Analysis of system trustworthiness based on information flow noninterference theory
《安全工程专业外语》考试复习资料 重点段落或者句子翻译

UNIT 11 Accident causation models事故致因理论The most important aim of safety management is to maintain and promote workers’health and safety at work. Understanding why and how accidents and other unwanted events develop is important when preventive activities are planned. Accident theories aim to clarify the accident phenomena, and to explain the mechanisms that lead to accidents. All modern theories are based on accident causation models which try to explain the sequence of events that finally produce the loss.安全管理的最重要的目的是维护和促进作业人员的工作健康和安全。
在制定预防措施时,了解事故和其他有害事件的原因,以及它们如何发展是非常重要的。
事故理论的目的是刻画事故的现象,并解释导致事故发生的机制。
所有现代的理论都是基于事故的因果关系模型,改模型试图解释最终产生损失的事件序列。
In ancient times, accidents were seen as an act of God and very little could be done to prevent them. In the beginning of the 20th century, it was believed that the poor physical conditions are the root causes of accidents.在古代,事故被看作是上帝的行为,人们很少可以去防止它们。
楼宇自控系统(BAS)

楼宇自控系统(BAS)Post By:2010/5/6 16:44:00 [只看该作者]摘要:楼宇自动化系统(BAS)又称建筑设备自动化系统,主要是用以对建筑物内的空调系统、给排水系统、照明系统、变配电系统以及电梯等系统设备进行集中监视、控制与管理的综合系统,一般为集散结构,即分散控制、集中管理;它是能否为人们提供一健康、舒适、高效的建筑环境的关键,故该系统的设计对一智能化大厦而言举足轻重。
关键词:BAS系统智能化1 引言智能化大厦是写字楼等公共建筑发展的一个趋势,是科技高度发展的结晶。
它由三个子系统组成:楼宇自动化系统(Building Aut omation System)、通讯自动化系统(Communication Automation S ystem)和办公自动化系统(Office Automation System)。
在国内,又将消防自动化系统(Fire Automation System) 和安保自动化系统(S ecurity Automation System)从楼宇自动化系统中独立出来,构成智能化大厦的五个子系统,这就是通常所说的5A智能化大厦。
楼宇自动化系统(BAS)又称建筑设备自动化系统,主要是用以对建筑物内的空调系统、给排水系统、照明系统、变配电系统以及电梯等系统设备进行集中监视、控制与管理的综合系统,一般为集散结构,即分散控制、集中管理;它是能否为人们提供一健康、舒适、高效的建筑环境的关键,故该系统的设计对一智能化大厦而言举足轻重。
2 是否采用BAS系统是否采用BAS系统,是建筑发展商和设计工程师首先要面对的问题,一般可以从以下几个方面考虑:(1)特别重要的,且具有—定规模的建筑,为保证其所属设备及安全系统具有较高的可靠性要求可以考虑采用BAS系统;(2)BAS系统的一次性投资能控制在项目总投资2%以下时可以考虑采用BAS系统;(3)能耗较大的建筑(如上万平方米,采用全空调系统的建筑),BA S系统的初投资可以在五年内收回时可以考虑采用BAS系统;(4)多功能的大型租赁性建筑可以考虑采用BAS系统;(5)当设备的控制与管理比较复杂,人工手动方式难以完成,必须依靠汁算机控制时,可以考虑采用BAS系统;(6)当采用BAS系统时,其投资与可靠性综合指标优于其他可采用的系统时,可以考虑采用BAS系统3 BAS系统的优点与目前工程中存在的问题3.1 BAS系统具有如下优点:(1)提高大楼的管理水平现代化的大楼,设备众多,且散落于大楼的各个角落,大楼的设备管理相当困难,有些设备如吊装于吊顶内部的新风机组,其送风温度靠人根本无法调节,BAS则可很容易地解决这些问题,使大楼的设备管理维持在一个较高水平;(2)降低工作人员的劳动量现代化大楼里的众多设备,依靠人力维持日常检修,劳动量巨大,需要相当多的工作人员,BAS系统则能自动诊断设备是否发生故障,因而只需少量工作人员即可维护设备管理;(3)节约能耗BAS系统通过及时调整大楼内设备的运行状况和数量,关闭不需要运行的设备,可以节约大量能耗。
安全系统工程专业英语

一、专业词汇翻译Accident Causation Models:事故致因模型Safety Policy and Planning:安全方针和计划Accident causation theory:事故致因理论Poor physical conditions:物的不安全状况Accident-proneness model:事故倾向模型Social security system :社会保障体系Accident reporting system:意外呈报制度Occupational illness:职业病System safety:系统安全Safety Engineering:安全工程System safety engineering:系统安全工程System safety program:系统安全规划Hazard analysis:危害分析Hazard identification:危险源辨识Hazard control:危险源控制Hazard evaluation:危险源评价Logical reasoning process 逻辑推理过程Warning device 报警装置Ergonomics process 人机工程过程Ergonomics committee 人机工程委员会Job site 工作现场Musculoskeletal disorder 肌股失常Chain of command 行政管理系统Hazard prevention and control 灾害预防与控制Hazard Identification 危险源辨识PPE(personal protective equipment)个人防护设备OSHA(Occupational Safety and Health Act)职业安全与健康条例planning and accountability 计划与职责planning and review 计划与评审budgetary constraint 预算限制Occupational Health and Safety Management System 职业健康安全管理系统Implementation method 实施方法System characteristic 系统特性systematic management 系统化管理Industrial Hygiene 工业卫生Cosmic ray 宇宙射线Terrestrial radiation 地面辐射Material Safety Data Sheet 物质安全技术说明书Hazard Communication Standard 危害通识标准Physical hazards 物理危险源safety culture 安全文化corporate culture 企业文化reciprocal relationship:互反关系organisational goals 组织目标Physiological needs 生理需求Safety needs 安全需求Social needs 社会需求Ego needs 自我需求Self-fulfillment 自我满足,自我实现Principle of motivation 激励原则Accident Investigation:事故调查After-the-fact approach to hazard identification 事后事后危险源辨识方法fact-finding process 寻找事实过程affixing blame 追究责任accident investigation procedure 事故调查程序Safety Electricity 电气安全Electrical shock 电击Groundfault Circuit interrupt:接地故障断路器First aid:急救Artificial ventilation(respiration):人工呼吸Cardio-pulmonary Resuscitation (CPR)心肺复苏Declaration of Conformity 符合性声明Insurance premium 保险费Safety device 安全防护装置HSE:health、safety、environment 健康、安全和环境管理体系ROPS:roll-over protective structure:翻车安全保护装置Manufacturing industry 制造业Transportation equipment 运输设备Excavation work 开挖施工Guard rail:防护围栏Confined space 狭小空间Rooflight sheet 采光屋面板Toe board 趾板mine fire 矿井火灾二、句型翻译1、Rasmussen and Jensen have presented a three-level skill-rule-knowledge model for describing the origins of the different types of human errors.Rasmussen和Jensen提出了一种技能—规范—知识的三级模型,用来描述不同类型的人为失误的来源。
实验室数据完整性要点解析

实验室数据完整性要点解析实验室数据完整性The enduring assets of a laboratory’s work are the records that documentthose activities. When laboratory records are used to support a regulatoryfunction, they are considered to be legal documents. It is of criticalimportance that data integrity is understood and adhered to by everyone workingin the laboratory environment.确保实验室工作被记录形成文档的这些活动,当实验室记录被用于支持法规要求,它被认为是一个法规文件,数据完整用于了解实验室环境中每个工作人员的情况是非常重要的。
All it takes is one kink in the chain to destroy your laboratory’sreputation所有情况的发生都可能破坏你实验室的可信度For records to be considered reliable and trustworthy, they must complywith the following criteria:记录应该是可靠和可信的,他必须符合以下关键点:•Legible and Understandable 易读易懂•Attributable 归属•Contemporaneous 同步•Original 原始性•Accurate 正确性•Complete 完整性•Consistent 一致性•Indelible 不可随意消除•Available 可用Legible andUnderstandable易读易懂A record that cannot be read or understood has no value and might as wellnot exist. All records should be composed so they conform to grammaticalconvention which should be consistent throughout.一份记录不能被阅读或者理解,那么他就是没有价值的或者是不存在。
系统分析师专业英语词汇

SMP对称多处理Symmetrical Multi-ProcessingMPP海量并行处理结构 Massive Parallel Processing运算器 Arithmetic and Logic Unit中央处理器 Central Processing Unit单指令流 Single Instruction Stream单数据流 Single Data stream多指令流 Multiple Instruction Stream 随机存取存储器 Random Access Memory动态随机存储器 Dynamic RAM静态随机存储器 Static RAM只读存储器 Read Only Memory可编程ROM Programmable ROM可擦除的PROM Erasable PROM电可擦除ROM E2PROM Electrically EPROM 掩模技术 mask散存 flash Memory相联存储器CAM Content Addressable Memory空白块 gap扇区 sector扇区的间隙 inter-sector gap间隔 inter-track gap磁道首端 Begining of Tape磁道末端 End of Tape压缩盘 Compact Disk只读压缩盘CDROM Compact Disk Readonly Memory查找时间 seek time廉价磁盘冗余阵列RAID Redundant Array of Inexpensive Disks独立磁盘冗余阵列 Redundant Array of Independent Disks数字视频光盘DVD Digital Video Disk可擦除光盘EOD Erasable Optional Disk 交互式光盘 CD-Interactive最近最少使用淘汰法LRU Least Recently Used写直达 write through写回 write back直接内存存取DMA Direct Memory Access DMA控制器 Direct Memory Access Control er ISA工业标准结构 Industrial Standard ArchitectureIDE电子集成驱动器 Integrated Drive ElectroniceSCSI小型计算机系统接口 Small Computer Standard InterfaceUSB通用串型总线 Universal Serial Bus IEEE美国电气电子工程师协会 Institute of Electrical and Electronics Engineers 扩展的EISA Extended ISA微通道结构MCA Micro Channel ArchitextureVESA视频电子标准协会 Vedio Electronic Standard AssociationPCL外设组件互联 Peripheral Component InterconnectedAGP加速图形接口 Accelerate Graphical PortESDI加强型小型设备接口 Enhanced Small Drive Interface集成设备电路IDE Integrated Device ElectronicsPCMCIA内存卡国际联合会Personal Computer Memory Card International Association复杂指令系统计算机CISC Complex Instruction Set Computer精简指令系统计算机RISC Reduced Instruction Set Computer流水线的吞肚率TP Through Putrate加速比 Speed Up Ratio均匀洗牌置换 Shuffle进程控制块PCB Process Control Block OPT最佳页面替换算法OPTimal replacementLRU最近最少使用算法 Least Recently UsedJCB作业控制块 Job Control BlockFCFS先来先服务 First Come and First ServedSJF短作业优先 Short Job FirstHRN响应比高者优先 Highest Response ratio NextSSTF最短寻道时间优先 Shortest SeekTime FirstSPOOLing外部设备同时联机操作Simultaneous Peripheral Operation OnlineHAL硬件抽象层Hardware Abstraction Layer开放系统互联参考模型OSI/RM Open System Interconnection Reference ModelOLTP联机事务处理 Online Transaction ProcessingOLAP联机分析处理Online Analytical ProcessingADT抽象数据类型 Abstract Data Type AP访问点 Access PointASP动态服务器页 Active Server Page活动图 Activity Diagram活跃的调解者 Active MediaACE可适配通信软件开发环境 Adaptive Communication EnvironmentARP地址解析协议Address Resolution ProtocolANSI美国国家标准化协会American National Standard InstituteASC㈡美国国家信息交换标准码 American Standard Code for Information Interchange应用工程Application Engineering应用程序框架菜谱 Application Framework cookbook Recipes应用编程接口 Application Programming Interface应用特定的 Application SpecificADL体系结构描述语言Architecture Description Language规格说明框架 Architecture Description Specification体系结构演化管理Architecture Evolution Management体系结构模式 Architecture Pattern体系结构权衡分析方法Architecture Tradeoff Analysis Method基于体系结构的软件设计Architecture-Based Software DesignAI人工智能 Artificial Intelligence 装配 AssembleACM美国计算机协会Association Computer MachineryADSL非对称数字用户环路 Asymmetrical Digital SubScriber LineAMI异步信息调用 Asynchronous Message InvocationATM异步传输模式 Asynchronous Transfer Model属性 Attribute可用性 Availability行为性模式 Behavioral行为元素包 Behavioral Elements行为合成 Behavioral Composition绑定 binding绑定模版 binding Template浏览器服务器模式 Browser / Server构造时 build-Time业务实体 Business Entity业务面 Business Facade业务层 Business Layer业务逻辑 Business Logic业务服务 Business ServiceB2B企业对企业 Business To BusinessB2C企业对客户 Business To Consumer业务部门 Business unit面向业务的 Business-oriented候选码 Candidate KeyCMMI能力成熟度模型综合Capability Maturity Model Integration获取 CaptureCIO首席信息官Chief Information OfficerBSP企业系统规划方法 Business System PlanningSDP战略数据规划方法Strategy Data PlanningIE信息工程方法Information EngineeringIRM信息资源管理 Information Resource ManagementCSMA/CD 载波监听多路访问/冲突检测Carrier Sense Multiple Access / Collision DetectCSS层叠式样表 Cascading Style Sheet 可变性 changeability类图 Class diagram分类 classify客户机服务器 Client / Server内聚性 cohesion通用元素 Common element通用机制 Common mechanism协作图 Collaboration diagramCDMA码分多址 Code Division Multiple AccessCOTS商业构件 Commercial Off the Shell CORBA通用对象请求代理机构Common Object Request Broker Architecture通用类型 Common Type编译时间 Compile-time复杂性 Complexity构件 Component构件依赖图 Component Depenfency Graph 构件图 Component DiagramCOM构件对象模型 Component Object Model CBSD基于构件的软件开发Component-Based Software Development 计算 Computation合成 Composition计算构件 Computational Component CASE计算机辅助软件工程 Computer Aided Software Engineer概念模型 Concept Model并发的 concurrent连接件 Connector配置 Configuration面向消费者 Comsumer-oriented上下文环境 context核心资源 Core Asset创建性模式 Creational PatternCRC循环冗余校验 Cyclic Redundant Check 数据层 data layer数据访问层 data access layer数据结构 data structureDBMS数据库管理系统DataBase Management SystemDoS拒绝服务攻击 Denial of Service部署图 Deployment Diagram 设计模式 Design Pattern设计约束 Design ConstraintsDFA确定有限状态自动机 Deterministic Finite Automation开发部门 Development Unit开发视图 Development View面向设备 Device-Oriented字典 Dictionary数字信封 Digital EnvelopeDCOM分布式构件对象模型Distribute Component Object ModelDCE分布式计算机环境Distribute Computing Envirnoment分布式系统 Distribute SystemDOM文档对象模型 Document Object Model DTD文档类型定义Document Type Definition领域工程 Domain Engineering领域模型 Domain Model领域建模 Domain ModelingCSF关键成功因素法 Critical Success FactorsSST战略集合转化法Strategy Set TransformationSSP战略系统规划法Strategy System Planning战略栅格法 Strategy GridVCA价值链分析法 Value-Chain Analysis SAM战略一致模型Strategy Alignment ModelERP企业资源计划 Enterprise Resource Planning知窍 Know-how知人 Know-who隐形知识 tacit knowledge显性知识 explicit knowledgeEIP企业信息门户Enterprise Information PortalEKP知识门户Enterprise Knowledge PortalEAP企业应用门户Enterprise Application PortalDSS决策支持系统Decision Support SystemMIS管理信息系统Management Information SystemBPR业务流程重组Business Process ReengineeringSOA 面向服务的体系结构Service Oriented Architecture信息库 RepositoryDNS域名系统 Domain Name System域名需求 Domain RequirementDSSA特定领域软件体系结构Domain Specific Software Architecture向下规模化 downsizingDHTML动态超文本标记语言Dynamic Hypertext Markup LanguageDII动态调用接口Dynamic Invocation InterfaceEAI企业应用集成Enterprise Application IntegrationG2G政府对政府 Government TO Government G2B政府对企业 Government To Business G2C政府对公民 Government To CitizenG2E政府对公务员 Government To Employee B2B企业对企业 Business To BusinessB2C企业对个人 Business To CustomerC2C个人对个人 Customer To Customer XML可扩展标记语言 eXtensible Markup LanguageDLL动态链接库 Dynamic Link Library动态软件体系结构Dynamic Software ArchitectureDSAM动态体系结构模型Dynamic Structure Architecture ModelEDI电子数据交换Electronic Data Interchange封装 encapsulation编码规则 Encoding RulesEAI企业应用集成Enterprise Application IntegrityEJB企业Java豆 Enterprise Java Bean ER图实体联系图 Entity Relationship Diagram封闭性 Envelopment纠错码 Error Correction以太网 Ethernet 评估 Evaluation事件广播 Event Broadcast决策者 Executive可扩充性 Expansibility可扩展性 ExtendibilityXAML可扩展应用程序标记语言 eXtensible Application Markup LanguageXLL可扩展连接语言eXtensible Link LanguageXSL可扩展样式语言eXtensible Stylesheet LanguageO2O从线上到线下 Offline To Online刻面描述符 Faceted Descriptor刻面分类法 Faceted Classification特征模型 