the network if it has not been loaded already. To do this, NetScript utilizes the NVN Connectivity Services to identify intermediate routers in the network, and the SOS Agents Services Layer to dispatch intermediate node MM agents to the routers. To start the end-node version of MM, the application communicates with the VNE on local machine, loads the end-node version of MM at the VNE, builds stream connections with the VNE, and begins communicating. Both the local and intermediate versions of MM operate by making VL connec-tions to local resources (e.g. UDP) and to remote resources (e.g. MM instances on other interme-diate nodes).Three features distinguish NetScript. First, NetScript provides a universal abstraction of a pro-grammable networking device; second, NetScript is a dynamic language; and third, NetScript is a dataflow language.NetScript provides a universal abstraction of a programmable networking device. Universality means that a NetScript program will execute on any VNE without regard for the current state or configuration (e.g. executing programs, connected devices) of that engine. NetScript constructs, along with services provided by the VNE, hide the heterogeneity of networking devices behind simple abstractions. In analogy, PostScript provides an abstraction of a universal, programmable printing device.NetScript is a dynamic language. This means that programs or devices can be added to or re-moved from a VNE on-the-fly, at runtime, without disturbing the execution of existing protocols. The language utilizes SOS Agent Services to dynamically execute and control NetScript agents that arrive from the network. It is also worth noting that the programmer need not explicitly con-nect NetScript programs together on a target VNE. Instead the program is simply delegated to a remote engine. When NetScript program arrives at a VNE for execution, the environment auto-matically configures the program and connects the program to other executing programs based on the type signature of that program. This automatic configuration is important because internal state can differ radically from one VNE to another. If a program depends for its execution on other programs or protocols (e.g. IP) that do not currently reside on a given engine, the program simply remains dormant until the dependent programs arrive from the network. Auto-configuration saves the programmer from writing complex, tedious and error-prone scaffolding code to ensure that a program will execute on all VNEs.NetScript’s computational model is based on dataflow. This model is sufficiently different from the conventional control-flow model of computing that it deserves elaboration. In a dataflow model, a computation is organized as a set of concurrent, communicating processes where the flow of data within the system drives the computation in each process. A dataflow computation is nicely described by a graph (see figure), where the nodes represent computational elements and the edges represent communication paths. Essentially, the arrival of data at the inputs of a pro-gram determines which part of the graph is computing, and which is not. This is in contrast with the traditional computer model which focuses on a single sequence of instructions (or statements) in a program. The control in a program determines the single execution path through the instruc-tion sequence.A dataflow model is particularly appropriate for network-based applications because network traffic is essentially asynchronous. Message streams arrive asynchronously from both the net-work and user programs; the arrival of a message triggers a computation in a NetScript program; the type of a message (its header) determines its path through a graph of connected NetScript programs. Another advantage of dataflow is that it greatly simplifies the construction of concur-rent programs. Coordinating and synchronizing multiple concurrent activities is often the most difficult part of building networked systems. Dataflow programs, however, do not require ex-plicit and complex synchronization mechanisms (e.g. mutex locks, semaphores) because such programs communicate solely through well-defined formal interfaces. This is particularly im-portant for NetScript programs, which will run on remote VNEs under a variety of hardware and software configurations, and therefore must make minimal assumptions about the host environ-ment.4. NETWORK MANAGEMENT APPLICATIONSThis section outlines some Network Management applications and shows how one could use NetScript to easily program these applications on a network. We describe a Remote Network Monitor, an SNMP Agent, and an ATM Signalling Protocol. Although we focus on Network Management applications here, NetScript could be used for other kinds of protocols also.4.1 REMOTE NETWORK MONITORA Remote Network Monitor allows an organization to watch the performance and health of a network and protocols from a remote location such as a workstation. Ideally, to get a reasonable view of the overall behavior of network, one would want to probe the network at strategic loca-tions within the network. These include both the intermediate nodes (switches, routers) and the end nodes (workstations, PCs). Information from the probes could be gathered in real-time at a workstation application to provide a system administrator with a comprehensive, dynamic view of her network. As we have discussed, the current network architecture does not permit easy pro-gramming of internal nodes. One could RMON MIBs to monitor the network, but RMON sup-ports only a rigid set of operations, and requires that filters be written with low-level bit manipu-lations. Additionally, the polling model in SNMP makes real-time monitoring of a large network impractical. Alternatively, one can dispatch NetScript monitoring agents throughout a program-mable network. These monitoring agents are essentially high-level filters that watch and instru-ment packet streams in real-time at VNEs. Each filter performs header classification of one or more streams, maintains counters in internal state variables, and uses a VL to report results back to the administrator’s monitoring application and display.4.2 SNMP AGENTS IN NETSCRIPTAlthough NetScript opens up new possibilities for private network management protocols, Net-Script can interoperate with, even implement existing standards like SNMP. This is of special importance when a NetScript VNE resides on a network managed by existing non-programmable infrastructure. Here we show how NetScript enables the construction of SNMP agents.An SNMP agent typically consists of three components. One component is a back-end that maintains the consistency of MIB data structures. The second performs MIB instrumentation. This