Submitted to IROS 2003 A Simple and Scalable Approach for HumanSystem Interaction
2003年考研英语作文题目及范文主题

2003年考研英语作文题目及范文主题全文共3篇示例,供读者参考篇1Title: 2003 Postgraduate Entrance Examination English Composition Topic and Sample EssayIn 2003, the topic for the English composition section of the postgraduate entrance examination was "Discuss the impact of globalization on society and the environment." This was a wide-ranging and complex topic that required candidates to demonstrate a thorough understanding of the issues surrounding globalization and its effects on various aspects of society and the environment.Globalization is a term that has become increasingly prevalent in recent years, as the world has become more interconnected through advances in technology and increased international trade and communication. While globalization has brought many benefits, such as increased economic growth and cultural exchange, it has also had a number of negative consequences, particularly in terms of its impact on society and the environment.One of the key effects of globalization on society has been the widening gap between the rich and the poor. As multinational corporations expand their reach and take advantage of cheap labor in developing countries, income inequality has increased both within and between countries. This has led to social unrest and instability in many parts of the world, as people feel marginalized and left behind by the forces of globalization.Globalization has also had a significant impact on the environment, as increased industrialization and the expansion of global supply chains have led to widespread pollution and environmental degradation. Deforestation, air and water pollution, and climate change are just some of the environmental issues that have been exacerbated by the forces of globalization. These environmental problems not only threaten the health and well-being of people around the world, but also endanger the long-term sustainability of the planet.In order to address these challenges, it is essential for society to take a more holistic and sustainable approach to globalization. This requires not only greater regulation and oversight of multinational corporations, but also a shift towards more environmentally-friendly and socially-responsible businesspractices. It also requires greater international cooperation and coordination, as the issues surrounding globalization are inherently global in nature and cannot be solved by any one country or organization alone.In conclusion, the impact of globalization on society and the environment is a complex and multifaceted issue that requires careful consideration and thoughtful action. By acknowledging the challenges and opportunities presented by globalization, and working together to find solutions that benefit all members of society and protect the environment, we can ensure a more sustainable and equitable future for generations to come.Overall, the 2003 postgraduate entrance examination English composition topic on the impact of globalization on society and the environment was a timely and relevant issue that required candidates to demonstrate their knowledge and critical thinking skills. By addressing the complexities of this topic in their essays, candidates were able to showcase their ability to analyze and evaluate complex social and environmental issues, and propose thoughtful solutions for a more sustainable and equitable future.篇2Title: 2003 National Postgraduate Entrance Examination English Writing Topic and Sample EssayIn 2003, one of the writing topics for the National Postgraduate Entrance Examination in China was "Learning to Be Alone". This topic encouraged candidates to reflect on the importance of solitude and independence in personal growth and development. Below is a sample essay that addresses this topic:Sample Essay:Learning to Be AloneIn today's fast-paced world, it seems that we are constantly surrounded by people, noise, and distractions. From our work to our social life, it can be difficult to find moments of solitude and time for self-reflection. However, learning to be alone is an essential skill that can greatly benefit our personal growth and well-being.Being alone does not necessarily mean being lonely. In fact, solitude can provide us with a valuable opportunity to disconnect from the outside world and connect with ourselves. It gives us the space to explore our thoughts, feelings, and desires without the influence of others. By spending time alone, we cangain a deeper understanding of who we are, what we value, and what we want out of life.Furthermore, being alone allows us to cultivate independence and self-reliance. When we are constantly surrounded by others, it can be easy to become dependent on their opinions, approval, and support. However, by learning to be alone, we can develop the confidence and resilience to stand on our own two feet. We can make decisions based on our own beliefs and values, rather than seeking validation from external sources.Moreover, solitude can be a source of creativity and inspiration. When we are alone, our minds are free to wander and explore new ideas and perspectives. We can engage in activities that bring us joy and fulfillment, whether it's reading a book, writing in a journal, or pursuing a hobby. By embracing solitude, we can tap into our inner creativity and unlock our full potential.In conclusion, learning to be alone is a valuable skill that can enhance our personal growth and well-being. Solitude provides us with the opportunity to connect with ourselves, develop independence, and cultivate creativity. By embracing moments of solitude in our busy lives, we can discover a sense of peace,clarity, and self-discovery that is essential for our emotional and mental health.Overall, the 2003 National Postgraduate Entrance Examination English Writing Topic of "Learning to Be Alone" challenged candidates to reflect on the benefits of solitude and independence in personal growth. By exploring this topic in depth, candidates were able to showcase their ability to think critically, express their ideas effectively, and engage with complex themes.篇3Title: 2003 Postgraduate English Writing Topic and Sample Essay ThemeIntroduction:The year 2003 was an important year for postgraduate students in China, as it marked the implementation of a new English writing test in the entrance examination. The topic of the essay was a pivotal part of the test, requiring students to demonstrate their language proficiency and critical thinking skills. In this article, we will delve into the 2003 postgraduate English writing topic and provide a sample essay as a reference for future test-takers.2003 Postgraduate English Writing Topic:The 2003 postgraduate English writing topic revolved around the theme of globalization and its impact on society. Test-takers were asked to discuss the following prompt:"Globalization has brought about significant changes to the world in recent years. Discuss the positive and negative effects of globalization on society, and provide examples to support your argument."Sample Essay:Globalization, as a phenomenon that has been shaping the world for decades, has had both positive and negative effects on society. In this essay, we will delve into the various aspects of globalization and analyze its impact on different aspects of society.On the positive side, globalization has led to increased interconnectivity and cultural exchange between nations. The ease of travel and communication has allowed people from different parts of the world to interact and learn from each other, leading to a more diverse and inclusive society. Additionally, globalization has facilitated the spread of technology andinnovation, leading to advancements in various fields such as medicine, communication, and transportation.Furthermore, globalization has also opened up new opportunities for economic growth and development. The integration of markets and the flow of goods and services across borders have created new avenues for trade and investment, boosting the economies of many countries. This has led to the creation of jobs, increased standard of living, and improved access to goods and services for people around the world.However, globalization also has its downsides. One of the negative effects of globalization is the widening wealth gap between the rich and the poor. As multinational corporations expand their operations, they often exploit cheap labor in developing countries, leading to inequality and social unrest. Moreover, the cultural homogenization brought about by globalization has led to the erosion of traditional customs and values, threatening the diversity and uniqueness of different societies.In addition, globalization has also been blamed for the degradation of the environment. The unbridled consumption and production driven by globalization have led to increased pollution, deforestation, and depletion of natural resources,posing a threat to the sustainability of the planet. Climate change, as a result of globalization, has become a pressing issue that requires global cooperation and action.In conclusion, globalization has had both positive and negative effects on society. While it has brought about increased connectivity, economic growth, and technological advancements, it has also led to social inequality, cultural homogenization, and environmental degradation. It is imperative for policymakers, businesses, and individuals to address the challenges posed by globalization and work towards creating a more equitable, sustainable, and inclusive world.Conclusion:The 2003 postgraduate English writing topic on globalization was a thought-provoking prompt that required test-takers to critically analyze the impact of this phenomenon on society. The sample essay provided in this article serves as a reference for future test-takers, highlighting the key points to consider when discussing the positive and negative effects of globalization. As the world continues to become more interconnected, it is essential for individuals to understand the implications of globalization and work towards building a more sustainable and inclusive global community.。
2003年考研英语作文答案

The Evolution of Technology and Its Impacton Society in 2003In the year 2003, the world was undergoing significant technological advancements that were revolutionizing various aspects of society. The internet, which had already established itself as a global phenomenon, was evolving rapidly, connecting people across the globe in unprecedented ways. Cellular phones, then still in their infancy, were starting to revolutionize communication, enabling people to stay connected regardless of their location.The impact of these technological advancements was felt in every sphere of life. In the realm of education, the internet provided access to vast repositories of knowledge, enabling students and researchers to explore topics beyond the confines of their physical libraries. Distance learning became a viable option, breaking down barriers and allowing individuals to pursue higher education regardless of their geographical location.Moreover, the business world was also transformed by the technological revolution. E-commerce was in its nascentstages, but it was already starting to change the waypeople shopped. Online stores provided convenience and a wider range of choices, appealing to consumers who valued efficiency and diversity.In the realm of entertainment, streaming services were beginning to emerge, offering a new way to consume music, movies, and TV shows. This not only provided consumers with more options but also allowed them to customize their viewing experience, shaping the future of media consumption. However, the rapid technological growth in 2003 was not without its challenges. The increasing interconnectednessof the world brought about concerns regarding privacy and security. With the rise of the internet, issues like cybercrime and data breaches started to emerge,necessitating the development of robust security measuresto protect personal information.Furthermore, the digital divide, the gap between those who had access to technology and those who did not, becamea pressing issue. This divide was not only economic butalso cultural and geographical, limiting the benefits of technological advancements to certain segments of society.Despite these challenges, the technological advancements in 2003 marked a significant milestone in the evolution of society. They paved the way for future innovations that have continued to reshape our world. From the widespread adoption of smartphones to the rise of social media and the internet of things, the technological revolution has transformed the way we live, work, and communicate.Looking back at 2003, it is evident that the technological advancements of that era laid the foundation for the interconnected and digital world we live in today. As we continue to navigate the complexities of this technological landscape, it is important to recognize the impact it has had on society and to address the challenges that lie ahead.**技术与社会的相互影响——2003年回顾**2003年,世界正经历着显著的技术进步,这些进步正在改变社会的各个方面。
