计算机专业英语大作业
计算机英语作业

计算机英语作业(一)班级:2011计本班姓名:程振宁、孙嘉仪学号:01、02Lost Lessons from 8-Bit BASIC失去8-Bit BASIC的教训Unstructured programming with GOTO is the stuff of legend, as are calling subroutines by line number--GOSUB 1000--and setting global variables as a mechanism for passing parameters.作为被调用子程序的行号--GOSUB 1000--和设置全局变量的机制传递参数,非结构化编程GOTO语句可以说是传说中的东西。
The little language that fueled the home computer revolution has been long buried beneath an avalanche of derision, or at least disregarded as a relic from primitive times. That's too bad, because while the language itself has serious shortcomings, the overall 8-bit BASIC experience has high points that are worth remembering.这个小语句,推动了家用电脑已经长埋在雪崩之下的革命,或者说至少藐视了那些远古的遗物。
这一点非常不好,因为虽然语言本身存在严重缺陷,但整个8位基础的编程经验还是有很多值得我们铭记的地方。
It's hard to separate the language and the computers it ran it on; flipping the power switch, even without a disk drive attached, resulted in a BASIC prompt. If nothing else, it could be treated as a calculator:PRINT "seconds in a week: ",60*60*24*7orPRINT COS(2)/2Notice how the cosine function is always available for use. No importing a library. No qualifying it with MATH.TRIG. 我们很难将这些允许在计算机上与语言分开;打开计算机电源开关,即使没有磁盘驱动器连接,也会产生基本的提示符;如果不出意外,我们可以将它视为一个计算器:输出“一周有多少秒”,60*60*24*7或者输出 COS(2)/2注意如何余弦函数必须是可解的。
计算机英语作业一
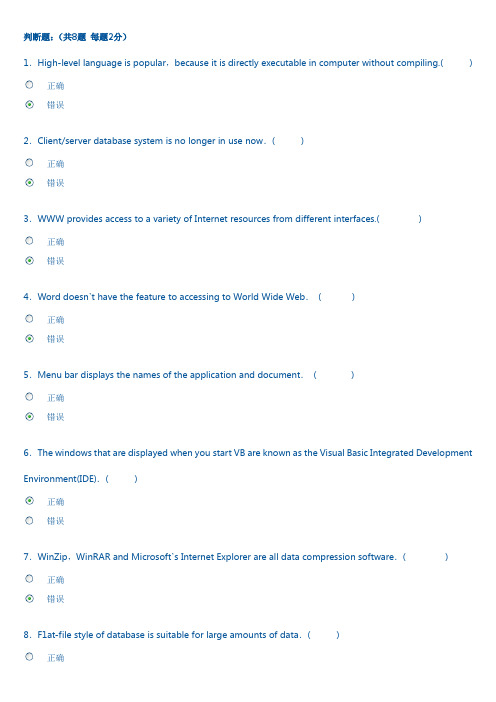
判断题:(共8题每题2分)1.High-level language is popular,because it is directly executable in computer without compiling.( )正确错误2.Client/server database system is no longer in use now.( )正确错误3.WWW provides access to a variety of Internet resources from different interfaces.( )正确错误4.Word doesn’t have the feature to accessing to World Wide Web.( )正确错误5.Menu bar displays the names of the application and document.( )正确错误6.The windows that are displayed when you start VB are known as the Visual Basic Integrated Development Environment(IDE).( )正确错误7.WinZip,WinRAR and Microsoft’s Internet Explorer are all data compression software.( )正确错误8.F1at-file style of database is suitable for large amounts of data.( )正确错误单词翻译:(共2题每题10分)1.desk publishing electronic spreadsheet hard diskdatabasecursor2.network permission computer virusemail attachment network securitysecurity patch翻译句子:(共7题每题4分)1.Information users only have to deal with one integrated environment rather than a number of separate information subsystems.信息用户只需要处理一个集成环境,而不是一系列独立的信息子系统。
计算机专业英语Unit 10范文

Unit 10 Program DesignText 1 Computer LanguagesExercises1. Choose the best answer to complete the following sentences.(1)The ( A ) is a language that was represented by long strings of ones and zeroes.A. machine languageB. high-level languageC. low-level languageD. assembly language(2)The ( D ) maps machine instructions to human-readable mnemonics.A. machine languageB. high-level languageC. low-level languageD. assembly language(3)The ( A ) turns the object file into an executable program.A. linkerB. compilerC. interpreterD. computer(4)The ( C ) is a software that translates instructions directly into actions.A. inkerB. compilerC. interpreterD. assembly language2. Fill in the blanks.(1)Computer language include machine language, assembly language and higher-levellanguages(2)Higher-level languages let people work with something approximating words andsentences.(3)Programs use "user-friendly interfaces," involving multiple windows, menus, dialogboxes.3. Translate and analyze the following sentences.(1)Compilers, however, introduce the extra steps of compiling and linking the code,which is inconvenient.句子组成:which引导的是定语从句,修饰steps翻译:但是编译程序却增加了一些额外的步骤来编译和链接代码,相比之下则不方便。
计算机专业英语Unit-9

Unit 9 Computer VirusText 1 Virus IntroductionExercises1. Multiple choices.(1) A virus is a ( A ).A. programB. computerC. bad manD. beast(2) A virus is a program that reproduces its own code by ( ABC ).A. adding to the end of a fileB. inserting into the middle of a fileC. simply placing a pointerD. replacing another program(3)( AD )is a type of executable file .A. COM fileB. TXT fileC. JPG fileD. EXE file(4)Similar to viruses, you can also find malicious code in ( ABC ).A. Trojan HorsesB. wormsC. logic bombsD. Microsoft Word Documents2. Fill in the blanks.(1) A virus is a program that reproduces its own code by attaching itself to otherexecutable files in such a way that the virus code is executed when the infectedexecutable file is executed .