Searching a terabyte of text using partial replication
计算机专业英语2013影印版课后答案(ComputingEssentials2013)选择题

计算机专业英语2013影印版课后答案(ComputingEssentials2013)选择题计算机专业英语2013影印版课后答案(Computing Essentials 2013)选择题Multiple 11. The keyboard, mouse, monitor, and system unit are:hardware output devices storage devices software2. Programs that coordinate computer resources, provide an interface, and run applications are known as:application programs operating systemsstorage systems utility programs3. A browser is an example of a:basic application specialized programsystem application utility program4. Although not as powerful as a supercomputer, this type of computer is capable of great processing speeds and data storage.mainframe media center midrange netbook5. The smallest type of microcomputer:netbook handheld midrange tablet PC6. RAM is a type of:computer memory network secondary storage 7. Unlike memory, this type of storage holds data and programs even after electrical power to the computer system has been turned off.primary RAM ROM secondary8. The type of file created by word processors to save, for example, memos, term papers, and letters.database document presentation worksheet9. The change in connectivity that uses the Internet and the Web to shift many computer activities from a user’s comput er to computers on the Internet.cloud computing high definition network USB10. The largest network in the world is [the]:Facbeook Internet Web USBMultiple 21. The network that connects computers all over the world.CERN Internet LAN Web2. The rules for exchanging data between computers.DSL protocols Web WWW3. Client-based e-mail accounts require this special program to be installed on your computer.e-mail client hyperlink Java utility4. Communities of individuals who share a common interest typically create Facebook:clients groups pages profiles5. E-mail that does not require an e-mail program installed on a user's computer is known as:blog podcast Webmail utility6. A very well-known microblog.LinkedIn MySpace Twitter Wikipedia7. These programs continually look for new information and update search services’ database programs.filters IM spiders wikis8. A type of search engine that submits requests to other search engines, organizes their responses, eliminates duplicate responses, orders hits, and then provides an edited list.directory search ISPmetasearch engine specialized search engine9. This is th e Internet’s equivalent to traditional cash.digital cash e-commerce icash Internet dollars 10. Using file transfer utility software, you can copy files to your computer from specially configured servers on the Internet. This is called:downloading filtering blogging uploadingMultiple 31. This type of software works with end users, application software, and computer hardware to handle the majority of technical details.application general purpose system utility2. A rectangular area that can contain a document, program, or message.dialog box form frame window3. Programs that create text-based documents.DBMS suites spreadsheets word processors 4. Programs that organize, analyze, and graph numeric data such as budgets and financial reports.DBMS suites spreadsheets word processors5. In a spreadsheet, the intersection of a row and column creates a:cell formula function label6. A collection of related data that is the electronic equivalent of a file cabinet.cell database document table7. A database tool that will quickly rearrange a table’s records according to a selected field.filter sort spreadsheet word processor8. Programs that combine a variety of visual objects to create attractive, visually interesting presentations.DBMS presentation graphics spreadsheet word processor 9. The primary disadvantage of this type of package is that the capabilities of each function are not as extensive as in individual programs.integrated office software utility10. A type of suite stored at a server on the Internet and available anywhere through Internet access.cloud integrated office utilityMultiple 41. These specialized graphics programs combine text and graphics to create publications of professional quality.desktop publishing programs image editorsimage galleries illustration programs2. Also known as drawing programs.desktop publishing programs image editorsimage galleries illustration programs3. Graphics programs used to create and edit vector images.desktop publishing programs image editorsimage galleries illustration programs4. An essential multimedia feature that allows user participation.Flash interactivity immersion raster5. Special programs used to create multimedia presentations.desktop publishing programs Flash editorsimage editors multimedia authoring programs 6. A widely used interactive animation application from Adobe.ACTION Flash Fuzzy WYSIWYG7. Programs for Web site design and HTML coding are called Web page editors orapps HTML editors VR programs Web editors8. This area of artificial intelligence is also known as expert systems.acoustics knowledge-based systems robotics virtual reality 9. A type of artificial intelligence that uses a database