Computer Organization and Architecture
操作系统概念第七版_第01章

Operating System Definition (Cont.)
No universally accepted definition “Everything a vendor ships when you order an operating system”
is good approximation
Operating-System Operations
Process Management Memory Management Storage Management
Protection and Security
Distributed Systems Special-Purpose Systems Computing Environments
Users
Operating System Concepts – 7th Edition, Jan 12, 2005
1.5
Houor ©2011
Four Components of a Computer System
Operating System Concepts – 7th Edition, Jan 12, 2005
OS is a control program
User view
Ease of use PC Resource utilization mainframe
Operating System Concepts – 7th Edition, Jan 12, 2005
1.7
Houor ©2011
1.13
Houor ©2011
Interrupt Timeline
计算机体系结构量化研究方法英文版第四版教学设计 (3)

Teaching Design for Quantitative Research Methods in Computer Architecture, 4th Edition IntroductionComputer architecture is the study of the design and organization of computer systems. As the field has evolved, so too have the tools and techniques used for research in computer architecture. This document outlines a teaching design for the fourth edition of the book Quantitative Research Methods in Computer Architecture, which provides an overview of the quantitative research methods most commonly used in the field.ObjectivesThe objectives of this teaching design are:1.To provide an overview of the fundamental concepts andprinciples of quantitative research methods in computerarchitecture.2.To enable students to design and perform experiments usingappropriate research methods.3.To help students develop critical thinking skills toevaluate research findings.Course OutlineThe course is divided into the following chapters:1.Introduction to Quantitative Research Methods in ComputerArchitecture2.Research Design and Experimental Design3.Sampling4.Measurement5.Data Analysis and Statistics6.Reporting Research FindingsChapter 1: Introduction to Quantitative Research Methods in Computer ArchitectureThis chapter provides an introduction to the course. It introduces the terminology and concepts commonly used in quantitative research, and the reasons for using quantitative research methods in computer architecture. It also reviews the different kinds of research questions that can be addressed using quantitative methods.Chapter 2: Research Design and Experimental DesignIn this chapter, students will learn about research design and experimental design. This chapter will cover topics such as identifying research questions, choosing experimental units, selecting the appropriate type of design, and choosing an experimental group and control group.Chapter 3: SamplingThis chapter covers the topic of sampling. Students will learn about different types of sampling methods, including random, stratified, and systematic sampling, and how to choose the appropriate sampling method based on their research questions.Chapter 4: MeasurementIn this chapter, students will learn about measurement and the different types of measurement scales used in quantitative research. They will also learn about the criteria for selecting appropriate measures and techniques for measuring different aspects of computer architecture.Chapter 5: Data Analysis and StatisticsIn this chapter, students will learn about data analysis and statistics. They will learn how to use statistical software to analyze data, conduct descriptive statistics, and use inferential statistics to test hypotheses.Chapter 6: Reporting Research FindingsThe final chapter of the course focuses on reporting research findings. Students will learn how to prepare reports, present findings to different audiences, and deal with ethical issues related to reporting research.Course RequirementsStudents will need to:1.Attend all lectures and participate in class discussions.plete all assigned readings before class.3.Participate in group discussions and group assignments.4.Write a final research paper on a topic related to thecourse.ConclusionThis teaching design provides a comprehensive overview of the quantitative research methods commonly used in computer architecture. Through this course, students will learn the theory and practical skills necessary to design and perform experiments using appropriate research methods. By the end of the course, students will be able to interpret, analyze, and report on research findings in a clear and concise manner.。