(2)To attach might mean physically adding to the end of a file, inserting into the middle ofa file, or simply placing a pointer to a different location on the disk somewhere wherethe virus can find it.(3)Similar to viruses, you can also find malicious code in Trojan Horses, worms, andlogic bombs.3. Translate and analyze the following sentences.(1)These self-replicating codes, when caused by some event, may do a potentially harmfula ct to your computer.句子组成:when引导时间状语从句做插入语,当…的时候.翻译:当这些自复制代码被一些事件触发时,或许会做出一些对你的电脑有潜在危害的行为.(2)M ore recently, scripts written for Internet web sites and/or included in E-mail can alsob e executed and infected.句子组成:scripts written…省略的定语从句完整形式scripts which were writtened….翻译:现在,为网站编写的或者包括在E-mail中的脚本也能够被执行和感染。
计算机专业英语参考答案Unit (6)[3页]
![计算机专业英语参考答案Unit (6)[3页]](https://img.taocdn.com/s3/m/e0df89bfe518964bce847c35.png)
Unit Six VirusSection Two Real World1. F2. G3. I4. J5. H6. A7. B8. E9. C 10. DFind InformationTask I.1.Her computer crashed.2.It might have been infected with a virus.3.No, it shouldn’t.4.Because E-mails are not system files.5.To try some anti-virus software like Kaspersky.Task II. 1. T 2. F 3. F 4. T 5. TWords BuildingTask I. 1. A 2. B 3. A 4. B 5. DTask II. 1. attachment 2. infection 3. container 4. exact 5. Essentially Task III. 1. B 2. G 3. A 4. H 5. F 6. C 7. I 8. J 9. D 10. ECheer up Your EarsTask I. 1. crashed 2. infected 3. spread 4. essential 5. at once6. executable7. exactly8. system9. contain 10. anti-virusTask II. 1. in a mess 2. sorry to say 3. latest type 4. check 5. at your service Task III. 1. C 2. B 3. D 4. A 5. DTable Talk1. take a look at2. give me a second3. infected files4. have no idea5. make sureSection Three Brighten Your Eyes病毒对计算机系统的影响正如我们现在所知,计算机病毒起源于1986年第一个个人电脑病毒Brain的产生。
20秋大工《专业英语(计算机英语)》在线作业2答案

1.Click the open folder button to open an existing workbook.()A.正确B.错误答案:A2.Click the Print button to print the workbook.()A.正确B.错误答案:Be the spell checker to correct spelling errors on the worksheet.()A.正确B.错误答案:A4.Click the backward Undo arrow to cancel the first action you performed.()A.正确B.错误答案:B5.The short for MIS is management information system.()A.正确B.错误答案:A6.A network interface on each computer, usually called a network interface card(NIC) or adapter.()A.正确B.错误答案:A7.FTP performs basic interactive file transfers between hosts.()A.正确B.错误答案:A8.Telnet enables users to cute terminal sessions with local hosts.()A.正确B.错误答案:B9.Most networks-even those with just two computers also contain a hub or switch to act as a connection point between the computers.()A.正确B.错误答案:A10.A VPN offers the security and full data access of a private WAN, but because it runs over the Internet, it is more affordable and complex.()A.正确B.错误答案:A11.Microsoft Office 2000 includes Word, _____, Outlook and FrontPage.A.ExcelB.Power PointC.AccessD.All of the above答案:D12.ERP is _____.A.Enterprise resource planning softwareB.Enterprise Application IntegrationC.Electronic Application IntegrationD.None of the above.答案:A13._____ is an operating system similar to Unix.A.Windows NTB.MS-DOSC.OS/2D.Linux答案:D14.A backup program _____.A.makes a copy of files you selectB.returns you to the previous programC.undoes the last change you madeD.None of the above答案:A15.TCP/IP refers to a suite of _____.A.systemB.control unitsC.application programsD.data communication protocols答案:D16.TCP/IP application layer protocols include the following except _____.A.HTTPB.FTPC.UDPD.Telnet答案:C17._____ provides reliable, full-duplex connections and reliable service by ensuring that data is resubmitted when transmission results in an error.A.TCPB.ARPC.UDPD.IP答案:A18._____ layer just above the internet layer.work InterfaceB.TCPC.Host-to-Host TransportD.Application答案:C19._____ are collections of two or more connected computers.A.VPNB.ModemworksD.Cable答案:C20.We abbreviate Virtual Private Networks to _____.A.NICB.VPNC.HUBD.MODEM答案:B。
计算机专业英语作业
度秘D rgree of the serect(English name: duer) is baidu world conference in 2015, new toprovide users with assistant secretary of search service robot. It on a broad index of the real world, on the basis of service and information, relying on strong baidu search and intelligent interactive technology, by using machine learning and artificial intelligence instead of people's behavior, degree of secret as full-time secretary, to provide users with a variety of quality services. Everyone can have intimate secretary is the secret of the dream. Every one of us, whether it's a grader, or aged and old people, can through the secret equally enjoy Internet service, find desires.译文:度秘(英文名:duer):是百度在2015年世界大会上全新推出的,为用户提供秘书化搜索服务的机器人助理。
