中山大学软件学院
中山大学2014年软件学院硕士研究生复试录取结果(更新)
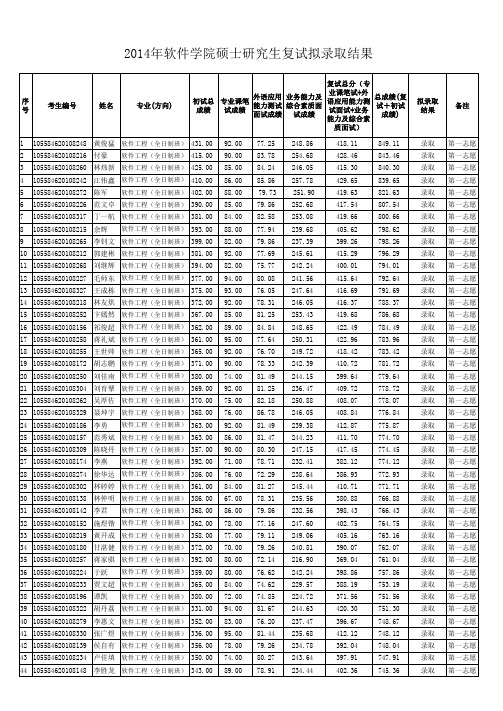
849.11 843.46 840.30 839.65 821.63 807.54 800.66 798.62 798.26 796.29 794.01 792.64 791.69 788.37 786.68 784.49 783.96 783.42 781.72 779.64 778.72 778.07 776.84 775.87 774.70 774.45 774.12 772.93 771.71 766.88 766.43 764.75 763.16 762.07 761.04 757.86 753.19 751.56 751.30 748.67 748.12 748.04 747.91 745.36
77.25 83.78 84.24 85.86 79.73 79.86 82.58 77.94 79.86 77.69 75.77 80.08 76.05 78.31 81.25 84.84 77.64 76.70 78.33 81.49 81.25 82.18 86.78 81.49 81.47 80.30 78.71 72.29 81.27 78.31 79.86 77.16 79.11 79.26 72.14 76.62 74.62 74.85 81.67 76.20 81.44 79.26 80.27 78.91
录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取 录取
第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿 第一志愿
国家示范性软件工程学院

5 北京理工大学 软件学院 School of Software Engineering, Beijing Institute of Technology 北京 北京
6 北京邮电大学 软件学院 School of Software Engineering, Beijing Univerisity of Posts and Telecommunications 北京 北京
35 中国科学技术大学 软件学院 School of Software Engineering, University of Science and Technology of China 合肥 安徽
36 中南大学 软件学院 School of Software Engineering, Central South University 长沙 湖南
29 西安电子科技大学 软件学院 School of Software Engineering, Xidian University 西安 陕西
30 西安交通大学 软件学院 College of Software and Microelectronics, Xi'an Jiaotong University 西安 陕西
3 北京航空航天大学 软件学院 School of Software Engineering, Beihang University 北京 北京
4 北京交通大学 软件学院 School of Software Engineering, Bejing Jiaotong University 北京 北京
21 南开大学 软件学院 School of Software Engineering, Nankai University 天津 天津
中山大学软件学院

2 4 00
关系 ・与广 州天河软 件 目 r东省技 f 行业 台 Ⅱ信科 技 新 太 秆拄 r . i -
东电信 等瑜 ;知高 I T .在学 生就 业培训 毕 她虫殴 技术 共卓 朕 * 强课蘑研 究等 多方而进 行了广 眨 的音作 .
理 拥有 包括 辜堪体 教童
生 专 用 机 房 近 20 0 方 5平
实验 室
学
配 各就 撇机
近 40 . I 0台 BM R 00 AS4  ̄ 务 器 ¥6 0 oo
軎 一台.拥有 I M Mi r s f O a l B c oot rce B A 企业褂 送的软 件一批 .软硬 伴 设备 E 等 价值超 过I O 万 元。 0 I
.
