(最新整理)aruba配置手册
Aruba3400无线控制器配置手册

Aruba3400无线控制器配置手册1.初始化配置1.1.无线控制器初始化配置Enter System name [Aruba3400]:Enter VLAN 1 interface IP address [172.16.0.254]:Enter VLAN 1 interface subnet mask [255.255.255.0]:Enter IP Default gateway [none]:Enter Switch Role, (master|local) [master]: ————————————控制器角色Enter Country code (ISO-3166), <ctrl-I> for supported list: cn———————控制器所在国家代码,此选项影响You have chosen Country code CN for China (yes|no)?: yes可用RF channel及功率参数Enter Time Zone [PST-8:0]: UTC8:0——————————————-时区系统(UTC、PST等)及所在时区Enter Time in UTC [06:07:59]: 6:11:30——————————————所选时区系统的标准时间而不是本地时间,Enter Date (MM/DD/YYYY) [8/14/2011]: 否则控制器的时钟可能就不对了。
Enter Password for admin login (up to 32 chars): ******Re-type Password for admin login: ******Enter Password for enable mode (up to 15 chars): ******Re-type Password for enable mode: ******Do you wish to shutdown all the ports (yes|no)? [no]:Current choices are:System name:VLAN 1 interface IP address: 172.16.0.254VLAN 1 interface subnet mask: 255.255.255.0IP Default gateway: noneSwitch Role: masterCountry code: cnTime Zone: UTC8:0Ports shutdown: noIf you accept the changes the switch will restart!Type <ctrl-P> to go back and change answer for any questionDo you wish to accept the changes (yes|no)yesCreating configuration... Done.System will now restart!Shutdown processing started1.2.恢复出厂设置-无线控制器注意以下两条command的区别:(Aruba3400) #write eraseAll the configuration will be deleted. Press 'y' to proceed :Write Erase successful(Aruba3400) #(Aruba3400) #write erase allSwitch will be factory defaulted. All the configuration and databases will be deleted. Press 'y' to proceed :(Aruba3400) #(Aruba3400) #(Aruba3400) #reloadDo you really want to reset the system(y/n): ySystem will now restart!write erase只删除配置文件。
Arubavlan基本配置手册

Aruba vlan 基本配置手册本章主要描述有关控制器的基本的网络配置,主要内容如下:一、VLANs 配置二、配置端口三、VLAN 协议四、配置静态路由五、环回IP地址配置六、控制器IP地址配置七、GRE隧道配置第一部分:VLANs配置/虚拟局域网配置2层交换机控制器的操作运用是以VLAN作为广播域,作为2层交换机,控制器要求需要外界的路径来实现与VLANs的路径连通。
该控制器还可以作为第三层交换机,可以定义VLAN 之间的交通路线的控制器。
你可以在控制器上配置一个/多个物理端口实现一个虚拟局域网。
另外,每个无线客户端口关联是连接到一个特定的虚拟局域网的端口控制器上。
你可以根据你的网络需要替换所有经认证授权的无线用户到单个VLAN或者替换到不同的VLANs。
VLANs可以单独存在在控制器里面或者可以通过802.1q VLAN标签存在在控制器外部。
你可以选择在控制器上为VLAN配置一个IP地址和子网掩码,当VLAN上最近的物理端口被激活的同时,该IP地址也被激活。
该VLAN IP地址可以作为外部设备的一个接入点,指向虚拟局域网IP地址的数据包不是为控制器指定的而是根据控制器的IP路由表来转发的。
创建和更新VLANs:创建和更新单个/多个VLANs1. 通过WEBUI 来创建或者修改单个VLAN1)打开2)点击“ADD新建”按钮创建一个新的VLAN。
(若需要修改,点击Edit按钮)具体参照58页创建一系列的VLANs。
3)为VLAN增加一个物理端口,点击选项4)点击2. 通过CLI(命令)创建或者修改VLAN3.通过WEBUI 来创建或者修改多个VLAN1)一次性增加并联的VLANs,点击2)在弹出的窗口,输入你想要创建的VLANs 序列。
例如,增加一个ID号码为200-300和302-350的VLAN,输入200-300,302-350。
3)点击“OK”4)为VLAN增加物理端点,点击“EDIT”进入你想要配置的VLAN页面,点击“PortSelection”选项设置端口。
Aruba WLAN简明配置手册-v1

Aruba WLAN简明配置手册目录1. 2. 3. 4. 录 ...................初始化配置1.1. 无线1.2. 恢复1.3. 恢复基本网络参2.1. 基本2.2. 控制2.3. 管理理解Aruba 3.1. 基本3.2. 基于配置范例 ...4.1. 建立4.2. 建立4.3. 建立4.4. 同一4.5. 设置4.6. 设定4.7. 配置4.8. 带宽.....................置 ...................线控制器初始复出厂设置-复出厂设置-参数配置及维本网络参数配制器基本维护理员帐号管理WLAN 配置结本WLAN 服务于角色的用户.....................立WPA2‐PSK 服立Portal 认证 立802.1X 认证一SSID 中为不置用户期限 ...定区域管理 ...置日志服务器宽限制 .....................................................化配置 ........无线控制器 Aruba AP .....护 .................置 ................操作 ............ ....................结构框架 ........务配置 ............策略管理 .........................服务...................................证 ...................不同用户配置.......................................... ........................................................................................................................................................................................................................................................................................................................................................................................置不同的权限....................................................................................目录................................................................................................................................................................................................................................................................................................................................限 ........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................ 2 (3)...... 3 ...... 4 ...... 4 (6)...... 6 ...... 7 ...... 9 . (11).... 11 .... 12 . (14).... 14 .... 19 .... 28 .... 38 .... 39 .... 43 .... 49 . (49)1. Ente Ente Ente Ente Ente Ente 项影You Ente Ente 间,Ente Ente Re-t Ente Re-t Do y Curr Syst VLAN VLAN IP D Swit Coun Time Port If y Type Do y Crea Syst初始1.1. 