它在广泛索引真实世界的服务和信息的基础上,依托百度强大的搜索及智能交互技术,通过人工智能用机器不断学习和替代人的行为,度秘媲美专职秘书,为用户提供各种优质服务。
计算机专业英语练习1
一般概念名词前的the在描述一般类型事物的名词,而不是该事物的特例前面用the:Many people are worried about the bad effects of mobiles on the brain.These are problems for students living away from the family.We don’t know the effects of such chemicals on the body.The role of the student at university level varies greatly from country to country.Most of our business is carried out over the telephone.The也用在描述形势、质量、过程或变化的抽象名词前面。
这些名词后面经常跟of something: There is a problem with the availability of clean water in some villages.The distribution of income is uneven in most countries.On the whole, the standard of living is better in urban areas.Many residents complained about the frequency of bus services.This advance was brought about by the development of antibiotics.He made a number of recommendations for the improvement of staff training.Doctors always stress the importance of a balanced diet.注意:the development/improvement of something描述的是一般的变化过程,而developments/improvements in something描述的是特定的变化:We try to keep up-to-date with new developments in information technology.名词短语前的a/an在形容词+单数名词而构成的短语前面要加a/an:He clearly has a good understanding of the issues.Many students have a part-time job while studying.The company has captured a significant share of the market.注意下列短语中副词(very, really, quite等)的位置:We have a very high percentage of women working in senior government posts.There was a really good atmosphere.In my view, this is quite a strong argument.注意以下普通名词短语:●to a certain extent/degree: I agree with you to a certain degree.I think they are also right to a certain extent.● a wide range/variety: We have a wide range of books to choose from.●a(n) large/small/equal number/amount:an equal number of men and women.● a high/large/small/greater proportion/percentage:a small proportion of patients.● a long time: I haven’t seen her for a long time.1.下列句子是正确的还是错误的?请改正其中有错误的句子。
计算机专业英语的作文模板
计算机专业英语的作文模板Title: Computer Science English Writing Template。
Introduction。
Computer science is a rapidly growing field that encompasses a wide range of topics, including software development, hardware design, networking, and artificial intelligence. As a computer science student, it is essential to be able to effectively communicate in English, as it is the lingua franca of the technology industry. In this article, we will provide a comprehensive template for writing essays and reports in computer science English.I. Introduction。
The introduction is the first part of your essay or report and should provide an overview of the topic you will be discussing. In computer science, this could include a brief history of the technology or an explanation of the problem you will be addressing. It should also include a thesis statement that outlines the main argument or purpose of your writing.II. Background。
专业计算机英文作文
专业计算机英文作文Title: The Evolution of Computer Science: A Journey through Time。
Introduction。
Computer science, as a discipline, has undergone a remarkable evolution over the decades. From its humble beginnings as a theoretical concept to its current status as a cornerstone of modern society, the field has continuously adapted and expanded. In this essay, we will explore the key milestones and transformations that have shaped the landscape of computer science.Early Foundations。
The roots of computer science can be traced back to the mid-20th century, with the development of the first electronic computers. Pioneering figures like Alan Turing and John von Neumann laid the groundwork for moderncomputing with their theoretical models of computation and architecture. These early efforts paved the way for the construction of the ENIAC, the world's first programmable electronic computer, in the 1940s.The Digital Revolution。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
