Search for all d-mincuts of a limited-flow network
Native Instruments MASCHINE MK3 用户手册说明书

The information in this document is subject to change without notice and does not represent a commitment on the part of Native Instruments GmbH. The software described by this docu-ment is subject to a License Agreement and may not be copied to other media. No part of this publication may be copied, reproduced or otherwise transmitted or recorded, for any purpose, without prior written permission by Native Instruments GmbH, hereinafter referred to as Native Instruments.“Native Instruments”, “NI” and associated logos are (registered) trademarks of Native Instru-ments GmbH.ASIO, VST, HALion and Cubase are registered trademarks of Steinberg Media Technologies GmbH.All other product and company names are trademarks™ or registered® trademarks of their re-spective holders. Use of them does not imply any affiliation with or endorsement by them.Document authored by: David Gover and Nico Sidi.Software version: 2.8 (02/2019)Hardware version: MASCHINE MK3Special thanks to the Beta Test Team, who were invaluable not just in tracking down bugs, but in making this a better product.NATIVE INSTRUMENTS GmbH Schlesische Str. 29-30D-10997 Berlin Germanywww.native-instruments.de NATIVE INSTRUMENTS North America, Inc. 6725 Sunset Boulevard5th FloorLos Angeles, CA 90028USANATIVE INSTRUMENTS K.K.YO Building 3FJingumae 6-7-15, Shibuya-ku, Tokyo 150-0001Japanwww.native-instruments.co.jp NATIVE INSTRUMENTS UK Limited 18 Phipp StreetLondon EC2A 4NUUKNATIVE INSTRUMENTS FRANCE SARL 113 Rue Saint-Maur75011 ParisFrance SHENZHEN NATIVE INSTRUMENTS COMPANY Limited 5F, Shenzhen Zimao Center111 Taizi Road, Nanshan District, Shenzhen, GuangdongChina© NATIVE INSTRUMENTS GmbH, 2019. All rights reserved.Table of Contents1Welcome to MASCHINE (25)1.1MASCHINE Documentation (26)1.2Document Conventions (27)1.3New Features in MASCHINE 2.8 (29)1.4New Features in MASCHINE 2.7.10 (31)1.5New Features in MASCHINE 2.7.8 (31)1.6New Features in MASCHINE 2.7.7 (32)1.7New Features in MASCHINE 2.7.4 (33)1.8New Features in MASCHINE 2.7.3 (36)2Quick Reference (38)2.1Using Your Controller (38)2.1.1Controller Modes and Mode Pinning (38)2.1.2Controlling the Software Views from Your Controller (40)2.2MASCHINE Project Overview (43)2.2.1Sound Content (44)2.2.2Arrangement (45)2.3MASCHINE Hardware Overview (48)2.3.1MASCHINE Hardware Overview (48)2.3.1.1Control Section (50)2.3.1.2Edit Section (53)2.3.1.3Performance Section (54)2.3.1.4Group Section (56)2.3.1.5Transport Section (56)2.3.1.6Pad Section (58)2.3.1.7Rear Panel (63)2.4MASCHINE Software Overview (65)2.4.1Header (66)2.4.2Browser (68)2.4.3Arranger (70)2.4.4Control Area (73)2.4.5Pattern Editor (74)3Basic Concepts (76)3.1Important Names and Concepts (76)3.2Adjusting the MASCHINE User Interface (79)3.2.1Adjusting the Size of the Interface (79)3.2.2Switching between Ideas View and Song View (80)3.2.3Showing/Hiding the Browser (81)3.2.4Showing/Hiding the Control Lane (81)3.3Common Operations (82)3.3.1Using the 4-Directional Push Encoder (82)3.3.2Pinning a Mode on the Controller (83)3.3.3Adjusting Volume, Swing, and Tempo (84)3.3.4Undo/Redo (87)3.3.5List Overlay for Selectors (89)3.3.6Zoom and Scroll Overlays (90)3.3.7Focusing on a Group or a Sound (91)3.3.8Switching Between the Master, Group, and Sound Level (96)3.3.9Navigating Channel Properties, Plug-ins, and Parameter Pages in the Control Area.973.3.9.1Extended Navigate Mode on Your Controller (102)3.3.10Navigating the Software Using the Controller (105)3.3.11Using Two or More Hardware Controllers (106)3.3.12Touch Auto-Write Option (108)3.4Native Kontrol Standard (110)3.5Stand-Alone and Plug-in Mode (111)3.5.1Differences between Stand-Alone and Plug-in Mode (112)3.5.2Switching Instances (113)3.5.3Controlling Various Instances with Different Controllers (114)3.6Host Integration (114)3.6.1Setting up Host Integration (115)3.6.1.1Setting up Ableton Live (macOS) (115)3.6.1.2Setting up Ableton Live (Windows) (116)3.6.1.3Setting up Apple Logic Pro X (116)3.6.2Integration with Ableton Live (117)3.6.3Integration with Apple Logic Pro X (119)3.7Preferences (120)3.7.1Preferences – General Page (121)3.7.2Preferences – Audio Page (126)3.7.3Preferences – MIDI Page (130)3.7.4Preferences – Default Page (133)3.7.5Preferences – Library Page (137)3.7.6Preferences – Plug-ins Page (145)3.7.7Preferences – Hardware Page (150)3.7.8Preferences – Colors Page (154)3.8Integrating MASCHINE into a MIDI Setup (156)3.8.1Connecting External MIDI Equipment (156)3.8.2Sync to External MIDI Clock (157)3.8.3Send MIDI Clock (158)3.9Syncing MASCHINE using Ableton Link (159)3.9.1Connecting to a Network (159)3.9.2Joining and Leaving a Link Session (159)3.10Using a Pedal with the MASCHINE Controller (160)3.11File Management on the MASCHINE Controller (161)4Browser (163)4.1Browser Basics (163)4.1.1The MASCHINE Library (163)4.1.2Browsing the Library vs. Browsing Your Hard Disks (164)4.2Searching and Loading Files from the Library (165)4.2.1Overview of the Library Pane (165)4.2.2Selecting or Loading a Product and Selecting a Bank from the Browser (170)4.2.2.1[MK3] Browsing by Product Category Using the Controller (174)4.2.2.2[MK3] Browsing by Product Vendor Using the Controller (174)4.2.3Selecting a Product Category, a Product, a Bank, and a Sub-Bank (175)4.2.3.1Selecting a Product Category, a Product, a Bank, and a Sub-Bank on theController (179)4.2.4Selecting a File Type (180)4.2.5Choosing Between Factory and User Content (181)4.2.6Selecting Type and Character Tags (182)4.2.7List and Tag Overlays in the Browser (186)4.2.8Performing a Text Search (188)4.2.9Loading a File from the Result List (188)4.3Additional Browsing Tools (193)4.3.1Loading the Selected Files Automatically (193)4.3.2Auditioning Instrument Presets (195)4.3.3Auditioning Samples (196)4.3.4Loading Groups with Patterns (197)4.3.5Loading Groups with Routing (198)4.3.6Displaying File Information (198)4.4Using Favorites in the Browser (199)4.5Editing the Files’ Tags and Properties (203)4.5.1Attribute Editor Basics (203)4.5.2The Bank Page (205)4.5.3The Types and Characters Pages (205)4.5.4The Properties Page (208)4.6Loading and Importing Files from Your File System (209)4.6.1Overview of the FILES Pane (209)4.6.2Using Favorites (211)4.6.3Using the Location Bar (212)4.6.4Navigating to Recent Locations (213)4.6.5Using the Result List (214)4.6.6Importing Files to the MASCHINE Library (217)4.7Locating Missing Samples (219)4.8Using Quick Browse (221)5Managing Sounds, Groups, and Your Project (225)5.1Overview of the Sounds, Groups, and Master (225)5.1.1The Sound, Group, and Master Channels (226)5.1.2Similarities and Differences in Handling Sounds and Groups (227)5.1.3Selecting Multiple Sounds or Groups (228)5.2Managing Sounds (233)5.2.1Loading Sounds (235)5.2.2Pre-listening to Sounds (236)5.2.3Renaming Sound Slots (237)5.2.4Changing the Sound’s Color (237)5.2.5Saving Sounds (239)5.2.6Copying and Pasting Sounds (241)5.2.7Moving Sounds (244)5.2.8Resetting Sound Slots (245)5.3Managing Groups (247)5.3.1Creating Groups (248)5.3.2Loading Groups (249)5.3.3Renaming Groups (251)5.3.4Changing the Group’s Color (251)5.3.5Saving Groups (253)5.3.6Copying and Pasting Groups (255)5.3.7Reordering Groups (258)5.3.8Deleting Groups (259)5.4Exporting MASCHINE Objects and Audio (260)5.4.1Saving a Group with its Samples (261)5.4.2Saving a Project with its Samples (262)5.4.3Exporting Audio (264)5.5Importing Third-Party File Formats (270)5.5.1Loading REX Files into Sound Slots (270)5.5.2Importing MPC Programs to Groups (271)6Playing on the Controller (275)6.1Adjusting the Pads (275)6.1.1The Pad View in the Software (275)6.1.2Choosing a Pad Input Mode (277)6.1.3Adjusting the Base Key (280)6.1.4Using Choke Groups (282)6.1.5Using Link Groups (284)6.2Adjusting the Key, Choke, and Link Parameters for Multiple Sounds (286)6.3Playing Tools (287)6.3.1Mute and Solo (288)6.3.2Choke All Notes (292)6.3.3Groove (293)6.3.4Level, Tempo, Tune, and Groove Shortcuts on Your Controller (295)6.3.5Tap Tempo (299)6.4Performance Features (300)6.4.1Overview of the Perform Features (300)6.4.2Selecting a Scale and Creating Chords (303)6.4.3Scale and Chord Parameters (303)6.4.4Creating Arpeggios and Repeated Notes (316)6.4.5Swing on Note Repeat / Arp Output (321)6.5Using Lock Snapshots (322)6.5.1Creating a Lock Snapshot (322)6.5.2Using Extended Lock (323)6.5.3Updating a Lock Snapshot (323)6.5.4Recalling a Lock Snapshot (324)6.5.5Morphing Between Lock Snapshots (324)6.5.6Deleting a Lock Snapshot (325)6.5.7Triggering Lock Snapshots via MIDI (326)6.6Using the Smart Strip (327)6.6.1Pitch Mode (328)6.6.2Modulation Mode (328)6.6.3Perform Mode (328)6.6.4Notes Mode (329)7Working with Plug-ins (330)7.1Plug-in Overview (330)7.1.1Plug-in Basics (330)7.1.2First Plug-in Slot of Sounds: Choosing the Sound’s Role (334)7.1.3Loading, Removing, and Replacing a Plug-in (335)7.1.3.1Browser Plug-in Slot Selection (341)7.1.4Adjusting the Plug-in Parameters (344)7.1.5Bypassing Plug-in Slots (344)7.1.6Using Side-Chain (346)7.1.7Moving Plug-ins (346)7.1.8Alternative: the Plug-in Strip (348)7.1.9Saving and Recalling Plug-in Presets (348)7.1.9.1Saving Plug-in Presets (349)7.1.9.2Recalling Plug-in Presets (350)7.1.9.3Removing a Default Plug-in Preset (351)7.2The Sampler Plug-in (352)7.2.1Page 1: Voice Settings / Engine (354)7.2.2Page 2: Pitch / Envelope (356)7.2.3Page 3: FX / Filter (359)7.2.4Page 4: Modulation (361)7.2.5Page 5: LFO (363)7.2.6Page 6: Velocity / Modwheel (365)7.3Using Native Instruments and External Plug-ins (367)7.3.1Opening/Closing Plug-in Windows (367)7.3.2Using the VST/AU Plug-in Parameters (370)7.3.3Setting Up Your Own Parameter Pages (371)7.3.4Using VST/AU Plug-in Presets (376)7.3.5Multiple-Output Plug-ins and Multitimbral Plug-ins (378)8Using the Audio Plug-in (380)8.1Loading a Loop into the Audio Plug-in (384)8.2Editing Audio in the Audio Plug-in (385)8.3Using Loop Mode (386)8.4Using Gate Mode (388)9Using the Drumsynths (390)9.1Drumsynths – General Handling (391)9.1.1Engines: Many Different Drums per Drumsynth (391)9.1.2Common Parameter Organization (391)9.1.3Shared Parameters (394)9.1.4Various Velocity Responses (394)9.1.5Pitch Range, Tuning, and MIDI Notes (394)9.2The Kicks (395)9.2.1Kick – Sub (397)9.2.2Kick – Tronic (399)9.2.3Kick – Dusty (402)9.2.4Kick – Grit (403)9.2.5Kick – Rasper (406)9.2.6Kick – Snappy (407)9.2.7Kick – Bold (409)9.2.8Kick – Maple (411)9.2.9Kick – Push (412)9.3The Snares (414)9.3.1Snare – Volt (416)9.3.2Snare – Bit (418)9.3.3Snare – Pow (420)9.3.4Snare – Sharp (421)9.3.5Snare – Airy (423)9.3.6Snare – Vintage (425)9.3.7Snare – Chrome (427)9.3.8Snare – Iron (429)9.3.9Snare – Clap (431)9.3.10Snare – Breaker (433)9.4The Hi-hats (435)9.4.1Hi-hat – Silver (436)9.4.2Hi-hat – Circuit (438)9.4.3Hi-hat – Memory (440)9.4.4Hi-hat – Hybrid (442)9.4.5Creating a Pattern with Closed and Open Hi-hats (444)9.5The Toms (445)9.5.1Tom – Tronic (447)9.5.2Tom – Fractal (449)9.5.3Tom – Floor (453)9.5.4Tom – High (455)9.6The Percussions (456)9.6.1Percussion – Fractal (458)9.6.2Percussion – Kettle (461)9.6.3Percussion – Shaker (463)9.7The Cymbals (467)9.7.1Cymbal – Crash (469)9.7.2Cymbal – Ride (471)10Using the Bass Synth (474)10.1Bass