An Overlay Network for Monitoring Activities of Computer Viruses
蓝牙室内定位服务的营销指南说明书

The Marketer’s Guide to Bluetooth® LE Indoor Location ServicesCREATING AMAZING ONSITE MOBILE EXPERIENCES WITH VIRTUAL BEACONSThe Marketer’s Guide to Bluetooth® LEIndoor Location ServicesCREATING AMAZING ONSITE MOBILE EXPERIENCES WITH VIRTUAL BEACONSLocation-based mobile marketing is a boon to every marketer tasked with delivering the right message to the right person at the right time. After all, there’s no better time to reach prospective customers than when they are nearby. And there’s no better way to provide personalized, targeted information than by combining what you already know about them with their current location inside your establishment.Most people are aware of the Global Positioning System (GPS), which is the defacto standard for location-based interaction when outdoors. It uses geofencing technology to trigger activities, such as push notifications, when a mobile device enters or leaves a virtual geographic boundary. However, GPS does not work when it comes to indoor location services. That is why a new technology, Bluetooth® Low Energy (BLE), has emerged to identify and engage with mobile employees, customers, and guests inside hotels, stores, convention centers, hospitals, and other establishments.If you’re reading this guide, chances are you’ve heard about Bluetooth® LE. Perhaps you’ve experimented with battery-powered BLE beacons, but struggled with the complexity of creating a complete solution from the disparate parts of different vendors. Maybe you ran a successful pilot, but when it came time to scale, your IT department said it would be too complicated and costly to manage.If so, you’re not alone. While indoor location using Bluetooth® LE has been around since Apple’s introduction of the iBeacon protocol in 2013, challenges with scalability, interoperability, and manageability have hampered large-scale adoption of this technology to date. Fortunately, this is all changing.New advancements in the wireless infrastructure, such as virtual beacons enabled by machine learning, have made Bluetooth®LE easy to deploy and operate at scale. In addition, the convergence of Wi-Fi and BLE has removed the need for an overlay network, making it more cost effective than ever to roll out indoor location services.We are in a new era of enterprise-grade, personalized, indoor-location services using BLE. Are you ready to take advantage of it? This paper will show you how.What you’ll learn:• Bluetooth® LE basics and common beaconing standards• T op use cases for BLE (e.g. analytics, wayfinding, proximity messaging and more)• Overcoming BLE deployment and management challenges• The Mist solution for BLE engagement• Getting startedTHE ABCS OF BLUETOOTH® LEBluetooth® is the ubiquitous communications technology we all use to connect our wireless headsets, keyboards, and hands-free systems to our smart phones and computers. Operating in the 2.4GHz band (the same as Wi-Fi), Bluetooth was designed for continuous streaming of voice and data over short distances, and comes standard in all modern mobile devices.Bluetooth® Low Energy (BLE) is a subset of the Bluetooth protocol introduced in 2011. Unlike classic Bluetooth’s continuous streaming, BLE was designed for transmitting short bursts of data. Because it stays in sleep mode until a connection is initiated, BLE consumes far less energy thanclassic Bluetooth. This energy efficiency is driving a new class of wireless devices and applications, from smart home sensors and wearables like Fitbits, to indoor-location beacons and proximity marketing.Beacons are devices that use Bluetooth ® LE to transmit short packetsthat are used for providing location-based information, such as proximitynotifications, location, and nearby items of interest. They can be usedfor anything from analyzing customer traffic patterns to providing turn-by-turn directions and delivering offers or other contextual informationbased on physical location. You can even turn your mobile phone into aBLE beacon for use cases such as letting the server in a restaurant knowyou would like another drink. There are two main protocols used for Bluetooth ® LE beaconing: iBeacon, introduced by Apple in 2013, and Eddystone, Google’s cross platform beaconing protocol that was launched in 2015. Both protocols work in a similar fashion by broadcasting a unique identifier that is picked up by a compatible app or operating system on the phone or other mobile devices, to determine its relative position at your location. (A third protocol, Altbeacon, was announced in July 2014 as an open source beacon protocol. It overcomes vendor tie-in, but lacks the widespread adoption of iBeacon and Eddystone.)It is worth pointing out that Bluetooth ® LE beacons are an opt-in solution. Mobile consumers grant permission to use their location information in exchange for content or services they consider valuable. Mobile devices must have Bluetooth ® and location services on, and either a mobile app configured for BLE, or Google Chrome installed (if you’re beacon is configured with Eddystone-URL). BLUETOOTH ®LE BEACON USE CASES ARE LIMITED ONLY BY YOUR IMAGINATION The more you integrate a mobile user’ location data with everything else you know about the user, the more personalized, valuable, and amazing the experience. With Bluetooth ® LE (BLE) now standard in all modern mobile devices (and expected to be in 90% of all devices by 2018), and more people enabling Bluetooth (required to pick up beacon signals) to communicate with their wireless peripherals, BLE beaconing is quickly moving from a nice-to-have to a must-have marketing technology in 2017.-- Boston Retail Partners surveyCompanies of all sizes are using BLE technology to gain tremendous insight into employee, customer, and guest behavior, and to offer helpful, convenient, and incredibly personalized new services. Here are just some of the use cases that are enabled with BLE indoor location services:Analytics – Gather zone-based user analytics, such as the average number of people in your establishment, the number of passersby, or the length of time each person spends at a particular display, area or department. Look at traffic patterns by time of day, day of week, or by season. Integrate with other data such as weather feeds and customer relationship management (CRM) to gain even greater insights.Wayfinding (Indoor Navigation) – A GPS-like navigation experience for indoor environments. Wayfinding typically offers turn-by-turn directions and a map showing the user moving toward his or her destination. Ideal for airports, hotels, casinos, tradeshows, events, malls, or any other large venue.Mobile DeviceBLE Tag Access PointPush Promotions – Consumers receive personalized notifications or offerson their smartphone, based on their proximity to a specific object—a storein a mall, or an aisle, product or brand once inside. Integrate with othercustomer data to deliver ever more personalized and relevant messages:Direct customers to a product they recently researched online, or promotea concert at a baseball game to a fan that follows the band.Proximity Messaging – Not all messages need be promotional. Providinghelpful information or additional content helps increase brand loyalty.Greet customers by name as they walk through the door. Provide specialoffers to premium guests. Offer customized information to museumpatrons or trade show guests as they approach a specific display or booth.Notify shoppers when their in-store purchases are ready for pickup.Personalized Experiences – Beacons coupled with other technology,such as RFID tags and digital signage, take personalization from theuser’s phone to the surrounding physical environment. Customers canbe greeted by name when they reach a specific display. Screens coulddisplay specific products of interest based on past purchases or even bythe products currently in their shopping carts. Even prices on digital tagscould change based on that customer’s loyalty points or stored coupons.Hyperlocal Check-in – Unlike Facebook or Foursquare, highly targeted check-ins enable consumers to tell you exactly where they are in your facility. This feature could be used in conjunction with specific location-based promotions or reward-based games, like a scavenger hunt.Employee Assistance – Find the closest sales associate for product inquiries or rapid checkout. Or enable your customers to direct an employee straight to them with the tap of a finger.Retargeting Ads – T argeting people who visit your website with ads on Facebook, Twitter and other