Age-old Question(naire)s

Age-old Question(naire)sJoy Goodman, Department of Computing Science, University of Glasgow (joy@),Audrey Syme, Roos Eisma, Department of Applied Computing, University of DundeeAbstractOlder people are an important and growing sector of the population, yet are often excluded by design. It is important to find out more about this user group so that they can be included effectively. As a first step towards this, we carried out a questionnaire and interview study in Scotland with 353 participants over the age of 50, investigating their use of and attitude towards technology. This is a method which can be very useful yet also fraught with difficulties. This paper therefore discusses how it can be used effectively, observing in particular the use of survey interviews in extracting more in-depth information. It also describes the study and some of its results, discussing trends in technology use among older people and possible reasons for these trends, noting in particular the effect of technology age and complexity. It also discusses the implications for designers.1. IntroductionRecent statistics show that the proportion of older people in developed countries is rapidly increasing [8]. Although this is a group with many people with large amounts of disposable income, they are often excluded by design, particularly of technological products [1]. This has prompted some recent work on design that includes older people, for example the Utopia project (Usable Technology for Older People: Inclusive and Appropriate – /projects/utopia), which has been formed expressly to address this issue. However there is still much to learn about the way this group relates to technology before design that includes older people can really be effective.There are several ways in which such knowledge can be obtained, such as interviews, focus groups, ethnographic methods and experiments. However, the diversity within the older population renders large-scale methods, in particular, questionnaire surveys, particularly useful for an initial investigation. Questionnaires can be problematic with poor return rates and self-selecting respondents, which can lead to biased results. In addition, it can be difficult to elicit in-depth information. However, their ability to obtain large-scale information relatively inexpensively means that the effort to overcome these problems is worth-while.Questionnaires have been used to survey basic aspects of older people’s technology use, particularly their computer and internet use. In the UK and Europe, surveys (e.g. [2,4,5]) indicate a drop in technology use with age. But these studies have often focused on specific technologies, and therefore do not provide a picture of technology use as awhole. Most also do not consider the trends within the older population nor the reasons for them.Therefore, as part of the Utopia project, we conducted a medium-scale questionnaire and interview study into the experiences of older people with technology. This paper describes the study and discusses the use of questionnaires as a means of getting to know user groups, focusing in particular on how to obtain more in-depth data. It also presents some of the results of the study, focusing on trends in technology use. We discuss what these indicate about reasons for technology use in this age group, and some implications of the results for designers.2. Method2.1 SampleThe sample comprised 353 older adults from Scotland, 25% aged 50-64, 43% 65-74, 27% 75-84 and 5% 85 or older. The gender distribution was female (68%) and male (32%).We used various methods of convenience sampling, distributing 42% of the received questionnaires through organisations, 38% directly through a researcher, using a variety of contact means, 17% through a relative or friend, and 3% through other means. These methods have more sampling bias than, for example, probability sampling using mail shots. However they allow more personal contact, and so richer, more in-depth information can be elicited, helping us to get to know the group better. They also let us develop contacts, both with organisations and individuals, for future work. For our survey these factors were important goals.Some effort was made to balance the age groups and computer experience of the sample, through the choice of organisations contacted. However the middle two age groups are still over-represented and it is also likely that participants use technology more than average. Therefore this paper mostly discusses trends in technology use, which are likely to hold true for the general population.2.2 ProcedureThe questionnaire was piloted with a small number of older adults (n=19). As a result, the structure of tables was clarified and more options were added to multiple-choice questions.The questionnaires were distributed between May and November 2002, as described above. They were mostly distributed through organisations, and were administered in an informal interview situation within libraries, sheltered housing complexes and social clubs. The questionnaire was self-administered by 74% of the sample and administered to 26%, mostly to older participants.Questionnaires distributed outside Scotland were excluded from statistical analysis.2.3 MaterialsThe start of the questionnaire described the Utopia project, the questionnaire’s aims, use of the data and instructions for completing the questionnaire. The body of the questionnaire comprised both closed multiple-choice and open-ended questions. It included demographic and lifestyle topics like age group, gender, accommodation and activity, so that their effect on technology use could be explored. It investigated the use of everyday technology, like televisions, telephones, videos and teletext, as well as that of computers. It also included short questions about a range of technology including mobile phones, DVDs and interactive TV, as well as more traditional technologies such as radios and microwaves. Space was provided at the end for comments on any area of technology. Finally, respondents were asked if they would like to participate further in the Utopia project, and could give contact details if interested.3. ResultsThere is not room to discuss all of the questionnaire’s results here. This paper concentrates on trends in technology use in order to investigate some of the factors affecting it and how these can be taken into account in product design and development.3.1 Differences with AgeFigure 1 shows the results for mobile phone use. There is a general decrease in their use with age, which is significant using a Chi squared test (p<0.01).Figure 1: Mobile phone use in the older population.Almost all the technologies surveyed show a similar decrease in use with age, significant using Chi squared (p<0.05 or p<0.01). This includes all the technologies listed in Table 2 below, except telephones, televisions and microwaves, which are not significantly affected.3.2 Differences with TechnologyDifferent technologies have different degrees of popularity and are affected by age to different extents, as shown in Table 2. In it, the significance values differ from thoseabove because only current use is considered.Overall frequency 50-64 65-74 75-84 85+ Significant ageeffectTelephone 99 100 99 98 100 NS (P>0.05) Television 98 98 98 100 100 NS (P>0.05) Radio 96 98 98 93 75 P<0.01 Microwave 85 92 86 76 62 P<0.01Video 83 89 90 70 62 P<0.01 CD player 72 85 78 52 28 P<0.01Computer 63 90 37 38 28 P<0.01 Mobile Phone 60 80 64 41 18 P<0.01Teletext 58 68 62 45 33 P<0.01 Personal Stereo 36 43 43 17 22 P<0.01Cable TV 28 36 22 29 13 NS (P>0.05)Text Messaging 19 32 20 5 5 P<0.01DVD 9 17 9 2 0 P<0.01 Interactive TV 7 11 6 5 0 P<0.01Internet through TV 2 4 2 2 0 NS (P>0.05)Table 2: Frequency (%) of current technology use (occasional or frequent) by age group.Telephones and televisions are the most popular and their use does not decline with age. Radios, microwaves and videos are also popular but their use is affected by age, while cable TV and internet through a TV are not significantly affected but are not very popular.3.3. Differences with Technology Age and ComplexityWe examined the effect of “technology age” on popularity by ranking technologies in approximate age order. We also considered the effect of technology complexity.However, because this is difficult to measure, we used a very approximate orderingwithin technologies of similar type.Figure 3 shows that, among the telecommunications equipment surveyed, there is adecrease in use with decreasing technology age and increasing complexity. Thedifferences in use are significant using one-sample proportions tests (p<0.01).Similarly, Figure 4 shows a general decrease in radio and television use as devices become newer, with the exception of radio (differences are significant using one-sample proportions tests, p<0.01). The effect of technology complexity is harder to discern as it depends heavily on the particular equipment and use. However we consider videos to be more complex than teletext or cable TV, since most video users in our survey used timer record, which is usually relatively complex. Yet videos are much more popular than these other technologies.3.4 CommentsComments given by respondents illuminate these figures by indicating barriers to and reasons for technology use by older people. The most common problem cited was psychological discomfort, such as confusion, frustration and lack of understanding. The feeling of being too old for new technology was also mentioned several times, e.g. “Too old to bother with more modern things” and “I am too old to learn new tricks”. Otherbarriers mentioned included cost and physical difficulties. Positive comments mostly focused on usefulness, mentioning a range of equipment with specific uses.4. Discussion4.1 Questionnaire methodologyWe suggest that administering a questionnaire face-to-face augments the questionnaire’s value. In this case the questionnaire not only provides useful figures and information, but can lead to further discussion and insight into how this user group relates to technology.In our survey, the questionnaire served as a stepping stone to further discussion on the technologies under investigation. For example, a closed question about mobile phones would, on occasion, evoke further discussion with a demonstration of the user’s own mobile phone. The researcher could then observe the user in action with their mobile, and see, for example, if they used all of the functions available and what problems they had. The researcher could then probe further, asking what they liked about it, why they didn’t use it or why they felt the need to buy one.Administering the questionnaire face-to-face also sometimes provided the opportunity to see how a device fitted into the user’s life. For instance, one respondent tentatively explained that he “thought” he could connect to the internet on his mobile phone, but had no idea how to use it. He didn’t even use the mobile frequently, but only when he visited his sister, as she lived in a caravan in the country. Another respondent, whose usage of technology was extremely minimal, became very animated when asked about her use of a microwave. She reported not being able to “live without it”. She said that, although she lived in a sheltered housing complex, she wanted to be as independent as possible with her cooking and that the microwave allowed her to do this.The questionnaire would also evoke discussions of devices not included in the questionnaire. For example, those in the oldest age group would often talk about the safety alarms they carried around, reporting design problems, such as them being too bulky or showing through their blouses. This brings up important concerns that would not otherwise be discovered in this study.These spontaneous excursions into own experiences and demonstrations of various personal devices were not rare events during the administration of the questionnaire. Additionally, attitudes towards technology could be expressed more easily in such a session. Although the comments sections allowed the respondents to express their opinions and attitudes, not all felt that they could do this. For example, when a 94 year respondent was asked if she knew what a personal stereo was or if she used one, she replied “What the heck would I do with that?”