Synth – General Handling (475)10.1.1Parameter Organization (475)10.1.2Bass Synth Parameters (477)11Working with Patterns (479)11.1Pattern Basics (479)11.1.1Pattern Editor Overview (480)11.1.2Navigating the Event Area (486)11.1.3Following the Playback Position in the Pattern (488)11.1.4Jumping to Another Playback Position in the Pattern (489)11.1.5Group View and Keyboard View (491)11.1.6Adjusting the Arrange Grid and the Pattern Length (493)11.1.7Adjusting the Step Grid and the Nudge Grid (497)11.2Recording Patterns in Real Time (501)11.2.1Recording Your Patterns Live (501)11.2.2The Record Prepare Mode (504)11.2.3Using the Metronome (505)11.2.4Recording with Count-in (506)11.2.5Quantizing while Recording (508)11.3Recording Patterns with the Step Sequencer (508)11.3.1Step Mode Basics (508)11.3.2Editing Events in Step Mode (511)11.3.3Recording Modulation in Step Mode (513)11.4Editing Events (514)11.4.1Editing Events with the Mouse: an Overview (514)11.4.2Creating Events/Notes (517)11.4.3Selecting Events/Notes (518)11.4.4Editing Selected Events/Notes (526)11.4.5Deleting Events/Notes (532)11.4.6Cut, Copy, and Paste Events/Notes (535)11.4.7Quantizing Events/Notes (538)11.4.8Quantization While Playing (540)11.4.9Doubling a Pattern (541)11.4.10Adding Variation to Patterns (541)11.5Recording and Editing Modulation (546)11.5.1Which Parameters Are Modulatable? (547)11.5.2Recording Modulation (548)11.5.3Creating and Editing Modulation in the Control Lane (550)11.6Creating MIDI Tracks from Scratch in MASCHINE (555)11.7Managing Patterns (557)11.7.1The Pattern Manager and Pattern Mode (558)11.7.2Selecting Patterns and Pattern Banks (560)11.7.3Creating Patterns (563)11.7.4Deleting Patterns (565)11.7.5Creating and Deleting Pattern Banks (566)11.7.6Naming Patterns (568)11.7.7Changing the Pattern’s Color (570)11.7.8Duplicating, Copying, and Pasting Patterns (571)11.7.9Moving Patterns (574)11.7.10Adjusting Pattern Length in Fine Increments (575)11.8Importing/Exporting Audio and MIDI to/from Patterns (576)11.8.1Exporting Audio from Patterns (576)11.8.2Exporting MIDI from Patterns (577)11.8.3Importing MIDI to Patterns (580)12Audio Routing, Remote Control, and Macro Controls (589)12.1Audio Routing in MASCHINE (590)12.1.1Sending External Audio to Sounds (591)12.1.2Configuring the Main Output of Sounds and Groups (596)12.1.3Setting Up Auxiliary Outputs for Sounds and Groups (601)12.1.4Configuring the Master and Cue Outputs of MASCHINE (605)12.1.5Mono Audio Inputs (610)12.1.5.1Configuring External Inputs for Sounds in Mix View (611)12.2Using MIDI Control and Host Automation (614)12.2.1Triggering Sounds via MIDI Notes (615)12.2.2Triggering Scenes via MIDI (622)12.2.3Controlling Parameters via MIDI and Host Automation (623)12.2.4Selecting VST/AU Plug-in Presets via MIDI Program Change (631)12.2.5Sending MIDI from Sounds (632)12.3Creating Custom Sets of Parameters with the Macro Controls (636)12.3.1Macro Control Overview (637)12.3.2Assigning Macro Controls Using the Software (638)12.3.3Assigning Macro Controls Using the Controller (644)13Controlling Your Mix (646)13.1Mix View Basics (646)13.1.1Switching between Arrange View and Mix View (646)13.1.2Mix View Elements (647)13.2The Mixer (649)13.2.1Displaying Groups vs. Displaying Sounds (650)13.2.2Adjusting the Mixer Layout (652)13.2.3Selecting Channel Strips (653)13.2.4Managing Your Channels in the Mixer (654)13.2.5Adjusting Settings in the Channel Strips (656)13.2.6Using the Cue Bus (660)13.3The Plug-in Chain (662)13.4The Plug-in Strip (663)13.4.1The Plug-in Header (665)13.4.2Panels for Drumsynths and Internal Effects (667)13.4.3Panel for the Sampler (668)13.4.4Custom Panels for Native Instruments Plug-ins (671)13.4.5Undocking a Plug-in Panel (Native Instruments and External Plug-ins Only) (675)13.5Controlling Your Mix from the Controller (677)13.5.1Navigating Your Channels in Mix Mode (678)13.5.2Adjusting the Level and Pan in Mix Mode (679)13.5.3Mute and Solo in Mix Mode (680)13.5.4Plug-in Icons in Mix Mode (680)14Using Effects (681)14.1Applying Effects to a Sound, a Group or the Master (681)14.1.1Adding an Effect (681)14.1.2Other Operations on Effects (690)14.1.3Using the Side-Chain Input (692)14.2Applying Effects to External Audio (695)14.2.1Step 1: Configure MASCHINE Audio Inputs (695)14.2.2Step 2: Set up a Sound to Receive the External Input (698)14.2.3Step 3: Load an Effect to Process an Input (700)14.3Creating a Send Effect (701)14.3.1Step 1: Set Up a Sound or Group as Send Effect (702)14.3.2Step 2: Route Audio to the Send Effect (706)14.3.3 A Few Notes on Send Effects (708)14.4Creating Multi-Effects (709)15Effect Reference (712)15.1Dynamics (713)15.1.1Compressor (713)15.1.2Gate (717)15.1.3Transient Master (721)15.1.4Limiter (723)15.1.5Maximizer (727)15.2Filtering Effects (730)15.2.1EQ (730)15.2.2Filter (733)15.2.3Cabinet (737)15.3Modulation Effects (738)15.3.1Chorus (738)15.3.2Flanger (740)15.3.3FM (742)15.3.4Freq Shifter (743)15.3.5Phaser (745)15.4Spatial and Reverb Effects (747)15.4.1Ice (747)15.4.2Metaverb (749)15.4.3Reflex (750)15.4.4Reverb (Legacy) (752)15.4.5Reverb (754)15.4.5.1Reverb Room (754)15.4.5.2Reverb Hall (757)15.4.5.3Plate Reverb (760)15.5Delays (762)15.5.1Beat Delay (762)15.5.2Grain Delay (765)15.5.3Grain Stretch (767)15.5.4Resochord (769)15.6Distortion Effects (771)15.6.1Distortion (771)15.6.2Lofi (774)15.6.3Saturator (775)15.7Perform FX (779)15.7.1Filter (780)15.7.2Flanger (782)15.7.3Burst Echo (785)15.7.4Reso Echo (787)15.7.5Ring (790)15.7.6Stutter (792)15.7.7Tremolo (795)15.7.8Scratcher (798)16Working with the Arranger (801)16.1Arranger Basics (801)16.1.1Navigating Song View (804)16.1.2Following the Playback Position in Your Project (806)16.1.3Performing with Scenes and Sections using the Pads (807)16.2Using Ideas View (811)16.2.1Scene Overview (811)16.2.2Creating Scenes (813)16.2.3Assigning and Removing Patterns (813)16.2.4Selecting Scenes (817)16.2.5Deleting Scenes (818)16.2.6Creating and Deleting Scene Banks (820)16.2.7Clearing Scenes (820)16.2.8Duplicating Scenes (821)16.2.9Reordering Scenes (822)16.2.10Making Scenes Unique (824)16.2.11Appending Scenes to Arrangement (825)16.2.12Naming Scenes (826)16.2.13Changing the Color of a Scene (827)16.3Using Song View (828)16.3.1Section Management Overview (828)16.3.2Creating Sections (833)16.3.3Assigning a Scene to a Section (834)16.3.4Selecting Sections and Section Banks (835)16.3.5Reorganizing Sections (839)16.3.6Adjusting the Length of a Section (840)16.3.6.1Adjusting the Length of a Section Using the Software (841)16.3.6.2Adjusting the Length of a Section Using the Controller (843)16.3.7Clearing a Pattern in Song View (843)16.3.8Duplicating Sections (844)16.3.8.1Making Sections Unique (845)16.3.9Removing Sections (846)16.3.10Renaming Scenes (848)16.3.11Clearing Sections (849)16.3.12Creating and Deleting Section Banks (850)16.3.13Working with Patterns in Song view (850)16.3.13.1Creating a Pattern in Song View (850)16.3.13.2Selecting a Pattern in Song View (850)16.3.13.3Clearing a Pattern in Song View (851)16.3.13.4Renaming a Pattern in Song View (851)16.3.13.5Coloring a Pattern in Song View (851)16.3.13.6Removing a Pattern in Song View (852)16.3.13.7Duplicating a Pattern in Song View (852)16.3.14Enabling Auto Length (852)16.3.15Looping (853)16.3.15.1Setting the Loop Range in the Software (854)16.4Playing with Sections (855)16.4.1Jumping to another Playback Position in Your Project (855)16.5Triggering Sections or Scenes via MIDI (856)16.6The Arrange Grid (858)16.7Quick Grid (860)17Sampling and Sample Mapping (862)17.1Opening the Sample Editor (862)17.2Recording Audio (863)17.2.1Opening the Record Page (863)17.2.2Selecting the Source and the Recording Mode (865)17.2.3Arming, Starting, and Stopping the Recording (868)17.2.5Using the Footswitch for Recording Audio (871)17.2.6Checking Your Recordings (872)17.2.7Location and Name of Your Recorded Samples (876)17.3Editing a Sample (876)17.3.1Using the Edit Page (877)17.3.2Audio Editing Functions (882)17.4Slicing a Sample (890)17.4.1Opening the Slice Page (891)17.4.2Adjusting the Slicing Settings (893)17.4.3Live Slicing (898)17.4.3.1Live Slicing Using the Controller (898)17.4.3.2Delete All Slices (899)17.4.4Manually Adjusting Your Slices (899)17.4.5Applying the Slicing (906)17.5Mapping Samples to Zones (912)17.5.1Opening the Zone Page (912)17.5.2Zone Page Overview (913)17.5.3Selecting and Managing Zones in the Zone List (915)17.5.4Selecting and Editing Zones in the Map View (920)17.5.5Editing Zones in the Sample View (924)17.5.6Adjusting the Zone Settings (927)17.5.7Adding Samples to the Sample Map (934)18Appendix: Tips for Playing Live (937)18.1Preparations (937)18.1.1Focus on the Hardware (937)18.1.2Customize the Pads of the Hardware (937)18.1.3Check Your CPU Power Before Playing (937)18.1.4Name and Color Your Groups, Patterns, Sounds and Scenes (938)18.1.5Consider Using a Limiter on Your Master (938)18.1.6Hook Up Your Other Gear and Sync It with MIDI Clock (938)18.1.7Improvise (938)18.2Basic Techniques (938)18.2.1Use Mute and Solo (938)18.2.2Use Scene Mode and Tweak the Loop Range (939)18.2.3Create Variations of Your Drum Patterns in the Step Sequencer (939)18.2.4Use Note Repeat (939)18.2.5Set Up Your Own Multi-effect Groups and Automate Them (939)18.3Special Tricks (940)18.3.1Changing Pattern Length for Variation (940)18.3.2Using Loops to Cycle Through Samples (940)18.3.3Using Loops to Cycle Through Samples (940)18.3.4Load Long Audio Files and Play with the Start Point (940)19Troubleshooting (941)19.1Knowledge Base (941)19.2Technical Support (941)19.3Registration Support (942)19.4User Forum (942)20Glossary (943)Index (951)1Welcome to MASCHINEThank you for buying MASCHINE!MASCHINE is a groove production studio that implements the familiar working style of classi-cal groove boxes along with the advantages of a computer based system. MASCHINE is ideal for making music live, as well as in the studio. It’s the hands-on aspect of a dedicated instru-ment, the MASCHINE hardware controller, united with the advanced editing features of the MASCHINE software.Creating beats is often not very intuitive with a computer, but using the MASCHINE hardware controller to do it makes it easy and fun. You can tap in freely with the pads or use Note Re-peat to jam along. Alternatively, build your beats using the step sequencer just as in classic drum machines.Patterns can be intuitively combined and rearranged on the fly to form larger ideas. You can try out several different versions of a song without ever having to stop the music.Since you can integrate it into any sequencer that supports VST, AU, or AAX plug-ins, you can reap the benefits in almost any software setup, or use it as a stand-alone application. You can sample your own material, slice loops and rearrange them easily.However, MASCHINE is a lot more than an ordinary groovebox or sampler: it comes with an inspiring 7-gigabyte library, and a sophisticated, yet easy to use tag-based Browser to give you instant access to the sounds you are looking for.What’s more, MASCHINE provides lots of options for manipulating your sounds via internal ef-fects and other sound-shaping possibilities. You can also control external MIDI hardware and 3rd-party software with the MASCHINE hardware controller, while customizing the functions of the pads, knobs and buttons according to your needs utilizing the included Controller Editor application. We hope you enjoy this fantastic instrument as much as we do. Now let’s get go-ing!