to provide assistance to users.acoustics expert systems robotics virtual reality 10. Another name for the database used in expert systems that contains specific facts and rules.access table expert table knowledge base rule baseMultiple 51. What type of software works with users, application software, and computer hardware to handle the majority of technical details?dapplication desktop Linux system2. The programs that convert programming instructions written by programmers into a language that computers understand and process are language: converters linguists managers translators3. The ability to switch between different applications stored in memory is called:diversion multitasking operational interference programming 4. Graphic representations for a program, type of file, or function: app icon image software5. This operating system feature is controlled by a mouse and changes shape depending on its current function.dialog box menu mouse pointer6. The operating system based on Linux, designed for Netbook computers, and focused on Internet connectivity throughcloud computing:Chrome Mac Unix Windows7. The mobile operating system developed by Apple and originally called iPhone OS:Android BlackBerry OS IOS Mac OS8. A utility program that makes copies of files to be used in case the originals are lost or damaged:Backup and Restore Disk Cleanup Disk Defragmenter Compactor 9. A troubleshooting utility that identifies and eliminates nonessential files, frees up valuable disk space, and improves system performance:Backup and Restore Disk Cleanup Disk Defragmenter Compactor 10. Windows makes it easy to update drivers with Windows:Backup Restore Driver UpdateMultiple 61. This container houses most of the electrical components for a computer system.carrier package system board system unit TV tuner2. Similar to notebooks, this system unit specializes in on-the-go Web browsing and e-mail access.chassis desktop media center netbook3. Computers can only recognize this type of electronic signal.analog bus digital maximum4. The main or motherboard is also known as the:computer board processor mobile system system board 5. How many bytes can a 32-bit-word computer access at one time?1 48 166. In a microcomputer system, the central processing unit is contained on a single:bus chip module RAM7. This type of memory divides large programs into parts and stores the parts ona secondary storage device.direct expanded random-access virtual8. Also known as NIC, this adapter card is used to connect a computer to a:AIA expansion graphics network9. This provides a pathway to connect parts of the CPU to each other.bus Plug and Play wired wireless10. Older ports that have largely been replaced by faster, more flexible ports are called:buses expandable legacy renderedMultiple 71. Most keyboards use an arrangement of keys known as:Alpha Daisy OptiKey QWERTY2. The device that controls a pointer displayed on the monitor.cord mouse printer scanner3. Also known as a roller ball, this device controls the pointer by rotating a ball with your thumb.trackball joystick cordless mouse stylus4. The type of screen that can be touched with more than one finger and supports zooming in and out by pinching and stretching your fingers.digital dynamic multitouch OLED5. Flatbed and document are types of:headsets HDTVs monitors scanners6. Device used by banks to automatically read those unusual numbers on the bottom of checks and deposit slips.MICR FDIC OMR UPC7. The most widely used audio-input device.mouse VR microphone TFT8. The monitor feature that specifies how often a displayed image is updated.aspect ratio dot pitch refresh rate resolution rate 9. Handheld, book-sized devices that display text and graphics.e-book readers HDTV lasers whiteboards10. This technology allows television stations to broadcast their programming directly to smartphones, computers, and digital media players.CRT HDTV LED Mobile DTVMultiple 81. RAM is sometimes referred to as:primary storage ratio active memoryread only memory secondary storage2. The actual physical material that holds the data and programs.primary storage media disk access3. Measures how tightly these charges can be packed next to one another on the disk.density cylinders tracks sectors4. When a read/write head makes contact with the hard disk’s surface, it causesa head:crash land pit scratch5. This hard-disk performance enhancement anticipates data needs.disk caching file compression file decompression RAID6. This type of storage uses pits and lands to represent 1s and 0s.cloud hard disk optical solid state7. DVD stands for:digital versatile disc digital video datadynamic versatile disc dynamic video disc8. USB drives are also known as:flash drives optical drives ports universal state bus9. An organizational strategy to promote efficient and safe use of data across the networks.cloud dynamic data mission statemententerprise storage system RAID10. A mass storage device that provides access to data archived on tapes.file system NAS RAID system tape libraryMultiple 91. The concept related to using computer networks to