ccna2答案第二章
CCNA2 题库

CCNA 2 - Chapter 11What is one advantage of using the cut-through switching method instead of the store-and-forward switching method?has a positive impact on bandwidth by dropping most of the invalid framesmakes a fast forwarding decision based on the source MAC address of the framehas a lower latency appropriate for high-performance computing applications*provides the flexibility to support any mix of Ethernet speeds2A network designer must provide a rationale to a customer for a design which will move an enterprise from a flat network topology to a hierarchical network topology. Which two features of the hierarchical design make it the better choice? (Choose two.)reduced cost for equipment and user trainingless required equipment to provide the same performance levelssimpler deployment for additional switch equipment*easier to provide redundant links to ensure higher availability*lower bandwidth requirements3What are two advantages of modular switches over fixed-configuration switches? (Choose two.)availability of multiple ports for bandwidth aggregationlower forwarding ratesneed for fewer power outlets*lower cost per switchincreased scalability*4Refer to the exhibit. Consider that the main power has just been restored. PC1 asks the DHCP server for IPv4 addressing. The DHCP server sends it an IPv4 address. While PC2 is still booting up, PC3 issues a broadcast IPv4 DHCP request. To which port will SW1 forward this request?to Fa0/1, Fa0/2, and Fa0/4 onlyto Fa0/1, Fa0/2, Fa0/3, and Fa0/4to Fa0/1 and Fa0/2 onlyto Fa0/1, Fa0/2, and Fa0/3 only*to Fa0/1 only5What is one function of a Layer 2 switch?forwards data based on logical addressinglearns the port assigned to a host by examining the destination MAC addressduplicates the electrical signal of each frame to every portdetermines which interface is used to forward a frame based on the destination MAC address*6Refer to the exhibit. Fill in the blank.There are ” 12” collision domains in the topology.7What is a collapsed core in a network design?a combination of the functionality of the access, distribution, and core layersa combination of the functionality of the access and core layersa combination of the functionality of the distribution and core layers*a combination of the functionality of the access and distribution layers 8What are two reasons a network administrator would segment a network with a Layer 2 switch? (Choose two.)to enhance user bandwidth*to eliminate virtual circuitsto create more broadcast domainsto isolate traffic between segments*to isolate ARP request messages from the rest of the networkto create fewer collision domains9Refer to the exhibit.How is a frame sent from PCA forwarded to PCC if the MAC address table on switch SW1 is empty?SW1 forwards the frame directly to SW2. SW2 floods the frame to all ports connected to SW2, excluding the port through which the frame entered the switch.SW1 floods the frame on all ports on the switch, excluding the interconnected port to switch SW2 and the port through which the frame entered the switch.SW1 floods the frame on all ports on SW1, excluding the port through which the frame entered the switch.*SW1 drops the frame because it does not know the destination MAC address.10Place the options in the following order:[+] appropriate for high performance computing applications[+] forwarding process can begin after receiving the destination address [+] may forward invalid frames[#] error checking before forwarding[#] forwarding process only begin after receiving the entire frame [#] only forward valid frames[+] Order does not matter within this group.[#] Order does not matter within this group.11What is a basic function of the Cisco Borderless Architecture distribution layer?aggregating Layer 3 routing boundaries*aggregating all the campus blocksacting as a backboneproviding access to the user12ABC, Inc. has about fifty hosts in one LAN. The administrator would like to increase the throughput of that LAN. Which device will increase the number of collision domains and thereby increase the throughput of the LAN?hubhostNICswitch*13What does the term “port density” represent for an Ethernet switch?the numbers of hosts that are connected to each switch portthe speed of each portthe memory space that is allocated to each switch portthe number of available ports*14Which type of transmission does a switch use when the destination MAC address is not contained in the MAC address table?anycastunicastbroadcast*multicast15What is a basic function of the Cisco Borderless Architecture access layer?aggregates Layer 3 routing boundariesprovides high availabilityaggregates Layer 2 broadcast domainsprovides access to the user*16What information is added to the switch table from incoming frames?source MAC address and incoming port number*destination MAC address and incoming port numberdestination IP address and incoming port numbersource IP address and incoming port number17Fill in the blank.A “converged” network is one that uses the same infrastructure to carry voice, data, and video signals.18An administrator purchases new Cisco switches that have a feature called StackPower. What is the purpose of this feature?It enables many switches to be connected with a special fiber-optic power cable to provide higher bandwidth.It enables the sharing of power among multiple stackable switches.*It enables many switches to be connected to increase port density.It enables many switches to be physically stacked in an equipment rack.It enables AC power for a switch to be provided from a powered patch panel.19Which switch form factor should be used when large port density, fault tolerance, and low price are important factors?fixed-configuration switchmodular switchstackable switch*rackable 1U switch20Refer to the exhibit. Fill in the blank.There are ” 5 ”CCNA 2 - Chapter 2Posted by beotron at 8:59 PM1. A static route that points to the next hop IP will have what administrative distance and metric in the routing table?• administrative distance of 0 and metric of 0• administrative distance of 0 and metric of 1• administrative distance of 1 and metric of 0• administrative distance of 1 and metric of 12. What address can be used to summarize networks 172.16.1.0/24, 172.16.2.0/24, 172.16.3.0/24, and 172.16.4.0/24?• 172.16.0.0/21• 172.16.1.0/22• 172.16.0.0 255.255.255.248• 172.16.0.0 255.255.252.03. The routers in the diagram use the subnet assignments shown. What is the most efficient route summary that can be configured on Router3 to advertise the internal networks to the cloud?• 192.1.1.0/26 and 192.1.1.64/27• 192.1.1.128/25• 192.1.1.0/23 and 192.1.1.64/23• 192.1.1.0/24• 192.1.1.0/25• 192.1.1.0/24 and 192.1.1.64/244. Refer to the exhibit. What is the significance of the /8 in the route to the 10.0.0.0 network?• It indicates that there are 8 hops between this router and the 10.0.0.0 network.• It represents the time, in milliseconds, it takes for a ping to reply when sent to the 10.0.0.0 network.• It indicates that there are 8 subnets in the destination network to which the router can forward packets.• It indicates the number of consecutive bits, from the left, in the destination IP address of a packet that must match 10.0.0.0 to use that route.5. Refer to the exhibit. How will packets destined to the 172.16.0.0 network be forwarded?• Router1 will perform recursive lookup and packet will exit S0/0.• Router1 will perform recursive lookup and packet will exit S0/1.• There is no matching interface associated with network 172.16.0.0 so packets will be dropped.• There is no matching interface associated with network 172.16.0.0 so packets will take gateway of last resort and exit out S0/2.6. A network administrator enters the following command into Router1: ip route 192.168.0.0255.255.255.0 S0/1/0. Router1 then receives a packet that is destined for 192.168.0.22/24. After finding the recently configured static route in the routing table, what does Router1 do next to process the packet? • drops the packet because the destination host is not listed in the routing table• looks up the MAC address of the S0/1/0 interface to determine the destination MAC address of the new frame• performs a recursive lookup for the IP address of the S0/1/0 interface before forwarding the packet• encapsulates the packet into a frame for the WAN link and forwards the packet out the S0/1/0 interface7. Refer to the exhibit. Given the output in the exhibit, how would a clock rate be determined for this link? • The rate would be negotiated by both routers.• A rate would not be selected due to the DCE/DTE connection mismatch.• The rate configured on the DTE determines the clock rate.• The rate configured on the DCE determines the clock rate.8. Refer to the exhibit. Which set of commands will configure static routes that will allow the WinterPark and the Altamonte routers to deliver packets from each LAN and direct all other traffic to the Internet? • WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/1• WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 198.18.222.0 255.255.255.255 s0/1• WinterPark(config)# ip route 172.191.67.0 255.255.255.0 192.168.146.1• WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2• WinterPark(config)# ip route 172.191.67.0 255.255.255.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/09. Hosts on two separate subnets cannot communicate. The network administrator suspects a missing route in one of the routing tables. Which three commands can be used to help troubleshoot Layer 3 connectivity issues? (Choose three.)• ping• show arp• traceroute• show ip route• show interface• show cdp neighbor d etail10. Refer to the exhibit. A company network engineer is assigned to establish connectivity between the two Ethernet networks so that hosts on the 10.1.1.0/24 subnet can contact hosts on the 10.1.2.0/24 subnet. The engineer has been told to use only static routing for these company routers. Which set of commands will establish connectivity between the two Ethernet networks?