—The MASCHINE team at Native Instruments.MASCHINE Documentation1.1MASCHINE DocumentationNative Instruments provide many information sources regarding MASCHINE. The main docu-ments should be read in the following sequence:1.MASCHINE Getting Started: This document provides a practical approach to MASCHINE viaa set of tutorials covering easy and more advanced tasks in order to help you familiarizeyourself with MASCHINE.2.MASCHINE Manual (this document): The MASCHINE Manual provides you with a compre-hensive description of all MASCHINE software and hardware features.Additional documentation sources provide you with details on more specific topics:▪Controller Editor Manual: Besides using your MASCHINE hardware controller together withits dedicated MASCHINE software, you can also use it as a powerful and highly versatileMIDI controller to pilot any other MIDI-capable application or device. This is made possibleby the Controller Editor software, an application that allows you to precisely define all MIDIassignments for your MASCHINE controller. The Controller Editor was installed during theMASCHINE installation procedure. For more information on this, please refer to the Con-troller Editor Manual available as a PDF file via the Help menu of Controller Editor.▪Online Support Videos: You can find a number of support videos on The Official Native In-struments Support Channel under the following URL: https:///NIsupport-EN. We recommend that you follow along with these instructions while the respective ap-plication is running on your computer.Other Online Resources:If you are experiencing problems related to your Native Instruments product that the supplied documentation does not cover, there are several ways of getting help:▪Knowledge Base▪User Forum▪Technical Support▪Registration SupportYou will find more information on these subjects in the chapter Troubleshooting.1.2Document ConventionsThis section introduces you to the signage and text highlighting used in this manual. This man-ual uses particular formatting to point out special facts and to warn you of potential issues. The icons introducing these notes let you see what kind of information is to be expected:This document uses particular formatting to point out special facts and to warn you of poten-tial issues. The icons introducing the following notes let you see what kind of information can be expected:Furthermore, the following formatting is used:▪Text appearing in (drop-down) menus (such as Open…, Save as… etc.) in the software and paths to locations on your hard disk or other storage devices is printed in italics.▪Text appearing elsewhere (labels of buttons, controls, text next to checkboxes etc.) in the software is printed in blue. Whenever you see this formatting applied, you will find the same text appearing somewhere on the screen.▪Text appearing on the displays of the controller is printed in light grey. Whenever you see this formatting applied, you will find the same text on a controller display.▪Text appearing on labels of the hardware controller is printed in orange. Whenever you see this formatting applied, you will find the same text on the controller.▪Important names and concepts are printed in bold.▪References to keys on your computer’s keyboard you’ll find put in square brackets (e.g.,“Press [Shift] + [Enter]”).►Single instructions are introduced by this play button type arrow.→Results of actions are introduced by this smaller arrow.Naming ConventionThroughout the documentation we will refer to MASCHINE controller (or just controller) as the hardware controller and MASCHINE software as the software installed on your computer.The term “effect” will sometimes be abbreviated as “FX” when referring to elements in the MA-SCHINE software and hardware. These terms have the same meaning.Button Combinations and Shortcuts on Your ControllerMost instructions will use the “+” sign to indicate buttons (or buttons and pads) that must be pressed simultaneously, starting with the button indicated first. E.g., an instruction such as:“Press SHIFT + PLAY”means:1.Press and hold SHIFT.2.While holding SHIFT, press PLAY and release it.3.Release SHIFT.Unlabeled Buttons on the ControllerThe buttons and knobs above and below the displays on your MASCHINE controller do not have labels.。
在这个网站里,你能快速找到电影中那些不知道名字的歌曲

在这个⽹站⾥,你能快速找到电影中那些不知道名字的歌曲通常⼤家寻找新歌的⽅式,可能就是打开⼀个播放器,然后播放⼀个最新歌曲列表,接着开始不断切歌,直到发现⾃⼰喜欢的,不过有时候我们也会被影视剧中偶然出现的歌曲所吸引,⽐如《银河护卫队》中星爵听的那⾸《Come and Get Your Love》,虽然歌曲是电影⼈物听的,但播放出来之后,却连观众也喜欢上了。
然⽽对国内观众来说,想找到这种欧美影视剧中的英⽂歌曲还是有点困难,既不知道名字,也记不住歌词,就算去搜索也未必搜得到,其实想找到这种影视剧中的歌曲也有简单⽅法,⽐如通过「tunefind」这个⽹站就能直接找到⼤量影视剧中的歌曲。
「tunefind」是⼀个专门收录欧美影视剧歌曲的⽹站,⽹站中的所有歌曲都会按照剧⽬进⾏归类,⽽相关的剧⽬也会按照热门程度、是否正在播放等条件进⾏排列,左右滑动即可进⾏翻看。
收录的歌曲不仅仅是剧中的主题曲、⽚尾曲,只要是在剧中出现过,哪怕只是很短暂的背景⾳乐,都会被收录进来,⽐如我们可以看到美剧《闪电侠》中共有283⾸歌,《权⼒的游戏》更多达611⾸歌。
点击进⼊剧⽬即可查看详细的歌曲列表,如果是拍了很多季的美剧,还会再按照第⼏季、第⼏集的⽅式进⾏细分,⽅便⼤家可以准确找到⾃⼰想听的那⾸歌。
歌曲可以在⽹页上直接点击播放,并且每⾸歌也会有相应的注释,说明这⾸歌是在剧中的什么情节时出现的,不过需要注意的是,⽹站中虽然收录了很多歌曲,但有不少是⽹友编辑上传的,如果歌曲确实正确⽆误,则会显⽰绿⾊的「√」,如果没有这个符号的话,则表⽰存疑,还需要仔细听⼀下才知道。
⽹站中歌曲和剧⽬的更新速度很快,很多最新上映的电影或电视剧都可以找到,⽐如最新上映的《终结者:⿊暗命运》就已经被收录进来了。
同时除了影视剧之外,⽹站中还有综艺专区和游戏专区,当然这些内容也都是来⾃于欧美地区,不过相⽐之下,游戏专区的内容可能更⼴为⼈知⼀些,⽐如最新的游戏《死亡搁浅》、《⽆主之地3》、《FIFA20》等,都是玩家们⽿熟能详的游戏作品。
Series 6 电磁炉说明书
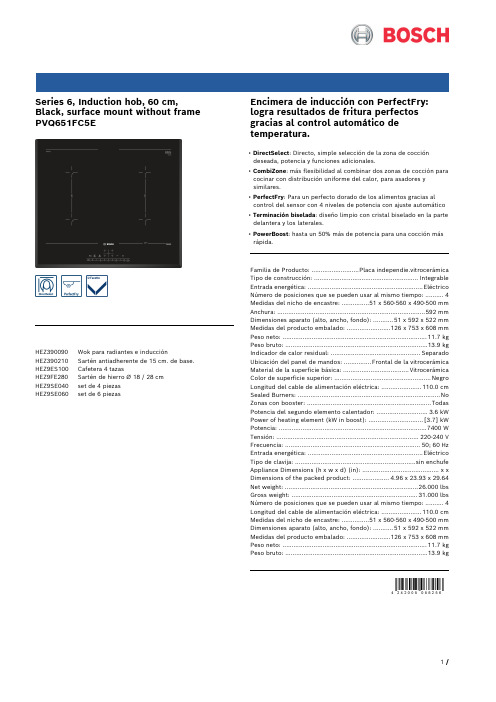
Series 6, Induction hob, 60 cm, Black, surface mount without frame PVQ651FC5EHEZ390090 Wok para radiantes e inducciónHEZ390210 Sartén antiadherente de 15 cm. de base. HEZ9ES100 Cafetera 4 tazasHEZ9FE280 Sartén de hierro Ø 18 / 28 cmHEZ9SE040 set de 4 piezasHEZ9SE060 set de 6 piezas Encimera de inducción con PerfectFry: logra resultados de fritura perfectos gracias al control automático de temperatura.• DirectSelect: Directo, simple selección de la zona de cocción deseada, potencia y funciones adicionales.• CombiZone: más flexibilidad al combinar dos zonas de cocción para cocinar con distribución uniforme del calor, para asadores y similares.• PerfectFry: Para un perfecto dorado de los alimentos gracias al control del sensor con 4 niveles de potencia con ajuste automático• Terminación biselada: diseño limpio con cristal biselado en la parte delantera y los laterales.• PowerBoost: hasta un 50% más de potencia para una cocción más rápida.Familia de Producto: ..........................Placa independie.vitrocerámica Tipo de construcción: .........................................................Integrable Entrada energética: ...............................................................Eléctrico Número de posiciones que se pueden usar al mismo tiempo: . (4)Medidas del nicho de encastre: ...............51 x 560-560 x 490-500 mm Anchura: .................................................................................592 mm Dimensiones aparato (alto, ancho, fondo): ...........51 x 592 x 522 mm Medidas del producto embalado: ........................126 x 753 x 608 mm Peso neto: ...............................................................................11.7 kg Peso bruto: ..............................................................................13.9 kg Indicador de calor residual: .................................................Separado Ubicación del panel de mandos: ...............Frontal de la vitrocerámica Material de la superficie básica: ....................................Vitrocerámica Color de superficie superior: .....................................................Negro Longitud del cable de alimentación eléctrica: ......................110.0 cm Sealed Burners: ..............................................................................No Zonas con booster: ....................................................................Todas Potencia del segundo elemento calentador: ............................3.6 kW Power of heating element (kW in boost): ..............................[3.7] kW Potencia: .................................................................................7400 W Tensión: ..............................................................................220-240 V Frecuencia: ..........................................................................50; 60 Hz Entrada energética: ...............................................................Eléctrico Tipo de clavija: ..................................................................sin enchufe Appliance Dimensions (h x w x d) (in): ..........................................x x Dimensions of the packed product: ....................4.96 x 23.93 x 29.64 Net weight: .........................................................................26.000 lbs Gross weight: .....................................................................31.000 lbs Número de posiciones que se pueden usar al mismo tiempo: . (4)Longitud del cable de alimentación eléctrica: ......................110.0 cm Medidas del nicho de encastre: ...............51 x 560-560 x 490-500 mm Dimensiones aparato (alto, ancho, fondo): ...........51 x 592 x 522 mm Medidas del producto embalado: ........................126 x 753 x 608 mm Peso neto: ...............................................................................11.7 kg Peso bruto: ..............................................................................13.9 kgSeries 6, Induction hob, 60 cm,Black, surface mount without frame PVQ651FC5EEncimera de inducción con PerfectFry: logra resultados de fritura perfectos gracias al control automático de temperatura.Prestaciones profesionalesDiseño:- Terminación biseladaRapidez:- Función Sprint en todas las zonasConfort:- 4 zonas de inducción- DirectSelect con 17 niveles de cocción- 2 Combi zones- 2-steps- Sensores touchControl- Programación de tiempo de cocción para cada zona y avisador acústico- Avisador acústico- sí- síPotencia y tamaño:- Regulación electrónica con 17 niveles de potenciaSeguridad:- Indicador de calor residual dual (H/h)- Main Switch- Detección de recipiente- Posibilidad de limitar la potencia total de la encimera- Desconexión de seguridad de la placa- Bloqueo de seguridad para niños automático o manual- Función Clean: bloqueo temporal del control- Display de consumo de energíaMedidas:- Dimensiones para instalación: (Al/An/F) 51 mm x 560 mm x 490 mm- Dimensiones del producto: (An/F) 592 mm x 522 mm- Min. espesor de mesa: 16 mm- Cable incluido- Potencia de conexión: 7.4 kwSeries 6, Induction hob, 60 cm, Black, surface mount without frame PVQ651FC5E。
极限交换机VDX6740和VDX6740T产品介绍说明书

The VDX 674 0 T-1G ( Fig ure 3) offers 4 8 10 0 0 BA SE-T p ort s and t w o 4 0 Gb E QSFP+ p ort s. Each 4 0 Gb E p ort can b e b roken out int o four ind ep end ent 10 Gb E SFP+ p ort s, p rovid ing an ad d it ional eig ht 10 Gb E SFP+ p ort s for up link. A ll 4 8 10 0 0 BA SE-T p ort s can b e up g rad ed t o 4 8 10 GBA SE-T p ort s via t he Cap acit y on Dem and (CoD) soft w are license. Tw o 4 0 Gb E p ort s are enab led as p art of t he b ase license. The ad d it ional t w o 4 0 Gb E p ort s can b e up g rad ed via t he Port s on Dem and ( PoD) soft w are license.