我院的 师资 由学院 专职 毅师 .国 内外著 名高 桎抖脐 机构 的学 喜 . 名企 业的 中高镫 管 k吊 帮资 著
深技 术^员组盛
我皖0 和撒 国0 司 订 丁告 怍
I M O al S N B A B rc U E e
崽普 、恩科
垩 书信等 跨
t与 姜国伊 里瞄理 I学 院建 血T Ⅱ撮主 教 师的 合作
№
H
- 目
r
十 女 #
51 7 ̄ 02
∞ !5 ̄ 一 4 5
Bl ̄ ? 4 lபைடு நூலகம்3 l … u ,ht / tp
2 0 年 开始至 夸已招 车科生五 百 多人, 阱究生目 百喜 ^ 02 年首 毕业生 1 l 4 ^,实 现T就业 串日n 百.
^:
维普资讯
中★软件 擘皖立 华 南
意 炽的 ^ 。 音
辐射浩 矗 .利用泛 璋二 埔蛏挤 延墟建 惶的 I遘 晕莽 垒璋÷ 韩 有搠 f L t
中山大学14A软件学院研究生论文导师一览表(2)
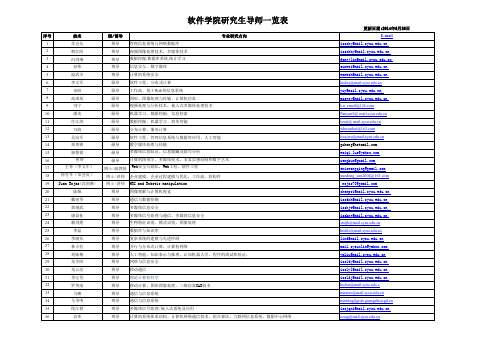
1常会友博导管理信息系统与网络数据库isschy@2朝红阳博导视频图像处理技术,多媒体技术isschhy@ 3冯剑琳博导数据挖掘,数据库系统,统计学习fengjlin@ 4孙伟博导信息安全、数字媒体sunwei@5温武少博导计算机系统安全wenwsh@6李文军硕导软件工程、分布式计算lnslwj@7余阳硕导工作流、基于Web的信息系统yuy@,8高成英硕导图形、图像处理与传输、计算机仿真mcsgcy@9刘宁硕导视频处理与分析技术,嵌入式多媒体处理技术Ln_email@10潘炎硕导机器学习,数据挖掘,信息检索Panyan5@ 11任江涛硕导数据挖掘、机器学习、商务智能issrjt@ 12万海硕导分布计算,服务计算whwanhai@13吴向军硕导软件工程、管理信息系统与数据库应用、人工智能issxjwu@14郑贵锋硕导数字媒体处理与传输gzheng@15骆伟祺硕导多媒体信息取证、信息隐藏及隐写分析weiqi.luo@16 曾坤硕导计算机图形学,多媒体技术,非真实感绘制和数字艺术zengkun@17 王青(李文军)博士/副教授 Web安全与隐私,Web工程,软件工程ericwangqing@18孙雪冬(常会友)博士/讲师企业建摸,企业过程建摸与优化,工作流,软构件xuedong_sun2004@ 19Juan Rojas(冯剑琳)博士/讲师HRI and Robotic manipulation rojas70@20陈佩博导图像理解与计算机视觉chenpei@ 21戴宪华博导通信与数据挖掘issdxh@ 22黄继武博导多媒体信息安全isshjw@, 23康显桂博导多媒体信号处理与通信,多媒体信息安全isskxg@ 24赖剑煌博导生物特征识别,模式识别,图象处理stsljh@25李磊博导数据库与知识库lnslile@26李晓东博导复杂系统的建模与先进控制lixd@27林小拉博导并行与分布式计算,计算机网络mail.sysuxlin@ 28刘咏梅博导人工智能,知识表示与推理,认知机器人学,程序的调试和验证.ymliu@29龙冬阳博导网络与信息安全issldy@ 30龙云亮博导移动通信isslyl@ 31娄定俊博导理论计算机科学issldj@ 32罗笑南博导移动计算,图形图象处理,三维仿真CAD技术lnslxn@.c33马啸博导通信与信息系统maxiao@34马争鸣博导通信与信息系统mzming@ 35倪江群博导多媒体信号处理/嵌入式系统及应用issjqni@ 36农革博导计算机系统体系结构、计算机网络通信技术、组合算法、互联网信息系统、数据中心网络issng@37秦家银博导通信与信息系统(无线CDMA通信技术)issqjy@ 38邱道文博导模糊逻辑及有关应用issqdw@39沈鸿博导并行与分布式计算,组合优化算法,网络路由,安全计算,数据挖掘shenh3@ 40谭洪舟博导智能信息系统,智能信息处理,IC设计,数据挖掘issthz@ 41王国利博导分布式信息处理isswgl@42印鉴博导数据挖掘,数据库与数据仓库,人工智能,智能信息处理issjyin@43余顺争博导计算机网络与通信syu@44张方国博导密码学与信息安全isszhfg@45张军博导人工智能、智能优化、遗传算法、外汇与股票趋势的时间序列分析与预测issai@46张雨浓博导神经网络,机器人,人工智能,并行分布计算,优化,算法研究zhynong@ 47蔡宏民硕导模式识别与智能系统caihongm@ 48陈炬桦硕导管理信息系统isscjh@ 49陈立硕导编码理论及其应用;宽带/超宽带无线通信理论与技术;通信理论与通信信号处理;chenli55@ 50成慧硕导数字信号处理chengh9@ 51范正平硕导Internet网络结构分析、网络病毒传播分析、zhpfan@52方艳梅硕导多媒体信息安全,多媒体信号处理与通信fangym@53高集荣硕导数据库、数据仓库、数据挖掘,网络软件gaojr@54郭清顺硕导企业信息化, 电子政务gqs@55郭雪梅硕导嵌入式系统与移动计算guoxuem@ 56胡海锋硕导图像信息处理与计算机视觉huhaif@ 57黄方军硕导图象分析与理解huangfj@ 58黄晓硕导无线电物理—无线网络,电路与系统—蓝牙技术huangx@59黄以华硕导多媒体信号处理和传输,嵌入式系统和应用sysuhyh@60纪庆革硕导游戏动画与虚拟现实、计算机图形学、计算机视觉、系统仿真、复杂网络issjqg@61李才伟硕导网络与多媒体isscwli@62李宁硕导计算机网络与信息处理lining@63李元新硕导天线电波理论与移动通信lipbzn@64李中华硕导嵌入式系统与应用、物联网与RFID技术。
中山大学软件学院本科生期末考试《数据库系统原理》(A卷)

中山大学软件学院本科生期末考试考试科目:《数据库系统原理》(A卷)学年学期:2014学年第3学期姓名:学院/系:软件学院学号:考试方式:开卷年级专业:考试时长:120分钟班别:第八条:“考试作弊者,不授予学士学位。
