CCNA基础测试题及答案
CCNA基础知识考题汇总

CCNA基础知识考题汇总1、OSI模型包括哪7层?答:从上到下分别为:应用层、表示层、会话层、传输层、网络层、数据链路层、物理层2、TCP/IP模型包括哪4层?答:从上到下分别为:过程/应用层、主机到主机层、因特网层、网络接入层3、思科组网模型包括哪3层?答:核心层、汇聚层、接入层4、TCP与UDP有何区别?答:1.TCP是基于全双工的、面向连接的、可靠传输协议,而UDP是无连接、不可靠传输协议。
2、TCP采用的是虚电路方式,而UDP不采用虚电路。
3、TCP的数据段格式与UDP的数据段格式不一样4、TCP含有窗口流量控制,而UDP没有5、TCP如何实现传输的可靠性?答:建立起虚电路连接的“三次握手”原则这是由于TCP的数据段格式而决定了TCP能进行面向连接的可靠传输。
6、DHCP服务提供了哪些内容?答:IP地址、子网掩码、域名、默认网关、DNS、WINS信息Windows查看本机ARP信息的命令是什么?答:arp-a7、Windows跟踪路径的命令是什么?答:Traceroute8、Windows长ping并改变包大小的命令是什么?答:ping -l size +ip地址.9、Windows查看本机路由表的命令是什么?答:show ip route10、IP地址分成哪两个部分?答:ip地址分成主机地址和网络地址11、如何快速计算某个IP所在的网络地址及广播地址?答:划分子网就需要计算子网掩码和分配相应的主机块,采用十进制计算方法。
12、VLSM及CIDR的全称是什么?答:VLSM是变长子网掩码;CIDR是无类的内部域路由13、WWW、FTP、DNS、Telnet、POP3、SMTP、远程桌面这些应用分别使用的TCP/UDP的哪些端口?答: www端口:80、 ftp端口:21 dns端口:53telnet端口:23 pop3端口:110 smtp端口:25windows终端(远程桌面)端口:338914、电脑对路由器交换机输入配置命令的途径有哪两种?15、笔记本电脑上没有COM端口时如何连接路由器交换机的console口?答:用一个USB转换com端口器16、路由器模拟成PC需要哪些配置?答:router(config)#no ip routingrouter(config)#ip default-gateway *.*.*.*router(config)#int f*/*router(config-if)#ip address *.*.*.*. (子网掩码)*.*.*.*router(confi-if)#no shutdown17、静态路由有哪两种写法?答:1、router(config)#ip route (目的地址)*.*.*.* (子网掩码)*.*.*.* (下一跳地址)*.*.*.*2、Router(config)#ip route(目的地址)*.*.*.* (子网掩码)*.*.*.* (本路由器的外出接口)f*/*18、如何配置/32的主机静态路由?19、静态路由、RIP、EIGRP、OSPF的默认管理距离是多少?答:静态路由的ad是1 rip的ad是120 eigrp的ad是90 ospf的ad是11020、默认路由和静态路由并存时,如何选路?答:静态21、静态路由配置后,进入路由表的条件是什么?答:1、接口存在,并且是激活的;2、下一跳可达22、PC-R1-R2-R3-Server,为了让PC访问Server,3台路由器最少共需要配置几条静态路由?答:至少4条静态路由23、静态路由如何修改管理距离?答:ip route 目地ip地址子网掩码下一跳地址/本地出接口后直接加要修改的AD号(0-255)24、RIP、EIGRP、OSPF的全称分别是什么?答:路由信息协议、增强内部网关路由协议、开放最短路径优先25、RIP协议属于哪种类型的路由协议,这种类型的路由协议有何特点?答:属于动态路由协议;其特点是能较好地适应网络状态的变化,但实现起来较为复杂,开销也比较大。
CCN认证试题中文答案

C C N A认证试题一(附答案和解析)中文版(一)1、目前,我国应用最为广泛的LAN标准是基于()的以太网标准.(A) IEEE 802.1(B) IEEE 802.2(C) IEEE 802.3(D) IEEE 802.5答案:C参考知识点:现有标准:IEEE 802.1 局域网协议高层IEEE 802.2 逻辑链路控制IEEE 802.3 以太网IEEE 802.4 令牌总线IEEE 802.5 令牌环IEEE 802.8 FDDIIEEE 802.11 无线局域网记住IEEE802.1-------IEEE802.5的定义以太网是一种计算机局域网组网技术。
IEEE制定的IEEE 802.3标准给出了以太网的技术标准。
它规定了包括物理层的连线、电信号和介质访问层协议的内容。
以太网是当前应用最普遍的局域网技术。
它很大程度上取代了其他局域网标准,如令牌环、FDDI和ARCNET。
以太网的标准拓扑结构为总线型拓扑,但目前的快速以太网(100BASE-T、1000BASE-T标准)为了最大程度的减少冲突,最大程度的提高网络速度和使用效率,使用交换机(Switch)来进行网络连接和组织,这样,以太网的拓扑结构就成了星型,但在逻辑上,以太网仍然使用总线型拓扑的C***A/CD介质访问控制方法。
电气电子工程师协会或IEEE(Institute of Electrical and Electronics Engineers)是一个国际性的电子技术与信息科学工程师的协会。
建会于1963年1月1日。
总部在美国纽约市。
在150多个国家中它拥有300多个地方分会。
目前会员数是36万。
专业上它有35个专业学会和两个联合会。
IEEE发表多种杂志,学报,书籍和每年组织300多次专业会议。
IEEE定义的标准在工业界有极大的影响。
下面列出:IEEE802.3以太网标准802.3--------- 10Base以太网标准802.3u-------- 100Base-T(快速以太网)802.3z-------- 1000Base-X(光纤吉比特以太网)802.3ab-------- 1000Base-T(双绞线吉比特以太网)答案:CE注:IP地址中关键是看她的主机位,将子网掩码划为二进制,1对应上3、Quidway系列路由器在执行数据包转发时,下列哪些项没有发生变化(假定没有使用地址转换技术)?()(A) 源端口号(B) 目的端口号(C) 源网络地址(D) 目的网络地址(E) 源MAC地址(F) 目的MAC地址答案:ABCD参考知识点:路由功能就是指选择一条从源网络到目的网络的路径,并进行数据包的转发。
CCNA—网络基础知识—C卷

xxxxxx 学院2014—2015学年第一学期《CCNA 认证—网络基础篇》 主考: C 卷网络D132\网络D141班院部:运输管理学院 专业(班级) 姓名 学号一、选择题(每题1分,共10分)( )1、交换机使用哪种协议做出选择性转发决定 A .源IP B .目的IP C .源MAC D .目的MAC ( )2、下列关于IP 网络地址的陈述,哪一项是正确的? A .所有主机位均设置为0 B .所有主机位均设置为1 C .分配了地址范围内的最大地址 D .所有网络为均设置为1( )3、哪种网络为客户提供对企业数据(如库存、部件列表订单)的有限访问? A .内部网B .外联网C .国际网D .Internet ( )4、OSI第二层采用哪种编制方式? A .逻辑 B .物理 C .MAC D .IP E .端口 ( )5、哪一种是最常用的网络层服务? A .HTTP B .FTP C .Telnet D .E-mail( )6、网络管理员正在建立包含22台主机的小型网络。
ISP 只分配了可路由的IP 地址。
网络员可以使用以下哪个地址快? A .10.11.12.16/28 B .172.31.255.128/27 C .192.168.1.0/28 D .209.165.202.128/27( )7、如果节点接受了帧并计算了CRC ,但与FCS 中的CRC 不匹配,该节点将如何做?A .丢弃帧B .从CRC 中重建帧 C .将帧转发到下一节点D .关闭帧到达的接口( )8、 UTP 电缆通过哪个过程可以避免串扰?A .电缆屏蔽B .线对双绞C .端点接口D .电缆中的覆层 ( )9、以太网MAC 地址有多少位? A .12 B .32 C .48 D .256( )10、路由器使用什么为数据包选择最佳路径? A .ARP 表 B .桥接表 C .路由表 D .交换表( )11、什么决定了TCP/IP 的发送站可以发送多少数据才会收到确认? A .数据段大小 B .传输速率 C .带宽 D .窗口大小( )12、在主要使用文本相互通信的两个人或多个人之间,他们使用的哪种通信形式属于基于文本的事实通信?A .网络日志B .维基C .即时消息D .博客 ( )13、OSI第二层采用哪种编制方式? A .逻辑 B .物理 C .MAC D .IPE .端口 ( )14、应用层是OSI 模型的第几层? A .第一 B .第三 C .第四 D .第七 ( )15、DHCP 能为网络上的客户端坐什么? A .有不受限的电话会话 B .播放视频流 C .获得IP 地址 D .跟踪间歇性的拒绝服务攻击 ( )16、TCP/UDP 端口号的用处?A .表明三次握手的开始B .重组数据段到正确的顺序C .标志发送者没有确认的情况可以发送的数据包的数量D .跟踪同时通过网络的不同的会话 ( )16、帧的数据字段内容是什么?A .64字节B .网络层PDUC .第二层源地址D .从应用层直接产生的数据 ( )17、有关网络的逻辑拓扑下面哪项是正确的?A .都是多路访问B .提供物理编制C .确定网络中节点如何连接D .影响网络中使用的MAC 类型---------------------------------------------------装 ---------------------------------订-----------------------------线----------------------------------------------( )18、在CSMA/CD中拥塞信号的目的是什么?A.允许介质恢复 B.确保所有节点看到冲突C.向其他节点通报这个节点将要发送 D.标识帧的长度( )19、如果需要尽可能多的子网同时每个子网32台主机,应使用哪个子网?A.255.255.255.240 B.255.255.255.0 C.255.255.255.224 D.255.255.255.192 ( )20、下列哪个帧字段由源节点创建并由目的节点用于确保传输的数据信号未因干扰、失真或信号丢失而产生更改?A.传输层差错校验字段 B.帧校验序列字段C.用户数据协议字段 D.纠错过程字段( )21、路由器在确定路劲时使用网络层地址的哪个部分?A.多播 B.多路复用 C.封装 D.多访问( )22、Linux的UNIX操作系统使用SAMBA,协议的版本是?A.SMB B.HTTP C.FTP D.SMTP( )23、在传输层,哪种流量控制能使发送主机保持接受主机避免冲突过载?A.尽力传输 B.封装 C.流控 D.拥塞避免( )24、终端系统使用端口号选择适当的应用程序。
CCNA认证基础试卷A-参考答案
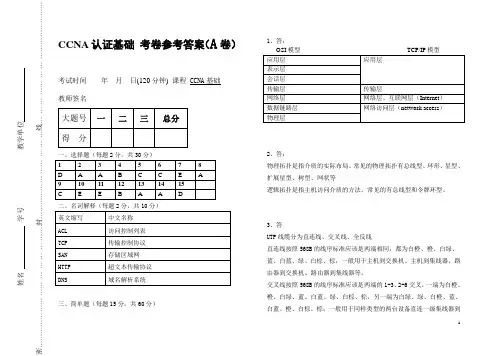
1 CCNA认证基础考卷参考答案(A卷)考试时间年月日(120分钟) 课程CCNA基础教师签名_____一、选择题(每题2分,共30分)二、名词解释(每题2分,共10分)三、简单题(每题15分,共60分)1、答:2、答:物理拓扑是指介质的实际布局。
常见的物理拓扑有总线型、环形、星型、扩展星型、树型、网状等逻辑拓扑是指主机访问介质的方法。
常见的有总线型和令牌环型。
3、答UTP线缆分为直连线、交叉线、全反线直连线按照568B的线序标准应该是两端相同,都为白橙、橙、白绿、蓝、白蓝、绿、白棕、棕,一般用于主机到交换机、主机到集线器、路由器到交换机、路由器到集线器等。
交叉线按照568B的线序标准应该是两端的1-3、2-6交叉,一端为白橙、橙、白绿、蓝、白蓝、绿、白棕、棕,另一端为白绿、绿、白橙、蓝、白蓝、橙、白棕、棕;一般用于同样类型的两台设备直连一级集线器到交换机,主机到路由器的连接。
全反线的线序为两端线序完全相反,一端为白橙、橙、白绿、蓝、白蓝、绿、白棕、棕,另一端则线序全部相反,为棕、白棕、绿、白蓝、蓝、白绿、橙、白橙。
全反线只用于计算机的串口与网络设备的控制台端口连接。
4、答:相同点:1)路由器和第3层交换机都是第3层的设备2)路由器和第3层交换机都具有路由功能3)路由器和第3层交换机都能够提供子网(或VLAN)间的通信4)路由器和第3层交换机都主要用于主干网上不同点:1)接口工作层次:路由器的接口只工作在第3层(路由接口)上,第3层交换机的接口可独自工作在第2层(交换接口)或第3层(路由接口)上。
2)软硬件实现:路由器是基于软件的路由设备,第3层交换机是硬件化的路由设备3)转发性能:路由器实现高转发性能的代价远高于第3层交换机4)接口类型:路由器的接口类型远丰富于第3层交换机5)路由能力:路由器的路由能力强大,第3层交换机的路由能力只需满足一般需要即可。
(路由协议、转发机制)6)应用场合:广域主干网中一般使用路由器,园区主干网中通常使用第3层交换机一、填空(每空2分,共20分)1如图所示,路由器A和B已经配置使用RIP作为动态路由协议,且路由器A和B上的所有接口都报告“interface is up, line protocol is up”。