- Meet s t od ay?s ap p licat ion d em and s w it h high perform ance and low latency
- Delivers line-rate t hroughput for all p ort s and p acket sizes
Dat a Sheet
OSHA现场作业手册说明书

DIRECTIVE NUMBER: CPL 02-00-150 EFFECTIVE DATE: April 22, 2011 SUBJECT: Field Operations Manual (FOM)ABSTRACTPurpose: This instruction cancels and replaces OSHA Instruction CPL 02-00-148,Field Operations Manual (FOM), issued November 9, 2009, whichreplaced the September 26, 1994 Instruction that implemented the FieldInspection Reference Manual (FIRM). The FOM is a revision of OSHA’senforcement policies and procedures manual that provides the field officesa reference document for identifying the responsibilities associated withthe majority of their inspection duties. This Instruction also cancels OSHAInstruction FAP 01-00-003 Federal Agency Safety and Health Programs,May 17, 1996 and Chapter 13 of OSHA Instruction CPL 02-00-045,Revised Field Operations Manual, June 15, 1989.Scope: OSHA-wide.References: Title 29 Code of Federal Regulations §1903.6, Advance Notice ofInspections; 29 Code of Federal Regulations §1903.14, Policy RegardingEmployee Rescue Activities; 29 Code of Federal Regulations §1903.19,Abatement Verification; 29 Code of Federal Regulations §1904.39,Reporting Fatalities and Multiple Hospitalizations to OSHA; and Housingfor Agricultural Workers: Final Rule, Federal Register, March 4, 1980 (45FR 14180).Cancellations: OSHA Instruction CPL 02-00-148, Field Operations Manual, November9, 2009.OSHA Instruction FAP 01-00-003, Federal Agency Safety and HealthPrograms, May 17, 1996.Chapter 13 of OSHA Instruction CPL 02-00-045, Revised FieldOperations Manual, June 15, 1989.State Impact: Notice of Intent and Adoption required. See paragraph VI.Action Offices: National, Regional, and Area OfficesOriginating Office: Directorate of Enforcement Programs Contact: Directorate of Enforcement ProgramsOffice of General Industry Enforcement200 Constitution Avenue, NW, N3 119Washington, DC 20210202-693-1850By and Under the Authority ofDavid Michaels, PhD, MPHAssistant SecretaryExecutive SummaryThis instruction cancels and replaces OSHA Instruction CPL 02-00-148, Field Operations Manual (FOM), issued November 9, 2009. The one remaining part of the prior Field Operations Manual, the chapter on Disclosure, will be added at a later date. This Instruction also cancels OSHA Instruction FAP 01-00-003 Federal Agency Safety and Health Programs, May 17, 1996 and Chapter 13 of OSHA Instruction CPL 02-00-045, Revised Field Operations Manual, June 15, 1989. This Instruction constitutes OSHA’s general enforcement policies and procedures manual for use by the field offices in conducting inspections, issuing citations and proposing penalties.Significant Changes∙A new Table of Contents for the entire FOM is added.∙ A new References section for the entire FOM is added∙ A new Cancellations section for the entire FOM is added.∙Adds a Maritime Industry Sector to Section III of Chapter 10, Industry Sectors.∙Revises sections referring to the Enhanced Enforcement Program (EEP) replacing the information with the Severe Violator Enforcement Program (SVEP).∙Adds Chapter 13, Federal Agency Field Activities.∙Cancels OSHA Instruction FAP 01-00-003, Federal Agency Safety and Health Programs, May 17, 1996.DisclaimerThis manual is intended to provide instruction regarding some of the internal operations of the Occupational Safety and Health Administration (OSHA), and is solely for the benefit of the Government. No duties, rights, or benefits, substantive or procedural, are created or implied by this manual. The contents of this manual are not enforceable by any person or entity against the Department of Labor or the United States. Statements which reflect current Occupational Safety and Health Review Commission or court precedents do not necessarily indicate acquiescence with those precedents.Table of ContentsCHAPTER 1INTRODUCTIONI.PURPOSE. ........................................................................................................... 1-1 II.SCOPE. ................................................................................................................ 1-1 III.REFERENCES .................................................................................................... 1-1 IV.CANCELLATIONS............................................................................................. 1-8 V. ACTION INFORMATION ................................................................................. 1-8A.R ESPONSIBLE O FFICE.......................................................................................................................................... 1-8B.A CTION O FFICES. .................................................................................................................... 1-8C. I NFORMATION O FFICES............................................................................................................ 1-8 VI. STATE IMPACT. ................................................................................................ 1-8 VII.SIGNIFICANT CHANGES. ............................................................................... 1-9 VIII.BACKGROUND. ................................................................................................. 1-9 IX. DEFINITIONS AND TERMINOLOGY. ........................................................ 1-10A.T HE A CT................................................................................................................................................................. 1-10B. C OMPLIANCE S AFETY AND H EALTH O FFICER (CSHO). ...........................................................1-10B.H E/S HE AND H IS/H ERS ..................................................................................................................................... 1-10C.P ROFESSIONAL J UDGMENT............................................................................................................................... 1-10E. W ORKPLACE AND W ORKSITE ......................................................................................................................... 1-10CHAPTER 2PROGRAM PLANNINGI.INTRODUCTION ............................................................................................... 2-1 II.AREA OFFICE RESPONSIBILITIES. .............................................................. 2-1A.P ROVIDING A SSISTANCE TO S MALL E MPLOYERS. ...................................................................................... 2-1B.A REA O FFICE O UTREACH P ROGRAM. ............................................................................................................. 2-1C. R ESPONDING TO R EQUESTS FOR A SSISTANCE. ............................................................................................ 2-2 III. OSHA COOPERATIVE PROGRAMS OVERVIEW. ...................................... 2-2A.V OLUNTARY P ROTECTION P ROGRAM (VPP). ........................................................................... 2-2B.O NSITE C ONSULTATION P ROGRAM. ................................................................................................................ 2-2C.S TRATEGIC P ARTNERSHIPS................................................................................................................................. 2-3D.A LLIANCE P ROGRAM ........................................................................................................................................... 2-3 IV. ENFORCEMENT PROGRAM SCHEDULING. ................................................ 2-4A.G ENERAL ................................................................................................................................................................. 2-4B.I NSPECTION P RIORITY C RITERIA. ..................................................................................................................... 2-4C.E FFECT OF C ONTEST ............................................................................................................................................ 2-5D.E NFORCEMENT E XEMPTIONS AND L IMITATIONS. ....................................................................................... 2-6E.P REEMPTION BY A NOTHER F EDERAL A GENCY ........................................................................................... 2-6F.U NITED S TATES P OSTAL S ERVICE. .................................................................................................................. 2-7G.H OME-B ASED W ORKSITES. ................................................................................................................................ 2-8H.I NSPECTION/I NVESTIGATION T YPES. ............................................................................................................... 2-8 V.UNPROGRAMMED ACTIVITY – HAZARD EVALUATION AND INSPECTION SCHEDULING ............................................................................ 2-9 VI.PROGRAMMED INSPECTIONS. ................................................................... 2-10A.S ITE-S PECIFIC T ARGETING (SST) P ROGRAM. ............................................................................................. 2-10B.S CHEDULING FOR C ONSTRUCTION I NSPECTIONS. ..................................................................................... 2-10C.S CHEDULING FOR M ARITIME I NSPECTIONS. ............................................................................. 2-11D.S PECIAL E MPHASIS P ROGRAMS (SEP S). ................................................................................... 2-12E.N ATIONAL E MPHASIS P ROGRAMS (NEP S) ............................................................................... 2-13F.L OCAL E MPHASIS P ROGRAMS (LEP S) AND R EGIONAL E MPHASIS P ROGRAMS (REP S) ............ 2-13G.O THER S PECIAL P ROGRAMS. ............................................................................................................................ 2-13H.I NSPECTION S CHEDULING AND I NTERFACE WITH C OOPERATIVE P ROGRAM P ARTICIPANTS ....... 2-13CHAPTER 3INSPECTION PROCEDURESI.INSPECTION PREPARATION. .......................................................................... 3-1 II.INSPECTION PLANNING. .................................................................................. 3-1A.R EVIEW OF I NSPECTION H ISTORY .................................................................................................................... 3-1B.R EVIEW OF C OOPERATIVE P ROGRAM P ARTICIPATION .............................................................................. 3-1C.OSHA D ATA I NITIATIVE (ODI) D ATA R EVIEW .......................................................................................... 3-2D.S AFETY AND H EALTH I SSUES R ELATING TO CSHO S.................................................................. 3-2E.A DVANCE N OTICE. ................................................................................................................................................ 3-3F.P RE-I NSPECTION C OMPULSORY P ROCESS ...................................................................................................... 3-5G.P ERSONAL S ECURITY C LEARANCE. ................................................................................................................. 3-5H.E XPERT A SSISTANCE. ........................................................................................................................................... 3-5 III. INSPECTION SCOPE. ......................................................................................... 3-6A.C OMPREHENSIVE ................................................................................................................................................... 3-6B.P ARTIAL. ................................................................................................................................................................... 3-6 IV. CONDUCT OF INSPECTION .............................................................................. 3-6A.T IME OF I NSPECTION............................................................................................................................................. 3-6B.P RESENTING C REDENTIALS. ............................................................................................................................... 3-6C.R EFUSAL TO P ERMIT I NSPECTION AND I NTERFERENCE ............................................................................. 3-7D.E MPLOYEE P ARTICIPATION. ............................................................................................................................... 3-9E.R ELEASE FOR E NTRY ............................................................................................................................................ 3-9F.B ANKRUPT OR O UT OF B USINESS. .................................................................................................................... 3-9G.E MPLOYEE R ESPONSIBILITIES. ................................................................................................. 3-10H.S TRIKE OR L ABOR D ISPUTE ............................................................................................................................. 3-10I. V ARIANCES. .......................................................................................................................................................... 3-11 V. OPENING CONFERENCE. ................................................................................ 3-11A.G ENERAL ................................................................................................................................................................ 3-11B.R EVIEW OF A PPROPRIATION A CT E XEMPTIONS AND L IMITATION. ..................................................... 3-13C.R EVIEW S CREENING FOR P ROCESS S AFETY M ANAGEMENT (PSM) C OVERAGE............................. 3-13D.R EVIEW OF V OLUNTARY C OMPLIANCE P ROGRAMS. ................................................................................ 3-14E.D ISRUPTIVE C ONDUCT. ...................................................................................................................................... 3-15F.C LASSIFIED A REAS ............................................................................................................................................. 3-16VI. REVIEW OF RECORDS. ................................................................................... 3-16A.I NJURY AND I LLNESS R ECORDS...................................................................................................................... 3-16B.R ECORDING C RITERIA. ...................................................................................................................................... 3-18C. R ECORDKEEPING D EFICIENCIES. .................................................................................................................. 3-18 VII. WALKAROUND INSPECTION. ....................................................................... 3-19A.W ALKAROUND R EPRESENTATIVES ............................................................................................................... 3-19B.E VALUATION OF S AFETY AND H EALTH M ANAGEMENT S YSTEM. ....................................................... 3-20C.R ECORD A LL F ACTS P ERTINENT TO A V IOLATION. ................................................................................. 3-20D.T ESTIFYING IN H EARINGS ................................................................................................................................ 3-21E.T RADE S ECRETS. ................................................................................................................................................. 3-21F.C OLLECTING S AMPLES. ..................................................................................................................................... 