”------------以下为试题区域,共7道大题,总分100分,考生请在答题纸上作答------------1. (10 marks) Let R = {A, B, C, D, E, F, G} and F = {AB→C, A→C, A→E, B→C, EF→EG, G→F}. Answer the following three questions.1)(4 marks) Compute the minimal cover of F.B→CA→CA→EEF→GG→F2)(4 marks) Decompose R into 3NF relations.{B, C}, {A, C, E}, {E, F, G} and {A, B, D, F} (OR {A, B, D, G})3)(2 marks) Is the composition in (b2) in BCNF? Briefly explain your answer.No. For {E, F, G} and G→F, G is not a candidate key.2. (10 marks)Assume there is an employee database Employee (eid: 8 bytes, ename: 16 bytes, did: 4 bytes, email: 12 bytes), where eid and ename are respectively the id and name of an employee and did is the id of the department in which the employee works. Suppose there are 50,000 employee records and 500 departments (i.e. each department has 100 employees on average). A page size is 1,000 bytes and a pointer costs 4 bytes.1)(4 marks) Assume that the employee file is sorted sequentially on did and there is noindex. Estimate the page access cost for retrieving the records of all employees working in a department with a given did. (You should show your argument and the main steps of the estimation clearly in the answer.)AnswerRecord size = 40 bytes, 25 records per page, 2,000 pages.Finding the first record requires log22000 + 3 more pages to search theremaining records (each dept has 100 employees which are distributed in 4pages).2)(6 marks) Assume only 20 pages of main memory are available for running theexternal sorting of the employee file on did.•How many PASSes are needed for the external sorting?•In each PASS, how many runs are created?•What is the total cost of the sorting in terms of pages?Answer:3 PASSes:PASS 0: 2000 pages / 20 pages per run = 100 runsPASS 1: ceil (100 runs / 19 runs per run) = 6 runsPASS 2: 1 runTotal cost: (2000 pages read per pass + 2000 pages write per pass) * 2 PASSes +2000 pages read per pass = 10000 pages (Note: Output is not counted!)Or: 2000 * (2 * 2 + 1) = 10000 pages transfer.3. (10 marks) Suppose a bookstore has the following five relational tables:BOOK (BID, TITLE, AID, SUBJECT, QUANTITY_IN_STOCK)AUTHOR (AID, NAME) CUSTOMER (CID, NAME)ORDER_DETAILS (OID, BID , QUANTITY) ORDER (OID, CID , ORDER_YEAR)In the above tables, keys are underlined and foreign keys are in italics . Each author has authored at least one book in the store. Each book has exactly one author. Each order is made by exactly one customer and has one or more associated record in ORDER_DETAILS (e.g., an order may contain different books).Express the following query using (i) SQL expressions, (ii) the relational algebra (RA).Find the distinct customer IDs (CID) of customers who have purchased more than 10 identical books in one order at least once.(i) SELECT DISTINCT CIDFROM ORDER_DETAILS od, ORDER oWHERE QUANTITY >= 10 AND od.OID = o.OID(ii)CID (σQUANTITY ≥ 10 (ORDER_DETAILSOID ORDER ))4. (10 marks) A B+ tree with n=5 is shown in Figure 1, in which only search keys are shown and pointers to the file system are hidden. We want to insert a data entry with search key “23”.Figure 1. A B+ Tree Structure1) Which of the following descriptions about the insertion operation is correct?A.The B+ tree contains 2 levels after insertion. 