rfc2207.RSVP Extensions for IPSEC Data Flows
中国联通本地综合承载与传送设备技术规范

中国联通本地综合承载与传送设备技术规范12中国联通公司发布中国联通本地综合承载传送网设备技术规范v1.0Technical Specification for China Unicom Local Unified Transport Network Equipment v1.0(NEQ)中国联通公司企业标准QB/CU 057- -1-18发布-1-18实施目次1范围............................................................................................ 错误!未定义书签。
2规范性引用文件 ....................................................................... 错误!未定义书签。
3定义、术语和缩略语 ............................................................... 错误!未定义书签。
4设备基本要求............................................................................ 错误!未定义书签。
4.1 设备基本要求..................................................................... 错误!未定义书签。
5通用技术规范............................................................................ 错误!未定义书签。
5.1 设备系统架构..................................................................... 错误!未定义书签。
一般的Internet电话的组网图
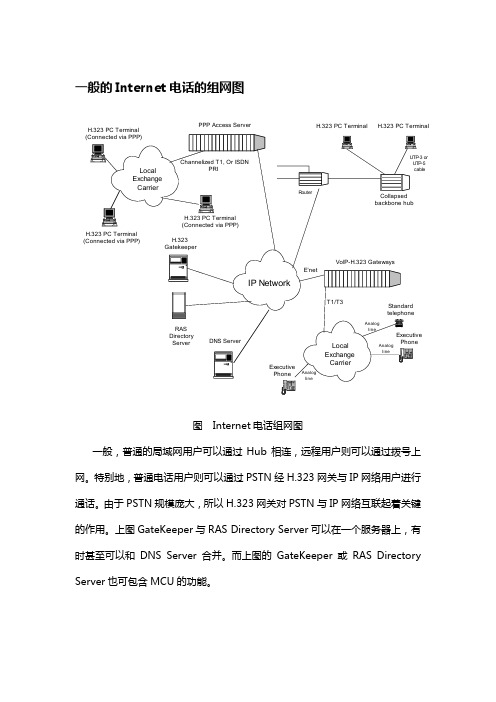
一般的Internet电话的组网图PPP Access Server H.323 PC Terminal H.323 PC Terminal图 Internet电话组网图一般,普通的局域网用户可以通过Hub相连,远程用户则可以通过拨号上网。
特别地,普通电话用户则可以通过PSTN经H.323网关与IP网络用户进行通话。
由于PSTN规模庞大,所以H.323网关对PSTN与IP网络互联起着关键的作用。
上图GateKeeper与RAS Directory Server可以在一个服务器上,有时甚至可以和DNS Server合并。
而上图的GateKeeper或RAS Directory Server也可包含MCU的功能。
3、传输协议在IETF的MMUSIC工作组的草案《The Internet Multimedia Conference Architecture》中定义的视讯会议的协议栈如下:|<--- Conference Management --->|<--- Media Agents --->|| | || Conference | Conference | Audio/ | Shared || Setup & Discovery | Course Control | Video | Applications |+-------------------------+------+--------+-+--------+------------+ +| S D P | | Distr. | RTP / | Reliable | || SAP | SIP | HTTP | SMTP | RSVP | Ctrl(1)| RTCP |Multicast(2)| |+-----+--+--+------+------+ +--+--------+----------+------------+--+| UDP | T C P | | U D P |+--------+----------------+---+--------------------------------------+| IP + IP Multicast |+--------------------------------------------------------------------+| Integrated Services Forwarding |+--------------------------------------------------------------------+ 图 Internet Multimedia Conferencing protocol stacks一般说来,呼叫建立和控制大多建立在TCP(面向连接)基础上,而音频流的传送则建立在UDP(面向无连接)基础上,为保证传送的实时性,IETF增加了几个重要的协议:1) RSVP:(Resource Reservation Protocol)一般说来,在IP网络上保留足够的带宽用于多媒体的传送是十分困难的,为此IETF定义了资源预留协议(RSVP)。
2025年软件资格考试信息处理技术员(初级)(基础知识、应用技术)合卷试卷及答案指导

2025年软件资格考试信息处理技术员(基础知识、应用技术)合卷(初级)自测试卷(答案在后面)一、基础知识(客观选择题,75题,每题1分,共75分)1、软件工程的三个基本要素是()A. 软件需求、软件设计、软件测试B. 软件需求、软件实现、软件维护C. 软件需求、软件项目管理、软件测试D. 软件设计、软件实现、软件维护2、在软件工程中,需求分析的主要目的是()A. 确定软件的功能和性能B. 设计软件的架构和模块C. 编写软件的源代码D. 测试软件的可用性和稳定性3、题干:以下关于操作系统内核的描述,正确的是()A. 操作系统内核是计算机硬件的一部分B. 操作系统内核是操作系统的核心部分,负责管理计算机硬件资源C. 操作系统内核只负责处理用户请求,不涉及硬件资源管理D. 操作系统内核是用户程序的一部分4、题干:以下关于数据库管理系统的描述,错误的是()A. 数据库管理系统(DBMS)是数据库系统的核心软件B. 数据库管理系统负责数据的存储、检索、更新和维护C. 数据库管理系统不负责数据的备份和恢复D. 数据库管理系统提供用户界面,方便用户对数据库进行操作5、在计算机系统中,以下哪个设备属于输入设备?A. 打印机B. 显示器C. 鼠标D. 键盘6、在操作系统中,以下哪个概念指的是计算机中程序和数据的存储区域?A. 内存B. 硬盘C. CPUD. 网络接口卡7、在计算机系统中,CPU与内存之间的数据传输宽度通常指的是什么?A. 数据总线的宽度B. 地址总线的宽度C. 控制总线的宽度D. 存储单元的大小8、下列哪一项不是操作系统的功能?A. 进程管理B. 文件管理C. 用户界面管理D. 硬件直接控制9、以下哪种数据结构最适合用于实现一个需要频繁插入和删除元素的有序序列?A. 链表B. 数组C. 二叉搜索树D. 平衡二叉搜索树 10、在面向对象编程中,以下哪个原则强调“一个类应该只包含它所需的功能,不应包含其他无关的功能”?A. 单一职责原则(Single Responsibility Principle, SRP)B. 开放封闭原则(Open-Closed Principle, OCP)C. 依赖倒置原则(Dependency Inversion Principle, DIP)D. 接口隔离原则(Interface Segregation Principle, ISP)11、在计算机网络中,用来衡量数据传输可靠性的指标是:A. 误码率B. 频带利用率C. 信道容量D. 吞吐量12、下列不属于操作系统基本功能的是:A. 处理器管理B. 存储管理C. 文件管理D. 程序设计13、以下关于计算机系统组成中,不属于硬件设备的是:A. CPUB. 主板C. 显卡D. 操作系统14、在计算机系统中,下列哪个部件主要用来存储和读取数据?A. CPUB. 内存C. 硬盘D. 显卡15、下列选项中哪一个不是计算机硬件?A. 操作系统B. 内存条C. 显卡D. 硬盘16、在下列存储单位中,哪个单位最大?A. GB (Gigabyte)B. KB (Kilobyte)C. MB (Megabyte)D. TB (Terabyte)17、以下关于数据结构中栈的描述,正确的是()A. 栈是一种线性表,其插入和删除运算都在一端进行B. 栈是一种非线性结构,其插入和删除运算都在一端进行C. 栈是一种非线性结构,其插入和删除运算都在另一端进行D. 栈是一种线性表,其插入和删除运算都在另一端进行18、在数据库管理系统中,以下关于SQL语言中JOIN操作的说法,错误的是()A. JOIN操作用于连接两个或多个表B. INNER JOIN操作返回两个表中匹配的行C. LEFT JOIN操作返回左表中所有的行,右表中没有匹配的行时返回NULLD. RIGHT JOIN操作返回右表中所有的行,左表中没有匹配的行时返回NULL19、在数据库设计中,E-R图(实体-联系图)用于描述数据的哪种模型?A. 逻辑模型B. 物理模型C. 概念模型D. 结构模型 20、下列选项中,哪一项不是软件工程的基本原则?A. 遵循良好的编程实践B. 提高软件的可重用性C. 增强软件的复杂度D. 保证软件的可靠性21、在关系数据库中,若要实现多个表之间数据的连接操作,通常使用以下哪种操作符?A. INB. BETWEENC. LIKE22、以下哪个选项不属于面向对象程序设计的基本原则?A. 封装B. 继承C. 多态D. 重载23、关于计算机网络的描述,下列哪一项是错误的?A. 计算机网络是由多台计算机通过通信设备和线路连接起来,按照网络协议实现数据通信和资源共享的系统。
File Transfer Protocol

File Transfer ProtocolFile Transfer Protocol (FTP) is a network protocol used to transfer data fromone computer to another through a network such as the Internet.FTP is a file transfer protocol for exchanging and manipulating files over a TCP computer network. A FTP client may connect to a FTP server to manipulate fileson that server. As there are many FTP client and server programs available for different operating systems, FTP is a popular choice for exchanging files independent of the operating systems involved.The TCP/IP model (RFC 1122)Application Layer BGP·DHCP·DNS·FTP·Gopher·GTP·HTTP·IMAP·IRC·NNTP·NTP·POP·RIP·RPC·RTCP·RTP·RTSP·SDP·SIP·SMTP·SNMP·SOAP·SSH·SSL·STUN·Telnet·TLS·XMPP·(more)Transport LayerTCP·UDP·DCCP·SCTP·RSVP·ECN·(more)Internet LayerIP (IPv4·IPv6) ·ICMP·ICMPv6·IGMP·IPsec·(more)Link Layer ARP·RARP·NDP·OSPF·Tunnels·Media Access Control·Device Drivers·(more)This box: view•talk•editConnection methodsFTP runs exclusively over TCP. It defaults to listen on port 21 for incoming connections from FTP clients. A connection to this port from the FTP Client forms the control stream on which commands are passed to the FTP server from theFTP client and on occasion from the FTP server to the FTP client. FTP uses out-of-band control, which means it uses a separate connection for control and data. Thus, for the actual file transfer to take place, a different connection is required which is called the data stream. Depending on the transfer mode, the process of setting up the data stream is different.In active mode, the FTP client opens a dynamic port, sends the FTP