计算机系统结构与计算机中的编码

1.1计算机系统结构计算机的发展历史:1946年,世界上第一台电子计算机ENIAC出现,之后经历了5个发展阶段:冯式结构计算机的组成部分:存储器、运算器、控制器、输入设备和输出设备。
强化的概念:计算机的工作过程:一般是由用户使用各种编程语言把所需要完成的任务以程序的形式提交给计算机,然后翻译成计算机能直接执行的机器语言程序,在计算机上运行。
计算机系统可以由下面的模型表示:计算机系统结构(computer architecture):指机器语言级机器(物理机器)的系统结构,它主要研究软件、硬件功能分配,确定软件、硬件界面(机器级界面),即从机器语言程序员或编译程序设计者的角度所看到的机器物理系统的抽象。
计算机组成(computer organization):是指计算机系统的逻辑实现,包括机器内部数据流和控制流的组成以及逻辑设计等,其目标是合理的把各种部件、设备组成计算机,以实现特定的系统结构,同时满足所希望达到的性能价格比。
计算机实现(computer implementation)是指计算机组成的物理实现。
这几个概念之间的关系可以用下面的图加以说明:计算机系统的分类:Flynn分类、冯氏分类、Handler分类和Kuck分类;Flynn分类:根据不同指令流—数据流组织方式把计算机系统分成4类。
(重点理解)指令流:机器指令的执行序列;数据流:由指令流调用的数据序列,包括输入数据和中间结果;多倍性:在系统性能的瓶颈部件上同时处于同样执行阶段的指令和数据的最大可能个数;I. 单指令流单数据流SISD——如单处理机II. 单指令流多数据流SIMD——如相联处理机III. 多指令流单数据流MISD——如流水线计算机IV. 多指令流多数据流MIMD——如多处理机冯氏分类:以最大并行度Pm把计算机系统结构分为4类,其中字宽W表示在一个字中同时处理的二进制位数,位宽B表示在一个位片中能同时处理的字数。
I. 字串位串WSBS(serial)(parallel)II. 字并位串WPBSIII. 字串位并WSBPIV. 字并位并WPBPHandler分类:根据并行度和流水线处理的程度将计算机系统结构分成3个层次I. 程序控制部件PCU的个数KII. 算术逻辑部件ALU或处理部件PE的个数DIII. 每个算术逻辑部件包含基本逻辑线路ELC的套数WKuck分类:与Flynn分类法类似,根据指令流、执行流和多倍性来分类。
coa考核大纲

《计算机组织与结构》考核大纲Chapter 1 Introduction(所占比例1%)1.1 Architecture & Organizationwhich belong to Architecture?which belong to Organization?1.2 Structure & Function1)计算机的四个功能与top层对应的四个结构Chapter 2 Computer Evolution and Performance(1%)2.1 A brief history of computers1)G1-G4计算机发展的各个阶段所使用的主要元件2)Von Neumann的程序存储概念(stored-program)3)Moore’ law描述的问题4)微电子学中,两个基本元件(gate、memory cell)与计算机四个功能之间的关系。
2.2 Designing for performance1)当前计算机性能发展的趋势2)性能平衡指的是平衡谁?Chapter 3 A top-level view of computer function and interconnection(3%)3.1 Computer Components1) memory的结构:存储单元(words)与address的关系(是内存最大容量和地址宽度的关系)2) 常用寄存器(MAR、MBR、PC、IR)的功能3.2 Computer Function1) 取指周期和执行周期的概念(fetch & execute)2) 中断(interrupt)过程的四个关键点:suspending, branching, processing, resuming3.3 Interconnection Structures1) Memory, I/O, CPU之间传输的信息2)DB、CB、AB三总线上传输的信息3.4 Bus Interconnection1) 根据功能不同,总线的分类2)根据性能不同,总线的分类Chapter 4 Cache Memory (20%)4.1 Computer memory system overview1) 存储器系统的主要特征?(memory 金字塔图反映的信息)2) 存储器系统的层次特点4.2 Cache memory1) Cache与memory的结构2)cache的行、memory的块,即line、block、way、set的含义。
计算机组成原理 教学大纲
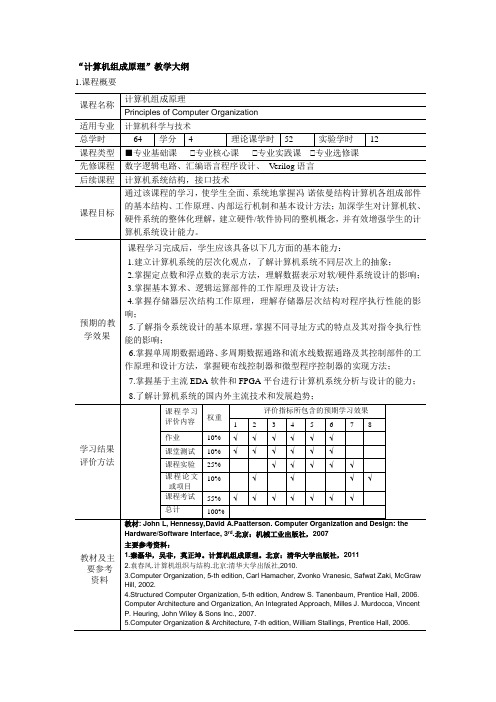
“计算机组成原理”教学大纲1.课程概要2.课程教学内容及建议学时第1章计算机系统概论本章的主要知识点包括冯诺伊曼计算机的组成与工作原理;计算机软/硬件互动关系;计算机不同层次的抽象与表示;CPU性能公式及性能评价方法。
本章课堂教学学时3学时,建议学生课后学习3学时。
第2章数据表示本章的主要知识点包括计算机内部数据的机器级表示及其不同数据表示的特点;浮点数据表示(包括表示形式、规格化、数据表示范围和IEEE754标准)及其应用;常见的数据校验方式(奇偶校验、海明校验和CRC校验)及其特点。
本章课堂教学学时5学时,建议学生课后学习5学时。
第3章运算器方法与运算器本章的主要知识点包括整数和浮点数的运算方法;算术/逻辑运算单元ALU的设计;溢出检测及其实现。
本章课堂教学学时8学时,建议学生课后学习5学时。
第4章存储器层次结构本章的主要知识点包括存储技术(SRAM、DRAM、ROM)及存储系统层次结构;存储期组织及其与CPU的链接;高速缓冲存储器及其在程序性能优化中的应用;虚拟存储器(重点掌握页式虚拟存储器和TLB的工作原理);辅助存储器(RAID)。
本章课堂教学学时12学时,建议学生课后学习20学时。
第5章指令系统本章的主要知识点包括指令格式及其设计;寻址方式;指令系统实例(以MIPS机为例) 本章课堂教学学时4学时,建议学生课后学习8学时。
第6章中央处理器本章的主要知识点包括CPU的组成与功能;数据通路的概念;数据通路设计(单周期和多周期);微程序控制器设计;硬布线控制器设计;流水线技术。
本章课堂教学学时10学时,建议学生课后学习20学时。
第7章系统总线本章的主要知识点包括总线特性;总线事务的概念;总线结构;总线仲裁;总线操作;总线举例(PCI,USB);总线标准等。
本章课堂教学学时4学时,建议学生课后学习4学时。
第8章输入/输出系统本章的主要知识点包括接口功能;常见I/O数据传送方式(程序查询、程序中断和DMA 方式)工作原理及其特点。
EECS 252 Graduate Computer Architecture Lec 01 - …

CS252 Executive Summary
The processor you built in CS152 What you‟ll understand after taking CS252
Also, the technology behind chip-scale multiprocessors
Performance (vs. VAX-11/780)
??%/year
1000 52%/year 100
10 25%/year
1 1978 1980 1982 1984 1986 1988 1990 1992 1994 1996 1998 2000 2002 2004 2006
• VAX : 25%/year 1978 to 1986 • RISC + x86: 52%/year 1986 to 2002 • RISC + x86: ??%/year 2002 to present
8/28 CS252-Fall’07 8
Uniprocessor Performance
10000
From Hennessy and Patterson, Computer Architecture: A Quantitative Approach, 4th edition, October, 2006
Supercomputers
3
CS252-Fall’07
What is Computer Architecture?