2 node splits are needed duringinsertion. The root node contains search key “15”.B.The B+ tree contains 3 levels after insertion. 1 node split is needed duringinsertion. The root node contains search key “20”.C.The B+ tree contains 3 levels after insertion. 2 node splits are needed duringinsertion. The root node contains search key “15”.D.The B+ tree contains 3 levels after insertion. 2 node splits are needed duringinsertion. The root node contains search key “20”.Answer: C2)We want to delete the data entry with search key “7”. How many leaf nodes store onlytwo data values after deletion?A.2B. 3C. 4D.5Answer: A5. (20 marks)You are given an initial hash structure with three keys already inserted as below. The hash function is h(x) = x mod 16. Draw five extendable hash structures corresponding for each insertion of the following search key values K: 7, 15, 20, 37, 18. Assume each bucket can hold two keys and the search key values arrive in the given order (i.e. 7 being the first coming key and 18 being the last one).You should follow the convention used by lecture slides: binary hash indices starting from the least significant bit. (E.g. 1 is the least significant bit of the 4 digit binary number 0001.)AnswerInsert 7Insert 15 and 20Insert 37Insert 186. (25 Marks) Consider a database consisting of the following three relation schemas:SAILORS (sid, sname, rating, age)BOATS (bid, bname, color)RESERVES (sid, bid, date, rname)The meaning of the attributes in the above schemas is self-explanatory. For example, sid is the sailor identity number and bname is the name of the boat. The primary keys of the relations are underlined. The attribute sid in RESERVES is a foreign key referencing SAILORS. The attribute bid in RESERVES is a foreign key referencing BOATS.The relation SAILORS has 100,000 tuples and 100 tuples of SAILORS fit into one page. The relation BOATS has 50,000 tuples and 25 tuples of BOATS fit into one page. The relation RESERVES has 10,000 tuples and 20 tuples of RESERVES fit on one page. We assume all attribute values and pointers in these three relations, if needed to be considered, are of the same size.(a)(10 marks) Assume that we use Indexed Nested Loop Join to computeSAILORS RESERVES using SAILORS as the outer relation. RESERVES have a primary B+-tree index with 2 levels on the join attribute. Estimate the cost of the join in terms of pages.Number of SAILORS pages: br = 100,000/100 = 1,000Number of SAILORS Tuples: nr = 100,000.The cost is br+ c * nr = 1,000 + (2+1) * 100,000 = 301,000.