Feature ModelFTP文件传输协议 File Transfer Protocol 业务IT整合 Business IT Alignment企业IT架构 Enterprise IT Architecture SA结构化分析 Structured AnalysisSD结构化设计 Structured DesignSP结构化程序设计Structured ProgramingDFD数据流图 Data Flow DiagramDD数据字典 Data DictionaryOO面向对象 Object-OrientedOMT对象建模技术Object Model TechnologyPLM产品生命周期管理 Product LifeCycle ManagementIRP信息资源规划 Information Resource PlaningFOPL一阶谓词逻辑 First Order Predicate Logic适应性 Flexibility强制条件 Force形式 Form形式和约 Formal Contracts形式化 Formalization基础包 Foundation框架 framework全文搜索 Full Text Search功能性 Functionality一般机制 General Mechanisms泛化 generalizationGA遗传算法 Genetic AlgorithmGIS地理信息系统Geographic Information SystemGPS全球定位系统Global Positioning SystemGSM全球移动通信系统 Global System for Mobile Communication胶水代码 Glue Code粒度 Granularity软件开发规模度量 Size MeasurementGUI图形用户界面 Graphic User Interface 网格计算 Grid Computing层次领域工程Hierarchical domain engineering层次性 HierarchyHMB层次消息总线 Hierarchy Message Bus 主机重定向 Host Redirector热点 hotspot超文本分类 Hypertext Classification HTML超文本标记语言 HyperText Markup LanguageHTTP超文本传输协议 HyperText Transfer Protocol识别 identify惯用模式 Idiomatic Paradigm实现 Implementation增量 Increment独立的 Independence间接 Indirect继承 Inheritance初始标识 initial marking初始原型 Initial PrototypeIEEE国际电气和电子工程师协会Institute of Electrical and Electronics Engineers可集成性 Integrability集成电路 Integrated CircuitISDN综合数字业务网Integrated Services Digital Network集成 IntegrationIDE集成开发环境Integration Development Environment交互 InteractionIDL接口定义语言 Interface Definition LanguageIR接口池 Interface RepositoryISO国际标准化组织International Standard OrganizationICMP网际控制报文协议 Internet Control Message ProtocolIGMP网际成组多路广播协议Internet Group Multicast ProtocolIP网际协议 Internet ProtocolRAP路由存取协议 Route Access Protocol ISP因特网服务提供商 Internet Service Provider互操作性 InteroperationIPC进程间通信InterProcess Communication企业内部网 IntranetIDS入侵检测系统 Instruction Detection SystemIPS入侵防护系统Instruction Prevention System调用 invocation迭代 Iteration反复的 IterativeJ2EE Java2企业版 Java To Enterprise EditionJ2ME Java2袖珍版 Java To Mirco Edition J2SE Java2标准版Java To Standard EditionDS数字签名 Digital SignatureITSEC信息技术安全评价准则 Information Technology Security Evaluation Criteria 信息技术安全评价通用准则Common Criteria ITSECSOC系统建在硅片上 System On a Chip MIS+S系统Management Information System + SecurityS+MIS系统Security + Management Information SystemSS+MIS系统:Super Security Management Information SystemCA认证中心 Certificate Authority TCSEC可信计算机系统准则Trusted Computer System Evaluation Criteria快速数据加密标准Fast DataEncipherment Algorithm瑞士国际数据加密算法IDEA International Data Encryption Algorithm 美国数据加密标准DES Data Encryption StandardMD5消息摘要算法Message Digest algorithm 5消息摘要 Message DigestSHA安全散列算法 Secure Hash Algorithm DSS数字签名标准Digital Signature StandardJava数据库连接Java DataBase Connectivity自反律 Reflexivity增广律 Augmentation传递律 TransitivityJDK Java开发工具包 Java Develop Kit JSP Java服务器页面 Java Service Page JVM Java虚拟机 Java Virtual Machine JPEG 联合图像专家组Joint Photo-Graphic Experts GroupKWIC 重组关键字 Keyword In Context关键字分类法 keyword classification遗留资源 Legacy asset遗留系统 Legacy System生命周期 Life Cycle更新对象列表 List of Updata objects LAN局域网 Local Area Network逻辑视图 Logic View可维护性 Maintainability管理信息系统MIS Management Information SystemMTBF平均失效间隔时间 Mean Time Between FailureMTTF平均失效等待时间Mean Time To FailureMAC介质访问控制 Media Access Control MEP信息交换模式Message Exchange Pattern元模式 meta model元元模式 meta meta Model方法签名 Method SignatureMAN城域网 Metropolitan Area Network 微方法 Micro-Method MDA模型驱动体系结构Model Driven ArchitectureMVC模型视图控制图Model-View-Controller可修改性 ModifiabilityMIL模块内连接语言Module Interconnection Language模块视图 Module ViewMPEG运动图像专家组Moving Picture Experts GroupMIMD多指令流多数据流Multiple Instruction Multiple Data多重性 Multiplicity命名空间缓冲 Namespace CacheNFS网络文件系统 Network Filing System 通知 Notification对象适配器 Object AdapterOCL对象约束语言Object Constraint Language对象图 Object DiagramOLE对象链结与嵌入Object Link and EmbeddingOMG对象管理集团Object Management Group对象模型 Object ModelOMT对象模型技术Object Modeling Technology对象 Object OrientationORB对象请求代理 Object Request Broker OOA面向对象分析Object-Oriented Analyzing对象数据库 Object-Oriented DataBase OOD面向对象设计Object-Oriented DesignOOP面向对象程序语言 Object-Oriented Programming单向 one-wayOA办公自动化 Office Automation面向对象框架 Object-Oriented framework SSO单点登录 Single Sign-OnKDC密钥分配中心Key Distribution Center票据授予票据 Ticket Granting Ticket SIM客户识别模块 Subscriber IdentityModuleECC椭圆曲线密码Elliptic Curve CryptosystemsWAP无线应用协议 Wireless Application ProtocolWTLS无线传输层安全 Wireless Transport Layer SecurityWDP无线数据报协议 Wireless Datagram Protocol双穴主机 Dual-HomeD屏蔽主机 Screened Host屏蔽子网 Screened SubnetVPN虚拟专用网络Virtual Private Network安全隧道技术 TunnelingPPTP点对点隧道协议Point to Point Tunneling ProtocolL2TP第二层通道协议 Layer Two Tunneling ProtocolL2F第二层转发Level 2 Forwarding ProtocolPPP点到点协议 Point to Point Protocol VPDN虚拟专用拨号网络 Virtual Private Dail-Up NetworkWAPI无线局域网安全机制WLAN Authentication and Privacy InfrastructureSET安全电子交易Secure Electronic TransanctionHTTPS安全套接字层上的超文本传输协议HyperText Transfer Protocol over Secure Socket LayerURI统一资源定位符 Universal Resource IdentifierRA注册中心 Registration Authority LRA本地注册中心Local Registration Authority嗅探器 SnifferIPSec IP协议安全性 Internet Protocol SecuritySSH安全外壳 Secure ShellSSL安全套接字层 Secure Sockets Layer TLS传输层安全协议Transport Layer Security PGP Pretty Good PrivacyS/MIME 安全多功能邮件扩展Secure/Multipurpose Internet Mail Extension安全属性 Simple Security Property星属性 Star Property特洛伊木马 TrojansDRP灾难恢复规划Disaster Recovery PlanningBRP业务恢复规划 Business Recumption PlanningCMP危机管理规划Crisis Management Planning持续可用性 Continuous Availability AM调幅 Amplitude ModulationFM调频 Frequent ModulationPM调相 Phase ModulationPCM脉码调制 Phase Code Modulation非归零编码 Non-Return Zero非归零反相编码 Non-Return Zero Inverse 非归零电频编码 Non-Return Zero Level 归零 Return ZeroFDDI光纤分布式数据接口Fiber Distributed Data Interface令牌环网络 Token Ring以太网 EthernetWAN广域网 Wide Area NetworkMAN城域网:Metropolitan Area Network ISDN综合业务数字网Integrated Services Digital NetworkADSL非对称网络数字用户线路 Asymmetric Digital SubScriber LineATM异步传输模式 Asynchronous Transfer NetworkDQDB分布式队列双总线Distributed Queue Dual BusOSI/RM开放系统互联参考模型Open System Interconnections/Reference ModelMAC介质访问控制层 Media Access Control LLC逻辑链路控制层 Logic Link Control TCP传输控制协议 Transmission Control ProtocolUDP用户数据报协议User DatagramProtocolNFS网络文件系统 Net File SystemTFTP简单文件传输协议Trival File Transfer ProtocolAS自治系统 Autonomous SystemIGP内部网关协议Interior Gateway ProtocolEGP外部网关协议Exterior Gateway ProtocolIGRP内部网关路由协议 Interior Gateway Routing ProtocolRIP路由信息协议 Routing Information ProtocolHFC同轴光纤技术 Hybrid Fiber Coaxial ISP因特网服务提供商 Internet Service ProviderDDN数字数据网 Digital Data Network OLTP在线事务处理OnLine Transction ProcessingOLAP联机分析处理OnLine Analyze ProcessingODBC开放数据库连接Open DataBase Connectivity有序的 ordered组织 OrganizationOEM原始设备制造商 Original Equipment Manufacture正交 orthogonal偏序 Partial Order模式目录 Pattern Catalog模式系统 Pattern System性能 PerformancePCL外部设备互联 Peripheral Component Interconnect视角 Perspective物理视图 Physical View管道过滤器 pipe-filter平台 Platform即插即用 plug and play主码 Primary KeyPOP3电子邮局协议 Post Office Protocol Version3问题领域 Problem Domain过程调用 Procedure Call 多态 Polymorphism权限 Privilege进程视图 Process View生产率 Productivity突出部分 Projections受保护的 Protected可移植性 ProtabilityPCL多变配置语言 Proteus Configuration LanguagePML过程建模语言Process Modeling Language代理 ProxyQA质量保证 Quality AssuranceQoS服务质量 Quality of ServiceRAM随机存取存储器 Random Access Memory ROM只读存储器 Read Only MemoryRUP统一过程 Rational United Process 恢复 Recovery递归的 RecursiveRISC精简指令集计算机Reduced Instruction Set Computer再工程 Reengineering可靠性 ReliabilityRMI远程方法调用Remove Method InvocationRPC远程过程调用 Remote Procedure Call CSMA/CA载波监听多路访问/冲突避免Carrier Sense Multiple Access with Collision AvoidancePDS综合布线系统 Premises Distributed System路由器 Routing Table表示 Represent表述 Representation请求响应 Requese Response需求 requirement仓库 RepositoryRDF资源描述框架 Resource Description Framework响应 Response重用 reuse风险曝光度 Risk ExposureCMM软件过程能力成熟度模型 Capability Maturity ModelCMMI能力成熟度模型集成Capability Maturity Model IntegrationPPP点对点协议 Point to Point Protocol HDLC高级数据链路控制 High-Level Data Link ControlSLIP串行线路网际协议Serial Line Internet ProtocolIPX互联网分组交换协议 Internetwork Packet eXchange ProtocolFTTC光纤到路边 Fiber To The Curb FTTZ光纤到小区 Fiber To The Zone FTTB光纤到大楼 Fiber To The Building FTTH光纤到户 Fiber To The HomeFTTF光纤到楼层 Fiber To The Floor PON无源光纤网络Passive Optical NetworkAPON基于ATM的无源光网络 ATM-PON EPON基于以太网的无源光网络Ethernet-PON电缆调制解调器 Cable ModemCDMA码分多址 Code Division Multiple AccessTDMA时分多址 Time Division Multiple AccessFDMA频分多址Frequency Division Multiple AccessHFC同轴光纤技术 Hybrid Fiber-Coaxial LAPD信道D进行指令传输控制协议 Link Access Procedure on the D Channel SONET同步光纤网络 Synchronous Optical NetworkSDH同步数字体系 Synchronous Digital HierarchyGSM全球移动通信系统 Global System for Mobile CommunicationLMDS区域多点分配服务 Local Multipoint Distribution ServicesMMDS多通道微波分配服务 Multichannel Microwave Distribution SystemRARP逆向地址解析协议 Reverse Address Resolution Protocol革命方式 RevolutionaryRIP路由信息协议 Routing Information Protocol 模式 Schema安全性 Security场景 Scenario语义 Semantic敏感点 Sensitivity Point顺序图 Sequence Diagram服务组合 Service Composition服务粒度 Service GranularitySOAD面向服务的分析与设计Service-Oriented Analysis and Design SOA面向服务的体系结构Service-Oriented Archtecture服务总线 Services Bus简单应用程序接口 Simple API for XML骨架 SkeletonSA软件体系结构 Software Architecture SAAM软件体系结构分析方法Software Architecture Analysis MethodSMTP简单邮件传输协议Simple Mail Transport ProtocolSOAP简单对象访问协议 Simple Object Access ProtocolSNMP简单网络管理协议 Simple Network Management ProtocolSCM软件配置管理Software Configuration ManagementSAA 软件体系结构助理Software Architecture Assistant软件危机 Software CrisisSDK软件开发工具包Software Development Kit软件工程 Software Engineering软件过程 Software Process软件产品线 Software Product Line稳定性 stability项目干系人 StakeholdersSGML标准通用标记语言Standard Generalized Markup LanguageSTL标准模版库Standard Template Library状态图 State Diagram实体类型 stereotype刺激 stimuli策略 Strategy结构性模式 StructuralSQL结构化语言查询 Structured Query Language客户桩 Stump从属系统 Subordinate System上级系统 Superordinate System挂起 SuspendSMP对称多处理系统Symmetric Multi Processing语法 syntaxSIS互联系统构成的系统System of Interconnected Systems面向系统的 System-Oriented瘦服务器 Thin Server线程 Thread标记 Token令牌环 Token Ring拓扑 Topology权衡 Tradeoff变迁 Trandition转移 TransitionTCP传输控制协议 Transmission Control Protocol三生命周期 Tri-LifeCycleUML统一建模语言Unified Modeling Language统一方法 United MethodUDDI统一描述,发现和集成协议 Universal Description Discovery and Integration URL通用资源定位符 Uniform Resource LocatorsURI统一资源标示符 Universal Resource IdentifityUSB通用串行总线 Universal Serial Bus 用例模型 UseCase Model用例图 UseCase Diagram用户对象 User Object用户驱动 User-DirvenVAS增值服务 Value Added Serve个性 variabilitiesVCD视频光盘 Video Compact DiscVOD视频点播系统 Video On Demand视点 ViewPoint视图 Views VLAN虚拟局域网Virtual Local Area NetworkVPN虚拟专用网络Virtual Private NetworkWeb服务 Web ServicesWSDL Web服务描述语言Web Services Description LanguageVRML虚拟现实建模语言 Virtual Reality Modeling LanguageWAN广域网 Wide Area NetworkWCDMA多频码分多址Wideband Code Division Multiple AccessWAP无线应用协议 Wireless Application ProtocolWWW万维网 World Wide WebW3C万维网联盟World Wide Web Consortium工作流 WorkflowAgile:敏捷Lean:精益Iterative:迭代式的Iteration:迭代Agile Manifesto:敏捷宣言Empirical:经验性的Empirical Process:经验性过程Transparency:透明性Inspect and Adapt:检视与调整Sprint:原意为冲刺,Scrum中的Sprint 无对应中文翻译,指一个迭代Sprint Goal:Sprint目标Product Owner :产品负责人简称PO Scrum Master :简称SM, 一般不翻译Development Team : Scrum开发团队Scrum Team:指PO,SM和开发团队Scrum Roles:Scrum角色,指PO,SM和开发团队Emergent :涌现的Product Backlog:产品待办列表,指需求清单Sprint Backlog:Sprint待办列表,指Sprint任务清单Sprint Burn-down Chart:Sprint燃尽图,团队用于做Sprint内的进展跟踪Release Burn-down Chart: 发布燃尽图,产品负责人做发布进展跟踪Sprint Planning Meeting: Sprint计划会议Daily Scrum Meeting:每日站会Sprint Review Meeting:Sprint评审会议Sprint Retrospective Meeting: Sprint 回顾会议Product Backlog Refinement: 产品待办列表梳理Product Backlog Item: 产品待办清单条目,简称PBIUser Story: 用户故事,指一条需求Story Point:衡量用户故事的工作量大小的计量单位Velocity: 团队速度Sprint Task: 实现一条需求需要做的一个技术任务Definition of Done: DoD,完成的定义Stakeholders:干系人Backlog:待办列表Artifact :工件Estimation :估算Collaboration:协作Scaling Scrum:大规模Scrum双绞线 Twist-Pair屏蔽双绞线 Shielded Twisted Pair非屏蔽双绞线 UnShieldedTwisted Pair CATV有线电视网Community Antenna TelevisionNIC网络接口卡 Network Interface Card OSI七层模型:物理层(Physical)数据链路层(Data Link)网络层(Network)传输层(Transport)会话层(Session)表示层(Presentation)应用层(Application)NAT网络地址转换Network Address Translation小版本发布 Frequent Release较少的文档 Minimal Documentation合作为重 Collaborative Focus客户直接参与 Customer Engagement 自动化测试 Automated Testing适用性计划调整 Adaptive Planning测试驱动开发 Test-Driven Development 持续集成 Continuous IntegrationCBSD基于构件的软件开发Component Based Software Development统一过程 Rational Unified Process PAD问题分析图 Problem Analysis Diagram PDL伪代码 Program Design Language IPO输入处理输出 Input/Process/Output PDOA面向问题域的分析 Problem Domain Orientd AnalysisWFM工作流管理 WorkFlow