• R1(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.1R2(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.2• R1(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.2R2(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.1• R1(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.2R2(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.1• R1(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.1R2(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.2• R1(config)# ip route 0.0.0.0 0.0.0.0 10.1.2.1R2(config)# ip route 0.0.0.0 0.0.0.0 10.1.1.111. Which of the following are displayed by the Router# show cdp neighbors command? (Choose three.) • load• platform• reliability• holdtime• local interface12. Refer to the exhibit. What two commands are required to provide connectivity between the192.168.1.0 and 10.0.0.0 networks without requiring recursive lookup? (Choose two.)• A(config)# ip route 10.0.0.0 255.0.0.0 s 0/1/0• A(config)# ip route 10.0.0.0 255.0.0.0 172.16.40.2• A (config)# ip route 10.0.0.0 255.0.0.0 s 0/0/0• B(config)# ip route 192.168.1.0 255.255.255.0 s 0/0/0• B (config)# ip route 192.168.1.0 255.255.255.0 172.16.40.1• B(config)# ip route 192.168.1.0 255.255.255.0 s 0/1/013. Refer to the exhibit. What two commands will change the next-hop address for the 10.0.0.0/8 network from 172.16.40.2 to 192.168.1.2? (Choose two.)• A(config)# no network 10.0.0.0 255.0.0.0 172.16.40.2• A(config)# no ip address 10.0.0.1 255.0.0.0 172.16.40.2• A(config)# no ip route 10.0.0.0 255.0.0.0 172.16.40.2• A(config)# ip route 10.0.0.0 255.0.0.0 s0/0/0• A(config)# ip route 10.0.0.0 255.0.0.0 192.168.1.214. What happens to a static route entry in a routing table when the outgoing interface is not available? • The route is removed from the table.• The router polls neighbors for a replacement route.• The route remains in the table because it was defined as static.• The router redirects the static route to compensate for the loss of the next hop device.15. A router has one static route to each destination network. Which two scenarios would require an administrator to alter the static routes that are configured on that router? (Choose two.)• The destination network no longer exists.• The destination network is moved to a different interface on the same router.• The path between the source and destination is upgraded with a higher bandwidth link.• A topology change occurs where the exi sting next-hop address or exit interface is not accessible.• The remote destination network interface has to be down for 15 minutes of maintenance.16. Why is it advisable to enter a next-hop IP address when creating a static route whose exit interface is an Ethernet network?• Adding the next-hop address eliminates the need for the router to do any lookups in the routing table before forwarding a packet.• In a multi-access network, the router cannot determine the next-hop MAC address for the Ethernet frame without a next-hop address.• Using a next-hop address in a static route provides a route with a lower metric.• In multi-access networks, using a next-hop address in a static route makes that route a candidate default route.17. The output of the Router# show interfaces serial 0/1 command displays the following:• Serial0/1 is up, line protocol is down.• What is the most likely cause for the line protocol being down?• Serial0/1 is shutdown.• There is no cable connecting the routers.• The remote rout er is using serial 0/0.• No clock rate has been set.18. Refer to the exhibit. Which static route should be configured on Router1 so that host A will be able to reach host B on the 172.16.0.0 network?• ip route 192.168.0.0 172.16.0.0 255.255.0.0• ip rou te 172.16.0.0 255.255.0.0 192.168.0.1• ip route 172.16.0.0 255.255.0.0 S0/0/1• ip route 172.16.0.0 255.255.0.0 S0/0/019. What two devices are responsible for converting the data from the WAN service provider into a form acceptable by the router? (Choose two).• the serial port of the router• a modem• a switch• the ethernet port of the router• a CSU/DSU device• a DTE device20. Which of the following is true regarding CDP and the graphic shown?• CDP running on Router D will gather information about routers A, B, C, and E.• By default, Router A will receive CDP advertisements from routers B and C.• If routers D and E are running different routing protocols, they will not exchange CDP information.• Router E can use CDP to identify the IOS running on Router B.21. Which two statements describe functions or characteristics of CDP? (Choose two.)• It starts up automatically and allows the device to detect directly connected neighbor devices that use CDP.• It operates at the network layer and allows two systems to learn about each other.• It creates a topology map of the entire network.• It allows systems to learn about each other even if different network layer protocols are configured.• It forwards advertisements about routes for faster convergence.22. Which piece of information is available from examining the output of the command show ip interface brief?• Interface speed and duplex• Interface MTU• Errors• Interface MAC address• Interface IP addressCCNA 2 - Chapter 31A network administrator is determining the best placement of VLAN trunklinks. Which two types of point-to-point connections utilize VLAN trunking? (Choose two.)between two switches that share a common VLANbetween a switch and a server that has an 802.1Q NIC*between a switch and a client PCbetween a switch and a network printerbetween two switches that utilize multiple VLANs*2What happens to a port that is associated with VLAN 10 when the administrator deletes VLAN 10 from the switch?The port automatically associates itself with the native VLAN. The port creates the VLAN again.The port goes back to the default VLAN.The port becomes inactive.*3Refer to the exhibit. Interface Fa0/1 is connected to a PC. Fa0/2 is a trunk link to another switch. All other ports are unused. Which security best practice did the administrator forget to configure?Configure all unused ports to a ‘black-hole’ VLAN that is not used f or anything on the network.Disable autonegotiation and set ports to either static access or static trunk.Change the native VLAN to a fixed VLAN that is distinct from all user VLANs and to a VLAN number that is not VLAN 1.All user ports are associated with VLANs distinct from VLAN 1 and distinct from the ‘black-hole’ VLAN.*4Which command is used to remove only VLAN 20 from a switch?no switchport access vlan 20delete flash:vlan.datno vlan 20*delete vlan.dat5A Cisco Catalyst switch has been added to support the use of multiple VLANs as part of an enterprise network. The network technician finds it necessary to clear all VLAN information from the switch in order to incorporate a new network design. What should the technician do to accomplish this task?Erase the startup configuration and reboot the switch.Erase the running configuration and reboot the switch.Delete the startup configuration and the vlan.dat file in the flash memory of the switch and reboot the switch.*Delete the IP address that is assigned to the management VLAN and reboot the switch.6What is the effect of issuing a switchport access vlan 20 command on the Fa0/18 port of a switch that does not have this VLAN in the VLAN database?VLAN 20 will be created automatically.*The command will have no effect on the switch.Port Fa0/18 will be shut down.An error stating that VLAN 20 does not exist will be displayed and VLAN 20 is not created.Which command displays the encapsulation type, the voice VLAN ID, and the access mode VLAN for the Fa0/1 interface?show mac address-table interface Fa0/1show interfaces Fa0/1 switchport*show interfaces trunkshow vlan brief8Place the options in the following order:- not scored -dynamic autononegotiatedynamic desirabletrunk9Port Fa0/11 on a switch is assigned to VLAN 30. If the command no switchport access vlan 30 is entered on the Fa0/11 interface, what will happen?Port Fa0/11 will be returned to VLAN 1.*VLAN 30 will be deleted.An error message would be displayed.Port Fa0/11 will be shutdown.What must the network administrator do to remove Fast Ethernet port fa0/1 from VLAN 2 and assign it to VLAN 3?Enter the no vlan 2 and the vlan 3 commands in global configuration mode. Enter the switchport trunk native vlan 3 command in interface configuration mode.Enter the switchport access vlan 3 command in interface configuration mode.*Enter the no shutdown in interface configuration mode to return it to the default configuration and then configure the port for VLAN 3.11Which two Layer 2 security best practices would help prevent VLAN hopping attacks? (Choose two.)Disable DTP autonegotiation on end-user ports.*Change the management VLAN to a distinct VLAN that is not accessible by regular users.Statically configure all ports that connect to end-user host devices to be in trunk mode.Change the native VLAN number to one that is distinct from all user VLANs and is not VLAN 1.*Use SSH for all remote management access.12In a basic VLAN hopping attack, which switch feature do attackers take advantage of?automatic encapsulation negotiationthe default automatic trunking configuration*an open Telnet connectionforwarding of broadcasts13A Cisco switch currently allows traffic tagged with VLANs 10 and 20 across trunk port Fa0/5. What is the effect of issuing a switchport trunk allowed vlan 30 command on Fa0/5?It allows only VLAN 30 on Fa0/5.