. These insights into respondents’ attitudes towards technology use go further than simple indications of frequency of use. Such expressions of attitude also help researchers to identify potential participants for further research.4.2 Trends in Technology use4.2.1 Age EffectsOur results show a significant decline with age in the use of most technologies. Exceptions are telephones, televisions and possibly microwaves. This agrees with other surveys [2,4,7] which have identified these trends across the age span as a whole, using coarser age groupings. We extend their results, showing that these trends continue within the older population. This also supports the few studies that have examined within this group (e.g. [5]).We cannot assume that this decline will disappear when those familiar with technology become the next generation of “older people”. Not only is new technology being continuously developed, but the figures for radio use show that age trends may continue even for well-established technology.This trend may make designers think that it is not worth-while developing products with this user group in mind. However the figures, while generally decreasing with age, are high enough to represent a large market, and negate assumptions that older people are not interested in technological products.Nevertheless, this trend does exist and presents a challenge when designing for older people. In order to meet this challenge, it is important to consider the reasons for it and make efforts to overcome them.4.2.2 ReasonsVarious reasons for differences in technology popularity in the general population have been proposed including the technology’s age, its cost in money and time, its learning curve and the extent of positive feedback from others [3]. These and similar reasons may also help to explain the trend described above.Length of time a technology has been availableThe most popular technologies are the telephone, television, radio, microwave and video. In addition, telephone, television and microwave use are not greatly affected by age. These technologies are all fairly well-established and were introduced earlier than the other devices surveyed, indicating that older technologies are more popular. This can also be seen within telecommunications and radio/TV devices. This may be caused, in part, by older people’s greater familiarity with older devices.However television is more popular than radio, despite radio being introduced much earlier. In addition, radios were popular when all the age groups surveyed were young adults, and so all groups should be equally familiar with them. Yet radio use continues to decline with age, suggesting that a technology’s age is not the only determining factor. This factor can be addressed, in part, by building on existing technologies and designing new devices to look like and use similar interfaces to older ones. Technology complexityThe complexity of a device, particularly of its interface, greatly affects its ease of use [6]. Many of the comments referred to psychological barriers related to complexity,indicating that this is a problem. It is therefore important to keep interfaces simple and have them evaluated by older people.However the relative popularity of videos compared to teletext and cable TV indicates that there is no simple relationship between complexity and technology use – decreased complexity does not always result in increased use.Other factorsThe positive questionnaire comments indicate that technology use is likely to increase if it is perceived to be useful. This applies not just to usefulness for practical activities, but also for entertainment, as shown by the popularity of television and radio. However usefulness is a difficult concept to determine, as it varies from person to person. It is important to find out what the users want and what they consider to be useful, and then to target design and marketing to their needs.Another frequently mentioned barrier was the feeling of being too old for new technology. One possibility for overcoming this is to demonstrate that older people can use technology, by making more usable systems, by appropriate training and by featuring older people in advertising and media.5. ConclusionsQuestionnaires can be a useful means for finding out about the older population, particularly in the early stages of a project. As well as quantitative data, they can provide an opportunity for further discussion with older people, allowing one to get to know the user group better. This paper presents some of the key results from such a study, highlighting trends towards decreasing technology use with age and discussing possible reasons for this, such as the effect of technology age and complexity. These barriers to use can be overcome, at least to some extent, by appropriate design.In the future, we hope to build on this work by investigating older people’s interactions with technology using different methodologies in smaller scale studies with novel applications.AcknowledgementsThis work is funded by the SHEFC UTOPIA project. We would also like to thank all of the organisations who helped us to distribute our questionnaire.References[1] Czaja, SJ and Lee, CC (2003). Designing Computer Systems for Older Adults. In The Human-Computer Interaction Handbook, ed. Jacko, JA and Sears, A. Mahwah, New Jersey. Chapter 21, 413-427[2] Down, D (2002). Family Spending - A report on the 2000-2001 FamilyExpenditure Survey. The Stationary Office, London, UK. Also available at/StatBase/Product.asp?vlnk=361&Pos=6&ColRank=1&Rank =272[3] Hamill, L (2000). The Introduction of New Technology into the Household. Personal Technologies, vol 4, 1-16[4] ICM Research for AgeConcern and Barclays (2002). Internet turns on men and women in different ways - new survey reveals./reviews/2002/it-internet-old-people.htm, August[5] Kubitschke, L, Hüsing, T, Strähler, B and Stroetmann, KA (2002). Older Citizens (50+) and European markets for ICT products and services: Representative data from the SeniorWatch user surveys. empirica Gesellschaft für Kommunikations-und Technologieforschung mbH. Chart report. Available from/swa/download/reports/SWA_chart_report.pdf[6] Norman, DA (1998). The Design of Everyday Things. MIT Press.[7] Rogers, WA, Cabrera, EF, Walker, N, Gilbert, DK and Fisk, AD (1996). A Survey of Automatic Teller Machine Usage across the Adult Life Span. Human Factors, vol 38, 156-166[8] U.S. Census Bureau (2002). International Data Base./ipc/www/idbnew.html (Updated: 10/10/02)。
2003联合军演英语作文

2003联合军演英语作文In the year 2003, a significant event took place that captured the attention of the world - the Joint Military Exercise between multiple nations. This exercise, which involved several countries from different continents, marked a milestone in international cooperation andmilitary strategy. The aim of this exercise was to strengthen military ties, enhance interoperability, and demonstrate the resolve of the participating nations in maintaining global peace and security.The exercise was planned and executed with utmost precision, involving thousands of troops, advanced weaponry, and complex strategies. The participating nations included the United States, European countries, and several others from Asia and the Pacific region. Each country brought its unique military capabilities and expertise, creating a diverse and comprehensive display of military might.The exercise was divided into various phases, each designed to test the troops' abilities in different scenarios. There were live-fire exercises, tactical manoeuvres, and simulations of combat situations. Theparticipating troops demonstrated exceptional coordination, discipline, and professionalism, showcasing their readiness to respond to any contingency.The significance of this exercise was not just in the scale and complexity but also in the message it sent to the world. It was a clear indication of the willingness of the participating nations to work together in times of crisis. It also served as a reminder of the importance of military preparedness and the role it plays in maintaining global stability.From a strategic perspective, the exercise was a resounding success. It achieved its objectives of improving military cooperation, enhancing interoperability, and demonstrating the participating nations' commitment to global peace and security. The exercise also provided valuable insights into the capabilities and strategies of the participating troops, which will be invaluable infuture military operations.The legacy of the Joint Military Exercise 2003 is profound. It remains a testament to the power of international cooperation and the importance of militarypreparedness in maintaining global peace and security. The exercise has set a precedent for future military exercises and cooperation, paving the way for stronger military alliances and a more secure world.**中文内容****2003年联合军演:全球视角**2003年,一件引起全球关注的重要事件发生了——多国联合军演。
2003北京第二外国语学院----综合英语

2003北京第二外国语学院----综合英语2003 年硕士研究生入学考试试卷考试科目:综合考试(英美文学)满分:40分I. Complete the following sentences by choosing and circling the best alternative (A, B or C) under each (20 points):1. The most prevalent kind of literature in feudal England was _. It was a long composition, sometimes in verse, sometimes in prose. describing the life and adventures of a noble here.A. the farceB. the romance C the melodrama2. Geoffrey Chaucer's language, now called . is vivid and exact.A. Old EnglishB. Middle EnglishC. Primitive English3. Apart from its religious significance, has had a great influence on English language and literature.A. the King Arthur BibleB. the King George BibleC. the King James Bible4. The Tragical History of Doctor Faustus was written by .A. Christopher MarloweB. John MiltonC. William Shakespeare5. John Donne (1573-1631), the founder of the school of poetry, lived and wrote during the successive reigns of Elizabeth to Charles I.A. MetaphoricalB. MetamorphicC. Metaphysical6. Essay on Criticism, a didactic poem written by Alexander Pope in heroic couplets, tells the poets and critics how to write and appreciate poetry according to the principles set up by the old writers.A. Anglo-SaxonB. Greek and RomanC. French and German7. The following quotation is taken from William Blake's The Marriage of Heaven and Hell—"What is now proved was once only "A. imagin'dB. reason'dC. learn'd8. William Wordsworth, have often been mentioned as the "Lake Poets" because they lived in the lake district in the northwestern part of England.A. John Keats and William Butler YeatsB. Samuel Taylor Coleridge and Robert SoutheyC. George Gordon Byron and Percy Bysshe Shelley9. Walter Scott's historical novels may be conveniently divided into three groups according to their subject-matter, namely, the group on the history of , the group on English history and the group on the history of European countries.A. ScotlandB. WalesC. Northern Ireland10. Matthew Arnold said, "It is of the last importance that English criticism should clearly discern what rule for its course, in order to avail itself of the field now opening to it; and to produce fruit for the future it ought to take. The rule may be summed upin one word ."A. disobedienceB. disinterestednessC. disconnectedness11. American