server the dynamic port number on which it is listening over the control stream and waits fora connection from the FTP server. When the FTP server initiates the data connection to the FTP client it binds the source port to port 20 on the FTP server.In order to use active mode, the client sends a PORT command, with the IP and port as argument. The format for the IP and port is "h1,h2,h3,h4,p1,p2". Eachfield is a decimal representation of 8 bits of the host IP, followed by the chosen data port. For example, a client with an IP of 192.168.0.1, listening on port 49154 for the data connection will send the command "PORT 192,168,0,1,192,2". The port fields should be interpreted as p1×256 + p2 = port, or, in this example,192×256 + 2 = 49154.In passive mode, the FTP server opens a dynamic port, sends the FTP client the server's IP address to connect to and the port on which it is listening (a 16-bit value broken into a high and low byte, as explained above) over the control stream and waits for a connection from the FTP client. In this case, the FTP client binds the source port of the connection to a dynamic port.To use passive mode, the client sends the PASV command to which the server would reply with something similar to "227 Entering Passive Mode(127,0,0,1,192,52)". The syntax of the IP address and port are the same as for the argument to the PORT command.In extended passive mode, the FTP server operates exactly the same as passive mode, however it only transmits the port number (not broken into high and low bytes) and the client is to assume that it connects to the same IP address that was originally connected to. Extended passive mode was added by RFC 2428 in September 1998.While data is being transferred via the data stream, the control stream sits idle. This can cause problems with large data transfers through firewalls which time out sessions after lengthy periods of idleness. While the file may well be successfully transferred, the control session can be disconnected by the firewall, causing an error to be generated.The FTP protocol supports resuming of interrupted downloads using the REST command. The client passes the number of bytes it has already received as argument to the REST command and restarts the transfer. In some commandline clients for example, there is an often-ignored but valuable command, "reget" (meaning "get again") that will cause an interrupted "get" command to be continued, hopefully to completion, after a communications interruption. Resuming uploads is not as easy. Although the FTP protocol supports the APPE command to append data to a file on the server, the client does not know the exact position at which a transfer got interrupted. It has to obtain the size of the file some other way, for example over a directory listing or using the SIZE command.In ASCII mode (see below), resuming transfers can be troublesome if client and server use different end of line characters.The objectives of FTP, as outlined by its RFC, are:1. To promote sharing of files (computer programs and/or data).2. To encourage indirect or implicit use of remote computers.3. To shield a user from variations in file storage systems among differenthosts.4. To transfer data reliably, and efficiently.Criticisms of FTP•Passwords and file contents are sent in clear text, which can be intercepted by eavesdroppers. There are protocol enhancements thatremedy this, for instance by using SSL, TLS or Kerberos.•Multiple TCP/IP connections are used, one for the control connection, and one for each download, upload, or directory listing. Firewalls may needadditional logic and/or configuration changes to account for theseconnections.•It is hard to filter active mode FTP traffic on the client side by using a firewall, since the client must open an arbitrary port in order to receive the connection. This problem is largely resolved by using passive mode FTP.•It is possible to abuse the protocol's built-in proxy features to tell a server to send data to an arbitrary port of a third computer; see FXP.•FTP is a high latency protocol due to the number of commands needed to initiate a transfer.•No integrity check on the receiver side. If a transfer is interrupted, the receiver has no way to know if the received file is complete or not. Someservers support extensions to calculate for example a file's MD5 sum (e.g.using the SITE MD5 command), XCRC, XMD5, XSHA or CRC checksum, however even then the client has to make explicit use of them. In theabsence of such extensions, integrity checks have to be managedexternally.•No date/timestamp attribute transfer. Uploaded files are given a new current timestamp, unlike other file transfer protocols such as SFTP, which allow attributes to be included. There is no way in the standard FTPprotocol to set the time-last-modified (or time-created) datestamp thatmost modern filesystems preserve. There is a draft of a proposedextension that adds new commands for this, but as of yet, most of thepopular FTP servers do not support it.Security problemsThe original FTP specification is an inherently insecure method of transferring files because there is no method specified for transferring data in an encrypted fashion. This means that under most network configurations, user names, passwords, FTP commands and transferred files can be "sniffed" or viewed by anyone on the same network using a packet sniffer. This is a problem common to many Internet protocol specifications written prior to the creation of SSL such asHTTP, SMTP and Telnet. The common solution to this problem is to use either SFTP (SSH File Transfer Protocol), or FTPS (FTP over SSL), which adds SSL or TLS encryption to FTP as specified in RFC 4217.FTP return codesMain article: List of FTP server return codesFTP server return codes indicate their status by the digits within them. A brief explanation of various digits' meanings are given below:•1xx: Positive Preliminary reply. The action requested is being initiated but there will be another reply before it begins.