Application
Gap too large to bridge in one step (but there are exceptions, e.g. magnetic compass)
Computer System Organization计算机系统的组成
Computer System Organization2.4 Memory Subsystem OrganizationMemory is also known as internal memory or main memory. It refers to the circuits in the computer that hold whatever programs and data are available for immediate use by the CPU. In this section we will review the different types of physical memory and discuss the memory hierarchy.2.4.1 Types of memoryThere are two major types of memory: Random Access Memory (RAM) and Read Only Memory (ROM). Many computer systems,including personal computers,include both ROM and RAM.1.RAMRAM, also called read/write memory, can be used to store data that changes. Unlike ROM, RAM is erasable, temporary, and volatile ---- meaning that it blanks out each time you turn the computer off. RAM is essential to a computer because it provides rapidly accessible circuitry where the CPU can run your programs and process your data. You may have dozens of computer games or other application software programs stored on a disk, but the computer cannot use them there; when you select a program to run, the computer must first copy it from the disk to RAM where the CPU can access it. It’s particularly important to remember that all the data you type into the computer goes directly to RAM. If you want to keep your data permanently, you must save it by copying it to a secondary storage device such as a disk. The amount of RAM in a computer can be very important. If your computer has too little memory, complicated programs will run slowly or won’t run at all. To stretch the amount of RAM, an operating system can use a strategy called virtual memory that reserves part of the hard disk for use as an extension to RAM. In a computer with virtual memory, less-used parts of programs are shifted from RAM to a hard disk and are moved back only when needed. Although virtual memory may allow your computer to run large programs, it will reduce the amount of secondary storage and may cause programs to run slowly because it takes time to swap data to and from the hard disk.(1)DRAMRAM chips are differentiated by how they maintain their data. Dynamic RAM or DRAM chips are like leaky capacitors. Initially data is stored in the DRAM chip, charging its memory cells to their maximum values. The charge slowly leaks out and would eventually go too low to represent valid data. Before this happens, however, refresh circuitry reads the contents of the DRAM and rewrites the data to its original locations, thus restoring the memory cells to their maximum charges. DRAM is used to construct the RAM in personal computers.(2)SRAMStatic RAM, or SRAM, is more like a register than a leaky capacitor. Oncedata is written to SRAM, its contents stay valid, and it does not have to be refreshed. Static RAM id faster than DRAM, but it is also much more expensive. The cache memory in personal computers is constructed from SRAM.2.ROMROM chips are designed for applications in which data only read. These chips are programmed with data by external programming unit before they are added to the computer system. Once this is done, the data usually does not change. A ROM chip is well suited for this purpose it is nonvolatile, meaning that the instructions recorded in it do not disappear when the power is off. When you turn the computer on, the permanent software in ROM boots the computer. To boot the computer, ROM first tells the CPU to determine what input, output, and storage devices happen to be attached to your computer. Then it instructs the CPU to check a disk to see if it contains operating system software that will let you start giving commands. The ROM in a typical personal computer also has a variety of self-test routines to make it easier to diagnose and repair hardware failures.There are several types of ROM chips, which are differentiated by how and how often they can be programmed.(1)Masked ROMA masked ROM, or simply a ROM, is programmed with data as the chip is fabricated. The mask used to create the chip is designed with the required data hard-wired into it. There chips are useful for consumer appliances, where large numbers of units are produced, and, once installed, data will not be changed.(2)PROMA PROM is a programmable ROM. Unlike the ROM, the PROM can be programmed by the user with any standard PROM programmer. Rather than being hard-wired, the PROM has a series of internal connections similar to fuses. Programming data into the PROM essentially blows the proper fuses so that each word of memory stores the correct value. Because these fuses cannot be restored once they are blown, PROM can only be programmed once. These chips are well suited for applications that could use a ROM but will not have a sufficient quantity of units manufactured to justify the cost of the ROM mask.(3)EPROMAn EPROM is an erasable PROM. As its name implies, an EPROM can be programmed like a PROM, but its contents can be erased and the chip reprogrammed. Programming an EPROM is akin to charging capacitors. The charged and uncharged capacitors cause each word id memory to store the correct value. These chips have a small clear window on their faces. The chip is erased by being placed under ultraviolet light that causes the capacitors to leak their charge, thus we can reset the chip’s contents. When in use, the window is usually covered with opaque tape to preventany ultraviolet rays in room light or sunlight from inadvertently destroying the contents of the chip. Because they are erasable, but are used in applications where their data does change, EPROM is typically usedin product development labs and in prototypes.(4)EEPROM or E2PROMAn EEPROM, sometimes denoted as E2PROM, is an electrically erasable PROM. It works like an EPROM, except that its contents are erased and reprogrammed electrically, rather than by using ultraviolet light. Unlike the EPROM, which must be entirely erased and then reprogrammed,it is possible to modify individual locations if the EEPROM while leaving other locations unchanged. EEPROM can be used in applications where the contents will by changed only rarely, as long as the programming hardware needed to reprogram the chip is included in the system circuitry. One common use for EEPTOM is the basic input/output system, or BIOS, of personal computers. This chip is usually not modified, except once or twice in the computer’s lifetime when the BIOS are updated with a newer version of its software.