完整版CCNA测试题库及答案

完整版CCNA测试题库及答案描述载波侦听多路由访问/冲突检测(CSMA/CD)的工作原理。
CSMA/CD是一种帮助设备均衡共享带宽的协议,可避免两台设备同时在网络介质上传输数据。
虽然他不能消除冲突,但有助于极大的减少冲突,进而避免重传,从而提高所的设备的数据传输效率。
区分半双工和全双工通信。
并指出两种方法的需求。
与半双工以太网使用一对导线不同,全双工以太网使用两队导线,全双工使用不同的导线来消除冲突,从而允许同时发送和接收数据,而半双工可接收或发送数据,但不能同时接收和发送数据,且仍会出现冲突。
要使用全双工,电缆两端的设备都必须支持全双工,并配置成一全双模式运行。
描述MAC地址的组成部分以及各部分包含的信息。
MAC(硬件)地址时一种使用十六进制表示的地址,长48位(6B)。
其中前24位(3B)称为OUI(Organizationally Unique Idebtifier,组织唯一表示符),有IEEE分配给NIC制造商;余下的部分呢唯一地标识了NIC识别十进制数对应的二进制值和十六进制值。
用这三种格式之一表示的任何数字都可以转换为其他两种格式,能够执行这种转换对理解IP地址和子网划分至关重要。
识别以太网帧中与数据链路层相关的字段。
在以太网中,与数据链路层相关的字段包括前导码,帧其实位置分隔符,目标MAC地址,源MAC地址,长度或者类型以及帧校验序列。
识别以太网布线相关的IEEE标准。
这些标准描述了各种电缆类型的功能和物理特征,包括(但不限于)10Base2、10Base5和10BaseT。
区分以太网电缆类型及其用途。
以太网电缆分3种:直通电缆,用于将PC或路由器的以太网接口连接到集线器或交换机;交叉电缆。
用于将集线器连接到集线器,集线器连接到交换机,交换机连接到交换机以及PC连接到PC;反转电缆,用于PC和路由器或交换机之间建立控制台连接。
描述数据封装过程及其在分组创建中的作用。
数据封装指的是在OSI模型各层给数据添加信息的过程,也成为分组创建。
思科CCNA学习试题答案

思科CCNA学习试题答案CCNA课程测试一、单项选择题:1、介质100BaeT的最大传输距离是:()A:10mB:100mC:1000mD:500m2、路由器下,由一般用户模式进入特权用户模式的命令是:()A:enableB:configC:interfaceD:router3、哪个命令可以成功测试网络:()A:Router>ping192.5.5.0B:Router#ping192.5.5.30C:Router>ping192.5.5.256D:Router#ping192.5.5.2554、介质工作在OSI 的哪一层()A:物理层B:数据链路层C:网络层D:传输层5、100baeT的速率是()Mbit/A:1B:10C:100D:10006、在启用IGRP协议时,所需要的参数是:()A:网络掩码B:子网号C:自治系统号D:跳数7、基本IP访问权限表的表号范围是:()A:1—100B:1-99C:100-199D:800-8998、查看路由表的命令是:()A:howinterfaceB:howrunC:howiprouteD:howtable9、工作在OSI第三层的设备是:()A:网卡B:路由器C:交换机D:集线器10、OSI第二层数据封装完成后的名称是:()A:比特B:包C:帧D:段11、为了禁止网络210.93.105.0ftp到网络223.8.151.0,允许其他信息传输,则能实现该功能的选项是:()A:acce-lit1deny210.93.105.0.0.0.0.0.0B:acce-lit100denytcp210.93.105.00.0.0.255223.8.151.00.0.0.255eqftpC:acce-lit100permitipanyanyD:acce-lit100denytcp210.93.105.00.0.0.255223.8.151.00.0.0.255eqftpacce-lit100permitipanyany12、路由器下“特权用户模式”的标识符是:()A:>B:!C:#D:(config-if)#13、把指定端口添加到VLAN的命令是:() A:vlanB:vlan-memberhipC:vtpD:witchport14、交换机工作在OSI七层模型的哪一层()A:物理层B:数据链路层C:网络层D:传输层15、在OSI七层模型中,介质工作在哪一层()A:传输层B:会话层C:物理层D:应用层16、交换机转发数据到目的地依靠()A:路由表B:MAC地址表C:访问权限表D:静态列表17、为了使配置私有IP的设备能够访问互联网,应采用的技术是()?A:NATB:VLANC:ACCESS-LISTD:DDR18、VLAN主干协议VTP的默认工作模式是()A:服务器模式B:客户端模式C:透明模式D:以上三者都不是19、路由器的配置文件tartup-config存放在()里A:RAMB:ROMC:FLASHD:NVRAM20、配置路由器特权用户“加密密码”的命令是:()A:pawordB:enablepawordC:enableecretD:pawd21、某网络中,拟设计10子网,每个子网中放有14台设备,用IP地址段为199.41.10.某,请问符合此种规划的子网掩码是()A:255.255.255.0B:255.255.240.0C:255.255.255.240D:255.248.0.022、在路由表中到达同一网络的路由有:静态路由、RIP路由、IGRP路由,OSPF路由,则路由器会选用哪条路由传输数据:()A:静态路由B:RIP路由C:IGRP路由D:OSPF路由23、扩展IP访问权限表的表号范围是:()A:1—100B:1-99C:100-199D:800-89924、把访问权限表应用到路由器端口的命令是:()A:permitacce-lit101outB:ipacce-group101outC:applyacce-lit101outD:acce-cla101out25、混合型协议既具有“距离矢量路由协议”的特性,又具有“链路状态路由协议”的特性,下列协议中属于混合型协议的是:()A:RIPB:OSPFC:EIGRPD:IGRP26、在路由器上,命令howacce-lit的功能是():A:显示访问控制列表内容B:显示路由表内容C:显示端口配置信息D:显示活动配置文件27、RIP路由协议认为“网络不可到达”的跳数是:()A:8B:16C:24D:10028、查看E0端口配置信息的命令是:()A:howacce-litB:howiprouteC:howverionD:howinterfacee029、配置路由器时,封装PPP协议的命令是:()A:encappppB:pppC:grouppppD:intppp30、路由器上“水平分割”的功能是:()A:分离端口B:阻止路由环路C:简化配置D:方便故障处理31、OSI七层模型中,“包”是哪一层数据封装的名称()A:物理层B:数据链路层C:网络层D:传输层32、OSI七层模型中,“段”是哪一层数据封装的名称()A:物理层B:数据链路层C:网络层D:传输层33、备份路由器IOS的命令是:()A:copyflahtftpB:copyrunning-configtftpC:copyIOStftpD:copytartup-configtftp34、PPP工作在OSI的哪一层()A:物理层B:数据链路层C:网络层D:传输层35、FTP工作在OSI哪一层()A:会话层B:表示层C:传输层D:应用层36、TELNET工作在OSI哪一层()A:会话层B:表示层C:传输层D:应用层37、SMTP工作在OSI哪一层()A:会话层B:表示层C:传输层D:应用层38、IP地址为:192.168.50.70,掩码为:255.255.255.248,则该IP地址所在子网的子网号为()A:192.168.50.32B:192.168.80.64C:192.168.50.96D:192.168.50.7139、IP地址为:192.168.50.70,掩码为:255.255.255.248,则该IP地址所在子网的广播地址为()A:192.168.50.32B:192.168.80.64C:192.168.50.96D:192.168.50.7140、IP地址为:192.168.50.70,掩码为:255.255.255.248,则该A:createB:interfaceC:encapulationD:ipaddre75、路由器上,命令“howint0”的显示结果为:Serial0iup,lineprotocolidown出现该结果的可能原因是()A:端口处于关闭状态B:物理端口被烧毁C:两端设备协议不一致D:路由表中无路由76、如果把路由器的某个端口的IP配置为:192.168.10.64,掩码配置为:255.255.255.248,则该端口()A:能和其他设备正常通信B:会变成“adminitrativelydown”状态C:端口被烧毁D:出现错误提示,配置命令执行失败77、网关的功能()A:过滤数据包B:不同网段通信C:校验数据帧D:把数据封装成“段”78、能够分配给设备的IP,应该是()A:网络有效IPB:网络号C:网络广播地址D:任意IP79、路由器“全局模式”的提示符为()A:>B:#C:(config)#D:(config-router)#80、路由器当前的模式为“端口模式”,要退回到“特权模式”,应该使用的快捷键为()A:ctrl+bB:ctrl+zC:ctrl+cD:ctrl+p81、下列命令中,无法正确执行的是()A:Router(config)#howrunB:Router#ping127.0.0.1C:Router(config)#hotn amecicoD:Router#reload82、路由器上,设置端口速率的命令是()A:clockrateB:bandwidthC:etD:encap83、路由器上,清空路由表的命令是()A:clearipB:deleteiprouteC:deleterouteD:cleariproute某84、路由表中,某条路由的“路由代码为D”,则表明该路由为()A:直连路由B:静态路由C:IGRP路由D:EIGRP路由85、两台路由器直连到一起,应该使用的线缆为()A:交叉线缆B:直通线缆C:反转线缆D:任意线缆86、通过路由器的“配置端口conole”对路由器进行配置,应该使用的线缆为()A:交叉线缆B:直通线缆C:反转线缆D:任意线缆87、下面对Cico2621路由器和Cico2501路由器描述中,错误的是()A:Cico2621路由器的可扩展性优于Cico2501路由器B:Cico2621是模块化路由器C:Cico2501上提供一个100Mbit/的快速以太网端口D:Cico2501是固定端口的路由器88、为了连接“帧中继”线路,网络中的路由器需要提供的端口类型为()A:FatEthernetB:SerialC:BRID:Ethernet89、路由器“特权模式”的提示符是:()A:>B:#C:(config)#D:(config-if)#90、下列关于路由器和交换机的描述中,错误的是()A:路由器可以用来连接internet B:二层交换机可以用来实现“异地网络”互连C:路由器可以用来做路径选择D:交换机可以转发广播二、多项选择题:正确答案的个数在每题的题后括号中有说明91、在路由器上,可以使用的命令有:()[选3个]A:pingB:howinterfaceC:howiprouteD:ipconfigE:wincfg92、在配置帧中继子接口时,在物理接口上应该配置的内容是:()[选3个]A:配置IP地址B:封装帧中继协议C:指定子接口类型D:设定子接口E:配置密码93、请选出交换机处理帧的三种模式:()[选3个]A:直通模式B:存储转发模式C:侦测模式D:分段模式E:阻塞模式94、对于IP为199.41.27.0,子网掩码为255.255.255.240,则该IP地址和子网掩码相作用会得到一系列IP,从下列选项中选出属于“有效IP”的选项:()[选3个]A:199.141.27.33B:199.141.27.112C:199.141.27.119D:199.141.27.126E:199.141.27.175F:199.141.27.20895、属于私有IP 段的是()[选3个]A:10.0.0.0-10.255.255.255B:172.16.0.0-172.31.255.255C:202.110.100.0-202.110.100.255D:192.168.0.0-192.168.255.255E:126.0.0.0-126.255.255.25596、下列哪一设备工作时,要用到OSI的七个层(一层到七层)()[选3个]A:PCB:网管机C:WEB服务器D:交换机E:路由器97、网络中经常使用DDN服务,请选出DDN的优点()[选3个]A:传输质量高B:接入方式灵活C:偷占带宽D:使用虚电路E:专用线路98、网络中经常使用“帧中继”服务,请选出帧中继的优点()[选3个]A:偷占带宽B:提供拥塞管理机制C:可以使用任意广域网协议D:灵活的接入方式99、默认情况下,IGRP衡量路径好坏时,考虑的因素为()[选2个]A:带宽B:可靠性C:最大传输单元D:延时100、交换机的三大功能为()[选3个]A:地址学习B:转发过滤C:消除回路D:发送数据包。
2023年CCNA考试真题
2023年CCNA考试真题2023年CCNA考试正式开考啦!本次考试涉及网络技术的基础知识,将对考生的技术水平进行全面考察。
下面是本次考试的真题,希望能够帮助考生更好地复习。