literature grew out of humble origins. Diaries, histories, journals, letters, commonplace books, travel books, sermons, in short, personal literature in its various forms, occupied a major position in the literature of .A. the early colonial periodB. the pre-colonial periodC. the pre-Christian period12. Puritan influence over American romanticism was conspicuously noticeable. One of its palpable manifestations was the fact that American romantic writers tended more than their English and European brothers.A. to socializeB. to philosophizeC. to moralize13. Alone in the woods one day, experienced a moment of ecstasy which he recorded thus in his Nature: "I become a transparent eye-ball. I am nothing. I see all. The currents of the Universal Being circulate through me; I am part or panicle of God.".A. Benjamin FranklinB. Henry David ThoreauC. Ralph Waldo Emerson14. Henry David Thoreau helped Ralph Waldo Emerson edit the Transcendentalist journal The Dial, and was susceptible to oriental influences such as Hinduism and .A. ConfucianismB. MaterialismC. Epicureanism15. A handy way of seeing modern American poetry is to find its sources in the two founts, .A. Wallace Stevens and Sylvia PlathB. Walt Whitman and Emily DickinsonC. Robert Frost and Elizabeth Bishop16. Although William Dean Howells, Henry James and Mark Twain all worked for ,there were obvious differences between them. In thematic terms, for instance, James wrote mostly of the upper reaches of American society, and Howells concerned himself chiefly with middle class life, whereas Twain dealt largely with the lower strata of society.A. naturalismB. neoclassicismC. realism17. The reason that Ezra Pound and Amy Lowell found value in Chinese poetry was because Chinese poetry is, by virtue of the ideographic and pictographic nature of the Chinese language, essentially poetry.A. impressionisticB. imagisticC. expressionistic18. F. Scott Fitzgerald's s eeks to trace the moral doom of its protagonist to thesapping influence of wealth and portrays an America dying, in bar-room brawls and decadence, of spiritual sterility and meaninglessness which characterized the times.A. The Gilded AgeB. The Sun Also RisesC. Tender Is the Night19. Both Beyond the Horizon and The Hairy Ape were written by .A. Eugene O'NeillB. Arthur MillerC. Sinclair Lewis20. career reached its exciting climax in 1976 when he was awarded the Pulitzer Prize and the Nobel Prize for Literature.A. Saul Bellow'sB. John Steinbeck'sC. William Faulkner'sII. Read the following poem by William Butler Yeats, and answer the three questions (10 points):The Second ComingTurning and turning in the widening gyreThe falcon cannot hear the falconer;Things fall apart; the centre cannot hold;Mere anarchy is loosed upon the world,The blood-dimmed tide is loosed, and everywhereThe ceremony of innocence is drowned;The best lack all conviction, while the worstAre full of passionate intensity.Surely some revelation is at hand:Surely the Second Coming is at hand.The Second Coming! Hardly are those words outWhen a vast image out of Spiritus MundiTroubles my sight: somewhere in sands of the desertA shape with lion body and the head of a man,A gaze blank and pitiless as the sun,Is moving its slow thighs, while all about tReel shadows of the indignant desert birds.The darkness drops again; but now I knowThat twenty centuries of stony sleepWere vexed to nightmare by a rocking cradle,And what rough beast, its hour come round at last,Slouches towards Bethlehem to be born?1. What images are used in the first stanza? What do they indicate respectively?2. What are the implications of the description of the "rough beast" in the second stanza?3. Why do you think the poem ends with a question mark?III. The following excerpt is taken from the short story A Clean, Well-Lighted Place by Ernest Hemingway. Read it, and answer the three questions (10 points): "Good night," said the younger waiter."Good night," the other said. Turning off the electric light he continued the conversation with himself. It is the light of course, but it is necessary that the place be clean and pleasant. You do not want music. Certainly you do not want music. Nor can you stand before a bar with dignity although that is all that is provided for these hours. What did he fear? It was not fear or dread. It was a nothing that he knew too well. It was all a nothing and a man was nothing too. It was only that the light was all it needed and a certain cleanness and order. Some lived in it and never felt it but he knew it all was nada y pues nada y nada y pues nada. Our nada who art in nada, nada be thy name thy kingdom nada thy will be nada in nada as it is in nada. Give us this nada our daily nada and nada us our nada as we nada our nadas and nada us not into nada but deliver us from nada; pues nada. Had nothing full of nothing, nothing is with thee. He smiledand stood before a bar with a shining steam pressure coffee machine."What's yours?" asked the barman."Nada.""Otro loco mas." said the barman and turned away."A little cup," said the waiter.The barman poured it for him."The light is very bright and pleasant but the bar is unpolished." the waiter said.The barman looked at him but did not answer. It was too late at night for conversation."You want another copita?" the barman asked."No, thank you," said the waiter and went out. He disliked bars and bodegas. A clean, well-lighted cafe was a very different thing. Now, without thinking further, he would go home to his room. He would lie in the bed and finally, with daylight, he would go to sleep. After all, he said to himself, it is probably only insomnia. Many must have it.1.What is the significance of the parodied Lord's Prayer?2.Why does the older waiter think that a clean, well-lighted cafe is "a very different thing"?3.What is the significance of the last sentence of the story ("Many must have it.")?2003 年硕士研究生入学考试试卷考试科目:综合考试(语言学)满分:30分I. Fill in each blank with a proper term. (15 points )1.L inguistics is usually defined as the ____ study of language.2.O ne general principle of linguistic analysis is the primacy of speech over .3.I n Saussure's view, the relationship betweensignifier(sound image) and signified (concept) is .4.T he branch of linguistics which studies the sound patterns of a language is called .5.A________ morpheme is one that cannot constitute a word by itself.6.The branch of general linguistics which is named ____ s tudies the internal structure of sentences.7.The relation, which was originally called associative relation by Saussure, is a relation holding between elements replaceable with each other at a particular place in a structure, or between one element present and the others absent.8.The sense relation between " A lent a book to B" and "B borrowed a book from A" is________..9.The sound [k] can be described with "voiceless, ____ , stop".10.Human languages enable their users to symbolize objects, events and concepts which are not present (in time and space) at the moment of communication. This quality is labelled as .11.Antonyms like "husband" v. "wife" are antonyms.12.Terms like "desk" and "stool" are ____ of the term " furniture".13.According to G. Leech, ______ meaning refers to logic, cognitive, or denotative content.14.IC is the short form of immediate ___ used in the study of syntax.15.Chomsky initiated the distinction between ___ and performance.II. Choose the correct one among the three choices for each statement. (5points) 1.A sound which is capable of distinguishg one word or one shape of word from another in agiven language is a ________________________ .a. allophoneb. phone c phoneme2.T he is the minimal distinctive unit in grammar, a unit which cannot be dividedwithout destroying or drastically altering the meaning, whether it is lexical or grammatical.a. morphemeb. phonemec. syllable3.W ords like pronouns, prepositions, conjunctions, articles are items.a. open-classb. closed-classc. neither open-class nor closed-class4.C ompound words consist of __________ morphemes.a. boundb. freec. both bound and free5.W hen language is used to get information from others, it serves an function./doc/628515796.html,rmativeb. directivec. InterrogativeIII. Give the phonetic term for each of the following locations in articulation. (4 points)1.Both lips2. Teeth3. Opening between vocal cords4. Ridge behind upper teethIV. Tell if each of the following statements is true or false. Ifyou think it false, correct it.(6 points)1.All syllables contain three parts: onset, nucleus and coda.2.Broad Transcription is intended to symbolize all the possible speech sounds, including the minute shades.3.The most important sociological use cf language is the performative function, by which people establish and maintain their status in society.2003 年硕士研究生入学考试试卷考试科目:综合考试(英美概况)满分:30分Instruction:You are required to answer all questions of this section on the pa per. In part II and partIII, answers should be given in English. The total time for this section is about 45 minutes.I . Choose the correct answer from the following four choices: (10分)4.In England, the Protestant Reformation began withA. Bloody MaryB. Queen ElizabethC. King Henry VIID. King Henry VIII5.Victorianism was characterized by the following exceptA.It was in an age of imperialism.B.It saw the great progress in social sciences.C.It was the age when the great progress was made in the field of communication.D.It was an age when the Battle of Waterloo was won by the Duke of Wellington.6.The Supreme Court of U.S.A. is composed ofA. six JudgesB. seven JudgesC. eight JudgesD. nine Judges7.The pilgrims were able to survive in America becauseA.they received help from the Indians.B.they were supported by rich companiesC.many ships brought them food from England.D.they had signed the Mayflower Compact8.Which of the following did not take place in the 1960s?A.The Anti-Viet Nam War MovementB.The Anti-Drug MovementC.Women's Liberation MovementD.Public protests by blacks and other minority groups.II .Explain the following in English. (20 分)1.the pioneer spirit2.the American Dream3.John Locke4.the separation of powers5.The Boston Tea PartyII. Answer the following question. (10分)Describe the divesity of the physical conditions of the U.S.A.2003 年硕士研究生入学考试试卷考试科目:综合考试(翻译)满分:40分6.英译汉(20分)说明:下为In Praise of the Humble Comma一文的节选。
《情报和智商测试》课件

▪ Yields excellent prediction to achievement
▪ Provides sensitivity to the cognitive disorders seen in many exceptional children
• A look at the Law
▪ Response to intervention
• Local comparison groups • Measurement of improvement • Research and reviews
▪ A cognitive approach to assessment
• Connecting LD definition with assessment of “basic psychological processes”
h
3
IDEIA 2004 Law
Individuals with Disabilities Education Improvement Act of 2004
➢ Definition of SLD remains
h
11
IDEIA 2004 Law
Definition of SLD remains the same
h
12
SLD Definition in Both Bills
➢ The definition of SLD has not changed
h
5
IDEA Reauthorization
➢ Reexamination of
2003考研英语真题(英一二通用)答案+解析
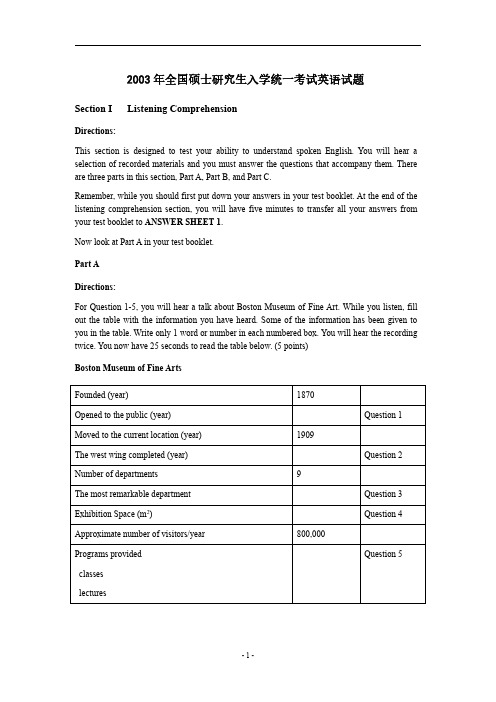