•2xx: Positive Completion reply. The action requested has been completed.The client may now issue a new command.•3xx: Positive Intermediate reply. The command was successful, but a further command is required before the server can act upon the request.•4xx: Transient Negative Completion reply. The command was not successful, but the client is free to try the command again as the failure is only temporary.•5xx: Permanent Negative Completion reply. The command was not successful and the client should not attempt to repeat it again.•x0x: The failure was due to a syntax error.•x1x: This response is a reply to a request for information.•x2x: This response is a reply relating to connection information.•x3x: This response is a reply relating to accounting and authorization.•x4x: Unspecified as yet•x5x: These responses indicate the status of the Server file system vis-a-vis the requested transfer or other file system action.Anonymous FTPA host which provides an FTP service may additionally provide Anonymous FTP access as well. Under this arrangement, users do not strictly need an account on the host. Instead the user typically enters 'anonymous' or 'ftp' when prompted for username. Although users are commonly asked to send their email address as their password, little to no verification is actually performed on the supplied data.As modern FTP clients typically hide the anonymous login process from the user, the ftp client will supply dummy data as the password (since the user's email address may not be known to the application). For example, the following ftp user agents specify the listed passwords for anonymous logins:•Mozilla Firefox (2.0) — mozilla@•KDE Konqueror (3.5) — anonymous@•wget (1.10.2) — -wget@•lftp (3.4.4) — lftp@The Gopher protocol has been suggested as an alternative to anonymous FTP, as well as Trivial File Transfer Protocol and File Service Protocol.[citation needed] Data formatWhile transferring data over the network, several data representations can be used. The two most common transfer modes are:1. ASCII mode2. Binary mode: In "Binary mode", the sending machine sends each file bytefor byte and as such the recipient stores the bytestream as it receives it.(The FTP standard calls this "IMAGE" or "I" mode)In "ASCII mode", any form of data that is not plain text will be corrupted. When a file is sent using an ASCII-type transfer, the individual letters, numbers, and characters are sent using their ASCII character codes. The receiving machine saves these in a text file in the appropriate format (for example, a Unix machine saves it in a Unix format, a Windows machine saves it in a Windows format). Hence if an ASCII transfer is used it can be assumed plain text is sent, which is stored by the receiving computer in its own format. Translating between text formats might entail substituting the end of line and end of file characters used on the source platform with those on the destination platform, e.g. a Windows machine receiving a file from a Unix machine will replace the line feeds with carriage return-line feed pairs. It might also involve translating characters; for example, when transferring from an IBM mainframe to a system using ASCII, EBCDIC characters used on the mainframe will be translated to their ASCII equivalents, and when transferring from the system using ASCII to the mainframe, ASCII characters will be translated to their EBCDIC equivalents.By default, most FTP clients use ASCII mode. Some clients try to determine the required transfer-mode by inspecting the file's name or contents, or by determining whether the server is running an operating system with the same text file format.The FTP specifications also list the following transfer modes:1. EBCDIC mode - this transfers bytes, except they are encoded in EBCDICrather than ASCII. Thus, for example, the ASCII mode server2. Local mode - this is designed for use with systems that are word-orientedrather than byte-oriented. For example mode "L 36" can be used totransfer binary data between two 36-bit machines. In L mode, the wordsare packed into bytes rather than being padded. Given the predominanceof byte-oriented hardware nowadays, this mode is rarely used. However,some FTP servers accept "L 8" as being equivalent to "I".In practice, these additional transfer modes are rarely used. They are however still used by some legacy mainframe systems.The text (ASCII/EBCDIC) modes can also be qualified with the type of carriage control used (e.g. TELNET NVT carriage control, ASA carriage control), although that is rarely used nowadays.Note that the terminology "mode" is technically incorrect, although commonly used by FTP clients. "MODE" in RFC 959 refers to the format of the protocol data stream (STREAM, BLOCK or COMPRESSED), as opposed to the format of the underlying file. What is commonly called "mode" is actually the "TYPE", which specifies the format of the file rather than the data stream. FTP also supports specification of the file structure ("STRU"), which can be either FILE (stream-oriented files), RECORD (record-oriented files) or PAGE (special type designed for use with TENEX). PAGE STRU is not really useful for non-TENEX systems, and RFC1123 section 4.1.2.3 recommends that it not be implemented.FTP and web browsersMost recent web browsers and file managers can connect to FTP servers, although they may lack the support for protocol extensions such as FTPS. This allows manipulation of remote files over FTP through an interface similar to that used for local files. This is done via an FTP URL, which takes the formftp(s)://<ftpserveraddress> (e.g., ftp:///). A password can optionally be given in the URL, e.g.:ftp(s)://<login>:<password>@<ftpserveraddress>:<port>. Most