sites that use retargeting is a powerfully cost-effective way to reserve your ad spend on people who have already indicated an interest in your business. Now imagine being able to do the same for people who walk into your store or other physical place of business.Virtual Concierges – Guests in a restaurant, mall, fitness club or other establishment can use their phones to order food and other services, which can be delivered right to their exact location.Asset Tracking – Is another popular use case for Bluetooth® LE beacons. Instead of broadcasting its ID to mobile devices, the beacon “listens” for the unique IDs of BLE tags attached to objects. Because these tags can be equipped with sensors—for things such as light, sound, movement and temperature—the applications are many, from tracking of wheelchairs and infusion pumps in a hospital, to monitoring the movement, speed and vibration of an airport baggage conveyor.Creative marketers in every industry are already dreaming up ways to leverage asset tracking to generate more revenue streams and increase productivity.BLE Engagement WayfindingProximity Messaging Real-time Location AnalyticsTRADITIONAL BLUETOOTH® LE DEPLOYMENT AND MANAGEMENT CHALLENGESWhile the use cases for Bluetooth® LE are compelling, historically it has been a challenge to deploy and operate large BLE networks in a cost-effective way. That is because the beaconing technology to date has required battery powered devices (i.e. transmitters), which create the following challenges:•Comprehensive site surveys are required to arrange and calibrate beacons for optimum performance and accuracy in a given environment.Want to move or add more beacons? Another site survey and recalibration is required. Because RF signals can be impacted by physical changes in the environment—such as new product displays, moved furniture, or even large influxes of people—the system will be plagued by poor performance until the beacons can be recalibrated. What retail store or event venue doesn’t change on a regular basis? Who has an IT staff capable of dealing with dynamic daily changes, like large groups of people, on demand?•High deployment costs. Many of the use cases above require alocation system with granular micro-location to deliver one to threemeter accuracy. This would requires thousands of beacons in a singlelocation, which creates substantial cost barriers.•Battery maintenance is problematic- While battery life has improved, alarge enterprise may deploy tens of thousands of beacons, distributedacross the globe. Locating and replacing dead batteries can be aweekly occurrence. The more you beacon to get accurate and timelylocation information, the faster you’ll be replacing batteries.I’m a battery-powered Beacon •Lack of enterprise-grade management means costly truck rollsand time-consuming manual processes. Physical beacons lack IPaddresses. As such, they can’t be identified by the network and bemanaged remotely by IT.•Aesthetics. Battery powered beacons are glued to the wall, often 25 feet apart. This can adversely impact the appearance of a location, which is often a nonstarter in hotels, museums, and other locations where aesthetics is important.•Risk of theft. Battery powered beacons can be stolen or knocked off the wall, creating additional management headaches.All told, a large enterprise can expect to pay approximately $300 per beacon in maintenance costs. Even if your use cases warranted the high cost, there is still the issue of inconsistent user experiences to consider. Differences in mobile device types (chipsets, OS, antenna, etc.), and dynamic changes to the RF environment—like that large influx of people-- can dramatically affect accuracy and user experience. Manual site surveys and RF calibrations simply cannot keep up.MIST VIRTUALIZES INDOOR LOCATIONFor indoor location services to truly take off, companies require BLE deployments that integrate with their existing networks, scale to handle millions of mobile devices, and automatically recalibrate for different device types and dynamic changes to the environment in real time.Fortunately, new solutions like the Mist Learning WLAN integrate BLE with Wi-Fi in a single A.I.-driven platform that is operated via the cloud.Unlike other WLANs that just integrate a single BLE beacon in anAccess Point and/or make it possible to monitor battery beacons viaa centralized management tool, Mist completely virtualizes the indoorlocation experience for maximum scale, performance, ease of use,and cost effectiveness. Here are the unique components of the Mistsolution:Access Points with directional BLE antenna array. The first step in a Bluetooth ® LE location service is to blanket the room with BLE signals. Rather than use physical beacons, Mist achieves this with a patented 16 element directional antenna array in Mist Access Points, which sends unique RF energy in multiple different directions. With BLE signals emanating from the AP, Mist eliminates the need for battery powered BLE beacons and lets mobile devices interact with an entire room instead of a single transmitter.Machine learning in the cloud. An iPhone 6s operate s very differentlythan an iPhone 5s or Samsung Galaxy on a wireless network. But knowingthat doesn’t make it any easier to recalibrate for every situation. T oaddress this, the Mist platform uses artificial intelligence to account fordifferences in devices, as well as constant changes to the RF environment—such as moving a chair, or adding a partition. It continuously takeslocation estimates from every-day use, examines them, detects the RFcharacteristics based on the actual input, and adapts the location formulato maximize accuracy.Machine learning operates across different end user device types,constructing specifically tailored path loss formulas. This is naturallynecessary as different devices have different RF characteristics. Bycontinuously and automatically adapting to different devices and changingRF environments, new Mist WLAN systems obviate the need for manualcalibration in BLE environments.Virtual Beacons. As mentioned above, Mist eliminates the need forbattery powered beacons by moving the Bluetooth ® LE beaconingfunctionality into the AP and using machine learning in the cloud. T oenable location-specific messages, Mist patented a new concept knownas virtual beacons. Virtual beacons use geofencing technology to allowspecific messages to be displayed anywhere on a floor plan (like GPS usesoutdoors). The message, range and location is completely configurableusing software – i.e. the Mist UI or APIs. With Mist, an unlimited numberof virtual beacons can be deployed in any physical environment, providingunsurpassed scalability and ease of use.The above technologies enable Mist to deliver 1-3m location accuracy with sub-second latency, making it ideal for all the use cases mentioned above. By integrating this functionality into an enterprise-grade WLAN platform, you save time and money on deployment and operations while ensuring maximum scalability and reliability.Machine Learning in the Cloud Patented Virtual BeaconsHOW TO START YOUR OWN INDOOR LOCATION JOURNEYNow that you understand the basics of Bluetooth ® LE and how to deploy a scalable solution, here is what you need to get started with indoor location services:A Bluetooth ® LE-enabled mobile appA mobile app with a compelling user experience is essential for a successful proof of concept. Y ou can start with a simple navigation or wayfinding app, or any number of readily available third-party apps designed specifically for your industry. If you have your own branded app, your beacon platform provider can supply your developers with the software developerkit (SDK) they’ll need to BLE-enable your app. You can also find expertBLE app development partners to help you customize your app or build one from the ground up.Indoor MapA digital map of your facility or campus is required for navigation andproximity marketing. Your POC use case will help you determine howextensive your initial indoor map needs to be. But you should alsoconsider what will be required and who will maintain your maps longterm. Indoor mapping and navigation vendors catering to a variety ofindustries can be found in the Mist BLE Alliance.Bluetooth ® LE beacon infrastructure and analyticsBeacons and accompanying software services are required for blue dotlocation and analytics. A few battery beacons are all you need to testpilot your application. However, we recommend you engage early withyour IT department, and an enterprise-grade BLE/Wi-Fi provider toensure your solution can scale.Management platformMost battery beacons are managed with a mobile app. When moving from POC to full-scale deployment, you may want to consider an enterprise-grade management system with machine learning and virtual beacon capabilities to avoid expensive overlay network management and unsatisfactory user experiences.YOUR CEO WILL THANK YOUThe wireless world is at a tipping point where every smartphone, tablet and laptop has BLE, making these devices ready for new indoor location-based services.Thanks to new modern wireless platforms with enterprise-grade BLE access points, machine learning in the cloud, and virtual beacon technology, the infrastructure is now ready to support the demand.The use cases for BLE are endless. Are you ready to take advantage of the enormous opportunity? Mist can help you with all the elements needed to deliver a great BLE user experience. Email *************and we will get you started.Mist Case Study。