Management WFMS工作流管理系统WorkFlow Management SystemCASE计算机辅助软件工程 Computer-Aided Software EngineeringP3E企业集成项目管理工具Primavera Project Planner for EnterpriserFPs功能点 Function PointACD结构环境图Architecture Context DiagramAFD结构流程图Architecture Flow DiagramDRE缺陷排除效率Defect Removal Efficiency在开发过程中缺陷被解决的数目 Defects Removed During a Development Phase在该阶段缺陷潜伏的数目:Defect latent in the Product at That Phase测试件 TestWare抽象工厂模式 Abstract Factory生成器模式 Builder工厂方法模式 Factory Method原型模式 Prototype单例模式 Singleton适配器 Adapter桥梁模式 Bridge组合模式 Composite装饰模式 Decorator外观模式 Facade享元模式 Flyweight代理模式 Proxy责任链模式 Chain of Reponsibility命令模式 Command解释器模式 Interpreter迭代器模式 Iterator中介者模式 Mediator备忘录模式 Memento观察者模式 Observer状态模式 State模版模式 Template Method访问者模式 Visitor系统分析师 System AnalystUML依赖关系Dependencies关联 Association汎化 generalization实现 Realization类图 Class Diagram对象图 Object Diagram构件图 Component Diagram组合结构图 Composite Structure Diagram 用例图 Use Case Diagram顺序图 Sequence Diagram通信图 Communication Diagram定时图 Timing Diagram状态图 State Diagram活动图 Activity Diagram部署图 Deployment Diagram制品图 Artifact Diagram包图 Package Diagram交互浏览图Interaction Overview Diagram用例规约 UseCase Specification迪米特原则 DemeterLKP最少知识法则Least Knowledge PrinciplePAD问题分析图 Problem Analysis Diagram PDL伪代码 Program Design Language ACD结构环境图Architecture Context Diagram对等联网P2P Peer To PeerMOM中间件 Message-Oriented Middleware ORB对象请求代理 Object Request Brokers STARS可靠性软件技术Software Technology For Adaptable Reliable Software名称空间 Name Prefix 变量函数命名 camelCase ProperCase面向对象技术的重用REBOOT Reuse Based on Object-Oriented Technique中国自主操作系统China Operation SystemOMG对象管理集团Object Management GroupDCOM分布式构件对象模式 Distributed Component Object Model遗留工程 Legacy EngineeringCOTS商业构件 Commercial Off-the-Shell 超文本方法 hypertext classification火焰图 Flame Group多条件判断语句 Multiple condition减少冗余代码 Reduce duplicated Code分支预测 Branch prediction把相关代码放在一起 Code adjacency Cache对齐 Cache line alignment减少函数调用 Reduce duplicated code结构事物 structural things行为事物 behavior things分组事物 grouping things注释事物 annotational things菜谱Application Framework cookbook recipes形式合约 formal contracts委托连接器 Delegate ConnectorRIA富互联网应用Rich Internet Application逻辑视图 logic view开发视图 development view进程视图 process view物理视图 physical view场景 scenarios3G通信技术 3rd generationIETF互联网工程任务组Internet Engineering Task Force区块链 BlockChainJava虚拟机 Java Virtual MachineCLR公共语言运行时Common Language RuntimeACE自适应通信环境Adaptive Communication EnvironmentRPC远程过程调用 Remote Procedure CallRMI远程方法调用Remote Method InvocationOMA对象管理结构Object Management ArchitectureJava服务器端小程序 Java ServletMOM消息中间件Message Oriented MiddlewareJSP Java服务器页面 Java Server Page JMSJava消息服务 Java Message Service JNDIJava命名目录接口 Java Naming and Directory InterfaceJAASJava认证和授权服务Java Authentication Authorization Service JCA J2EE连接体系结构 J2EE Connector ArchitectureJava事务API Java Transaction API SAX简单应用程序接口 Simple API for XML 虚拟计算 Virtual Computing实用计算 Utility ComputingMSP管理服务提供商 Management Service Provider普适计算Pervasive Computing Ubiquitous Computing指令集的并行Instruction-Level ParallelismASIC专用集成电路 Application Specific Integrated CircuitIP知识产权 Intellectual PropertyDSI动态骨架接口Dynamic Skeleton InterfacePOA可携带对象适配器 Portable Object AdapterOMG对象管理集团Object Management GroupEJB企业Java豆 Enterprise Java Bean 刻面描述符 Facet descriptor适应性 FlexibilityC2体系结构 Component-ConnectorSVG可伸缩向量图Scalable Vector Graphics动态HTML Dynamic HTMLIE浏览器 Internet ExplorerCSS层叠样式表 Cascading Style Sheets DOM文档对象模型 Document Object Model XHTML可扩展超文本标识语言 eXtensible HyperText Markup LanguageXUL基于XML的用户界面语言 XML User Interface Language敏感点 Sensitivity Point权衡点 Tradeoff PointRIA富互联网应用Rich Internet ApplicationADL体系结构描述语言Architecture Description LanguageATAM体系结构权衡分析方法 Architecture Tradeoff Analysis MethodACP Agile Certified Practitioner精益敏捷 LeanDevelopment敏捷教练认证 Certified ScrumMaster软件危机 Software Crisis复杂性 ComplexitySAAM软件体系结构分析方法Software Architecture Analysis MethodDTD文档类型定义Document Type DefinitionRDF资源描述框架 Resource Description FrameworkUDDI统一描述,发现和集成 Universal Description Discovery and Integration 服务粒度 Service Granularity企业体系结构 Enterprise Architecture LDAP轻量目录访问协议Lightweight Directory Access ProtocolPKI公共密钥基础设施Public Key InfrastructureSOAD面向服务的分析与设计Service-Oriented Analysis and Design BPM业务流程建模Business Process ModelingCBD基于组件的软件开发 Component Based Development可用性 Availability可靠性 reliabilitySGML标准通用标记语言Standard Generalized Markup LanguageXSL可扩展样式表语言eXtensible StyleSheet LanguageXLL可扩展连接语言eXtensible LinkLanguageXQL XML查询语言:XML Query Language SOAD面向服务的分析与设计Service-Oriented Analysis and Design WS-BPELWeb服务业务流程执行语言WebService Business Process Execution Language商业中心 Business centric架构中心 Architecture centric两个生命周期 Two Life cycle approach 遗留资源 Legacy assets核心资源 core assets可变性管理 Variability Management领域共性管理 Commonality Management SCA服务构件体系结构 Service Component Architecture。
ITIL中英文对照
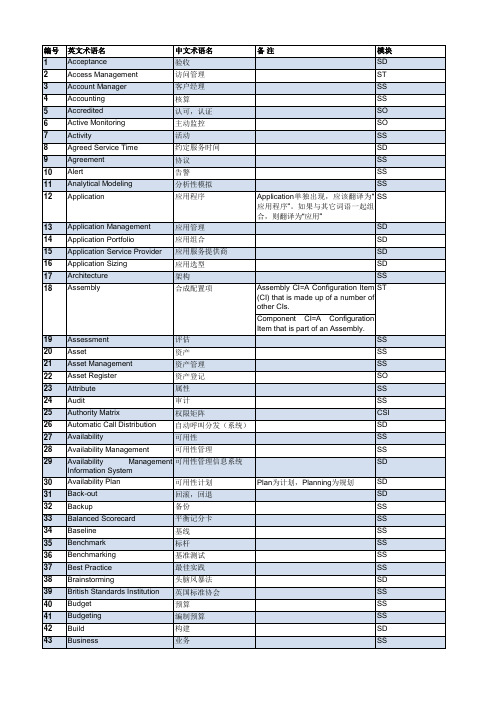
Business Relationship 业务关系管理 Management Business Service 业务服务 Business Service Management 业务服务管理 Business Unit Call Call Centre Call Type Capability Capability Maturity Model Capability Integration Capacity Maturity 业务单元 呼叫 呼叫中心 呼叫类型 能力 能力成熟度模型 Model 能力成熟度模型集成 容量
99 100 101 102 103 104 105 106 107 108 109 110 111 112
Component Failure Impact Analysis Computer Telephony Integration Concurrency Confidentiality Configuration Configuration Baseline Configuration Control Configuration Identification Configuration Item Configuration Management
业务连续性计划 业务客户 业务影响分析 业务目标 业务运营 业务管理 业务流程
SD SS SS SS SS 应该翻译成“业务视角”,但意译 SS 为“业务管理”。 SS SS SS SS SS SS SS SO SS CSI Capability是 能 力 , 即 具 备完 成项 SS 工作的技能和知识,Capacity是容 量,即在具备能力的前提下可以完 成多少项工作。 SS Capacity management不仅仅是个 SD 容量的概念,详见《中国IT服务管 理指南》中阐述,不过翻译成容量 也是可以的,另外为了和capability 这个术语区分开来,所以我同意改 成“容量管理。” SS SD SS SS SS SS SS
《风险评价技术及方法》 8._Operating_and_Support_Hazard_Analysis
Chapter 8Operating and SupportHazard Analysis8.1INTRODUCTIONThe operating and support hazard analysis (O&SHA)is an analysis technique for identifying hazards in system operational tasks,along with the hazard causal factors,effects,risk,and mitigating methods.The O&SHA is an analysis technique for specifically assessing the safety of operations by integrally evaluating operational procedures,the system design,and the human system integration (HSI)interface.The scope of the O&SHA includes normal operation,test,installation,mainten-ance,repair,training,storage,handling,transportation,and emergency /rescue oper-ations.Consideration is given to system design,operational design,hardware failure modes,human error,and task design.Human factors and HSI design considerations are a large factor in system operation and therefore also in the O&SHA.The O&SHA is conducted during system development in order to affect the design for future safe operations.8.2BACKGROUNDThis analysis technique falls under the operations design hazard analysis type (OD-HAT)because it evaluates procedures and tasks performed by humans.The basic analysis types are described in Chapter 3.An alternate name for this analysis technique is the operating hazard analysis (OHA).131Hazard Analysis Techniques for System Safety ,by Clifton A.Ericson,IICopyright #2005John Wiley &Sons,Inc.132OPERATING AND SUPPORT HAZARD ANALYSISThe purpose of the O&SHA is to ensure the safety of the system and personnel in the performance of system operation.Operational hazards can be introduced by the system design,procedure design,human error,and/or the environment.The overall O&SHA goal is to:1.Provide safety focus from an operations and operational task viewpoint.2.Identify task or operationally oriented hazards caused by design,hardwarefailures,software errors,human error,timing,and the like.3.Assess the operations mishap risk.4.Identify design system safety requirements(SSRs)to mitigate operational taskhazards.5.Ensure all operational procedures are safe.The O&SHA is conducted during system development and is directed toward developing safe design and procedures to enhance safety during operation and main-tenance.The O&SHA identifies the functions and procedures that could be hazar-dous to personnel or,through personnel errors,could create hazards to equipment, personnel,or both.Corrective action resulting from this analysis is usually in the form of design requirements and procedural inputs to operating,maintenance,and training manuals.Many of the procedural inputs from system safety are in the form of caution and warning notes.The O&SHA is applicable to the analysis of all types of operations,procedures, tasks,and functions.It can be performed on draft procedural instructions or detailed instruction manuals.The O&SHA is specifically oriented toward the hazard analysis of tasks for system operation,maintenance,repair,test,and troubleshooting.The O&SHA technique provides sufficient thoroughness in identifying and mitigating operations and support-type hazards when applied to a given system/ subsystem by experienced safety personnel.A basic understanding of hazard analy-sis theory is essential as well as knowledge of system safety concepts.Experience with,or a good working knowledge of,the particular type of system and subsystem is necessary in order to identify and analyze hazards that may exist within pro-cedures and instructions.The methodology is uncomplicated and easily learned. Standard O&SHA forms and instructions have been developed that are included as part of this chapter.The O&SHA evaluates the system design and operational procedures to identify hazards and to eliminate or mitigate operational task hazards.The O&SHA can also provide insight into design changes that might adversely affect operational tasks and procedures.The O&SHA effort should start early enough during system develop-ment to provide inputs to the design and prior to system test and operation.The O&SHA worksheet provides a format for entering the sequence of operations,pro-cedures,tasks,and steps necessary for task accomplishment.The worksheet also provides a format for analyzing this sequence in a structured process that produces a consistent and logically reasoned evaluation of hazards and controls.8.4DEFINITIONS133Although some system safety programs(SSPs)may attempt to replace the O&SHA with a preliminary hazard analysis(PHA),this is not recommended since the PHA is not oriented specifically for the analysis of operational tasks. Use of the O&SHA technique is recommended for identification and mitigation of operational and procedural hazards.8.3HISTORYThe O&SHA technique was established very early in the history of the system safety discipline.It was formally instituted and promulgated by the developers of MIL-STD-882.It was developed to ensure the safe operation of an integrated sys-tem.It was originally called operating hazard analysis(OHA)but was later expanded in scope and renamed O&SHA to more accurately reflect all operational support activities.8.4DEFINITIONSTo facilitate a better understanding of O&SHA,the following definitions of specific terms are provided:Operation An operation is the performance of procedures to meet an overall objective.For example,a missile maintenance operation may be“replacing missile battery.”The objective is to perform all the necessary procedures and tasks to replace the battery.Procedure A procedure is a set of tasks that must be performed to accomplish an operation.Tasks within a procedure are designed to be followed sequentially to properly and safely accomplish the operation.For example,the above battery repla-cement operation may be comprised of two primary procedures:(1)battery removal and(2)battery replacement.Each of these procedures contains a specific set of tasks that must be performed.Task A task is an element of work,which together with other elements of work comprises a procedure.For example,battery removal may consist of a series of sequential elements of work,such as power shutdown,compartment cover removal, removal of electrical terminals,unbolting of battery hold down bolts,and battery removal.Figure8.1portrays these definitions and their interrelationships.It should be noted that tasks might be further broken down into subtasks,sub-subtasks,and so forth.8.5THEORYFigure 8.2shows an overview of the basic O&SHA process and summarizes the important relationships involved.The intent of the O&SHA is to identify and mitigate hazards associated with the operational phases of the system,such as deployment,maintenance,calibration,test,training,and the like.This