数据结构与算法分析 第9章 答案 Larry Nyhoff 清华大学出版社
数据结构(C语言版清华大学出版社)-章课后部分答案

第八章选择题1. C2.A3.B4.C5.D6.B7.B8.A9.D 10.D 11.C 12.C填空题1.n、n+12. 43.8.25( 折半查找所在块 )4.左子树、右子树5.266.顺序、(n+1)/2、O(log2n)7.m-1、[m/2]-18.直接定址应用题1.进行折半查找时,判定树是唯一的,折半查找过程是走了一条从根节点到末端节点的路径,所以其最大查找长度为判定树深度[log2n]+1.其平均查找长度约为[log2n+1]-1.在二叉排序树上查找时,其最大查找长度也是与二叉树的深度相关,但是含有n个节点的二叉排序树不是唯一的,当对n个元素的有序序列构造一棵二叉排序树时,得到的二叉排序树的深度也为n,在该二叉树上查找就演变成顺序查找,此时的最大查找长度为n;在随机情况下二叉排序树的平均查找长度为1+4log2n。
因此就查找效率而言,二分查找的效率优于二叉排序树查找,但是二叉排序树便于插入和删除,在该方面性能更优。
3. 评价哈希函数优劣的因素有:能否将关键字均匀的映射到哈希表中,有无好的处理冲突的方法,哈希函数的计算是否简单等。
冲突的概念:若两个不同的关键字Ki和Kj,其对应的哈希地址Hash(Ki) =Hash(Kj),则称为地址冲突,称Ki和K,j为同义词。
(1)开放定址法(2)重哈希法(3)链接地址法4.(1)构造的二叉排序树,如图(2)中序遍历结果如下:10 12 15 20 24 28 30 35 46 50 55 68(4)平均查找长度如下:ASLsucc = (1x1+2x2+3x3+4x3+5x3)/12 = 41/128.哈希地址如下:H(35) = 35%11 = 2H(67) = 67%11 = 1H(42) = 42%11 = 9H(21) = 21%11 = 10H(29) = 29%11 = 7H(86) = 86%11 = 9H(95) = 95%11 = 7H(47) = 47%11 = 3H(50) = 50%11 = 6H(36) = 36%11 = 3H(91) = 91%11 = 3第九章选择题1. D2.C3.B4.D5.C6.B7.A8.A9.D 10.D填空题1.插入排序、交换排序、选择排序、归并排序2.移动(或者交换)3.归并排序、快速排序、堆排序4.保存当前要插入的记录,可以省去在查找插入位置时的对是否出界的判断5.O(n)、O(log2n)6.直接插入排序或者改进了的冒泡排序、快速排序7.Log2n、n8.完全二叉树、n/29.1510.{12 38 25 35 50 74 63 90}应用题11.(1)Shell排序(步长为5 3 1)每趟的排序结果初始序列为100 87 52 61 27 170 37 45 61 118 14 88 32步长为5的排序14 37 32 61 27 100 87 45 61 118 170 88 52步长为3的排序结果14 27 32 52 37 61 61 45 88 87 170 100 118步长为1的排序结果14 27 32 37 45 52 61 61 87 88 100 118最后结果14 27 32 37 45 52 61 61 87 88 100 118 170(2)快速排序每趟的排序结果如图初始序列100 87 52 61 27 170 37 45 61 118 14 88 32第一趟排序[32 87 52 61 27 88 37 45 61 14]100[118 170]第二趟排序[14 27]32[61 52 88 37 45 61 87]100 118[170]第三趟排序14[27]32[45 52 37]61[88 61 87]100 118[170]第四趟排序14[27]32[37]45[52]61[87 61]88 100 118[170]第五趟排序14[27]32[37]45[52]61[87 61]88 100 118[170]最后结果14[27]32[37]45[52]61[61]87 88 100 118[170](3)二路归并排序每趟的排序结果初始序列[100][87][52][61][27][170][37][45][61][118][14][88][32]第一趟归并[87 100][52 61][27 170][37 45][61 118][14 88][32]第二趟归并[52 61 87 100][27 37 45 170][14 61 88 118][32]第三趟归并排序[27 37 45 52 61 87 100 170][14 32 61 88 118]第四趟归并排序[14 27 32 37 45 52 61 61 87 88 100 118 170]最后结果14 27 32 37 45 52 61 61 87 88 100 118 17012.采用快速排序时,第一趟排序过程中的数据移动如图:算法设计题1.分析:为讨论方便,待排序记录的定义为(后面各算法都采用此定义):#define MAXSIZE 100 /* 顺序表的最大长度,假定顺序表的长度为100 */ typedef int KeyType; /* 假定关键字类型为整数类型 */typedef struct {KeyType key; /* 关键字项 */OtherType other; /* 其他项 */}DataType; /* 数据元素类型 */typedef struct {DataType R[MAXSIZE+1]; /* R[0]闲置或者充当哨站 */int length; /* 顺序表长度 */}sqList; /* 顺序表类型 */设n个整数存储在R[1..n]中,因为前n-2个元素有序,若采用直接插入算法,共要比较和移动n-2次,如果最后两个元素做一个批处理,那么比较次数和移动次数将大大减小。
数据结构第九章--查找-习题及答案

第九章查找一、选择题1•若查找每个记录的概率均等,则在具有n 个记录的连续顺序文件中采用顺序查找法查找一个记录,其平均查找长度ASL 为()。