【第一部分:选择题】(共10题,每题2分,共计20分)1. OSI模型中,位于网络层的协议是:A. TCPB. IPC. HTTPD. UDP2. 下面哪个命令可以查看路由表信息:A. pingB. tracertC. ipconfigD. route print3. 在IP地址192.168.0.1/24中,/24表示什么意思:A. 子网掩码B. 路由器IP地址C. 网络IDD. 主机ID4. 下面哪个协议可以实现主机与交换机之间的通信:A. BGPB. ARPC. MPLSD. SNMP5. 下面哪个命令可以查看IP地址的连通性:A. telnetB. netstatC. pingD. tracert6. VLAN是指:A. 虚拟本地区域网络B. 可视化局域网C. 个人局域网D. 无线局域网7. 下面哪个设备可以实现不同局域网之间的互联:A. 集线器B. 路由器C. 交换机D. 网桥8. 下面哪个协议负责在网络中寻找设备的物理地址:A. ARPB. ICMPC. OSPFD. BGP9. 下面哪个命令可以查看交换机的端口信息:A. show ip interface briefB. show mac-address-tableC. show running-configD. show version10. 下面哪个协议可以实现安全的远程登录:A. FTPB. HTTPC. SSHD. Telnet【第二部分:填空题】(共5题,每题4分,共计20分)1. 在OSI模型中,位于物理层的设备是_________。
2. 在TCP/IP协议族中,位于传输层的协议是_________。
3. IP地址由_________位二进制数组成。
CCNA考试题目及答案640-802_2008_10_6
Exam CISCO-640-8021.Which two methods are examples of implementing Layer 2 security on a Cisco switch? (Choose two.) A:disable trunk negotiation on the switchB:enable Cisco Discovery Protocol globally to monitor for malicious devicesC:configure a switch port host where appropriateD:enable HTTP access to the switch for security troubleshootingE:use only protected Telnet sessions to connect to the Cisco deviceF:install a modem on the auxiliary port for emergency accessCorrect Answers: A, C2.Which type of attack is characterized by a flood of packets that are requesting a TCP connection to a server?A: denial of service B: brute forceC: reconnaissance D: Trojan horseCorrect Answers: A3.Refer to the exhibit. S0/0 on R1 is configured as a multipoint interface to communicate with R2 and R3 in this hub-and-spoke Frame Relay topology. While testing this configuration, a technician notes that pings are successful from hosts on the 172.16.1.0/24 network to hosts on both the 172.16.2.0/25 and 172.16.2.128/25 networks. However, pings between hosts on the 172.16.2.0/25 and 172.16.2.128/25 networks are not successful. What could explain this connectivity problem?A: The ip subnet-zero command has been issued on the R1 router.B: The RIP v2 dynamic routing protocol cannot be used across a Frame Relay network.C: Split horizon is preventing R2 from learning about the R3 networks and R3 from learning about the R2 networks.D: The 172.16.2.0/25 and 172.16.2.128/25 networks are overlapping networks that can be seen by R1, but not between R2 and R3.E: The 172.16.3.0/29 network used on the Frame Relay links is creating a discontiguous network between the R2 and R3 router subnetworks.Correct Answers: C4.Which of the following are true regarding the command output shown in the display? (Choose two.) A:There are at least two routers participating in the RIP process.B:A ping to 192.168.168.2 will be successful.C:A ping to 10.0.15.2 will be successful.D:RtrA has three interfaces participating in the RIP process.Correct Answers: A, C5.Refer to the exhibit. What is the effect of the configuration that is shown?A: It configures SSH globally for all logins.B: It tells the router or switch to try to establish an SSh connection first and if that fails to use Telnet.C: It configures the virtual terminal lines with the password 030752180500.D: It configures a Cisco network device to use the SSH protocol on incoming communications via the virtual terminal ports.E: It allows seven failed login attempts before the VTY lines are temporarily shutdown.Correct Answers: D6.Refer to the exhibit. The two connected ports on the switch are not turning orange or green. What would be the most effective steps to troubleshoot this physical layer problem? (Choose three.)A:Ensure that the Ethernet encapsulations match on the interconnected router and switch ports. B:Ensure that cables A and B are straight-through cables.C:Ensure cable A is plugged into a trunk port.D:Ensure the switch has power.E:Reboot all of the devices.F:Reseat all cables.Correct Answers: B, D, F7.Refer to the exhibit. PC_1 is sending packets to the FTP server. Consider the packets as they leave RouterA interface Fa0/0 towards RouterB. Drag the correct frame and packet address to their place in the table.Drag and drop question. Drag the items to the proper locations.Correct Answers:8.Refer to the exhibit. The FMJ manufacturing company is concerned about unauthorized access to the Payroll Server. The Accounting1, CEO, Mgr1, and Mgr2 workstations should be the only computers withaccess to the Payroll Server. What two technologies should be implemented to help prevent unauthorized access to the server? (Choose two.)A:access lists B:encrypted router passwordsC:STP D:VLANsE:VTP F:wireless LANsCorrect Answers: A, D9.An administrator is configuring a router that will act as the hub in a Frame Relay hub-and-spoke topology. What is the advantage of using point-to-point subinterfaces instead of a multipoint interface on this router?A: It avoids split-horizon issues with distance vector routing protocols.B: Only one IP network address needs to be used to communicate with all the spoke devices.C: Point-to-point subinterfaces offer greater security compared to a multipoint interface configuration.D: Only a single physical interface is needed with point-to-point subinterfaces, whereas a multipoint interface logically combines multiple physical interfaces.Correct Answers: A10.Which statement is correct about the internetwork shown in the diagram?A: Switch 2 is the root bridge.B: Spanning Tree is not running.C: Host D and Server 1 are in the same network.D: No collisions can occur in traffic between Host B and Host C.E: If Fa0/0 is down on Router 1, Host A cannot access Server 1.F: If Fa0/1 is down on Switch 3, Host C cannot access Server 2.Correct Answers: E11.Which two values are used by Spanning Tree Protocol to elect a root bridge? (Choose two.)A:amount of RAMB:bridge priorityC:IOS versionD:IP addressE:MAC addressF:speed of the linksCorrect Answers: B, E12.Refer to the graphic. It has been decided that