*It allows a native VLAN of 30 to be implemented on Fa0/5.It allows VLANs 1 to 30 on Fa0/5.It allows VLANs 10, 20, and 30 on Fa0/5.14Refer to the exhibit. A frame is traveling between PC-A and PC-B through the switch. Which statement is true concerning VLAN tagging of the frame?No VLAN tag is added to the frame.*A VLAN tag is added when the frame is accepted by the switch.A VLAN tag is added when the frame is forwarded out the port to PC-B.A VLAN tag is added when the frame leaves PC-A.15Refer to the exhibit. PC-A and PC-B are both in VLAN 60. PC-A is unable to communicate with PC-B. What is the problem?The native VLAN is being pruned from the link.The VLAN that is used by PC-A is not in the list of allowed VLANs on the trunk.*The trunk has been configured with the switchport nonegotiate command. The native VLAN should be VLAN 60.16What VLANs are allowed across a trunk when the range of allowed VLANs is set to the default value?All VLANs will be allowed across the trunk.*Only the native VLAN will be allowed across the trunk.The switches will negotiate via VTP which VLANs to allow across the trunk. Only VLAN 1 will be allowed across the trunk.17Under which two occasions should an administrator disable DTP while managing a local area network? (Choose two.)on links that should not be trunking*when connecting a Cisco switch to a non-Cisco switch*on links that should dynamically attempt trunkingwhen a neighbor switch uses a DTP mode of dynamic autowhen a neighbor switch uses a DTP mode of dynamic desirable18Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.Which PCs will receive the broadcast sent by PC-C?PC-D, PC-E*PC-A, PC-B, PC-D, PC-EPC-A, PC-BPC-A, PC-B, PC-D, PC-E, PC-FPC-A, PC-B, PC-E19Which two statements are true about VLAN implementation? (Choose two.)The network load increases significantly because of added trunking information.Devices in one VLAN do not hear the broadcasts from devices in another VLAN.*The size of the collision domain is reduced.VLANs logically group hosts, regardless of physical location.*The number of required switches in a network decreases.20Refer to the exhibit. DLS1 is connected to another switch, DLS2, via a trunk link. A host that is connected to DLS1 is not able to communicate to a host that is connected to DLS2, even though they are both in VLAN 99. Which command should be added to Fa0/1 on DLS1 to correct the problem?switchport trunk allowed vlan add 99switchport trunk native vlan 66*switchport mode dynamic autoswitchport nonegotiate21Which switch feature ensures that no unicast, multicast, or broadcast traffic is passed between ports that are configured with this feature?switch port securityPVLAN protected port*ACLVLAN22Fill in the blank. Use the full command syntax.The ” show vlan brief” command displays the VLAN assignment for all ports as well as the existing VLANs on the switch.23Which three statements accurately describe VLAN types? (Choose three).An 802.1Q trunk port, with a native VLAN assigned, supports both tagged and untagged traffic.*A management VLAN is any VLAN that is configured to access management features of the switch.*A data VLAN is used to carry VLAN management data and user-generated traffic.Voice VLANs are used to support user phone and e-mail traffic on a network. VLAN 1 is always used as the management VLAN.After the initial boot of an unconfigured switch, all ports are members of the default VLAN.*24Which command should the network administrator implement to prevent the transfer of DTP frames between a Cisco switch and a non-Cisco switch?S1(config-if)# switchport mode trunkS1(config-if)# switchport mode accessS1(config-if)# switchport nonegotiate*S1(config-if)# switchport mode dynamic desirableS1(config-if)# switchport trunk allowed vlan noneCCNA 2 - Chapter 41What type of IPv6 address is required as a minimum on IPv6 enabled interfaces?staticglobal unicastlink-local*loopbackunique local2In order for packets to be sent to a remote destination, what three pieces of information must be configured on a host? (Choose three.)default gateway*hostnameDNS server addressDHCP server addressIP address*subnet mask*3What two pieces of information are displayed in the output of the show ip interface brief command? (Choose two.)MAC addressesLayer 1 statuses*IP addresses*next-hop addressesinterface descriptionsspeed and duplex settings4Place the options in the following order:next hopdestination networkmetric- not scored -administrative distanceroute timestamproute source protocol- not scored -5Which two items are used by a host device when performing an ANDing operation to determine if a destination address is on the same local network? (Choose two.)destination MAC addressnetwork numberdestination IP address*source MAC addresssubnet mask*6Refer to the exhibit. A network administrator issues the show ipv6 route command on R1. What two conclusions can be drawn from the routing table? (Choose two.)Packets that are destined for the network 2001:DB8:ACAD:2::/64 will be forwarded through Fa0/1.R1 does not know a route to any remote networks.*The interface Fa0/1 is configured with IPv6 address2001:DB8:ACAD:A::12.*Packets that are destined for the network 2001:DB8:ACAD:2::54/128 will be forwarded through Fa0/0.The network FF00::/8 is installed through a static route command.7Refer to the exhibit. What is the purpose of the highlighted field in the line that is displayed from the show ip route command?It indicates that this is a directly connected route.It indicates that this route has been deleted from the routing table. It indicates that this route was learned via EIGRP.*It indicates that this is a default route.8Which two statements correctly describe the concepts of administrative distance and metric? (Choose two.)The metric varies depending which Layer 3 protocol is being routed, such as IP.A router first installs routes with higher administrative distances. The value of the administrative distance can not be altered by the network administrator.Routes with the smallest metric to a destination indicate the best path.* Administrative distance refers to the trustworthiness of a particular route.*The metric is always determined based on hop count.9What are two functions of a router? (Choose two.)It manages the VLAN database.It increases the size of the broadcast domain.It controls the flow of data via the use of Layer 2 addresses.It determines the best path to send packets.*It connects multiple IP networks.*10A packet moves from a host on one network to a device on a remote network within the same company. If NAT is not performed on the packet, which two items remain unchanged during the transfer of the packet from source to destination? (Choose two.)destination MAC addresssource ARP tablesource IP address*destination IP address*source MAC addressLayer 2 header11。
ccna第二学期练习答案

ERouting Chapter 1 - CCNA Exploration: 路由协议和概念 (版本1口令可用于限制对 Cisco IOS 所有或部分内容的访问。
请选择可以用口令保护的模式和接口。
(选择三项。
)VTY 接口控制台接口特权执行模式2路由器从相连的以太网接口收到消息后,会更改哪项报头地址,再将消息从另一个接口发送出去第 2 层源地址和目的地址3请参见图示。
网络管理员已经为路由器连接到直连网络的接口配置了如图所示的 IP 地址。
从路由器 ping 相连网络上的主机口之间相互 ping 都会遭到失败。
此问题最可能的原因是什么必须使用no shutdown命令启用接口。
4请参见图示。
主机 A ping 主机 B。
当 R4 收到对以太网接口的 ping 时,哪两块报头信息包括在内(选择两项。
)目的 IP 地址:目的 MAC 地址:5网络管理员刚把新配置输入 Router1。
要将配置更改保存到 NVRAM,应该执行哪一条命令Router1# copy running-config startup-config6您需要配置图中所示的串行连接,必须在 Sydney 路由器上发出以下哪条配置命令才能与 Melbourne 站点建立连接(选择三Sydney(config-if)# ip addressSydney no shutdownSydney(config-if)# clock rate 560007请参见图示。
从路由器的运行配置输出可得出什么结论显示的命令决定了路由器的当前运行情况。
8请参见图示。
在主机 2 连接到 LAN 上的交换机后,主机 2 无法与主机 1 通信。
导致此问题的原因是什么主机 1 和主机 2 位于不同的网络中。
9输入以下命令的作用是什么R1(config)# line vty 0 4R1(config-line)# password check123R1(config-line)# login设置通过 Telnet 连接该路由器时使用的口令10以下哪一项正确描述了路由器启动时的顺序加载 bootstrap、加载 IOS、应用配置11加载配置文件时的默认顺序是怎样的NVRAM、TFTP、CONSOLE12请参见图示。
CCNA02-final3

1Which of the following are required when adding a network to the OSPF routing process conf iguration? (Choose three.)network addressloopback addressautonomous system numbersubnet maskwildcard maskarea ID2Using default settings, what is the next step in the router boot sequence after t he IOS loads from flash?Perf orm the POST routine.Search for a backup IOS in ROM.Load the bootstrap program f rom ROM.Load the running-config file from RAM.Locate and load the startup-config file from NVRAM.3Refer to the exhibit. What is the most efficient summarization of the routes attached to router R1?198.18.0.0/16198.18.48.0/21198.18.32.0/22198.18.48.0/23198.18.49.0/23198.18.52.0/224Refer to the exhibit. When troubleshooting a network, it is important to interpret the output of various router commands. On the basis of the exhibit, which three statem (Choose three.)The missing information f or Blank 1 is the command show ip route .The missing information f or Blank 1 is the command debug ip route .The missing information f or Blank 2 is the number 100.The missing information f or Blank 2 is the number 120.The missing information f or Blank 3 is the letter R.The missing information f or Blank 3 is the letter C.5Refer to the exhibit. Packets destined to which two networks will require the router to perform a recursive lookup? (Choose t wo.)10.0.0.0/864.100.0.0/16128.107.0.0/16172.16.40.0/24192.168.1.0/24192.168.2.0/246When presented with multiple valid routes to a destination, what criteria does a router use to determine which routes to add to the routing table?The router selects the routes with the best metric. All routes that hav e the same best metric are added to the routing table.The router f irst selects routes with the lowest administrative distance. The resulting routes are then prioritized by metric and the routes with the best metric arouting table.The router selects the routes with the lowest administrativ e distance. All routes with the same lowest administrative distanc e are added to the routing table.The router installs all routes in the routing table but uses the route with the best metric most when