process consists of utilizing both design information and known hazard information to verify complete safety coverage and control of hazards.Operational task hazards are identified through the meticulous analysis of each detailed procedure that is to be performed during system operation or support.Input information for the O&SHA consists of all system design and operation information,operation and support manuals,as well as hazards identified by other program hazard analyses.Typically the following types of information are available and utilized in the O&SHA:1.Hazards and top-level mishaps (TLMs)identified from the preliminary hazardlist (PHL),PHA,subsystem hazard analysis (SSHA),system hazard analysis (SHA),and health hazard assessment (HHA)2.Engineering descriptions of the system,support equipment,and facilities3.Written procedures and manuals for operational tasks to be performed Procedure 1OperationProcedure 3 Procedure 2•Task 1.1•Subtask 1.1a•Subtask 1.1b•Task 1.2•Subtask 1.2a •Task 2.1 •Task 2.2 •Task 2.3 •Task 3.1 •Task 3.2 •Task 3.3Figure 8.1Operationdefinitions.Figure 8.2O&SHA overview.134OPERATING AND SUPPORT HAZARD ANALYSIS8.6METHODOLOGY1354.Chemicals,materials,and compounds used in the system production,oper-ation,and support5.Human factors engineering data and reports6.Lessons learned,including human error mishaps7.Hazard checklistsThe primary purpose of the O&SHA is to identify and mitigate hazards resulting from the system fabrication,operation,and maintenance.As such,the following information is typically output from the O&SHA:1.Task hazards2.Hazard causal factors(materials,processes,excessive exposures,errors,etc.)3.Risk assessment4.Safety design requirements to mitigate the hazard5.The identification of caution and warning notes for procedures and manuals6.The identification of special HSI design methods to counteract human-error-related hazardsGenerally,the O&SHA evaluates manuals and procedural documentation that are in the draft stage.The output of the O&SHA will add cautions and warnings and poss-ibly new procedures to thefinal documentation.8.6METHODOLOGYThe O&SHA process methodology is shown in Figure8.3.The idea behind this pro-cess is that different types of information are used to stimulate hazard identification. The analyst employs hazard checklists,mishap checklists,and system tools.Typical system tools might include functionalflow diagrams(FFDs),operational sequence diagrams(OSDs),and indentured task lists(ITLs).Table8.1lists and describes the basic steps of the O&SHA process.The O&SHA process involves performing a detailed analysis of each step or task in the oper-ational procedure under investigation.The objective of the O&SHA is to identify and mitigate hazards that might occur during the operation and support of the system.The human should be considered an element of the total system,both receiving inputs and initiating outputs during the conduct of this analysis.Hazards may result due to system design,support equipment design,test equipment,human error,HSI,and/or procedure design. O&SHA consideration includes the environment,personnel,procedures,and equipment involved throughout the operation of a system.The O&SHA may be performed on such activities as testing,installation,modification,maintenance, support,transportation,ground servicing,storage,operations,emergency escape, egress,rescue,postaccident responses,and training.The O&SHA also ensures that operation and maintenance manuals properly address safety and healthrequirements.The O&SHA may also evaluate adequacy of operational and support procedures used to eliminate,control,or abate identified hazards or risks.The O&SHA effort should start early enough to provide inputs to the design and prior to system test and operation.The O&SHA is most effective as a continuing closed-loop iterative process,whereby proposed changes,additions,and formu-lation of functional activities are evaluated for safety considerations,prior to formal acceptance.O&SHA considerations should include:1.Potentially hazardous system states under operator control2.Operator hazards resulting from system design (hardware aging and wear,distractions,confusion factors,worker overload,operational tempo,exposed hot surfaces,environmental stimuli,etc.)3.Operator hazards resulting from potential human error4.Errors in procedures and instructions5.Activities that occur under hazardous conditions,their time periods,and theactions required to minimize risk during these activities /time periods6.Changes needed in functional or design requirements for system hardware /software,facilities,tooling,or support /test equipment to eliminate or control hazards or reduce associated risks7.Requirements for safety devices and equipment,including personnel safetyand life supportequipmentO&SHA Worksheets•Hazards •Mishaps •Causal sources •Risk •SCFs and TLMs •Mitigation methods •SSRsFigure 8.3O&SHA methodology.136OPERATING AND SUPPORT HAZARD ANALYSIS8.Warnings,cautions,and special emergency procedures (e.g.,egress,rescue,escape,render safe,explosive ordnance disposal,back-out,etc.),including those necessitated by failure of a computer software-controlled operation to produce the expected and required safe result or indicationTABLE 8.1O&SHA ProcessStepTask Description 1Define system operation.Define,scope,and bound the operation to beperformed.Understand the operation and itsobjective.2Acquire data.Acquire all of the necessary design and operationaldata needed for the analysis.These data includeboth schematics and operation manuals.3List procedures and detailed tasks.Make a detailed list of all procedures and tasks to beconsidered in the O&SHA.This list can be takendirectly from manuals,procedures,or operationalplans that are already written or in draft form.4Conduct O&SHA. a.Input task list into the O&SHA worksheets.b.Evaluate each item in the task list and identifyhazards for the task.pare procedures and tasks with hazardchecklists.pare procedures and tasks with lessonslearned.e.Be cognizant of task relationships,timing,andconcurrent tasks when identifying hazards.5Evaluate risk.Identify the level of mishap risk presented by thehazard with,and without,mitigations in thesystem design.6Recommend corrective action.Recommend corrective action necessary toeliminate or mitigate identified hazards.Workwith the design organization to translate therecommendations into SSRs.Also,identify safetyfeatures already in the design or procedures thatare present for hazard mitigation.7Ensure caution and warnings are implemented.Review documented procedures to ensure thatcorrective action is being implemented.Ensurethat all caution and warning notes are inputted inmanuals and /or posted on equipmentappropriately,as recommended in the O&SHA.8Monitor corrective action.Participate in verification and validation ofprocedures and review the results to ensure thatSSRs effectively mitigate hazards.9Track hazards.Transfer identified hazards into the hazard trackingsystem (HTS).Update hazards in the HTS ascausal factors and risk are identified in theO&SHA.10Document O&SHA.Document the entire O&SHA process on theworksheets.Update for new information andclosure of assigned corrective actions.8.6METHODOLOGY 1379.Requirements for packaging,handling,storage,transportation,maintenance,and disposal of hazardous materials10.Requirements for safety training and personnel certification11.The safety effect of nondevelopmental items(NDI)and commercial off-the-shelf(COTS)items,both in hardware and software,during system operation12.The safety effect of concurrent tasks and/or procedures8.7WORKSHEETThe O&SHA is a detailed hazard analysis utilizing structure and rigor.It is desirable to perform the O&SHA using a specialized worksheet.Although the specific format of the analysis worksheet is not critical,as a minimum,the following basic infor-mation is required from the O&SHA:1.Specific tasks under analysis2.Identified hazard3.Effect of hazard4.Hazard causal factors(varying levels of detail)5.Recommended mitigating action(design requirement,safety devices,warningdevices,special procedures and training,caution and warning notes,etc.)6.Risk assessment(initial andfinal)Figure8.4shows the columnar format O&SHA worksheet recommended for SSP usage.This particular worksheet format has proven to be useful and effective in many applications,and it provides all of the information necessary from an O&SHA.System: Operation:Operating and Support Hazard Analysis Analyst:Date:Task HazardNo.Action FMRI Status1324 567111391081214 Hazard Causes Effects IMRI Recommended CommentsFigure8.4Recommended O&SHA worksheet.138OPERATING AND SUPPORT HAZARD ANALYSIS8.7WORKSHEET139The following instructions describe the information required under each column entry of the O&SHA worksheet:1.System This entry identifies the system under analysis.2.Operation This entry identifies the system operation under analysis.3.Analyst This entry identifies the name of the O&SHA analyst.4.Date This entry identifies the date of the O&SHA analysis.5.Task This column identifies the operational task being analyzed.List anddescribe each of the steps or tasks to be performed.If possible,include the purpose and the mode or phase of operation being performed.6.Hazard Number This is the number assigned to the identified hazard in theO&SHA(e.g.,O&SHA-1,O&SHA-2).This is for future reference to the particular hazard source and may be used,for example,in the hazard action record(HAR).The hazard number is at the end of the worksheet because not all tasks listed will have hazards associated with them,and this column could be confusing at the front of the worksheet.7.Hazard This column identifies the specific hazard,or hazards,that couldpossibly result from the task.(Remember:Document all hazard consider-ations,even if they are later proven to be nonhazardous.)8.Causes This column identifies conditions,events,or faults that could causethe hazard to exist and the events that can trigger the hazardous elements to become a mishap or accident.9.Effects This column identifies the effect and consequences of the hazard,should it occur.The worst-case result should be the stated effect.10.Initial Mishap Risk Index(IMRI)This column provides a qualitativemeasure of mishap risk significance for the potential effect of the identified hazard,given that no mitigation techniques are applied to the hazard.Risk measures are a combination of mishap severity and probability,and the recommended values from MIL-STD-882are shown below.Severity Probability1.Catastrophic A.Frequent2.Critical B.Probable3.Marginal C.Occasional4.Negligible D.RemoteE.Improbable11.Recommended Action This column establishes recommended preventivemeasures to eliminate or mitigate the identified hazards.Recommendations generally take the form of guideline safety requirements from existing sources or a proposed mitigation method that is eventually translated intoa new derived SSR intended to mitigate the hazard.SSRs are generatedafter coordination with the design and requirements organizations.Hazard mitigation methods should follow the preferred order of precedence140OPERATING AND SUPPORT HAZARD ANALYSISestablished in MIL-STD-882for invoking or developing safety require-ments,which are shown below.Order of Precedence1.Eliminate hazard through design selection.2.Control hazard through design methods.3.Control hazard through safety devices.4.Control hazard through warning devices.5.Control hazard through procedures and training.12.Final Mishap Risk Index(FMRI)This column provides a qualitativemeasure of mishap risk significance for the potential effect of the identified hazard,given that mitigation techniques and safety requirements are applied to the hazard.The same values used in column10are also used here.ments This column provides a place to record useful informationregarding the hazard or the analysis process that are not noted elsewhere.14.Status This column states the current status of the hazard,as being eitheropen or closed.Note in this analysis methodology that each and every procedural task is listed and analyzed.For this reason,not every entry in the O&SHA form will constitute a hazard since not every task is hazardous.This process documents that the O&SHA considered all tasks.8.8HAZARD CHECKLISTSHazard checklists provide a