(b)(5 mark)Assume that 26% of the sailors have the rating bigger than 5. Estimate theresult size of sid(σrating>5 SAILORS) in terms of pages.Size = 26% * 100,000 / 100/4 = 65 pages260 divided by 4, for there is projection and all the attributes have same size(c)(10 marks) Consider the following two strategies to compute the join operationSAILORS BOATS RESERVES.Strategy 1: (SAILORS BOATS) RESERVESStrategy 2: (SAILORS RESERVES) BOATSWhich strategy is better? Explain the reason(s) of your choice based on the size of the intermediate result using the above strategies.Strategy 2 is better.Because in Strategy 1, SAILORS BOATS is equal to the cross-product of the two relations and the size of the join result will become as large as 100,000 * 50,000 = 5,000,000,000 tuples. This intermediate result is very large and later when joining this intermediate result with RESERVES, the cost is also large.In comparison, in Strategy 2, SAILORS RESERVES has only 10,000 tuples. And later when joining this intermediate result with BOATS, the cost is also small.7. (15 Marks) Consider a schedule S which consists of four transactions as follows:S = <T3_R(U), T2_R(X), T2_W(X), T3_R(X), T1_R(Y), T1_W(Y), T3_W(X), T1_R(Z), T4_R(Z), T4_W(Z), T2_W(Y), T3_R(Y)>The notation is self-explanatory. For example, T1_R(X) means that transaction T1 reads item X.(a)(5 marks) Fill in the following table representing S with the usual notations in lectureslides. The first operation R(U) has been shown in the table. Show clearly all conflicting pairs with downward arrows on the operations.(b)(5 marks) Construct the precedence graph of S. Explain why or why not the schedule isconflict-serializable.Precedence Graph of S:No cycle.(c)(5 marks) Suppose the format of the “commit” operation is Ci where i = 1, 2, 3, or 4.For example, the operation C1 means that the transaction T1 commits. Append all the commit statements to S so that the schedule becomes recoverable. For example, one append can be SC4C3C2C1 which means running S and then C4, C3, C2, C1. (Note that you should NOT change the sequence of the operations in S other than appending S with the four commit statements to make the schedule recoverable.)Recoverable (but not cascadeless) schedule: SC1C2C3C4 or (SC1C2C4C3) or (SC1C4C2C3) (Note: any permutation of Ci satisfies the commit order constraints: C1→C2, C1→C3, C1→C4, C2→C3 is correct)。
中山大学软件学院专业课计算机组成原理课件第5章

Sec.1.3 Introduction to assembly programming
A program that consists of 0s and 1s is called machine language. Assembly languages provides mnemonics for the machine code instructions, plus other features that made programming faster and less prone to error. Assembly language programs must be translated into machine code by a program called an assembler. Assembly language is referred to as a low-level language because it deals directly with the internal structure of the CPU.
CHAPTER 1
Sec.1.3 Introduction to assembly programming
MOV instruction
Simply stated, the MOV instruction copies data from one location to another. It has the following format:
SS).