load balancing.7Refer to the exhibit. All routers in the network are running RIPv2 and EIGRP with default routing protocol settings and have interfaces configured with the bandwidths t exhibit. Which protocol will be used and how will traffic between the Router1 LAN and Router5 LAN be routed through the network?RIPv2 will load balance across both paths between Router1 and Router5.EIGRP will load balance across both paths between Router1 and Router5.RIPv2 traffic will use the path Router1, Router2, Router5 because it has the least hops.EIGRP traffic will use the path Router1, Router3, Router4, Router5 because it has the best metric.8Of the listed routing protocols, which two will propogate LSPs to all neighbors? (Choose two.)IS-ISEIGRPOSPFRIPv1RIPv29Refer to the exhibit. Routers 1 and 2 are directly connected over a serial link. Pings are f ailing between the two routers. W hat change by the administrator will correctSet the encapsulation on both routers to PPP.Decrease the bandwidth on Serial 0/1/0 on router 2 to 1544.Change the cable that connects the routers to a crossover cable.Change the IP address on Serial 0/1/0 on router 2 to 192.168.0.1/30.10Refer to the exhibit. Which three statements are true of the routing table for Router1? (Choose three.)The route to network 172.16.0.0 has an AD of 156160.Network 192.168.0.16 can best be reached using FastEthernet0/0.The AD of EIGRP routes has been manually changed to a value other than the default value.Router1 is running both the EIGRP and OSPF routing process.Network 172.17.0.0 can only be reached using a default route.No default route has been conf igured.11Which statement correctly describes a feasible successor in EIGRP?It is a primary route that is stored in the routing table.It is a backup route that is stored in the routing table.It is a primary route that is stored in the topology table.It is a backup route that is stored in the topology table.12Refer to the exhibit. A ping from R1 to 10.1.1.2 is successful, but a ping from R1 to 192.168.2.0 fails. What is the cause of this problem?There is no gateway of last resort at R1.The serial interf ace between the two routers is down.A default route is not configured on R1.The static route for 192.168.2.0 is incorrectly conf igured.13Refer to the exhibit. A network administrator has run the show interface command. The output of this command is displayed. What is the first step that is required toSwitch the cable with a known working cable.Issue the no shutdown command on the interface.Configure the interf ace as a loopback interface.Set the encapsulation for the interface.14Which two locations can be the source of the Cisco IOS that is used by a router during the bootup process? (Choose two.)flash memoryRAMNVRAMTFTP serverconfiguration register15All routers in a network are configured in a single OSPF area with the same priority value. No loopback interface has been set on any of the routers. Which secondrouters use to determine the router ID?The highest MAC address among the active interfaces of the network will be used.There will be no router ID until a loopback interf ace is configured.The highest IP address among the activ e FastEthernet interfaces that are running OSPF will be used.The highest IP address among the activ e interfaces will be used.16Refer to the exhibit. A network administrator has conf igured OSPF using the following command:network 192.168.1.32 0.0.0.31 area 0Which router interf ace will participate in OSPF?FastEthernet0/0FastEthernet0/1Serial0/0/0Serial0/0/117Refer to the exhibit. All routers are properly configured with default configurations and are running the OSPF routing protocol. The network is f ully converged. A host on th with a host on the 192.168.2.0/24 network.Which path will be used to transmit the data?The data will be transmitted v ia R3-R2.The data will be transmitted v ia R3-R1-R2.The traffic will be load-balanced between two paths — one via R3-R2, and the other via R3-R1-R2.The data will be transmitted v ia R3-R2, and the other path via R3-R1-R2 will be retained as the backup path.18Which two situations require the use of a link-state protocol? (Choose two.)Fast convergence of the network is critical.The network is very large.The network administrator has limited knowledge to configure and troubleshoot routing protocols.The network is a flat network.The capacity of the router is low.19Refer to the exhibit. What is the meaning of the highlighted value 120?It is the metric that is calculated by the routing protocol.It is the v alue that is used by the DUAL algorithm to determine the bandwidth for the link.It is the administrative distance of the routing protocol.It is the hold-down time, measured in seconds, before the next update.20In a lab test environment, a router has learned about network 172.16.1.0 through four different dynamic routing processes. Which route will be used to reach this nD 172.16.1.0/24 [90/2195456] via 192.168.200.1, 00:00:09, Serial0/0/0O 172.16.1.0/24 [110/1012] via 192.168.200.1, 00:00:22, Serial0/0/0R 172.16.1.0/24 [120/1] via 192.168.200.1, 00:00:17, Serial0/0/0I 172.16.1.0/24 [100/1192] via 192.168.200.1, 00:00:09, Serial0/0/021Which statement is true about the RIPv1 protocol?It is a link-state routing protocol.It excludes subnet information from the routing updates.It uses the DUAL algorithm to insert backup routes into the topology table.It uses classless routing as the default method on the router.22Refer to the exhibit. The 10.4.0.0 network f ails. What mechanism prevents R2 f rom receiving false update information regarding the 10.4.0.0 network?split horizonhold-down timersroute poisoningtriggered updates23Which statement is true about the metrics used by routing protocols?A metric is a value used by a particular routing protocol to compare paths to remote networks.A common metric is used by all routing protocols.The metric with the highest value is installed in the routing table.The router may use only one parameter at a time to calculate the metric.24Refer to the exhibit. Both routers are using the RIPv2 routing protocol and static routes are undef ined. R1 can ping 192.168.2.1 and 10.1.1.2, but is unable to ping 192.16 What is the reason for the ping f ailure?The serial interf ace between two routers is down.R2 is not forwarding the routing updates.The 192.168.4.0 network is not included in the RIP configuration of R2.RIPv1 needs to be configured.25Which statement correctly describes a feature of RIP?RIP is a link-state routing protocol.RIP uses only one metric—hop count— for path selection.Adv ertised routes with hop counts greater than 10 are unreachable.Messages are broadcast every 10 seconds.26Refer to the exhibit. When the show cdp neighbors command is issued f rom router C, which devices will be displayed in the output?B, DA, B, DD, SWH-2SWH-1, A, BSWH-1, SWH-2A, B, D, SWH-1, SWH-227Refer to the exhibit. Although R2 is conf igured correctly, host A is unable to access the Internet. What are two static routes that can be c onfigured on R1, either of which w (Choose two.)ip route 0.0.0.0 0.0.0.0 Fa0/0ip route 0.0.0.0 0.0.0.0 Fa0/1ip route 0.0.0.0 0.0.0.0 10.1.1.1ip route 0.0.0.0 0.0.0.0 10.1.1.2ip route 209.165.202.0 255.255.255.0 10.1.1.128Which component is typically used to connect the WIC interface of a router to a CSU/DSU?V.35 cableRJ-45 adaptercrossover cablestraight-through cable29Refer to the exhibit. Which combination of IP address and subnet mask can be used on the serial interf ace of Router2 in order to put the interf ace in the same networ interface of Router1?IP 172.16.0.18, subnet mask 255.255.255.0IP 172.16.32.15, subnet mask 255.255.255.240IP 172.16.0.18, subnet mask 255.255.255.252IP 172.16.32.18, subnet mask 255.255.255.25230Refer to the exhibit. Which host has a combination of IP address and subnet mask on the same network as Fa0/0 of Router1?host Ahost Bhost Chost D31Refer to the exhibit. OSPF is used f or the routing protocol and all interf aces are configured with the correct IP addresses and subnet masks. During testing, it is foun unable to form an adjacency with R2. What is the cause of this problem?Both routers have been configured with incorrect router IDs.Both routers have been configured in different OSPF areas.Both routers have been configured with an incorrect network type.Both routers have been configured with different hello and dead intervals.32You hav e been asked to explain converged networks to a trainee. How would you accurately describe a converged network?A network is converged when all routers have f ormed an adjacency.A network is converged immediately after a topology change has occurred.A network is converged when all routers flush the unreachable networks from their routing tables.A network is converged after all routers share the same information, calculate best paths, and update their routing tables.33 A network administrator is in charge of two separate networks that share a single building. What dev ice will be required to connect the two networks and add a comthe Internet that can be shared?hubrouteraccess pointEthernet switch34Which port should a terminal emulator be connected to in order to access a router without network connectivity?T1serialconsoleFastEthernet35Refer to the exhibit. What needs to be done to allow these two routers to connect successf ully?Add a clock rate to S0/0/0 on R1.Add an interface description to S0/0/1 on R2.Change the serial interface on R2 to S0/0/0 so that it matches R1.Change the IP address of S0/0/1 on R2 so that it is in the same subnet as R1.36Refer to the exhibit. Based on the partial output in the exhibit, why can users establish a console connection to this router without entering a password?The login command was not entered on the console line.The enable password