VMware网络操作手册说明书

DatasheetAccelerate application security and networking across private, public and hybrid cloudsToday’s tools for monitoring the dataflow for optimum east-west traffic can be challenging and time-consuming because they involve manual processes. Niche and legacy network management tools do not provide converged visibility across virtual and physical networks to optimize performance. Customers need a simple, easy-to-use, end-to-end management tool to troubleshoot and get best practices compliance for VMware NSX ®, VMware SD-WAN ™, and VMware Cloud ™ deployments.VMware Aria Operations ™ for Networks (formerly VMware vRealize ® Network Insight ™) integrates with many vendors and can help provide end-to-end visibility with both physical and virtual infrastructure with a comprehensive flow assessment. This provides visibility for modeling security and firewall rules, and viewing that network segmentation is working by monitoring compliance postures over time. In addition, VMware Aria Operations for Networks can help you improve performance and availability with converged visibility across physical and virtual networks. You can also simplify NSX operations management with an intuitive UI and natural language search to quickly pinpoint issues and troubleshoot, as well as get best practices deployment and compliance recommendations.VMware Aria Operations for Networks Assurance and Verification enables formal verification by using a unified mathematical model of how the network functions. This improves network performance with more proactive monitoring capabilities in comparison to typical reactive network monitoring. Business intent checks enable better network planning and troubleshooting, which result in the assurance of better uptime and network resiliency.VMware Aria Operations for Networks Universal is available as an on-premises deployment or as a federated cloud software-as-a-service (SaaS) offering.At a glanceVMware Aria Operations for Networks delivers intelligent operations for software-defined networking and security. VMware Aria Operations for Networks consists of both SaaS and on-premises solutions. These offerings help customers build an optimized, highly available and secure network infrastructure across multi-cloud environments. They accelerate application discovery, migration, network segmentation planning and deployment; enable visibility across virtual and physical networks; and provide operational views to manage and scale VMware NSX, VMware Cloud on AWS, VMware SD-WAN, VMware NSX Advanced Load Balancer ™, VMware HCX®, and many other deployments.VMware Aria Operations for NetworksOn-premises, SaaS, and federated SaaS offeringsFigure 1: VMware Aria Operations for Networks provides security planning and network visibility across the virtual cloud network.Use casesNetworking• Gain unified visibility across hybrid and multi-cloud environments• Gain visibility for NSX, VMware SD-WAN, VMware HCX, Kubernetes, VMware Cloud on AWS, Amazon Web Services (AWS), Microsoft Azure, Azure VMware Solution, Google Cloud VMware Engine, Oracle Cloud VMware Solution, and VMware Cloud on Dell• Gain visibility between overlay and underlay networks • Enable end-to-end troubleshooting, traffic and path analytics • Enable network assurance and verification• Utilize guided network troubleshooting for intuitive root-cause analysisApplications• Enable application discovery and plan application migrations • Measure application latency and performance• Reduce mean time to repair (MTTR) for application connectivity issues • Optimize application performance by eliminating network bottlenecks • Analyze traffic and apps across hybrid cloud and multi-cloudSecurity• Plan app security and cloud migration• Plan security; recommend firewall policies and network segmentation apps • Troubleshoot security for hybrid applications and designated crown jewels across virtual machines (VMs), containers and clouds • Map dependencies to reduce risk during app migrationKey benefits• Accelerate network segmentationplanning and deployment with VMware Aria Operations for Networks working together with NSX Intelligence ™• Audit changes to the security posture and ensure compliance• Troubleshoot quickly across virtual and physical network and security infrastructure• Manage and scale NSX deployments with confidence• Manage network and security across private clouds, public clouds and SD-WAN consistently• Reduce business risk by mapping application dependencies during application migration planning • Accelerate performance of your business-critical applications by optimizing your network and eliminating bottlenecks• Operationalize Kubernetes and troubleshoot connectivity issues between containerized workloadsVMware Aria Operations for Networks for VMware SD-WAN• End-to-end visibility of VMware SD-WAN connectivity to the cloud and the data center• Flow and traffic analysis of applications and business services used by edge sites• Site-/branch-level visibility and troubleshooting of connectivity to apps and the data center• Licensing for the VMware Aria Operations for Networks add-on for VMware SD-WAN is based on edges, VMware SD-WAN bandwidth, and term length • When used to monitor the data center, VMware Aria Operations for Networks for VMware SD-WAN requires either VMware Aria Operations for Networks Universal, the SaaS version of VMware Aria Operations for Networks, or VMware Aria Operations for Networks EnterpriseVMware Aria Operations for Networks Assurance and VerificationFor each license purchased, the software will allow monitoring of one network device. The term network device refers to routers, switches, firewalls and load balancers that are not processor or CPU based.Support and professional servicesVMware offers global support and subscription (SnS) services to all VMware Aria Operations for Networks customers. For customers requiring additional services, VMware also offers professional services engagements on bestpractices and getting started with your deployment, both directly and through an extensive network of certified professionals: /services .Learn moreFor more feature packaging details, refer to the VMware Aria Operations for Networks documentation .VMware Aria Operations for Networks on-premises term licenses are also available in one- and three-yearsubscription terms with VMware NSX. Read the VMware Product Guide for more information.Licensing for Remote Office Branch Office is available by VMs instead of CPU. Native public cloud licensing is available with vCPU.VMware Aria Operations for Networks Universal is available in one-, three-, and five-year subscriptions. For more information, read the VMware Cloud Services Guide .The solution is available in VMware Aria Universal Suite ™ (formerly vRealize Cloud Universal ™) Enterprise Plus as one-, three-, and five-year subscriptions. Visibility for VDI is available by CCU.For information or to purchase VMware products, call 877-4-VMWARE (outside North America, +1-650-427-5000), visit /products or search online for an authorized reseller in your area at .For detailed product specifications and system requirements, refer to the VMware Aria Operations for Networks documentation .。
Review_for_Chapter_2,川大计网部分习题答案第二章