3-22G.P HOTOGRAPHS AND V IDEOTAPES.................................................................................................................. 3-22H.V IOLATIONS OF O THER L AWS. ....................................................................................................................... 3-23I.I NTERVIEWS OF N ON-M ANAGERIAL E MPLOYEES .................................................................................... 3-23J.M ULTI-E MPLOYER W ORKSITES ..................................................................................................................... 3-27 K.A DMINISTRATIVE S UBPOENA.......................................................................................................................... 3-27 L.E MPLOYER A BATEMENT A SSISTANCE. ........................................................................................................ 3-27 VIII. CLOSING CONFERENCE. .............................................................................. 3-28A.P ARTICIPANTS. ..................................................................................................................................................... 3-28B.D ISCUSSION I TEMS. ............................................................................................................................................ 3-28C.A DVICE TO A TTENDEES .................................................................................................................................... 3-29D.P ENALTIES............................................................................................................................................................. 3-30E.F EASIBLE A DMINISTRATIVE, W ORK P RACTICE AND E NGINEERING C ONTROLS. ............................ 3-30F.R EDUCING E MPLOYEE E XPOSURE. ................................................................................................................ 3-32G.A BATEMENT V ERIFICATION. ........................................................................................................................... 3-32H.E MPLOYEE D ISCRIMINATION .......................................................................................................................... 3-33 IX. SPECIAL INSPECTION PROCEDURES. ...................................................... 3-33A.F OLLOW-UP AND M ONITORING I NSPECTIONS............................................................................................ 3-33B.C ONSTRUCTION I NSPECTIONS ......................................................................................................................... 3-34C. F EDERAL A GENCY I NSPECTIONS. ................................................................................................................. 3-35CHAPTER 4VIOLATIONSI. BASIS OF VIOLATIONS ..................................................................................... 4-1A.S TANDARDS AND R EGULATIONS. .................................................................................................................... 4-1B.E MPLOYEE E XPOSURE. ........................................................................................................................................ 4-3C.R EGULATORY R EQUIREMENTS. ........................................................................................................................ 4-6D.H AZARD C OMMUNICATION. .............................................................................................................................. 4-6E. E MPLOYER/E MPLOYEE R ESPONSIBILITIES ................................................................................................... 4-6 II. SERIOUS VIOLATIONS. .................................................................................... 4-8A.S ECTION 17(K). ......................................................................................................................... 4-8B.E STABLISHING S ERIOUS V IOLATIONS ............................................................................................................ 4-8C. F OUR S TEPS TO BE D OCUMENTED. ................................................................................................................... 4-8 III. GENERAL DUTY REQUIREMENTS ............................................................. 4-14A.E VALUATION OF G ENERAL D UTY R EQUIREMENTS ................................................................................. 4-14B.E LEMENTS OF A G ENERAL D UTY R EQUIREMENT V IOLATION.............................................................. 4-14C. U SE OF THE G ENERAL D UTY C LAUSE ........................................................................................................ 4-23D.L IMITATIONS OF U SE OF THE G ENERAL D UTY C LAUSE. ..............................................................E.C LASSIFICATION OF V IOLATIONS C ITED U NDER THE G ENERAL D UTY C LAUSE. ..................F. P ROCEDURES FOR I MPLEMENTATION OF S ECTION 5(A)(1) E NFORCEMENT ............................ 4-25 4-27 4-27IV.OTHER-THAN-SERIOUS VIOLATIONS ............................................... 4-28 V.WILLFUL VIOLATIONS. ......................................................................... 4-28A.I NTENTIONAL D ISREGARD V IOLATIONS. ..........................................................................................4-28B.P LAIN I NDIFFERENCE V IOLATIONS. ...................................................................................................4-29 VI. CRIMINAL/WILLFUL VIOLATIONS. ................................................... 4-30A.A REA D IRECTOR C OORDINATION ....................................................................................................... 4-31B.C RITERIA FOR I NVESTIGATING P OSSIBLE C RIMINAL/W ILLFUL V IOLATIONS ........................ 4-31C. W ILLFUL V IOLATIONS R ELATED TO A F ATALITY .......................................................................... 4-32 VII. REPEATED VIOLATIONS. ...................................................................... 4-32A.F EDERAL AND S TATE P LAN V IOLATIONS. ........................................................................................4-32B.I DENTICAL S TANDARDS. .......................................................................................................................4-32C.D IFFERENT S TANDARDS. .......................................................................................................................4-33D.O BTAINING I NSPECTION H ISTORY. .....................................................................................................4-33E.T IME L IMITATIONS..................................................................................................................................4-34F.R EPEATED V. F AILURE TO A BATE....................................................................................................... 4-34G. A REA D IRECTOR R ESPONSIBILITIES. .............................................................................. 4-35 VIII. DE MINIMIS CONDITIONS. ................................................................... 4-36A.C RITERIA ................................................................................................................................................... 4-36B.P ROFESSIONAL J UDGMENT. ..................................................................................................................4-37C. A REA D IRECTOR R ESPONSIBILITIES. .............................................................................. 4-37 IX. CITING IN THE ALTERNATIVE ............................................................ 4-37 X. COMBINING AND GROUPING VIOLATIONS. ................................... 4-37A.C OMBINING. ..............................................................................................................................................4-37B.G ROUPING. ................................................................................................................................................4-38C. W HEN N OT TO G ROUP OR C OMBINE. ................................................................................................4-38 XI. HEALTH STANDARD VIOLATIONS ....................................................... 4-39A.C ITATION OF V ENTILATION S TANDARDS ......................................................................................... 4-39B.V IOLATIONS OF THE N OISE S TANDARD. ...........................................................................................4-40 XII. VIOLATIONS OF THE RESPIRATORY PROTECTION STANDARD(§1910.134). ....................................................................................................... XIII. VIOLATIONS OF AIR CONTAMINANT STANDARDS (§1910.1000) ... 4-43 4-43A.R EQUIREMENTS UNDER THE STANDARD: .................................................................................................. 4-43B.C LASSIFICATION OF V IOLATIONS OF A IR C ONTAMINANT S TANDARDS. ......................................... 4-43 XIV. CITING IMPROPER PERSONAL HYGIENE PRACTICES. ................... 4-45A.I NGESTION H AZARDS. .................................................................................................................................... 4-45B.A BSORPTION H AZARDS. ................................................................................................................................ 4-46C.W IPE S AMPLING. ............................................................................................................................................. 4-46D.C ITATION P OLICY ............................................................................................................................................ 4-46 XV. BIOLOGICAL MONITORING. ...................................................................... 4-47CHAPTER 5CASE FILE PREPARATION AND DOCUMENTATIONI.INTRODUCTION ............................................................................................... 5-1 II.INSPECTION CONDUCTED, CITATIONS BEING ISSUED. .................... 5-1A.OSHA-1 ................................................................................................................................... 5-1B.OSHA-1A. ............................................................................................................................... 5-1C. OSHA-1B. ................................................................................................................................ 5-2 III.INSPECTION CONDUCTED BUT NO CITATIONS ISSUED .................... 5-5 IV.NO INSPECTION ............................................................................................... 5-5 V. HEALTH INSPECTIONS. ................................................................................. 5-6A.D OCUMENT P OTENTIAL E XPOSURE. ............................................................................................................... 5-6B.E MPLOYER’S O CCUPATIONAL S AFETY AND H EALTH S YSTEM. ............................................................. 5-6 VI. AFFIRMATIVE DEFENSES............................................................................. 5-8A.B URDEN OF P ROOF. .............................................................................................................................................. 5-8B.E XPLANATIONS. ..................................................................................................................................................... 5-8 VII. INTERVIEW STATEMENTS. ........................................................................ 5-10A.G ENERALLY. ......................................................................................................................................................... 5-10B.CSHO S SHALL OBTAIN WRITTEN STATEMENTS WHEN: .......................................................................... 5-10C.L ANGUAGE AND W ORDING OF S TATEMENT. ............................................................................................. 5-11D.R EFUSAL TO S IGN S TATEMENT ...................................................................................................................... 5-11E.V IDEO AND A UDIOTAPED S TATEMENTS. ..................................................................................................... 5-11F.A DMINISTRATIVE D EPOSITIONS. .............................................................................................5-11 VIII. PAPERWORK AND WRITTEN PROGRAM REQUIREMENTS. .......... 5-12 IX.GUIDELINES FOR CASE FILE DOCUMENTATION FOR USE WITH VIDEOTAPES AND AUDIOTAPES .............................................................. 5-12 X.CASE FILE ACTIVITY DIARY SHEET. ..................................................... 5-12 XI. CITATIONS. ..................................................................................................... 5-12A.S TATUTE OF L IMITATIONS. .............................................................................................................................. 5-13B.I SSUING C ITATIONS. ........................................................................................................................................... 5-13C.A MENDING/W ITHDRAWING C ITATIONS AND N OTIFICATION OF P ENALTIES. .................................. 5-13D.P ROCEDURES FOR A MENDING OR W ITHDRAWING C ITATIONS ............................................................ 5-14 XII. INSPECTION RECORDS. ............................................................................... 5-15A.G ENERALLY. ......................................................................................................................................................... 5-15B.R ELEASE OF I NSPECTION I NFORMATION ..................................................................................................... 5-15C. C LASSIFIED AND T RADE S ECRET I NFORMATION ...................................................................................... 5-16。
教你用CE消除歌曲中的原唱声 口令password

教你用CE消除歌曲中的原唱声很多朋友都在为自己喜欢的歌曲找不到伴奏而烦恼,以下就系统的介绍一下怎么用 Cool Edit Pro (以下简称 CE )来消除歌曲中原唱声以达到伴奏带的效果。
只要有歌曲的原唱音频文件,就能很快的制作成伴奏。
能消原唱的软件很多,而制作出来的伴奏也有所不同,但都达不到理想的效果。
消除原唱后得出的伴奏不能完全做到原版伴奏的效果,一般都会残留部分原唱的声音,而且有些音频都会有所损伤。
所以我们介绍的只是消除原唱和以最大限度来保证伴奏的质量。
但若想得到更高质量的伴奏,还得靠大家自身多多练习和摸索了。
这里我们仅就 CE 作下介绍。
CE 不是自动化的软件,所以音频处理效果如何,最主要的还是要靠大家自己去听。
如果有兴趣的话,可以花些时间多多摸索经验,以求达到自己想要的音质。
不管怎样,仍旧希望这个方法能给大家带来一点帮助。
一、为什么能消原唱假设我们的电脑里有一个音频文件,不管是 mp3 、 wma 或是 wav 都好,通常就是一首歌曲。
我们听到的一首歌曲中有原唱、伴奏。
而原唱的特征大致分为两种: 1 、人声的声像位置在整个声场的中央(左右声道平衡分布); 2 、声音频率集中在中频和高频部分。
看完这些后,我们就知道要把“左右声道的对等声音且频率集中在中频和高频部分的声音”消除掉。
二、用 Cool Edit Pro 消除原唱的基本方法“消除原唱”也就是通常我们看到的“消音”。
用 CE 消除原唱,方法其实很简单,但想要提高它的音质还是得下点功夫哦。
我们这里所说的“消音”只是 CE 菜单中的一个独立功能,选择并使用就立即会有结果。
但是要想得到更好的效果,还得进行更多细致的音频处理和调整。
OK ,下面介绍具体实施步骤。
1 、首先进入 CE 的“单轨”编辑模式界面。
“文件”→“打开”调入一个音频文件。
这里以庾澄庆的《命中注定》为例,文件名为“命中注定 .mp3 ”。
2 、打开音频后选择“效果”→“波形振幅”→“声道重混缩”,在打开的窗口中选择“预置”里面的“ Vocal Cut ”见(图 1 ),保持对话框上的默认设置,点“确定”按钮。
欧美硬朗灰色通用模板

YOUR TITLE
Lorem ipsum dolor sit amet, consectetur adipiscing elit,
sed do eiusmod tempor incididunt ut labore et
YOUR TITLE
03
YOUR TITLE
Lorem ipsum dolor sit amet, consectetur adipiscing elit,
30%
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor
50%
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor
YOUR TITLE
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt
您的标题
Lorem ipsum dolor sit amet, consectetur
Lorem ipsum dolor sit amet, consectetur adipiscing elit,
magna aliqua. Ut enim ad minim
您的标题
Lorem ipsum dolor sit amet, consectetur
YOUR TITLE HERE
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor
DS2208数字扫描器产品参考指南说明书

-05 Rev. A
6/2018
Rev. B Software Updates Added: - New Feedback email address. - Grid Matrix parameters - Febraban parameter - USB HID POS (formerly known as Microsoft UWP USB) - Product ID (PID) Type - Product ID (PID) Value - ECLevel
-06 Rev. A
10/2018 - Added Grid Matrix sample bar code. - Moved 123Scan chapter.