无线er System n er VLAN 1 i er VLAN 1 i er IP Defau er Switch R er Country 影响have chose er Time Zon er Time in er Date (MM er Password type Passwo er Password type Passwo you wish to rent choice tem name: N 1 interfa N 1 interfa Default gat tch Role: m ntry code: e Zone: UTC ts shutdown you accept e <ctrl-P> you wish to ating confi tem will no 化配置线控制器初name [Aruba interface I interface s ult gateway Role, (mast code (ISO-en Country ne [PST-8:0UTC [06:07M/DD/YYYY) d for admin ord for adm d for enabl ord for ena o shutdown es are: ace IP addr ace subnet teway: none master cn C8:0 n: no the change to go back o accept th iguration..ow restart!置初始化配置a3400]: P address ubnet mask y [none]: er|local) 3166), <ctr code CN for 0]: UTC8:0—7:59]: 6:11[8/14/2011n login (up min login: *e mode (up able mode: *all the por ress: 172.16mask: 255.2e es the swit k and chang he changes . Done. 置[172.16.0.2[255.255.2[master]: —rl-I> for s r China (ye ——————:30————]: to 32 char ****** to 15 char ****** rts (yes|no 6.0.254 255.255.0ch will res e answer fo (yes|no)yes 254]: 255.0]: ——————supported l es|no)?: ye ———————————— rs): ******rs): ******o)? [no]: start! or any ques s ——————ist: cn ——es ————-时—————— 否则* * stion ——控制器角—————— 可用时区系统(UT —所选时区系则控制器的时角色 —控制器所在用RF channe C、PST 等)系统的标准时时钟可能就不在国家代码,el 及功率参数及所在时区时间而不是本不对了。
aruba配置手册

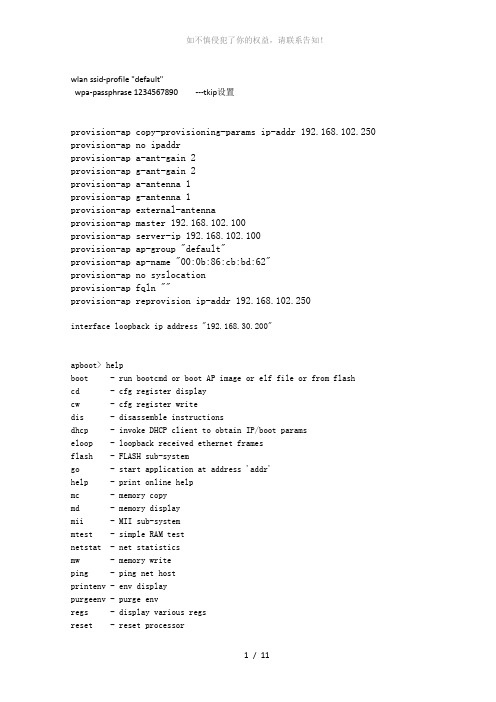
wlan ssid-profile "default"wpa-passphrase 1234567890 ---tkip设置provision-ap copy-provisioning-params ip-addr 192.168.102.250 provision-ap no ipaddrprovision-ap a-ant-gain 2provision-ap g-ant-gain 2provision-ap a-antenna 1provision-ap g-antenna 1provision-ap external-antennaprovision-ap master 192.168.102.100provision-ap server-ip 192.168.102.100provision-ap ap-group "default"provision-ap ap-name "00:0b:86:cb:bd:62"provision-ap no syslocationprovision-ap fqln ""provision-ap reprovision ip-addr 192.168.102.250interface loopback ip address "192.168.30.200"apboot> helpboot - run bootcmd or boot AP image or elf file or from flashcd - cfg register displaycw - cfg register writedis - disassemble instructionsdhcp - invoke DHCP client to obtain IP/boot paramseloop - loopback received ethernet framesflash - FLASH sub-systemgo - start application at address 'addr'help - print online helpmc - memory copymd - memory displaymii - MII sub-systemmtest - simple RAM testnetstat - net statisticsmw - memory writeping - ping net hostprintenv - env displaypurgeenv - purge envregs - display various regsreset - reset processorrun - run commands in an environment variablesaveenv - save environment variables to persistent storagesetenv - set variable in env (ipaddr/netmask/gatewayip/master/serverip) setenv ipaddr x.x.x.xsetenv netmask x.x.x.xsetenv gatewayip x.x.x.xsetenv serverip x.x.x.xsetenv master x.x.x.xtcpdump - dump received packetstcpsend - send TCP packettftpboot - boot via tftptlb - dump TLBtrace - dump trace bufferversion - print monitor versionwdog - stop refreshing watchdog timerapboot>No spanning-tree 关闭spanning-treeAdp discover disable 关闭ADPAdp imgp-join disable 关闭im-j一、WEB页面认证1、wlan ssid-profile (staff-ssid-profile) :定义ssid配置文件1.1 essid staff :定义ssid下的essid—显示出来的ssid2、wlan virtual-ap (staff-vap-profile) :定义virtual-ap的配置文件2.1 ssid-profile (staff-ssid-profile) :在virtual-ap下引用定义过SSID2.2 vlan ID aa,bb :把virtual-ap加入到要ssid所属VLAN3、aaa profile staff-aaa-profile :定义AAA认证配置文件4、aaa server-group (staff-servergroup) :定义server-group配置文件4.1 auth-server internal :定义认证服务器为本地认证4.2 set role condition role value-of 设置角色set role condition <condition> set-value <role> position <number>5、aaa authentication captive-portal (staff-auth-profile) :captive-portal配置5.1 server-group staff-servergroup :在下面引用定义过的server-group6、user-role staff-logon :定义用户登陆前权限的配文件6.1 access-list session logon-control position 1定义用户登陆前的权限--位置16.2 access-list session captiveportal position 2 定义用户登陆前的权限--26.3 Captive-Portal staff-auth-profile position 3定义过captive-portalRe-authentication interval 480 再次认证间隔480秒默认3600秒7、user-role vip-role :定义用户成功登陆后的配置文件7.1session-acl allowall 赋予所有允许权限session-acl http-acl 只有http8、wlan virtual-ap staff-vap-profile :进入定义过的virtual-ap配置文件8.1 aaa-profile staff-aaa-profile :引用定义过的AAA配置文件9、ap-group default :定义ap-group,最好用默认的9.1 virtual-ap staff-vap-profile :引用定义过的Virtual-ap配置文件10、aaa profile staff-aaa-profile :进入定义过的AAA配置文件10.1 initial-role staff-logon :把initial-role改为定义过用户登陆前配置11、aaa authentication-server internal use-local-switch :定义认证SERVER为本地交换机12、local-userdb add username staff password 123456 role vip-role :定义用户的登陆的用户名和密码及权限二、MAC 地址认证配置1、wlan ssid-profile (staff-ssid-profile) :定义ssid配置文件1.1 essid staff :定义ssid下的essid2、wlan virtual-ap (staff-vap-profile) :定义virtual-ap的配置文件2.1 ssid-profile (staff-ssid-profile) :virtual-ap下引用定义过的SSID配置文件2.2 vlan ID :把virtual-ap加入到要ssid所属的VLAN3、aaa profile staff-aaa-mac-profile :定义AAA认证配置文件4、aaa authentication mac staff-mac-profile :定义mac配置文件4.1 Delimiter dash :定义mac地址的格式4.2 Case upper (upper/lower):定义mac地址的大/小写备注:aaa authentication mac staff-mac-profileclone <profile>delimiter {colon|dash|none}max-authentication-failures 数字aaa authentication mac mac-blacklist MAC黑名单max-authentication-failures 5 最多认证失败次数5、aaa server-group (staff-macservergroup) :定义server-group配置文件5.1 auth-server internal :定义认证服务器为本地认证5.2 set role condition role value-of6、user-role staff-logon :定义用户登陆前权限的配文件6.1 access-list session logon-control :定义用户登陆前的权限6.2 access-list session captiveportal :定义用户登陆前的权限7、user-role vip-role :定义用户成功登陆后的配置文件7.1session-acl allowall :赋予权限8、wlan virtual-ap staff-vap-profile :进入定义过的virtual-ap配置文件8.1 aaa-profile staff-aaa-mac-profile :引用定义过的AAA配置文件9、ap-group default :定义ap-group,最好用默认的9.1 virtual-ap staff-vap-profile :引用定义过的Virtual-ap配置文件10、aaa profile staff-aaa-mac-profile :进入定义过的AAA配置文件10.1 initial-role staff-logon :把initial-role改为定义过的用户登陆前的配置文件10.2 authentication-mac staff-mac-profile :把定义的authentication mac文件引用10.3 mac-server-group staff-macservergroup :把定义的servergroup加入11、aaa authentication-server internal use-local-switch :定义认证SERVER为本地交换机12、local-userdb add username mac地址password mac地址 role vip-role :定义用户的登陆的用户名和密码及权限注意:如果是有线直接连在端口上的话要进行认证必须把连接口设为UNTRUSTED.同时在设定:进入aaa authentication wired 后设定:profile (staff-aaa-profile) 为你设定认证的AAA profileBlacklist:5次错误就拒绝访问show aaa authentication captive-portal default:Max authentication failures 改为5次show aaa authentication dot1x default:Max authentication failures 改为5次1、aaa bandwidth-contract "256" kbits "256"2、aaa bandwidth-contract "256" kbits 256ip access-list session "pass"any any any permit queue low!user-role "ap512"access-list "pass" position 1bw-contract "256" per-user upstreambw-contract "256" per-user downstreamaaa bandwidth-contract "2M-BW" mbits "2" 带宽2M控制aaa bandwidth-contract 128_up kbits 128 带宽128k控制aaa bandwidth-contract 512 kbits 512aaa bandwidth-contract 64 kbits 64aaa bandwidth-contract 256 kbits 256aaa bandwidth-contract 1 mbits 1 带宽1M控制aaa bandwidth-contract 128_up kbits 128user-role 128bw-contract 128_up per-user upstreamuser-role ap-rolesession-acl controlsession-acl ap-acl!user-role pre-employeesession-acl allowallMaster mobility controller configuration1Initial setup of Aruba-master2Core VLAN configuration and IP addressing3Core VLAN port assignment4Loopback IP address ----- interface loopback ip address 设置环回地址Deploy APs5配置AP VLAN6配置 AP VLAN DHCP Server7Connect Aruba APs8Provisioning Aruba APs(Aruba-master) (config-if)#write mSaving Configuration...ip dhcp pool "userpool" 定义pool的名字default-router 192.168.11.254 定义默认路由网关—loopback地址dns-server 192.168.11.254---202.106.0.20 定义DNS网关lease 8 0 0network 192.168.11.0 255.255.255.0service dhcp 启动dhcpinterface gigabitethernet 1/1no muxportswitchport mode trunkip default-gateway 192.168.0.254interface vlan 1no ip addressno ip igmpinterface gigabitethernet 1/1no switchport access vlaninterface loopback ip address "192.168.0.100"(Aruba800-4) (config) # show ip interface briefInterface IP Address / IP Netmask Admin Protocolvlan 1 172.16.0.254 / 255.255.255.0 up upvlan 10 192.168.0.1 / 255.255.255.0 up upvlan 30 192.168.30.200 / 255.255.255.0 up uploopback unassigned / unassigned up up(Aruba800-4) (config) # rf arm-profile default ----------关闭ARM后调整channel---ok (Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #assignment disable (Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #no scan(Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #write memoryrf dot11g-radio-profile "default"tx-power 20 ------------------------发射功率调整rf dot11g-radio-profile "default"channel 11 ------------------------调整AP信道interface vlan 20ip address 192.168.0.1 255.255.255.0ip nat insideno ip igmp存配置:24 (Aruba2400) #configure t25(Aruba2400) (config) #copy tftp: 172.16.0.100 aruba2400-0904.cfg flash: 2400.bak 26(Aruba2400) (config) #copy flash: 2400.bak flash: 2400.cfg27(Aruba2400) # copy running-config tftp: 192.168.4.100 aruba2400-0904.cfgRadius配置:aaa authentication-server radius Radius1host <ipaddr>key <key>enableaaa server-group corpnetauth-server Radius1dot1x配置:aaa authentication dot1x corpnetaaa profile corpnetauthentication-dot1x corpnetdot1x-default-role employeedot1x-server-group corpnetvirtual AP:wlan ssid-profile corpnetessid Corpnetopmode wpa2-aeswlan virtual-ap corpnetvlan 1aaa-profile corpnetssid-profile corpnetap-group defaultvirtual-ap corpnet时间设定:time-range workhours periodic周期weekday 09:00 to 17:00ip access-list session restricted 受限制any any svc-http permit time-range workhoursany any svc-https permit time-range workhoursuser-role guestsession-acl restrictedmesh设置:ap mesh-radio-profile <profile-name>11a-portal-channel <11a-portal-channel>11g-portal-channel <11g-portal-channel>a-tx-rates [6|9|12|18|24|36|48|54]beacon-period <beacon-period>children <children>clone <source-profile-name>g-tx-rates [1|2|5|6|9|11|12|18|24|36|48|54]heartbeat-threshold <count>hop-count <hop-count>link-threshold <count>max-retries <max-retries>metric-algorithm {best-link-rssi|distributed-tree-rssimpv <vlan-id>rts-threshold <rts-threshold>tx-power <tx-power>ap mesh-radio-profile <profile-name>clone <source-profile-name>ap-group <group>mesh-radio-profile <profile-name>ap-name <name>mesh-radio-profile <profile-name>wlan ssid-profile <profile>essid <name>opmode <method> 方式wpa-passphrase <string> (if necessary)wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>virtual-ap <name># ip access-list session "Employee-Policy"any any any permit queue lowRemote AP配置The firewall must be configured to pass NAT-T traffic (UDP port 4500) to the controller.)1、Configure a public IP address for the controller.2、Configure the VPN server on the controller. The remote AP will be a VPN client to the server.3、Configure the remote AP role.4、Configure the authentication server that will validate the username and password for the remote AP.5、Provision the AP with IPSec settings, including the username and passwordfor the AP, before you install it at the remote location.1、Cli:vlan <id>interface fastethernet <slot>/<port>switchport access vlan <id>interface vlan <id>ip address <ipaddr> <mask>2、Using the CLI to configure VPN server:vpdn group l2tpppp authentication PAPip local pool <pool> <start-ipaddr> <end-ipaddr>crypto isakmp key <key> address <ipaddr> netmask <mask>3、Using the CLI to configure the user role:(table1) (config) # user-role remote(table1) (config-role) #session-acl allowallip access-list session <policy>any any svc-papi permitany any svc-gre permitany any svc-l2tp permitany alias mswitch svc-tftp permitany alias mswitch svc-ftp permit4、Using the CLI to configure the VPN authentication profile:4.1 aaa server-group <group>auth-server <server>4.2 aaa authentication vp ndefault-role <role>server-group <group>5、Using the CLI to enable double encryption:ap system-profile <profile>double-encryptap-name <name> 需要插上远端AP后配置ap-system-profile <profile>Using the CLI to enable double encryption:ap system-profile <profile>double-encryptap-name <name>ap-system-profile <profile>Using the CLI to configure the AAA profile:aaa profile <name>initial-role <role>authentication-dot1x <dot1x-profile>dot1x-default-role <role>dot1x-server-group <group>Using the CLI to define the backup configuration in the virtual AP profile: wlan ssid-profile <profile>essid <name>opmode <method>wpa-passphrase <string> (if necessary)wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>virtual-ap <name>orap-name <name>virtual-ap <name>Using the CLI to configure the DHCP server on the AP:ap system-profile <name>lms-ip <ipaddr>master-ip <ipaddr>rap-dhcp-server-vlan <vlan>wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>ap-system-profile <name>virtual-ap <name>orap-name <name>ap-system-profile <name> virtual-ap <name>。
Aruba快速配置手册

Aruba快速配置手册测试环境:连接在同一台交换机上面AP93 ip:172.16.20.254/244Aruba-650 VLAN 1:192.168.16.0/24AP VLAN 20:172.16.20.0/24User VLAN 30:172.16.30.1/241、Aruba-650初始化配置基本配置成功之后,会提示你自动重启2、通过web界面登录,浏览器输入https://192.168.16.1633、配置Aruba-650 上联端口的接入模式为trunk,允许所有vlan 通过(Aruba650) (config) #interface gigabitethernet 1/0(Aruba650) (config-if)#switchport mode trunk(Aruba650) (config-if)#switchport trunk allowed vlan all4、Aruba650配置DHCP,其中VLAN 20:172.16.20.0/24、AC的VLAN1:192.168.16.0/24、USER的VLAN 30:172.16.30.0/24;配置三个DHCP (Aruba650) (config) #vlan 20(Aruba650) (config) #interface vlan 20(Aruba650) (config-subif)#ip address 172.16.20.1 255.255.255.0(Aruba650) (config-subif)#operstate up(Aruba650) (config-subif)#no shut(Aruba650) (config-subif)#exit(Aruba650) (config) #ip dhcp pool ap(Aruba650) (config-dhcp)#network 172.16.20.0 255.255.255.0(Aruba650) (config-dhcp)#default-router 172.16.20.1(Aruba650) (config-dhcp)#dns-server 61.177.7.1(Aruba650) (config-dhcp)#exit(Aruba650) (config) #service dhcp(Aruba650) (config) #vlan 30(Aruba650) (config) #interface vlan 30(Aruba650) (config-subif)#ip address 172.16.30.1 255.255.255.0 (Aruba650) (config-subif)#operstate up(Aruba650) (config-subif)#no shut(Aruba650) (config-subif)#exit(Aruba650) (config) #ip dhcp pool user_client(Aruba650) (config-dhcp)#network 172.16.30.0 255.255.255.0 (Aruba650) (config-dhcp)#default-router 172.16.30.1(Aruba650) (config-dhcp)#dns-server 61.177.7.1查看已配置的DHCP,show ip dhcp database(Aruba650) (config) #show ip dhcp databaseDHCP enabled# apsubnet 172.16.20.0 netmask 255.255.255.0 {option vendor-class-identifier "ArubaAP";option vendor-encapsulated-options "192.168.16.163";option domain-name-servers 61.177.7.1;option routers 172.16.20.1;range 172.16.20.2 172.16.20.254;authoritative;}# user_clientsubnet 172.16.30.0 netmask 255.255.255.0 {option vendor-class-identifier "ArubaAP";option vendor-encapsulated-options "192.168.16.163";option