Workstation 1 should be denied access to Server1. Which of the following commands are required to prevent only Workstation 1 from accessing Server1 while allowing all other traffic to flow normally? (Choose two.)A:RouterA(config)# interface fa0/0RouterA(config-if)# ip access-group 101 outB:RouterA(config)# interface fa0/0RouterA(config-if)# ip access-group 101 inC:RouterA(config)# access-list 101 deny ip host 172.16.161.150 host 172.16.162.163RouterA(config)# access-list 101 permit ip any anyD:RouterA(config)# access-list 101 deny ip 172.16.161.150 0.0.0.255 172.16.162.163 0.0.0.0 RouterA(config)# access-list 101 permit ip any anyCorrect Answers: B, C13.How many subnets can be gained by subnetting 172.17.32.0/23 into a /27 mask, and how many usable host addresses will there be per subnet?A: 8 subnets, 31 hostsB: 8 subnets, 32 hostsC: 16 subnets, 30 hostsD: 16 subnets, 32 hostsE: A Class B address can't be subnetted into the fourth octet.Correct Answers: C14.Which spread spectrum technology does the 802.11b standard define for operation?A: IRB: DSSSC: FHSSD: DSSS and FHSSE: IR, FHSS, and DSSSCorrect Answers: B15.What is the maximum data rate specified for IEEE 802.11b WLANs?A: 10 MbpsB: 11 MbpsC: 54 MbpsD: 100 MbpsCorrect Answers: B16.Refer to the output from the show running-config command in the exhibit. What should the administrator do to allow the workstations connected to the FastEthernet 0/0 interface to obtain an IP address?A: Apply access-group 14 to interface FastEthernet 0/0.B: Add access-list 14 permit any any to the access list configuration.C: Configure the IP address of the FastEtherent 0/0 interface to 10.90.201.1.D: Add an interface description to the FastEthernet 0/0 interface configuration.Correct Answers: C17.Which additional configuration step is necessary in order to connect to an access point that has SSID broadcasting disabled?A: Set the SSID value in the client software to public.B: Configure open authentication on the AP and the client.C: Set the SSID value on the client to the SSID configured on the AP.D: Configure MAC address filtering to permit the client to connect to the AP.Correct Answers: C18.What is the function of the Cisco IOS command ip nat inside source static 10.1.1.5 172.35.16.5?A: It creates a global address pool for all outside NAT transactions.B: It establishes a dynamic address pool for an inside static address.C: It creates dynamic source translations for all inside local PAT transactions.D: It creates a one-to-one mapping between an inside local address and an inside global address. E: It maps one inside source address to a range of outside global addresses.Correct Answers: D19.What three pieces of information can be used in an extended access list to filter traffic? (Choose three.)A:protocolB:VLAN numberC:TCP or UDP port numbersD:source switch port numberE:source IP address and destination IP addressF:source MAC address and destination MAC addressCorrect Answers: A, C, E20.Given the partial router configuration in the graphic, why does the workstation with the IP address 192.168.1.153/28 fail to access the Internet? (Choose two.)A:The NAT inside interfaces are not configured properly.B:The NAT outside interface is not configured properly.C:The router is not properly configured to use the access control list for NAT.D:The NAT pool is not properly configured to use routable outside addresses.E:The access control list does not include the IP address 192.168.1.153/28 to access the Internet. Correct Answers: A, C21.A network administrator wants to add a line to an access list that will block only Telnet accessby the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. What command should be issued to accomplish this task?A: access-list 101 deny tcp 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23access-list 101 permit ip any anyB: access-list 1 deny tcp 192.168.1.128 0.0.0.15 host 192.168.1.5 eq 23access-list 1 permit ip any anyC: access-list 1 deny tcp 192.168.1.128 0.0.0.255 192.168.1.5 0.0.0.0 eq 21access-list 1 permit ip any anyD: access-list 101 deny tcp 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23access-list 101 permit ip any anyE: access-list 101 deny ip 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23access-list 101 permit ip any anyF: access-list 101 deny ip 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23access-list 101 permit ip any anyCorrect Answers: A22.HotspotHotspot question. Click on the correct location or locations in the exhibit. Correct Answers:23.What functions do routers perform in a network? (Choose two.)A:packet switchingB:access layer securityC:path selectionD:VLAN membership assignmentE:bridging between LAN segmentsF:microsegmentation of broadcast domainsCorrect Answers: A, C24.Refer to the exhibit. Each of these four switches has been configured with a hostname, as well as being configured to run RSTP. No other configuration changes have been made. Which switch will have only one forwarding interface?A: SwitchAB: SwitchBC: SwitchCD: SwitchDCorrect Answers: B25.Refer to the exhibit. All of the routers in the network are configured with the ip subnet-zero command. Which network addresses should be used for Link A and Network A? (Choose two.)A:Network A - 172.16.3.48/26B:Network A - 172.16.3.128/25C:Network A - 172.16.3.192/26D:Link A - 172.16.3.0/30E:Link A - 172.16.3.40/30F:Link A - 172.16.3.112/30Correct Answers: B, D26.Which destination addresses will be used by Host A to send data to Host C? (Choose two.)A:the IP address of Switch 1B:the MAC address of Switch 1C:the IP address of Host CD:the MAC address of Host CE:the IP address of the router's E0 interfaceF:the MAC address of the router's E0 interfaceCorrect Answers: C, F27.Refer to the graphic. Host A is communicating with the server. What will be the source MAC address