A .(n-1)/2B.n/2C.(n+1)/2D.n 2. 下面关于二分查找的叙述正确的是()A. 表必须有序,表可以顺序方式存储,也可以链表方式存储C.表必须有序,而且只能从小到大排列B. 表必须有序且表中数据必须是整型,实型或字符型D.表必须有序,且表只 能以顺序方式存储3. 用二分(对半)查找表的元素的速度比用顺序法() A. 必然快B.必然慢C.相等D.不能确定4. 具有12个关键字的有序表,折半查找的平均查找长度()A.3.1B.4C.2.5D.55.当采用分块查找时,数据的组织方式为()A. 数据分成若干块,每块内数据有序B. 数据分成若干块,每块内数据不必有序,但块间必须有序,每块内最大(或最小)的数据组成索引块C. 数据分成若干块,每块内数据有序,每块内最大(或最小)的数据组成索引块D. 数据分成若干块,每块(除最后一块外)中数据个数需相同6. 二叉查找树的查找效率与二叉树的((1))有关,在((2))时其查找效率最低(1) :A.高度B.结点的多少C.树型D.结点的位置(2) :A.结点太多B.完全二叉树C.呈单枝树D.结点太复杂。
7. 对大小均为n 的有序表和无序表分别进行顺序查找,在等概率查找的情况下,对于查找失败,它们的平均查找长度是((1)),对于查找成功,他们的平均查找长度是((2))供选择的答案:A.相同的B.不同的9.分别以下列序列构造二叉排序树,与用其它三个序列所构造的结果不同的是()A .(100,80,90,60,120,110,130)B.(100,120,110,130,80,60,90) C. (100,60,80,90,120,110,130)D.(100,80,60,90,120,130,110)10. 在平衡二叉树中插入一个结点后造成了不平衡,设最低的不平衡结点为A,并已知A 的左孩子的平衡因子为0右孩子的平衡因子为1,则应作()型调整以使其平衡。
《数据结构》第九章习题参考答案

《数据结构》第九章习题参考答案《数据结构》第九章习题参考答案一、判断题(在正确说法的题后括号中打“√”,错误说法的题后括号中打“×”)1、快速排序是一种稳定的排序方法。
(×)2、在任何情况下,归并排序都比简单插入排序快。
(×)3、当待排序的元素很大时,为了交换元素的位置,移动元素要占用较多的时间,这是影响时间复杂度的主要因素。
(√)4、内排序要求数据一定要以顺序方式存储。
(×)5、直接选择排序算法在最好情况下的时间复杂度为O(n)。
( ×)6、快速排序总比简单排序快。
( ×)二、单项选择题1.在已知待排序文件已基本有序的前提下,效率最高的排序方法是(A)。
A.直接插入排序B.直接选择排序C.快速排序D.归并排序2.下列排序方法中,哪一个是稳定的排序方法?(B)A.直接选择排序B.折半插入排序C.希尔排序D.快速排序3、比较次数与排序的初始状态无关的排序方法是( B)。
A.直接插入排序B.起泡排序(时间复杂度O(n2))C.快速排序D.简单选择排序4、对一组数据(84,47,25,15,21)排序,数据的排列次序在排序的过程中的变化为(1)84 47 25 15 21 (2)15 47 25 84 21 (3)15 21 25 84 47 (4)15 21 25 47 84 则采用的排序是( A)。
A. 选择B. 冒泡C. 快速D. 插入5、快速排序方法在(D)情况下最不利于发挥其长处。
A. 要排序的数据量太大B. 要排序的数据中含有多个相同值C. 要排序的数据个数为奇数D. 要排序的数据已基本有序6、用某种排序方法对线性表{25,84,21,47,15,27,68,35,20}进行排序,各趟排序结束时的结果为:(基准)20,21,15,25,84,27,68,35,47(25)15,20,21,25,47,27,68,35,84(左20右47)15,20,21,25,35,27,47,68,84(左35右68)15,20,21,25,27,35,47,68,84 ;则采用的排序方法为(C)。
数据结构与算法分析课后题答案
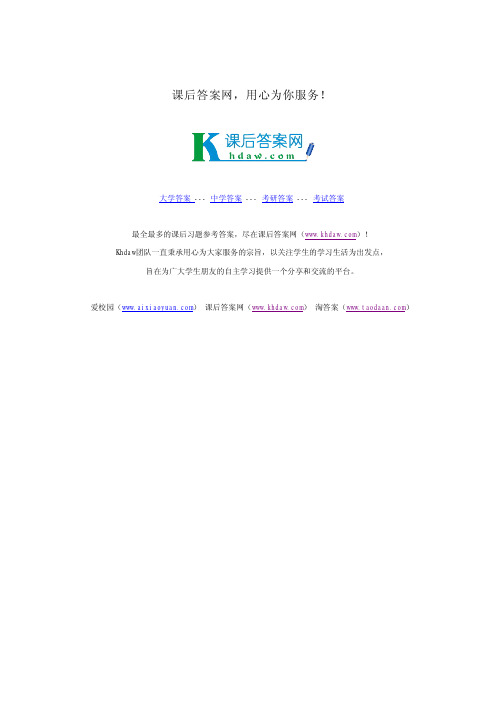
Chapter 5:Hashing5.1(a)On the assumption that we add collisions to the end of the list (which is the easier way if a hash table is being built by hand),the separate chaining hash table that results is shown here.4371132361734344419996791989123456789(b)96794371198913236173434441990123456789-25-w w w .k h d a w .com课后答案网(c)96794371132361734344198941990123456789(d)1989cannot be inserted into the table because hash 2(1989)=6,and the alternative locations 5,1,7,and 3are already taken.The table at this point is as follows:4371132361739679434441991234567895.2When rehashing,we choose a table size that is roughly twice as large and prime.In our case,the appropriate new table size is 19,with hash function h (x ) = x (mod 19).(a)Scanning down the separate chaining hash table,the new locations are 4371in list 1,1323in list 12,6173in list 17,4344in list 12,4199in list 0,9679in list 8,and 1989in list 13.