link people and resources.connectivity GPS TCP/IP Wi-Fi2. A high-frequency transmission cable that delivers television signals as well as connects computers in a network. coaxial hi def 3-D twisted pair3. A short-range radio communication standard that transmits data over short distances of up to approximately 30 feet. Bluetooth broadband DSL TCP/IP4. The speed with which a modem transmits data is called its:digital velocity dynamic rate modular rating transfer rate5. The bandwidth typically used for DSL, cable, and satellite connections to the Internet.baseband broadband medium band voiceband6. Every computer on the Internet has a unique numeric address called a(n):IP address DNS broadcast packet7. Sometimes referred to as a LAN adapter, these expansion cards connect a computer to a network.PCMCIA NIC server VPN8. A device that allows one LAN to be linked to other LANs or to larger networks.IDS network gateway PAN switch9. Typically using Wi-Fi technology, these wireless access points are typically available from public places such as coffee shops, libraries, bookstores, colleges, and universities.hotspots extranets PANs LANs10. Star, tree, and mesh are three types of network:topologies protocols strategies devicesMultiple 101. The three primary privacy issues are accuracy, property, and:access ethics ownership security2. To easily get names, addresses, and other details about a person using only his or her telephone number, government authorities and others use a(n): adware cookie keystroke logger reverse directory worm3. Browsers store the locations of sites visited in a:history menu tool bar firewall4. The browser mode that eliminates history files and blocks most cookies.detect insert privacy sleep5. The information that people voluntarily post in social networking sites, blogs, and photo- and video-sharing sites is used to create their:access approval firewall online identity phish6. Computer criminals who specialize in stealing, trading, and using stolen credit cards over the Internet are known as: carders card scammers cyber traders identity thieves7. Programs that come into a computer system disguised as something else are called:Trojan horses viruses Web bugs zombies8. The use of the Internet, cell phones, or other devices to send or post content intended to hurt or embarrass another person is known as:cyber-bullying online harassmentsocial media discrimination unethical communication9. Special hardware and software used to con trol access to a corporation’s private network is known as a(n):antivirus program communication gatefirewall spyware removal program10. To prevent copyright violations, corporations often use:ACT DRM VPN WPAMultiple 111. People who react to technology by thinking computers are magic boxes capable of solving all kinds of problems that computers really can’t handle are: cynics frustrated na?ve proactive2. The type of person that looks at technology in a positive realistic way is:cynical proactive na?ve frustrated3. Books, journals, and trade associations are the best sources to help you:develop personal contacts develop specialtieslook for innovative opportunities maintain your computer competency 4. If your career is in marketing, it makes sense to develop a specialty in:database desktop publishingprogramming systems analysis and design5. What computer professional repairs and installs computer components and systems?computer technician data entry workerdesktop publisher software engineer6. What computer professional designs, tests, and researches encryption procedures?cryptographer network administratorprogrammer software engineer7. What computer professional uses database management software to determine the most efficient ways to organize and access data?cryptographer database administratorprogrammer software engineer8. What computer professional oversees the work of programmers, computer specialists, systems analysts, and other computer professionals?information systems manager network managersoftware engineer technical writer9. What computer professional creates, tests, and troubleshoots computer programs?network manager programmersoftware engineer technical writer10. What computer professional plans and designs information systems?network manager programmersoftware engineer systems analyst。
云计算与大数据技术-课后习题答案docx (6)[1页]
![云计算与大数据技术-课后习题答案docx (6)[1页]](https://img.taocdn.com/s3/m/02edc3eb6394dd88d0d233d4b14e852458fb396f.png)
6.11 习题答案
1.启动Hadoop集群可以使用一条命令,也可以使用两条命令,它们分别是什么?
答:使用一条命令:start-all.sh;使用两条命令:start-dfs.sh和start-yarn.sh。
2.Hadoop启动成功之后,使用jps命令,分别回答在master和slave端,至少需要看到那几个服务进程已经启动才表示Hadoop启动正确?
答:master机器上:NameNode、SecondaryNameNode、ResourceManager服务进程;slave机器上:NodeManager、DataNode服务进程。
3.试述ZooKeeper正确启动之后,可以看见的它的守护进程是什么?
答:QuorumPeerMain进程。
4.HBase启动成功之后,分别在master和slave端可见的它的守护进程是什么?
答:在hbase的主节点master机器可见HMaster、HRegionServer进程,在从节点slave上可见HRegionServer进程。
5.试叙述如果需要Hbase正常工作的话,Hbase、ZooKeeper、Hadoop三者的启动先后顺序。
答:先启动Hadoop,再启动ZooKeeper,最后启动ZooKeeper。
在前一个正确的基础上,后一个才可以正确运行。
6.试述在安装Hive之前,必须在Linux服务上事先安装什么数据库软件?
答:安装mysql数据库软件。
7.试述在安装Kafka之前,需要在Linux环境下,必须事先安装好什么软件或服务?