2003年全国硕士研究生入学统一考试英语试题Section I Listening ComprehensionDirections:This section is designed to test your ability to understand spoken English.You will hear a selection of recorded materials and you must answer the questions that accompany them.There are three parts in this section,Part A,Part B,and Part C.Remember,while you should first put down your answers in your test booklet.At the end of the listening comprehension section,you will have five minutes to transfer all your answers from your test booklet to ANSWER SHEET1.Now look at Part A in your test booklet.Part ADirections:For Question1-5,you will hear a talk about Boston Museum of Fine Art.While you listen,fill out the table with the information you have heard.Some of the information has been given to you in the table.Write only1word or number in each numbered box.You will hear the recording twice.You now have25seconds to read the table below.(5points)Boston Museum of Fine ArtsFounded(year)1870Opened to the public(year)Question1Moved to the current location(year)1909The west wing completed(year)Question2Number of departments9The most remarkable department Question3Exhibition Space(m2)Question4Approximate number of visitors/year800,000Programs providedQuestion5classeslecturesPart BDirections:For Questions6-10,you will hear an interview with an expert on marriage problems.While you listen,complete the sentences or answer the e not more than3words for each answer.You will hear the recording twice.You now have25seconds to read the sentences and questions below.(5points)What should be the primary source of help for a troubled couple?________.Question6Writing down a list of problems in the marriage may help a troubled couple discuss them ________.Question7Who should a couple consider seriously turning to if they can’t talk with each other? ________.Question8Priests are usually unsuccessful in counseling troubled couples despite their________. Question9According to the old notion,what will make hearts grow fonder?________.Question10 Part CDirections:You will hear three pieces of recorded material.Before listening to each one,you will have time to read the questions related to it.While listening,answer each question by choosing[A],[B],[C] or[D].After listening,you will have time to check your answers you will hear each piece once only.(10points)Questions11-13are based on the following talk about napping,you now have15seconds to read questions11-13.11.Children under five have abundant energy partly because they________.[A]sleep in three distinct parts[B]have many five-minute naps[C]sleep in one long block[D]take one or two naps daily12.According to the speaker,the sleep pattern of a baby is determined by________.[A]its genes[B]its habit[C]its mental state[D]its physical condition13.The talk suggests that,if you feel sleepy through the day,you should________.[A]take some refreshment[B]go to bed early[C]have a long rest[D]give in to sleepQuestions14-16are based on the following interview with Sherman Alexie,an American Indian poet.You now have15seconds to read Questions14-16.14.Why did Sherman Alexie only take day jobs?[A]He could bring unfinished work home.[B]He might have time to pursue his interests.[C]He might do some evening teaching.[D]He could invest more emotion in his family.15.What was his original goal at college?[A]to teach in high school[B]to write his own books[C]to be a medical doctor[D]to be a mathematician16.Why did he take the poetry-writing class?[A]To follow his father.[B]For an easy grade.[C]To change his specialty.[D]For knowledge of poetry.Questions17-20are based on the following talk about public speaking.You now have20 seconds to read Questions17-20.17.What is the most important thing in public speaking?[A]Confidence.[B]Preparation.[C]Informativeness.[D]Organization.18.What does the speaker advise us to do to capture the audience’s attention?[A]Gather abundant data.[B]Organize the idea logically.[C]Develop a great opening.[D]Select appropriate materials.19.If you don’t start working for the presentation until the day before,you will feel________.[A]uneasy[B]uncertain[C]frustrated[D]depressed20.Who is this speech most probably meant for?[A]Those interested in the power of persuasion.[B]Those trying to improve their public images.[C]Those planning to take up some public work.[D]Those eager to become effective speakers.You now have5minutes to transfer all your answers from your test booklet to ANSWER SHEET1.Section II Use of EnglishDirections:Read the following text.Choose the best word(s)for each numbered blank and mark[A],[B], [C]or[D]on ANSWER SHEET1.(10points)Teachers need to be aware of the emotional,intellectual,and physical changes that young adults experience.And they also need to give serious大21家to how they can best 大22家such changes.Growing bodies need movement and大23家,but not just in waysthat emphasize competition.大24家they are adjusting to their new bodies and a whole host of new intellectual and emotional challenges,teenagers are especially self-conscious and needthe大25家that comes from achieving success and knowing that their accomplishments are大26家by others.However,the typical teenage lifestyle is already filled with so much competition that it would be大27家to plan activities in which there are more winners thanlosers,大28家,publishing newsletters with many student-written book reviews,大29家student artwork,and sponsoring book discussion clubs.A variety of small clubs can provide 大30家opportunities for leadership,as well as for practice in successful大31家dynamics.Making friends is extremely important to teenagers,and many shy students need the 大32家of some kind of organization with a supportive adult大33家visible in the background.In these activities,it is important to remember that the young teens have大34家attention spans.A variety of activities should be organized大35家participants can remain active as long as they want and then go on to大36家else without feeling guilty and without letting the other participants大37家.This does not mean that adults must accept irresponsibility.大38家,they can help students acquire a sense of commitment by大39家for roles that are within their大40家and their attention spans and by having clearly stated rules.21.[A]thought[B]idea[C]opinion[D]advice22.[A]strengthen[B]accommodate[C]stimulate[D]enhance23.[A]care[B]nutrition[C]exercise[D]leisure24.[A]If[B]Although[C]Whereas[D]Because25.[A]assistance[B]guidance[C]confidence26.[A]claimed[B]admired[C]ignored[D]surpassed27.[A]improper[B]risky[C]fair[D]wise28.[A]in effect[B]as a result[C]for example[D]in a sense29.[A]displaying[B]describing[C]creating[D]exchanging30.[A]durable[B]excessive[C]surplus[D]multiple31.[A]group[B]individual[C]personnel[D]corporation32.[A]consent[B]insurance[C]admission[D]security33.[A]particularly[B]barely[D]rarely34.[A]similar[B]long[C]different[D]short35.[A]if only[B]now that[C]so that[D]even if36.[A]everything[B]anything[C]nothing[D]something37.[A]off[B]down[C]out[D]alone38.[A]On the contrary[B]On the average[C]On the whole[D]On the other hand39.[A]making[B]standing[C]planning[D]taking40.[A]capabilities[B]responsibilities[C]proficiency[D]efficiencySection III Reading ComprehensionPart ADirections:Read the following four texts.Answer the questions below each text by choosing[A],[B],[C]or [D].Mark your answers on ANSWER SHEET1(40points)Text1Wild Bill Donovan would have loved the Internet.The American spymaster who built the Office of Strategic Services in the World War II and later laid the roots for the CIA was fascinated with information.Donovan believed in using whatever tools came to hand in the “great game”of espionage--spying as a“profession.”These days the Net,which has already re-made such everyday pastimes as buying books and sending mail,is reshaping Donovan’s vocation as well.The latest revolution isn’t simply a matter of gentlemen reading other gentlemen’s e-mail. That kind of electronic spying has been going on for decades.In the past three or four years,the World Wide Web has given birth to a whole industry of point-and-click spying.The spooks call it “open-source intelligence,”and as the Net grows,it is becoming increasingly influential.In1995 the CIA held a contest to see who could compile the most data about Burundi.The winner,by a large margin,was a tiny Virginia company called Open Source Solutions,whose clear advantage was its mastery of the electronic world.Among the firms making the biggest splash in this new world is Straitford,Inc.,a private intelligence-analysis firm based in Austin,Texas.Straitford makes money by selling the results of spying(covering nations from Chile to Russia)to corporations like energy-services firm McDermott International.Many of its predictions are available online at .Straitford president George Friedman says he sees the online world as a kind of mutually reinforcing tool for both information collection and distribution,a spymaster’s st week his firm was busy vacuuming up data bits from the far corners of the world and predicting a crisis in Ukraine.“As soon as that report runs,we’ll suddenly get500new Internet sign-ups from Ukraine,”says Friedman,a former political science professor.“And we’ll hear back from some of them.”Open-source spying does have its risks,of course,since it can be difficult to tell good information from bad.That’s where Straitford earns its keep.Friedman relies on a lean staff of20in Austin.Several of his staff members have military-intelligence backgrounds.He sees the firm’s outsider status as the key to its success. Straitford’s briefs don’t sound like the usual Washington back-and-forthing,whereby agencies avoid dramatic declarations on the chance they might be wrong.Straitford,says Friedman,takes pride in its independent voice.41.The emergence of the Net has________.[A]received support from fans like Donovan[B]remolded the intelligence services[C]restored many common pastimes[D]revived spying as a profession42.Donovan’s story is mentioned in the text to________.[A]introduce the topic of online spying[B]show how he fought for the U.S.[C]give an episode of the information war[D]honor his unique services to the CIA43.The phrase“making the biggest splash”(Line1,Paragraph3)most probably means________.[A]causing the biggest trouble[B]exerting the greatest effort[C]achieving the greatest success[D]enjoying the widest popularity44.It can be learned from Paragraph4that________.[A]Straitford’s prediction about Ukraine has proved true[B]Straitford guarantees the truthfulness of its information[C]Straitford’s business is characterized by unpredictability[D]Straitford is able to provide fairly reliable information45.Straitford is most proud of its________.[A]official status[B]nonconformist image[C]efficient staff[D]military backgroundText2To paraphrase18th-century statesman Edmund Burke,“all that is needed for the triumph of a misguided cause is that good people do nothing.”One such cause now seeks to end biomedical research because of the theory that animals have rights ruling out their use in research.Scientists need to respond forcefully to animal rights advocates,whose arguments are confusing the public and thereby threatening advances in health knowledge and care.Leaders of the animal rights movement target biomedical research because it depends on public funding,and few people understand the process of health care research.Hearing allegations of cruelty to animals in research settings,many are perplexed that anyone would deliberately harm an animal.For example,a grandmotherly woman staffing an animal rights booth at a recent street fair was distributing a brochure that encouraged readers not to use anything that comes from or is tested in animals—no meat,no fur,no medicines.Asked if she opposed immunizations,she wanted to know if vaccines come from animal research.When assured that they do,she replied,“Then I would have to say yes.”Asked what will happen when epidemics return,she said,“Don’t worry,scientists will find some way of using computers.”Such well-meaning people just don’t understand.Scientists must communicate their message to the public in a compassionate, understandable way--in human terms,not in the language of molecular biology.We need to make clear the connection between animal research and a grandmother’s hip replacement,a father’s bypass operation,a baby’s vaccinations,and even a pet’s shots.To those who are unaware that animal research was needed to produce these treatments,as well as new treatments and vaccines,animal research seems wasteful at best and cruel at worst.Much can be done.Scientists could“adopt”middle school classes and present their own research.They should be quick to respond to letters to the editor,lest animal rights misinformation go unchallenged and acquire a deceptive appearance of truth.Research institutions could be opened to tours,to show that laboratory animals receive humane care. Finally,because the ultimate stakeholders are patients,the health research community should actively recruit to its cause not only well-known personalities such as Stephen Cooper,who has made courageous statements about the value of animal research,but all who receive medical treatment.If good people do nothing,there is a real possibility that an uninformed citizenry will extinguish the precious embers of medical progress.46.The author begins his article with Edmund Burke’s words to________.[A]call on scientists to take some actions[B]criticize the misguided cause of animal rights[C]warn of the doom of biomedical research[D]show the triumph of the animal rights movement47.Misled people tend to think that using an animal in research is________.