(b)The new locations are 9679in bucket 8,4371in bucket 1,1989in bucket 13,1323in bucket 12,6173in bucket 17,4344in bucket 14because both 12and 13are already occu-pied,and 4199in bucket 0.-26-w ww .k h d a w.com课后答案网(c)The new locations are 9679in bucket 8,4371in bucket 1,1989in bucket 13,1323in bucket 12,6173in bucket 17,4344in bucket 16because both 12and 13are already occu-pied,and 4199in bucket 0.(d)The new locations are 9679in bucket 8,4371in bucket 1,1989in bucket 13,1323in bucket 12,6173in bucket 17,4344in bucket 15because 12is already occupied,and 4199in bucket 0.5.4We must be careful not to rehash too often.Let p be the threshold (fraction of table size)atwhich we rehash to a smaller table.Then if the new table has size N ,it contains 2pN ele-ments.This table will require rehashing after either 2N − 2pN insertions or pN deletions.Balancing these costs suggests that a good choice is p = 2/ 3.For instance,suppose we have a table of size 300.If we rehash at 200elements,then the new table size is N = 150,and we can do either 100insertions or 100deletions until a new rehash is required.If we know that insertions are more frequent than deletions,then we might choose p to be somewhat larger.If p is too close to 1.0,however,then a sequence of a small number of deletions followed by insertions can cause frequent rehashing.In the worst case,if p = 1.0,then alternating deletions and insertions both require rehashing.5.5(a)Since each table slot is eventually probed,if the table is not empty,the collision can beresolved.(b)This seems to eliminate primary clustering but not secondary clustering because all ele-ments that hash to some location willtry the same collision resolution sequence.(c,d)The running time is probably similar to quadratic probing.The advantage here is thatthe insertion can’t fail unless the table is full.(e)A method of generating numbers that are not random (or even pseudorandom)is given in the references.An alternative is to use the method in Exercise 2.7.5.6Separate chaining hashing requires the use of pointers,which costs some memory,and thestandard method of implementing calls on memory allocation routines,which typically are expensive.Linear probing is easily implemented,but performance degrades severely as the load factor increases because of primary clustering.Quadratic probing is only slightly more difficult to implement and gives good performance in practice.An insertion can fail if the table is half empty,but this is not likely.Even if it were,such an insertion would be so expensive that it wouldn’t matter and would almost certainly point up a weakness in the hash