-07 Rev. A
11/2019
Added: - SITA and ARINC parameters. - IBM-485 Specification Version.
No part of this publication may be reproduced or used in any form, or by any electrical or mechanical means, without permission in writing from Zebra. This includes electronic or mechanical means, such as photocopying, recording, or information storage and retrieval systems. The material in this manual is subject to change without notice.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Computers&Operations Research29(2002)1843–1858/locate/dsw Search for all d-Mincuts of a limited- ow networkWei-Chang Yeh∗Department of Industrial Engineering,Feng Chia University,P.O.Box67-100,Taichung407,TaiwanReceived1May2000;received in revised form1February2001AbstractIn this presentation,we developed an intuitive algorithm based on some simple concepts that were found in this study.It is more e cient than the best-known existing algorithm.The computational complexity of the proposed algorithm is analyzed and compared with the existing methods.One example is illustrated to show how all d-MCs are generated by our proposed algorithm.As evidence of the utility of the proposed approach,extensive computational results on random test problems are presented.Our results compare favorably with previously developed algorithms in the literature.Scope and purposeMany real-world systems are multistate systems composed of multistate components in which the reliability can be computed in terms of the lower bound points of level d,called d-Mincuts(d-MCs). Such systems(electric power,transportation,etc.)may be regarded as ow networks whose arcs have independent,discrete,limited and multivalued random capacities.In this study,all MCs are assumed to be known in advance and we focused on how toÿnd the entire d-MCs before calculating the reliability value of a network.Analysis of our algorithm and comparison to existing algorithms shows that our proposed method has the following advantages:(1)the number of d-MC candidates is less than those in the existing methods,(2)the d-MC candidates are simpler toÿnd and verify,which makes the method more e ective than the existing methods,and(3)our method is easier to understand and implement.? 2002Elsevier Science Ltd.All rights reserved.Keywords:Reliability;Limited- ow network;d-MC;Max- ow1.IntroductionMultistate systems are more practical and reasonable in many real-life situations.Analysis of multistate systems extends to binary-state systems and has become a new subject in system ∗Tel.:+886-4-2321-6168;fax:886-4-2208-4168.E-mail address:wcyeh@.tw(W.-C.Yeh).0305-0548/02/$-see front matter?2002Elsevier Science Ltd.All rights reserved.PII:S0305-0548(01)00062-41844W.-C.Yeh/Computers&Operations Research29(2002)1843–1858reliability.A limited- ow network is a multistate system composed of multistate components. For example,an electric power transmission and distribution system may supply power at dif-ferent levels and only certain levels will satisfy the load(or demand,stress)level.The reliability evaluation of a multistate system is NP-hard[11–13]but practical.Several authors have presented some approaches to evaluate the probability that the system capacity level is d[1–10,14–21].Most of these methods are formulated in terms of either d-MPs or d-MCs.However,it seems that only Xue[5,6],Jane et al.[1,17],and Yeh[7,8]have presented algorithms to search for all d-MPs and=or d-MCs for a general multistate case.Many of the steps in their method seem to be super uous when applied to limited- ow networks[1,5,6,8]. Even for a smaller sized problem,it is still impossible to evaluate the reliability of a multistate system in a reasonable time using their algorithm.The need for an e cient and intuitive method to search for all d-MCs thus arises.The purpose of this paper is to develop an intuitive algorithm based on some simple concepts that were found in this study to search for all d-MCs.It is more e cient than the best-known existing algorithm.The computational complexity of the proposed algorithm is analyzed and compared with the existing methods.As evidence of the utility of the proposed approach,we present extensive computational results on random test problems.The results compare favorably with previously developed algorithms in the literature.The paper is organized as follows.Section2describes the notation,nomenclature and as-sumptions required.Section3contains the formulation for d-MCs in a limited- ow network, and some lemmas and theorems are discussed.In Section4,the best-known algorithm[8] (Algorithm0)is discussed.Section5describes our main algorithm(Algorithm1)which is an improvement upon the best-known algorithm(Algorithm0)using some simple concepts that are discussed in Section3.Section6illustrates how to generate all d-MCs in a network through a numerical example using putational experiments are provided in Section7. Concluding remarks are given in Section8.2.Notation,nomenclature and assumptions2.1.NotationG(V;E;W)a ow network with the set of nodes V={v i|16i6n},the set of arcs E={e i|16i6m},and W denotes the max-capacity of arcsn;m the number of nodes in V and arcs in E,respectivelys;t s;t∈V are the speciÿed source node and sink node,respectivelye i the i th arc in E(v i;v j)the arc(in E)from node v i to node v j,where v i and v j∈VO(e i)a system vector in which the capacity level is1for e i and0for other arcsW(e);w(e)the max-capacity and capacity level of arc e∈E in G(V;E;W),respec-tivelyC i the i th MC in G(V;E;W)W.-C.Yeh /Computers &Operations Research 29(2002)1843–18581845C ij ˙d (C i )C ij =(x 1;x 2;:::;x m )is the j th d -MC candidate (system-state)vector gen-erated from C i in G (V;E;W ),where x k =w (e k ), x k =d for e k ∈C i and x l =W (e l )for e l ∈C i C ij ˙d (C i )and C ij is (not)a d -MC G (V;E;C ij )the network corresponds to G (V;E;W )except C ij (e k )=x k 6W (e k )for e k ∈C i and C ij (e k )=W (e k )=x k for e k ∈C i ,if C ij =(x 1;x 2;:::;x m )G d;k (V;E;C ij )the remaining ow network after sending d capacity through node s to node t in G (V;E;C ij ),and then increase one capacity level of the k th arc in C i C i (e k )the max-capacity level of e k ∈E in G (V;E;C ij ),where ∀C ij ˙d (C i )M (X )the system max- ow from node s to node t under the system-state X X 6(=;¡)YX =(x 1;x 2;:::;x m )6(=;¡)Y =(y 1;y 2;:::;y m )i.f.f.x i 6(=;¡)y i for all i =1;2;:::;m MC(MP)mincut(minpath)2.2.Nomenclatured -MC for 06d ¡the value of max- ow in G (V;E;W ),a system-state vector,whose M (X )=d ,is said to have the capacity level d .A system-state vector X is a d -MC if and only if (1)its capacity level is d and (2)M (X +o (e i ))¿d for each e i ∈E and w (e i )¡W (e i )Demand (or load)level dthe demand level d is a non-negative integer-valued load or stress requirement for a given ually it is a random variable whose distribution { d }can be determined through con-tinuous observation and forecasting System reliability if the demand level d is a deterministic constant,then R d =Pr {C :M (C )¿d }is the system reliability.If the de-mand d is random,then the system reliability R d is deÿned as Pr {X :M (X )¿d } d .These two are consistent with the general reliability deÿnition viz.R d =Pr {strength ¿stress }Assumptions.The limited- ow network satisÿes the following assumptions [1,7,8,22–24]:Each node is perfectly reliable.The capacity of each arc is a non-negative integer-valued random variable according to a given distribution.The capacities of di erent arcs are statistically inde-pendent.All ows in the network obey the conservation law.3.Model formulation and preliminariesIf the ow network is series–parallel,then each d -MC candidate is a real d -MC [1].There-fore,we only focus on a non-series–parallel ow network in the remainder of this study.The relationship between the max- ow and the min s –t cut in Theorem 1is a very fundamental concept.Its proof can be found in any textbook about network ow theory [22–24].1846W.-C.Yeh /Computers &Operations Research 29(2002)1843–1858Theorem 1.The value of max- ow from source node s to sink node t equals the value of the min s–t cut in G (V;E;W ).The following theorem is originated and proved from Jane et al.[1].It is described that an MC satisfying three conditions simultaneously in Theorem 2is a d -MC candidate.It is used in the Implicit Algorithm of our paper to generate d -MC candidates.Theorem 2.Let C be a d-MC ;then there exists at least one MC C i ;such that the following three conditions hold : C i (e )=d for all e ∈C i ,C i (e )6W (e )for all e ∈C i ;C i (e )=W (e )for all e ∈C i .At least one arc exists in common between any d -MC candidate,say C ij ,and any min s –t cuts in G (V;E;C ij ).Lemma 1.Let C ij ˙d (C i ).Then C i ∩C ∗=∅;if C ∗is any one of min s–t cuts in G (V;E;C ij ).Proof.If there exists a min s –t cut C ∗in G (V;E;C ij )such that C i ∩C ∗=∅,then C ∗is also a min s –t cut in G (V;E;W ),i.e.this is contradictory to the case in which d is less than the value of max- ow in G (V;E;W ).Therefore,the proof follows.The following discusses some special properties about the d -MC candidates.Lemma 2.Let C ij ˙d (C i );S ij be a set of min s–t cuts in G (V;E;C ij );and C ∗∈S ij −{C i }.If C ik (e )¡ C ij (e );where ∀e ∈C i ∩C ∗and ∀C ik ˙d (C i );then C ik #d (C i ).Proof.Since C ij (e ∗)=C ik (e ∗)=W (e ∗)for all e ∗∈C ∗−C i ,if C ik (e )¡ C ij (e )for all e ∈C i ∩C ∗,then C ik (C ∗)6 C ik (e )+ C ik (e ∗)¡ C ij (e )+ W (e ∗)6d .Therefore,we have M (C ik )¡d ,i.e.C ik #d (C i ).From Lemma 2,we have the following result.Corollary1.Let C ij ˙d (C i );S ij be a set of min s–t cuts in G (V;E;C ij );and C ∗∈S ij −{C i }.If C ik ∼=d (C i );then C ik (e )¿ C ij (e );where ∀e ∈C i ∩C ∗.Lemma 3.Let C ij ˙d (C i );S ij be a set of min s–t cuts in G (V;E;C ij );and C ∗∈S ij −{C i }.If C ik ∼=d (C i )and W (e ∗)¿C ij (e ∗);then C ik (e )¿ C ij (e );where ∀e ∈C i ∩C ∗and ∃e ∗∈C i −C ∗.Proof.From Corollary 1,we already have C ik (e )¿ C ij (e ),where ∀e ∈C i ∩C ∗and C ik ∼=d (C i ).IfC ik (e )= C ij (e )and W (e ∗)¿C ij (e ∗),where ∀e ∈C i ∩C ∗and ∃e ∗∈C i −C ∗,thenW.