答:Kafka工作的时候需要jdk和zookeeper服务,所以必须事先安装。
大数据专业英语教程 Unit 10 What Is Hadoop

节点失效,节点故障;点失效 容错 作业调度 集群资源管理 分散,展开 完成,实现,执行 并行处理 按比例增加,按比例提高 说得委婉些,说得好听一点
Abbreviations
HPC (High Performance Computing) SAN (Storage Area Network) RDBMS (Relational DataBase Management System) HDFS (Hadoop Distributed File System)
New Words
ห้องสมุดไป่ตู้
restriction throughput availability localize
[] [] [❖] []
n.限制,约束 n.吞吐量,生产量,生产能力 n.可用性,有效性,实用性 v.(使)局部化,本地化
Phrases
programming language tea cozy software library Apache Software Foundation non-profit organization free,open-source software distributed system machine-generated data log data data preparation scripting language
外文文献译文(样例)

MSE协议攻击1引言2004年,CacheLogic公司(现名Velocix)根据一项六个月的调查指出,BitTorrent(以下简称BT)流量约占Internet总流量的33%[1]。
尽量各项调查得出的结论之间存在一定差异,但不可否认的是,BT的应用已经越来越广泛。
BT的大规模应用给网络性能带来了一定的负面影响。
因此,一些ISP已经开始对BT 进行限速。
为了应对这一情况,BT客户端的开发者设计了MSE协议,其主要目的是对数据流提供混淆功能,其次提供一定的保密和认证功能[2]。
BT客户端的开发者并没有基于已知的公有协议(例如IPSec),而是完全重新设计了MSE协议。
本文描述了MSE协议的大量漏洞,利用这些漏洞可以完全恢复出密钥和导致种子指纹的泄露。
我们把这种攻击应用到不同平台下的各种客户端。
结果显示,MSE协议具有大量漏洞,且协议本身有许多细节之处仍待完善。
2BitTorrent协议BitTorrent协议的设计目的是在网络上高效地传输大型文件。
当需要分发大型文件时,将之分解为文件块,并由多个节点提供下载,以减轻网络中单个节点的成本和负载。
当使用BitTorrent协议下载文件时,几乎将同时开始上传文件块。
BT网络由四个部分组成:下载者、做种者、Web服务器和Tracker服务器。
在使用BT协议共享某个文件之前,必须先创建一个种子文件。
这个种子文件包含了需要下载的共享文件中各个文件块的信息,包括Tracker信息、共享的文件块总数、所有文件块的哈希值等基本信息。
当下载完成后,可以利用这些哈希值来验证文件的完整性。
此外,文件中还包含一个用其它部分的元数据计算得到的哈希值InfoHash。
InfoHash值可以用来确定某个特定的种子文件。
除了将种子文件分发给用户下载外,还必须将文件信息报告给Tracker服务器。
Tracker服务器的工作是跟踪记录所有做种者的信息,并保持下载者之间的相互通信。
当用户使用BT协议下载文件时,首先从Web服务器上下载种子文件。
Replication Server数据复制技术及实例

: ‘
项 目所 有 的模 型文 件都 列在 Mo e x lrr 图中 , d l poe 视 E 脚 本文件 以 及命令 执行 的 结果 都列在 Mo eigOup t d l tu 视 n 图。在 编辑 器 中设 计整 个 系统模 型 ,编辑 器包含 多种 设计 工 具 ,通过托 拽 就可 以画 出 系统的 拓扑 结构 图。
— 一
动构 建 。
进行数 据分 析 的是数 据仓 库 (ev r 2I 。 s re . Q) 各个超 市的 销 3! " 发 R pi t nS ’ r 州 缘 . e l ai ov 的 c o c 售数 据在数 据库 中是 相 当繁 多的 ,但 对于 提供 决策 支持 来 说 ,只需要 分析 部分数 据就 够 了 。 构 建好 R piain S r e 系统后 , 面要开 发 它的对 e l t ev r c o 下
维普资讯
1 6毪 9Ⅲ
Vt . 6 , 1 1 NO 9 .
团图口AMIPI R日口RII AYP圃IO I( ̄ACN t OIpA W . J
技服园 术务地
技 术 服 务 园 地
连 3 载() 0
( 上接第 8 ) 期
R pi t 1Sre 数据复制技术及 实例 e l a o evr c i1
3I 协 缱 ., l 系统 的 ,
0 : ’ ‘ . :a; 。 : 一… 一 . … 蠢二 篓…
:
点 爱 兰
…
一 \ . 一 一 一
目
.