[A]cruel but natural[B]inhuman and unacceptable[C]inevitable but vicious[D]pointless and wasteful48.The example of the grandmotherly woman is used to show the public’s________.[A]discontent with animal research[B]ignorance about medical science[C]indifference to epidemics[D]anxiety about animal rights49.The author believes that,in face of the challenge from animal rights advocates,scientistsshould________.[A]communicate more with the public[B]employ hi-tech means in research[C]feel no shame for their cause[D]strive to develop new cures50.From the text we learn that Stephen Cooper is________.[A]a well-known humanist[B]a medical practitioner[C]an enthusiast in animal rights[D]a supporter of animal researchText3In recent years,railroads have been combining with each other,merging into supersystems, causing heightened concerns about monopoly.As recently as1995,the top four railroads accounted for under70percent of the total ton-miles moved by rails.Next year,after a series of mergers is completed,just four railroads will control well over90percent of all the freight moved by major rail carriers.Supporters of the new supersystems argue that these mergers will allow for substantial cost reductions and better coordinated service.Any threat of monopoly,they argue,is removed by fierce competition from trucks.But many shippers complain that for heavy bulk commodities traveling long distances,such as coal,chemicals,and grain,trucking is too costly and the railroads therefore have them by the throat.The vast consolidation within the rail industry means that most shippers are served by only one rail company.Railroads typically charge such“captive”shippers20to30percent more than they do when another railroad is competing for the business.Shippers who feel they are being overcharged have the right to appeal to the federal government’s Surface Transportation Board for rate relief,but the process is expensive,time-consuming,and will work only in truly extreme cases.Railroads justify rate discrimination against captive shippers on the grounds that in the long run it reduces everyone’s cost.If railroads charged all customers the same average rate,they argue,shippers who have the option of switching to trucks or other forms of transportation would do so,leaving remaining customers to shoulder the cost of keeping up the line.It’s a theory to which many economists subscribe,but in practice it often leaves railroads in the position of determining which companies will flourish and which will fail.“Do we really want railroads to be the arbiters of who wins and who loses in the marketplace?”asks Martin Bercovici,a Washington lawyer who frequently represents shippers.Many captive shippers also worry they will soon be hit with a round of huge rate increases. The railroad industry as a whole,despite its brightening fortunes,still does not earn enough to cover the cost of the capital it must invest to keep up with its surging traffic.Yet railroads continue to borrow billions to acquire one another,with Wall Street cheering them on.Consider the$10.2billion bid by Norfolk Southern and CSX to acquire Conrail this year.Conrail’s netrailway operating income in1996was just$427million,less than half of the carrying costs of the transaction.Who’s going to pay for the rest of the bill?Many captive shippers fear that they will,as Norfolk Southern and CSX increase their grip on the market.51.According to those who support mergers,railway monopoly is unlikely because________.[A]cost reduction is based on competition[B]services call for cross-trade coordination[C]outside competitors will continue to exist[D]shippers will have the railway by the throat52.What is many captive shippers’attitude towards the consolidation in the rail industry?[A]Indifferent.[B]Supportive.[C]Indignant.[D]Apprehensive.53.It can be inferred from Paragraph3that________.[A]shippers will be charged less without a rival railroad[B]there will soon be only one railroad company nationwide[C]overcharged shippers are unlikely to appeal for rate relief[D]a government board ensures fair play in railway business54.The word“arbiters”(Line7,Paragraph4)most probably refers to those________.[A]who work as coordinators[B]who function as judges[C]who supervise transactions[D]who determine the price55.According to the text,the cost increase in the rail industry is mainly caused by________.[A]the continuing acquisition[B]the growing traffic[C]the cheering Wall Street[D]the shrinking marketText4It is said that in England death is pressing,in Canada inevitable and in California optional. Small wonder.Americans’life expectancy has nearly doubled over the past century.Failing hips can be replaced,clinical depression controlled,cataracts removed in a30-minute surgical procedure.Such advances offer the aging population a quality of life that was unimaginablewhen I entered medicine50years ago.But not even a great health-care system can cure death--and our failure to confront that reality now threatens this greatness of ours.Death is normal;we are genetically programmed to disintegrate and perish,even under ideal conditions.We all understand that at some level,yet as medical consumers we treat death as a problem to be solved.Shielded by third-party payers from the cost of our care,we demand everything that can possibly be done for us,even if it’s useless.The most obvious example is late-stage cancer care.Physicians--frustrated by their inability to cure the disease and fearing loss of hope in the patient--too often offer aggressive treatment far beyond what is scientifically justified.In1950,the U.S.spent$12.7billion on health care.In2002,the cost will be$1,540billion. Anyone can see this trend is unsustainable.Yet few seem willing to try to reverse it.Some scholars conclude that a government with finite resources should simply stop paying for medical care that sustains life beyond a certain age--say83or so.Former Colorado governor Richard Lamm has been quoted as saying that the old and infirm“have a duty to die and get out of the way,”so that younger,healthier people can realize their potential.I would not go that far.Energetic people now routinely work through their60s and beyond, and remain dazzlingly productive.At78,Viacom chairman Sumner Redstone jokingly claims to be53.Supreme Court Justice Sandra Day O’Connor is in her70s,and former surgeon general C. Everett Koop chairs an Internet start-up in his80s.These leaders are living proof that prevention works and that we can manage the health problems that come naturally with age.As a mere 68-year-old,I wish to age as productively as they have.Yet there are limits to what a society can spend in this pursuit.As a physician,I know the most costly and dramatic measures may be ineffective and painful.I also know that people in Japan and Sweden,countries that spend far less on medical care,have achieved longer,healthier lives than we have.As a nation,we may be overfunding the quest for unlikely cures while underfunding research on humbler therapies that could improve people’s lives.56.What is implied in the first sentence?[A]Americans are better prepared for death than other people.[B]Americans enjoy a higher life quality than ever before.[C]Americans are over-confident of their medical technology.[D]Americans take a vain pride in their long life expectancy.57.The author uses the example of cancer patients to show that________.[A]medical resources are often wasted[B]doctors are helpless against fatal diseases[C]some treatments are too aggressive[D]medical costs are becoming unaffordable58.The author’s attitude toward Richard Lamm’s remark is one of________.[A]strong disapproval[B]reserved consent[C]slight contempt[D]enthusiastic support59.In contrast to the U.S.,Japan and Sweden are funding their medical care________.[A]more flexibly[B]more extravagantly[C]more cautiously[D]more reasonably60.The text intends to express the idea that________.[A]medicine will further prolong people’s lives[B]life beyond a certain limit is not worth living[C]death should be accepted as a fact of life[D]excessive demands increase the cost of health carePart BDirections:Read the following text carefully and then translate the underlined segments into Chinese.Your translation should be written clearly on ANSWER SHEET2.(10points)Human beings in all times and places think about their world and wonder at their place in it. Humans are thoughtful and creative,possessed of insatiable curiosity.61)Furthermore,humans have the ability to modify the environment in which they live,thus subjecting all other life forms to their own peculiar ideas and fancies.Therefore,it is important to study humans in all their richness and diversity in a calm and systematic manner,with the hope that the knowledge resulting from such studies can lead humans to a more harmonious way of living with themselves and with all other life forms on this planet Earth.“Anthropology”derives from the Greek words anthropos:“human”and logos“the study of.”By its very name,anthropology encompasses the study of all humankind.Anthropology is one of the social sciences.62)Social science is that branch of intellectual enquiry which seeks to study humans and their endeavors in the same reasoned,orderly, systematic,and dispassioned manner that natural scientists use for the study of natural phenomena.Social science disciplines include geography,economics,political science,psychology,and sociology.Each of these social sciences has a subfield or specialization which lies particularly close to anthropology.All the social sciences focus upon the study of humanity.Anthropology is a field-study oriented discipline which makes extensive use of the comparative method in analysis.63)The emphasis on data gathered first-hand,combined with a cross-cultural perspective brought to theanalysis of cultures past and present,makes this study a unique and distinctly important social science.Anthropological analyses rest heavily upon the concept of culture.Sir Edward Tylor’s formulation of the concept of culture was one of the great intellectual achievements of19th century science.64)Tylor defined culture as“…that complex whole which includes belief,art, morals,law,custom,and any other capabilities and habits acquired by man as a member of society.”This insight,so profound in its simplicity,opened up an entirely new way of perceiving and understanding human life.Implicit within Tylor’s definition is the concept that culture is learned,shared,and patterned behavior.65)Thus,the anthropological concept of“culture,”like the concept of“set”in mathematics, is an abstract concept which makes possible immense amounts of concrete research and understanding.Section IV Writing66.Directions:Study the following set of drawings carefully and write an essay in which you should1)describe the set of drawings,interpret its meaning,and2)point out its implications in our life.You should write about200words neatly on ANSWER SHEET2.(20points)2003年考研英语真题答案解析Section I:Listening Comprehension(20points)Part A(5points)1.18762.19813.textiles4.19,1375.concerts Part B(5points)6.(the couple)themselves7.constructively8.a qualified psychologist9.good intentions10.absencePart C(10points)11.[D]12.[A]13.[D]14.[B]15.[C]16.[B]17.[B]18.[C]19.[A]20.[D]Section II:Use of English(10points)一、文章总体分析文章主要论述了教师们应该关注青少年在成长时期所经历的情感、心智和生理上的变化,并采取方法帮助他们适应这些变化,健康成长。
ISO 13485 2003 英文版标准

ii
© ISO 2003 — All rights reserved
ISO 13485:2003(E)
ContentsPaFra bibliotekeForeword ............................................................................................................................................................ iv 0 0.1 0.2 0.3 0.4 1 1.1 1.2 2 3 4 4.1 4.2 5 5.1 5.2 5.3 5.4 5.5 5.6 6 6.1 6.2 6.3 6.4 7 7.1 7.2 7.3 7.4 7.5 7.6 8 8.1 8.2 8.3 8.4 8.5 Introduction ........................................................................................................................................... v General ................................................................................................................................................... v Process approach .....................................................................................