of the frames received by Host A from the server?A: the MAC address of router interface e0B: the MAC address of router interface e1C: the MAC address of the server network interfaceD: the MAC address of host ACorrect Answers: AB28.Click the console of the HOME router . Input the folling command into CLI on the right side Home> enableHome # show runHome # show cdp neighborexamine the configuration informations related to problem solution.Drag and drop question. Drag the items to the proper locations.Correct Answers:29.When a new trunk is configured on a 2950 switch, which VLANs by default are allowed over the trunk link?A: no VLANsB: all VLANsC: only VLANs 1 - 64D: only the VLANs that are specified when creating the trunkCorrect Answers: B30.Which of the following is true regarding the use of switches and hubs for network connectivity?A: Switches take less time to process frames than hubs take.B: Switches do not forward broadcasts.C: Hubs can filter frames.D: Using hubs can increase the amount of bandwidth available to hosts.E: Switches increase the number of collision domains in the network.Correct Answers: E31.Why does the data communication industry use the layered OSI reference model? (Choose two.)A:It divides the network communication process into smaller and simpler components, thus aiding component development, design, and troubleshooting.B:It enables equipment from different vendors to use the same electronic components, thus saving research and development funds.C:It supports the evolution of multiple competing standards, and thus provides business opportunities for equipment manufacturers.D:It encourages industry standardization by defining what functions occur at each layer of the model. E:It provides a means by which changes in functionality in one layer require changes in other layers.Correct Answers: A, D 32.HotspotHotspot question. Click on the correct location or locations in the exhibit. Correct Answers:33.Which of the following statements describe the network shown in the graphic? (Choose two.)A:There are two broadcast domains in the network.B:There are four broadcast domains in the network.C:There are six broadcast domains in the network.D:There are four collision domains in the network.E:There are five collision domains in the network.F:There are seven collision domains in the network.Correct Answers: A, FBPlease Input correct Answer here:35.Refer to the exhibit. The network shown in the exhibit is running the RIPv2 routing protocol. The network has converged, and the routers in this network are functioning properly. The FastEthernet0/0 interface on R1 goes down. In which two ways will the routers in this network respond to this change? (Choose two.)A:All routers will reference their topology database to determine if any backup routes to the 192.168.1.0 network are known.B:Routers R2 and R3 mark the route as inaccessible and will not accept any further routing updates from R1 until their hold-down timers expire.C:Because of the split-horizon rule, router R2 will be prevented from sending erroneous information to R1 about connectivity to the 192.168.1.0 network.D:When router R2 learns from R1 that the link to the 192.168.1.0 network has been lost, R2 will respond by sending a route back to R1 with an infinite metric to the 192.168.1.0 network.E:R1 will send LSAs to R2 and R3 informing them of this change, and then all routers will send periodic updates at an increased rate until the network again converges.Correct Answers: C, D36.What is the media access method used by Gigabit Ethernet?A: CSMA/CAB: CSMA/CDC: token passingD: point-to-pointE: logical link controlCorrect Answers: B37.DropDrag and drop question. Drag the items to the proper locations.Correct Answers:38.Why will a switch never learn a broadcast address?A: Broadcasts only use network layer addressing.B: A broadcast frame is never forwarded by a switch.C: A broadcast address will never be the source address of a frame.D: Broadcast addresses use an incorrect format for the switching table.E: Broadcast frames are never sent to switches.Correct Answers: C39.An inbound access list has been configured on a serial interface to deny packet entry for TCP andUDP ports 21, 23 and 25. What types of packets will be permitted by this ACL? (Choose three.)A:FTPB:TelnetC:SMTPD:DNSE:HTTPF:POP3Correct Answers: D, E, F40.Refer to the exhibit. After HostA pings HostB, which entry will be in the ARP cache of HostA to support this transmission?Please Input correct Answer here:switch port fa0/1 to establish a link with router R1 using the IEEE standard protocol? (Choose three.)A:Switch(config)# interface fastethernet 0/1B:Switch(config-if)# switchport mode accessC:Switch(config-if)# switchport mode trunkD:Switch(config-if)# switchport access vlan 1E:Switch(config-if)# switchport trunk encapsulation islF:Switch(config-if)# switchport trunk encapsulation dot1qCorrect Answers: A, C, F42.Refer to the exhibit. What kind of cable should be used to make each connection that is identified by the numbers shown?A: 1 - Ethernet crossover cable2 - Ethernet straight-through cable3 - fiber optic cable4 - rollover cableB: 1 - Ethernet straight-through cable2 - Ethernet straight-through cable3 - serial cable4 - rollover cableC: 1 - Ethernet rollover cable2 - Ethernet crossover cable3 - serial cable4 - null modem cableD: 1 - Ethernet straight-through cable2 - Ethernet crossover cable3 - serial cable4 - rollover cableE: 1 - Ethernet straight-through cable2 - Ethernet crossover cable3 - serial cable4 - Ethernet straight-through cableCorrect Answers: B43.At which layers of the OSI model do WANs operate? (Choose two.)A:application layerB:session layerC:transport layerD:network layerE:datalink layerF:physical layerCorrect Answers: E, FBPlease Input correct Answer here:Central1(config)#router