web-browsers require the use of passive mode FTP, which not all FTP servers are capable of handling. Some browsers allow only the downloading of files, but offer no way to upload files to the server.FTP and NAT devicesThe representation of the IPs and ports in the PORT command and PASV reply poses another challenge for NAT devices in handling FTP. The NAT device must alter these values, so that they contain the IP of the NAT-ed client, and a port chosen by the NAT device for the data connection. The new IP and port will probably differ in length in their decimal representation from the original IP and port. This means that altering the values on the control connection by the NAT device must be done carefully, changing the TCP Sequence and Acknowledgment fields for all subsequent packets.For example: A client with an IP of 192.168.0.1, starting an active mode transfer on port 1025, will send the string "PORT 192,168,0,1,4,1". A NAT device masquerading this client with an IP of 192.168.15.5, with a chosen port of 2000 for the data connection, will need to replace the above string with "PORT192,168,15,5,7,208".The new string is 23 characters long, compared to 20 characters in the original packet. The Acknowledgment field by the server to this packet will need to be decreased by 3 bytes by the NAT device for the client to correctly understand that the PORT command has arrived to the server. If the NAT device is not capable of correcting the Sequence and Acknowledgement fields, it will not be possible to use active mode FTP. Passive mode FTP will work in this case, because the information about the IP and port for the data connection is sent by the server, which doesn't need to be NATed. If NAT is performed on the server by the NAT device, then the exact opposite will happen. Active mode will work, but passive mode will fail.It should be noted that many NAT devices perform this protocol inspection and modify the PORT command without being explicitly told to do so by the user. This can lead to several problems. First of all, there is no guarantee that the used protocol really is FTP, or it might use some extension not understood by the NAT device. One example would be an SSL secured FTP connection. Due to the encryption, the NAT device will be unable to modify the address. As result, active mode transfers will fail only if encryption is used, much to the confusion of the user.The proper way to solve this is to tell the client which IP address and ports to use for active mode. Furthermore, the NAT device has to be configured to forward the selected range of ports to the client's machine.See also Application-level gatewayFTP over SSH (SFTP)FTP over SSH (SFTP) refers to the practice of tunneling a normal FTP session over an SSH connection.Because FTP uses multiple TCP connections (unusual for a TCP/IP protocol that is still in use), it is particularly difficult to tunnel over SSH. With many SSH clients, attempting to set up a tunnel for the control channel (the initial client-to-server connection on port 21) will protect only that channel; when data is transferred, the FTP software at either end will set up new TCP connections (data channels) which will bypass the SSH connection, and thus have no confidentiality, integrity protection, etc.If the FTP client is configured to use passive mode and to connect to a SOCKS server interface that many SSH clients can present for tunneling, it is possible to run all the FTP channels over the SSH connection.Otherwise, it is necessary for the SSH client software to have specific knowledge of the FTP protocol, and monitor and rewrite FTP control channel messages and autonomously open new forwardings for FTP data channels. Version 3 of SSH Communications Security's software suite, and the GPL licensed FONC are two software packages that support this mode.FTP over SSH is sometimes referred to as secure FTP; this should not be confused with other methods of securing FTP, such as with SSL/TLS (FTPS). Other methods of transferring files using SSH that are not related to FTP include SFTP and SCP; in each of these, the entire conversation (credentials and data) is always protected by the SSH protocol.See also•FTAM•FTPFS•List of FTP server return codes•List of FTP commands•List of file transfer protocols•OBEX•Shared file access•TCP Wrapper•Comparison of FTP client software•List of FTP server software•Comparison of FTP server softwareFurther readingThe protocol is standardized in RFC 959 by the IETF as:•RFC 959 File Transfer Protocol (FTP). J. Postel, J. Reynolds. Oct-1985.This obsoleted the preceding RFC 765 and earlier FTP RFCs back to the original RFC 114.•RFC 1579 Firewall-Friendly FTP.•RFC 2228 — FTP Security Extensions•RFC 2428 — Extensions for IPv6, NAT, and Extended passive mode Sep-1998.•RFC 3659 — Extensions to FTP. P. Hethmon. March-2007. External links•FTP Reviewed — a review of the protocol notably from a security standpoint•Raw FTP command list•FTP Sequence Diagram (in PDF format)Retrieved from "/wiki/File_Transfer_Protocol"。
RSVP的RFC

RFC 2205: The version 1 functional specification was described in RFC 2205 (Sept. 1997) by IETF. Version 1 describes the interface to admission (traffic) control that is based "only" on resource availability. Later RFC2750 extended the admission control support.
RFC 4558, "Node-ID Based Resource Reservation Protocol (RSVP) Hello: A Clarification Statement" (June 2006).
RFC 3936, "Procedures for Modifying the Resource reSerVation Protocol (RSVP)" (October 2004), describes current best practices and specifies procedures for modifying RSVP.
RFC 4495, "A Resource Reservation Protocol (RSVP) Extension for the Reduction of Bandwidth of a Reservation Flow" (May 2006), extends RSVP to enable the bandwidth of an existing reservation to be reduced instead of tearing down the reservation.