should be an enable secret password.No username and password combination has been configured.Console connections cannot be conf igured to require users to provide passwords.37Refer to the exhibit. When a static IP address is being configured on the host, what address should be used for the default gateway?10.1.1.110.1.1.2172.16.1.1192.168.1.138Refer to the exhibit. The entire 192.168.1.0 network has been allocated to address hosts in the diagram. Utilizing VLSM with contiguous address blocks, which set of pref ixes could be used to create an addressing solution with a minimum waste of IP addresses?39What is a function of a router?It extends the Layer 2 broadcast domain.It eliminates collisions among PCs on the same local network.It provides connectivity among PCs on the same physical segment.It forwards packets to different IP networks based on Layer 3 inf ormation.40Refer to the exhibit. Which solution provides the most efficient use of router resources for forwarding traffic between BR and HQ?RIPRIPv2EIGRPstatic routes41Refer to the exhibit. A network administrator configures a static route on router R1 to reach the 192.168.1.0/24 network. Which IP address should be used as the next ip route command?192.168.1.1192.168.2.1192.135.250.1192.135.250.242Refer to the exhibit. The network is conf igured with RIPv2. However, network administrators notice that communication cannot be successfully completed f rom one L network administrator issues the show ip route command on the HQ router. Based on the output, what should be done to correct the problem?Disable the load balancing feature of RIPv2.Issue the no auto-summary command for RIPv2.Replace RIPv2 with EIGRP which supports VLSM.Make sure that the network statements include the correct subnet mask.43Which protocol is used by EIGRP to deliver and receive update packets?FTPRTPTCPTFTPUDP44Refer to the exhibit. What OSPF network statements are required for the router B to adv ertise the three networks that are attached?router ospf 1network 10.0.0.0 0.0.0.255 area 0router ospf 1network 10.1.1.0 0.3.255.255 area 0network 10.10.1.0 0.255.255.255 area 0network 10.20.1.0 0.255.255.255 area 0router ospf 1network 10.1.1.0 0.0.0.3 area 0network 10.10.1.0 0.0.255.255 area 0network 10.20.1.0 0.0.255.255 area 0router ospf 1network 10.1.1.0 0.0.0.3 area 0network 10.10.1.0 0.0.0.255 area 0network 10.20.1.0 0.0.0.255 area 045Which two v alues are used by default to calculate a metric in EIGRP? (Choose two.) loaddelayreliabilityhop countbandwidth46Refer to the exhibit. Which statement is true concerning the routing configuration?Using dy namic routing instead of static routing would hav e required f ewer configuration steps.The 10.1.1.0/24 and 10.1.2.0/24 routes have adjacent boundaries and should be summarized.Packets routed to the R2 Fast Ethernet interface require two routing table lookups.The static route will not work correctly.47Refer to the exhibit. On the basis of the show running-config output, which option correctly ref lects the routes that will be listed in the R2 routing table?48Refer to the exhibit. Which command should be issued to configure the address of the router interface that is attached to this computer?Router(config-if)# ip address 192.168.2.1 255.255.255.0Router(config-if)# ip address 192.168.2.2 255.255.255.0Router(config-if)# ip address 192.168.0.1 255.255.255.0Router(config-if)# ip address 192.168.0.2 255.255.255.049Refer to the exhibit. Which route will be removed from the routing table if manual EIGRP summarization is disabled on the Serial0/0/0 interface of Router3?0.0.0.0/0172.16.0.0/16172.16.1.0/24172.16.3.0/3050Refer to the exhibit. All interfaces are addressed and f unctioning correctly. The network administrator runs the tracert command on host A. Which two f acts could be output of this command? (Choose two.)The gateway for Host A is missing or improperly conf igured.The gateway for Host B is missing or improperly conf igured.The entry for 192.168.1.0/24 is missing f rom the routing table of R1.The entry for 192.168.1.0/24 is missing f rom the routing table of R2.The entry for 192.168.2.0/24 is missing f rom the routing table of R1.The entry for 192.168.2.0/24 is missing f rom the routing table of R2.。
CCNA第2期 2a DsmbISP Fina
下列有关FTP 运作的说法中哪一项正确?在DTP(数据传输过程)功能完成后随即启用PI(协议解释程序)功能。
DTP 功能负责控制登录序列。
FTP 需要两条连接,一条用于发送控制信息,一条用于文件数据传输。
传输完成后,PI 和DTP 将自动关闭。
哪种路由协议使用DUAL 算法计算到达目的地的最短路径?OSPFEIGRPRIPBGP请参见图示。
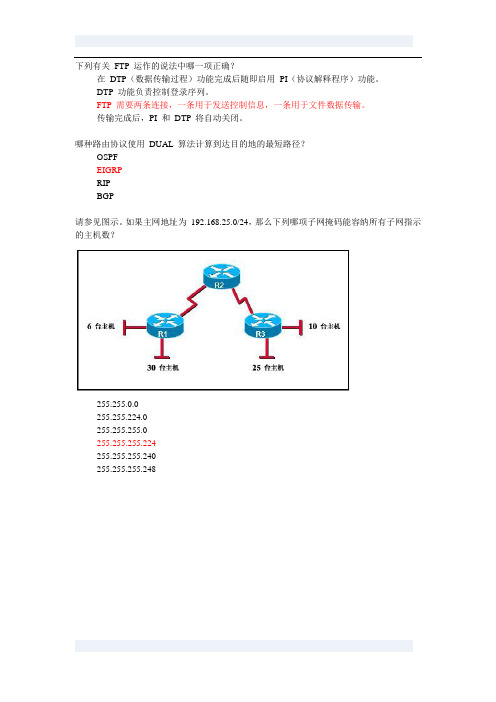
如果主网地址为192.168.25.0/24,那么下列哪项子网掩码能容纳所有子网指示的主机数?255.255.0.0255.255.224.0255.255.255.0255.255.255.224255.255.255.240255.255.255.248请参见图示。
网络管理员使用以下命令在RTB 上配置了一条默认路由:RTB(config)# ip route 0.0.0.0 0.0.0.0 fa0/0PC3 可以成功ping 通RTB。
但是当从PC3 发出的回应请求数据包到达PC1 后,却没有应答返回PC3。
怎样解决此问题?必须对RTA 进行配置,使其可以将数据包转发至192.168.2.0 网络。
需要修改ip route 命令,以便将下一跳地址设置为10.1.1.5。
需要修改ip route 命令,以便将下一跳地址设置为192.168.2.1。
需从RTB 路由器配置中删除ip route 命令。
需要在RTA 上另外配置一条下一跳地址为10.1.1.6 的默认路由。
在图中所示的其中一台路由器上执行show ip route 命令,显示下列输出:C 192.168.4.0/24 is directly connected, Serial0/0R 192.168.5.0/24 [120/1] via 192.168.4.2, 00:00:19, Serial0/0R 192.168.1.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1R 192.168.2.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1C 192.168.3.0/24 is directly connected, Serial0/1此命令是从哪一台路由器执行的?ABCD192.168.17.111/28 属于哪一类地址?主机地址网络地址广播地址组播地址某黑客尝试获取存储在公司网络内部某台服务器上的机密信息。
CCNA02-final2

1 Which of the following are primary functions of a router? (Choose two.)packet switchingmicrosegmentationdomain name resolutionpath selectionflow control2Which three statements are true regarding the encapsulation and de-encapsulation of packets when traveling through a router? (Choose three.)The router modifies the TTL field, decrementing it by one.The router changes the source IP to the IP of the exit interface.The router maintains the same source and destination IP.The router changes the source physical address to the physical address of the exit interface.The router changes the destination IP to the IP of the exit interface.The router sends the packet out all other interfaces, besides the one it entered the router on.3Refer to the exhibit. Which path will traffic from the 172.16.1.0/24 network take to get to the 10.0.0.0/24 network?ADCABCIt will load balance the traffic between ADC and ABCIt will send the traffic via ABC, and will use ADC as a backup path only when ABC fails.4Refer to the exhibit. The network is running the RIP routing protocol. Network 10.0.0.0 goes down. Which statement is true regarding how the routers in this topology event?Router4 will learn about the failed route 30 seconds later in the next periodic update.Split horizon will prevent Router4 from fowarding packets to the 10.0.0.0 network until the holddown timer expires.Router5 immediately flushes the unreachable route from its routing table.Router5 will send Router4 a triggered update with a metric of 16 for network 10.0.0.0.5Refer to the exhibit. Which three statements are true of the routing table for Router1? (Choose three.)The route to network 172.16.0.0 has an AD of 156160.Network 192.168.0.16 can best be reached using FastEthernet0/0.The AD of EIGRP routes has been manually changed to a value other than the default value.Router1 is running both the EIGRP and OSPF routing process.Network 172.17.0.0 can only be reached using a default route.No default route has been configured.6If a router is booting with its default configuration register setting and its NVRAM lacks boot system commands, from where will the router try to load the IOS imageROMRAMNVRAMflashTFTP server7Two routers need to be configured within a single OSPF area. Which two components need to be configured on both routers to achieve this? (Choose two.)the same process IDthe same area IDnetwork addresses and wildcard masksthe same router IDthe same loop back address8Refer to the exhibit. The hosts on the R1 LAN are unable to access the Internet. What is incorrectly configured?the IP address of the Fa0/0 interface at R1the IP address of the S0/0/1 interface at R2the IP address of the S0/0/0 interface at R1the subnet mask of the S0/0/1 interface at R29Refer to the exhibit. Which summarization should R1 use to advertise its networks to R2?192.168.1.0/24192.168.0.0/24192.168.0.0/22192.168.1.0/2210Refer to the exhibit. Host A is unable to access the Internet. What is the reason for this?The IP address of host A is incorrect.The default gateway of host A is incorrect.The Fa0/1 interfaces of the two routers are configured for different subnets.The subnet mask for the Fa0/0 interface of R1 is incorrect.11Refer to the exhibit. A device is required to complete the connection between router R1 and the WAN. Which two devices can be used for this? (Choose two.)a CSU/DSU devicea modeman Ethernet switcha huba bridge12Refer to the exhibit. A network engineer has run the show version command on R3. Upon rebooting, R3 does not load the start-up configuration settings.What could be the cause of this problem?There is insufficient NVRAM.There is insufficient flash memory.The configuration register is not configured with the default setting.The system image file is not located in NVRAM.13Refer to the exhibit. A router learns a route to the 192.168.6.0 network, as shown in the output of the show ip rip database command. However, upon running the sh command, the network administrator sees that the router has installed a different route to the 192.168.6.0 network learned via EIGRP. What could be the reason for th route?Compared to RIP, EIGRP has a lower administrative distance.Compared to EIGRP, RIP has a higher metric value for the route.Compared to RIP, the EIGRP route has fewer hops.Compared to RIP, EIGRP has a faster update timer.14Refer to the exhibit. R1 is configured properly for a single area OSPF, and R2 has been recently installed in