-C.Yeh /Computers &Operations Research 29(2002)1843–18581847M (C ik +o (e ∗))=C ik (C ∗)=d .This is in contrast to the case in which C ik ∼=d (C i ).Thus,the proof follows.Corollary2.Let C ij ˙d (C i )with M (C ij )=d .If there is only an arc ;e ∈C i ;such that C ij (e )¡W (e )and e is also in a min s–t cut in G (V;E;C ij );then C ij is a d-MC .The following theorem is directly obtained from Theorem 2and Lemma 3.It is one of the most important results in this study.It will be employed in our algorithm to reduce the number of d -MC candidates.It also reduces the total time to verify which d -MC candidate is indeed a d -MC.Theorem 3.If S i is a set of min s–t cuts in G (V;E;C ij )for all C ij ˙d (C i );then ;C i (e )=d f or all e ∈C i ;C i (e )6W (e )f or all e ∈C i ;C i (e )=W (e )f or all e ∈C i ; C i (e )¿ C ij (e );where ∀e ∈C i ∩C ∗;∀C ∗∈S i −C i =∅and ∃e ∗∈C i −C ∗such that W (e ∗)¿C ij (e ∗):From the deÿnition of d -MC,a d -MC candidate is not a d -MC,if its capacity level is less than d .The following two theorems will be put in our algorithm to reduce the time of verifying which d -MC candidate with capacity level d is indeed a d -MC.Theorem 4.If C ij ˙d (C i );M (C ij )=d;and there is no other min s–t cut in G (V;E;C ij );then C ij ∼=d (C i ).Proof.C ij is the only one min s –t cut in G (V;E;C ij ).Thus,M (C ij +o (e ))¿d for all e ∈C i and C ij (e )¡W (e ).Therefore,C ij ∼=d (C i ).Theorem 5.Let C ij ˙d (C i );M (C ij )=d;S ij be a set of min s–t cuts in G (V;E;C ij );and E c ={e |e ∈C i −C ∗;∀C ∗∈S ij −{C i }}.If E c =∅or C ij (e )=W (e )for all e ∈E c ;then C ij ∼=d (C i ).Proof.Since C ij ˙d (C i )and M (C ij )=d ,if M (C ij +o (e ))¿d for all e ∈C i and C ij (e )¡W (e ),then C ij ∼=d (C i )from the deÿnition of d -MC.Any arc in C i −E c belongs to at least one min s –t cut in S ij −{C i },i.e.M (C ij +o (e ))¿d for all e ∈C i −E c while C ij (e )¡W (e ).If E c =∅,then C i −E c =C i .If C ij (e )=W (e )for all e ∈E c ,then M (C ij +o (e ∗))¿d for all e ∗∈C i −E c and Cij (e ∗)¡W (e ∗).The theorem now follows.Two consecutive d -MC candidates are generated from the same MC with nearly the same system vector.From this special structure,the max- ow of one of the two consecutive d -MC candidates may be easy to ÿnd without using any existing max- ow algorithm [25–27],if the1848W.-C.Yeh/Computers&Operations Research29(2002)1843–1858max- ow of the other candidate is known.The following theorem is another important result in our study.It originates from the above simple concept.It is also more e cient than any other max- ow algorithm[25–27]and will be implemented in our algorithm to reduce the run time forÿnding the max- ow.Theorem6.Let C ij˙d(C i);C ik˙d(C i);and C ik=C ij−o(e x)+o(e y).1unit capacity can be sent back from node t to node s through e x but not e y in G(V;E;C ij).After that;let C ij(e y)=C ij(e y)+1;if only1more unit capacity can be sent from node s to node t through e y but not e x;then M(C ij)=M(C ik);otherwise M(C ij)=M(C ik).Proof.Trivial.4.The best-known algorithmTo compare the e ciency and the time complexity between the proposed algorithm and best-known algorithm[8],the best-known algorithm(Algorithm0)is discussed in this sec-tion.Assume that all MCs also have been known in advance,the family of all d-MCs of an MC C i can then be found and checked using the best-known algorithm in the following steps:Algorithm0:[8]0.Let j←1and S i←∅.e the Implicit Algorithm toÿnd a d-MC candidate,say C ij(∈S i),of the followingmathematical model:C i(e)=d for all e∈C i;C i(e)6W(e)for all e∈C i;C i(e)=W(e)for all e∈C i:If no such d-MC candidate exists,then halt.2.If M(C ij)=d then k←1.Otherwise,j←j+1and go to Step1.3.If the capacity level of e k∈E in G(V;E;C ij)is equal to W(e k),then go to Step5.4.If M(C ij+o(e k))=d then j←j+1and go to Step1.5.If k¡m,then k←k+1and go to Step3.Otherwise C ij is d-MC,S i←S i∪{C ij};j←j+1and go to Step1.Algorithm0is based only on the deÿnition of d-MC with the time complexity O(m 0) [8],where 0is the total number of d-MC candidates and O( )is the time complexity to ÿnd the max- ow.However,there is still ample room to improve Algorithm0.For example, the number of d-MC candidates,which is found using the time-consuming and very burden-some Implicit Algorithm,can be reduced if the proposed properties discussed in Theorem3 are implemented.Next,Theorems4and5also can be implemented in Algorithm0to checkW.-C.Yeh /Computers &Operations Research 29(2002)1843–18581849if a d -MC candidate is a real d -MC while its capacity level is d .The max-capacity of the arcs between two consecutive d -MC candidates found in the Implicit Algorithm is nearly the same,except if there are only two arcs:one is 1unit capacity larger and the other is 1unit capacity smaller than that in the other d -MC candidate.Therefore,Theorem 6may be a better way to ÿnd the max- ow of each d -MC candidate than the most e cient max- ow algorithm.According to the above discussions,we propose a more e cient algorithm in the next section.5.The proposed algorithmA simpler but more e cient method (Algorithm 1)than Algorithm 0to ÿnd all d -MCs,where d is less than the max- ow in G (V;E;W ),generated from an MC is presented next.Suppose that all MCs have been precomputed,the family of all d -MCs of each MC can then be derived using the following steps:Algorithm 1:1.0.Let j ←0;C ij ←∅;S i ←∅,and V c ←{a |a ∈V ,and (v;a )or (a;v )in C ij ,where v ∈V }.1.1.(Implement Theorem 3)Let j ←j +1and use the Implicit Algorithm to ÿnd a d -MC candidate C ij of the following mathematical model: C i (e )=d for all e ∈C i ;C i (e )6W (e )for all e ∈C i ;C i (e )=W (e )for all e ∈C i ; C i (e )¿ C ij (e );where e ∈C i ∩C ∗k ;for all C ∗k ∈S i =∅:If no such d -MC candidate exists,then halt.1.2.If C ij =C i;j −1+o (e x )−o (e y ),then calculate M (C ij )by using Algorithm 2,otherwise use the max- ow e the max- ow algorithm to ÿnd M (C ij ).If M (C ij )¡d ,then C ij #d (C i )and go to Step 1.1.1.4.Check C ij and ÿnd a min s –t cut set S i by using Algorithm 3.Go to Step 1.1.Algorithm 2:(Implement Theorem 6)2.0.Send 1unit capacity from node t to node s through e x but not e y .2.1.Send 1unit capacity from node s to node t through e y but not e x .If this is impossible,then C ij #d (C i )and return to Step 1.1,otherwise M (C ij )=d and return to Step 1.4.Algorithm 3:(Implement Theorems 4and 5under the assumption of M (C ij )=d )3.0.Let V s ←V c ;V r ←V;E c ←∅, ag ←0,and E r ←E −(∪{e }),where ∀e ∈E and w (e )=C ij (e ).1850W.-C.Yeh /Computers &Operations Research 29(2002)1843–18583.1.If ∃v s ∈V s ,then V s ←V s −{v s };V r ←V r −{v s };V ∗←{v s },and E s ←∅,otherwise go to Step 3.6.3.2.Let v ∈V ∗and V ∗←V ∗−{v }.If A ={a |a ∈V r with (v;a )or (a;v )in E r }=∅,then V ∗←V ∗∪A;V r ←V r −A;V s ←V s −A ,and repeat Step 3.2.3.3.Let E s ←E s ∪{e |e =(v;a )or (a;v )in E −E r and a ∈V r }.If V ∗=∅,then go to Step 3.2.3.4.If E s =C i ,then C ∗ij ←(C i −E s )∪(E s −C i )and ag ←1,otherwise go to Step 3.1.3.5.If C ij (e )=d for ∀e ∈C ∗ij ,then S i ←S i ∪{C ∗ij },E c ←E c ∪(C i −E s ),and go to Step 3.1.3.6.(Implement Theorem 4)If ag =0,then C ij ∼=d (C i )and return to Step 1.1.3.7.(Implement Theorem 5)If E c =∅or C ij (e )=W (e )for all e ∈E c ,then C ij ∼=d (C i )and return to Step 1.1,otherwise,let E ∗c ←E c −{e |e ∈E c with C ij (e )=W (e )}.3.8.If ∃e ∈E ∗c ,then E ∗c ←E ∗c −{e }and C ij (e )←C ij (e )+1,else C ij ∼=d (C i )and return to Step 1.1.3.9.If 1unit capacity can be sent send from node s to node t through e ,then C ij #d (C i )and return to Step 1.1,otherwise,C ij (e )←C ij (e )−1and go to Step 3.9.From Algorithm 2,it takes O (2m )to send 1unit capacity from node s back to node t through two di erent directed paths.We have thus proved the following lemma.Lemma 4.Algorithm 2determines the capacity level of a d-MC candidate in O (m )time .It is not necessary for S i to be the set of all min s –t cuts in Algorithm 3.Otherwise,its number of elements will grow exponentially with the number of nodes.If C ∗∈S i =∅in Algorithm 3,then C ∗is a min s –t cut in G (V;E;C ij ),where ∃C ij ˙d (C i ).Moreover,C ∗∩C ij =∅from Lemma 1.Lemma 5.Algorithm 3runs in O (n )time to ÿnd the subset of S i (from Steps 3:0to 3:5)in G (V;E;C ij ).Proof.The construction of Algorithm 3investigates each node at most once only.Thus this lemma is implied.Lemma 6.Algorithm 3runs in O (m ·|C i |)time from Steps 3:8to 3:9.Proof.In the worst case,M (C ij +o (e ))must be larger than d for all e ∈C i from the deÿnition of d -MCs.It also takes O (m )time in Step 3.8to make sure that 1unit capacity can be sent from node s to node t through e .This result establishes the lemma.Followings directly from Lemmas 4–6,the following theorem summarizes the implication of the related result.Theorem 7.Algorithm 1ÿnds and checks the family of d -MC candidates of an MC in O ((mn +m ·|C i |) 1)=O (m 2 1)time ;where 1is the total number of d -MC candidates generated inW.-C.Yeh/Computers&Operations Research29(2002)1843–18581851 Step1:1of Algorithm1.Since ¿m; 0¿ 1,and from Theorem7,Algorithm1is more e cient than Algorithm0.6.An exampleThe next example illustrates our algorithm for the d-MCs problem.For the sake of conve-nience,we use lower bar(“”)in the number to denote the max-capacity of a relative arc in a d-MC candidate.Example1.There are4MCs in the following network(see Fig.1):C1={e1;e4};C2={e2;e5}, C3={e1;e3;e5}and C4={e2;e3;e4}.Use Algorithm1toÿnd and verify all2-MCs(d=2)in Fig.1,where nodes1and2are the source and sink nodes,respectively.The arc e is marked by W(e).Solve:(theÿrst d-MC candidate C11that generates from C1)1.0.Let j←0;C1j←∅;S1←∅; ag←0,and V c←{1;2;4}.1.1.By using the Implicit Algorithm(see Fig.2a),one of the feasible solu-tions of C1={e1;e4}that satisÿes C1(e1)+C1(e4)=2;(C1(e1);C1(e4))6(3;1),and (C1(e2);C1(e3);C1(e5))=(2;1;2)is C11=(2;2;1;0;2).1.2.According to the max- ow algorithm,the M(C11)=2in G(V;E;C11).1.3.From Algorithm3,there is no other min s–t cut in G(V;E;C11),i.e. ag=0,so C11isa2-MC.::(Generate from C3)1.0.Let j←0;C3j←∅;S3←∅,and V c←{1;2;3;4}.1.1.By using the Implicit Algorithm(see Fig.2b),one of the feasible solutions ofC3={e1;e3;e5}that satisÿes C3(e1)+C3(e3)+C3(e5)=2;(C3(e1);C3(e3);C3(e5)) 6(3;1;2)and(C3(e2);C3(e4))=(2;1)is C31=(2;2;0;1;0).1.2.According to the max- ow algorithm,the max- ow is2in G(V;E;C31).Fig.1.The network in Example1.1852W.