domain-name-servers 61.177.7.1;option routers 172.16.30.1;range 172.16.30.2 172.16.30.254;authoritative;}5、开启Aruba650的telnet端口,telnet cli6、新增的SSID的模式为open定义aaa profile(Aruba650)(config)#aaa profile open-aaa(Aruba650) (AAA Profile "open-aaa") #Initial-role authenticated //默认为logon 打开IE 会有问题(Aruba650) (AAA Profile "open-aaa") #exit定义ssid profile(Aruba650) (config)# wlan ssid profile open-ssid(Aruba650) (SSID Profile "open-ssid") #essid Aruba-AP //定义ssid名字(Aruba650) (SSID Profile "open-ssid") #opmod opensystem //定义加密方式(Aruba650) (SSID Profile "open-ssid") #exit定义virtual-ap profile(Aruba650) (config) #wlan virtual-ap open-vap(Aruba650) (Virtual AP profile "open-vap") #aaa prolife open-aaa //关联aaa profile(Aruba650) (Virtual AP profile "open-vap") #ssid profile open-ssid //关联ssid profile(Aruba650) (Virtual AP profile "open-vap") #vlan 30 //关联用户vlan创建的open-aaaAAA相关联定义ap-group profile(Aruba650) (config) #ap-group open-ap(Aruba650) (AP group "open-ap") #virtual-ap open-vap //关联virtual-ap profileap加组到定义好的ap-group(Aruba650) (config)#ap-regroup [ap-name | serial-num | wired-mac]open-ap创建的AP组最后需要做NAT,才能让VLAN 30的客户能够出去上网,输入一下命令就可以上网了、(Aruba650) (config) #interface vlan 30(Aruba650) (config-subif)#ip nat inside7、查看吐出的SSID:Aruba-AP8、连接Aruba-AP,查看获取的IP地址,可以上网输入以上为Aruba650测试文档。
aruba配置手册(参考模板)
wlan ssid-profile "default"wpa-passphrase 1234567890 ---tkip设置provision-ap copy-provisioning-params ip-addr 192.168.102.250 provision-ap no ipaddrprovision-ap a-ant-gain 2provision-ap g-ant-gain 2provision-ap a-antenna 1provision-ap g-antenna 1provision-ap external-antennaprovision-ap master 192.168.102.100provision-ap server-ip 192.168.102.100provision-ap ap-group "default"provision-ap ap-name "00:0b:86:cb:bd:62"provision-ap no syslocationprovision-ap fqln ""provision-ap reprovision ip-addr 192.168.102.250interface loopback ip address "192.168.30.200"apboot> helpboot - run bootcmd or boot AP image or elf file or from flashcd - cfg register displaycw - cfg register writedis - disassemble instructionsdhcp - invoke DHCP client to obtain IP/boot paramseloop - loopback received ethernet framesflash - FLASH sub-systemgo - start application at address 'addr'help - print online helpmc - memory copymd - memory displaymii - MII sub-systemmtest - simple RAM testnetstat - net statisticsmw - memory writeping - ping net hostprintenv - env displaypurgeenv - purge envregs - display various regsreset - reset processorrun - run commands in an environment variablesaveenv - save environment variables to persistent storagesetenv - set variable in env (ipaddr/netmask/gatewayip/master/serverip) setenv ipaddr x.x.x.xsetenv netmask x.x.x.xsetenv gatewayip x.x.x.xsetenv serverip x.x.x.xsetenv master x.x.x.xtcpdump - dump received packetstcpsend - send TCP packettftpboot - boot via tftptlb - dump TLBtrace - dump trace bufferversion - print monitor versionwdog - stop refreshing watchdog timerapboot>No spanning-tree 关闭spanning-treeAdp discover disable 关闭ADPAdp imgp-join disable 关闭im-j一、WEB页面认证1、wlan ssid-profile (staff-ssid-profile) :定义ssid配置文件1.1 essid staff :定义ssid下的essid—显示出来的ssid2、wlan virtual-ap (staff-vap-profile) :定义virtual-ap的配置文件2.1 ssid-profile (staff-ssid-profile) :在virtual-ap下引用定义过SSID2.2 vlan ID aa,bb :把virtual-ap加入到要ssid所属VLAN3、aaa profile staff-aaa-profile :定义AAA认证配置文件4、aaa server-group (staff-servergroup) :定义server-group配置文件4.1 auth-server internal :定义认证服务器为本地认证4.2 set role condition role value-of 设置角色set role condition <condition> set-value <role> position <number>5、aaa authentication captive-portal (staff-auth-profile) :captive-portal配置5.1 server-group staff-servergroup :在下面引用定义过的server-group6、user-role staff-logon :定义用户登陆前权限的配文件6.1 access-list session logon-control position 1定义用户登陆前的权限--位置16.2 access-list session captiveportal position 2 定义用户登陆前的权限--26.3 Captive-Portal staff-auth-profile position 3定义过captive-portalRe-authentication interval 480 再次认证间隔480秒默认3600秒7、user-role vip-role :定义用户成功登陆后的配置文件7.1session-acl allowall 赋予所有允许权限session-acl http-acl 只有http8、wlan virtual-ap staff-vap-profile :进入定义过的virtual-ap配置文件8.1 aaa-profile staff-aaa-profile :引用定义过的AAA配置文件9、ap-group default :定义ap-group,最好用默认的9.1 virtual-ap staff-vap-profile :引用定义过的Virtual-ap配置文件10、aaa profile staff-aaa-profile :进入定义过的AAA配置文件10.1 initial-role staff-logon :把initial-role改为定义过用户登陆前配置11、aaa authentication-server internal use-local-switch :定义认证SERVER为本地交换机12、local-userdb add username staff password 123456 role vip-role :定义用户的登陆的用户名和密码及权限二、MAC 地址认证配置1、wlan ssid-profile (staff-ssid-profile) :定义ssid配置文件1.1 essid staff :定义ssid下的essid2、wlan virtual-ap (staff-vap-profile) :定义virtual-ap的配置文件2.1 ssid-profile (staff-ssid-profile) :virtual-ap下引用定义过的SSID配置文件2.2 vlan ID :把virtual-ap加入到要ssid所属的VLAN3、aaa profile staff-aaa-mac-profile :定义AAA认证配置文件4、aaa authentication mac staff-mac-profile :定义mac配置文件4.1 Delimiter dash :定义mac地址的格式4.2 Case upper (upper/lower):定义mac地址的大/小写备注:aaa authentication mac staff-mac-profileclone <profile>delimiter {colon|dash|none}max-authentication-failures 数字aaa authentication mac mac-blacklist MAC黑名单max-authentication-failures 5 最多认证失败次数5、aaa server-group (staff-macservergroup) :定义server-group配置文件5.1 auth-server internal :定义认证服务器为本地认证5.2 set role condition role value-of6、user-role staff-logon :定义用户登陆前权限的配文件6.1 access-list session logon-control :定义用户登陆前的权限6.2 access-list session captiveportal :定义用户登陆前的权限7、user-role vip-role :定义用户成功登陆后的配置文件7.1session-acl allowall :赋予权限8、wlan virtual-ap staff-vap-profile :进入定义过的virtual-ap配置文件8.1 aaa-profile staff-aaa-mac-profile :引用定义过的AAA配置文件9、ap-group default :定义ap-group,最好用默认的9.1 virtual-ap staff-vap-profile :引用定义过的Virtual-ap配置文件10、aaa profile staff-aaa-mac-profile :进入定义过的AAA配置文件10.1 initial-role staff-logon :把initial-role改为定义过的用户登陆前的配置文件10.2 authentication-mac staff-mac-profile :把定义的authentication mac文件引用10.3 mac-server-group staff-macservergroup :把定义的servergroup加入11、aaa authentication-server internal use-local-switch :定义认证SERVER为本地交换机12、local-userdb add username mac地址password mac地址 role vip-role :定义用户的登陆的用户名和密码及权限注意:如果是有线直接连在端口上的话要进行认证必须把连接口设为UNTRUSTED.同时在设定:进入aaa authentication wired 后设定:profile (staff-aaa-profile) 为你设定认证的AAA profileBlacklist:5次错误就拒绝访问show aaa authentication captive-portal default:Max authentication failures 改为5次show aaa authentication dot1x default:Max authentication failures 改为5次1、aaa bandwidth-contract "256" kbits "256"2、aaa bandwidth-contract "256" kbits 256ip access-list session "pass"any any any permit queue low!user-role "ap512"access-list "pass" position 1bw-contract "256" per-user upstreambw-contract "256" per-user downstreamaaa bandwidth-contract "2M-BW" mbits "2" 带宽2M控制aaa bandwidth-contract 128_up kbits 128 带宽128k控制aaa bandwidth-contract 512 kbits 512aaa bandwidth-contract 64 kbits 64aaa bandwidth-contract 256 kbits 256aaa bandwidth-contract 1 mbits 1 带宽1M控制aaa bandwidth-contract 128_up kbits 128user-role 128bw-contract 128_up per-user upstreamuser-role ap-rolesession-acl controlsession-acl ap-acl!user-role pre-employeesession-acl allowallMaster mobility controller configuration1Initial setup of Aruba-master2Core VLAN configuration and IP addressing3Core VLAN port assignment4Loopback IP address ----- interface loopback ip address 设置环回地址Deploy APs5配置AP VLAN6配置 AP VLAN DHCP Server7Connect Aruba APs8Provisioning Aruba APs1 Default5 VLAN0004 Fa2/0-23 Gig2/24 Gig2/25(Aruba-master) (config-if)#write mSaving Configuration...ip dhcp pool "userpool" 定义pool的名字default-router 192.168.11.254 定义默认路由网关—loopback地址dns-server 192.168.11.254---202.106.0.20 定义DNS网关lease 8 0 0network 192.168.11.0 255.255.255.0service dhcp 启动dhcpinterface gigabitethernet 1/1no muxportswitchport mode trunkip default-gateway 192.168.0.254interface vlan 1no ip addressno ip igmpinterface gigabitethernet 1/1no switchport access vlaninterface loopback ip address "192.168.0.100"(Aruba800-4) (config) # show ip interface briefInterface IP Address / IP Netmask Admin Protocolvlan 1 172.16.0.254 / 255.255.255.0 up upvlan 10 192.168.0.1 / 255.255.255.0 up upvlan 30 192.168.30.200 / 255.255.255.0 up uploopback unassigned / unassigned up up(Aruba800-4) (config) # rf arm-profile default ----------关闭ARM后调整channel---ok (Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #assignment disable (Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #no scan(Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #write memoryrf dot11g-radio-profile "default"tx-power 20 ------------------------发射功率调整rf dot11g-radio-profile "default"channel 11 ------------------------调整AP信道interface vlan 20ip address 192.168.0.1 255.255.255.0ip nat insideno ip igmp存配置:24 (Aruba2400) #configure t25(Aruba2400) (config) #copy tftp: 172.16.0.100 aruba2400-0904.cfg flash: 2400.bak 26(Aruba2400) (config) #copy flash: 2400.bak flash: 2400.cfg27(Aruba2400) # copy running-config tftp: 192.168.4.100 aruba2400-0904.cfgRadius配置:aaa authentication-server radius Radius1host <ipaddr>key <key>enableaaa server-group corpnetauth-server Radius1dot1x配置:aaa authentication dot1x corpnetaaa profile corpnetauthentication-dot1x corpnetdot1x-default-role employeedot1x-server-group corpnetvirtual AP:wlan ssid-profile corpnetessid Corpnetopmode wpa2-aeswlan virtual-ap corpnetvlan 1aaa-profile corpnetssid-profile corpnetap-group defaultvirtual-ap corpnet时间设定:time-range workhours periodic周期weekday 09:00 to 17:00ip access-list session restricted 受限制any any svc-http permit time-range workhoursany any svc-https permit time-range workhoursuser-role guestsession-acl restrictedmesh设置:ap mesh-radio-profile <profile-name>11a-portal-channel <11a-portal-channel>11g-portal-channel <11g-portal-channel>a-tx-rates [6|9|12|18|24|36|48|54]beacon-period <beacon-period>children <children>clone <source-profile-name>g-tx-rates [1|2|5|6|9|11|12|18|24|36|48|54]heartbeat-threshold <count>hop-count <hop-count>link-threshold <count>max-retries <max-retries>metric-algorithm {best-link-rssi|distributed-tree-rssi mpv <vlan-id>rts-threshold <rts-threshold>tx-power <tx-power>ap mesh-radio-profile <profile-name>clone <source-profile-name>ap-group <group>mesh-radio-profile <profile-name>ap-name <name>mesh-radio-profile <profile-name>wlan ssid-profile <profile>essid <name>opmode <method> 方式wpa-passphrase <string> (if necessary)wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>virtual-ap <name># ip access-list session "Employee-Policy"any any any permit queue lowRemote AP配置The firewall must be configured to pass NAT-T traffic (UDP port 4500) to the controller.)1、Configure a public IP address for the controller.2、Configure the VPN server on the controller. The remote AP will be a VPN client to the server.3、Configure the remote AP role.4、Configure the authentication server that will validate the username and password for the remote AP.5、Provision the AP with IPSec settings, including the username and passwordfor the AP, before you install it at the remote location.1、Cli:vlan <id>interface fastethernet <slot>/<port>switchport access vlan <id>interface vlan <id>ip address <ipaddr> <mask>2、Using the CLI to configure VPN server:vpdn group l2tpppp authentication PAPip local pool <pool> <start-ipaddr> <end-ipaddr>crypto isakmp key <key> address <ipaddr> netmask <mask>3、Using the CLI to configure the user role:(table1) (config) # user-role remote(table1) (config-role) #session-acl allowallip access-list session <policy>any any svc-papi permitany any svc-gre permitany any svc-l2tp permitany alias mswitch svc-tftp permitany alias mswitch svc-ftp permit4、Using the CLI to configure the VPN authentication profile:4.1 aaa server-group <group>auth-server <server>4.2 aaa authentication vp ndefault-role <role>server-group <group>5、Using the CLI to enable double encryption:ap system-profile <profile>double-encryptap-name <name> 需要插上远端AP后配置ap-system-profile <profile>Using the CLI to enable double encryption:ap system-profile <profile>double-encryptap-name <name>ap-system-profile <profile>Using the CLI to configure the AAA profile:aaa profile <name>initial-role <role>authentication-dot1x <dot1x-profile>dot1x-default-role <role>dot1x-server-group <group>Using the CLI to define the backup configuration in the virtual AP profile: wlan ssid-profile <profile>essid <name>opmode <method>wpa-passphrase <string> (if necessary)wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>virtual-ap <name>orap-name <name>virtual-ap <name>Using the CLI to configure the DHCP server on the AP:ap system-profile <name>lms-ip <ipaddr>master-ip <ipaddr>rap-dhcp-server-vlan <vlan>wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>ap-system-profile <name>virtual-ap <name>or如不慎侵犯了你的权益,请联系告知!ap-name <name>ap-system-profile <name>virtual-ap <name>(本资料素材和资料部分来自网络,仅供参考。
Aruba 无线控制器配置手册

上海市徐汇区漕宝路 400 号明申商务广场 608 室
路雨信息为您提供最佳的无线体验
十、 修改 AP 名称和所在组
在新跳出来的页面里在 AP Group 的下拉选项里选择合适的已经建立好的 AP Group, 把页面拉到最下端后修改 AP 的名称。具体操作如下图:
上海市徐汇区漕宝路 400 号明申商务广场 608 室
配置好以上的设置后,我们就可以使用配置好的 IP 地址,在 PC 端通过 HTTPS 连接到 控制器上进行配置。
三、 配置新的 Policy
配置接入客户端在接入到无线网络后的规则。使用页面的方式找到 configuration SECURITY Access Control Policies 在 policy 下可以配置接入客户端的 rules。这些 rule 可以根据源和目标的来进行,同时还可以配置相应的协议 rule。示例如下:
七、 配置 SSID 和加密方式
SSID 里可以配置连接加密方式和修改 SSID 名称。 具体的配置路径如下: Configuration WIRELESS AP Configuration SSID 修改示例如下图:
上海市徐汇区漕宝路 400 号明申商务广场 608 室
路雨信息为您提供最佳的无线体验
上海市徐汇区漕宝路 400 号明申商务广场 608 室
路雨信息为您提供最佳的无线体验
Do you wish to shutdown all the ports (yes|no)? [no]: Current choices are: System name: Aruba200 VLAN 1 interface IP address: 192.168.0.123 VLAN 1 interface subnet mask: 255.255.255.0 IP Default gateway: none Switch Role: master Country code: cn Time Zone: PST-8:0 Ports shutdown: no If you accept the changes the switch will restart! Type <ctrl-P> to go back and change answer for any question Do you wish to accept the changes (yes|no)y System restarted!
Aruba 无线AP及AC配置精编版

Aruba 无线AP及AC配置Aruba在无线配置方面的主要特点:使用以profile为单元的方式分解无线配置参数,根据无线配置参数的功能,分解成一个个独立的profiles,下层Profile可以提供给多个上层profile进行使用,上层profile也可以包含多个不同功能的下层profile。
以这样的方式达到参数重用的最大化,减少参数保存冗余。
例如SSID Profile(包含AP的名称,加密方式等等)包含EDCA Parameters Station Profile(Clients到AP的流量优先级参数),EDCA Paramters AP Profile(AP到Clients的流量优先级参数),High-throughput SSID Profile(802.11n的40MH的利用),这三个Profile还可以被其他的SSID Profile包含。
一、AP组Aruba以AP组的方式保存具有相同配置AP的所有参数。
所有被WAC发现的AP(还未进行配置)都被默认分配到一个"default"的AP组,一个AP只能属于一个AP组,多个AP 可以属于同一个AP组。
可以建立新的AP组,然后把特定的AP分配到新建的AP组。
可以修改AP组的参数,使修改参数应用到所有属于这个AP组的AP,也可以对一个特定的AP进行参数修改,修改的参数将覆盖AP组对应的参数。