华为路由器 配置IPSec

目录
目录
7 配置 IPSec ...................................................................................................................................7-1
7.1 简介..............................................................................................................................................................7-2 7.1.1 IPSec 概述 ...........................................................................................................................................7-2 7.1.2 基于证书认证机制的 IPSec ..............................................................................................................7-2
文档版本 02 (2008-12-15)
华为所有和机密iLeabharlann 版权所有 © 华为技术有限公司
目录
Secoway USG50 配置指南 安全防范分册
7.5.3 配置证书验证...................................................................................................................................7-21 7.5.4 检查配置结果...................................................................................................................................7-21 7.6 维护............................................................................................................................................................7-21 7.6.1 查看 IPSec 处理报文的统计信息 ...................................................................................................7-21 7.6.2 调试 IPSec ........................................................................................................................................7-21 7.6.3 调试 IKE...........................................................................................................................................7-22 7.6.4 删除 IKE SA.....................................................................................................................................7-22 7.6.5 删除 SA ............................................................................................................................................7-22 7.6.6 清除 IPSec 统计报文 .......................................................................................................................7-23 7.6.7 维护低速加密卡...............................................................................................................................7-23 7.6.8 维护 CA............................................................................................................................................7-24 7.7 配置举例....................................................................................................................................................7-25 7.7.1 配置采用 Manual 方式建立 SA 示例 .............................................................................................7-25 7.7.2 配置采用 IKE 方式建立 SA 示例(预共享密钥) .......................................................................7-32 7.7.3 配置采用 IKE 方式建立 SA 示例(RSA 签名) ..........................................................................7-39
rfc中常用的测试协议

rfc中常用的测试协议引言在计算机网络领域中,为了确保网络协议的正确性和稳定性,测试协议起到了至关重要的作用。
RFC(Request for Comments)是一系列文件,用于描述互联网相关协议、过程和技术。
在RFC中,也包含了一些常用的测试协议,用于验证和评估网络协议的功能和性能。
本文将介绍RFC中常用的测试协议,并深入探讨其原理和应用。
二级标题1:PING协议三级标题1.1:概述PING协议是一种常用的网络测试协议,用于测试主机之间的连通性。
它基于ICMP (Internet Control Message Protocol)协议,通过发送ICMP Echo Request报文并等待目标主机的ICMP Echo Reply报文来判断目标主机是否可达。
三级标题1.2:工作原理PING协议的工作原理如下: 1. 发送方主机生成一个ICMP Echo Request报文,并将目标主机的IP地址作为目的地。
2. 发送方主机将报文发送到网络中。
3.中间路由器收到报文后,将报文转发到下一跳路由器。
4. 目标主机收到ICMP Echo Request报文后,生成一个ICMP Echo Reply报文,并将其发送回发送方主机。
5. 发送方主机收到ICMP Echo Reply报文后,通过比较报文中的标识符和序列号等字段,判断目标主机是否可达。
三级标题1.3:应用场景PING协议在网络中的应用非常广泛,常用于以下场景: - 测试主机之间的连通性,判断网络是否正常工作。
- 测试网络延迟,通过计算ICMP Echo Request报文的往返时间来评估网络质量。
- 排查网络故障,通过检查ICMP Echo Reply报文中的错误码来定位故障原因。
二级标题2:Traceroute协议三级标题2.1:概述Traceroute协议用于跟踪数据包从源主机到目标主机经过的路径。
它通过发送一系列的UDP报文,并在每个报文中设置不同的TTL(Time to Live)值来实现。
ipsec中文rfc

组织:中国互动出版网(/)RFC文档中文翻译计划(/compters/emook/aboutemook.htm)E-mail:********************译者:sword(************************)译文发布时间:2001-7-25版权:本中文翻译文档版权归中国互动出版网所有。
可以用于非商业用途自由转载,但必须保留本文档的翻译及版权信息。
Network Working Group D. HarkinsRequest for Comments: 2409 D. CarrelCategory: Standards Track cisco SystemsNovember 1998Internet密钥交换(IKE)(The Internet Key Exchange)本备忘录的现状本文档指定了一个Internet 团体的Internet标准协议,并请求讨论和建议以作改进。
请参考当前版本的“Internet官方协议标准”(STD 1),查看本协议的标准化进程和现状。
本文档的分发不受限制。
版权通告Copyright (C) The Internet Society (1998)。
保留所有的权利。
目录1.摘要 22.讨论 23.术语和定义 33.1必要的术语 33.2符号 33.3完全后继保密 43.4安全联盟 44.简介 55.交换 65.1 使用签名来验证的IKE第一阶段 85.2 使用公共密钥加密的第一阶段验证 85.3 使用修改过的公钥加密模式来进行第一阶段的验证 10 5.4 使用共享密钥的第一阶段协商 115.5 第二阶段——快速模式 125.6 新组模式 145.7 ISAKMP信息交换 156 Oakley组 156.1 第一个Oakley缺省组 156.2 第二个Oakley组 166.3 第三个Oakley组 166.4 第四个Oakley组 167. 完整IKE交换的负载爆炸 177.1 使用主模式的第一阶段 177.2 使用快速模式的第二阶段 188. 完全后继保密举例 2010.安全考虑 2111.IANA考虑 2211.1 属性类 2211.2 加密算法类 2211.3 hash算法 2211.4 组描述和组类型 2311.5 存活期类型 2312. 鸣谢 2313.参考 23附录A 25属性分配号码 25属性种类 26种类值 26附录B 28作者地址 30作者的注释 30完全版权声明 311.摘要ISAKMP ([MSST98])中对验证和密钥交换提出了结构框架,但没有具体定义。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Network Working Group L. Berger Request for Comments: 2207 FORE Systems Category: Standards Track T. O’MalleyBBNSeptember 1997RSVP Extensions for IPSEC Data FlowsStatus of this MemoThis document specifies an Internet standards track protocol for the Internet community, and requests discussion and suggestions forimprovements. Please refer to the current edition of the "InternetOfficial Protocol Standards" (STD 1) for the standardization stateand status of this protocol. Distribution of this memo is unlimited.AbstractThis document presents extensions to Version 1 of RSVP. Theseextensions permit support of individual data flows using RFC 1826, IP Authentication Header (AH) or RFC 1827, IP Encapsulating SecurityPayload (ESP). RSVP Version 1 as currently specified can support the IPSEC protocols, but only on a per address, per protocol basis not on a per flow basis. The presented extensions can be used with bothIPv4 and IPv6.Berger & O’Malley Standards Track [Page 1]Table of Contents1 Introduction . . . . . . . . . . . . . . . . . . . . . . . 22 Overview of Extensions . . . . . . . . . . . . . . . . . . 33 Object Definition. . . . . . . . . . . . . . . . . . . . . 43.1 SESSION Class . . . . . . . . . . . . . . . . . . . . 53.2 FILTER_SPEC Class . . . . . . . . . . . . . . . . . . 53.3 SENDER_TEMPLATE Class . . . . . . . . . . . . . . . . 64 Processing Rules . . . . . . . . . . . . . . . . . . . . . 64.1 Required Changes. . . . . . . . . . . . . . . . . . . 64.2 Merging Flowspecs . . . . . . . . . . . . . . . . . . 74.2.1 FF and SE Styles. . . . . . . . . . . . . . . . . . 74.2.2 WF Styles . . . . . . . . . . . . . . . . . . . . . 85 IANA Considerations. . . . . . . . . . . . . . . . . . . . 86 Security Considerations. . . . . . . . . . . . . . . . . . 