(5) Flash EEPROMA special type of EEPROM called a flash EEPROM is electrically erasable in blocks of data, rather than individual locations. It is well suited for applications that write blocks of data and can be used as a solid stated. It is also used for data storage in digital cameras. Flash EEPROM can only be rewritten with data a finite number of times, which currently limits its widespread use in computer systems.RAM and ROM chips are available in a variety of sizes. If the memory needed for the computer is larger than the capacity of one chip, it is necessary to combine a number of chips to form the required memory size. 2.4.2 Memory hierarchyThe memory hierarchy system consists of all storage devices employedin a computer system from the slow but high-capacity auxiliary memory toa relatively faster main memory, to an even small and faster cache memory accessible to the high-speed processing logic. The components in a typical memory hierarchy are shown in Figure 2-3.The memory unit that communicates directly with the CPU is called the main memory. Devices that provide backup storage are called auxiliary memory. The most common auxiliary memory devices used in computer system are magnetic disks and tapes. They are used for storing system programs, large data files, and other backup information. Only programs and data currently needed by the CPU reside in main memory when needed. When programs not resided in main memory are needed by the CPU, they are broughtin from auxiliary memory. Programs not currently needed in main memory are transferred into auxiliary memory to provide space for currently used programs and data.A special very-high-speed memory called a cache is sometimes used toincrease the speed of processing by making current programs and data available to the CPU at a rapid rate. The cache memory is employed in computer systems to compensate for the speed differential between main memory access time and processor logic. CPU logic is usually faster than main memory access time and processing speed is limited primarily by the speed of main memory. A technique used to compensate for the mismatch in operating speeds is to employ an extremely fast, small cache between the CPU and main memory whose access time is close to processor logic clock cycle time. The cache is used for storing segments of programs currently being executed in the CPU and temporary data frequently needed in the present calculations. By making programs and data available at a rapid rate, it is possible to increase the performance rate of the computer.Figure 2-3 shows the CPU has direct access to both cache and main memory but not to auxiliary memory. In memory hierarchy system, each component is involved with a different level. The reason for having two or three levels of memory hierarchy is economics. As storage capacity of the memory increases, the cost per bit for storing binary information decreases and the access time of the memory becomes longer. The auxiliary memory has a large storage capacity, is relatively inexpensive, but has low access speed compared to main memory. The cache memory is very small, relatively expensive, and has very high access speed. Thus as the memory access speed increases, so does its relative cost. The overall goal of using a memory hierarchy is to obtain the highest-possible average access speed while minimizing the total cost of the entire memory system. 2.5 I/O Subsystem OrganizationIn this section, we will describe the I/O interface, and modes of transfer.2.5.1 I/O Devices1. KeyboardsComputer keyboards were originally designed to imitate to imitate electric typewrites so that typists could learn to use computer more easily. The demands of computer technology, however, have led to keys and keyboard layouts never before seen on a typewriter. While a typewriter has only about 50 keys, a computer keyboard may have 100 or more. A computer’s keys are generally divided into four clusters: alphanumeric key, function keys, cursor keys, and the numeric keypad. Alphanumeric keys include letters, numbers, and punctuation marks. They are arranged much like the keys on a typewriter. Function keys are labeled F1, F2, and so on up to F12 or F15. They can be used for giving common commands such as “Print” or “Quit program”. The precise purpose of any function key varies from one program to another. Cursor keys are used to move the cursor around on the screen. The cursor is the little blinking symbol that indicates where things will happen next on the screen. When you are typing, the cursor always blinks just to the tight of the last character you typed. Cursor keys include the arrow keys for moving up, down, left, and right,ad well as the Home, and End keys. The numeric keypad includes the mathematical keys found on a standard calculator.2. MouseMice are popular because it is easier to point than to type, and because the arrow keys don’t work very well for drawing pictures or moving things on the screen. A mouse consists of a ball mounted under a plastic housing with one or more buttons on top. As you move the mouse around the tabletop, sensors inside register the rolling of the ball and move the cursor around the screen to match. There are three basic ways of giving commands with the mouse. First, you can click the button to identify something----perhaps to indicate which part of a drawing you want to change. Second, you can drag the mouse; that is, you can hold the button down while you move the mouse. Dragging can be used to move a drawing across the screen. The third way to give a command is to double-click the mouse’s button by pressing it twice within about a half second. Double-click is used to select things on the screen.The simplest pointing tool of all, of course, is the finger. In fact, touch screens are widely used in department---- store advertising displays, information kiosks, lottery game machines, and other places where users are not expected to have much familiarity with computers. On these machines you simply touch the part of the display screen you want to select, just as you might push a vending machine’s button. Depending on the sensing method used by the touch screen, your finger might interrupt a network of infrared rays protected across the screen’s surface. This would tell the computer where you pointed.3.MonitorA monitor, or display screen, provides a convenient but temporary way to view information. The earliest computer monitors were simply converted television sets. While ordinary TVs are still used for some video games, most computer programs today demand higher-quality monitors. The quest for better monitors has taken two paths: the improvement of TV-like screens and the development of flat screens.4. PrintersDifferent kinds of computer printers use