common source for readily recognizing hazards.Since no single checklist is ever really adequate in itself,it becomes necessary to develop and utilize several different checklists.Utilizing several checklists may result in some repetition,but complete coverage of all hazardous elements will be more cer-tain.If a hazard is duplicated,it should be recognized and condensed into one hazard.Remember that a checklist should never be considered a complete and final list but merely a catalyst for stimulating hazard recognition.Chapter4on PHL analysis provided some example general-purpose hazard checklists applicable to system design.Figure8.5provides an example hazard checklist applicable to operational tasks.This example checklist is not intended to represent all hazard sources but some typical considerations for an O&SHA.8.9SUPPORT TOOLSThe functionalflow diagram(or functional block diagram)simplifies system design and operation for clarity and e of the FFD for O&SHA evaluation of procedures and tasks is recommended.Indentured equipment lists were defined in Chapter 1as a valuable aid in under-standing systems and performing hazard analyses.ITLs are also developed to assist in the design and development of operations.Operational sequence diagrams (OSDs)are a special type of diagram used to define and describe a series of operations and tasks using a graphical format.The OSD plots a flow of information,data,or energy relative to time (actual or sequen-tial)through an operationally defined system using standard symbols to relate actions taken.Actions in the OSD may include inspections,data transmittal /receipt,Figure 8.6Operational sequence diagramsymbols.Figure 8.5Operational hazard checklist.8.9SUPPORT TOOLS141142OPERATING AND SUPPORT HAZARD ANALYSISFigure8.7Example operational sequence diagram.storage,repair,decision points,and so forth.The OSD helps to display and simplify activities in a highly complex system and identify procedurally related hazards.Symbols used in the OSD are adapted from the American Society of Mechanical Engineers(ASME)flowchart standards,as shown in Figure8.6.The OSD method-ology was originally defined in MIL-H-46855[1].An example OSD is shown in Figure8.7for a missile system.Note that the subsystems are denoted along the top,and time is denoted in the left-hand column.8.10GUIDELINESThe following are some basic guidelines that should be followed when completing the O&SHA worksheet:1.Remember that the objective of the O&SHA is to evaluate the system designand operational procedures to identify hazards and to eliminate or mitigate operational task hazards.2.Start the O&SHA by populating the O&SHA worksheet with the specific tasksunder investigation.3.A hazard write-up in the O&SHA worksheet should be clear and understand-able with as much information necessary to understand the hazard.4.The O&SHA hazard column does not have to contain all three elements of ahazard:hazardous element(HE),initiating mechanisms(IMs),and outcome (O).The combined columns of the SSHA worksheet can contain all three components of a hazard.For example,it is acceptable to place the HE in the hazard section,the IMs in the cause section and the O in the effect section.The hazard,causes,and effects columns should together completely describe8.11EXAMPLES143the hazard.These columns should provide the three sides of the hazard triangle(see Chapter2).8.11EXAMPLES8.11.1Example1To demonstrate the O&SHA methodology,a hypothetical procedure will be ana-lyzed.The selected example procedure is to replace an electrical outlet receptacle in a weapons maintenance facility.The receptacle contains220VAC,so the pro-cedure is a hazardous operation.The detailed set of tasks to accomplish this pro-cedure is provided in Table8.2.Tables8.3,8.4,and8.5contain the O&SHA worksheets for this example.The following should be noted from this example analysis:1.Every procedural task is listed and evaluated on the worksheet.2.Every task may not have an associated hazard.3.Even though a task may not have an identified hazard,the task is still docu-mented in the analysis to indicate that it has been reviewed.8.11.2Example2In order to further demonstrate the O&SHA methodology,the same hypothetical Ace Missile System from Chapters4,5,and6will be used.The system design is shown again in Figure8.8.Figure8.9shows the basic planned operational phases for the Ace Missile Sys-tem.Phase4has been selected for O&SHA in this example.The detailed set of tasks to accomplish phase4procedure is provided in Table8.6.TABLE8.2Example Electrical Outlet ReplacementProcedureStep Description of Task1.0Locate circuit breaker2.0Open circuit breaker3.0Tag circuit breaker4.0Remove receptacle wall plate—2screws5.0Remove old receptacle—2screws6.0Unwire old receptacle—disconnect3wires7.0Wire new receptacle—connect3wires8.0Install new receptacle—2screws9.0Install old wall plate—2screws10.0Close circuit breaker11.0Remove circuit breaker tag12.0Test circuitT A B L E 8.3O &S H A E x a m p l e 1—W o r k s h e e t 1144T A B L E 8.4O &S H A E x a m p l e 1—W o r k s h e e t 2145T A B L E 8.5O &S H A E x a m p l e 1—W o r k s h e e t 3146It should be noted that in a real-world system the steps in Table 8.3would likely be more refined and consist of many more discrete and detailed steps.The steps have been kept simple here for purposes of demonstrating the O&SHA technique.Tables 8.7through 8.10contain the O&SHA worksheets for the Ace Missile System example.- Warhead - Battery- Computer/SW - Receiver - Destruct - Fuel- Rocket BoosterFigure 8.8Ace Missile System.Phase 6 Phase 7Phase 1 Phase 2 Phase 3 Phase 4 Phase 5 Figure 8.9Ace functional flow diagram of missile operational phases.TABLE 8.6Missile Installation in Launch Tube Procedure Step Description of Task4.1Remove missile from ship storage locker.4.2Load missile onto handcart transporter.4.3Transport missile to launch tube.4.4Hoist missile into launch tube.4.5Run missile tests.4.6Install missile cables.4.7Remove S&A pins.4.8Place missile in standby alert.8.11EXAMPLES147T A B L E 8.7O &S H A E x a m p l e 2—W o r k s h e e t 1148T A B L E 8.8O &S H A E x a m p l e 2—W o r k s h e e t 2149T A B L E 8.9O &S H A E x a m p l e 2—W o r k s h e e t 3S y s t e m :A c e M i s s i l e S y s t e mO p e r a t i o n :M i s s i l e I n s t a l l a t i o n i n L a u n c h T u b eO p e r a t i n g a n d S u p p o r t H a z a r d A n a l y s i s A n a l y s t :D a t e :T a s kH a z a r d N o .H a z a r dC a u s e s E f f e c t s I M R IR e c o m m e n d e d A c t i o n F M R I C o m m e n t s S t a t u sT a s k 4.5:R u n m i s s i l e t e s t s .O H A -9M i s s i l e t e s t c a u s e s m i s s i l e l a u n c h .T e s t e q u i p m e n t f a u l t ;s t r a y v o l t a g e o n t e s t l i n e s .I n a d v e r t e n t m i s s i l e l a u n c h ,r e s u l t i n g i n p e r s o n n e l i n j u r y .1D D e v e l o p t e s t e q u i p m e n t p r o c e d u r e s a n d i n s p e c t i o n s R e q u i r e t r a i n e d a n d q u a l i fie d p e r s o n n e l C a u t i o n n o t e t o e n s u r e S &A p i n s a r e i n s t a l l e d 1E O p e nO H A -10M i s s i l e t e s t c a u s e s d e s t r u c t s y s t e m i n i t i a t i o n .T e s t e q u i p m e n t f a u l t ;s t r a y v o l t a g e o n t e s t l i n e s .I n a d v e r t e n t m i s s i l e d e s t r u c t i n i t i a t i o n ,r e s u l t i n g i n p e r s o n n e l i n j u r y .1D D e v e l o p t e s t e q u i p m e n t p r o c e d u r e s a n d i n s p e c t i o n s R e q u i r e t r a i n e d a n d q u a l i fie d p e r s o n n e l C a u t i o n n o t e t o e n s u r e S &A p i n s a r e i n s t a l l e d 1E O p e nT a s k 4.6:I n s t a l l m i s s i l e c a b l e s .O H A -11C a b l e s i n c o r r e c t l y i n s t a l l e d ,r e s u l t i n g i n m i s m a t e d c o n n e c t o r s t h a t c a u s e w r o n g v o l t a g e s o n m i s s i l e l a u n c h w i r e .H u m a n e r r o r r e s u l t s i n i n c o r r e c t c o n n e c t o r m a t i n g t h a t p l a c e s w r o n g v o l t a g e s o n c r i t i c a l c o n n e c t o r p i n s .I n a d v e r t e n t m i s s i l e l a u n c h ,r e s u l t i n g i n p e r s o n n e l d e a t h /i n j u r y .1DR e q u i r e t r a i n e d a n d q u a l i fie d p e r s o n n e l C a u t i o n n o t e t o e n s u r e S &A p i n s a r e i n s t a l l e d D e s i g n c o n n e c t o r s t o p r e v e n t m i s m a t i n g1E O p e nP a g e :3o f 4150。
CISSP Review Notes
THIS STUDY GUIDE WAS GREATLY IMPROVED BY HENRY GUZ MANIN JANUARY2005THANKS FOR YOUR CONTRIBUTIONJanuary2006:Thanks to Intensified for his correction about CSMA/CA being used on WLAN and NOT CSMA/CD as it was specified.Good catch!!Access ControlTelecommunications&Network SecuritySecurity Management PracticesApplication and System DevelopmentCryptographySecurity Architecture and ModelsOperations SecurityBCP and DRPLaw,Investigation,and EthicsPhysical SecurityAccess ControlAccess control protects the system s and resources from unauthorized access,and,usually determ ines the level of authorization.Subject-Entity requiring access to an object–user or process.(Active).Object-Entity to which access is requested–file,process.(Passive).Access control consists of the following primary areasIdentificationAuthenticationAuthorizationAccountabilityThe last three of these are largely com prised of‘logical access controls’.IdentificationBiometrics Very sophisticated and accurate,but expensive.Type1error Rejection on authorized individuals–false reject rate(FRR)Type2error Acceptance of individual that should be rejected(FAR)CER Crossover error rate–point at which false acceptance equals false rejection–expressed as a percentage.Important m easurement of biometric system’s accuracy.The lower the better.Other barriers to widespread adoption of biometrics include user acceptance,enrollment tim e and throughput.Collected biometric images are stored in a corpus.Effectiveness versus Acceptance of biometric devicesOrder of Effectiveness Order of AcceptancePalm scan Iris scanHand geom etry Keystroke dynamicsIris scan Signature dynamicsRetina pattern Voice verificationFingerprint Facial recognitionVoice verification FingerprintFacial Recognition Palm scanSignature Dynamics Hand GeometryKeystroke Dynamics Retina PatternAuthenticationThe three general types of authentication areSom ething a person knows.Som ething a person has.Som ething a person is.Strong authentication requires two of these three(two-factor authentication). PasswordsPasswords are the m ost com monly used,but also considered one of the weakest.A cognitive passwords is information only you should know,like your m other’s m aiden nam e.One-time PasswordsThere are two types of one-tim e password–synchronous and asynchronous.One-tim e passwords are usually generated by a token device that com municates with anauthentication service.Synchronous–Token device synchroniz es with authentication server via a tim e based or event based synchronization.Token device and auth server share the sam e secret key.Asynchronous–Uses a challenge-response schem e to com munication with theauthentication server.Other authentication mechanismsPrivate key–digitally signing a m essage.Passphrase–transformed into a virtual passwordMem ory card–holds information but does not process it.ATM card.Sm art card–capability of processing information.AuthorizationThe system knows who you are(authentication)and m ust now decide if you can carry out the requested actions.This is where authorization com es into play.Access criteria is the crux of authorizationAccess criteria types can be broken up intoRolesGroupsPhysical or logical(network)locationTim e of dayTransaction typeAll access criteria should default to“no access”.Need to know principleManagement’s job is to determ ine the“need to know”.Adm inistrator job is to configure access control and security m echanisms to fullfil the need to know requirements.Single Sign-on MechanismsScripting Batch files containing logic details.Insecure.High m aintenance recording and m aintaining scripts.KerberosKerberos is a single sign-on system that uses sym metric key cryptography(DES)and end to end encryption.Kerberos eliminates the need for transm itting passwords over the network.In order to implem ent Kerberos,all software in use m e be Kerberoscom patible