function.Double hashing eliminates primary and secondary clustering,but the compu-tation of a second hash function can be costly.Gonnet and Baeza-Yates [8]compare several hashing strategies;their results suggest that quadratic probing is the fastest method.5.7Sorting the MN records and eliminating duplicates would require O (MN log MN )timeusing a standard sorting algorithm.If terms are merged by using a hash function,then the merging time is constant per term for a total of O (MN ).If the output polynomial is small and has only O (M + N )terms,then it is easy to sort it in O ((M + N )log (M + N ))time,which is less than O (MN ).Thus the total is O (MN ).This bound is better because the model is less restrictive:Hashing is performing operations on the keys rather than just com-parison between the keys.A similar bound can be obtained by using bucket sort instead of a standard sorting algorithm.Operations such as hashing are much more expensive than comparisons in practice,so this bound might not be an improvement.On the other hand,if the output polynomial is expected to have only O (M + N )terms,then using a hash table saves a huge amount of space,since under these conditions,the hash table needs only-27-w w w .k h d a w .c o m课后答案网O (M + N )space.Another method of implementing these operations is to use a search tree instead of a hash table;a balanced tree is required because elements are inserted in the tree with too much order.A splay tree might be particularly well suited for this type of a problem because it does well with sequential paring the different ways of solving the problem is a good programming assignment.5.8The table size would be roughly 60,000entries.Each entry holds 8bytes,for a total of 480,000bytes.5.9(a)This statement is true.(b)If a word hashes to a location with value 1,there is no guarantee that the word is in the dictionary.It is possible that it just hashes to the same value as some other word in the dic-tionary.In our case,the table is approximately 10%full (30,000words in a table of 300,007),so there is a 10%chance that a word that is not in the dictionary happens to hash out to a location with value 1.(c)300,007bits is 37,501bytes on most machines.(d)As discussed in part (b),the algorithm will fail to detect one in ten misspellings on aver-age.