=
—
图 2 Daa aeDe eo me t ese t , tb s v lp n rp eie P x
OCP读书笔记(21) - 题库(ExamA)
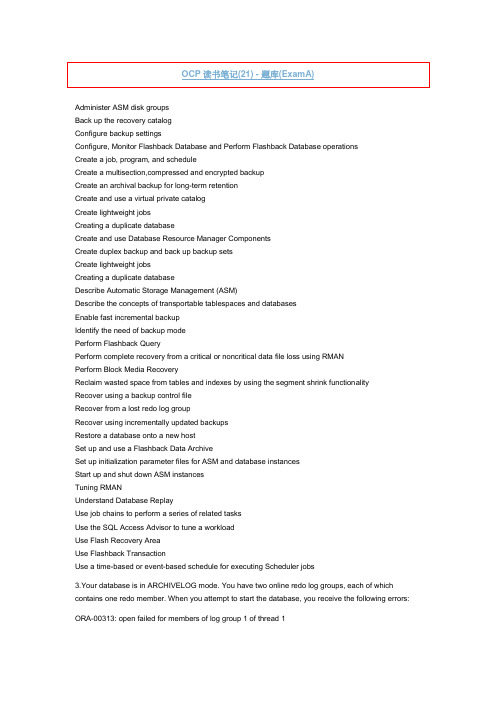
Administer ASM disk groupsBack up the recovery catalogConfigure backup settingsConfigure, Monitor Flashback Database and Perform Flashback Database operationsCreate a job, program, and scheduleCreate a multisection,compressed and encrypted backupCreate an archival backup for long-term retentionCreate and use a virtual private catalogCreate lightweight jobsCreating a duplicate databaseCreate and use Database Resource Manager ComponentsCreate duplex backup and back up backup setsCreate lightweight jobsCreating a duplicate databaseDescribe Automatic Storage Management (ASM)Describe the concepts of transportable tablespaces and databasesEnable fast incremental backupIdentify the need of backup modePerform Flashback QueryPerform complete recovery from a critical or noncritical data file loss using RMANPerform Block Media RecoveryReclaim wasted space from tables and indexes by using the segment shrink functionalityRecover using a backup control fileRecover from a lost redo log groupRecover using incrementally updated backupsRestore a database onto a new hostSet up and use a Flashback Data ArchiveSet up initialization parameter files for ASM and database instancesStart up and shut down ASM instancesTuning RMANUnderstand Database ReplayUse job chains to perform a series of related tasksUse the SQL Access Advisor to tune a workloadUse Flash Recovery AreaUse Flashback TransactionUse a time-based or event-based schedule for executing Scheduler jobs3.Your database is in ARCHIVELOG mode. You have two online redo log groups, each of which contains one redo member. When you attempt to start the database, you receive the following errors:ORA-00313: open failed for members of log group 1 of thread 1ORA-00312: online log 1 thread 1: 'D:\REDO01.LOG'You discover that the online redo log file of the current redo group is corrupted.Which statement should you use to resolve this issue?A. ALTER DATABASE DROP LOGFILE GROUP 1;B. ALTER DATABASE CLEAR LOGFILE GROUP 1;C. ALTER DATABASE CLEAR UNARCHIVED LOGFILE GROUP 1;D. ALTER DATABASE DROP LOGFILE MEMBER 'D:\REDO01.LOG';Answer: C11.View the Exhibit to examine the metrics with a threshold. Which statement is true regarding the Number of Transactions (per second) metric?A. Oracle uses statistical relevance to determine when an adaptive threshold has been breached for the metric.B. The statistics for the metric values observed over the baseline time period are not examined to determine threshold values.C. Oracle determines when an adaptive threshold has been breached based on the maximum value captured by the baseline.D. The total concurrent number of threshold violations, which must occur before an alert is raised for the metric, has been set to zero.Answer: AAdaptive thresholds enable you to monitor and detect performance issues while minimizing administrative overhead. Adaptive thresholds can automatically set warning and critical alert thresholds for some system metrics using statistics derived from metric values captured in the moving window baseline. The statistics for these thresholds are recomputed weekly and might result in new thresholds as system performance evolves over time. In addition to recalculating thresholds weekly, adaptive thresholds might compute different thresholds values for different times of the day or week based on periodic workload patterns.14.Which two statements are true regarding hot patching? (Choose two.)A. It requires relinking of the Oracle binary.B. It does not require database instance shutdown.C. It can detect conflicts between two online patches.D. It is available for installing all patches on all platforms.E. It works only in a single database instance environment.Answer: B,C15.You are in the process of creating a virtual private catalog in your Oracle Database 11g database. ThePROD1, PROD2, and PROD3 Oracle Database 10g databases are registered in the base recoverycatalog. The database user who owns the base recovery catalog is CATOWNER. CATOWNER executesthe following command to grant privileges to a new user VPC1 using Oracle Database 11g RMANexecutables:RMAN> GRANT CATALOG FOR DATABASE prod1, prod2 TO vpc1;Then you issue the following commands:RMAN> CONNECT CATALOG vpc1/oracle@catdb;RMAN> SQL "EXEC catowner.dbms_rcvcat.create_virtual_catalog;"What is the outcome of the above commands?A. They execute and create a virtual catalog for pre-Oracle 11g clients.B. They produce an error because PROD1 and PROD2 databases belong to the older version.C. They produce an error because you need to connect as CATOWNER to execute this packagedprocedure.D. They produce an error because you need to connect to the target database to execute this packaged procedure.Answer: A19.A PL/SQL procedure queries only those columns of a redefined table that were unchanged by theonline table