or,“kerberized”.The com ponents of Kerberos areKDC Key distribution center.Holds user’s and services’keys.The foundation of kerberos is the client and server’s trust in the KDC.The KDC actually consists of a ticket granting service and authentication server.Principals Entities requiring KDC services–users,apps or services.The KDC and each principal share a secret key.Ticket Tickets are created by the KDC and given to a principle when that principle needs to authenticate to another principle.Realm A“realm”is the set of com ponents and principles that the KDC provides services for.AS Authentication service–this is part of the KDC.Kerberos Authentication ProcessThe client trusts the KDC and the services trust the KDC due to their secret keys.An overview of the process when a client wan’t to use a service via Kerberos isThe client sends its user id and the nam e of the requested service to the KDC.The KDC provides a session key for the client and service to use.One is encrypted with the user secret key and the other with the service secret key.The KDC generates a service ticket containing both session keys.This ticket is sent back to the client.The user enters their password and if the password is correct,the client converts it into the necessary key to decrypt the client session key in the ticket.The client decrypts the client portion of the ticket to get the session key and sends the ticket on to the service.The service uses its own private key to decrypt the session key.The user and service are now authenticated to each other and com municate withencrypted data via the session key.Secret key Shared between KDC and a principle.Session key Shared between two principles.Kerberos weaknessKerberos has a number of weaknesses that can m ake it vulnerable to attack.Som e of these areThe KDC is a single point of failure.The secret keys are tem porarily stored on user’s workstations,in m emory,etc.Session keys are decrypted and reside on user’s workstations.Vulnerable to password guessing.Does not protect network traffic.When a user changes password,the KDC database needs to be updated with a new corresponding secret key.Replay attacks can be used against Kerberos.Secure European System for Applications in a Multiuser Environment.Sesam e is a single sign-on system designed to address som e of the kerberos weaknesses.It uses public key cryptography for distribution of secret keys and supports MD5and CRC32hashing.Still vulnerable to password guessing.Sesam e uses the Needham-Schroeder protocol.No local processing.Thin clients for the user to login to the network just to be able to use the com puter.Kryptoknight is another single sign-on protocol similar to Kerberos.The m ain difference is that there is a peer-to-peer relationship am ong parties and the KDC.An access control m odel is a fram ework that dictates how subjects access objects.There are three m ain types of access control m odel m andatory access control,discretionary access control and role-based access control.The creator of a file is the‘owner’and can grant ownership to others.Access control is at the discretion of the owner.Most com mon implem entation is through access control lists.Discretionary access control is required for the Orange Book “C”Level.Much m ore structured.Is based on security labels and classifications.Access decisions are based on clearance level of the data and clearancelevel of the user,and,classification of the object.Rules are m ade by m anagement,configured by the adm inistrators and enforced by the operating system.Mandatoryaccess control is required for the Orange Book“B”Level.Continually adm inistered set of controls by role within organization.Access rights assigned to roles–not directly to users.Roles are tighter controlled than groups-a user can only have one role.Can use different types of RBACRole-based Role within organization.Task-based Specific task assigned to the user.Lattice-based Upper and Lower boundsAccess Control Techniques and TechnologiesOnce a com pany decides on the access control m odel to use,the technologies andtechniques to implement that m odel need to be determ inedRole-based Can be used with MAC–Labels assigned to roles.Or with non-discretionary controls such as NT Groups.Rule-based Example-Router or firewall rules–user cannot change.•Restricted interfacesMenus and shells–ATM m achineDatabase viewsPhysically constrained interfaces.•Access Control MatrixTable of subjects and objects indicating access.•Capability TablesSpecifies the access a certain subject has to specific objects.Corresponds to arow in the access control m atrix.Bound to subject.Access Control ListsBound to object.List of subjects authorized to access a specific object,and,the level of access/authorization.•Content-dependantDatabase views are a good example–access is based on the data content itself.•Context-dependantAccess is based on location,tim e of day,previous access history,etc.Access Control AdministrationAccess control adm inistration is either centralized,decentralized or a hybrid of the two.Examples of centralized access control technologies includeRADIUS Rem ote Authentication Dial-In User ually used for dialup.Access server requests user login credentials and forwards to a backend RADIUS server.Can use callback for additional security.TACACS(Terminal Access Controller Access Control System).There are several types of TACACSTACACS Com bines its authentication and authorization processes.Passwords arestatic.XTACACS Separates authentication,authorization and accounting processes.TACACS+XTACACS with two-factor user authentication.Supports tokenauthentication.Security DomainA security dom ain is defined as a“realm of trust”.Subjects and objects share com monsecurity policies and procedures and are m anaged by the sam e system.Also used within operating system s and applications to protect system files or processes.It can also be defined as the com plete set of resources available to a user.Access Control MethodsThere are three broad categories of access control layersAdm inistrativeTechnicalPhysicalPolicies and procedures Guidelines+standards+baselinesPersonnel controls Hiring,firing,promotions,transfers,separation of duties,rotation of duties,forced vacation.Supervisory structures Clear lines of reporting.Awareness TrainingSecurity Testing Drills,penetration testing,queries to em ployees,interviews,reviews.Network segregation.Perimeter security.Com puter controls.Work area separation.Data backups.Cabling.System Access–See previous access control m echanisms.Network architecture–Logical controls can provide segregation and protection of an environment.I/P address ranges,subnets,routing between networks,etc.Network Access–Logical network access controls–routers,switches,NICs,bridges.Encryption and ProtocolsControl Z one–Technical and physical control.Surrounds and protects network devices that em it electrical signals.TEMPEST related.Access Control TypesEach control m ethod can also perform different functionality.The functionality types are PreventativeDetectiveCorrectiveDeterrentRecoveryCom pensatingFor examplePreventative-AdministrativePolicies and procedures,effective hiring practices,background checks,data classification, security awareness training.Preventative-PhysicalBiometrics,badges,swipe cards,guards,dogs,m otion detectors,fences,m antraps,locks and alarms.Preventative-TechnicalPasswords,biometrics,sm art cards,encryption,call-back system s,database views,antivirus software,ACLs,firewalls,IDSAuditingAuditing capabilities ensure that users are held accountable for their actions,verify that policies are enforced,deter improper actions and are an investigative tool.There are3m ain types of audit toolAudit reductionVariance detectionAttack-signature detectionAudit data m ust be protected from unauthorized viewing and m odif ication.Access Control PracticesThe following tasks should be carried out regularlyDeny access to undefined or anonymous accountsLimit and m onitor adm inistration accountsSuspend access after a number of failed loginsRem ove accounts as soon as som eone leaves an organization.Format Access Control ModelsThe Bell LaPadula m odel is built on state m achine concepts and focuses on confidentiality.The objective of this m odel is to ensure that the initial state is always secure and that transitions always result in a secure state.Bell LaPadula defines asecure state through3m ultilevel propertiesSimple Security Policy No read up–a lower level subject cannot read a higher level object.Protecting confidentiality.Security*(star)property No write down–do not allow confidential information to be written to a local level,where a lower level subject will be able to view it.Discretionary Security Property Uses a discretionary access control m atrix tom anage exceptions.The Biba m odel is lattice based and focuses on integrity m ore than confidentiality.Biba specifies the following three axiomsSimple Integrity Axiom No read down.A higher level subject cannot read information from a lower level.This prevents higher level reports and data being corrupted by lower level(and less trustworthy)information.Integration*(Star)Axiom No write up.A subject cannot write data above itssecurity level–higher level data m ight be com promised by lower level,less trustworthy data.A subject at one integrity level cannot invoke a subject at a higher integrity levelwas developed after the Biba m odel and ensures integrity.The Clark-Wilson Model utilizes separation of duties to ensure that authorized users do not m ake unauthorized changes to data.In this way task are divided into different parts and different subjects each do different parts.Often tim es subjects under the Clark-Wilson Model cannot access data directly,but m ust instead go through a program or other third party,which helps to ensure the subject has the proper classification.This m odel has em p hasis on internal and external consistency.Clark-Wilson uses well form ed transactions,separation of duties and the labeling of subjects and objects with programs to m aintain integrity.Security properties are partly defined through five certification ru les,suggesting the check that should be conducted so that the security policy is consistent with the application requirements.CDI–Constrained Data Item A data item whose integrity m ust be preserved.IVPS–Initial Verification Procedures Confirm that all CDIs are in a valid integrity state when the IVP is run.TP–Transformation Procedure Manipulates the CDIs through a well-formedtransaction,which transforms a CDI from one valid integrity state to another.UDI–Unconstrained Data Item Data item s outside of the control area such as input information.Any TP that takes a UDI as input m ust either convert the UDI into a CDI or reject the UDI and perform no transaction at all.Unauthoriz ed disclosure of informationThere are several ways in which information can be inadvertently disclosed.The follow item s are related to information disclosureObject Reuse Reassigning m edia to a subject when m edia m ight still contain som e residual information.Make sure m edia is cleaned.Degaussing works best.Object reuse controls are required for TCSEC B2and above.Emanation Picking up radiation em itted by devices.Can use TEMPEST technology to block.TEMPEST is very expensive,som e alternatives areWhite Noise–Unif orm spectrum of random electrical signals used to disguise realdata.Z ones–Control z ones.Access Control MonitoringKeeping track of who attem pts to access specific resources,access control m onitoring is an important detective m echanism usually carried out by intrusion detection system s Network Based IDS Monitors network,or a segm ent of the network(passive).Known as NIDS.Placem ent of sensors is a critical part of configuring a network based IDS.Place a sensor on the outside firewall to detect attacks and inside the firewall to detect invasions.Another factor to consider is that the network traffic should never exceed the IDS threshold,or the IDS m ay just start to drop packets.Host-Based Monitors a specific system,such as your critical servers.Intrusion detection system s have two m ain m ethods of operationKnowledge/Signature based This type of IDS looks for known attacks and istherefore weak vs new attacks.There are less false alarms.This type of IDS m ay also fail to detect“slow”attacks extended over a long period of tim e.Behavior based/Statistical IDS This type of IDS detects deviations from expected behavior of users and system s.May use expert system s.Detects new attacks anddoesn’t rely on a database of signatures to be updated,but,can cause m ore falsepositives.Relational Database SecurityRelational database security is a growing area of concern.The following are areasrelating to database technology and securitySchema Description of the database and its ually written using a DDL.Cardinality Number of rows in a table.Degree Number of columns in a table.Domain The set of all allowable values an attribute can take.Entity Integrity&Referential IntegrityView-Virtual table defined from other tables that is used to restrict access,hideattributes and provide content-dependant access.Views help implem ent least privilege and need to know principles.To protect against“inference attacks”,databases m ay have a m inimum query set size and prohibit query of“all but one”tuples.Highly secure system s m ay also em ploycontext dependant access control where the tuples a user can read are based on those already read.ThreatsThe m ain categories of threat to access control m echanisms areDictionary attack.Brute force attack.Spoofing at login–fake login screen to capture details.A“trusted path”can m it igate login spoofing.The following m easures are used to com pensate for internal and external accessviolationsBackupsRAIDFault toleranceBusiness continuity planningInsuranceTopTELECOMMUNICATIONS&NETWORK SECURITYOpen Systems Interconnect(OSI)modelDeveloped early1980s and introduced in1984•Application|Presentation|ApplicationSession|____________Transport<-->Host to HostNetwork<-->Internet Layer.Data Link|Physical|Network Access Layer.