Chapter 2 Review QeustionsR1,R3,R4,R5,R10,R11,R13,R15,R16,R20,R21,R22,R27,R28R1. List five nonproprietary Internet applications and the application-layer protocols that they use.Answer:The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP;e-mail: SMTP.R3. What is the difference between network architecture and application architecture?Answer:Network architecture refers to the organization of the communication process into layers (e.g., the five-layer Internet architecture). Application architecture, on the other hand, is designed by an application developer and dictates the broad structure of the application (e.g., client-server or P2P)•R4What information is used by a process running on one host to identify a process running on another host?Answer:The IP address of the destination host and the port number of the destination socket.•R5For a P2P file-sharing application, do you agree with the statement, “There is no notion of client and server sides of a communication session”? Why or why not?Answer:No. As stated in the text, all communication sessions have a client side and a server side. In a P2P file-sharing application, the peer that is receiving a file is typically the client and the peer that is sending the file is typically the server.•R10Recall that TCP can be enhanced with SSL to provide process-to-process security services, including encryption. Does SSL operate at the transport layer or the application layer? If the application developer wants TCP to be enhanced with SSL, what does the developer have to do ?Answer:SSL operates at the application layer. The SSL socket takes unencrypted data from the application layer, encrypts it and then passes it to the TCP socket. If the application developer wants TCP to be enhanced with SSL, she has to include the SSL code in the application.•R11What is meant by a handshaking protocol?Answer:A protocol uses handshaking if the two communicating entities first exchange control packets before sending data to each other. SMTP uses handshaking at the application layer whereas HTTP does not.•R13Telnet into a Web server and send a multiline request message. Include in the request message the If-modified-since: header line to force a response message with the 304 Not Modified status code.Answer:Issued the following command (in Windows command prompt) followed by the HTTP GET message to the “”web server:> telnet 80Since the index.html page in this web server was not modified since Fri, 18 May 2007 09:23:34 GMT, the following output was displayed when the above commands were issued on Sat, 19 May 2007. Note that the first 4 lines are the GET message and header lines input by the user and the next 4 lines (starting from HTTP/1.1 304 Not Modified) is the response from the web server.•R15Suppose Alice, with a Web-based e-mail account (such as Hotmail or gmail), sends a message to Bob, who accesses his mail from his mail server using POP3. Discuss how the message gets from Alice’s host to Bob’s host. Be sure to list the series of application-layer protocols that are used to move the message between the two hosts.Answer:Message is sent from Alice’s host to her mail server over HTTP. Alice’s mail server then sends the message to Bob’s mail server over SMTP. Bob then transfers the message from his mail server to his host over POP3.•R16Print out the header of an e-mail message you have recently received. How many Received: header lines are there? Analyze each of the header lines in the message.Answer: skipped•R20Consider a new peer Alice who joins BitTorrent without possessing any chunks. Without any chunks, she cannot become a top-four uploader for any of the other peers, since she has nothing to upload. How then will Alice get her first chunk?Answer:Alice will get her first chunk as a result of she being selected by one of her neighbors as a result of an “optimistic unchoke,”for sending out chunks to her.•R21In BitTorrent, suppose Alice provides chunks to Bob throughout a 30-second interval. Will Bob necessarily return the favor and provide chunks to Alice in this same interval? Why or why not?Answer:It is not necessary that Bob will also provide chunks to Alice. Alice has to be in the top 4 neighbors of Bob for Bob to send out chunks to her; this might not occur even if Alice is provides chunks to Bob throughout a 30-second interval.•R22What is an overlay network? Does it include routers? What are the edges in the overlay network? How is the query-flooding overlay network created and maintained?Answer:The overlay network in a P2P file sharing systemconsists of the nodes participating in the file sharingsystem and the logical links between the nodes. There is a logical link (an “edge”in graph theory terms) from node A to node B if there is a semi-permanent TCPconnection between A and B. An overlay network does not include routers. With Gnutella, when a node wants to join the Gnutella network, it first discovers the IPaddress of one or more nodes already in the network. It then sends join messages to these nodes. When the node receives confirmations, it becomes a member of the of Gnutella network. Nodes maintain their logical links with periodic refresh messages.•R27For the client-server application over TCP described in section 2.7, why must the server program be executed before the client program? For the client-server application over UDP described in Section 2.8, why may the client program be executed before the server program?Answer:For the TCP application, as soon as the client is executed, it attempts to initiate a TCP connection with the server. If the TCP server is not running, then the client will fail to make a connection. For the UDP application, the client does not initiate connections (or attempt to communicate with the UDP server) immediately upon execution•R28The UDP server described in Section 2.8 needed only one socket, where the TCP server described in Section 2.7 needed two sockets. Why? If the TCP server were to support n simultaneous connections, each from a different client host, how many sockets would the TCP server need?Answer:With the UDP server, there is no welcoming socket, and all data from different clients enters the server through this one socket. With the TCP server, there is awelcoming socket, and each time a client initiates aconnection to the server, a new socket is created. Thus, to support n simultaneous connections, the serverwould need n+1 sockets.ProblemsP1,P4,P5,P7,P8,P16,P24,P25•P1True or false?a. A user requests a Web page that consists of some textand three images. For this page, the client will sendone request message and receive four responsemessages.b.Two distinct Web pages (for example,/research.html and/student.html)can be sent over the same persistent connection.c.With nonpersistent connection between browser andorigin server, it is possible for a single TCP segment to carry two distinct HTTP request messages.d.The Date: header in the HTTP response messageindicates when the object in the response was lastmodified.Answer:a) Fb) Tc) Fd) F•P4Obtain the HTTP/1.1 specification (RFC2616). Answer the following questions: a.Explain the mechanism used forsignaling between the client and serverto indicate that a persistent connection is being closed. Can the client, theserver ,or both signal the close of aconnection?b.What encryption services are providedby HTTP?Answer:a) Persistent connections are discussed in section 8 ofRFC 2616 (the real goal of this question was to getyou to retrieve and read an RFC). Sections 8.1.2 and8.1.2.1 of the RFC indicate that either the client or theserver can indicate to the other that it is going to close the persistent connection. It does so by including theincluding the connection-token "close" in theConnection-header field of the http request/reply.b) HTTP does not provide any encryption services.•P5Read RFC 959 for FTP. List all of theclient commands that are supported by the RFC.Answer:Access control commands:USER, PASS, ACT, CWD, CDUP, SMNT, REIN, QUIT.Transfer parameter commands:PORT, PASV, TYPE STRU, MODE.Service commands:RETR, STOR, STOU, APPE, ALLO, REST, RNFR, RNTO, ABOR, DELE,RMD, MRD, PWD, LIST, NLST, SITE, SYST, STAT, HELP, NOOP.