(e)A 20-page document would have about 60misspellings.This algorithm would be expected to detect 54.A table three times as large would still fit in about 100K bytes and reduce the expected number of errors to two.This is good enough for many applications,especially since spelling detection is a very inexact science.Many misspelled words (espe-cially short ones)are still words.For instance,typing them instead of then is a misspelling that won’t be detected by any algorithm.5.10To each hash table slot,we can add an extra field that we’ll call WhereOnStack, and we cankeep an extra stack.When an insertion is first performed into a slot,we push the address (or number)of the slot onto the stack and set the WhereOnStack field to point to the top of the stack.When we access a hash table slot,we check that WhereOnStack points to a valid part of the stack and that the entry in the (middle of the)stack that is pointed to by the WhereOn-Stack field has that hash table slot as an address.5.14(2)000000100000101100101011(2)01010001011000010110111101111111(3)100101101001101110011110(3)1011110110111110(2)110011111101101111110000000001010011100101110111-28-w w w .k hd a w.c o m 课后答案网。
数据结构 第9章答案

第9章 查找参考答案一、填空题(每空1分,共10分)1. 在数据的存放无规律而言的线性表中进行检索的最佳方法是 顺序查找(线性查找) 。
2. 线性有序表(a 1,a 2,a 3,…,a 256)是从小到大排列的,对一个给定的值k ,用二分法检索表中与k 相等的元素,在查找不成功的情况下,最多需要检索 8 次。
设有100个结点,用二分法查找时,最大比较次数是 7 。
3. 假设在有序线性表a[20]上进行折半查找,则比较一次查找成功的结点数为1;比较两次查找成功的结点数为 2 ;比较四次查找成功的结点数为 8 ;平均查找长度为 3.7 。
解:显然,平均查找长度=O (log 2n )<5次(25)。
但具体是多少次,则不应当按照公式)1(log 12++=n nn ASL 来计算(即(21×log 221)/20=4.6次并不正确!)。
因为这是在假设n =2m -1的情况下推导出来的公式。
应当用穷举法罗列:全部元素的查找次数为=(1+2×2+4×3+8×4+5×5)=74; ASL =74/20=3.7 !!!4.【计研题2000】折半查找有序表(4,6,12,20,28,38,50,70,88,100),若查找表中元素20,它将依次与表中元素 28,6,12,20 比较大小。
5. 在各种查找方法中,平均查找长度与结点个数n 无关的查找方法是 散列查找 。
6. 散列法存储的基本思想是由 关键字的值 决定数据的存储地址。
7. 有一个表长为m 的散列表,初始状态为空,现将n (n<m )个不同的关键码插入到散列表中,解决冲突的方法是用线性探测法。
如果这n 个关键码的散列地址都相同,则探测的总次数是 n(n-1)/2=( 1+2+…+n-1) 。
(而任一元素查找次数 ≤n-1)二、单项选择题(每小题1分,共27分)( B )1.在表长为n的链表中进行线性查找,它的平均查找长度为A. ASL=n; B. ASL=(n+1)/2;C. ASL=n +1; D. ASL≈log2(n+1)-1( A )2.【计研题2001】折半查找有序表(4,6,10,12,20,30,50,70,88,100)。
清华大学出版社数据结构(C++版)(第2版)课后习题答案最全整理

清华大学出版社数据结构(C++版)(第2版)课后习题答案最全整理第1 章绪论课后习题讲解1. 填空⑴()是数据的基本单位,在计算机程序中通常作为一个整体进行考虑和处理。
【解答】数据元素⑵()是数据的最小单位,()是讨论数据结构时涉及的最小数据单位。
【解答】数据项,数据元素【分析】数据结构指的是数据元素以及数据元素之间的关系。
⑶从逻辑关系上讲,数据结构主要分为()、()、()和()。
【解答】集合,线性结构,树结构,图结构⑷数据的存储结构主要有()和()两种基本方法,不论哪种存储结构,都要存储两方面的内容:()和()。
【解答】顺序存储结构,链接存储结构,数据元素,数据元素之间的关系⑸算法具有五个特性,分别是()、()、()、()、()。
【解答】有零个或多个输入,有一个或多个输出,有穷性,确定性,可行性⑹算法的描述方法通常有()、()、()和()四种,其中,()被称为算法语言。
【解答】自然语言,程序设计语言,流程图,伪代码,伪代码⑺在一般情况下,一个算法的时间复杂度是()的函数。
【解答】问题规模⑻设待处理问题的规模为n,若一个算法的时间复杂度为一个常数,则表示成数量级的形式为(),若为n*log25n,则表示成数量级的形式为()。
【解答】Ο(1),Ο(nlog2n)【分析】用大O记号表示算法的时间复杂度,需要将低次幂去掉,将最高次幂的系数去掉。
2. 选择题⑴顺序存储结构中数据元素之间的逻辑关系是由()表示的,链接存储结构中的数据元素之间的逻辑关系是由()表示的。
A 线性结构B 非线性结构C 存储位置D 指针【解答】C,D【分析】顺序存储结构就是用一维数组存储数据结构中的数据元素,其逻辑关系由存储位置(即元素在数组中的下标)表示;链接存储结构中一个数据元素对应链表中的一个结点,元素之间的逻辑关系由结点中的指针表示。
⑵假设有如下遗产继承规则:丈夫和妻子可以相互继承遗产;子女可以继承父亲或母亲的遗产;子女间不能相互继承。