eigrp 23Central1(config-router)#network 192.168.33.045.The network security policy requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy? (Choose two.)A:Switch1(config-if)# switchport port-security maximum 1B:Switch1(config)# mac-address-table secureC:Switch1(config)# access-list 10 permit ip hostD:Switch1(config-if)# switchport port-security violation shutdownE:Switch1(config-if)# ip access-group 10Correct Answers: A, D46.Refer to the exhibit. A problem with network connectivity has been observed. It is suspected that the cable connected to switch port Fa0/9 on Switch1 is disconnected. What would be an effect of this cable being disconnected?A: Host B would not be able to access the server in VLAN9 until the cable is reconnected.B: Communication between VLAN3 and the other VLANs would be disabled.C: The transfer of files from Host B to the server in VLAN9 would be significantly slower.D: For less than a minute, Host B would not be able to access the server in VLAN9. Then normal network function would resume.Correct Answers: D47.Refer to the exhibit. The FMJ manufacturing company is concerned about unauthorized access to the Payroll Server. The Accounting1, CEO, Mgr1, and Mgr2 workstations should be the only computers with access to the Payroll Server. What two technologies should be implemented to help prevent unauthorized access to the server? (Choose two.)A:access listsB:encrypted router passwordsC:STPD:VLANsE:VTPF:wireless LANsCorrect Answers: A, D48.Refer to the exhibit. NAT has been used to convert all the IP addresses on the internal network to the single address 128.107.1.1 as traffic is routed toward the Internet. Which of these statements accurately describes what will happen when the IP traffic returns from the Internet destined for hosts on the internal network?A: ExternalRouter will require a route to 172.16.0.0/16 in its routing table to properly direct the traffic.B: InternalRouter will convert the source IP addresses of all packets before forwarding them onto the internal network.C: ExternalRouter will translate the destination IP addresses of all packets before forwarding them to InternalRouter.D: As InternalRouter will be receiving traffic from ExternalRouter, the destination IP addresses will already have been converted to 172.16.0.0/16 addresses.E: ExternalRouter can use the directly connected interface on the 128.107.0.0/27 network to route return traffic to its originators.Correct Answers: E49.Refer to the exhibit. A network associate needs to configure the switches and router in the graphic so that the hosts in VLAN3 and VLAN4 can communicate with the enterprise server in VLAN2. Which two Ethernet segments would need to be configured as trunk links? (Choose two.)A:AB:BC:CD:DE:EF:FCorrect Answers: C, F50.Which statement is correct regarding the operation of DHCP?A: A DHCP server uses a ping to detect address conflicts.B: A DHCP server uses a gratuitous ARP to detect DHCP clients.C: A DHCP client uses a ping to detect address conflicts.D: A DHCP client uses a gratuitous ARP to detect a DHCP server.E: If and address conflict is detected, the address is removed from the pool for an amount of time configurable by the administrator.Correct Answers: A51.A Cisco router that was providing Frame Relay connectivity at a remote site was replaced with a different vendor's frame relay router. Connectivity is now down between the central and remote site. What is the most likely cause of the problem?A: mismatched LMI typesB: incorrect DLCIC: mismatched encapsulation typesD: incorrect IP address mappingCorrect Answers: C52.Which additional configuration step is necessary in order to connect to an access point that has SSID broadcasting disabled?A: Set the SSID value in the client software to public.B: Configure open authentication on the AP and the client.C: Set the SSID value on the client to the SSID configured on the AP.D: Configure MAC address filtering to permit the client to connect to the AP.Correct Answers: C53.What is the default routing update period for RIPv2?A: 15 secondsB: 30 secondsC: 180 secondsD: 240 secondsCorrect Answers: B54.Acknowledgements, sequencing, and flow control are characteristics of which OSI layer?A: Layer 2B: Layer 3C: Layer 4D: Layer 5E: Layer 6F: Layer 7Correct Answers: C55.An access list has been designed to prevent HTTP traffic from the Accounting Department from reaching the HR server attached to the Holyoke router. Which of the following access lists will accomplish this task when grouped with the e0 interface on the Chicopee router?A: permit ip any anydeny tcp 172.16.16.0 0.0.0.255 172.17.17.252 0.0.0.0 eq 80B: permit ip any anydeny tcp 172.17.17.252 0.0.0.0 172.16.16.0 0.0.0.255 eq 80C: deny tcp 172.17.17.252 0.0.0.0 172.16.16.0 0.0.0.255 eq 80permit ip any anyD: deny tcp 172.16.16.0 0.0.0.255 172.17.17.252 0.0.0.0 eq 80permit ip any anyCorrect Answers: D56.Which of the following are key characteristics of PPP? (Choose three.)A:can be used over analog circuitsB:maps Layer 2 to Layer 3 addressC:encapsulates several routed protocolsD:supports IP onlyE:provides error correctionCorrect Answers: A, C, E57.Refer to the exhibit. The network administrator must complete the connection between the RTA of the XYZ Company and the service provider. To accomplish this task, which two devices could be installed at the customer site to provide a connection through the local loop to the central office of the provider? (Choose two.)A:WAN switchB:PVCC:ATM switchD:multiplexerE:CSU/DSUF:modemCorrect Answers: E, F58.What is the maximum data rate specified for IEEE 802.11b WLANs?A: 10 MbpsB: 11 MbpsC: 54 MbpsD: 100 MbpsCorrect Answers: B59.Refer to the exhibit. A technician is troubleshooting a host connectivity problem. The host is unable to ping a server connected to Switch_A. Based