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
A Simple and Scalable Approach for Human-System InteractionAshley D. Tews, Gaurav S. Sukhatme, Maja J. MatarićUSC Robotics Research Lab, Center for Robotics and Embedded Systems,Computer Science Department, University of Southern CaliforniaLos Angeles, USA{atews|gaurav|mataric}@Abstract— While there is much research concerning one-to-one human and physical system interaction, there is little on the larger scale of many-to-many. We propose an interaction infrastructure for many human operators to utilize a large number of robots and systems. The primary criterion for scalable interaction is to reduce the communication required for interaction while providing a simple but functional interface. To achieve this, we assume that each system and robot has some degree of autonomy allowing the humans to have a supervisory role in the interaction. Our approach is analyzed in detail on a large-scale experiment involving several systems offering many tasks and services to many users. The scalability criteria are analyzed in the context of this experiment and demonstrate the infrastructure to be a valid interaction mechanism for many systems and many users.1IntroductionThe interaction between a physical system and a human can occur at many levels. There is much research on one-to-one (e.g., single robot and single human) interaction but these approaches would not be applicable for a larger number of interactions. This is mainly due to the large and dedicated communication paths required for interaction between entities, especially if they require tightly coupled interaction.In this paper, we investigate many-to-many interaction: what is required to facilitate it. We intend our method to scale to the order of hundreds of systems and users, where a system is defined as a robot or embedded device. It is anticipated that multitudes of these types of systems will soon be used to achieve goals beyond their current small-scale applications. These goals may be building large structures on Earth, in space, or on other planets. They may also be human-coordinated de-mining or search and rescue efforts, where a few human supervisors can coordinate many robots. It is assumed that many of these applications would use systems that have some degree of autonomy, such that they are supervised by humans rather than operated by them.In its simplest form, human-system interaction consists of the human, the system, and the interaction mechanism. The system and human interact through a communication medium, whether it has an explicit form such as spoken language or message passing, or implicit such as a robot observing a human's deliberate actions. To extend the numbers of entities (humans and systems) capable of interacting, the communication bandwidth required between them must be kept low. Additionally, the interaction mechanism should be efficient and allow for inter-system collaboration to occur if possible. These requirements are the inspiration for the design of our interaction infrastructure.First, the infrastructure requires a low communication bandwidth between itself, users and systems. The assumption that the systems are relatively autonomous contributes to this. Second, the infrastructure is efficient in the sense that the latencies in processing user requests are small. Third, it provides functionality beyond connecting users to systems by providing task queues for systems and allowing services to be combined.To determine how the infrastructure conforms to these requirements, two experiments are presented in this paper. The first demonstrates the task queuing ability with many users accessing a service offered by a single system. The second is a larger scale experiment involving five robotic and embedded systems and hundreds of users. The experiments allow the efficiency and communications aspects of the infrastructure’s operation to be examined.2Related WorkIn [1], a taxonomy is presented categorizing human and intelligent system interaction. It defines an intelligent system as a system that allows user interaction (e.g., tele-robotics[2]). The categories in the taxonomy include the application of the research, researchSubmitted to IROS 2003approach, system autonomy, interaction distance, and interaction media, with each category divided into subcategories. Numerous references are grouped under these categories, illustrating the vastness of the field. A key axis omitted from this classification is the scalability of the interaction methods.In this section of the paper, we classify human-system architectures in terms of their scalability, assuming a system consists of a set of nodes that provide a set of services to users. These classifications are shown in Table 1 and are discussed in the following sections, separating them into single (non-shaded table entries) and multi-user architectures (shaded table entries).TABLE 1U SER/SYSTEM SCALABILITY CLASSIFICATIONUsers Systems1One One2One Multiple3Multiple One4Multiple MultipleSingle-user System ArchitecturesThere are many examples relating to the entries in the table above. The issues concerning scalability are highlighted when examining them. An important issue that affects the scalability of an approach is how tightly coupled the users are with the systems. This concerns both access to system resources and levels of control over system services. A system that allows interaction with only a single user can allow the user full access to system resources and control of its services. To scale this to more users can be difficult due to the service attributes (such as communication bandwidth) having to be shared. Tele-operation of a single system node is an example where this is highlighted [2][3].Multi-robot research also provides single system examples where multiple robots can be controlled individually or as a group by a single user [4][5][6][7]. In each of these systems, the nodes have a certain degree of autonomy and the user has either high-level group control, or low-level individual control. This indicates that the higher the number of users an interaction architecture has to deal with, the looser the coupling between users and systems.The concept of a single user for multiple systems indicates a hierarchical command structure where there is a top-level entity that controls the systems below its level.Multi-user System ArchitecturesMulti-user systems are forced to address issues of scalability, system resource allocation, and control. A key concern is how to control the information and communication pathways for multiple users. Common approaches involve using multi-agent architectures [8][9][10][11] and the Internet.In the context of human-system interaction, multi-agent architectures typically offer services to users with suitable access to the systems they serve. Examples include interactive workspaces [12][13] which consist of dedicated environments with embedded devices providing services for users. The users generally must be in the environment to access the services.JINI [14] is an example of a multiagent architecture that allows systems’ services to be offered to users. There is little restriction on what constitutes a user or a system since a user can offer services as a system would and a system can be a user of services. Each component connected to a JINI architecture is required to run the Java Virtual Machine.Multi-user/multi-robot architectures are demonstrated by [15][16]. These systems use the Internet as a communication medium for commanding robots from remote locations.Many of the examples presented in this section are scalable only in their local operating environment or application domain. Furthermore, they generally have high overhead for implementation and communication. The infrastructure we present in the next section is intended to operate beyond these limits by providing a simple and efficient interaction mechanism.3The InfrastructureFigure 1. A simplified view of the infrastructure for connecting multiple users to multiple system services. Many-to-many interaction is shown as broken lines and potential one-to-one as solid.The infrastructure is based on a server/client architecture as shown in Figure 1. Each system is typically a robot, robot group, or embedded system (e.g., a security camera network) that offers its capabilities as services for the users. Each entity (system or user) has a client that interfaces with the server and manages the low-level signal and message passing betweentheinfrastructure components. It is assumed that the server's contact information is known to all systems and users wishing to use the infrastructure. The server is the centralized hub of operations that manages the allocation of systems' services to users’ requests. The data flow throughout the infrastructure is by UDP communication. This is chosen over TCP primarily to reduce the communication overhead.Each system that connects to the infrastructure sends its service list to be added to the server’s database. The systems may optionally request task queues to be set up for them in the server to facilitate multiple user requests. Each user that connects to the infrastructure is presented with the global service list from the server’s database. The users select whichever services they require and are connected to the corresponding systems if they are not put on a queue. The appropriate level (coupling) of interaction is then established between the user and the selected service, and is system- and service-dependent. The communication between the user and the service is decoupled from the server to maximize bandwidth for interaction and not burden the server from carrying out its higher level operations. However, the bandwidth may be reduced if the user is currently interacting with multiple services. The interaction between a user and a service continues until either terminates it or the service completes. In the latter case, the user and server are notified so the service is ready for another request. A more detailed description of the infrastructure’s operation is provided in [17].4ExperimentsOur experiments were carried out in the Stage simulator using Player devices [18]. Stage has been demonstrated on dozens of projects to provide a valid representation of real robot operations. Player provides a suite of software clients that represent the handlers for the devices on the robots, such as sonar, SICK laser range-finders, and Sony PTZ color cameras. The combination of Player and Stage allows programs developed and tested in Stage to transfer to the real robots.Our first experiment consists of several users requesting a service from a single system. It allows an analysis of the efficiency of the infrastructure while demonstrating the benefit of using task queuing. The second experiment involves more users and systems, to demonstrate the infrastructure’s operation in a higher scale, more realistic application.4.1Experiment 1This experiment shows the operation of the infrastructure using a single system, 25 users, and task queuing. The system provides a random-wander service represented by a robot that randomly wanders about the environment and provides information about its current location. The task lasts for 20 seconds, then terminates and becomes available for the next request. The system, users, and server are run on separate machines.The parameters for the experiment are shown in Table 2. An automated user is generated upon system start-up and every 15 seconds thereafter, until 25 have been generated. Once a user is on line, they immediately select the service if it is available. If it is not, they do not make another attempt. The number of tasks that can be completed ranges from 12 to 25, depending on the size of the task queue. With no task queue, the maximum number of requests that can be fulfilled is determined by the user generation rate versus the task running time. This equates to every other user’s task being fulfilled which is 12 or 13 depending on the efficiency of the infrastructure. When task queues are used, the minimum size of the queue required to manage all requests for this experiment is derived from the difference between task request rate (0.067/s) and task completion rate (0.05/s) for the length of time that tasks are generated (360s). This determines a theoretical queue size of 6.12, which can manage all requests assuming negligible latencies in the infrastructure and system.T ABLE 2P ARAMETERS FOR EXPERIMENT 2Number of users generated25User generation frequency15 secondsExperiment running time500 secondsTask running time20 secondsMinimum achievable requests12 or 13Maximum achievable requests25Queue size0, 3, 5, or 7For the buffered approaches, the server’s response time to a user’s request is generally between 60 and 80ms, regardless of the buffer size. The approach with no buffering is indifferent to whether the user’s requests are fulfilled or denied and the response times are between 50 and 60ms. The statistics for task fulfillment are shown in Table 3.T ABLE 3U SERS’ REQUESTS FULFILLEDBuffer Size Requests Fulfilled013 (52%)321 (84%)523 (92%)725 (100%)These results demonstrate that a buffer size of seven allows all users’ requests to be fulfilled within theconstraints of the experiment parameters. It also demonstrates that the time for the server to manage these requests is negligible, since the theoretical maximum number of requests that could be fulfilled within the time limit was achieved. This would not be possible if the server was inefficient with processing the queued requests.The times taken for the system to respond to requests are shown in Figure 2. These times are measured from when the user submitted a request to when they were notified their request was being processed by the system.Unsuccessful attempts are recorded as a response time of 0 to identify the corresponding requests.Figure 2. User client service request response times (solid lines corresponding to the left y axis) compared to the number of requests in the queue (broken lines corresponding to the right y axis).For the system with no task queuing (not shown in Figure 2), the response times consistently averaged 75ms.For the buffered approaches, the response times varied depending on the size of the task queue. In all buffered approaches, the first 10 users had their requests fulfilled.Once each buffer is full, the next generated request is denied. Since the task length is 20 seconds and the first user in the queue is currently connected to the task, each approach has a maximum theoretical response time for the requests of:(buffer_size – 1) x task_length (1)This gives 40, 80 and 120 seconds for the three, five and seven-buffer approaches, respectively. These upper limits are apparent in the graph.4.2 