数据结构与算法习题册参考答案

三. 判断题
1. 有 n 个元素依次进栈,则出栈序列有(n-1)/2 种。 F 2. 栈可以作为实现过程调用的一种数据结构。 T 3. 在栈满的情况下不能做进栈操作,否则将产生“上溢”。 T 4. 在循环队列中,front 指向队头元素的前一个位置,rear 指向队尾元素的位置,则队 满的条件是 front=rear。 F
数据结构与算法 习题册
(课后部分参考答案)
《数据结构与算法》课程组
目录
目录
课后习题部分 第一章 绪论 ......................................................................................................... 1 第二章 线性表...................................................................................................... 3 第三章 栈和队列 .................................................................................................. 5 第四章 串 ............................................................................................................. 8 第五章 数组和广义表 ......................................................................................... 10 第六章 树和二叉树 ............................................................................................ 13 第七章 图 ........................................................................................................... 16 第九章 查找 ....................................................................................................... 20 第十章 排序 ....................................................................................................... 23
数据结构第三版第九章课后习题参考答案
}
}
设计如下主函数:
void main()
{ BSTNode *bt;
KeyType k=3;
int a[]={5,2,1,6,7,4,8,3,9},n=9;
bt=CreatBST(a,n);
//创建《教程》中图 9.4(a)所示的二叉排序树
printf("BST:");DispBST(bt);printf("\n");
#define M 26 int H(char *s)
//求字符串 s 的哈希函数值
{
return(*s%M);
}
构造哈希表 void Hash(char *s[]) //
{ int i,j;
char HT[M][10]; for (i=0;i<M;i++)
//哈希表置初值
HT[i][0]='\0'; for (i=0;i<N;i++) { j=H(s[i]);
//求每个关键字的位置 求 // s[i]的哈希函数值
while (1)
不冲突时 直接放到该处 { if (HT[j][0]=='\0') //
,
{ strcpy(HT[j],s[i]);
break;
}
else
//冲突时,采用线性线性探测法求下一个地址
j=(j+1)%M;
}
} for (i=0;i<M;i++)
printf("%2d",path[j]);
printf("\n");
}
else { path[i+1]=bt->key;
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Chapter 9: ADT Implementations: Templates and Standard Containers Exercises 9.3
1.
template <typename DataType> DataType average(DataType a, DataType b) { return (a + b)/2; }
6.
template <typename DataType> int search(DataType x[], int length, DataType target) { for (int index = 0; index < length; index++) if (x[index] == target) return index; return -1; } // index of -1 denotes not found
2.
template <typename DataType> DataType max(DataType a, DataType b) { if (a > b) return a; else return b;
3.
template <typename DataType> DataType median (DataType a, DataType b, DataType c) { DataType max = a, min = b; if (a < b) { max = b; min = a; } if (c > max) return max; else if (c < min) return min; else return c; }
7.