redefinition. What happens to the PL/SQL procedure after the online table redefinition?A. It remains valid.B. It becomes invalid for all options of online table redefinition but automatically gets revalidated the nexttime it is used.C. It becomes invalid for all options of online table redefinition and is automatically recompiled duringonline redefinition of the table.D. It becomes invalid only if the storage parameters have been modified and it automatically getsrevalidated the next time it is used.Answer: A22.An index called ORD_CUSTNAME_IX has been created on the CUSTNAME column in the ORDERStable using the following command:SQL>CREATE INDEX ord_custname_ix ON orders(custname);The ORDERS table is frequently queried using the CUSTNAME column in the WHERE clause. You wantto check the impact on the performance of the queries if the index is not available. You do not want theindex to be dropped or rebuilt to perform this test.Which is the most efficient method of performing this task?A. disabling the indexB. making the index invisibleC. making the index unusableD. using the MONITORING USAGE clause for the indexAnswer: B24.Which of the following information will be gathered by the SQL Test Case Builder for the problems pertaining to SQL-related problems? (Choose all that apply.)A. ADR diagnostic filesB. all the optimizer statisticsC. initialization parameter settingsD. PL/SQL functions, procedures, and packagesE. the table and index definitions and actual dataAnswer: B,C,E答案解析:参考:/cd/E11882_01/server.112/e41573/sql_overview.htm#PFGRF16001此题答案有误,E错误,不包含actual data。
2022年考研考博-考博英语-昆明理工大学考试全真模拟易错、难点剖析AB卷(带答案)试题号:67
2022年考研考博-考博英语-昆明理工大学考试全真模拟易错、难点剖析AB卷(带答案)一.综合题(共15题)1.单选题Does using a word processor affect a writer’s style? The medium usually does do something to the message after all, even if Marshall McLuhan’s claim that the medium simply is the message has been heard and largely forgotten now. The question matters. Ray Hammond, in his excellent guide The Writer and the Word Processor, predicts that over half the professional writers in Britain and the USA will be using word processors by the end of 1985. The best-known recruit is Len Deighton, from as long ago as 1968, though most users have only started since the microcomputer boom began in 1980.Ironically word processing is in some ways psychologically more like writing in rough than typing, since it restores fluidity and provisionally to the text. The typist’s dread of having to get out the tippex, the scissors and paste, or of redoing the whole thing if he has any substantial second thoughts, can make him consistently choose the safer option in his sentences, or let something stand which he knows to be unsatisfactory or incomplete, out of weariness. In word processing the text is loosened up whilst still retaining the advantage of looking formally finished.This has, I think, two apparently contradictory effects. The initial writing can become excessively sloppy and careless, in the expectation that it will be corrected later. That crucial first inspiration is never easy to recapture, though, and therefore, on the other hand, the writing can become over-deliberated, lacking in flow and spontaneity, since revision becomes a large part of composition. However, these are faults easier to detect in others than in oneself. My own experience of the sheer difficulty of committing any words at all to the page means I’m grateful for all the help I can get.For most writers, word processing quite rapidly comes to feel like the ideal method (and can always be a second step after drafting on paper if you prefer). Most of the writers interviewed by Hammond say it has improved their style, (“immensely”,says Deighton). Seeing your own word on a screen helps you to feel cool and detached about them.Thus it is not just by freeing you from the labor of mechanical retyping that a word processor can help you to write. One author (Terence Feely) claims it has increased his output by 400%. Possibly the feeling of having a reactive machine, which appears to do things, rather than just have things done with it, accounts for this—your slave works hard and so do you.Are there no drawbacks? It costs a lot and takes time to learn—“expect to lose week s of work”,says Hammond, though days might be nearer the mark. Notoriously it is possible to lose work altogether on a word processor, and this happens to everybody at least once. The awareness that what you have written no longer exists anywhere at all, is unbelievably enraging and baffling.Will word processing generally raise the level of professional writing then? Does it make writers better as well as more productive? Though all users insist it has done so for them individually, this is hard to believe. But reliance happens fast. 1.What appears to be changing rapidly in Britain and the USA?2.Typing a manuscript in the conventional manner may make a writer().3.One effect of using a word processor may be that the ongoing revision of a text().4.It is claimed here that word processors create().5.As far as learning to use a word processor is concerned, the author of the passage feels that Hammond().