surprisingly different technologies. Some printers squirt ink, some apply heat to sensitive paper, others hammer inked ribbons, and still others create images with lasers. Laser printers work by reflecting a laser beam from a rapidly rotating octagonal mirror onto a light-sensitive roller. Ink-jet printers work by squirting tiny droplets of liquid ink at the paper. Dot-matrix printer features a moveable print head containing a row of tiny pins. The pins push an inked ribbon against the paper, producing a matrix (or pattern) of dots. As the print head moves back and forth across the page, the dots can form either letters or graphics.5. ModemA modem, short for modulator-demodulator, is used for communicating between computers. The modem converts a computer’s electronic impulses to a form that can be transmitted over a telephone line. When the signal reaches the destination computer, another modem reconverts the signal to computer understandable form. Some modems are book-sized boxes that plug into the back pf a computer; others fit inside the computer’s housing.2.5.2 I/O InterfaceInput-output interface provides a method for transferring information between internal storage and external I/O devices. Peripherals connected to a computer need special communication links for interfacing with the central processing unit. The purpose of the communication link is to resolve the differences that exist between the central computer and each peripheral. The major differences are:● Peripheral are electromechanical and electromagnetic device and their manner or of operation is different from the operation of the CPU and memory, which are electronic devices. Therefore, a conversion of signal values may be required.● The data transfer rate of peripherals is usually slower than the transfer rate of the CPU, and consequently , a synchronization mechanism may be needed.● Data codes and formats in peripherals differ from the word format in the CPU and memory.●The operating modes of peripherals are different from each other and each must be controlled so as not to disturb the operation of other peripherals connected to the CPU.To resolve these differences, computer systems include special hardware components between the CPU and peripherals to supervise and synchronize all input and output transfers. These components are called interface units because they interface between the processor bus and the peripheral device. In addition, each device may have its own controller that supervises the operations of the particular mechanism in the peripheral. I/O interface shows in Figure 2-1. Each peripheral decodes the address and control received from the I/O bus, interprets them for the peripheral, and provides signals for the peripheral controller. It also synchronizes the data flow and supervises the transfer between peripheral and processor.2.5.3Modes of TransferBinary information received from an external device is usually stored in memory for later processing. Information transferred from the central computer into an external device originates in the memory unit. The CPU merely executes the I/O instructions and may accept the data temporarily, but the ultimate source or destination is the memory unit. Data transfer between the central computer and I/O devices may be handled in a variety of modes. Some modes use the CPU as an intermediate path; the otherstransfer the data directly to and from the memory unit. Data transfer to and from peripherals may be handled in one of three possible modes:●Programmed I/O●Interrupts●Direct memory access(DMA)1. Programmed I/OProgrammed I/O operations are the result of I/O instructions written in the computer program. Each data item transfer is initiated by an instruction in the program. Usually, the transfer is to and from a CPU register and peripheral. Other instructions are needed to transfer the data to and from CPU and memory. Transferring data under program control requires constant monitoring of the peripheral by the CPU. Once a data transfer is initiated, the CPU is required to monitor the interface to see when a transfer can again be made. It is up to the programmed instructions executed in the CPU to keep close tabs on everything that is taking place in the interface unit and the I/O device.In the programmed I/O method, the CPU stays in a program loop until the I/O unit indicates that it is ready for data transfer. This is a time-consuming process since it keeps the processor busy needlessly. It can be avoided by using an interrupt facility and special commands to inform the interface to issue an interrupt request signal when the data are available from the device. In the meantime the CPU can proceed to execute another program. The interface meanwhile keeps monitoring the device. When the interface computer. Upon detecting the external interrupt signal, the CPU momentarily stops the task it is processing, branches to a service program to process the I/O transfer, and then returns to the task it was originally performing.2. InterruptsAn alternative to the CPU constantly monitoring the flag is to let the interface inform the computer when it is ready to transfer data. This mode of transfer uses the interrupt facility. While the CPU is running a program, it does not check the flag. However, when the flag is set, the computer is momentarily interrupted from proceeding with the current program and is informed of the fact that the flag has been set. The CPU deviates from what it is doing to take care of the input or output transfer. After the transfer is completed, the computer returns to the previous program to continue what it was doing before the interrupt.The CPU responds to the interrupt signal by storing the return address from the program counter into a memory stack and then controls branches to a service routine that processes the required I/O transfer. The way that the processor chooses the branch address of the service routine varies from one unit to another. In principle, there are two methods foraccomplishing this. One is called vectored interrupt and the other, interrupt. In an interrupt, the branch address is assigned to a fixedlocation in memory. In a vectored interrupt, the source that interruptssupplies the branch information to the computer. This information iscalled the interrupt vector. In some computers the interrupt vector isan address that points to a location in memory where the beginning addressof the I/O service routine is stored.3. Direct memory access (DMA)Another aspect of computer system performance that can be improvedis the transfer of data between memory and I/O devices. This is a commonoperation in computer