/*-- ListT.h -----------------------------------------------------------This header file defines the data type List for processing lists. Basic operations are: Constructor empty: Check if list is empty insert: Insert an item erase: Remove an item display: Output the list <<: Output operator -----------------------------------------------------------------------*/ #include <iostream> #ifndef LISTT #define LISTT const int CAPACITY = 1024; template <typename ElementType> class List { public: /******** Function Members ********/ /***** Class constructor *****/ List(); /*--------------------------------------------------------------------Construct a List object. Precondition: None Postcondition: An empty List object has been constructed; mySize is 0. ---------------------------------------------------------------------*/ – 97 –
– 96 –
Chapter 9
5.
template <typename DataType> void arrayMaxMin(DataType x[], int length, DataType & min, DataType & max) { min = max = x[0]; for (int i = 1; i < length; i++) { if (x[i] < min) min = x[i]; if (x[i] > max) max = x[i]; } }
// current size of list stored in myArray // array to store list elements
– 98 –
Chapter 9
//--- Definition of class constructor template <typename ElementType> inline List<ElementType>::List() : mySize(0) {} //--- Definition of empty() template <typename ElementType> inline bool List<ElementType>::empty() const { return mySize == 0; } //--- Definition of display() template <typename ElementType> inline void List<ElementType>::display(ostream & out) const { for (int i = 0; i < mySize; i++) out << myArray[i] << " "; } //--- Definition of output operator template <typename ElementType> inline ostream & operator<<(ostream & out, const List<ElementType> & aList) { aList.display(out); return out; } //--- Definition of insert() template <typename ElementType> void List<ElementType>::insert(ElementType item, int pos) { if (mySize == CAPACITY) { cerr << "*** No space for list element -- terminating " "execution ***\n"; exit(1); } if (pos < 0 || pos > mySize) { cerr << "*** Illegal location to insert -- " << pos << ". List unchanged. ***\n"; return; } // First shift array elements right to make room for item for(int i = mySize; i > pos; i--) myArray[i] = myArray[i - 1]; // Now insert item at position pos and increase list size myArray[pos] = item; mySize++; }
Chapter 9
/***** empty operation *****/ bool empty() const; /*--------------------------------------------------------------------Check if a list is empty. Precondition: None Postcondition: true is returned if the list is empty, false if not. ---------------------------------------------------------------------*/ /***** insert and erase *****/ void insert(ElementType item, int pos); /*-------------------------------------------------------------------Insert a value into the list at a given position. Precondition: item is the value to be inserted; there is room in the array (mySize < CAPACITY); and the position satisfies 0 <= pos <= mySize. Postcondition: item has been inserted into the list at the position determined by pos (provided there is room and pos is a legal position). ---------------------------------------------------------------------*/ void erase(int pos); /*-------------------------------------------------------------------Remove a value from the list at a given position. Precondition: The list is not empty and the position satisfies 0 <= pos < mySize. Postcondition: element at the position determined by pos has been removed (provided pos is a legal position). --------------------------------------------------------------------*/ /***** output *****/ void display(ostream & out) const; /*------------------------------------------------------------------Display a list. Precondition: The ostream out is open. Postcondition: The list represented by this List object has been inserted into out. ---------------------------------------------------------------------*/ private: /******** Data Members ********/ int mySize; ElementType myArray[CAPACITY]; }; //--- end of List class template //------ Prototype of output operator template <typename ElementType> ostream & operator<< (ostream & out, const List<ElementType> & lt;typename DataType> DataType arraySum(DataType x[], int length) { DataType sum = x[0]; for (int index = 1; index < length; index++) sum += x[index]; return sum; }