•P7Suppose within your Web browser you click on a link to obtain a Web page. The IP address for the associated URL is not cached in your local host, so a DNS lookup is necessary to obtain the IP address. Suppose that nDNS servers are visited before your host receives theIP address from DNS; the successive visits incur andRTTof RTT1,…RTTn. Further suppose that the Webpage associated with the link contains exactly one object, consisting of a small amount of HTML text. LetRTT0denote the RTT between the local host and theserver containing the object. Assuming zero transmission time of the object, how much time elapses from when the client clicks on the link until the client receives the object?Answer:The total amount of time to get the IPaddress iselapses to set up the Once the IP address is known, RTTTCP connection and another RTTelapses to requestand receive the small object. The total response time is•P8Referring to Problem P7,suppose theHTML file references three very smallobjects on the same server. Neglecting transmission times, how much timeelapses witha.Non-persistent HTTP with no parallelTCP connections?b.Non-persistent HTTP with parallelconnections?c.Persistent HTTP?Answer: a)b)c)•P16Consider distributing a file of F=5 Gbits to N peers. The server has an upload rateof us =20Mbps, and each peer has adownload rate of di =1Mbps and anupload rate of u. For N=10,100, and1,000 and u=100Kbps, 250Kbps,and 500Kbps,prepare a chart giving the minimum distribution time for each of the combinations of N and u for both client-server distribution and P2P distribution.Answer:For calculating the minimum distribution time for client-server distribution, we use the following formula:Similarly, for calculating the minimum distribution time for P2P distribution, we use the following formula:•P24Suppose that in UDPClient.java we replace the LineDatagramSocket clientSocket= new DatagramSocket();withDatagramSocket clientSocket= new DatagramSocket(5432);Will it become necessary to changeUDPServer.java? What are the port numbers for the sockets in UDPClient and UDPServer?What were they before making this change?Answer:•P25Install and compile the Java ProgramsTCPClient and UDPCLient on one hostand TCPServer and UDPServer onanother host.a.Suppose you run TCPClient before yourun TCPServer. What happens? Why?b.Suppose you run UDPCLient before yourun UDPServer. What happens? Why?c.What happens if you use different portnumbers for the client and server sides?Answer:a)If you run TCPClient first, then the client will attempt to make a TCP connection with a non-existent server process.A TCP connection will not be made.b) UDPClient doesn't establish a TCP connection with the server. Thus, everythingshould work fine if you first run UDPClient, then run UDPServer, and then type some input into the keyboard.c) If you use different port numbers, then the client will attempt to establish a TCP connection with the wrong process or a non-existent process. Errors will occur.。
Mellanox vSAN 网络解决方案说明说明书
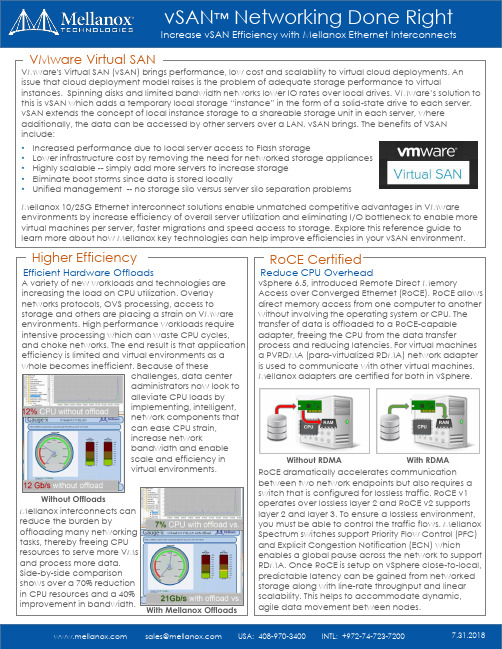
vSAN ™Networking Done RightIncrease vSAN Efficiency with Mellanox Ethernet InterconnectsHigher EfficiencyEfficient Hardware OffloadsA variety of new workloads and technologies are increasing the load on CPU utilization. Overlay networks protocols, OVS processing, access tostorage and others are placing a strain on VMware environments. High performance workloads require intensive processing which can waste CPU cycles, and choke networks. The end result is that application efficiency is limited and virtual environments as a whole becomes inefficient. Because of thesechallenges, data center administrators now look to alleviate CPU loads by implementing, intelligent, network components that can ease CPU strain, increase networkbandwidth and enable scale and efficiency in virtual environments.Mellanox interconnects can reduce the burden byoffloading many networking tasks, thereby freeing CPU resources to serve more VMs and process more data. Side-by-side comparison shows over a 70% reduction in CPU resources and a 40% improvement in bandwidth.Without OffloadsWith Mellanox OffloadsvSphere 6.5, introduced Remote Direct MemoryAccess over Converged Ethernet (RoCE). RoCE allows direct memory access from one computer to another without involving the operating system or CPU. The transfer of data is offloaded to a RoCE-capable adapter, freeing the CPU from the data transferprocess and reducing latencies. For virtual machines a PVRDMA (para-virtualized RDMA) network adapter is used to communicate with other virtual machines. Mellanox adapters are certified for both in vSphere.RoCE dramatically accelerates communication between two network endpoints but also requires a switch that is configured for lossless traffic. RoCE v1 operates over lossless layer 2 and RoCE v2 supports layer 2 and layer 3. To ensure a lossless environment, you must be able to control the traffic flows. Mellanox Spectrum switches support Priority Flow Control (PFC) and Explicit Congestion Notification (ECN) whichenables a global pause across the network to support RDMA. Once RoCE is setup on vSphere close-to-local, predictable latency can be gained from networked storage along with line-rate throughput and linear scalability. This helps to accommodate dynamic, agile data movement between nodes.RoCE CertifiedReduce CPU OverheadWith RDMAWithout RDMA VMware Virtual SANVMware's Virtual SAN (vSAN) brings performance, low cost and scalability to virtual cloud deployments. An issue that cloud deployment model raises is the problem of adequate storage performance to virtualinstances. Spinning disks and limited bandwidth networks lower IO rates over local drives. VMware’s solution to this is vSAN which adds a temporary local storage “instance” in the form of a solid -state drive to each server. vSAN extends the concept of local instance storage to a shareable storage unit in each server, where additionally, the data can be accessed by other servers over a LAN. vSAN brings. The benefits of VSAN include:•Increased performance due to local server access to Flash storage•Lower infrastructure cost by removing the need for networked storage appliances •Highly scalable --simply add more servers to increase storage •Eliminate boot storms since data is stored locally•Unified management --no storage silo versus server silo separation problemsMellanox 10/25G Ethernet interconnect solutions enable unmatched competitive advantages in VMwareenvironments by increase efficiency of overall server utilization and eliminating I/O bottleneck to enable more virtual machines per server, faster migrations and speed access to storage. Explore this reference guide to learn more about how Mellanox key technologies can help improve efficiencies in your vSAN environment.Scalable from a half rack to multiple racksHalf Rack 12 nodesFull Rack 24 nodesPay As You Grow Switching10 Racks up to 240 nodesDeployment Config134411GbE link: 1GbE Transceiver125/10GbE link: QSFP to SFP+324100GbE link: QSFP to QSFP 100/40GbE link: QSFP to QSFP Provisioning & Orchestration▪Zero-touch provisioning ▪VLAN auto-provisioning▪Migrate VMs without manual configuration▪VXLAN/DCI support for VM migration across multiple datacenters for DRMonitoring▪Performance monitoring ▪Health monitoring ▪Detailed telemetry▪Alerts and notificationsAutomated Network▪½ 19” width, 1U height ▪18x10/25GbE + 4x40/100GbE ▪57W typical (ATIS)2Mellanox InterconnectsiSERStorage virtualization requires an agile and responsive network. iSER accelerates workloads by using an iSCSI extensions for RDMA. Using the iSER extension lowers latencies and CPU utilization to help keep pace with I/O requirements and provides a 70% improvement in throughput and 70% reduction in latencies through Mellanox Ethernet interconnects.Deliver 3X EfficiencyHyper-ConvergedReduce CapEx ExpenseHyper-Converged Infrastructure (HCI) is a demanding environment for networking interconnects. HCI consists of three software components: compute virtualization, storage virtualization and management, in which all three require an agile andresponsive network. Deploying on 10, or better, 25G network pipes assists as does network adapters and switches with offload capabilities to optimizeperformance and availability of synchronization and replication of virtualized workloads.CapEx Analysis: 10G vs. 25GMellanox adapters and switches accelerate VM resources toimprove performance, enhance efficiency and provide high-availability and are a must-have feature for any VMware environment. Ethernet AdaptersMellanox Connect-X adapters:▪Enable near-native performance for VMs thru Stateless offloads ▪Extend hardware resources to 64 PF, 512 VF w/ SR-IOV & ROCE ▪Accelerate virtualized networks with VXLAN, GENEVE & NVGRE ▪Align network services withcompute services for multitenant network supportIncreasing vSAN EfficiencyIncrease vSAN Efficiency with Mellanox Ethernet Interconnects。
CiteSpace中文手册

FURUNO deepsea