1、创建一个AP组(例如:temp):2、把一个AP分配到特定的AP组:Configuration > Wireless> AP Installation,选择特定的AP,点击provision.在AP Group中选择特定的AP组名称(例:选择上面创建的temp组)。
注:修改一个AP所属的AP组,需要重启AP才生效。
二、Virtual APAP发送的Beacon,probe respones包中包含了WLAN的SSID,认证方式,支持的速率等信息,STA关联到BSSID(通常为AP的MAC地址)。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
(完整)aruba配置手册编辑整理:尊敬的读者朋友们:这里是精品文档编辑中心,本文档内容是由我和我的同事精心编辑整理后发布的,发布之前我们对文中内容进行仔细校对,但是难免会有疏漏的地方,但是任然希望((完整)aruba配置手册)的内容能够给您的工作和学习带来便利。
同时也真诚的希望收到您的建议和反馈,这将是我们进步的源泉,前进的动力。
本文可编辑可修改,如果觉得对您有帮助请收藏以便随时查阅,最后祝您生活愉快业绩进步,以下为(完整)aruba配置手册的全部内容。
拓扑图如下:客户的要求如下:ap地址通过核心交换机分配,全部在一个vlan中无线用户地址通过核心交换机分配,按照楼层不同,对应不同的vlan,分配不同的地址用户采用web或802。
1x认证方式,与内部radius认证服务器联动所有ap均向外公布同一个ssid设备初始化设置拿到设备后,先进行初始化配置,恢复设备到出厂设置状态,在恢复出厂设置后,通过console 连接到设备上,按照下面的提示进行初始信息的输入:Enter System name [Aruba5000]: Aruba-masterEnter VLAN 1 interface IP address [172.16.0.254]:Enter VLAN 1 interface subnet mask [255.255.255.0]:Enter IP Default gateway [none]:Enter Switch Role, (master|local) [master]:Enter Country code (ISO—3166), 〈ctrl-I〉 for supported list: cn You have chosen Country code CN for China (yes|no)?: yEnter Time Zone [PST—8:0]:Enter Time in GMT [09:44:27]:Enter Date (MM/DD/YYYY) [3/6/2007]:Enter Password for admin login (up to 32 chars): *****Re—type Password for admin login:*****Enter Password for enable mode (up to 15 chars):******Re-type Password for enable mode: ******Do you wish to shutdown all the ports (yes|no)? [no]: nCurrent choices are:System name: Aruba800—4VLAN 1 interface IP address: 172。
16.0。
254VLAN 1 interface subnet mask: 255.255。
255.0IP Default gateway: noneSwitch Role: masterCountry code: cnTime Zone: PST-8:0Ports shutdown: nIf you accept the changes the switch will restart!Type 〈ctrl—P〉 to go back and change answer for any questionDo you wish to accept the changes (yes|no)yCreating configuration.。
Done.System will now restart!完成了初始化配置后,就可以登录设备,输入初始化设置时配置的用户名/密码,以及enable 密码,就可以进入设备的特权模式。
User: adminPassword: *****(Aruba800-4)〉enPassword:******(Aruba800—4) #集中控制器基本配置此时,我们已经可以登录172.16.0.254这个地址来通过web页管理设备了,下面,我们结合上面的拓扑图,来说明aruba设备的基本配置.在用户的真实网络环境中,不能保证17216.0。
254这个地址一定全网路由可达,所以,根据需要,我们首先修改vlan1的地址,保证集中控制器全网路由可达。
下面是命令行方式:(Aruba800-4) (config-if)#interface vlan 1(Aruba800-4) (config-subif)# ip address 172。
16.0.254Switch IP Address is Modified。
Switch should be rebooted now(Aruba800—4) #reloadDo you want to save the configuration(y/n): ySaving Configuration...Saved ConfigurationDo you really want to reset the system(y/n): ySystem will now restart!Shutdown processing startedSyncing data。
.done。
Web设置如下:注意,vlan1的地址在修改后,设备会重新启动。
同时,我们建议为集中控制器配置loopkback接口地址,且与vlan1在同一个地址段里,因为只要设备在加电运行,loopkback接口就不会down掉,为了保证可靠性,建议配置一下loopkback 接口的地址。
命令行方式如下:(Aruba800-4) (config)#interface loopback(Aruba800-4)(config—loop)#ip address 172.160。
253 255。
255。
255。
0web页方式如下:根据拓扑所示,集中控制器与核心交换机之间通过Trunk连接,选择需要做trunk的端口号,选择native vlan号。
也可以配置trunk线路允许通过的vlan id。
通过下面的命令来设置: (Aruba800-4) (config) #interface fastethernet 1/8(Aruba800—4) (config-if)#switchport trunk en dot1q(Aruba800-4) (config—if)# switchport mode trunk(Aruba800—4) (config—if)#no sh(Aruba800-4)(config—if)#switchport trunk allowed vlan add 1-100web设置如下:接下来,需要在集中控制器上配置相对应的vlan,建议vlan号与核心交换机上相同,并且创建对应的vlan interface接口地址.记住一定要添加一个vlan interface接口地址,否则,如果采用web认证方式,会出现无法显示认证页面的情况。
如果该vlan的用户需要上公网,也就是说该vlan的用户需要做nat,那么还需要配置启用该vlan的nat功能。
加入该命令后,集中控制器会在与缺省路由匹配的接口上为该vlan的用户启用nat功能。
如果该vlan的用户使用dhcp的方式获得ip地址,那么还要使用ip helper—address来指定dhcp服务器的地址。
命令行如下:(Aruba800-4) (config-subif)#vlan 100(Aruba800-4)(config) #interface vlan 100(Aruba800—4)(config—subif)#ip address 172。
16。
100.1 255。
255.255.0 (Aruba800-4) (config-subif)#no sh(Aruba800-4) (config—subif)#ip nat inside(Aruba800—4) (config—subif)#ip helper-address 172。
16。
0.254 web设置如下:如果采用aruba控制器作为dhcp服务器,那么相关命令行配置如下:(Aruba800-4) (config)#service dhcp(Aruba800—4) (config) #ip dhcp pool pool1(Aruba800—4) (config-dhcp)#network 172.16。
0。
0 255.255。
255.0 (Aruba800—4) (config-dhcp)#default-router 172.16。
0.254(Aruba800-4) (config—dhcp)#dns-server 172.16.0。
254web配置方式如下:地址池的名称、地址段、网关和dns服务器都是必须要填写的,特别是dns服务器地址,一定要填一个,否则在采用web认证方式时,也会出现无法显示认证页面的问题。
配置完成后,应如下图所示,还要在全局启用dhcp服务,即Enable DHCP Server.集中控制器实际上工作在2层模式,所以需要一条缺省网关:(Aruba800-4) (config) #ip default-route 192.168。
50.1web设置如下:至此,网络层面的设置基本完成,接下来,就需要配置无线用户的身份认证信息了。
一般情况下,可以使用集中控制器内置的数据库,来完成用户的登录认证,如果网络中有RADIUS或者LADP 等认证服务器,也可以很方便的与其联动。
使用内置数据库认证的配置如下:配置完成后,应该如下图所示:如果是与RADIUS服务器联动,相关配置如下:完成radius服务器的添加后,如下图所示:在完成了用户认证的配置后,可以开始配置相关的ssid.Ssid的配置有2种情况,一种是在通用界面下配置,此时配置的每一个ssid,都会被每一个ap接收并广播出去,且每个ssid只能为接入的用户分配一个vlan的地址,即所有接入该ssid的用户,都会分配到同一个地址段内的地址。
在这种情况下,这样的配置方式不能满足上图的要求,所以,我们要采用另一种配置ssid 的方式,即针对每个location来配置ssid。
Aruba允许用户为每个ap配置location,采用的3为的点分十进制方式,比如1.1。
1,分别表示建筑物号、楼层号、ap号.当然了,也可以根据实际情况,来自行定义这3个数字的含义。
我们首先说明如何配置通用模式下的ssid,如下图所示:在图中我们需要设置的内容包括ssid的名称,支持的无线类型,采用的认证和加密方式,使用的认证服务器类型,以及无线用户接入时分配到IP地址所属的vlan号。