the network. Which set of commands is required to confi OSPF for the networks that are connected to R2?R2(config)# router ospf 1R2(config-router)# network 192.168.2.0 0.0.0.255 area 0R2(config-router)# network 10.1.1.0 0.0.0.3 area 0R2(config)# router ospf 1R2(config-router)# network 192.168.2.0 0.0.0.255 area 0R2(config)# router ospf 2R2(config-router)# network 10.1.1.0 0.0.0.3 area 0R2(config)# router ospf 1R2(config-router)# network 192.168.2.0 0.0.0.255 area 0R2(config-router)# network 10.1.1.0 0.0.0.3 area 1R2(config)# router ospf 1R2(config-router)# network 192.168.2.0 0.0.0.255 area 0R2(config-router)# network 10.0.0.0 0.0.0.3 area 115Refer to the exhibit. What information can be determined from the displayed output?EIGRP packets are waiting to be sent to the neighbors.The adjacencies between the routers are yet to be established.The IP address 192.168.10.10 is configured at serial interface S0/0/1 of router R2.Router R2 is receiving hello packets from a neighbor with the IP address 192.168.10.10 via the R2 S0/0/1 interface.16Refer to the exhibit. The interfaces of all routers are configured for OSPF area 0. R3 can ping R1, but the two routers are unable to establish a neighbor adjacency. W network administrator do to troubleshoot this problem?Check if the interfaces of the routers are enabled.Check the hello and dead intervals between the routers.Check the process ID of both routers.Check if CDP is enabled on all the routers.17Refer to the exhibit. A network administrator has configured OSPF using the following command:network 192.168.1.32 0.0.0.31 area 0Which router interface will participate in OSPF?FastEthernet0/0FastEthernet0/1Serial0/0/0Serial0/0/118Which two statements are true for link-state routing protocols? (Choose two.)Routers that run a link-state protocol can establish a complete topology of the network.Routers in a multipoint network that run a link-state protocol can exchange routing tables.Routers use only hop count for routing decisions.The shortest path first algorithm is used.Split horizon is used to avoid routing loops.19Refer to the exhibit. A network administrator adds this command to router R1: ip route 192.168.2.0 255.255.255.0 S0/0/0. What is the result of adding this commandThis route is automatically propagated throughout the network.The traffic for network 172.16.1.0 is forwarded to network 192.168.2.0.A static route is established.The traffic for all Class C networks is forwarded to 172.16.1.2.20Refer to the exhibit. What is the meaning of the highlighted value 120?It is the metric that is calculated by the routing protocol.It is the value that is used by the DUAL algorithm to determine the bandwidth for the link.It is the administrative distance of the routing protocol.It is the hold-down time, measured in seconds, before the next update.21Which statement is true about the RIPv1 protocol?It is a link-state routing protocol.It excludes subnet information from the routing updates.It uses the DUAL algorithm to insert backup routes into the topology table.It uses classless routing as the default method on the router.22Which two technologies can be used in distance vector routing protocols to prevent routing loops? (Choose two.)authenticationlink-state advertisementshold-down timersSpanning Tree Protocolsplit horizon23Refer to the exhibit. PC1 is unable to access the Internet. What is the cause of the problem?An incorrect IP address is configured between the two routers.No static route is configured on Router2.A routing loop has occurred.No routing protocol is configured on either of the two routers.24Which mechanism helps to avoid routing loops by advertising a metric of infinity?route poisoningsplit horizonhold-down timertriggered updates25Which statement is true about the metrics used by routing protocols?A metric is a value used by a particular routing protocol to compare paths to remote networks.A common metric is used by all routing protocols.The metric with the highest value is installed in the routing table.The router may use only one parameter at a time to calculate the metric.26Which two statements are true about the EIGRP successor route? (Choose two.)It is saved in the topology table for use if the primary route fails.It may be backed up by a feasible successor route.It is used by EIGRP to forward traffic to the destination.It is flagged as active in the routing table.After the discovery process has occurred, the successor route is stored in the neighbor table.27In which situation would a default static route be recommended?when connecting an edge router to the Internetwhen variable length subnet masking is in effectwhen there is more than one valid route for a destination networkwhen a destination network has a larger mask than any routes in the routing table28Refer to the exhibit. A technician has configured the interfaces on the Router, but upon inspection discovers that interface FastEthernet0/1 is not functioning. Which ac correct the problem with FastEthernet0/1?A clock rate should be added to the interface configuration.The subnet mask should be added to the interface configuration.An interface description needs to be added to the interface configuration.The no shutdown command needs to be added to the interface configuration.29Refer to the exhibit. Which combination of IP address and subnet mask can be used on the serial interface of Router2 in order to put the interface in the same networ interface of Router1?IP 172.16.0.18, subnet mask 255.255.255.0IP 172.16.32.15, subnet mask 255.255.255.240IP 172.16.0.18, subnet mask 255.255.255.252IP 172.16.32.18, subnet mask 255.255.255.25230 A network administrator is analyzing routing update behavior on a network that has both EIGRP and OSPF configured on all routers. Both protocols appear in the oprotocols. However, only EIGRP internal routes appear in the routing tables. Which statement correctly explains the scenario?The OSPF protocol has a higher cost than EIGRP.The EIGRP protocol has a lower metric than OSPF.The EIGRP protocol was configured first on the router.The EIGRP protocol has a lower administrative distance than OSPF.31Which prompt is used to allow a user to change the IP address of an interface on a router?Router>Router#Router(config)#Router(config-if)#32Refer to the exhibit. R1 and R2 are adjacent routers both running RIP. All interfaces on both routers are correctly configured and operational. Both routers are configu connected interfaces in routing updates. R2 is not showing any routes from R1 in the routing table. What is the likely cause?The adjacent interfaces are passive.The distance of 120 exceeds 15 hops.R2 will not accept version 1 updates from R1.Routes are being summarized by R1 but not by R2.33 A network administrator is in charge of two separate networks that share a single building. What device will be required to connect the two networks and add a comthe Internet that can be shared?hubrouteraccess pointEthernet switch34 A network administrator must use the subnet 172.16.128.0/18 to create 6 additional subnets each containing up to 2000 hosts for local LANs. Which subnet mask sadministrator use to create the new subnets?255.255.224.0255.255.240.0255.255.248.0255.255.252.035Because of a topology change, the next hop IP address in the current static route must be reconfigured. How can a static route entry be altered to accommodate aKeep the existing static route and configure a new static route with the correct next hop IP address.Negate the existing static route and configure a new static route with the correct next hop IP address.Do nothing. The existing static route will automatically update the next hop entry with the new IP address.Keep the existing static route, reload the router, and configure a new static route with the correct next hop IP address.36Refer to the exhibit. What needs to be done to allow these two routers to connect successfully?Add a clock rate to S0/0/0 on R1.Add an interface description to S0/0/1 on R2.Change the serial interface on R2 to S0/0/0 so that it matches R1.Change the IP address of S0/0/1 on R2 so that it is in the same subnet as R1.37Refer to the exhibit. Based on the partial output in the exhibit, why can users establish a console connection to this router without entering a password?The login command was not entered on the console line.The enable password should be an enable secret password.No username and password combination has been configured.Console connections cannot be configured to require users to provide passwords.38Refer to the exhibit. Host A is having problems accessing server A. All routers have the same EIGRP configuration as router RTR_A. What should be done so that ho server A?Add the command no auto-summary on all routers.Change the network statements to include a wildcard mask.Adjust the EIGRP hello timers to account for the network delay.Add the command eigrp log-neighbor-changes on all routers.39Refer to the exhibit. The network administrator has run the following command on R1.R1(config)# ip route 192.168.2.0 255.255.255.0 172.16.1.2What is the result of running this command?Traffic for network 192.168.2.0 is forwarded to 172.16.1.2.This route is automatically propagated throughout the entire network.Traffic for all networks is forwarded to 172.16.1.2.The command invokes a dynamic routing protocol for 192.168.2.0.40What are two ways that a router can learn of the paths to destination networks? (Choose two.)updates from other routersDHCP information broadcastsmanual configuration of routesARP requests from connected routersinspection of the destination IP address in data packetsupdates from the SMTP management information base41Why is fast convergence desirable in networks that use dynamic routing protocols?Hosts are unable to access their gateway until