All brand and product names are registered trademarks, trademarksor service marks of their respective holders.SPECIFICATIONS SUBJECT TO CHANGE WITHOUT NOTICE1312 PDF Printed in JapanCatalogue No. GC-020tFURUNO ELECTRIC CO., LTD.Nishinomiya, Hyogo, Japan FURUNO U.S.A., INC.Camas, Washington, FURUNO NORGE A/S Ålesund, Norway www.furuno.no FURUNO (UK ) LIMITEDHavant, Hampshire, FURUNO DANMARK A/S Hvidovre, Denmark www.furuno.dkFURUNO SVERIGE ABVästra Frölunda, Sweden www.furuno.seFURUNO FRANCE S.A.S.Bordeaux-Mérignac, France www.furuno.fr FURUNO ITALIA S.r.l.Genoa, ItalyFURUNO ESPAÑA S.A.Madrid, Spain www.furuno.es FURUNO FINLAND OY Espoo, Finland www.furuno.FURUNO POLSKA Sp. Z o.o.Gdynia, Poland www.furuno.plFURUNO EURUS LLCSt. Petersburg, Russian Federation .ruFURUNO DEUTSCHLAND GmbHRellingen, Germany www.furuno.de FURUNO HELLAS S.A.Glyfada, Greece www.furuno.grFURUNO (CYPRUS) LTDLimassol, Cyprus .cy FURUNO KOREA CO., LTD.Busan, KoreaFURUNO SHANGHAI CO., LTD.Shanghai, China /cn RICO (PTE ) LTDSingapore.sgPlease visit and get more ideas about FURUNO!FURUNO, a world's leading manufacturer of Marine Electronics,offers a comprehensive range of Navigation and Communications equipmentFor safe and efficient navigation, FURUNO provides a wide range of innovative radio-communications and radio-navigation equipment complying with IMO, ITU, IEC, ISO and other relevant standards. Our equipment and systems are designed with state-of-the-art technologies, software expertise and sensor engineering.FURUNO radar can be connected to an Ethernet network for a variety of user requirements. Each of X- and S-band radar can be interswitched without using extra equipment.Displays official Electronic Navigational Charts (ENC) S-57 Edition, ARCS charts and C-MAP CM 93 Edition 3. The ECDIS can overlay a radar image, ARPA and AIS data with the chart, when conducting, route planning and route monitoring.Featuring total integration of ARPA Radar and ENC Display System, FURUNO Chart Radar series display the radar images together with ENC at the same time.Model: FMD-3300Model: FCR-28x9Model: FEA-2807Model: FCR-28x7Models: FAR-21x7(19" LCD )/FAR-28x7(23" LCD )Models: FMD-3200(19" LCD )/FMD-3300(23" LCD )Models: FCR-21x9(19" LCD )/FCR-28x9(23" LCD )Models: FEA-2107(19" LCD )/FEA-2807(23" LCD )Models: FCR-21x7(19" LCD )/FCR-28x7(23" LCD )RadarIntegrated Navigation SystemElectronic Chart Display and Information SystemChart RadarModel: FAR-21x7Model: FAR-28x7FURUNO VOYAGER is an Integrated Navigation System comprising ECDIS, Radar, conning display, steering system, radio-navigation equipment, VHF radios, chart table, etc., and offers Track Control System. The bridge console complies with the requirements set by various classification societies and matches with a bridge layout of modern merchant vessels.Delivers full coverage of Inmarsat-C services: EGC reception, Inmarsat E-mail, distress message handling,LCR IP RoutingVPNIP PBXTraffic ControlTraffic Control Onboard LAN NetworkIP phone Pre-paid call Surveillance camera Monitoring systemw w w.sa f e c o m n e t.c o mFirewall IP Routing VPN IP PBXLCR (Least Cost Routing)FirewallLCR is the process of selecting the path of communications traffic based on cost, allowing for automatic selection of the most cost-efficient communication line available. It is possible to set VSAT, which is charged by monthly fixed flat rate, as the default communication means, and switch over to “pay-as-you-go” FleetBroadband whenever the VSAT line is out. This way, total cost for communicatoin can be reduced.IP routing is a set of protocols to facilitate IP connection between onboard network and the public Internet.VPN (Virtual Private Network) is a secure way of connecting to onshore office network from a remote location, using the Internet. Since encryption is applied to the communication, the network data packets can be transported privately, preventingunauthorized users from reading the private network packets. This way, the same network environment as onshore offices can be constructed onboard vessels. Compared with using exclusive circuit services to construct secure network between vessels and onshore offices, VPN has the advantage of reducing communication cost.IP PBX is a PBX for IP telephones utilizing IP network, unlikePABX commonly used for analog telephone network. The system is designed to interoperate with the conventional PABX, onboard public addressor system as well as VoIP of Inmarsat and VSAT.Traffic control is the control of computer network traffic tooptimize performance of communication. This can be achieved by setting order of priority for data to be handled (Quality of Service: QoS), and restricting the volume of communication at a time, applications to be used as well as access to certain contents.A firewall is designed to permit or deny network transmissions to protect networks against unauthorized access by malware from the public Internet, i.e., computer viruses and keyloggers, while permitting legitimate communications to pass.InquiryReceipt。
富士通 FLASHWAVE
F L A S H W A V E®4500 Mul tiservice Provisioning Pla tforMToday’s optical transport networks are increasingly defined by the unpredictable convergence of voice, data and video technologies. They are shaped by accelerating service demands and shifting business models that aim to reduce overall operational expenditures. To succeed, national, local and multiservice providers need extremely flexible and scalable infrastructure equipment that will adapt to emerging bandwidth fluctuations.Transition to Packet ServicesThe Fujitsu FLASHWAVE ® 4500 Multiservice Provisioning Platform (MSPP) provides a unified platform for both packet and SONET-derived services. The FLASHWAVE 4500 MSPP solves majorbusiness and network problems by reducing transport costs and power requirements, conserving valuable space and simplifying network management. The system allows convergence of data, synchronous and asynchronous networks, increasing revenue without the expense of overlay networks.Converged Ethernet ServicesThe MEF-certified FLASHWAVE 4500 platform supports a wide range of Ethernet interfaces and features. Utilized as a hybrid TDM/packet device, the inherent bandwidth granularity within a single system can realize further savings.A Quantum Leap in Efficiency and ScalabilityThe FLASHWAVE 4500 MSPP provides a quantum leap in network efficiency. It delivers a flexible, multiservice optical transport solution for a comprehensive range of applications. This highlyscalable system easily expands to become a Multiservice Switching Platform (MSSP), supporting ultra high-capacity grooming applications. Such scalable expansion previously required an expensive Digital Cross-connect System (DCS).Optical Flexibility and DensityThe FLASHWAVE 4500 system offers an extremely cost- and space-effective solution for traditional SONET Add/Drop Multiplexer (ADM) applications. Its architecture supports advanced functionality, such as high-density Ethernet transport, data aggregation, versatile multirate optical interfaces and optional integrated DS1/DS3 grooming.The FLASHWAVE 4500 platform enables you to:Migrate ▶ TDM to packet with efficient Gigabit Ethernet (GbE) streams within the SONET layer.Unify ▶ service delivery and applications with a single, flexible multirate card (OC-3 to OC-48).Trusted to Deliver with Proven ReliabilityFujitsu has deployed more than 400,000 Network Elements (NEs) throughout every sector of thecommunications market in North America. Our platforms have also been proven via rigorous independent assessment. One example is testing of the FLASHWAVE 4500 system by the U.S. Defense Information Systems Agency (DISA)-sanctioned Joint Interoperability Test Command (JITC) for use in the DISA Defense Information System Network (DISN).Migra tion to etHernetFuture-Proof Strategy, ScalabilityThe FLASHWAVE 4500 system’s switch fabric units match system capacity to that of the network, helping tocontrol capital outlay. The platform enables an elegant scalable solution, allowing grooming capacity to be added as needed. This architecture scales from MSPP (70 Gbps) to MSSP (300 Gpbs) single-rack configurations, protecting initial capital investments. The system integrates multiple service, transport and grooming elements into a single NE. A centralized non-blocking STS-1 switching architecture, combined with an optional 20 Gbps VT1.5 switching fabric, provides flexible grooming within the STS-1 to ensure maximum use of available bandwidth.Ethernet Flexibility, AggregationThe FLASHWAVE 4500 system enables flexible management and cost-effective transport of Ethernet services.Packet transport efficiency is optimized by utilizing features such as VCAT, LCAS, & RPR. The platform’s Trunking Port (TPORT) function can efficiently aggregate multiple VLAN and EoS WAN services onto a single GbE LAN facility. This capability is ideal for applications that require Ethernet aggregation, such as wireless backhaul.TPORT functionality also reduces routers/switch ports, external cabling and FLASHWAVE 4500 system interface ports. Optional redundant GbE hand-offs provide facility and