MOV AX, 2345H ;load 2345H into AX
MOV DS, AX
MOV instruction
• In the 8086 CPU, data can be moved among all the registers shown in
中山大学软件学院

传
网
2 0 年开 始 至 今 已招 本科 生五 百 多人 ,研究 生 四百 多 人 。2 0 02 04
‘
联 系 人 焦 老 师
届毕 业 生 I 1 ,实现 了就 业率 百分 百 。 4人
维普资讯
“ 种素 质” 、 “ 个 层次 ” 、 “ 种 能 力” 。 “ 三 四 六 三种 素 质 ” ,即 创新 素 质 、 团队 素 质和 敬 业素
;
“ 个 层次 ”即 高级 程 序 员 ,系统 分 析 与设 计 员 ,I 四 T项 目管理 员 ,I T企 业 发展 战略 决 策 和经 营管
员四 个 层次 ; “ 种 能 力 ”即 分析 与 解决 问题 的能 力 ,交流 与 组织 协 调 的能 力 ,主 动 获取 知 识 的能 六
,
科 学 高效管 理项 }的能 力 ,工 程 实践 的能 力 和参 与 国际 竞争 的能 力 。 ]
我院 的 师 资 由学 院 专 职 教师 ,国 内 外著 名 高 校科 研 机 构 的 学 者 ,著 名 企业 的 中 高级 管 理 人 员和资
一
台 , 拥 有 I , M ir s f、 Or ce BM Coot a l,
等 企 业赠 送 的软 什 一批 ,软 硬 件 设 备
[ 过 I0 万 元 。 超 0 1
一
地 邮 址 , 市 中… 夫学软 件 学院 ¨l 编 51 27 0 5
1 真 0 0-8 3 73 2 4l 6
邑信 等 众 多知 I T企 业 ,1 生 就 业培 圳 ,牛业 实践 ,技 术 享 ,联 合开 芏学 题 研 究等 多 方面进 行 了广泛 的 合作 。
加盐哈希

加盐哈希的工作原理12330416 郑锦泽广州中山大学软件学院电子政务510006【摘要】本文主要讲述什么是加盐、为什么要加盐、怎么加盐【关键词】加盐,salty hash一:什么是加盐在密码学里,盐是指一串随机的数据,加盐即是将这串数据作为一个单项函数(如哈希函数)的额外的输入。
【1】例图:二:为什么要加盐哈希加密算法,尤其是MD5算法,一直被认为是不可能被破解的。
但如今,已经好有几种方法可以破解了。
1. 暴力破解(brute-force attack)暴力破解即在某个长度下尝试每一种可能的组合,这种方法计算代价太大,而且低效,但也是最有效的方法,如果破解时间足够长的话。
2. 字典破解(brute-force attack)字典破解即将一些单词、短语、常见密码和其他可能用作密码的单词存入字典,并取其加密后的哈希值,与真正密码的哈希值作对比。
3. 查找表(Lookup Table)和字典破解很相似,不同点在于是将加密后的哈希值存入文件,并进行排序优化。
4. 反查表(Reverse Lookup Table)综合暴力破解跟字典破解,先将已知的用户名跟哈希后的密码对应起来,然后寻找某个密码哈希值对应的用户,因为很多用户使用同个密码是很正常的。
5. 彩虹表(Rainbow Table)和查找表很类似,只不过是牺牲查找速度来增大存储数目。
彩虹表对长度8以下的密码尤为有效。
因此,原始的哈希算法已经不再安全,但其不可逆性却让密码专家们不忍心抛弃,于是就在其基础上,实现了新的加密算法,那就是加盐。
三:怎么加盐以上的五种破解方法,除了暴力破解外,都有一个共同特点,那就是要求每一次加密的结果都相同,也就是相同的密码加密后的结果一定是相同的。
因此,防破解的办法就在于防止这种必然,也就是说,让相同的密码加密后的结果不一样,这就是加盐的秘诀所在。
当注册时,我们可以随机生成个字符串,将其拼接在密码中,可以在前面添加,也可以在后面添加,甚至可以在中间某个位置添加。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
中山大学软件学院软件工程硕士研究生课程教学大纲Course Profile for Master of Software Engineering (MSE) Students最近更新/ Revision : 2009.09.10课程编号Course Code SE-901课程名称Course Title软件工程进展Advances in Software Engineering课程类别Course Type 专业必修课Compulsory学分Credits3理论环节Lecture Sessions51实验环节Laboratory Sessions周学时Hours per Week 3总学时Total Hours学时合计Total51开课学期Semester 第一学年秋季学期Fall semester, 1st year课程负责人Course Coordinator 李师贤教授Prof. Shi-xian LIEmail : lnslsx@Homepage : PENDING主要授课教师Principal Instructors 李师贤教授、常会友教授、李文军教授、周晓聪副教授、毛明志副教授、潘炎博士、舒忠梅博士Prof. Shi-xian LI, Prof. Hui-you CHANG, Prof. Wen-jun LI, A/Prof. Xiao-cong ZHOU, A/Prof. Ming-zhi MAO, Dr. Yan PAN, Dr. Zhong-mei SHU教学助理配置TeachingAssistantsNone课外交流时间Office Hours 主讲教师:每周2小时。
Instructor: 2 hours per week.教学助理:无。
TA: N/A.课程主页HomepagePENDING 讨论社区ForumPENDING课程描述Course Description 本课程旨在让学生了解软件工程中一些前沿的理论和技术,以及一些新的研究方向。
本课程由多名教师以模块化方式教学,目前覆盖软件体系结构(SA)、基于构件的软件开发(CBSD)、面向方面的软件开发(AOSD)、基于COTS的软件开发、开源软件运动、实验软件工程(ESE)、软件工程经济学等知识模块。
本课程所选的模块将随着软件工程领域的发展而变化。
本课程的考核采取论文的方式,学生针对自己感兴趣的知识模块,进一步阅读相关参考文献,撰写一篇符合软件工程研究模式和学术论文规范的课程论文。
The goal of the course is to introduce some advanced theories and technologies to students. Currently, this course covers the following topics: Software Architecture (SA); Component-Based Software Development (CBSD); Aspect-Oriented Software Development (AOSD); Commercial Off-The-Shelf (COTS); Open Source; EmpiricalSoftware Engineering (ESE); Software Engineering Economics. These topics will beadjusted according the developing of software engineering.先修课程PrerequisitesNone后续课程SuccessiveCoursesNone理论教学部分Lecture Sessions教材Textbook No textbook specified. Students will be provided with course handouts including lecture slides, ebooks and research papers.