the network is converged.Routers will not allow packets to be forwarded until the network is converged.Routers may make incorrect forwarding decisions until the network has converged.Routers will not allow configuration changes to be made until the network has converged.42A router learns about network 192.168.10.128/27 from multiple sources. Which option represents the best route and will be placed in the routing table?S 192.168.10.128/27 [1/0] via 192.168.10.226R 192.168.10.128/27 [120/2] via 192.168.10.226, 00:00:14, Serial0/0/0O 192.168.10.128/27 [110/1563] via 192.168.10.226, 00:00:09, Serial0/0/0D 192.168.10.128/27 [90/21026560] via 192.168.10.226, 00:00:16, Serial0/0/043Which candidate route has the longest match for a packet with a destination address of 10.30.16.48?10.30.0.0/1610.30.15.0/2310.30.16.0/2410.30.16.32/2710.30.16.32/3044Which feature of RIPv2 enables it to function as a classless routing protocol?Subnet masks are included in routing updates.Routing updates are triggered by topology changes.Next-hop addresses are included in routing updates.Multicast addresses are used to send routing updates.45Refer to the exhibit. The network has three connected routers: R1, R2, and R3. The routes of all three routers are displayed. All routers are operational and pings are network.Which ping will fail?from R1 to 172.16.1.1from R1 to 192.168.3.1from R2 to 192.168.1.1from R2 to 192.168.3.146 A technician configures the Fa0/0 interface on a router with ip address 192.168.3.5 255.255.255.252. What additional command must be issued by the technicianinterface to forward traffic?Router(config-if)# exitRouter(config-if)# no shutdownRouter(config-if)# clock rateRouter# copy running-config startup-config47Refer to the exhibit. On the basis of the show running-config output, which option correctly reflects the routes that will be listed in the R2 routing table?48Refer to the exhibit. A router interface is configured with the command ip address 172.16.3.31 255.255.192.0. Which set of addressing values would allow a compute to the router interface to communicate with remote networks?A: 172.16.3.254 B: 255.255.192.0 C: 172.16.3.31A: 172.16.3.31 B: 255.255.192.0 C: 172.16.3.255A: 172.16.3.254 B: 255.255.255.0 C: 172.16.3.31A: 172.16.3.31 B: 255.255.255.0 C: 172.16.3.149Refer to the exhibit. Packets destined to which two networks will require the router to perform a recursive lookup? (Choose two.)10.0.0.0/864.100.0.0/16128.107.0.0/16172.16.40.0/24192.168.1.0/24192.168.2.0/2450Refer to the exhibit. When all of the commands that are shown in the exhibit are entered at the correct router prompt, what is the name of the router?nameciscorouterhostname。
2.计算机网络原理第二章课后习题及答案

第二章1. (Q2)For a communication session between a pair of processes, which process is the client and which is the server?Answer:The process which initiates the communication is the client; the process that waits to be contacted is the server..2. (Q3) What is the difference between network architecture and application architecture?Answer:Network architecture refers to the organization of the communication processintolayers (e.g., the five-layer Internet architecture). Application architecture, on the other hand, is designed by an application developer and dictates the broadstructure of the application (e.g., client-server or P2P)3. (Q4) What information is used by a process running on one host to identify a process running on another host?Answer: The IP address of the destination host and the port number of the destinationsocket.4. (Q6) Referring to Figure 2.4, we see that none of the application listed in Figure 2.4 requires both no data loss and timing. Can you conceive of an application that requires no data loss and that is also highly time-sensitive?Answer: There are no good example of an application that requires no data loss and timing.If you know of one, send an e-mail to the authors5. (Q9) Why do HTTP, FTP, SMTP, and POP3 run on top of TCP rather than on UDP?Answer: The applications associated with those protocols require that all application databe received in the correct order and without gaps. TCP provides this servicewhereas UDP does not.6. (Q11) What is meant by a handshaking protocol?Answer: A protocol uses handshaking if the two communicating entities first exchangecontrol packets before sending data to each other. SMTP uses handshaking at theapplication layer whereas HTTP does not.7. (Q13) Telnet into a Web server and send a multiline request message. Include in the request message the If-modified-since: header line to force a response message with the 304 Not Modified status code.Answer: Issued the following command (in Windows command prompt) followed by theHTTP GET message to the “” web server:> telnet 80Since the index.html page in this web server was not modified since Fri, 18 May2007 09:23:34 GMT, the following output was displayed when the abovecommands were issued on Sat, 19 May 2007. Note that the first 4 lines are theGET message and header lines input by the user and the next 4 lines (startingfrom HTTP/1.1 304 Not Modified) is the response from the web server.8. (Q14) Consider an e-commerce site that wants to keep a purchase record for each of its customers. Describe how this can be done with cookies.Answer: When the user first visits the site, the site returns a cookie number. This cookie number is stored on the user’s host and is managed by the browser. During each subsequent visit (and purchase), the browser sends the cookie number back to the site. Thus the site knows when this user (more precisely, this browser) is visiting the site.9. (Q15) Suppose Alice, with a Web-based e-mail account (such as Hotmail or gmail), sends a message to Bob, who accesses his mail from his mail server using POP3. Discuss how the message gets from Alice’s host to Bob’s host. Be sure to list the series of application-layer protocols that are used to move the message between the two hosts.Answer: Message is sent from Alice’s host to her mail server over HTTP. Alice’s mail server then sends the message to Bob’s mail server over SMTP. Bob then transfers the message from his mail server to his host over POP3.10. (Q10) Recall that TCP can be enhanced with SSL to provide process-to-process securityservices, including encryption. Does SSL operate at the transport layer or the application layer? If the application developer wants TCP to be enhanced with SSL, what does the developer have to do?Answer: SSL operates at the application layer. The SSL socket takes unencrypted data fromthe application layer, encrypts it and then passes it to the TCP socket. If theapplication developer wants TCP to be enhanced with SSL, she has to include theSSL code in the application.11. (Q16) Print out the header of an e-mail message you have recently received. How manyReceived: header lines are there? Analyze each of the header lines in the message.Answer: from 65.54.246.203 (EHLO )Received:(65.54.246.203) by with SMTP; Sat, 19 May 2007 16:53:51 -0700from ([65.55.135.106]) by Received: with Microsoft SMTPSVC(6.0.3790.2668); Sat, 19 May 2007 16:52:42 -0700 Received: from mail pickup service by with Microsoft SMTPSVC; Sat,19 May 2007 16:52:41 -0700Message-ID: <*******************************************>Received: from 65.55.135.123 by with HTTP; Sat, 19 May 2007 23:52:36 GMTFrom: "prithuladhungel"<***************************>To: ******************Bcc:Subject: Test mailDate: Sat, 19 May 2007 23:52:36 +0000Mime-Version:1.0Content-Type: Text/html; format=flowedReturn-Path: ***************************Figure: A sample mail message headerReceived: This header field indicates the sequence in which the SMTP serverssend and receive the mail message including the respective timestamps.In this example there are 4 “Received:” header lines. This means the mailmessage passed through 5 different SMTP servers before being delivered to thereceiver’s mail box. The la st (forth) “Received:” header indicates the mailmessage flow from the SMTP server of the sender to the second SMTP server inthe chain of servers. The sender’s SMTP server is at address 65.55.135.123 andthe second SMTP server in the chain is .The third “Received:” header indicates the mail message flow from the secondSMTP server in the chain to the third server, and so on.Finally, the first “Received:” header indicates the flow of the mail message fromthe forth SMTP server to t he last SMTP server (i.e. the receiver’s mail server) inthe chain.Message-id: The message has been given this*************************************************(bybay0-omc3-s3.bay0.hotmail.com. Message-id is a unique string assigned by the mail systemwhen the message is first created.From: This indicates the email address of the sender of the mail. In the givenexample,**************************************To: This field indicates the email address of the receiver of the mail. In theexample, the ****************************Subject: This gives the subject of the mail (if any specified by the sender). In theexample, the subject specified by the sender is “Test mail”Date: The date and time when the mail was sent by the sender. In the example,the sender sent the mail on 19th May 2007, at time 23:52:36 GMT.Mime-version: MIME version used for the mail. In the example, it is 1.0.Content-type: The type of content in the body of the mail message. In theexample, it is “text/html”.Return-Path: This specifies the email address to which the mail will be sent if thereceiver of this mail wants t o reply to the sender. This is also used by the sender’smail server for bouncing back undeliverable mail messages of mailer-daemonerror messages. In the example, the return path is“***************************”.12. (Q18) Is it possible for an organizat ion’s Web server and mail server to have exactly thesame