module protection for mission-critical applications. Key Technical AdvantagesThe FLASHWAVE 4500 platform supports a wide range of services, while improving the bottom line:Integrated▶MSPP and high-density MSSP on a single platformModular▶ and flexible multirate service interface to conserve shelf real estateTunable▶optics for reduced sparing inventoriesN ext-Generation▶data, video and voice services, plus operational continuity with existing networksD iverse▶ MEF-9 and MEF-14 certified E-Line and E-LAN services over a reliable SONET platformKey Network BenefitsThe FLASHWAVE 4500 platform delivers a full range of services and architectures utilizing SONET andEthernet technologies:Full Line-Rate▶ Gigabit Ethernet provisioning over all SONET/DWDM backbonesAdvanced▶ service aggregation and grooming (DS1, DS3, STS-1, optical and Ethernet)Simplified▶ network management and visibility (performance monitoring data)Converged▶ data, synchronous and asynchronous networks without expensive overlay networks oPtiMiZeD for efficiencYTHE WINNING COMBINATION KEY NETWORK BENEFITS OVERLAY NETWORKSMODULAR/FLEXIBLEMULTIRATE SERVICEINTEGRATEDMSPP/MSSPINVENTORYREDUCTIONSIMPLIFIED NETWORK MANAGEMENTcritical netWorK aPPlicaWireless BackhaulFor wireless-carrier backhaul services, the FLASHWAVE 4500 is the transport platform of choice, deliveringEthernet aggregation and TDM grooming. The platform enables a smooth migration in supporting anincreasing amount of data over the wireless infrastructure at optimized cost.Core and Dedicated RingsOptical flexibility and density, dependability and cost efficiency make the FLASHWAVE 4500 platform ideal for incumbent national carriers deploying core, dedicated ring and path-protected mesh topologies. Multiservice TransportWith a single multirate card, the FLASHWAVE 4500 platform provides the ultimate in optical flexibility, easysparing and low maintenance costs.Transition to BroadbandThe FLASHWAVE 4500 system is the ideal migration platform to assure a smooth transition to a more packet-centric network. The platform simultaneously maintains important revenue-bearing OC-n/TDM services.DCS and Optical HubbingThe FLASHWAVE 4500 system supports optical hubbing of OC-3/12/48/192 rings. This enables traffic aggregation and grooming across multiple networks when utilized with the inherent DCS functionality.Scalable, Dependable, Cost-EffectiveFujitsu offers a broad selection of professional services to assist at every stage in a network’s evolution and operation. From planning through deployment and ongoing maintenance to future enhancements, Fujitsu Network Life Cycle Services are available whenever needed. Our comprehensive range of services includesnetwork and system design, training, customized deployment, craft interface software, migration planning and more. Your Fujitsu sales representative can guide you in selecting the right service options for your business.Popular planning and deployment services for the FLASHWAVE 4500 platform include:N ETSMART ▶® 1500 Element Management System – Simplify Operations, Administration, Maintenance and Provisioning (OAM&P) through a secure point-and-click interface. A dvance Hardware Replacement ▶ – Ensure uninterrupted operation with spares supplied within four hours or by the next business day. R emote Technical Assistance ▶ – Our Technical Assistance Center is your central point of contact for resolving network issues in collaboration with highly trained Fujitsu engineers—24 x 7 x 365.Service Support Packages for Ongoing MaintenanceIf you’re looking for a complete professional maintenance solution, Fujitsu service support packages have the right combination of flexibility and comprehensive assurance. Choose the level and types of service you need to supplement your own resources. Our service support packages help keep your network running smoothly, provide critical care and protect the longevity of your investment.Network Operations CenterWith a full range of vendor-independent network fault and performance monitoring features, the Fujitsu Network Operations Center (NOC) offers guaranteed, round-the-clock system protection. Our reliable NOC facility is available as a primary or supplemental operations resource. This service not only helps you control costs and maintain high levels of customer satisfaction, it also provides trustworthy and reliable after-hours and emergency coverage.netWorK life cYcle servicesArchitecturesTerminal▶Linear ADM (1+1)▶Unidirectional Path Switched Ring (UPSR)▶Two Fiber-Bidirectional Line Switched Ring (2F-BLSR)▶Four Fiber-Bidirectional Line Switched Ring (4F-BLSR)▶Dedicated Path Protected Mesh (DPPM)▶Resilient Packet Ring (RPR)▶InterfacesDS1 64-pin AMP▶® CHAMP connectors DS3/EC1 BNC connectors▶OC-3/STM-1 S C for dual unit; LC for quad unit,▶MPO connector for 8-port unit1310 nm widebandOC-12/STM-4 L C, FC, SC or ST for single unit;▶LC for quad unit;MPO connector for 8-port unit1310 nm wideband1550 nm wideband (single unit only) OC-48/STM-16 L C, FC, SC or ST connectors▶1310 nm wideband1550 nm tunable narrowband(8 λ @ 50 GHz)OC-192/STM-64 L C, FC, SC or ST connectors▶1310 nm wideband; 1550 nm wideband1550 nm tunable narrowband(4 λ @ 100 GHz)1550 nm full band tunable to 88 λ(@ 50 GHz spacing) G.709 compliant Ethernet (EoS) R J-45 connectors for▶10/100Base-T Ethernet;LC or SC connectors for GigabitEthernetEthernet Aggregation LC connectors for dual port unit▶(trunking port, RPR) 850 nm wideband; 1310 nm widebandHigh/Low Order Aggregation Switching ProtectionDS1 1+1 or unprotected▶DS3/EC1 1:n (n=1 to 6) or unprotected▶DS3 Transmux 1+1 or 1:n (n=1 to 6)▶OC-3/STM-1 1+1, UPSR, DPPM or unprotected▶OC-12/STM-4 1+1, UPSR, DPPM or unprotected▶OC-48/STM-16 1+1, UPSR, 2F-BLSR, DPPM▶or unprotectedOC-192/STM-64 1+1, UPSR, 2F-BLSR, 4F-BLSR,▶DPPM or unprotectedEthernet R PR or unprotected;▶Port Link Aggregation orUnit Link AggregationSwitch matrices 1+1▶Synchronization 1+1▶SynchronizationInternal Stratum 3 timing source▶Synchronization Status Messaging (SSM)▶D S1 Building Integrated Timing Supply (BITS) primary and ▶secondary clock output/inputLine timing▶FLASHWAVE 4500 Single-Shelf ConfigurationOperationsI n-service expansion from MSPP to MSSP with common ▶operations benefitsStandard RPR embedded management plane▶TL1 protocol over X.25, OSI/LCN or IP/LCN▶Simple Network Management Protocol (SNMP)▶TCP/IP and X.25 gateway functionality▶Software download and remote memory backup/restore ▶M anaged via NETSMART 500 craft user interface and▶NETSMART 1500 EMSDS1, DS3, OC-3 and OC-12 digital test access▶PM Threshold Provisioning on a per facility basis▶G.709 compliant digital wrapper for narrowband OC-192 ▶optical channel adaptationAutomatic equipment protection group creation▶Interoperable with all Fujitsu transmission products▶Full suite of in-service hardware and software upgrades ▶NEBS Level 3 compliant▶Telcordia OSMINE compliant▶Power Consumption/Heat Dissipation Per shelf (typical) 400 W (1364 BTU/hr)▶Power Input –48 V DC (A and B)▶Operating EnvironmentTemperature 0 to 50 °C (32 to 122 °F)▶Humidity 5 to 95% (non-condensing)▶Physical CharacteristicsDimensions (H x W x D) 22.75 x 21.5 x 12"▶(578 x 546 x 305 mm) Weight (fully loaded) 137 lb (62 kg)▶FLASHWAVE 4500 Multishelf ConfigurationFujitsu Network Communications Inc.2801 Telecom Parkway, Richardson, TX 75082Tel: 800.777.FAST (3278) Fax: 972.479.6900/telecom© Copyright 2008 Fujitsu Network Communications Inc.FLASHWAVE® and NETSMART® are trademarks of Fujitsu Network Communications Inc. (USA). FUJITSU (and design)® and THE POSSIBILITIES ARE INFINITE™ are trademarks of Fujitsu Limited. All Rights Reserved.。
NetOmnia 形成今天的网络规划与您的合作 全面以太网保证性能和SLA管理说明书