87 References . . . . . . . . . . . . . . . . . . . . . . . .108 Acknowledgments . . . . . . . . . . . . . . . . . . . . .109 Authors’ Addresses . . . . . . . . . . . . . . . . . . . .10A Options Considered . . . . . . . . . . . . . . . . . . . .11A.1 UDP Encapsulation . . . . . . . . . . . . . . . . . .11A.2 FlowID Header Encapsulation . . . . . . . . . . . . .12A.3 IPSEC Protocol Modification . . . . . . . . . . . . .12A.4 AH Transparency . . . . . . . . . . . . . . . . . . .131 IntroductionRecently published Standards Track RFCs specify protocol mechanismsto provide IP level security. These IP Security, or IPSEC, protocols support packet level authentication, [RFC 1826], and integrity andconfidentiality [RFC 1827]. A number of interoperableimplementations already exist and several vendors have announcedcommercial products that will use these mechanisms.The IPSEC protocols provide service by adding a new header between a packet’s IP header and the transport (e.g. UDP) protocol header. The two security headers are the Authentication Header (AH), forauthentication, and the Encapsulating Security Payload (ESP), forintegrity and confidentiality.RSVP is being developed as a resource reservation (dynamic QoS setup) protocol. RSVP as currently specified [RFC 2205] is tailored towards IP packets carrying protocols that have TCP or UDP-like ports.Protocols that do not have such UDP/TCP-like ports, such as the IPSEC protocols, can be supported, but only with limitations.Specifically, for flows of IPSEC data packets, flow definition canonly be done on per IP address, per protocol basis.Berger & O’Malley Standards Track [Page 2]This memo proposes extensions to RSVP so that data flows containingIPSEC protocols can be controlled at a granularity similar to what is already specified for UDP and TCP. The proposed extensions can beused with both IPv4 and IPv6. Section 2 of this memo will provide an overview of extensions. Section 3 contains a description of extended protocol mechanisms. Section 4 presents extended protocol processing rules. Section 5 defines the additional RSVP data objects.2 Overview of ExtensionsThe basic notion is to extend RSVP to use the IPSEC SecurityParameter Index, or SPI, in place of the UDP/TCP-like ports. Thiswill require a new FILTER_SPEC object, which will contain the IPSECSPI, and a new SESSION object.While SPIs are allocated based on destination address, they willtypically be associated with a particular sender. As a result, twosenders to the same unicast destination will usually have differentSPIs. In order to support the control of multiple independent flows between source and destination IP addresses, the SPI will be included as part of the FILTER_SPEC. When using WF, however, all flows to the same IP destination address using the same IP protocol ID will share the same reservation. (This limitation exists because the IPSECtransport headers do not contain a destination demultiplexing valuelike the UDP/TCP destination port.)Although the RESV message format will not change, RESV processingwill require modification. Processing of the new IPSEC FILTER_SPECwill depend on the use of the new SESSION object and on the protocol ID contained in the session definition. When the new FILTER_SPECobject is used, the complete four bytes of the SPI will need to beextracted from the FILTER_SPEC for use by the packet classifier. The location of the SPI in the transport header of the IPSEC packets isdependent on the protocol ID field.The extension will also require a change to PATH processing,specifically in the usage of the port field in a session definition. An RSVP session is defined by the triple: (DestAddress, protocol ID, DstPort). [RFC 2205] includes the definition of one type of SESSION object, it contains UDP/TCP destination ports, specifically "a 16-bit quantity carried at the octet offset +2 in the transport header" orzero for protocols that lack such a field. The IPSEC protocols do Berger & O’Malley Standards Track [Page 3]not contain such a field, but there remains a requirement fordemultiplexing sessions beyond the IP destination address. In order to satisfy this requirement, a virtual destination port, or vDstPort, is introduced. The vDstPort value will be carried in the new SESSION object but not in the IPSEC transport header. The vDstPort allowsfor the differentiation of multiple IPSEC sessions destined to thesame IP address. See Section 5 for a discussion of vDstPort ranges. In PATH messages, the SENDER_TEMPLATE for IPSEC flows will have thesame format as the modified FILTER_SPEC. But, a new SESSION objectwill be used to unambiguously distinguish the use of a virtualdestination port.Traffic will be mapped (classified) to reservations based on SPIs in FILTER_SPECs. This, of course, means that when WF is used all flows to the same IP destination address and with the same IP protocol IDwill share the same reservation.The advantages to the described approach are that no changes toRFC1826 and 1827 are required and that there is no additional perdata packet overhead. Appendix A contains a discussion of theadvantages of this approach compared to several other alternatives.This approach does not take advantage of the IPv6 Flow Label field,so greater efficiency may be possible for IPv6 flows. The details of IPv6 Flow Label usage is left for the future.3 Object DefinitionThe FILTER_SPEC and SENDER_TEMPLATE used with IPSEC protocols willcontain a four byte field that will be used to carry the SPI. Rather than label the modified field with an IPSEC specific label, SPI, the label "Generalized Port Identifier", or GPI, will be so that theseobject may be reused for non-IPSEC uses in the future. The name for these objects are the IPv4/GPI FILTER_SPEC, IPv6/GPI FILTER_SPEC,IPv4/GPI SENDER_TEMPLATE, and IPv6/GPI SENDER_TEMPLATE. Similarly,the new SESSION objects will be the IPv4/GPI SESSION and the IPv6/GPI SESSION. When referring to the new objects, IP version will not beincluded unless a specific distinction between IPv4 and IPv6 is being made.Berger & O’Malley Standards Track [Page 4]3.1 SESSION ClassSESSION Class = 1.o IPv4/GPI SESSION object: Class = 1, C-Type = 3+-------------+-------------+-------------+-------------+| IPv4 DestAddress (4 bytes) |+-------------+-------------+-------------+-------------+| Protocol ID | Flags | vDstPort |+-------------+-------------+-------------+-------------+o IPv6/GPI SESSION object: Class = 1, C-Type = 4+-------------+-------------+-------------+-------------+| |+ +| |+ IPv6 DestAddress (16 bytes) +| |+ +| |+-------------+-------------+-------------+-------------+| Protocol ID | Flags | vDstPort |+-------------+-------------+-------------+-------------+3.2 FILTER_SPEC ClassFILTER_SPEC class = 10.o IPv4/GPI FILTER_SPEC object: Class = 10, C-Type = 4+-------------+-------------+-------------+-------------+| IPv4 SrcAddress (4 bytes) |+-------------+-------------+-------------+-------------+| Generalized Port Identifier (GPI) |+-------------+-------------+-------------+-------------+Berger & O’Malley Standards Track [Page 5]o IPv6/GPI FILTER_SPEC object: Class = 10, C-Type = 5+-------------+-------------+-------------+-------------+| |+ +| |+ IPv6 SrcAddress (16 bytes) +| |+ +| |+-------------+-------------+-------------+-------------+| Generalized Port Identifier (GPI) |+-------------+-------------+-------------+-------------+3.3 SENDER_TEMPLATE ClassSENDER_TEMPLATE class = 11.o IPv4/GPI SENDER_TEMPLATE object: Class = 11, C-Type = 4Definition same as IPv4/GPI FILTER_SPEC object.o IPv6/GPI SENDER_TEMPLATE object: Class = 11, C-Type = 5Definition same as IPv6/GPI FILTER_SPEC object.4 Processing RulesThis section presents additions to the Processing Rules presented in [RFC 2209]. These additions are required in order to properlyprocess the GPI SESSION and FILTER_SPEC objects. Values forreferenced error codes can be found in [RFC 2205]. As in with theother RSVP documents, values for internally reported (API) errors are not defined.4.1 Required ChangesBoth RESV and PATH processing will need to be changed to support the new objects. The