component consists of various routines to collect and maintain MIB variables such as traffic counters. The final component is a front-end to SNMP. This component parses incoming SNMP requests, interacts with the MIB back-end, and generates SNMP replies or traps. NetScript could be used to implement all three components. The NetScript implementation of the MIB back-end would consist of NetScript programs that provide atomic access to MIB variables. To perform instrumentation, NetScript stream analysis programs can report and manipulate MIB status vari-ables. A NetScript front-end would consist of programs that parse SNMP request packets and call an appropriate back-end program to get or set a MIB variable.4.3 ATM SIGNALLING PROTOCOLThe term ATM Signalling refers to the connection setup phase in an ATM network. ATM net-works use a signaling protocol to open and close virtual circuits on an ATM network. To do this, a the switching protocol must negotiate circuit setup with all intermediate switches in a path from source to destination in a virtual circuit. Typically, this involves sending signalling cells between switches. The emerging standard for ATM signalling (Q.2931) is a comprehensive, scaleable signalling protocol for large networks. Because current ATM switches are constructed as closed, vertically integrated black-boxes it is not currently possible for customers to deploy small subsets of the standard or even private signalling protocols. Nor is it possible for vendors to incremen-tally upgrade installed control software as the relevant standards emerge and evolve. One possi-bility is to make an ATM network programmable by embedding a VNE in the vendor switches, adaptation cards, and host software. NetScript agents installed at the switches would maintain switching tables that map virtual circuits to input and output ports. These agents parse, interpret, and forward incoming private or standard signalling cells set up and tear down circuits in the network.5. RELATED WORKNetScript shares similar goals with the Active Networks [4] initiative at MIT and the Switch-Ware [5] effort at the University of Pennsylvania and Bellcore. Like NetScript, these projects seek to make the network programmable. The Active Network extends the concept of a packet from a passive data object to one that might contain a fully-functional active program. This ap-proach is not incompatible with that of NetScript. Indeed, mobile NetScript programs are encap-sulated in conventional protocol messages, for example IP. The SoftSwitch project is attempting to build a programmable switch. They intend to explore security operating system issues among others.The central difference between our work and Active Net or SoftSwitch is our focus on the pro-grammability of networks. NetScript uses a single, universal language, specifically designed for protocol implementation in a programmable network; the Active Network project currently uses Safe-Tcl [6] while SoftSwitch uses Java [7]. We believe that a single language based on the right model can greatly simplify protocol construction, can be more effectively optimized for efficient performance, is easier to secure, and will allow us maximum flexibility in experimenting with appropriate programming features.Another difference is that NetScript treats the network as a single programmable abstraction (the NVN) rather than an heterogeneous collection of programmable routers, switches and end-nodes. We believe that this approach will enable programming of massive Internet-sized ne tworks. Java and Telescript [8] are programming languages also intended for networked applications. Java is targeted as a language for programming user-interface functionality in Web browsers. TeleScript is an agent-based language for Internet commerce. Both languages provide abstrac-tions to support their respective domains. NetScript’s abstractions are designed specifically for dynamic implementation of protocols in a programmable network.6. CONCLUSIONSThis paper provides a preliminary overview of the NetScript project. Several challenges exist if networks are to become programmable:1. How to organize a network to support programmability of node functions while assuringinteroperability with a variety of nodes and protocol stacks of current networks and ena-bling scalability for large networks. The NetScript project is pursuing a virtual network ar-chitecture that provide effective answers to this challenge.2. How to facilitate effective dynamic distribution and execution of software to programnetwork nodes. The NetScript project is building on the delegated agent technology intro-duced in [2],[1] to address this challenge.3. How to create a simple and effective paradigm to program packet stream processing innetwork nodes. The NetScript language has developed a dataflow programming model that addresses this challenge.Several additional challenges, not addressed in this paper, are investigated by the project.1. How to assure that node programs are efficient to handle fast real-time performance re-quirements.2. How to ensure the security of programmable nodes against unauthorized access. Success of this research would mean that we have established effective mechanisms to program intermediate network nodes with the same ease and efficiency available for programming end nodes. Success would mean that intermediate node functions can be programmed and deployed through simple, open and rapid processes that do not require standard committees or vendors re-sources. Success would mean that NetScript programs can be generated and deployed in interme-diate node engines to control and manage their functions with the same simplicity as Postscript programs are applied in printing engines.7. REFERENCES[1] SMARTS, SMARTS Operational Server Manual, . 1994, System Management Arts.[2] Yemini, Y., G. Goldszmidt, and S. Yemini. Network Management by Delegation. in The Sec-ond International Symposium on International Network Management. 1991. Washington DC.[3] daSilva, S. and Y. Yemini, NetScript Language Tutorial and Reference, . 1996, Columbia University Computer Science Department: New York.[4] Tennenhouse, D.L. and D.J. Wetherall, Towards Active Networks, . 1996, MIT Laboratory for Computer Science.[5] Smith, J.M., et al., SwitchWare: Accellerating Network Evolution (White Paper), . 1996, University of Pennsylvania Computer Science Department.[6] Borenstein, N. Email with a Mind of its Own: The Safe-Tcl Language for Enabled Mail. in IFIP International Conference. 1994. Barcelona, Spain.[7] Gosling, J. and H. McGilton, The Java Language Environment: A White Paper, . 1995, Sun Microsystems.[8] White, J.E., Telescript Technology: The Foundation for the Electronic Marketplace, . 1994, General Magic.11。