systems. Loading programs or data files from diskinto memory, saving files on disk, and accessing virtual memory pages onany secondary storage medium all fall into this category of operations.Consider a typical system consisting of a CPU, memory, and one or moreinput/output devices. Assume one of the I/O devices is a disk drive andthat the computer must load a program from this drive into memory. TheCPU would read the first byte of the program and then write that byte tomemory. Then it would do the same for the second byte and each succeedingbyte, until it had loaded the entire program into memory.This is, at best, inefficient. Loading data into, and then writing dataout of, the CPU significantly slows down the transfer. The CPU does notmodify the data at all, so it only serves as an additional stop for dataon the way to its final destination. The process would be much quickerif we could bypass the CPU and transfer data directly from the I/O deviceto memory. Direct memory access, or DMA does exactly that.A DMA controller implements direct memory access in a computer system.It connects directly to the I/O device at one end and to the system busesat the other end. It also interacts with the CPU, both via the system busesand two new direct connections.To transfer data from an I/O device to memory, the DMA controller firstsends a bus request to the CPU by setting BR to 1. When it is ready togrant this request, the CPU sets its bus grant signal, BG, to 1. The CPUalso tri-states its address, data, and control lines, thus truly grantingcontrol of the system buses to the DMA controller. The CPU will continueto tri-state its outputs as long as BR is asserted.Now that the DMA controller has of the system buses, it can performthe desired data transfers. To load data from an I/O device into memory,it asserts the appropriate I/O control signals and loads data from theI/O device into its internal DMA data register. Next, it writes this datato memory. To do this, it outputs the memory address onto the system’saddress bus and the data onto the data bus. The DMA controller also assertsthe appropriate signals on the system’s control bus to cause memory toread the data. DMA controller then writes the second data value to thefollowing memory location, continuing until it has transferred the entireblock of data.To understand how the DMA controller performs this transfer, we must examine its internal architecture. The DMA controller includes several registers. The DMA address register contains the memory address to be used in the data transfer. The CPU treats this register as one or more output ports. The DMA count register, sometimes called the word count register, contains the number of bytes of data to be transferred. Like the DMA address register, it is also treated as an output port by the CPU. The DMA control register accepts commands from the CPU. Most DMA controllers also have a status register. This register supplies information to the CPU, which accesses it as an input port. DMA controllers also usually include circuitry to abort the transfer if the I/O device is not ready in some predetermined amount of time. This is called timeout。
计算机组成原理 英文
计算机组成原理英文Computer Organization PrinciplesComputer organization principles refer to the foundational concepts and principles that govern the design and operation of computer systems. These principles are crucial in understanding how computers work and how they can be optimized for better performance and efficiency.One fundamental principle in computer organization is the concept of abstraction. Abstraction allows us to hide complex details and focus on higher-level functionality. In computer systems, abstraction is used to simplify the design and programming process. For example, programming languages provide a high-level abstraction for software developers, allowing them to write code without worrying about the underlying hardware implementation.Another principle is the hierarchy of computer components. Computer systems consist of multiple layers, each responsible for a different level of functionality. The main layers include the application layer, operating system layer, hardware layer, and digital logic layer. Each layer builds upon the layer below it, resulting in a hierarchical structure. This hierarchy enables modular design and allows for easy modification or replacement of individual components without affecting the entire system.The principle of von Neumann architecture is another cornerstone of computer organization. This architecture, proposed by John von Neumann in the 1940s, is the fundamental design concept for most modern computers. It consists of a central processing unit (CPU),memory, input/output (I/O) devices, and a control unit. The CPU fetches instructions from memory, executes them, and stores the results back in memory. This architecture enables the execution of a wide range of tasks and provides flexibility in program execution.Furthermore, the principle of parallelism is essential for improving computer performance. Parallel computing utilizes multiple processing units or cores to execute tasks simultaneously, thereby increasing the system's processing power. Various techniques like pipelining, multiprocessing, and multi-threading are employed to achieve parallelism, allowing for faster execution of tasks and improved system throughput.Another crucial principle in computer organization is the conceptof memory hierarchy. Memory hierarchy refers to the organization of different types of memory storage in a computer system. It includes registers, cache memory, main memory (RAM), and secondary storage devices (like hard drives). The memory hierarchy is designed to provide faster access to frequently used data while accommodating larger storage capacities at lower cost. In conclusion, understanding the principles of computer organization is vital for comprehending the inner workings of computer systems. These principles provide the foundation for designing and optimizing computer architecture and ensure efficient and reliable operation of computer systems.。
中科大计算机组成原理课件ppt
• 唐本(William Stallings)
– 农村包围城市:总线、存储、I/O、ALU、CPU
• llxx
– 目标:理解构建计算机系统的过程
• 十字箴言:“功能、组织、过程、定时、度量”
– China-ring:快速原型法(prototype)
• 总线、RAM、CPU,存储系统(Cache、辅存)、I/O、ALU
• 基于x86的Debug环境,编写任意10个数值的冒 泡排序程序,并调试运行。
– 成果要求:
• 报告设计过程、结果(汇编代码、内存数据段映像)、出现 的典型问题及解决过程; • 要求结果体现个人ID。
实验课
• 设计实现《计算机系统概论》的 LC-3模型机(见附录A/C)
– 共16条指令,指令集具有RISC特征
Basic computer organization, first look at pipelines + caches 从C语言程序的执行 角度讨论计算机组成 原理,但重点关注 MIPS处理器和存储系 统,其他关注很少
Computer Architecture, First look at parallel architectures
Course Schedule
1. 2. 3. 4. 5. 6.