教学参考书References [1] B. Boehm. Software Engineering Economics. Prentice Hall, 1981, ISBN0-138-22122-7中译版:李师贤等译,《软件工程经济学》,软件工程技术丛书,北京:机械工业出版社,2004,ISBN 7-111-14389-2[2] C. Jones. Estimating Software Costs: Bringing Realism to Estimating, 2nd Ed.McGraw-Hill Osborne Media, 2007, ISBN 0-071-48300-4中译版:刘从越等译,《软件项目估计》(第2版),软件工程研究院,北京:电子工业出版社,2008,ISBN 7-121-05806-6[3] I. Jacobson and Pan-Wei Ng. Aspect-Oriented Software Development with UseCases. Addison Wesley, 2005, ISBN 0-321-26888-1影印版:《基于用例的面向方面软件开发》,北京:机械工业出版社,2006,ISBN 7-111-17771-1中译版:徐锋译,《AOSD中文版——基于用例的面向方面软件开发》,北京:电子工业出版社,2005,ISBN 7-121-01831-4[4] A. Colyer, A Clement, G. Harley and M. Webster. Eclipse AspectJ: Aspect-OrientedProgramming with AspectJ and the Eclipse AspectJ Development Tools. Addison Wesley, 2004, ISBN 0-321-24587-3中译版:钱竹青等译,《Eclipse AspectJ中文版——利用Eclipse和AspectJ进行面向方面程序设计》,北京:清华大学出版社,2006,ISBN 7-302-13976-8[5] C. Wohlin, P. Runeson, M. Host, M. C. Ohlsson, B. Regnell and A. Wesslen.Experimentation in Software Engineering: An Introduction. Kluwer Academic Publishers, 2000, ISBN 0-792-8682-5教学方法Approach1. Theoretical lectures combined with studies of research papers.理论教学内容Lectures Preface. Introduction (3 hr)Instructor: Prof. Wen-jun LIintroduction to this course; research pattern in software engineering; how to read and write a paper in software engineering.Module I. Software Engineering Economics (12 hr)Instructor: Prof. Shi-xian LI1. Principles and Methods of Software Cost Estimation (6 hr)case studies on software cost estimation; basic COCOMO model; intermediate COCOMO model; performance models; cost-effectiveness models; multi-goal decision analysis. alternative methods.2. Software Cost Estimation and Life-Cycle Management (6 hr)software maintenance cost estimation; software life-cycle cost estimation; software project planning and control. improving software productivity.Module II. Component-based Software Development (9 hr)Instructor: Prof. Hui-you CHANG1. Introduction to Component-Based Software Development (3 hr)basic concepts and revolutionary history of CBSD (Component-Based Software Development); components and standards; software architecture; patterns and frameworks.2. Technology and Processes of Component-Based Software Development (3 hr)CBSD: industrialization of software engineering; component-based issurance solution: an architecture for success; CBSD: a roadmap to e-business success.3. Components Library and Component Marketplace (2 hr)technology of components library or services library; Internet component marketplace;CBSD resources.4. Software Patterns and Components (1 hr)patterns in CBSD, including: analysis patterns; design patterns; process patterns; and organizational patterns.Module III. Aspect-Oriented Software Development (9 hr)Instructor: A/Prof. Xiao-cong ZHOU1. Introduction to AOSD (Aspect-Oriented Software Development) (2 hr)history of aspect-oriented programming and aspect-oriented software development;motivation of aspect-oriented software development; nature of aspect-orientation; basic concepts and common terminology of aspect-oriented software development.2. Aspect-Oriented Analysis and Design (2 hr)introduction to aspect-oriented software development with use cases: motivation, basic ideas and a simple example; brief