on the results of the testing, what could be the problem?A: A remote physical layer problem exists.B: The host NIC is not functioning.C: TCP/IP has not been correctly installed on the host.D: A local physical layer problem exists.Correct Answers: D60.When a router is connected to a Frame Relay WAN link using a serial DTE interface, how is the interface clock rate determined?A: It is supplied by the CSU/DSU.B: It is supplied by the far end router.C: It is determined by the clock rate command.D: It is supplied by the Layer 1 bit stream timing.Correct Answers: A61.Refer to the exhibit. RouterA is configured to use NAT in overload mode PC_A is sending packets to Web Server. Drag the addresses to fill in the NAT terminology table with their associated IP address values. Note: Addresses may be used, none, once or more.Drag and drop question. Drag the items to the proper locations. Correct Answers:62.Refer to the exhibit. The network shown in the exhibit is running the RIPv2 routing protocol. The network has converged, and the routers in this network are functioning properly. The FastEthernet0/0 interface on R1 goes down. In which two ways will the routers in this network respond to this change? (Choose two.)A:All routers will reference their topology database to determine if any backup routes to the 192.168.1.0 network are known.B:Routers R2 and R3 mark the route as inaccessible and will not accept any further routing updates from R1 until their hold-down timers expire.C:Because of the split-horizon rule, router R2 will be prevented from sending erroneous information to R1 about connectivity to the 192.168.1.0 network.D:When router R2 learns from R1 that the link to the 192.168.1.0 network has been lost, R2 will respond by sending a route back to R1 with an infinite metric to the 192.168.1.0 network.E:R1 will send LSAs to R2 and R3 informing them of this change, and then all routers will send periodic updates at an increased rate until the network again converges.Correct Answers: C, D63.The Ethernet networks connected to router R1 in the graphic have been summarized for router R2 as192.1.144.0/20. Which of the following packet destination addresses will R2 forward to R1, according to this summary? (Choose two.)A:192.1.159.2B:192.1.160.11C:192.1.138.41D:192.1.151.254E:192.1.143.145F:192.1.1.144Correct Answers: A, D64.Refer to the exhibit. Host B is actively communicating by Ethernet with the server. Host A has frames to send to the Internet. How will host A proceed?A: Host A will listen and transmit when there is no traffic on the segment.B: Host A will immediately begin transmitting because the destination is different.C: Host A must wait for the server to reply to host B before transmitting.D: Host A will immediately begin transmitting because it has priority based on its MAC address. E: Host A can send its frames at any time because it will be sending them through the router. Correct Answers: A65.Why would a network administrator configure port security on a switch?A: to prevent unauthorized Telnet access to a switch portB: to limit the number of Layer 2 broadcasts on a particular switch portC: to prevent unauthorized hosts from accessing the LAND: to protect the IP and MAC address of the switch and associated portsE: to block unauthorized access to the switch management interfaces over common TCP portsCorrect Answers: C66.What is the effect of using the service password-encryption command?A: Only the enable password will be encrypted.B: Only the enable secret password will be encrypted.C: Only passwords configured after the command has been entered will be encrypted.D: It will encrypt the secret password and remove the enable secret password from the configuration. E: It will encrypt all current and future passwords.Correct Answers: E67.Which two devices can interfere with the operation of a wireless network because they operate on similar frequencies? (Choose two.)A:copierB:microwave ovenC:toasterD:cordless phoneE:IP phoneF:AM radioCorrect Answers: B, D68.Which type of attack is characterized by a flood of packets that are requesting a TCP connection to a server?A: denial of serviceB: brute forceC: reconnaissanceD: Trojan horseCorrect Answers: A69.Refer to the exhibit. A technician is investigating a problem with the network that is shown. The router is a 2800 model and all switches are 2950 models. These symptoms have been observed:- All of the user hosts can access the Internet.- None of the user hosts can access the server located in VLAN 9.- All of the hosts can ping each other.What could cause these symptoms?。
思科CCNA考试答案(全)
CCNA思科考试答案(全)第 1 章考试1一家拥有10 名员工的小型公司使用单个LAN 在计算机之间共享信息。
哪种类型连接适合此公司?由当地电话服务提供商提供的拨号连接能够使公司方便且安全地连接员工的虚拟专用网络通过当地服务提供商建立的私有专用线路通过当地服务提供商提供的宽带服务(如DSL)答案:4解析:对于这种小型办公室,比较适合通过被称为数字用户线路(DSL) 的常见宽带服务实现Internet 连接,这种服务由当地的电话服务提供商提供。
由于员工人数很少,带宽的问题并不突出。
如果公司较大,在远程站点有分支机构,则专用线路会更加适合。
如果公司员工需要通过Internet 与公司联系,则采用虚拟专用网。
2哪种网络情况需要使用WAN?员工工作站需要获取动态分配的IP 地址。
员工在出差时需要通过VPN 连接到公司电子邮件服务器。
分支机构的员工需要与同一园区网络上的另一座建筑物内的公司总部共享文件。
员工需要访问托管在其建筑物内DMZ 中的公司Web 服务器上的网页。
答案:2解析:当出差的员工需要通过WAN 连接到公司电子邮件服务器时,VPN 将通过WAN 连接在员工笔记本电脑与公司网络之间创建一个安全隧道。
通过DHCP 获取动态IP 地址是LAN 通信的功能。
在企业园区的不同建筑物之间共享文件可通过LAN 基础设施来实现。
DMZ 是企业LAN 基础设施内一个受保护的网络。
3以下哪项描述了WAN 的特征?WAN 和LAN 在同一地理范围内运行,但有串行链路。
WAN 网络归运营商所有。
所有串行链路均被视为WAN 连接。
WAN 可提供到园区主干网的终端用户网络连接。
答案:2解析:WAN 可用于将企业LAN 互连到远程分支机构站点LAN 和远程工作人员站点。
WAN 归运营商所有。
虽然WAN 连接一般通过串行接口实现,但并不是所有串行链路均连接至WAN。
LAN(而非WAN)可在组织中提供终端用户网络连接。
4电路交换WAN 技术的两个常见类型是什么?(请选择两项。
思科网络基础考题及答案
网段2
网段3
网段4
网段5
窗体底端
27
窗体顶端
在Cisco IOS设备中,启动配置文件存储于何处?
闪存
NVRAM
RAM
ROM
窗体底端
28
窗体顶端
下列哪三个IPv4地址代表子网的广播?(选择三项)
172.16.4.63 /26
172.16.4.129 /26
172.16.4.191 /26
172.16.4.51 /27
窗体顶端
窗体底端
关闭窗口
考试系统
3.参加考试
参加考试- ENetwork Final Exam - CCNA Exploration:网络基础知识(版本4.0)
窗体顶端
剩余时间:
窗体底端
31
窗体顶端
请参见图示。主机A正在向主机B传输数据。主机A将使用什么地址作为此通信中的目的IP地址和目的MAC地址?