问题1选项A.The style writers are employing.B.The way new writers are being recruited.C.The medium authors are using.D.The message authors are putting forward.问题2选项A.have a lot of second thoughtsB.become overcritical of his or her workC.make more mistakesD.take few risks问题3选项A.is done with too little attentionB.produces a sloppy effectC.fails to produce a fluent styleD.does not encourage one to pick up mistakes问题4选项A.a feeling of distance between a writer and his or her workB.the illusion that you are the servant of the machineC.a sensation of powerD.a reluctance in the author to express himself or herself问题5选项A.is understating the problemB.exaggerates one drawbackC.is too skeptical about the advantageD.overestimates the danger of losing text【答案】第1题:C第2题:D第3题:C第4题:A第5题:B【解析】1.细节事实题。
集美大学思科网络技术上级实验题目及答案翻译
实验1:第一章测试1 Which of the following are functions of a web browser without the addition of plug-ins? [Choose three.](cde)下列哪项是一个没有插件的web浏览器的功能?解释:连接、接触服务器,请求、接受信息a. displays Quicktime movies 显示Quicktime电影b. displays flash animation 显示flash动画c. requests information .请求信息d. contacts web servers 接触web服务器e. receives information 接收信息f. updates IRQ…s更新IRQ的2 Why were TCP/IP protocols developed?(a)为什么TCP / IP协议开发?a. To allow cooperating computers to share resources across a network 允许合作的计算机通过网络共享资源b. To insure that error correction of each packet takes place. 对每个数据包发生的误差修正。
c. To allocate resources that are needed for operating a computer on a LAN. 在局域网内分配那些需要操作的电脑的资源d. To determine the "best path" decision making when forwarding packets of data.确定“最佳路径”转发数据包时的决策3 In an 8 bit binary number, what is the total number of combinations of the eight bits?(b)在一个8位二进制数,八个比特的组合的总数吗? 解释:0(0000 0000) - 255(1111 1111)a. 255b. 256c. 512d. 128e. 254f. 10244 Which statements best describe a physical connection? [Choose two.]哪个陈述最好的形容物理连接。
TPO38托福阅读答案解析
1. According to paragraph 1, what happens to the light when a specimen is being viewed with a light microscope?A. The light continues unchanged directly into the viewer's eye or onto film.B. A glass lens bends the light to form a magnified image of the specimen.C. The light is projected onto photographic film to produce a blurred image.D. The intensity of the light increases a thousand times.Paragraph 1 is marked with ►答案:B 选项正确解析:本题根据 the light,specimen 和a light microscope 定位到第一段这几句:The first microscopes were light microscopes, which work by passing visible light through a specimen. Glass lenses in the microscope bend the light to magnify the image of the specimen and project the image into the viewer's eye or onto photographic film. 第二句讲了光学显微镜的原理,就是折射光以放大标本的图像,并且把图像投射到观察者的眼睛里或者投射到胶卷上。
选项 B 符合这句话的前半句,正确。
Google云计算中的技术
System Interactions:
Leases and Mutation Order
Leases maintain a mutation order across all chunk replicas Master grants a lease to a replica, called the primary The primary choses the serial mutation order, and all replicas follow this order Minimizes management overhead for the Master
distributed multi-server vs vs centralized? client-server?
Expensive (to have redundancy) Concurrency => Interleaving => Bugs Failures lead to incorrectness.
The Design
Cluster consists of a single master and multiple chunkservers and is accessed by multiple clients
The Master
Maintains all file system metadata.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
SearchingaTerabyteofTextUsingPartialReplicationZhihongLuKathrynS.McKinleyDepartmentofComputerScience,UniversityofMassachusetts,Amherst,MA01003zlu,mckinleycs.umass.edu
AbstractTheexplosionofcontentindistributedinformationretrieval(IR)systemsrequiresnewmecha-nismsinordertoattaintimelyandaccurateretrievalofunstructuredtext.Inthispaper,weinves-tigateusingpartialreplicationtosearchaterabyteoftextinourdistributedIRsystem.Weuseareplicaselectiondatabasetodirectqueriestorelevantreplicasthatmaintainqueryeffectiveness,butatthesametimerestrictssomesearchestoasmallpercentageofdatatoimproveperformanceandscalability,andtoreducenetworklatency.WefirstinvestigatequerylocalitywithrespecttotimeandreplicasizeusingreallogsfromTHOMASandExcite.Ourevidenceindicatesthatthereissuf-ficientquerylocalitytojustifypartialreplicationforinformationretrievalandpartialreplicationcanachievebetterperformancethancachingqueries,becausethereplicaselectionalgorithmfindssim-ilaritybetweennon-identicalqueries,andthusincreasesobservedlocality.Wethenuseavalidatedsimulatortocomparedatabasepartitioningtopartialreplicationwithloadbalancing,andfindpartialreplicationismuchmoreeffectiveatdecreasingqueryresponsetimethanpartitioning,evenwithfewerresources,anditrequiresonlymodestquerylocality.Wealsodemonstratetheaveragequeryresponsetimeunder10secondsforavarietyofworkloadswithpartialreplicationonaterabytetextdatabase.