introduction to theme approach; applying aspect-orientation in software engineering, e.g. using aspect-oriented technology to capture run-time information of software, etc.3. Aspect-Oriented Programming in AspectJ (5 hr)what is an aspect in AspectJ; key design properties of AspectJ language; how to define join points and pointcuts in AspectJ; how to define advice in AspectJ; how to define inter-type declarations in AspectJ; writing aspect-oriented programs with AspectJ and Eclipse AspectJ development tools; brief introduction to other aspect-oriented programming languages.Module IV. Open Source and COTS (Commercial Off-The-Shelf) (12 hr)Instructor: Dr. Yan PAN1. Introduction to Open Source (3 hr)history of open source software; motivation of “free software”; successful stories of open source; business mode of open source; new trends in open source; open source technical stack; open source licenses.2. Web Application Development with Open Source Frameworks (4 hr)(1) Introduction to Spring (2 hr): successful stories of Spring framework; Inversion ofControl (IoC) in Spring; Aspect-Oriented Programming (AOP) in Spring; transaction management; exception translator; filter; case studies.(2) Introduction to Hibernate (1 hr): basics of object-relation mapping (O/R mapping);general framework of Hibernate; key elements of Hibernate; properties configuration of sessionFactory ; configuration of mapping files; case studies and best practice.(3) Introduction to Struts (1 hr): MVC pattern; key elements of web frameworks; stateless roundtrip of HTTP protocol; JSP and Struts tags; action in Struts; configuration of Struts; case studies.3. Commonly Used Open Source Tools (2 hr)concepts of unit testing; testing with JUnit; logging with log4j; building software with Ant; source code management with CVS.4. COTS (Commercial Off-The-Shelf) (3 hr)PENDING.Module V. Empirical Software Engineering (12 hr)Instructor: A/Prof. Xiao-cong ZHOU1. Introduction to ESE (Empirical Software Engineering) (1 hr)general introduction to the area of empirical study; why empirical study is important in software engineering; how to study this module.2. Empirical Strategies and Measurement in Software Engineering (2 hr)overview of empirical strategies: surveys, case studies and experiments; empirical strategies comparison; empiricism in a software engineering context; basic concepts of measurement; measurement in software engineering.3. Experiment Process: Definition & Planning (3 hr)general introduction to experiment process; experiment definition; experiment planning: context selection, hypothesis formulation, variables selection, selection of subjects, experiment design, instrumentation, validity evaluation.4. Experiment Process: Operation & Analysis (3 hr)experiment operation; analysis and interpretation: descriptive statistics, data set reduction, basic concepts of hypothesis testing; introduction to t-test, Mann-Whitney test, F-test, paired t-test, Wilcoxon test, sign test, ANOVA (analysis of variance), Kruskal-Wallis test.5. An Example of Empirical Study in Software Engineering (3 hr)an example experiment to compare C and C++: problem statement, experiment planning, analysis and interpretation.Totally 51 out of 57 hours.布置作业Assignments None总评成绩计算Course AssessmentClass Participation20% Research Paper 80% 评分标准GradingTotal 100%。