changes ensure consistency and extend portprocessing.The following PATH message processing changes are required:o When a session is defined using the GPI SESSION object, onlythe GPI SENDER_TEMPLATE may be used. When this condition isviolated, end-stations should report a "Conflicting C-Type" API error to the application.Berger & O’Malley Standards Track [Page 6]o For PATH messages that contain the GPI SESSION object,end-stations must verify that the protocol ID corresponds to aprotocol known to use the GPI SESSION object. Values 51 (AH)or 50 (ESP) must be supported by implementations supportingthe described IPSEC extensions. If an unknown protocol ID isused, then the API should report an "API Error" to theapplication.o For such messages, the vDstPort value should be recorded.The vDstPort value forms part of the recorded state and is used to match Resv messages, but it is not passed to traffic control. Non-zero values of vDstPort are required. This requirementensures that a non-GPI SESSION object will never merge with aGPI SESSION object. Violation of this condition causes an"Invalid Destination Port" API error.The changes to RESV message processing are:o When a RESV message contains a GPI FILTER_SPEC, the sessionmust be defined using the GPI SESSION object. Otherwise, this is a message formatting error.o The GPI contained in the FILTER_SPEC must match the GPIcontained in the SENDER_TEMPLATE. Otherwise, a "No senderinformation for this Resv message" error is generated.o When the GPI FILTER_SPEC is used, each node must createa data classifier for the flow described by the quadruple:(DestAddress, protocol ID, SrcAddress, GPI). The data classifier will need to look for the four byte GPI at transport headeroffset +4 for AH, and at transport header offset +0 for ESP.4.2 Merging FlowspecsWhen using this extension for IPSEC data flows, RSVP sessions aredefined by the triple: (DestAddress, protocol Id, vDstPort).Similarly, a sender is defined by the tuple: (SrcAddress, GPI), where the GPI field will be a four byte representation of a generalizedsource port. These extensions have some ramifications depending upon the reservation style.4.2.1 FF and SE StylesIn the FF and SE Styles, the FILTER_SPEC object contains the(SrcAddress, GPI) pair. This allows the receiver to uniquelyidentify senders based on both elements of the pair. When mergingexplicit sender descriptors, the senders may only be consideredidentical when both elements are identical.Berger & O’Malley Standards Track [Page 7]4.2.2 WF StylesThese extensions provide very limited service when used with WF style reservations. As described, the SENDER_TEMPLATE and FILTER_SPEC each contain the GPI. In a WF style reservation, the RESV message doesNOT contain a FILTER_SPEC (after all, it is a wildcard filter), andthe SENDER_TEMPLATE is ignored (again, because any sender isallowed). As a result, classifiers may match all packets whichcontain both the session’s destination IP address and protocol ID to such WF reservations.Although a solution for this limitation is not proposed, this issueis not seen as significant since IPSEC applications are less likelyto use WF style reservations.5 IANA ConsiderationsThe range of possible vDstPort values is broken down into sections,in a fashion similar to the UDP/TCP port ranges.0 Illegal Value1 - 10 Reserved. Contact authors.11 - 8191 Assigned by IANA8192 - 65535 DynamicIANA is directed to assign the well-known vDstPorts using thefollowing criteria: Anyone who asks for an assigned vDstPort mustprovide a) a Point of Contact, b) a brief description of intendeduse, and c) a short name to be associated with the assignment (e.g."ftp").6 Security ConsiderationsThe same considerations stated in [RFC 2205], [RFC 1826], and [RFC1827] apply to the extensions described in this note. There are two additional issue related to these extensions.First, the vDstPort mechanism represents another data element aboutthe IP Flow that might be available to an adversary. Such data might be useful to an adversary engaging in traffic analysis by monitoring not only the data packets of the IP Flow but also the RSVP controlmessages associated with that Flow. Protection against trafficanalysis attacks is outside the scope of this mechanism. Onepossible approach to precluding such attacks would be deployment and use of appropriate link-layer confidentiality mechansisms, such asencryption.Berger & O’Malley Standards Track [Page 8]Secondly, Changes in SPI values for a given flow will affect RSVPflows and reservations. Changes will happen whenever that flowchanges its Security Association. Such changes will occur when aflow is rekeyed (i.e. to use a new key). Rekeying intervals aretypically set based on traffic levels, key size, threat environment, and crypto algorithm in use. When an SPI change occurs it will, inmost cases, be necessary to update (send) the correspondingSENDER_TEMPLATEs and FILTER_SPECs. IPSEC implementations, RSVPapplications, and RSVP end-station implementations will need to take the possibility of changes of SPI into account to ensure properreservation behavior. This issue is likely to be a tolerable, since rekeying intervals are under the control of local administrators.Many, if not most, RSVP sessions will not need to deal with thisrekeying issue. For those applications that do need to deal withchanges of SPIs during a session, the impact of sending new PATH and RESV messages will vary based on the reservation style being used.Builders of such applications may want to select reservation stylebased on interaction with SPI changes.The least impact of an SPI change will be to WF style reservations.For such reservations, a new SENDER_TEMPLATE will need to be sent,but no new RESV is required. For SE style reservations, both a newSENDER_TEMPLATE and a new RESV will need to be sent. This willresult in changes to state, but should not affect data packetdelivery or actual resource allocation in any way. The FF style will be impacted the most. Like with SE, both PATH and RESV messages will need to be sent. But, since FF style reservations result in senderreceiving its own resource allocation, resources will be allocatedtwice for a period of time. Or, even worse, there won’t be enoughresources to support the new flow without first freeing the old flow.A way around this FF/SPI-change problem does exist. Applicationsthat want FF style reservations can use multiple SE reservations.Each real sender would have a separate SESSION (vDstPort) definition. When it came time to switch SPIs, a shared reservation could be made for the new SPI while the old SPI was still active. Once the new SPI was in use, the old reservation could be torn down. This is lessthan optimal, but will provide uninterrupted service for a set ofapplications.Berger & O’Malley Standards Track [Page 9]7 References[RFC 2205] Braden, R., Ed., Zhang, L., Estrin, D., Herzog, S.,and S. Jamin, "Resource ReSerVation Protocol (RSVP)-- Version 1 Functional Specification", RFC 2205,September 1997.[RFC 2209] Braden, R., Ed., Zhang, "Resource ReSerVationProtocol (RSVP) -- Version 1 Message ProcessingRules", RFC 2209, September 1997.[RFC 1825] Atkinson, R., "Security Architecture for the InternetProtocol", RFC 1825, NRL, August 1995.[RFC 1826] Atkinson, R., "IP Authentication Header", RFC 1826, NRL, August 1995.