“Each protocol at a specific OSI layer com municates with a protocol that operates at the sam e OSI layer on another com puter.This happens through encapsulation”The protocols,technologies and com puters that operate within the OSI m odel are called open systems.Application LayerThe application layer works closest to the user and handled m essage exchanges,terminal sessions,etc.The application does not include the actual applications,but the protocols(APIs)that support the applications.Examples of protocols running in the application layer includeSMTP,HTTP,LPD,FTP,WWW,Telnet,TFTPPresentation LayerThe presentation layer received data from the application layer and puts it into a form at that all com puters using the OSI m odel can understand.The presentation layer is not concerned with the m eaning of data,but the correct syntax and form at.The presentation layer can often be considered a“translator”.This layer also handles encryption and com pression.ASCII,JPEG,TIF,GIF,Encryption,Com pression,MIDI,MPEGSession LayerWhen two com puters need to com munication,or transfer information,a connectionsession needs to be set up between them.The session layer is responsible forestablishing a connection,m aintaining it during data transfer and releasing it when done.The session layer works in3phasesConnection establishmentData TransferConnection releaseCom mon protocols at the session layer areSSL,NFS,SQL,RPCTransport LayerWhen two com puters are going to com municate,they m ust first agree on how m uch information each will send at a tim e,how to determ ine if data was lost in order toretransmit and other parameters.The com puters agree on these parameters through a process at the transport layer,OSI layer4.The transport layer helps provide m ore reliable data transfer,error correction and flow control.It assem bles data into a stream for transm itting over the network,and handledm ultiplexing if necessary.The transport layer also handles the teardown of virtualcircuits and the m ultiplexing of upper layer applications.TCP,UDP,SPXNetwork LayerThe m ain responsibility of the network layer is to insert information into the packet’s header so that it can be properly routed.Routing protocols build and m aintain their tables at this layer.The protocols at this layer do not ensure packet delivery–they rely on the transport layer for that.Protocols operating at this level includeIP,ICMP,RIP(Routing information protocol),OSPF(Open shortest path first),BGP(Border gateway protocol)and Internet group m anagement protocol(IGMP)Most routers also run in the network layer.Data Link LayerAs data travels down the ISO stack it com es to a point where it needs to be translated into LAN or WAN binary form at for line transm ission.This happens at the data link layer.The data link layer is where the operating system knows what form at the data fram e m ust be in to transm it over Token Ring,Ethernet,FDDI,ATM,etc.Network cards bridge the data link and physical layer.The data link layer actuallyconsists of two sub layersMedia Access Control(MAC)Logical Link Control(LLC)Protocols operating in the data link layer includeSLIP,PPP,RARP,L2F,L2TP,ISDN ARPBridges operate in the data link layer.Physical LayerThe physical layer converts bits into voltage for transm ission.This layer controlssynchronization,data rates,line noise and physical m edium access.Protocols operating in the physical layer includeRS232,SONET,HSSI,X.21Repeaters operating in the physical layer.OSI defines6basic security services to secure OSI com municationsAuthenticationAccess ControlData confidentialityData integrityNon-repudiationLogging and MonitoringIn addition,the OSI m odel defines8security m echanisms.A security m echanism is a control that is implemented in order to provide the6basic security servicesEnciphermentDigital SignaturesAccess ControlData IntegrityAuthenticationTraffic PaddingRouting ControlNotarizationTCP/IPI/P is a network layer protocol and provides datagram routine services.Two m ain protocols work at the transport layer,TCP and UDP.TCP Handshake1.Host--------SYN--------->Host B<-----SYN/ACK----->---------ACK-------->The TCP/IP m odel has4layersApplicationHost to hostInternetNetwork AccessThe TCP/IP m odel layers correspond to the ISO m odel layers as followsApplication Application,presentation,session.Host to Host TransportInternet NetworkNetwork Access Data Link,PhysicalThe Host-to-host layer handlesTCP-Virtual Circuit,sequenced,slower,m ore reliableUDP-“Best effort”,connectionless.Internet layerI/P-No guarantee of delivery,delivery in sequence or only once.ARP-I/P to MACRARP-MAC to I/PICMPThe I/P header contains a protocol field.Som e com mon protocols are-ICMP–IGMP6-TCP17–UDPWithin the I/P protocol suite,when an application form ats data for sending overthe network,it is a message.At the transport layer,TCP works on the data and it is now a segment i.Thesegm ent is passed to the network layer.The network layer adds addressing and routine and the bundle is now called adatagram.The datagram is passed off to the data link layer which fram es the datagram witha header&trailer.It is now called a frame.TCP UDPApplication Layer Message MessageTransport Layer Segm ent PacketNetwork Layer Datagram DatagramData Link Layer Fram e Fram eClass A Unauthoriz ed access of restricted network services.Also called“login abuse”. Refers to legitim ate users accessing network services that should be restricted to them.Class B Unauthoriz ed use of a network for non-business purposes.Class C EavesdroppingClass D DOS and other disruptionsClass E Network Intrusion.Refers to the use of unauthorized access to break into the network from the outside.Classic cases are spoofing,piggybacking and backdoor exploitation.Class F Probing.An active variation of eavesdropping.Additional Attacks SYN attacks,Buffer Overflow,Teardrop attack and Sm urf.Common Session Hi-jacking attacks•IP Spoofing attacks.•TCP sequence number attacks.•Other fragmentation attacks–using fragmented packets to hide true contact. NETWORKINGMost of the differences between LAN and WAN take place at the data link layer“Two LANs connected by a router is an internetwork,not a bigger LAN.Each LAN has its own addressing schem e and broadcast and com munication m echanisms.If they are connected by different data link technologies such a fram e relay of X.25then we are looking at a WAN”Usually a bus or star topologyIEEE802.3standardShared m edia–all devices take turns and detect collisionsUses broadcast and collision dom ainsCSMA/CD access m ethod(Carrier Sense Multiple Access with Collision Detection)Uses coaxial or twisted pair.Common Implementationses coaxial cable.Max length of185m eters and provides up to 10mbs es BNC connectors.es thicket coaxial cable.Longer cable segm ents and lessinterference.10baseT Twisted-pair copper wiring.RJ45connectors,usually in a star topology with a hub or switch.Fast Ethernet Regular ethernet running at100mbps over twister pair wiring.Ethernet Types Table10base2,ThinNet Co-Axial10mbps10base5,ThickNet Co-Axial10mbps10base-T UTP10mbps100base-FX,Fast UTP100mbps1000base-T UTP1,000mbps802.5standard,originally developed by IBMSignal travels in a logical ringEach com puter is connected to a hub called a Multistation Access Unit(MAU) 16mbps capacityActive Monitor–removes fram es that are continually circulatingBeaconing–attem pts to work around errors.Fiber Distributed Data InterfaceDeveloped by ANSIHigh speed token-passing m edia access technologySpeed of100mbvps–usually used as a backbone network using fiber optics.Fault tolerance–second counterrotating ring.Can be used up to100kms,so popular in MANsCDDI(copper distributed data interface)is a version that can be used locally.802.8standard.CABLINGLAN Media Standard CharacteristicsEthernet802.3Shared m ediaBroadcast&Collision DomainsCSMA/CDCoaxial or twisted cable10mbps–1gbpsToken Ring802.5Devices connect to center MAUToken-passing access m ethodTransm ission speeds of4-16m pbsActive m onitor and beaconing FDDI802.8Token-passing access m ethodDual counter rotating ring–fault tolerance100mbps over fiber-opticLong distance at high speed*CDDI works over UTPBandwidth Size of pipeData Rate Am ount of dataCoaxialCopper core surrounded by shielding layer。
无线传感器网络中的信任管理
ISSN 1000-9825, CODEN RUXUEW E-mail: jos@Journal of Software, Vol.19, No.7, July 2008, pp.1716−1730 DOI: 10.3724/SP.J.1001.2008.01716 Tel/Fax: +86-10-62562563© 2008 by Journal of Software. All rights reserved.∗无线传感器网络中的信任管理荆琦1,2, 唐礼勇1,2+, 陈钟1,21(北京大学信息科学技术学院软件研究所网络信息安全研究室,北京 100871)2(北京大学高可信软件技术教育部重点实验室,北京 100871)Trust Management in Wireless Sensor NetworksJING Qi1,2, TANG Li-Yong1,2+, CHEN Zhong1,21(Network and Information Security Laboratory, Institute of Software, School of Electronics Engineering and Computer Science, PekingUniversity, Beijing 100871, China)2(Key Laboratory of High Confidence Software Technoloies of the Ministry of Education, Peking University, Beijing 100871, China)+ Corresponding author: E-mail: tly@Jing Q, Tang LY, Chen Z. Trust management in wireless sensor networks. Journal of Software, 2008,19(7):1716−1730. /1000-9825/19/1716.htmAbstract: Cryptography based security solutions are not enough for WSNs when there are attacks from interior,which are caused by compromised nodes. Trust management can deal with this problem efficiently, and enhance thesecurity, reliability and impartiality of the system. This paper gives a detailed introduction to the characteristics, thetaxonomy, and the design of the framework, the vulnerability analysis, the attack models and the countermeasures.Among which the design of the framework, including the trust factors, the computation models and the applicationof trust, is the core of a trust management system and is given a deep insight into. In the end, several typical trustmanagement systems are introduced. A panoramic view and detailed analysis of current trust based systems inWSNs are given.Key words: wireless sensor networks (WSNs); trust management; reputation; vulnerability; watchdog摘要: 作为对基于密码体系的安全手段的重要补充,信任管理在解决WSNs(wireless sensor networks)中的内部攻击,识别恶意节点、自私节点及低竞争力节点,提高系统安全性、可靠性和公平性等方面有着显著优势.综述了WSNs环境下信任管理的特点、分类方法、框架设计、脆弱性分析、攻击模型及对策,在此基础上介绍了WSNs下的典型信任管理系统.以信任计算模型为中心的WSNs环境下信任管理框架的设计是信任管理系统的核心,从信任要素、信任计算模型和信任值的应用这3个方面对其进行了深入讨论.最后,总结了WSNs环境下信任管理的研究现状,提出了值得参考的研究发展方向.关键词: 无线传感器网络;信任管理;信誉;脆弱性;监控机制中图法分类号: TP393文献标识码: A无线传感器网络(wireless sensor networks,简称WSNs)近年来受到了学术界和产业界的一致关注.