•
概论(4) 总线(4) RAM/ROM(4) ISA(4) CPU (4)
功能、组成、时序、中断系统
A模型CPU控制器设计(6)
组合逻辑、微程序
7.
•
MIPS处理器设计(6)
指令集、单周期、多周期、流水线
8. 9.
•
Cache(4) 辅存(5)
MIT
• 我在这里的第一学期上了一门叫 《计算机系统设计》得 本科课程,其辛苦程度真实一言难尽。十五个星期内交了 十次作业,作了六次课程设计。有的设计还分几个部分, 分开交设计报告。所以设计报告大概也交了有十次左右。 最恐怖的是有一次,十天内要交六份作业或设计报告,而 且当时正值其他几门课正在期中考试。抱怨是没有用的, 老师说:"我很抱歉。但这门课很重要,请大家不停的工 作。"学生从一般的逻辑时序电路开始设计(数电都已忘 得差不多了);核心是自行设计"麻雀虽小五脏俱全"得 ALU,单指令周期CPU(single cycle CPU);多指令 CPU(Multi-cycle CPU);以直到最后实现流水线(pipe line)32位MIPS CPU和Cache。一门课下来,所有与计 算机CPU有关的知识全部融会贯通。硬件设计水平也有了 很大提高(就是太累)。
计算机用英语怎么说
计算机用英语怎么说计算机俗称电脑,是一种用于高速计算的电子计算机器,可以进行数值计算,又可以进行逻辑计算,还具有存储记忆功能。
是能够按照程序运行,自动、高速处理海量数据的现代化智能电子设备。
计算机是20世纪最先进的科学技术发明之一,对人类的生产活动和社会活动产生了极其重要的影响,并以强大的生命力飞速发展。
那么你知道计算机用英语怎么说吗?下面来学习一下吧。
计算机英语说法1:computer计算机英语说法2:calculating machine计算机的相关短语:计算机网络computer network ; computer ; Data network ; Computer communication电子计算机 computer ; electronic computer ; Manoj Chutiya ; Computing machine计算机系统结构computer architecture ; Computer Systems Organization ; Computer systems architecture ; Computing architecture个人计算机 personal computer ; PC ; PC Magazine ; appliance computer计算机二级 VFP ; VF ; visual foxpro ; VB小型计算机minicomputer ; small size computer ; Mini computers ; laptop计算机的英语例句:1. He programmed his computer to compare all the possible combinations.他给他的计算机编制了一套程序,以比较所有可能的组合。
2. They found their computers producing different resultsfrom exactly the same calculation.他们发现他们的计算机进行完全相同的计算会得出不同的结果。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Computer Organization and ArchitectureSCR 1043Semester 2, 09/10Tutorial: Central Processing Unit and Pipelining1.What is the difference between a microprocessor and a microprogram. Is itpossible to design a microprocessor without a microprogram? Are allmicroprogrammed computers also microprocessors?2. What general roles are performed by CPU registers?3. Explain the difference between hardwired control and microprogrammed control.4. What is the function of the condition codes?5.The control logic for many CPUs is organized using microcode. What is thealternative to microcode? What are the advantages and disadvantages of using or not using microcode?6. If the last operation on a computer with an 8-bit word was an addition in whichthe two operands were 2 and 3, what would be the value of the following flags?✓Carry✓Zero✓Overflow✓Sign✓Even parity✓Half-carry (auxiliary carry).7. What if the operands of Question 4 were -1 (2’s complement) and 1?8. Trace the execution of the instructions below by showing all the changes in CPUregisters (control and general purpose registers) as well as the micro-operationsrelated to the instructions.Memory address Instruction39D MOV CX, NUM39E ADD CX, 139F MOV NUM2, CX9. Write the sequence of micro-operations required to add a number to the ACCwhen the number isa. an immediate operandb. a direct-address operandc. an indirect-address operand10. The ALU can add its two input registers, and it can logically complement the bitsof eithe r input register, but it cannot subtract. Numbers are to be stored in two’scomplement representation. List the micro-operations the control unit mustperform to execution a subtraction instruction.11. Assume that the control memory word is 24 bit each. The control portion of themicroinstruction format is divided into two fields. A micro-operation field of 13bits specifies the micro-operations to be preformed. An address selection fieldspecifies a condition, based on the flags that will cause a microinstruction branch.There are eight flags.a. How many bits are in the address selection field?b. How many bits are in the address field?c. What is the size of the control memory?12. We wish to provide 8 control words for each machine instruction routine.Machine instruction opcodes have 5 bits and control memory has 1024 words.Suggest a mapping from the instruction register to the control address register.13. A control memory has 4096 words of 24 bits each.a. How many bits are there in the control address register?b. How many bits are there are for the select field and address field of themicroinstruction?14. Using the mapping procedure as shown in Method 1 of the lecture slide, give thefirst microinstruction address for the following operation code:a. 0010b. 1011c. 111115. Formulate a mapping procedure that provides 8 consecutive microinstructions foreach routine. The operation has six bits and the control memory has 2048 words.16. Show how a 9-bit microoperation field in a microinstruction can be divided intosubfields to specify 46 microoperations. How many microoperations can bespecified in one microinstruction?17. Why is a two-stage instruction pipeline unlikely to cut the instruction cycle timein half, compare with the use of no pipeline?18. Assume an 8088 is executing a program in which the probability of a programjump is 0.1. For simplicity, assume that all instructions are two bytes long.a. What fraction of the instruction fetch bus cycles is wasred?b. Repeat if the instruction queue is 8 bytes long.19. Assume a pipeline processor with 4 stages: fetch instruction (FI), decodeinstruction and calculate addresses (DA), fetch operand (FO), and execute (EX).Draw the space time diagram for a sequence of 7 instructions, in which the thirdinstruction is a branch that is taken and in which there are no data dependencies.20. Assume that RISC architecture ALU instructions have three register operands andthat the result is stored into the first (left-most) register. The architecture isimplemented in ordinary (not superscalar) pipelined fashion so that, in best case, one instruction can be completed in each cycle. The pipeline has 5 phases(instruction fetch, instruction decode, register read, ALU, write back).Observe the following set of instructions generated by the compiler (instructionnumber on left):1 Load R2, VarX ; Regs(2) <- Mem(VarX)2 Add R5, R5, R2 ; Regs(5) <- Regs(5) + Regs(2)3 Loop Move R2, R6 ; Regs(2) <- Regs(6)4 Add R3, R3, R25 Add R2, R3, R56 Jnzer R3, Loop ; Jnzer is jmp not zero7 Move R1, R2Many aspects in the preceding code segment may reduce the execution speedfrom the maximum possible.Describe precisely the problem types defined below and mark in a clear way one occurrence of each problem type in the preceding code segment (if it appearsthere):✓data dependency✓control dependency✓structural dependencyHow can one avoid or reduce the performance problems caused by each problem type?21. Pipelining can be applied within the ALU to speed up floating-point operations.Consider the case of floating-point addition and subtraction. In simplified terms,the pipeline could have 4 stages: 1. Compare the exponents; 2. Choose theexponent and align the mantissa/significant; 3. Add or subtract themantissa/significant; 4. Normalized the results. The pipeline can be considered to have two parallel threads, one handling exponents and one handling significant.Answers4.Answer:Condition codes are bits set by the CPU hardware as the result of operations. Forexample, an arithmetic operation may produce a positive, negative, zero, or overflow result. In addition to the result itself being stored in a register or memory a condition code is also set. The code may subsequently be tested as part of a conditional branch operation.6 & 7Answer:8.Answer:10.Answer:Consider the instruction SUB R1, X, which subtracts the contents of location X from the contents of register R1, and places the result in R1.t1: MAR ← IR(address))t2: MBR ←Memoryt3: MBR ←Complement (MBR)t4: MBR ←Increment (MBR)t5: R1 ←R1) + (MBR)11.Answer:a. Three bits are needed to specify one of 8 flags.b. 24 – 13 – 3 = 8c. 28= 256 words X 24 bits = 6144 bits.12.Answer:An address for control memory requires 10 bits (210 = 1024). A very simple mappingwould be this:opcode XXXXXcontrol address 00XXXXX000This allows 8 words between successive addresses.13.Answer:a.12 bits in CARb.12 bits for Select, 12 bits for Address.14.Answer:a.0 0010 00b.0 1011 00c.0 1111 0015.Answer:Total 11 bit in CAR, 6 bit for opcodes, 3 bit for micro-instructions00 000000 000 (starting address)17.Answer:There could be two possibilities:a.The execution time will generally be longer than the fetch time. Execution willinvolve reading and storing operands and the performance of some operation. Thus,the fetch stage may have to wait for some time before it can empty its buffer.b. A conditional branch instruction makes the address of the next instruction to befetched unknown. Thus, the fetch stage must wait until it receives the nextinstruction address from the execute stage. The execute stage may then have towait while the next instruction is fetched.18.Answer:The occurrence of a program jump wastes up to 4 bus cycles (corresponding to the 4bytes in the instruction queue when the jump is encountered). For 100 instructions, the number of non-wasted bus cycles is, on average, 90 x2 = 180.a.The number wasted is as high as 10x4 = 40. Therefore the fraction of wastedcycles is 40/(180 + 40) = 0.18.b.If the capacity of the instruction queue is 8, then the fraction of wasted cycles is80/(180 + 80) = 0.319.Answer:21.Answer:Extra Questions1. Trace the execution of the instructions below by showing all the changes in CPU register (control and general purpose registers) as well as the micro-operations related to the instructions.2. There are 6 segments as follows:The interface delay is 4 ns.a.What is the execution time for 10 instructions without pipeline?b.What is the execution time for 10 instructions with pipeline?c.What is the maximum/theoretical speedup?d.What is the real speedup?3. Assume a pipeline processor with 4 stages: instruction fetch (IF), operand fetch (OF), instruction execute (IE) and operand store (OS). Draw the space time diagram and solve the problem of data dependency using NOP for the following sequence of instructions:ADD AH, BHSUB AH, 2CMP AH, 04. With the same pipeline processor as question 3, draw the space time diagram for the following sequence of instructions:ADD AH, BHSUB CH, 2JMP A1AND AH, 011FSHL BH, 3A1: MUL AH, BHa.Solve the branching problem using NOP.b.Solve the same problem by rearranging the instructions.。