[RFC 1827] Atkinson, R., "IP Encapsulating Security Payload", RFC1827, NRL, August 1995.8 AcknowledgmentsThis note includes ideas originated and reviewed by a number ofindividuals who did not participate in this note’s writing. Theauthors would like to acknowledge their contribution. We thank RanAtkinson <rja@>, Fred Baker <fred@>, Greg Troxel<gdt@>, John Krawczyk <jkrawczyk@> for muchappreciated input and feedback. Special appreciation goes to BobBraden <braden@> for his detailed editorial and technicalcomments. We also thank Buz Owen, Claudio Topolcic, Andy Veitch, and Luis Sanchez for their help in coming up with the proposed approach. If any brain-damage exists in this note, it originated solely fromthe authors.9 Authors’ AddressesLou Berger Tim O’MalleyFORE Systems BBN Corporation6905 Rockledge Drive 10 Moulton StreetSuite 800 Cambridge, MA 02138Bethesda, MD 20817Phone: 301-571-2534 Phone: 617-873-3076EMail: lberger@ EMail: timo@Berger & O’Malley Standards Track [Page 10]A Options ConsideredThis sections reviews other approaches that were explored indeveloping the described extensions. They are included here toprovide additional context into the general problem. All listedoptions were rejected by the working group.Four other options were considered:1. UDP EncapsulationAdd a UDP header between the IP and the IPSEC AH or ESPheaders.2. FlowID Header EncapsulationAdd a new type of header between the IP and the IPSEC AH orESP headers.3. IPSEC modificationModify IPSEC headers so that there are appropriate fields insame location as UDP and TCP ports.4. AH TransparencySkip over the Authentication Header packet classifierprocessing.A.1 UDP EncapsulationSince current SESSION and FILTER object expect UDP or TCP ports, this proposal says let’s just give it to them. The basic concept is toadd a UDP port between the IP and AH/ESP headers. The UDP portswould provide the granularity of control that is need to associatespecific flows with reservations.Source and destination ports would be used, as normal, in RSVPsession definition and control. The port fields would also need tobe used to identify the real transport level protocol (e.g. ESP)being used. Also since many UDP ports are assigned as well knownports, use of port numbers would be limited. So, the port fieldswould need to be used to unambiguously identify 1) the next levelprotocol, 2) the RSVP session, and 3) the RSVP reservation.The advantages of this option is that no RSVP changes are required.The disadvantages is that, since the headers aren’t in the expectedlocation, RFC 1826 and RFC 1827 are violated.Berger & O’Malley Standards Track [Page 11]A.2 FlowID Header Encapsulation[This option was originally proposed by Greg Troxel <gdt@>.]This option is very similar to option 1, but is more generic andcould be adopted as a standard solution. The notion is to use UDPlike ports for the sole purpose of flow identification. RSVP wouldtreat this new protocol exactly the same as UDP.The difference between this and UDP encapsulation is in destinationhost processing. The destination host would essentially ignore port information and use a new field, protocol ID, to identify whichprotocol should process the packet next. Some examples of protocolIDs correspond to TCP, UDP, ESP, or AH.The format of the FlowID Header would be:+---------------+---------------+---------------+---------------+| Source Port | Dest Port |+---------------+---------------+---------------+---------------+| Ver | Len | Protocol ID | Checksum |+---------------+---------------+---------------+---------------+1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 82 bytes source port 4 bits length-32 (2)2 bytes dest port 8 bits protocol ID4 bits version (1) 16 bits checksumThe advantage of this protocol is that flow identification isseparated from all other protocol processing. The disadvantage isthat the addition of a header violates RFC 1826 and 1827, and alsothat applications using RSVP will need to add this extra header onall data packets whose transport headers do not have UDP/TCP likeports.A.3 IPSEC Protocol ModificationThe basic notion of this option is to leave RSVP as currentlyspecified and use the Security Association Identifier (SPI) found in the IPSEC headers for flow identification. There are two issues with using the SPI. The first is that the SPI is located in the wronglocation when using Authentication (AH). The second issue is how to make use of the SPI.The first issue is easy to fix, but violates RFC 1826. UDP and TCPhave port assignments in the first 4 bytes of their headers, each is two bytes long, source comes first, then destination. The ESP header has the SPI in the same location as UDP/TCP ports, the AH doesn’t. Berger & O’Malley Standards Track [Page 12]The IP Authentication Header has the following syntax:+---------------+---------------+---------------+---------------+| Next Header | Length | RESERVED |+---------------+---------------+---------------+---------------+| Security Parameters Index |+---------------+---------------+---------------+---------------+| |+ Authentication Data (variable number of 32-bit words) || |+---------------+---------------+---------------+---------------+1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 8Simply reversing the first 4 bytes with the SPI we will have the SPI in the location that RSVP expects. This would be non-standard, orrequire a major (i.e. not backward compatible) change to RSVP 1826.The second issue is how to make use of the SPI. Per the current RSVP specification, the first two bytes of a flow’s SPI will need to becarried in the PATH message and the second two bytes in the RESVmessage. The biggest problem is that the SPI is normally selected by the receiver and is likely to be different for EACH sender. (Thereis a special case where the same SPI is used by all senders in amulticast group. But this is a special case.) It is possible tohave the SPI selected prior to starting the RSVPsession. This willwork for unicast and the special multicast case. But using thisapproach means that setup time will usually be extended by at least 1 round trip time. Its not clear how to support SE and WF stylereservations.The advantage of this approach is no change to RSVP. Thedisadvantages are modification to RFC1827 and limited support of RSVP reservation styles.A.4 AH TransparencyThe source of the RSVP support of IPSEC protocols problem is that the real transport header is not in the expected location. With ESPpackets, the real source and destination ports are encrypted andtherefore useless to RSVP. This is not the case for authentication. For AH, the real header just follows the Authentication Header. So, it would be possible to use the real transport header for RSVPsession definition and reservation.To use the transport header, all that would need to be done is forthe flow classifier to skip over AHs before classifying packets. No modification to RSVP formats or setup processing would be required.Applications would make reservations based on transport (i.e., UDP or Berger & O’Malley Standards Track [Page 13]TCP) ports as usual.The advantages of this approach are no changes to either IPSECprotocols or RSVP formats. The major disadvantage is that routersand hosts must skip all AHs before classifying packets. The working group decided that it was best to have a consistent solution for both AH and ESP.Berger & O’Malley Standards Track [Page 14]。