这些配置项对远程访问指定了三条Telnet线路。
这些配置项对远程访问指定了四条Telnet线路。
这些配置项将控制台口令和Telnet口令设置为"c13c0"。
因为Telnet配置不完整,所以Telnet访问将遭到拒绝。
允许使用"c13c0"作为口令访问Telnet。
窗体底端
26
窗体顶端
请参见图示。电缆1和电缆2的两端分别按照特定的物理层要求接线。表中按编号列出了每个网段以及网络技术人员在该网段不同网络组件之间已经安装的电缆。根据给定的数据回答,哪些网段的电缆安装正确?(选择三项)
192.168.18.48
192.168.18.49
192.168.18.52
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CCNA试题1.What is the correct order for the OSI model? BP=Presentation, S=Session, D=Datalink, Ph=Physical, T=Transport, A= Application, N=NetworkA. P S A PH D N TB. A P S T N D PHC. PH D N T A S PD. P S A T N D PHIt is crucial you not only memorize this and know what each layer does.2. What is encapsulation? CA. Putting the header on an incoming frameB. Putting a header on an incoming segmentC. Putting a header on an outgoing frameD. Putting a header on an outgoing bitThis also includes trailers and can be put on segments, packets, and frames.3. Which layer is most concerned with user applications? AA. ApplicationB. PresentationC. NetworkD. Physical4. Which of the following is de-encapsulation?AA. Stripping the header from a frameB. Putting a header on a segmentC. Putting a header on a frameD. Stripping a frame from a linkThis also includes trailers as in question 2.5. What layer converts data into segments? CA. ApplicationB. PresentationC. TransportD. Physical6. What layer converts data into Packets? AA. NetworkB. ApplicationC. PhysicalD. Data Link7. What layer converts data into Frames? CA. ApplicationB. PhysicalC. Data LinkD. Transport8. What layer converts data into bits? DA. ApplicationB. SessionC. Data LinkD. PhysicalAll of the layers need to convert data into something that they can pass down to the next level, with the exception of the Application layer which hands data to the Presentation layer.The Presentation layer encrypts, and compresses before sending it to the Session layer for it s first conversion.9. Which layer is most concerned with getting datafrom the beginning to the final destination? DA. ApplicationB. PresentationC. SessionD. TransportThe transport layer is most concerned with reliable transportation from one end to the other.10. Which of the following is not a part of the Session layer? BA. Establishing a sessionB. Ensuring error free segmentsC. Ending a sessionD. Keeping the sender and receiver from sending a message at the same time That is the job of the Transport layer.11. Which of the following is not a job for the presentation layer? Choose 2 CDA. Data representationB. CompressionC. Dialog managementD. TransmissionE. EncryptionC is handled by the session layer, andD is handled by the Transport layer12. What does Peer to Peer communication involve? DA. Each layer communication with the layer below itB. Each layer communication with layer above itC. Each layer communicating with adjacent layer in another systemD. Each layer communication with it s corresponding layer in another systemAnswer D.Answer C sounds correct also, but adjacent and corresponding are two different things. The session layer can only communicate with the session layer in another system for example.13. Why does the industry use a layered model?Choose all correct ABCDA. When you enhance one layer it doesn t affect the other layersB. Design and development can be made in a modular fashionC. Network operations can be simplifiedD. Troubleshooting can be simplified.14. Which two of the following are not from the physical layer? ADA. SDLCB. V.35C. HSSID. ISDNE. RS-232Answer A D.SDLC and ISDN are W AN protocols that function at the data link layer15. Which two answers are functions of the OSI model"s network layer? BCA. Sequencing of framesB. Path determinationC. Packet switchingD. Packet sequencingAnswer B C. Sequencing is done at the data link layer. D is fictional.16. What is an example of a MAC address? DA. Az32:6362:2434B. Sj:2817:8288C. GGG:354:665D. A625:cbdf:6525The address is a 48 bit address which requires 12 Hex digits.A hex digit can t be past the letter F. Hex stands for 16. 1-9 and A-F make up numbers that are valid.17. Which of the following is not part of the data link layer? EA. Transports data across the physical linkB. Performs physical addressingC. Performs flow controlD. Determines network topologyE. Terminates a sessionThis is part of the session layer18. Which of the following are data link protocols? ADEA. HDLCB. FTPC. SQLD. ISDNE. Token RingFTP is an application and SQL is a session layer protocol.19. Of the following address AA77:3827:EF54, which of the following is the vendor portion? AA. AA7738B. 27EF54C. AA77D. EF54The vendor code is how you can tell who made the card. The last 6 digits are the physical address.20. Which of the following are examples of layer 3 addressing? ABA. 165.33.4.34B. AA77:3827:EF54C. HHHH:hg:7654D. 76The first is a TCPIP address and the second is an IPX address21. What is considered Layer 3 addressing? BA. Data Link LayerB. Network LayerC. Application LayerD. None of thesePhysical is Layer 1, then data link, and then Network. This is the same layer that routers are on. A22. What layer are Bridges on?A. Data LinkB. PhysicalC. ApplicationD. TransportBridges segment networks but are not able to determine addresses like the network layer does.23. Repeaters are on what layer? CA. TransportB. SessionC. PhysicalD. ApplicationAll repeaters can do is boost a signal. An active hub is a good example of a repeater. A switching hub is a good example of layer 3 addressing, since switches go by network addresses and IPX addresses rather than just boost signals. Bridges can only read mac addresses, and not the full IPX or TCPIP addresses.24. Which of the following are considered routing protocols? ADA. OSPFB. IPC. IPXD. EIGRPE. Token RingAnswers B and C are routed protocols, whereas A and D are the protocols that do the routing. This is easily confused. You can remember it by thinking that the routing protocols that haul the routed protocols are like a tug ship pulling a barge. The barge is full of data.25. Which two of the following are considered connection oriented communication? ADA. Setup and maintenance procedures are performed to ensure message delieveryB. A physical circuit exists between two communicating devicesC. It is a best effort type of communicationD. A virtual connection exists between the twoB is not a necessity, andC is not accurate. TCP is connection oriented and UDP is not26. Which of the following are not WAN protocols? Choose 2 CDA. Frame RelayB. A TMC. EthernetD. FDDIE. ISDNEthernet and FDDI are LAN protocols.27. Which of the following will allow you to view NVRAM s contents? AEA. show configurationB. show protocolsC. show versionD. show running-configE. show startup-configAnswer A E. These show the backup configuration stored in NVRAM. The other anwsers allow youto view RAM.28. Which of the following contains the OS image? AA. FlashB. NVRAMC. RAMD. InterfacesROM will be used if Flash is unavailable. NVRAM is the backup configuration, and RAM is the active configuration29. Which of the following indicates the router is in privilege mode? AA. Router#B. Router>C. Router-D. Router* Answer B shows the router in user mode.30. What does "show cdp neighbors" not show? Neighbors___C______A. device idC. ios versionD. port type and number31. Which of the following will show you the clock? DA. cl?B. Cl ?C. Clock?D. Clock ?By typing this the router will finish the command and show the clock.32. CDP operates at which layer? DA. TransportB. NetworkC. Data linkD. PhysicalCDP allows a network device to exchange frames with other directly connected networked devices.33. Which command does not show two devices are not routing packets between them successfully? ACDA. pingB. show interfaceC. traceD. telnetAnswer A C D. With these commands you can tell whether or not you have communication. Show interface just verifies there is a connection34. What keystrokes shows the possible commands in privilege mode? ABA. helpB. hC. ctrl+hD. ?Answers A and B will give a brief description when typed, and C is not valid.35. Which two items contain versions of the router s configuration file? BCA. flashB. nvramC. ramD. romA and D contain the OS.36. Which of the following commands will allow you to review the contents of RAM?A. show configuration BCDC. show versionD. show running-configE. show startup-configA and E allow you to see NVRAM.37. Which of the following will allow you to add, modify, or delete commands in the startup configuration file? DA. show startup-configB. show running-configC. configure terminalD. configure memoryAnswer C allows you to change items in the running configuration file38. Which command would be used to restore a configuration file to RAM? ____A____TFTP running-configA. router#copyB. router>copyC. router*copyD. router^copyYou must be in privilege mode when executing this, which is why you see the # sign.39. Which of the following commands will display the running configuration file to a terminal? AA. show running-configB. show router-configC. router#show flashD. router>show versionIt can only be shown in privilege mode.40. If you need to copy the currently executing configuration file into NVRAM,which command would you use? CA. router#copy startup-config running-configB. router#copy startup-config TFTPC. router#copy running-config startup-configD. router>copy startup-config running-configAnswers ABC show that the router is in privilege mode which is necessary to complete this action, but only C shows the correct syntax.。