网址一:/hub/save-computer-from-Hackers网址二:/hub/What-is-Phishing姓名:**学号:************分校:通州(一)原文1.What is Computer Hacking?Computer hacking is a malicious act, so it is important for your computer and data to protect from Hacking. Computer Hacking refers to the process of making malicious modifications to a software or hardware to accomplish an aim outside the original creator's objective. Hackers are usually expert programmers who usually see hacking as a real life application of their skills.Hacking has become a nuisance in recent times and the protection from hacking has become more complex. Infact, the hackers have become so good that even the software giants are feeling a headache. Nintendo recently reported a loss of $975 million due to privacy and Microsoft has lost an estimated $900 million in five years.Well, the Giants are not the only targets of these hackers, even common individuals are not safe. The dangers range from little thefts to sponsored terrorism. These include stealing personal information and spying your activities. They can get to your secrets and destroy your credit. The dangers are possibly endless.How to protect from HackingPrevention is Better Than Cure. The problem of computer hacking has become really serious. But there are some basic methods which are usually the best to guarantee a Hacker-free system. Here, I am going to introduce some basic tips to save your computer and data from hackers.Using Antivirus SoftwareAntivirus software are one of the basic tools for your data and computer to protect from hacking. Antivirus software act as a protecting net that catches any potential threat before it reaches your system. They can prevent unauthorized access to your computer, protects your system from viruses and cloaks your data ports from intruders searching for any opening. The dangers range from little thefts to sponsored terrorism. These include stealing personal information and spying your activities.Nowadays anti virus software are completely automated. Go for the best when choosing anti virus software and make sure that you scan your system for viruses atleast once a week. Norton antivirus from Symantecis one of the leading products in the industry. Avastis another great antivirus tool to protect from hacking.Using FirewallWhat is a Firewall?A firewall is a set of programs located at the network gateway server which protects a private network from unauthorized access from other networks. The term firewall is originally referred to a wall intended to confine a fire.A firewall protects your computer from offensive websites and potential hackers. It keeps your data and information safe from unwanted intruders. Firewalls are designed to prevent unauthorized access to your network, much like a locked door.Thus firewall is a vital tool for your strategy against hackers so don't forget to set up one for your system. Microsoft has a built-in firewall software but you can also try the Symantec firewall.Using Anti Spyware SoftwareWhat is a Spyware?A spyware is a self installing software which secretly gathers information about a person's computing activities such as surfing habits and viewed sites. Spywares are truly a hacker's tool, not only collecting personal information but also interfering with user control by installing additional software and redirecting web browsers.Anti spyware software are designed to save your computer from hackers. They not only protect your computer by detection and removal of spywares but also preventing automatic installation of these malicious programs. Spysweeperis a great anti spyware software to guarantee a spyware free computer.Email SecurityEmail is one of the leading hacker's tools. Hackers use emails to transmit malicious software to your computer. Emails are usually very cheap which gives the hackers loads of opportunities. One of the basic tips to prevent hacking is to be extra careful with emails. The most important tip is that you should never hand out your real email address to a stranger. Never open an email arriving from an unknown source and never try to open an attachment with an email if you don't know the sender. Aviraantivirus is a useful tool to filter your emails for potential threats as well as provide premium protection for your computer.Software updatesHackers are always searching for security gaps in your system. Anti virus and anti spyware software usually lose their effectiveness with time as new and more advanced malicious programs are created by hackers.Its important to go for the latest security software in the market to guaranteemaximum security from threats. Make sure you frequently check out for software updates or set your software to update automatically.Internet