-C.Yeh/Computers&Operations Research29(2002)1843–1858Fig.2.The2-MCs generated from MC by using the Implicit Algorithm.1.3.From Algorithm3,because S3←S3∪{C∗31};E c←C3−C∗31={e1;e3},and it isimpossible to send1more unit capacity from node s to node t,where C∗31={e2;e5}is another min s–t cut in G(V;E;C31),we have that C31is not a2-MC.1.1.By using the Implicit Algorithm(see Fig.2b)again,C32=(1;2;0;1;1)isanother of the feasible solutions of C3={e1;e3;e5}that C3(1)+ C3(e3)+C3(e5)=2;(C3(e1);C3(e3);C3(e5))6(3;1;2);(C3(e2);C3(e4))=(2;1)and C3(e5)¿C31(e5)=0(⇒C3(e1)=1).1.2.M(C32)=1from Algorithm2.Therefore,C32is not a2-MC.1.3.From Algorithm3,S3←S3∪{C∗32},where C∗32={e1;e4}is a min s–t cut in G(V;E;C32).1.1.By using the Implicit Algorithm again,there is an other2-MCcandidate of C3={e1;e3;e5}that satisÿed C3(e1)+C3(e3)+ C3(e5)=2;(C3(e1);C3(e3);C3(e5))6(3;1;2);(C3(e2);C3(e4))=(2;1);C3(e1)=1,and C3(e1)¿C32(e1)=1(⇒C3(e1)=2).::The result forÿnding and verifying all d-MCs by using Algorithm1is listed in Table1.putational resultTo compare the e ciency(running time)of the entire algorithm(Algorithm1)proposed in this paper against the best-known existing method(Algorithm0),these two algorithms were implemented in C++and carried out on a personal computer with Pentium III microproces-sor of1G MHz.The unit of the running time was(CPU)second.The capacity on each arc was randomly generated in discrete uniform distribution U[0;9].All of the non-integer values obtained from this experiment were rounded down to two digits,e.g.9:354and9:355were rounded down to9:35and9:36,respectively.The notations involved in the computation results from this experiment are listed below.•n;m;N MC;N Can and N d-MC:the average numbers of nodes,arcs,MCs,d-MC candidates and real d-MCs,respectively.Table1Final results of Example1i C i j C ij=(e1;e2;e3;e4;e5)A2-MC?E c Other min s–t cut(s) 1{e1;e4}1(2;2;1;0;2)Yes a∅no2(1;2;1;1;2)Yes a∅no2{e2;e5}1(3;2;1;1;0)Yes a∅no2(3;1;1;1;1)Yes a∅no3(3;0;1;1;2)Yes b{e5}{e2;e3;e4}3{e1;e3;e5}1(2;2;0;1;0)No c{e1;e3}{e2;e5}2(1;2;0;1;1)No d{e3;e5}{e1;e4}4{e2;e3;e4}1(3;2;0;0;2)Yes a∅no2(3;1;1;0;2)Yes a∅no3(3;1;0;1;2)Yes a∅no4(3;0;1;1;2)Yes b{e5}{e2;e5}a Since ag=0,i.e.no other min s–t cut in G(V;E;C ij)in Step3.6.b Since C ij(e)=W(e)in Step3.7for all e∈E c.c Since1unit capacity cannot be sent from node s to node t through e1after C31(e1)←C31(e1)+1.C3(e5)¿0⇒C3(e5)=1or2.d Since M(C32)=1¡2,we have C3(e1)¿1⇒C3(e1)=2.Table2Comparison of the results from n(n=5;6;:::;10)for Algorithms0and1n m N MC N Can N d-MC T1T0T0=T1N Can=N MC N d-MC=N MC N d-MC=N Can 59.177.40719.53203.540.000.0197.2327.510.28 613.6715.008419.732767.340.050.112.43561.32184.490.33 718.8030.1087,789.0035,754.600.92 2.933.182916.581187.860.41 825.7362.80860,672.04365,181.2317.6559.543.3713,704.975814.990.42 932.33125.2912,180,625.997,403,043.92554.432258.184.0797,222.7859,089.290.61 1040.95252.8727,319,651.5019,026,105.282943.5022,000.237.47108,037.9175,240.370.70•T0and T1:the average running time of Algorithms0and1,respectively.•T0=T1;N Can=N MC;N d-MC=N MC and N d-MC=N Can:the ratios of the values of T0and T1;N Can and N MC;N d-MC and N MC,and N d-MC and N Can,respectively.Due to the characteristics of NP-hard problem and the limitations of personal computers, the proposed algorithm solves only medium sized problems.Therefore,in the experiment,only six levels of n were employed;namely,n=5;6;:::;10.For each level of n;30problems were generated.Each set of problems was run for various values of d=2;3;:::;9.This totals up to 1440problems.parison of the e ciency of both algorithms for n=5;:::;10The results obtained by both algorithms for n=5;6;:::;10are presented in Table2.Table2 provides the average CPU times for the two algorithms for each n,the average numbers of arcs,MCs,d-MC candidates and real d-MCs.Three ratios are listed in the last three columnsof Table2to show the relationships among the number of MCs,d-MC candidates and real d-MCs.The ratio T0=T1is also shown in Table2to demonstrate the e ciency of the proposed algorithm.If there is a non-zero capacity arc between each pair of nodes,then there are n(n−1)=2 arcs in this network[23].The capacity on each arc was randomly generated in discrete uniform distribution U[0;9]in this experiment,i.e.the capacity of1=10arcs is expected to be zero. Therefore,m is close to9n(n−1)=20in Table2.The numbers of MCs,d-MC candidates and real d-MCs increase exponentially with n [1,7,8,13].The average running time also increases while the number of d-MC candidates and real d-MCs are increased.This can be seen from Table2where all of the values of T0;T1;N MC;N Can,and N d-MC tend to increase as n increases.However,an interesting observation is that the increasing speeds of the above values tend to decrease as n increases. For example,before rounding into two digits,the values of T1are0:0019494;0:0461359,and 0:9193073for n=5;6,and7,respectively,but the ratios of the two consecutive values of T1:0:0461359=0:0019494=23:67¿0:9193073=0:0461359=19:93decrease.The val-ues of N Can=N MC;N d-MC=N MC,and N d-MC=N Can also tend to increase as n increases.This results from(the increasing speed of the number of real d-MCs)¿(the increasing speed of the number of d-MC candidates)¿(the increasing speed of the number of MCs)while n is increasing. The results presented in Table2indicate that T0and T1are all less than one CPU second for n=5and6,while T0quickly climbs to almost1min for n=8.As n increases,the running times for both algorithms become prohibitively long.The maximum average running time T0, which occurs when n=10;is more than6h,but still less than50min for T1.From the same table,as n increases,T0=T1increases.Therefore,the larger the value for n,the more e cient Algorithm1is over Algorithm0.parison of the e ciency of both algorithms for d=2;:::;9Next,the in uence of d on the problem di culty is analyzed.From the same experiment, there are a total of30×6=180di erent data sets for each d.The corresponding results for di erent values of d from2,3to9,are collected and compared in Table3.The values of T0;T1;N Can and N d-MC all tend to increase as d increases in Table3.An inter-esting observation,similar to Section7.1,is that the increasing speeds of the above valuesTable3Comparison of the results from d(d=2;3;:::;9)for Algorithms0and1d N Can N d-MC N d-MC=N Can T1T0T0=T1 212,475.3311,974.730.96 2.34 4.17 1.78 378,765.6374,212.730.9413.8343.04 3.11 4381,541.34346,795.980.9163.75157.82 2.48 51,576,096.331,405,574.530.89252.89693.46 2.74 65,948,653.865,328,844.910.90583.812368.62 4.06 716,831,240.872,324,673.610.141481.236206.24 4.19 833,182,680.614,103,301.390.123019.3312,449.99 4.12 945,536,136.394,735,861.490.102696.5710,197.90 3.78tend to decrease as d increases.For example,the values of T1are2:34;13:83,and63:75 for d=2;3,and4,respectively,but the ratios of the two consecutive values of T1:13:83=2:34¿63:75=13:83decrease.The value of N d-MC=N Can decreases as d increases.The computational results presented in Table3indicate an increase in the problem di culty with an increase in d except at d=9.This may be due to the fact that the maximal capacity of each arc is only9.From T0=T1in Table3,Algorithm1is more e cient than the best-known algorithm, implemented in Algorithm0.parison of the e ciency of both algorithms for both d and nFinally,how the factors of both d and n simultaneously a ect the number of d-MC candidates, real d-MCs and average running time is discussed as follows.From the same experiment, the corresponding result of T0;T1,the number of d-MC candidates and real d-MCs for each (n;d)pair(d=2;3;:::;9and n=5;6;:::;10)are summarized in Table4.There are in total,30 di erent problems for each(n;d)pair.It is very obvious that T1is less than T0in all theTable4Comparison of the results from n=5;6;:::;10and d=2;3;:::;9for Algorithms0and1n\d2*******T150.000.000.000.000.000.000.000.0060.010.010.020.030.050.070.080.0970.020.060.170.400.79 1.46 2.19 2.2580.150.66 2.15 5.7515.0832.2350.8534.329 1.06 5.4422.3980.11258.80696.951377.711993.021012.8176.83357.751431.073228.148156.6516685.1114149.72T050.000.000.000.010.000.010.010.0060.010.020.050.090.150.200.190.1970.050.210.63 1.41 2.85 5.237.61 5.4180.40 2.107.5321.4660.24130.55193.9360.119 2.7416.8278.45308.601070.452997.645834.937755.851021.82239.10860.263829.1813078.0034103.8168663.2553365.86N Can5102.90216.80371.77571.43802.501048.771263.771378.30 6416.331120.632473.974899.108593.0313178.5016851.3719824.93 71526.905366.1314918.1733337.5366378.37125501.60198667.47256615.80 85416.9725070.0083772.37222739.13574213.471268862.732243057.502462244.13 917203.0093843.97397820.071465486.004837389.7713472080.4329162976.3047998208.37 1050185.90346976.271789891.707729544.8030204546.0086106773.20167473267.29222478546.80N d-MC587.80162.33237.27293.23308.00292.83200.4746.37 6351.43843.201631.202902.904255.275042.333768.333344.03 71416.804615.5711688.0022907.4740769.2068652.1790190.8745796.73 85079.7022654.4369537.40171457.83441638.40860704.131164663.10185714.83 916546.8086927.90354779.571277369.934097960.8710688676.5719257684.2023444405.50 1048365.87330072.971642902.436958515.8327388137.7068615613.8097438486.9335791005.80。