Experiment 2This experiment presents an indication of the scalability aspects of the infrastructure, using five systems located in simulated office space and hundreds of users over four hours of operation. Each system consists of robots or embedded devices and provides varying numbers and types of service. The services are classified as discrete or continuous. Discrete services provide onlythe immediate status of a sensor while continuous services provide streaming updates of their task status.Each system is briefly described next.1) Murdoch – continuous servicesA task-allocation system, Murdoch [19][20] is a form of a Contract Net Protocol [21] used to control three robots in this experiment. Each robot is capable of carrying out three tasks: random walk, target tracking,and delivery. Random walking requires a robot to wander randomly and provides location information to the user.For target tracking, the robot acquires and follows a colored mobile object. The object’s position is provided to the user. The delivery service requires the user to input the destination coordinates for the robot to navigate to.Once a robot is tasked, it does not carry out another task until the current one is terminated. The Murdoch-controlled robots each have a task buffer set up for them on the server.2) Tracking – continuous servicesEight robots are positioned to provide almost complete coverage of the corridors using a tracking system from [22]. Each is equipped with a color camera and reports the global positions of simulated humans. This system provides three services concurrently and the system client is configured to manage up to ten simultaneous requests.3) Room Cleaning/Trashing – continuous servicesThis system involves a robot carrying out room cleaning and object scattering tasks. The cleaning task is similar to vacuuming or trash-collecting where a robot moves objects to a certain area in a room. Trashing involves dispersing these objects. The users can request either of these services and the system manages one request at a time.4 & 5) Room Lights and Room Occupied - discrete servicesThirty-three rooms in the simulated building have sensors that determine whether the room is occupied and the status of its lights. A room is considered occupied if it contains a simulated person. For the Room Lights system, the lights are automated to switch on and off at random times.4.2.1 SetupStage is used to simulate the robots and the environment which is the second floor of the USC Computer Science building (Figure 3). This presents a realistic office space environment with corridors and rooms for the robots to carry out their tasks, and allows the systems’ parameter settings to be used for testing in the real world [17]. Apart from the service robots, there are also three simulated humans (implemented as robots)1113151719212325ClientR e s p o n s e T i m e (m s )N u m b e r o f Q u e u e d T a s k sthat wander randomly through rooms and corridors. Each “human” has a differently colored marker for identification.Figure 3. The simulated environment showing robots in their initial positions.The statistics for the experiment configuration are shown in Table 4. In the table, a ‘node’ is defined as either a robot or embedded device. There are 80 services in total. Note that the tracking system has eight nodes capable of three services each, but the system only provides three services in total. This is due to each robot operating in parallel with its peers, so they form a global, rather than a local sensor network.T ABLE 4E XPERIMENT ENTITIES AND SERVICESSystem No. ofNodes Servicesper nodeTotalSystemServicesTotalUsersperSystemMurdoch339 3 (+6) Tracking83310 Cleanup1221RoomLights33133N/aRoomOccupied33133N/a T OTAL7880In Table 4, the ‘Total Users per System’ column indicates how many users can utilize the system simultaneously. Each Murdoch system allocates one robot per request and allows two requests to be buffered in the task queue, hence the ‘+6’. The discrete services do not have a limit to the number of users they can manage since requests are handled with a single response. All systems except Cleanup remain connected to the server while managing requests.The users are real and simulated. The simulated users are generated randomly on several different computers and can make random service selections. The maximum number of services they can be interacting with is arbitrarily chosen to be two. The user clients, system clients and server connect to each other over a 10Mb/slocal area network and the experiment is conducted over four continuous hours of operation.4.2.2ResultsThe overall statistics of the experiment are shown in Table 5. Over 200 users per hour connected with a maximum of 32 being simultaneously on line. Not all users requested services and of those that did, approximately 80% of the requests were fulfilled. Requests were rejected for several reasons depending on the system:Murdoch - the request queues are full;Tracking- the maximum number of user requests is being managed;Cleanup - a request is made from an outdated service list. Other rejections occurred if a user selected a service and logged out before notification was received from the system that the request is being processed.T ABLE 5S TATISTICS FOR EXPERIMENT 2Total users985Maximum users on line32Total requested services916Total fulfilled services730Total requested service lists2022The high number of service list requests results from the users initially being sent the global list of services from the server upon connection. Users also generally refreshed their list prior to selecting a service to ensure they were not making selections from an outdated list. The system usage statistics are shown in Table 6. The continuous service systems were connected to the infrastructure for the longest period of time but had fewerrequests due to the large number of discrete services, and the more lengthy running times of the continuous services.T ABLE 6S YSTEM USAGE STATISTICSSystemNo. of Services Running Time (%)No.Requests Request Ratio (%)Murdoch 910015116.4Tracking 310014215.5Cleaner 277.924 2.6Room occ.3365.834737.9Room lights3353.325327.6The times for the systems to respond to user requests is shown in Figure 4. This is measured as the time the users had to wait before getting acknowledgement from the system that their request is being fulfilled. Generally, the times are low except for the Murdoch systems which had task queuing. Since there were no time limits imposed for service usage, a queued request took an arbitrary amount of time to be fulfilled.Figure 4. Example response times for users requesting services.Server StatisticsApart from the number of systems, services, and users the infrastructure managed during the experiment,another important analysis of scalability is the communication throughput for the infrastructure’s operations. Since the server is the centralized hub of operations, the following analysis is based on its communication with the clients.The most time-consuming and data intensive transaction for the server is processing requests for the global service list. Figure 5 shows the throughput of information for these requests during the experiment.The size of the requests are shown in gray (bytes received) with the service list size (bytes sent) in black.The steps in the service list size indicate when a new system was added to the server’s database and its services’ descriptions are added to the global list. Thesmall fluctuations indicate when services were unavailable. This occurred often for the Cleanup system.The other requests sent to the server are service requests and service termination messages. A service termination message can be sent from either the system or a user connected to the service. The user sends this message when finished with the service. The system sends this message to indicate the service is to be removed from the global service list. These messages are typically 100 bytes or less. The average time for the server to process both types of message is less than a millisecond with the maximum time less than 40ms.Figure 5. The number of bytes sent and received by the server in response to a service list request.Figure 6 illustrates how the rate of requests affects the server's response times for all messages it received. The maximum request rate was 11 per second. Upon analyzing the requests during the high burst time, most were found to be service list requests, which require the most bandwidth. As can be seen from the response times,the server’s efficiency was not affected by this rate. The size of the service list, however, did have an affect that is apparent by correlating the steps in response times in Figure 6 to the steps in ‘Bytes Sent’ in Figure 5.Figure 6. Number of responses/second versus response time for the server.02040608010012014055527263886548870378303939510912123051354014715Event Time (s)554238042066033785996851151113338Time (sec)N u m b e r o f B y t e s S e n t20000400006000080000100000120000140000Cleaning Murdoch Light Status Room Status Tracking5SummaryThe primary issues identified to allow large numbers of users to interact with large numbers of systems include reducing the amount of communication required for interaction, providing a highly efficient interaction mechanism as a substrate for potential interactions, and providing additional functionality for managing multiple systems and users. Our interaction infrastructure has addressed each of these issues. By assuming that the systems are relatively autonomous, much of the communication overhead is reduced since simple commands can be issued to task a system. Moreover, the communication required for the general operation of the infrastructure is minimal. This increases the infrastructure’s efficiency in managing requests. Finally, the extended functionality is provided by allowing task queuing and service linking.We have demonstrated each of these issues in the experiments presented here and in our previous work with real robots [17]. The next stage of evaluation is to determine the scalability limits of the infrastructure in terms of the number of systems it can manage simultaneously, the maximum frequency of requests, and message throughput. Further development on the infrastructure includes distributing the server to provide redundancy and increased scalability.Bibliography[1] A. Agah, "Human Interactions with Intelligent Systems: ResearchTaxonomy", Computers and Electrical Engineering, 2001, no. 27, pp. 71-107.[2]R. Murphy, and E. Rogers, "Cooperative Assistance for RemoteRobot Supervision", Presence, Special Issue, vol. 5, no. 2, pp. 224-240, 1996.[3]K. Kawamura, R. Peters, C. Johnson, P. Nilas, P. and S. Thongchai,"Supervisory Control of Mobile Robots Using Sensory Egosphere", IEEE Symposium on Computational Intelligence in Robotics and Automation, Jul. 29-Aug. 01, Banff, Canada, 2001.[4]K. Ali, and R. Arkin, "Integration of Reactive and TeleroboticControl in Multi-agent Robotics Systems", From Animals to Animats 3: SAB 1994, pp. 473-478.[5]R. Arkin, T. Collins, and Y. Endo, "Tactical Mobile Robot MissionSpecification and Execution", Mobile Robots XIV,Boston, MA, September, 1999, pp. 150-163.[6]H. Jones, and M. Snyder, M. "Supervisory Control of MultipleRobots Based on a Real-time Strategy Game Interaction Paradigm", Proceedings of the 2001 IEEE International Conference on Systems, Man, and Cybernetics, Tucson, AZ, October 2001, pp.383-388.[7]P. Rybski, I. Burt, T. Dahlin, M. Gini, D. Hougen, D. Krantz, F.Nageotte, N. Papanikolopoulos, and S. Stoeter, "System Architecture for Versatile Autonomous and Teleoperated Control of Multiple Miniature Robots", Proceedings of the 2001 IEEE International Conference on Robotics and Automation, Seoul, Korea, 2001. [8]T. Finin, R. Fritzson, D. McKay, and R. McEntire, "KQML as anAgent Communication Language", Proceedings of the Third International Conference on Information and Knowledge Management, ACM Press, 1994, pp. 456-463.[9]S. Goldsmith, S. Spires, and L. Phillips, "Object Frameworks forAgent System Development", Sandia National Laboratories, Tech.Rep. SAND98-0742A, 1998.[10]L. Phillips, S. Goldsmith, and S. Spires, "CHI: A General AgentCommunication Framework", Sandia National Laboratories, Tech.Rep. SAND98-2825C, 1998.[11]S. Ponnekanti, B. Lee, A. Fox, P. Hanrahan, and T. Winograd,"ICrafter: A Service Framework for Ubiquitous Computing Environments", Proceedings of the Ubiquitous Computing Conference. Lecture Notes in Computer Science", vol. 2201, 2001, pp. 56-75.[12] A. Fox, B. Johanson, P. Hanrahan, and T. Winograd, "IntegratingInformation Appliances into an Interactive Workspace", IEEE Computer Graphics and Applications, May/June, 2000, pp. 54-65.[13]J. Lee, and H. Hashimoto, "Intelligent Space - Its concept andcontents", Proceedings of the 2000 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Takamatsu, Japan, 2000, vol. 2. pp. 1358-1363.[14]Sun Microsystems. Jini Network Technology,[Online], Availablefrom: /software/jini [13 March 2003].[15]I. Elhajj, J. Tan, N. Xi, W. Fung, Y. Liu, T. Kaga, Y. Hasegawa, andT. Fukuda, "Multi-site Internet-based Cooperative Control of Robotic Operations", Proceedings of the 2000 IEEE/RSJ International Conference on Intelligent Robots and Systems, Takamatsu, Japan, 2000, pp.826-831.[16]H. Surmann, and M. Theißinger, "ROBODIS: A Dispatching Systemfor Multiple Autonomous Service Robots", Proceedings of the FSR'99 Robotics Applications for the Next Millenium, Pittsburgh, PA, 1999, pp. 168-173.[17] A. Tews, M. Matarić, and G. Sukhatme, “A Scalable Approach toHuman-Robot Interaction”, accepted, IEEE International Conference on Robotics and Automation, Taipei, Taiwan, 2003. [18] B. Gerkey, R. Vaughan, K. Støy, A. Howard, G. Sukhatme, and M.Matarić, "Most Valuable Player: A Robot Device Server for Distributed Control", Proceedings of the IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS 2001), Wailea, Hawaii, Oct. 29-Nov. 3, 2001, pp. 1226-1231.[19] B. Gerkey, and M. Matarić, "Principled Communication forDynamic Multi-Robot Task Allocation", Experimental Robotics VII, LCNIS 271, Springer-Verlag, 2001, pp. 353-362.[20] B. Gerkey, and M. Matarić, "Sold!: Auction Methods for Multi-Robot Coordination", in IEEE Transactions on Robotics and Automation Special Issue on Multi-robot Systems, vol. 18, no. 5, Tamio Arai, Enrico Pagello and Lynne Parker Eds., 2002, pp. 758-768.[21]R. Davis and R. Smith, “Negotiation as a Metaphor for DistributedProblem Solving, Artificial Intelligence, vol. 20, no. 1, 1983, pp. 63-109.[22] B. Jung, and G. Sukhatme, "A Region-based Approach forCooperative Multi-Target Tracking in a Structured Environment,"accepted, IEEE/RSJ International Conference on Intelligent Robots and Systems, Switzerland, Sep. 30-Oct. 04, 2002, pp. 2764-2769.。