1IntroductionAsinformationandusersproliferatethroughtheInternetandintranets,distributedinformationretrieval(IR)systemsmustcopewiththechallengesofscale.Distributingexcessiveworkloadsandsearchingaslittledataaspossiblewhilemaintainingacceptableretrievalaccuracyaretwowaystoimproveperfor-manceandscalabilityofadistributedIRsystem.Apartialreplicaofatextdatabase,whichincludes
1querylogicaswellasasubsetofthedocuments,servesthesetwopurposes.Replicatingtextdatabasesonmultipleserverscandistributeexcessiveworkloadsposedonasingleserver.Partialreplicationonserversthatareclosertotheiruserscanimproveperformancebyreducingnetworktrafficandminimiz-ingnetworklatency.Replicatingasmallpercentageofatextdatabaseanddirectingqueriestoarelevantpartialreplicafurtherimprovesperformancebysearchinglessdata.DistributeddatabasesandtheWebusecachingandreplicationtodistributeworkloadsandimprovesystemperformance[1,2,3,4,5,10,14,20,29,31,32].Bothcachingandreplication,ofcourse,requirequeryanddocumentlocality,repeatedaccesstothesamepartofthedatabase.Ourinvestiga-tionofpartialreplicationisuniquefrompreviousworkoncachingandreplicationforseveralreasons.First,structureddatabasesandwebcachinguseasimple,exacttestofsetmembershiptodetermineiftherequestedrecordordocumentmatchesthequery.Wecouldusethesameapproach;butbecauseusersdonotallthinkthesame,manydistinctqueriesreturnthesamedocumentsandthusexactmatchunnecessarilydegradeslocalityandthusperformance.Wearethefirsttodemonstratethisdegradation:upto15%onourtraces,evenwithaveryrestrictivedefinitionofquerysimilarity.WeuseserverlogsfromTHOMAS[21]andExcite[13]forourexperiments.Althoughothersreportonquerylocality[12,18],thereexitsnowidelyavailable,shared,orstandardquerysetswithlocalityproperties.Wereportthelocalitypropertiesofourtraces,andfindlocalitythatremainshigh(above20%)overtime(weeks).Theseresultssuggestwemayupdatethereplicasinfrequentlyand/oruseeventstotriggerupdates,andtheywillcontinuetosatisfymanyqueriesandimproveperformance.Tousereplicasratherthancachesandmaintainretrievaleffectiveness,aselectionfunctionmustdeterminewhetherreplicascontainall,some,ornoneoftherelevantdocumentsforaquery.Wedescribesuchafunctionelsewhere[24].Inthispaperusingahierarchyofreplicas,wereportonperformanceasafunctionoflocalityusingavalidatedsimulator[23].ThesimulatorcloselymatchesourprototypesystemthatusesInQueryforthebasicIRfunctionalityonalltextdatabases:originalandreplicated[9].Wecomparetheperformanceofsearchingaterabyteoftextusingpartialreplicationtopartitioning,andfindpartialreplicationismoreeffectiveatreducingexecutiontime,evenwithmanyfewerresources,anditrequiresonlymodestquerylocalitytoachievebetter,sometimesmuchbetter,performance.Weare
2thefirsttoreportperformanceforaterabyteoftext;whereaspreviousworkisonthescaleofgigabytes.Theremainderofthispaperisorganizedasfollows.Thenextsectionfurthercomparesourworktorelatedwork.InSection3,wecharacterizethelocalityandaccesspatternsofourtestlogsfromTHOMASandExcite.Wealsodefineournotionofquerysimilarity,andshowitincreaseslocalityupto15%.Section4describesthereplicationarchitecture.Section5reportsontheperformanceofsearch-ingaterabyteoftextusingpartialreplicationandcomparesperformancewithcollectionpartitioning.Section6summarizesourresultsandconcludes.