随着∗ Supported by the National Natural Science Foundation of China under Grant No.60773163 (国家自然科学基金)Received 2007-10-12; Accepted 2008-03-27荆琦等:无线传感器网络中的信任管理1717WSNs应用的日益复杂,其安全需求也呈现多样性,传统的基于密码体系的安全机制主要用于抵抗外部攻击,无法有效解决由于节点被俘获而发生的内部攻击.而且由于传感器节点能力所限,WSNs中往往采用基于对称密码算法的安全措施,当节点被俘获时很容易发生秘密信息泄露,如果无法及时识别被俘获节点,则整个网络将被控制.在实际应用中,WSNs常常被部署在战场环境或者无法实施物理保护的环境中,节点被俘获的现象极易发生,这就需要有效机制及时识别被俘获节点,有针对性地采取相应措施以减小系统损失.信任管理被认为是对传统的基于密码体制安全措施的有效补充,在对等网络、网格以及普适计算环境等网络环境中已被广泛研究.1 信任管理1996年,Blaze提出了信任管理的概念[1],用授权委托的方式解决“陌生人”授权问题.他提出的PolicyMaker 和KeyNote将授权与公钥绑定,互相认识的个体根据相互间信任关系直接签署授权凭证,以授权委托的方式实现信任传递,两个陌生个体之间如果存在“信任链”就可以进行授权,也可以签署间接凭证.这种信任管理系统最终体现为一个分布式授权系统,许多其他分布式授权系统,包括SPKI(simple public key infrastructure)[2], RT(role-based trust-management framework)[3],dRBAC(distributed role-based access control)[4]等,也都采用了类似思想.授权个体收集被授权个体的所有相关信息(凭证),根据本地策略和授权请求通过策略推理引擎检查一致性,决定是否授权.虽然信任委托使得对客体的访问更加灵活,但是却削弱了客体所有者对客体的控制.文献[5]对信任系统的安全性进行了研究,即在系统中的策略发生变化时,会对访问控制产生多大影响.此外,策略的一致性检验、凭证的收集也是研究重点.在这里,授权凭证的签署可以看成授权个体与被授权个体之间信任关系的体现,授权个体赋予被授权个体与其信任等级相当的权限.但是这里的“信任等级”只是对授权客体模糊的主观认知(也可能基于某些客观因素,如其他个体颁发的凭证等),个体根据自己对被授权个体的“信任”作出授权决策,以策略的方式在授权凭证中描述.在这种信任管理系统中,信任通过凭证中的授权策略间接体现,信任不能被直接而精确地表达.另一类主要的信任管理系统,对“信任”进行量化评估,个体将所有相关信息量化,包括对被评估个体的行为观察、与被评估个体的交互记录以及其他个体的意见等,利用适当的计算模型得到对方的信任值.用信任值可以灵活地调节网络安全措施的实施,包括密码算法强度、授权决策等,使之针对不同个体进行个性化管理.还可以将信任值用于路由层、应用层(如网上购物系统)等,用于提高网络的安全性、健壮性.这种信任管理系统中的信任往往体现为一个综合的信任值,不能很好地体现不同种类信任对系统的不同影响.个体间通过互相发送被评价个体的信任值来传递信任,信任管理策略主要包括抗攻击及决策应用等方面,一般较为简单,研究重点在于如何获得准确、适用的信任值.个体间的信任是各信任管理系统中一致的基本因素,在此基础上,一些研究试图将上述两类信任管理相结合,充分发挥二者各自的优势.文献[6]力图用统一的四层模型集成各种现有信任管理系统,包括信息收集层、鉴别层、语意层及评价层,各层之间相对独立,可以利用现有信任管理系统的模块,比如将PolicyMaker用于语意层的策略推理.基于信任度的授权委托模型TBAD(trustworthiness-based authorization delegation model)[7],在授权委托过程中引入信任度,使授权委托不再是简单的二值决策,并且利用信任度门限值控制授权委托深度.2 无线传感器网络中的信任管理WSNs具有节点资源有限、网络应用相对单一的特点.而且,一般情况下整个网络从属于一个机构.所以,WSNs的授权策略较为简单,无须采取授权凭证方式的信任管理.而且,基于公开密钥算法的授权凭证的签署和授权凭证中公钥的使用也不适合于资源有限的WSNs.所以,目前对WSNs的信任管理系统的研究主要集中于对节点进行信任值评估,借助信任值评估增强WSNs的安全性、健壮性等方面.在WSNs设计伊始,针对当前因特网由于起步时设计上的安全缺陷引起的众多问题,研究者一致认为安全应该渗透到WSNs设计的各个方面.对于WSNs的信任管理,一直陆续有人关注.2003年,Sapon等人基于信任管理识别问题位置以及问题区域[8],实现了基站与节点间基于地理信息的安全路由.2004年,Ganeriwal-Srivastava 提1718 Journal of Software软件学报 V ol.19, No.7, July 2008出RFSN(reputation based framework for sensor networks)[9]是一个较为完整的基于信誉的WSNs中的信任管理系统.2005年,Krasniewski等人的TIBFIT(trust index based fault tolerance for data faults in sensor networks)将信任用于安全的数据融合[10].2006年,Garth等人将信任管理用于簇头(cluster head,简称CH)选举[11].2006年以来,国内许多单位也开始针对无线传感器网络信任管理的研究,包括中国科学院软件研究所[12]、国防科学技术大学[13]、复旦大学[14]、东北大学[15]、武汉大学[16]等.随着WSNs基础研究的逐渐成熟,相关应用的逐步拓展,对WSNs中信任管理的关注也逐年上升.由于传感器节点资源有限而导致的节点自私行为,以及由于节点被俘获而导致的恶意行为等,都会严重影响WSNs的正常运行.而节点被俘获后,其存储的秘密就会暴露,这对基于密码体系的安全措施构成了很大的威胁,所以,WSNs 中安全架构的设计都要考虑如何在部分节点被俘获时仍能正常运转.用信任管理识别恶意节点、自私节点,识别错误数据,将信任管理应用于路由、数据融合、簇头选举等WSNs的各项基础支撑技术及应用支撑技术中,将信任管理与WSNs的安全架构相结合,可以全面提高WSNs的安全性和可用性.2.1 无线传感器网络中信任管理的分类2.1.1 无线传感器网络中信任管理的分类层次式信任管理是指对信任值的评估、传递以及存储等管理具有层次特点,往往与网络拓扑及信任值的应用有着紧密联系.如基于基站与传感器节点自然的层次结构而形成的以基站为中心的信任管理;在有簇结构的WSNs中,会形成基站-簇头节点-普通节点的3层信任管理;在安全的数据汇聚应用中,信任管理往往基于汇聚树的层次结构.在层次式信任管理中,信任可以逐层传递,上级存储所有下级或者相邻下级的信任值[10].信任也可以逐级汇聚,形成不同层次的信任值[16,17].平面式信任管理是指在信任管理的过程中,网络中所有节点及基站地位是平等的,采取相同的计算模型和管理策略,没有明显的中心或层次[9].2.1.2 全局信任管理和本地信任管理全局信任管理是指节点在整个网络中具有唯一的信任值,一般在有簇结构的WSNs中常见[10,16].本地信任管理则是指被评估节点在不同评估节点处的信任值可能不一致,节点根据本地存储的信任值作出决策[8,13,18],或者根据本地信任值以及邻居节点发送的信誉综合决策[9,19].2.1.3 基于信誉的信任管理和基于本地信息采集的信任管理在进行信任评估时,由于信息不完全可能会造成评估值的偏差.为了获得更为准确的信任值,往往需要综合考虑其他节点的信任评估值以修正本地的评估结果,这就是基于信誉的信任管理的基本思想[9,12,17,19].但是在WSNs中,由于节点资源有限,为了减少通信及计算耗费,有的信任管理系统在信任值评估时,只简单考虑节点本身对被评估节点的观察结果以及交互行为评价等本地信息,节省了其他节点传输信誉值的能量耗费[8,11,13,18,20−22].2.1.4 通用信任管理和应用相关信任管理通用信任管理是指综合考虑信任定义的各方面要素定义的一套完整的信任管理框架,包括信息采集、传递、存储、计算、更新等信任管理各方面的设计.信任值的计算不具有针对性,是对节点可信性的一个综合评估,可以用于WSNs网络运行及应用的所有相关技术中[9,12,19].而应用相关信任管理具有很强的针对性,信任管理过程中的所有环节设计都与特定的应用密切相关,比如用于安全路由的信任管理往往需要识别自私节点、低竞争力节点[8,13,18],而用于安全数据融合的信任管理一般不需要处理自私节点,甚至在一些系统中,当恶意节点没有发送错误数据时(只进行丢包、更改目标地址等行为)也不会影响其信任值[8,20,21].2.2 WSNs中信任管理框架由于无线传感器节点资源有限,所以WSNs环境下的信任管理框架需要根据WSNs环境的特点进行传输、计算、存储等各方面的优化.WSNs信任管理系统体系结构如图1所示.2.2.1 信任要素建立一个信任管理体系首先要明确信任的组成要素,即信任主要包括哪些方面的因素.这与信任的定义直荆琦 等:无线传感器网络中的信任管理 1719 接相关,也是整个信任管理框架设计与实现的基本依据.不同的信任定义下信任的组成要素差别很大,如Grandison-Sloman [23]认为,信任是相信实体具有在一定上下文环境下进行可靠、安全行为的能力,这个定义就明确了:① 信任是上下文相关的;② 信任包括系统可靠性和安全性等方面的因素.而实际上由于对信任的定义不同,许多信任管理系统不考虑上下文信息,也有的不考虑系统可靠性方面的问题,还有的只研究自私节点问题,Data for trust computingTrust computing unit L o c a l o b s e r v a t i o n Transmission …S e c u r e r o u t i n g S e c u r e c l u s t e r H e a d e l e c t i o n S e c u r e a g g r e g a t i o n Security scheme based on trust managementD e c i s i o n -M a k i n g u n i t Trust management in WSNs R e p u t a t i o nR e p u t a t i o n R e p u t a t i o n ……Others Cryptography Application data Sensor node Fig.1 General architecture of trust management systems for WSNs图1 WSNs 信任管理系统体系结构一般来说,WSNs 环境下信任主要来自对以下几方面因素全部或部分的综合评估:(1) 通信方面的因素在WSNs 中,控制命令或应用数据的传输是节点可被观察到的主要行为.恶意节点可能会表现为丢弃、篡改数据包等行为,自私节点也可能会因为节省能量而丢弃需要转发的数据包.通过观察节点的通信行为识别恶意节点或者自私节点,是信任管理系统的常用机制.常用的监控方法为将网卡设置为混杂模式[9,20,21,24],通过监听邻居节点的行为判断其是否正确转发了数据包.这需要在本地设置缓冲区,如果邻居节点及时转发了数据包,并且与缓冲区内的数据包一致,则认为节点可信,增加其信任值;否则,减小其信任值.但是,混杂模式下需要节点一直处于监听状态,这是十分耗能的做法,传感器节点需要定期地进入睡眠状态以节省能量.所以,许多信任管理系统不采用这种方式监控,或者在其他取代方法不可行时才采用.另一种常用的方法是修改路由协议(常采用源路由方式)[8,13,19],使目的节点在接收到数据包时回复,参与路由的各节点以及源节点如果收到了回复包,则认为邻居节点转发了数据包,增加其信任值.此外,还可以对一定时间间隔内邻居节点发送的数据包数量计数,如果超过了预设上限,可以怀疑其在进行DoS 攻击;如果没有达到预设下限,可以怀疑其为自私节点[19].通信方面的因素是大部分信任管理系统主要考虑的部分,但是,也有的信任管理系统不将其纳入考虑范围,如一些基于信任管理的安全数据融合[10,20],其信任值评估常常只考虑数据的一致性,而忽略节点的通信行为.(2) 密码学方面的因素在大部分应用中,信任管理机制是基于密码学安全机制的补充手段,用以提高网络的安全性.同时,密码机制也成为许多信任管理系统中信任评估的主要考虑因素之一.密码机制可以用于信任值的初始化——将拥有对密钥的邻居节点的信任值置为1,否则为0(信任值∈[0,1])[13].也可以用于信任值更新——若节点无法解密数据包为有意义的明文,则提高加密数据包节点的信任值,否则减低[11,19];若消息鉴别码(message authentication code,简称MAC)通过验证,则提高节点的信任值,否则,降低[19].在存在哈希链机制的系统中,如果当前哈希值不可推导,1720 Journal of Software软件学报 V ol.19, No.7, July 2008则降低相应节点的信任值;如果当前哈希值可推导,但与上一哈希值相隔甚远,则可以认为传输过程中发生丢包,根据哈希链间隔适当降低相应节点信任值[19].(3) 应用数据方面的因素数据采集是WSNs的主要应用之一,传感器节点根据应用需要采集数据,通过sink传送至信息处理服务器.后者对所采集的数据进行分析、记录,有时会回复信息.在信息上传过程中,为了减少网络中的信息流量,减小传输能耗及存储需求,常常会采用数据汇聚(data aggregation,有时也称为数据融合—— data fusion)手段.信任管理常常被用于提高系统对错误数据的容错能力,识别错误信息,提高上传数据的准确性.数据可信性判断根据粒度可以分为是否有事件发生[10]以及被报告数据的内容是否一致[20,21,25,26].在判断数据一致性时,可以与数据融合技术相结合.(4) 其他因素除了上述几个主要因素之外,根据信任管理系统设计目标的不同,还有其他一些影响节点信任值的因素.文献[20,21]认为,信任值越高的节点,被选择执行任务的几率越高,电量耗费得越快,所以将电量作为信任值计算的考虑因素之一,以延长整个网络生命周期.文献[8,18]中将节点的可用性也作为信任值计算因素之一,在基于锚节点定位的WSNs中,可以利用锚节点定期探测节点的生存状态,也可以定期发送Hello消息以确定节点是否存活.但是,节点定期休眠也会影响其可用性.基于冗余增加判断的准确性是常用手段,所以许多系统要求网络部署有足够的密度[8,18,20,21].2.2.2 信任计算信任计算是信任管理系统的核心,包括信任值预定义、信任值初始化、信任值合成等步骤,其中信任值合成与更新是信任计算的核心.在对等网络及网格计算等网络环境下,概率模型、模糊集计算模型、博弈模型及有向图等模型都被尝试,适用于不同的应用.在WSNs环境下,由于计算、存储以及通信各方面的限制,不适于应用复杂的计算模型,信任管理系统一般采用比值计算等简单方法.(1) 信任预定义信任预定义主要确定信任的表示方式,如用模糊集表示、功能性元组表示还是单数值表示,大部分模型都是单数值表示.此外,还需要进一步确定信任值定义区间,信任表示为离散式的信任等级还是连续信任值区间,正负区间对称表示还是正区间,常用的信任值定义区间如[−1,1],[0,1],或者类似[−3, −2, −1,0,1,2,3]及[0,1,2,3]的等级表示.最后,还需要定义因素映射函数,即第 2.2.1节中各类因素相对应的数据如何统一映射到相应区间内的数值表示,以参与信任值计算.(2) 信任值初始化信任值初始化与信任预定义直接相关,一般包括两种方式:全部节点统一初始化为相同信任值;或者通过一个初始化阶段进行节点信任值初始化.初始信任值分为悲观、乐观和中间值3种,相对应地,将所有节点初始化为信任值区间的最低值、最高值和中间值.悲观信任初始化可以防止恶意节点为了洗刷自身的低信任记录,伪装成新节点重新进入网络,但是不利于新节点正常加入网络.不过,由于WSNs一般结构相对静止,所以比较适合要求较严格的WSNs应用.从另外的角度来看,乐观初始化[10]也比较适合WSNs的特点——整个网络往往属于一个组织所有,具有天然的彼此完全信任的基础.有的信任管理系统通过一个初始化阶段进行信任值的初始化,一般是根据网络刚完成部署后可获得的数据进行,数据来源为第 2.2.1节中的部分因素,如文献[8,18]根据鉴别机制和可用性进行信任值初始化,文献[13]将可以解密消息并用共享对密钥加密回复的节点信任值初始化为1.(3) 信任值合成在WSNs中,信任值的合并更多地是采用简单的比值与加法计算,尽量采用简单计算模型以节省能耗.总的来说,信任值的合成包括横向、纵向与分级3种.(a) 横向合成信任值的横向合成,主要包括节点本地获取的关于被评价节点各类信任因素数据(local information,简称LI)的合成(local sum,简称LS),来自其他节点的被评价节点信誉的合成(reputation sum,简称RS),以及LI 与信誉的荆琦 等:无线传感器网络中的信任管理 1721 合成(local-reputation sum,简称LRS)三方面.其中LI 和信誉也被称为一手、二手信息.不同的信任管理系统横向合成的差异很大.由于信誉值的获得需要很大的传输能耗,所以有些系统只采取LS [8,13,18,20,21].但是,由于各类信任管理系统对于各类信任因素数据采集的方式不一样,很有可能发生信息不完整的情况,造成被评价节点的LS 不能反映其实际信任值,所以还是有些系统采用LS 与RS 相结合的方式[9,17,19].可以分别LS,RS,然后进行LRS;也可以先LS 再LRS;还可以用统一的公式直接LRS.Table 1 Analysis of computational models for trust management in WSNs 表1 WSNs 信任管理系统计算模型比较分析表Trust management systemTrust factors Trust evaluation Transverse integration Vertical integration Hierarchy integration Communication payload Computation cost Storage [19], PLUS [27] T, C,LS-RS-LRS − − − A L H TRANS [8][18] T, C,O LS − − − MP L M SecCBSN [28] T, O RS-TU V − − A, MP L H GTMS[17] I (LS+TU)-RS-LRS TR R GT A L H RFSN[9] T, C,D, O (LS+TU)-(RS+TU) -LRSTR, PR R − A, MP L H [11] T LS V − − A L H Simple weight model[20], [21] D, O LS-RS TR −GT A L M TIBFIT[10] D TU − P − −L L Exponential model [7] D TU − P − −L L BRSN[9] T, C,D, O LRS+TU TR, PR R − A, MP L H Statistical model [29] T, D LS-RS-LRS TR R −MP L H Game theory model[24] T, O LS − − − − L M I: Number of success/fail interactions, T: Transmission factors, C: Cryptography factors, D: Application data factors, O: Other factors; TR: Take (functions of) trust values of judges as the coefficients of reputations they sent, PR: Only “good” reputations considered, V: Vote; R: Higher proportion of RT, P: Higher proportion of PT; GT: Group trust value computing; A: Aggregation, MP: Packages specially for trust evaluation (acknowledge packages, beacon, et al .); H: High; M: Middle; L: Low由于LS 是基于节点本身采集的数据计算,所以被认为完全可信.但是对于其他节点发送的信誉值,则需要考虑其可信性.许多系统在RS 时将其他节点于评价节点处的信任值作为其发送的信誉值的系数,节点在评价节点处的信任值越高,其发送的信誉值所占比重越大[9,19].此外,为了避免Bad-Mouthing 攻击,许多系统只计算好的信誉值(只发送好的信誉值或者信誉值高于门限值时才参加计算)[9].但是,这样系统内就无法交流关于恶意节点或自私节点的信息,所以,有的系统接受可信任节点报告的坏信誉值,不过又会存在报复行为的可能性.如果最终采用LRS 合成信任值,并将其作为信誉值传递,则会发生节点A 对某节点进行信任评估时,其LS 结果通过信誉值的传递回到A 并参与RS 及LRS 的计算.为了避免这种循环现象的发生,文献[9]只将LS 的结果作为信誉 传递.(b) 纵向合成信任值的纵向合成是指信任在时间轴方向的计算,将近期信任值(recent trust,简称RT)与历史信任(past trust,简称PT)合并,也称为信任的更新(trust update,简称TU).信任值的横向合成与纵向合成交叉进行,根据具体的信任管理系统需求存在多种组合[16].如可以LS-TU,RS-TU,然后LRS [9];也可以LRS-TU.这里涉及到何时更新的问题,可以事件触发更新,也可以定期更新.用Beta 分布表示信任值,基于贝叶斯公式进行信任值更新是信任管理系统常用的手段[9].信任更新时根据RT 和PT 所占的比重可以分为两种更新方式:① PT 所占比重大,可以防止恶意节点在发现自己信任值过低时,短期内进行特定行为来弥补.② RT 所占比重大,也称为信任老化(aging),迫使节点一直处于正常状态,因为一旦发生恶意行为,就会被严厉惩罚.但是由于信任值随着时间流逝而降低,这对于通信不频繁地区的节点不公平.可以通过系统定期产生通信流量来弥补这一缺陷.1722 Journal of Software软件学报 V ol.19, No.7, July 2008(c) 分级合成在层次式信任管理系统中,有时存在信任的逐级合成,主要包括两类:①在逐级上行过程中,所能获取信息的范围逐渐增加,对节点信任值逐级修正[21].②每级结构有自己的信任值,如GTMS(group based trust management scheme)中节点和簇可以分别有自己的信任值[17],需要在节点、簇和网络分级进行相应的信任值的合成.2.2.3 决策与应用应用决策是体现信任管理系统价值的部分,与信任管理系统的目标紧密相连.虽然各类系统具体目标不同,但是信任管理系统的基本功能就是识别系统中的不可信节点,包括恶意节点、自私节点以及低竞争力节点.但是,这些节点本质上不同,要采用不同的策略.恶意节点一旦确定就要进入黑名单;自私节点要采取激励和惩罚措施,增加其参与的积极性;适当减少低竞争力节点的参与,提高公平性,延长整个网络的生命.信任值决策较多地采用门限值来判定特异节点.对于具体应用,不同系统处理细节上也有很大差异.基于信任管理的安全路由用探测技术定位问题节点[8,18];将低信任、低竞争力节点从转发列表删除;广播黑名单或者修改路由协议绕过恶意节点.基于信任管理的安全信息融合将节点的信任值作为其采集数据的权重进行数据融合[20,21].在基于信任管理的簇头选举中,根据信任值选举出的候选节点还需要通过原簇头的Challenge-Response测试才可以正式当选[11].文献[13]根据文献[30]中的思想将不同安全性需求的数据划分等级,定义相应的信任等级,只有信任等级高于所传送数据对应的信任等级的节点才可以进入该类数据转发列表.在基于信誉的信任管理系统中,通过推荐协议实现信誉值的传送[9].文献[22]利用移动代理管理节点的信任.也有些信任管理系统只定义“单纯”的信任管理,不涉及具体的决策与应用细节[17].3 针对WSNs中信任管理的脆弱性分析、攻击模型及对策既然信任管理主要用于增强网络的安全性、可靠性,针对信任管理系统本身的脆弱性分析和攻击模型就显得尤为重要.WSNs中增加信任管理系统带来的系统安全性、可靠性方面的提高,如果不能抵消其带来的设计复杂性、能耗、脆弱性等方面的代价,则认为信任管理系统无须存在.Dolev-Yao是常用的网络攻击模型,是指在整个网络被控制的情况下,通信可能发生被窃听、丢弃、重放、修改、伪造等攻击行为.但是WSNs环境下针对系统的不同应用环境,攻击模型也有所不同.文献[31]认为,在WSNs环境中,除非攻击者预先获知网络部署地点,并部署好自己的监控设备,否则,在系统初始化阶段相对安全.也有研究者认为,Dolev-Yao模型没有涉及Sybil攻击、共谋等问题,所以不够全面[6].下面根据信任管理系统针对的目标节点的不同类别来进行系统的脆弱性分析,建立攻击模型.3.1 恶意节点恶意节点是指敌方部署的外来节点,或者被敌方俘获的网络中合法节点.恶意节点可能单个行动,也可能集体行动.多个恶意节点还有可能有计划地进行共谋,目前为止,对于共谋没有特别有效的对策.对于恶意节点,一般系统会采取较为严厉的措施,如文献[11]通过challenge-response机制确认某节点是恶意节点之后,将不再允许该节点或其他节点通过任何手段提升其信任值.信任管理系统针对的恶意节点行为主要分为以下3类:(1) 直接恶意行为直接的恶意行为包括丢弃数据包、更改数据内容、更改数据包地址、不按源路由规定而随意转发数据包、频繁发送伪造数据包等.黑洞攻击与灰洞攻击都是丢弃数据包的攻击行为,前者是指恶意节点将所有节点发送过来的数据包丢弃,后者与之不同的是选择性丢弃数据包.这些恶意行为可以用第2.2.1节(1)中所述方法发现.(2) 间接恶意行为间接的恶意行为是指通过降低正常节点信誉值(bad-mouthing),或者提高恶意节点信誉值,达到影响网络正常运行的目的,可以是单独节点的行为,也可以是共谋.对于Bad-Mouthing的对策见第2.2.2节中信任值的横向。
MSA教育资料(BOSCH)
7
Internal | Department | 17/05/2011 | © Robert Bosch GmbH 2011. All rights reserved, also regarding any disposal, exploitation, reproduction, editing, distribution, as well as in the event of applications for industrial property rights.
measurement process 测量过程 fixture 夹具 software 软件
assumption 假设 environment 环境
4
Internal | Department | 17/05/2011 | © Robert Bosch GmbH 2011. All rights reserved, also regarding any disposal, exploitation, reproduction, editing, distribution, as well as in the event of applications for industrial property rights.
Measurement System Analysis (MSA)
1. What is measurement system 测量系统是什么?
2) Some basic concepts: 一些基本概念
Measurement Value = True Value + Measurement Error 测量值 = 真值 + 测量误差
6
Internal | Department | 17/05/2011 | © Robert Bosch GmbH 2011. All rights reserved, also regarding any disposal, exploitation, reproduction, editing, distribution, as well as in the event of applications for industrial property rights.