alias for a hostname (for example, )? What would be the type for the RR that contains the hostname of the mail server?Answer: Yes an organization’s mail server and Web server can have the sa me alias for ahost name. The MX record is used to map the mail server’s host name to its IPaddress.13. (Q19) Why is it said that FTP sends control information “out-of-band”?Answer:FTP uses two parallel TCP connections, one connection for sending controlinformation (such as a request to transfer a file) and another connection foractually transferring the file. Because the control information is not sent over thesame connection that the file is sent over, FTP sends control information out ofband.14. (P6) Consider an HTTP client that wants to retrieve a Web document at a given URL. The IPaddress of the HTTP server is initially unknown. What transport and application-layer protocols besides HTTP are needed in this scenario?Answer:Application layer protocols: DNS and HTTPTransport layer protocols: UDP for DNS; TCP for HTTP15. (P9) Consider Figure2.12, for which there is an institutional network connected to theInternet. Suppose that the average object size is 900,000 bits and that the average request rate from the institution’s browsers to the origin servers is 10 requests per second. Also suppose that the amount of time it takes from when the router on the Internet side of the access link forwards an HTTP request until it receives the response is two seconds on average (see Section 2.2.5).Model the total average response times as the sum of the average access delay (that is, the delay from Internet router to institution router) and the average Internet delay. For the average access delay, use △/(1-△β), where △is the average time required to send an object over the access link and βis the arrival rate of objects to the access link.a. Find the total average response time.b. Now suppose a cache is installed in the institutional LAN. Suppose the hit rate is 0.6. Findthe total response time.Answer:a.The time to transmit an object of size L over a link or rate R is L/R. The average timeisthe average size of the object divided by R:Δ= (900,000 bits)/(1,500,000 bits/sec) = 0.6 secThe traffic intensity on the link is (1.5 requests/sec)(0.6 sec/request) = 0.9. Thus, theaverage access delay is (0.6 sec)/(1 - 0.9) = 6 seconds. The total average response timeis therefore 6 sec + 2 sec = 8 sec.b.The traffic intensity on the access link is reduced by 40% since the 40% of therequestsare satisfied within the institutional network. Thus the average access delayis(0.6 sec)/[1–(0.6)(0.9)] = 1.2 seconds. The response time is approximately zero iftherequest is satisfied by the cache (which happens with probability 0.4); the averageresponse time is 1.2 sec + 2 sec = 3.2 sec for cache misses (which happens 60% of thetime). So the average response time is (0.4)(0 sec) + (0.6)(3.2 sec) = 1.92 seconds.Thusthe average response time is reduced from 8 sec to 1.92 sec.16. (P12) What is the difference between MAIL FROM: in SMTP and From: in the mail messageitself?Answer: The MAIL FROM: in SMTP is a message from the SMTP client that identifies the senderof the mail message to the SMTP server. TheFrom: on the mail message itself is NOTanSMTP message, but rather is just a line in the body of the mail message.17. (P16) Consider distributing a file of F = 5 Gbits to N peers. The server has an upload rate ofu s = 20 Mbps, and each peer has a download rate of d i =1 Mbps and an upload rate of u. For N = 10, 100, and 1,000 and u = 100 Kbps, 250 Kbps, and 500 Kbps, prepare a chart giving the minimum distribution time for each of the combinations of N and u for both client-server distribution and P2P distribution.Answer:For calculating the minimum distribution time for client-server distribution, we use thefollowing formula:D cs = max {NF/u s , F/d min }Similarly, for calculating the minimum distribution time for P2P distribution, we use thefollowing formula:D P 2P = max {F /u s ,F /d min ,NF /( u s + u i n i =1 )} Where,F = 5 Gbits = 5 * 1024 Mbits u s = 20 Mbps d min = d i = 1 MbpsClient Server:N 10 100 1000 200 Kbps10240 51200 512000 u 600 Kbps10240 51200 512000 1Mbps10240 51200 512000Peer to Peer:N 10 100 1000 200 Kbps10240 25904.3 47559.33 U 600 Kbps10240 13029.6 16899.64 1 Mbps10240 10240 10240。
CCNA学习指南第2章复习题中英文翻译版

CCNA学习指南第2章复习题中英文翻译版1. What are the decimal and hexadecimal equivalents of the binary number 10011101?(Choose two.)1. 二进制数10011101等效的十进制和十六进制数分别是多少?(选择两项。
)A. 159B. 157C. 185D. 0x9DE. 0xD9F. 0x1592. Which of the following allows a router to respond to an ARP request that is intended for a remote host?2. 下列哪一项允许路由器对远端主机的ARP请求做出响应?A. Gateway DP网关DPB. Reverse ARP (RARP)反向ARPC. Proxy ARP代理ARPD. Inverse ARP逆向ARPE. Address Resolution Protocol (ARP)地址解析协议3. You want to implement a mechanism that automates the IP configuration, including IP address, subnet mask, default gateway, and DNS information. Which protocol will you use to accomplish this?3. 你想实现自动IP配置,包括IP地址,子网掩码,默认网关和DNS信息。
你应该使用什么协议来完成这?A. SMTP简单传输协议B. SNMP简单网络管理协议C. DHCP动态主机控制协议D. ARP地址解析协议4.What protocol is used to find the hardware address of a local device?4. 什么协议用来找本地设备的硬件地址?A.RARPB. ARPC. IPD. ICMPE. BootP5. Which of the following are layers in the TCP/IP model? (Choose three.)5. 下列哪些层属于TCP/IP模型?(选择三项。
CCNA第二学期第二章考试答案

以下是针对您未获得满分的试题给出的反馈。
某些交互式试题可能不显示您的答案。
分项分数:1哪个接口是包含用于管理24 个端口以太网交换机的IP 地址的默认位置?正确响应您的响应VLAN 1Fa0/0Fa0/1连接到默认网关的接口VLAN 99此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.1 使用初始设置配置交换机2下列关于使用全双工快速以太网的陈述中,哪三项是正确的?(请选择三项。
)正确响应您的响应通过双向数据流改善了性能。
由于禁用了设备上的冲突检测功能,因此性能得到了改善。
节点以全双工单向数据流运行。
由于网卡可以检测到冲突,因此性能得到了改善。
全双工快速以太网在两个方向上提供100% 的效率。
由于网卡能更快速地处理帧,因此延迟减少了。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.2 配置交换机端口3使用mdix auto 配置命令会对交换机上的以太网接口产生什么影响?正确响应您的响应自动检测双工设置自动检测接口速度自动检测铜电缆类型自动将第一个检测到的MAC 地址分配给接口此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.2 配置交换机端口4在Cisco IOS 软件无法加载的情况下,网络管理员需要哪种类型的电缆将PC 与交换机连接才能恢复它?正确响应您的响应同轴电缆控制台电缆交叉电缆直通电缆因为交换机上没有运行Cisco IOS 软件,所以管理员需要使用控制台电缆将PC 连接到交换机控制台端口,比便将来自PC 的软件转移到交换机。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.1 使用初始设置配置交换机5在对连接问题进行故障排除时,网络管理员发现交换机端口状态LED 在绿色和琥珀色之间跳转。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
第二章静态路由CCNA2 Exploration: 路由协议和概念(版本(2010-12-19 13:03:52)标签:分类:窗体顶端ERouting Chapter 2 - CCNA Exploration: 路由协议和概念(版本哪两项说法描述了CDP 的功能或特点?(选择两项。
)它会自动启动,允许设备检测使用CDP 的直连邻居设备。
它运行在网络层,允许两个系统彼此获知对方。
它会创建整个网络的拓扑图。
它允许系统彼此之间相互了解,而无论它们所配置的网络层协议是否相同。
它转发有关路由的通告,以加速收敛过程。
窗体顶端两个独立子网上的主机之间无法通信。
网络管理员怀疑其中一个路由表中缺少路由。
可以使用哪三条命令来3 层连通性问题?(选择三项。
)pingshow arptracerouteshow ip routeshow controllersshow cdp neighbor窗体顶端路由器配置有到达每个目的网络的静态路由。
下列哪两种情况需要管理员变更该路由器上配置的静态路由项。
)目的网络不再存在。
目的网络移到同一路由器的不同接口。
源和目的之间的路径已升级为带宽更高的链路。
出于维护目的,远程目的网络接口需要关闭15 分钟。
拓扑结构发生变化,导致现有的下一跳地址或送出接口无法访问。
窗体底端窗体顶端网络管理员在Router1 中输入了以下命令:ip route S0/1/0。
Router1 随后收到发往的数据包。
在路由表刚配置的静态路由之后,Router1 接下来将如何处理该数据包?丢弃该数据包,因为路由表中未列出目的主机查找S0/1/0 接口的MAC 地址以确定新帧的目的MAC 地址在转发该数据包之前递归查找S0/1/0 接口的IP 地址将该数据包封装到适合该WAN 链路的帧中,并将其从S0/1/0 接口转发出去窗体底端窗体顶端请参见图示。
目的地为网络的数据包会被如何转发?Router1 会执行递归查找,数据包将从S0/0 接口发出。
Router1 会执行递归查找,数据包将从S0/1 接口发出。
没有与网络关联的匹配接口,因此数据包将被丢弃。
没有与网络关联的匹配接口,因此数据包将采用“最后选用网关”,从S0/2 接口发出。
窗体底端窗体顶端请参见图示。
根据如图所示的输出,该链路的时钟频率会如何确定?此频率将由两台路由器协商得出。
由于DCE/DTE 连接错误,因此不会选择任何频率。
DTE 上配置的频率决定了时钟频率。
DCE 上配置的频率决定了时钟频率。
窗体底端窗体顶端Router# show cdp neighbors 命令会显示下列哪些内容?(选择三项。
)负载平台可靠性保持时间本地接口窗体底端窗体顶端为什么在创建送出接口为以太网络的静态路由时输入下一跳IP 地址是明智之举?添加下一跳地址将使路由器在转发数据包时不再需要在路由表中进行任何查找。
在多路访问网络中,如果没有下一跳地址,路由器将无法确定以太网帧的下一跳MAC 地址。
在静态路由中使用下一跳地址可以为路由提供较低的度量。
在多路访问网络中,在静态路由中使用下一跳地址可以使该路由成为候选默认路由。
窗体底端窗体顶端当外发接口不可用时,路由表中的静态路由条目有何变化?该路由将从路由表中删除。
路由器将轮询邻居以查找替用路由。
该路由将保持在路由表中,因为它是静态路由。
路由器将重定向该静态路由,以补偿下一跳设备的缺失。
窗体底端窗体顶端指向下一跳IP 的静态路由在路由表中会显示怎样的管理距离和度量?管理距离为0,度量为0管理距离为0,度量为1管理距离为1,度量为0管理距离为1,度量为1窗体底端窗体顶端以下有关CDP 和图示的说法中,哪项是正确的?路由器D 上运行的CDP 会收集有关路由器A、B、C 和E 的信息。
默认情况下,路由器A 将从路由器B 和 C 接收CDP 通告。
如果路由器D 和E 运行的路由协议不同,那么它们不会交换CDP 信息。
路由器E 可以使用CDP 来识别路由器B 上运行的IOS。
窗体底端窗体顶端哪一个地址可以用来总结从到的所有网络?窗体底端窗体顶端图中的路由器使用如图所示的子网分配。
对Router3 而言,要将内部网络通告给网云,最有效的路由总结是和和和窗体底端窗体顶端请参见图示。
要使WinterPark 和Altamonte 路由器能够传送来自每个LAN 的数据包并将所有其它流量转应该使用哪一组命令来配置静态路由?WinterPark(config)# ip route 0.0.0.0 Altamonte(config)# ip routeAltamonte(config)# ip route s0/1WinterPark(config)# ip route 0.0.0.0 Altamonte(config)# ip routeAltamonte(config)# ip route s0/1WinterPark(config)# ip route WinterPark(config)# ip route 0.0.0.0 Altamonte(config)# ip routeip routeAltamonte(config)# ip routeAltamonte(config)# ip route 0.0.0.0 s0/0窗体底端窗体顶端请参见图示。
公司的网络工程师收到任务,要在两个以太网之间建立连通性,使10.1.1.0/24 子网上的主机上的主机通信。
该工程师被告知公司路由器只能使用静态路由。
使用下列哪一组命令可以在这两个以太网接?R1(config)# ip route 10.1.2.0R2(config)# ip routeip route 10.1.2.0R2(config)# ip routeip route 10.1.1.0R2(config)# ip routeip route 10.1.1.0R2(config)# ip routeip route 0.0.0.0R2(config)# ip route窗体底端窗体顶端请参见图示。
下列哪两条命令会将10.0.0.0/8 网络的下一跳地址从更改为?(选择两项。
)A(config)# no network 10.0.0.0no ip address 10.0.0.1no ip route 10.0.0.0ip route 10.0.0.0 s0/0/0A(config)# ip route 10.0.0.0窗体底端窗体顶端通过检查show ip interface brief 命令的输出可得到什么信息?接口速度和双工设置接口MTU错误接口MAC 地址接口IP 地址窗体底端窗体顶端请参见图示。
在到达10.0.0.0 网络的路由中,/8 表示什么意思?它表示该路由器与10.0.0.0 网络之间有8 跳。
它表示发送到10.0.0.0 网络的ping 得到应答所需的时间(毫秒)。
它表示路由器可将数据包转发到带有8 个子网的目的网络。
它表示在数据包目的IP 地址中,从左开始有多少个连续比特位必须与10.0.0.0 匹配才能使用这条路由窗体底端窗体顶端Router# show interfaces serial 0/1 命令的输出显示了如下内容:Serial0/1 is up, line protocol is down.线路协议为down(关闭)的原因最可能是什么?Serial0/1 为关闭状态。
路由器未连接电缆。
远程路由器正在使用serial 0/0 接口。
尚未设置时钟频率。
窗体底端窗体顶端请参见图示。
要使和10.0.0.0 网络之间连通并且无需递归查找,需要使用下列哪两条命令?(选择两项。
A (config)# ip route 10.0.0.0 s 0/1/0A(config)# ip route 10.0.0.0(config)# ip route 10.0.0.0 s 0/0/0B(config)# ip route s 0/0/0B (config)# ip routeip route s 0/1/0窗体底端窗体顶端请参见图示。
为使主机A 能够连接到网络上的主机B,应在Router1 上配置哪种静态路由?ip routerouteroute S0/0/1百度文库- 让每个人平等地提升自我11ip route S0/0/0窗体底端窗体顶端哪两种设备负责将来自W AN 服务提供商的数据转换为路由器可以接受的形式?(选择两项。
)路由器的串行端口调制解调器交换机路由器的以太网端口CSU/DSU 设备DTE 设备窗体底端。