SecurityBeing extra careful while surfing is the best way to protect your computer from hackers. Simple precautions can mean the difference between a secure and vulnerable system. A great way to save yourself from hackers is to avoid visiting hacker controlled sites usually committed to porn, free downloads and online gaming. Also be extra careful while downloading something from an unknown source. Never ignore a security warning about a site. Its better to be safe than sorry.Educate YourselfWhen working for an offensive against hackers, the most important step is to educate yourself. Hacking is a dynamic topic with developments arising every moment. Hackers are intelligent and innovative and you should be prepared for it.Computers are vulnerable. No matter what you do, its impossible to be 100% save. Important data like personal detail and credit card information should never be saved directly on a computer. A password protector is a great way to protect this data.Another great way to secure your computer is to use a password on your computer. Well, it can't really save you if your computer gets stolen (in case of a laptop) but can save you from unauthorized people who can reach to your computer.Windows updateMicrosoft Windows is the best OS which comes with almost all the tools to protect you and your computer from hacking. To make the most of this, it is important to keep your windows updated. An easy way to do this is by checking for updates at Microsoft Windows Update. You can also set your windows security software to check for updates automatically so you don't miss anything. ...2. What is a Phishing Attack?Identity theft has become the new white collar crime and it has grown tremendously. Criminals that steal identities use them in a number of ways. One of the most common tricks is to use a stolen identity to open a line of credit. The line of credit is then depleted by the thief and the actual person receives the bill. Identities are also stolen for malicious intent, such as stealing a military officer’s email credentials in hopes of carrying out fictitious orders to troops.Phishing is a relatively new term to describe ploys used by criminals trying to steal identities. Phishing scams are on the rise:"During 2004, close to 2 million U. S. citizens had their checking accounts raided by cyber-criminals. With the average reported loss per incident estimated at $1200, total losses were close to $2 billion. The incidence of phishing e-mails―e-mails thatattempt to steal a consumer’s user name and password by imitating e-mail from a legitimate financial institution –has risen 4,000 percent over the past six months."•What is Phishing VideoThe term “phishing” is based on the term “fishing”. With fishing you bait a hook and try to catch fish. If you do not receive a bite, you often change the type of bait until you start catching fish. With phishing, the bait is typically an email that appears legitimate. The email typically asks for a bank customer to validate their information, however, the email redirects the customer to a fictitious bank site made to look like the legitimate bank site (James, 2005). The criminals hope the customer will not notice the redirected bank site is fictitious and that they will validate their account information. There are numerous phishing emails used as bait and criminals hope the more bait they use, the greater chances someone will fall for the scam.The key to preventing identity theft is awareness. Financial institutions typically do not ask for account information validation. Any emails that ask for account validation or social security numbers, should be validated. The link contained within the email can be checked for legitimacy. These links often go to bogus sites that can easily be determined by the website link. For example, if you bank at and you receive an email that has a link and takes you to .customer.cz, this should raise suspicion. Phishing scams not only use email, but the telephone is also used. A typical scam involves a telephone call with someone impersonating your credit card company and asking you to validate your social security number, date of birth, etc. Credit card companies already have this information and do not need you to validate it. A simple line of defense is to ask the caller for the credit card company’s number and call them back。