NetOmnia™Comprehensive Ethernet assurance performance and SLA management1A key challenge of delivering Ethernet services is the time-consuming task of network monitoring. Many key metrics must be accurately measured to assess the performance of an entire, often multivendor, network. The lack of a single, unified management system further complicates this challenge, as operators must work with multiple management systems: an inefficient, time consuming, and costly overhead. Gathering data to support accurate and effective performance measurement across an entire Ethernet network is, therefore, often a best-effort project involving a substantial amount of manual work.In addition, end customers and subscribers often want to know how well the service provider is executing on Service-Level Agreements (SLAs). Providing real-time and accurate reports for SLA management is difficult to produce on a continuous basis; an error here can result in lost revenue, not to mention lost customers.To address these challenges, Fujitsu is offering NetOmnia™, a comprehensive Ethernet Assurance Performance and SLA management system providing end-to-end service assurance and service quality management solutions in a multivendor environment. NetOmnia enables youto achieve three keybusiness objectives:• M onitor Ethernet-related performancedata efficiently in aconstantly changingnetwork• P rovide consistent-looking, meaningfulperformance and SLAmanagementinformation tostakeholders• R educe or eliminateinstances and impactof customer SLAviolations Next-Generation Visualization to Improve Network Performance NetOmnia Ethernet Assurance is a multivendor, MEF-compliant solution that provides end-to-end visualization and monitoring of Ethernet services to ensure and improve customer experience. With off-the-shelf, multivendor support, NetOmnia can be deployed and configured quickly to discover Ethernet services and begin monitoring and reporting on the health and status of customer services. NetOmnia provides configurable monitoring and visualization of service quality metrics such as availability, delay, jitter, and frame loss, as well as the ability to create and monitor custom-defined metrics. Deliver Better Service, Increase Revenue, Reduce CostsNetOmnia SLA Manager, an optional overlay, enables service providers to easily define, track and report on contractual SLAs. NetOmnia can seamlessly monitor the operational performance of customer services to show the impact of network degradation and service outages on per-contract corporate SLAs.With NetOmnia, technicians can define SLAs based on service quality and service availability. It is also possible to define the conformance period and configurable levels for warning and violation notifications. SLA reports can be delivered to customers on a scheduled basis to provide differentiated service to improve customer retention.In contrast to solutions that merely provide monthly SLA reports, NetOmnia provides real time reports on SLA compliance and predicts SLA violations based on current trends. Reports can be scheduled and automatically delivered to both users and end customers.NetOmnia™End-to-End, MEF-Compliant Service AssuranceNetOmnia helps you offer profitablecarrier-class Ethernet servicesNetOmnia’s Workflow Automationempowers users to create automations andnotifications based on performance criteria23Innovative Performance and SLA ManagementNetOmnia delivers dramatic innovation that takes network performance and SLA management to the next level with true end-to-end services visibility and ease of use. This system is highly scalable and supports a distributed, high-availability clusterenvironment. NetOmnia takes advantage of the latest software and hardware technologies to offer you:• 100% Web 2.0-based architecture requiring no administration • Easy integration with existing software systems• Simple Web browser-based access—no Java software needed • F ull compliance with ITU-T Y.1731, IEEE 802.1ag and 802.3ah, andMEF 10.2, 15, and 17 standards• Comprehensive discovery, mapping, and monitoring of:• Devices and physical ports • Logical interfaces, including UNIs • Ethernet Virtual Connections • Point-to-point• Multipoint-to-multipoint • Traffic profiles• CIR, CBS, EIR, EBS, and color mode • Testing and diagnostics• Customer-centric performance monitoring and SLA management • Customer portals available for SLA conformance reports • One system to monitor a multivendor hardware environment • Support for multiple customer networks without risk of data leakage • C ustomized reporting capabilities including key performance and keyquality indicators (KPIs and KQIs)• D etailed metrics on key service quality parameters such asavailability, delay, jitter, throughput, frame loss ratio, and packet loss• Deploys in days and configures in weeks, not months • New network devices can be added in just minutes• Auto-discovery of EVCs and VLANs provides out-of-box functionality • M ultivendor support ensures seamless end-to-end service viewsacross vendorsNetOmnia ™NetOmnia Helps you Focus on Your Core BusinessNetOmnia allows users to create and run detailed summary and top-n reports4Building and maintaining a monitoring system typically consumes a large quantity of resources and time; in turn, this impairs a service provider’s ability to deliver and maintain revenue-generating services. NetOmnia reduces this burden by freeing network operations staff to focus on core business goals, not on reporting.Backed by a Market-Leading Solutions ProviderWith NetOmnia, service providers also get the support of Fujitsu, a leading innovator in Connection-Oriented Ethernet and a market leader in packet optical networking solutions. Fujitsu offers a broad portfolio of multivendor network services and wide experience sourcing and selecting the best network technologies available. NetOmnia enables us to offer you a truly vendor agnostic Ethernet service assurance and SLA management solution.NetOmnia ™© Copyright 2013 Fujitsu Network Communications Inc. FUJITSU (and design)® and “shaping tomorrow with you” are trademarks of Fujitsu Limited in the United States and other countries. All Rights Reserved. NetOmnia ™ is a trademark of Centina Systems, Inc. All other trademarks are the property of their respective owners. Configuration requirements for certain uses are described in the product documentation. Features and specifications subject to change without notice. 1.0/04.13Fujitsu Network Communications Inc.2801 Telecom Parkway, Richardson, TX 75082 Tel: 800.777.FAST (3278) Fax: 972.479.6900/telecomMultivendor Ethernet Assurance and SLA ManagementNetOmnia consolidates, filters and correlates alarms across the entire network。
CYME电力系统分析软件模块参考指南说明书
CYME power system analysis softwareModule reference guideReliable modeling, analytics and planning tools to improve the performance of the distribution systemCYMEPower Engineering Software and Solutions2EATONCYME Power System Analysis Software Module Reference Guide – October 2020CYME power system analysis softwareBase packageCYMDIST is the distribution system analysis base package of the CYME software suite. It bundles all the modeling and analysis tools required to perform the various types of simulations involved in electric distribution system planning. The calculation engines supportbalanced or unbalanced distribution models that are built with any combination of phases and operated in radial, looped or meshed configu-rations. Reliable modeling, analytics and planning tools to improve the performance of the distribution system.3EATONCYME Power System Analysis Software Module Reference Guide – October 2020CYME power system analysis softwareAdditional module optionsEaton is a registered trademark.All other trademarks are property of their respective owners.Eaton1000 Eaton Boulevard Cleveland, OH 44122United States Eaton's Energy Automation Division CYME International T & D 1485 Roberval, Suit 104St. Bruno, QC Canada J3V 3P8P: 450.460.3655 F: 450.461.0966P: 800.361.3627 (Canada/USA)/cyme© 2020 EatonAll Rights ReservedPublication No. PA917005EN October 2020Follow us on social media to get thelatest product and support information.* Distribution Resource Integration and Value Estimation (DRIVE) is provided under license and is powered by technological research developed by the Electrical Power Research Institute, Inc. (EPRI).EPRI does not endorse or advocate for any particular measure, valuation, answer, finding, conclusion, hypothesis, assumption, or other result.CYME power system analysis softwareAdditional module options。
《城市轨道交通供电系统工程施工质量验收规范》标准全文
量安全监督总站负责技术内容的解释。执行过程中,请各有关单位结合实际,不断总结经验,
并将发现的问题、意见和建议函告杭州市建设工程质量安全监督总站[地址:莫干山路 100 号耀江国际大厦 A 座 12 楼,邮政编码:311005],以供修订时参考。
本规范主编单位、参编单位、主要起草人和主要审查人: 本规范主编单位:杭州市建设工程质量安全监督总站
本规范共分 10 章,主要技术内容包括:1 总则;2 术语;3 基本规定;4 牵引及降压变 电所;5 刚性架空接触网;6 柔性架空接触网;7 接触轨;8 杂散电流腐蚀防护系统;9 可视 化接地系统;10 电力监控与电能质量管理系统。
本规范由浙江省住房和城乡建设厅负责管理和对强制条文的解释,由杭州市建设工程质
浙江省工程建设标准
城市轨道交通供电系统施工质量验收规范
Code for acceptance of construction quality of power supply system engineering of urban rail transit
DB33/T ××/××××-201×
主编单位:杭州市建设工程质量安全监督总站 中铁电气化局集团有限公司 中铁二局集团有限公司
中铁电气化局集团有限公司 中铁二局集团有限公司 本规范参编单位:中国电建集团华东勘测设计研究院有限公司 杭州市地铁集团有限责任公司 宁波市轨道交通集团有限公司 中铁十一局集团电务工程有限公司 中铁一局集团电务工程有限公司 浙江丽水宏瑜建设有限公司 浙江德光建筑工程有限公司 浙江瓯立园林建设有限公司 纳琦绿能工程有限公司 浙江鸿旭园林建设有限公司 浙江罗邦建设有限公司 丽水市金丰建筑工程有限公司 丽水市鼎旺建设工程有限公司 浙江瓯业园林建设有限公司 丽水市汇桦市政园林有限公司 浙江屹立建设有限公司 浙江华歌建设有限公司 本规范主要起草人:史文杰 周静增 肖国军 雷 鸣 蔡佳旻 周 军 施云琼 王祥涛 于镇川 郭润桥 唐兆军 孙海东 王海涛 左传文 郭 忠 叶波涛 徐 俊 吴赟胤 王存建 王 波 朱智文 赵加建 范 卿 韩明学 陈俊卿 周洪波 何贵龙 黄美香 潘国平 蒋 真 本规范主要审查人:石西全 赵宇宏 戴新国 游劲秋 张 燕 袁 林 刘 伟 洪秀敏
