应许之地(The Promised Land)房屋布局-推荐下载
The control of urban sprawl

The Control of Urban SprawlChris Couch and Jay KarechaThe Past.It can be argued that the improvements in systems urban transportation in the late 19th century led to the first wave of urban sprawl in Britain. The last quarter of that century saw a dramatic fall in the density of new working class housing developments as the introduction of suburban railways, horse-buses and later, trams, permitted the colonisation of large areas of cheap land beyond the urban periphery. However, the dependency upon public transport routes tended to lead to a star-shaped pattern of urban growth that retained some access to the countryside through the ‘green wedges’ that remained between the growth corridors.Control of this urban sprawl was one of the earliest reasons for the introduction of town planning in Great Britain. The Housing, Town Planning Etc, Act 1909, for the first time permitted local authorities to prepare town planning schemes for land beyond the existing urban area that was liable to be developed in the foreseeable future. Although there was no attempt to limit the amount of land to be developed, land use zoning and controls over the density of development gave planners an opportunity to determine and manage the pattern and form of urban growth.By the end of the first world war, new housing policies were introduced to meet an acute housing shortage. The Ministry of Health for the first time subsidised the building of council housing (social housing) from central government funds. Influenced by the ‘Garden Cities Movement’ and the Tudor Walters Report (1918), the Ministry encouraged the building of large low density ‘cottage estates’ on the edge of major cities. Changing economic circumstances also led to a boom in speculative private housebuilding for owner occupation. These estates too comprised sprawling, low density, housing built on green field sites. These twin strands of residential expansion were both supported by and encouraged investment in urban public transport systems, most notably in extensions to the London Underground.By the end of the twenties there was growing concern and opposition to the unprecedented scale and extent of urban sprawl that seemed to be enveloping every city in the country. A new Town and Country Planning Act had been passed in 1932 but with little effect on sprawl. In particular,“there was one aspect of suburban development which caused particular public and political concern in the 1930s building boom. This was the tendency for arterial roads to be subject to ill-considered ribbon development of cheaper housing extending out well beyond the more continuous built-up areas. The practice saved the developers the cost of building proper residential roads, but damaged the scenic quality and undermined the efficiency and safety of main roads by mixing local and through traffic. It was disliked even by many of the right-wing opponents of town and country planning” (Ward, 1994, p48).The Restriction of Ribbon Development Act 1935, gave highway authorities specific powers to prevent this abuse. Nevertheless, neither Act had any significant impact on the total volume of urban sprawl, especially as around one third of the new housing was planned and developed by local authorities themselves and most of the rest was facilitated and controlledby other public policies in some shape or form. Between 1922 and 1939 over 340,000 hectares of rural land were converted to urban uses: a 40% increase in the total urban area of the country (Ward, 1994, p49). It was therefore inevitable that questions would be asked about how sprawl might be controlled and whether its form should be better planned. Supporters of the ‘Garden Cities Movement’ had long argued that urban growth could be accommodated in planned and self-contained satellite towns that would combine ‘the best of town and country’ and avoid the monotony and lack of amenity of ever-sprawling suburbs. Another strand of argument called for the introduction of ‘green belts’ around and between cities to prevent unplanned urban incursions into the countryside and the coalescence of adjoining settlements.In his Greater London Plan of 1944, Patrick Abercrombie put forward proposals for the planning of the capital in four rings: an inner urban ring (the pre-1914 city) which would be subject to urban renewal; a suburban ring (mainly developed between 1919 and 1939) where little change was anticipated; a green belt where virtually all urban development would be prohibited; and an outer country ring where a number of satellite towns were proposed to accommodate London’s need for growth and the overspill caused by the renewal of the inner ring.The New Towns Act 1946, allowed the Government to establish New Town Development Corporations to develop new or satellite towns around London and other major cities as a mechanism for containing urban growth and sprawl within planned settlements. The Town and Country Planning Act 1947, extended the obligation to produce development plans to all local planning authorities in order to plan the use and development of land throughout the country. Land saving, controlling urban expansion and a disdain for suburbia were emerging issues debated by planners during the post-war years. In 1955 Circular 42/55 allowed local planning authorities to formally incorporate ‘green belts’ into statutory development plans, so providing them with greater powers to control and limit urban sprawl than they had ever had before.But urban sprawl continued, partly fuelled by a massive programme slum-clearance in all the major cities. Urban populations fell as cleared areas were rebuilt at lower densities and many cleared households were moved out to new peripheral council estates, expanded towns and new towns. At the same time economic growth combined with low interest rates supported a second boom in speculative building for owner occupation, only this time demand was coming from households who were car-owners and able to consider living at ever greater distances from the urban core and no longer tied to public transport routes. Urban sprawl began to fill the rural gaps in the star-shaped city and create more circular urban forms, divorcing more urban dwellers from easily experiencing the countryside.Throughout the period of the slum clearance programmes, from the 1930s to the 1960s the major cities had been losing population. Until late in the period this reduction in urban density was perceived as beneficial for it was associated with (though not the cause of) improvements in housing conditions and public health. It also provided space for new schools and other amenities. However, between the late 1960s and early 1970s there was to be a sea-change in urban policy. Whereas falling urban densities had been perceived as beneficial, the huge falls in urban populations now being recorded were perceived as problematic, particularly as the local tax base began to decline at the same time as residual (non-migrating, non-sprawling) populations were tending to be disproportionately old, poor and dependent upon local authority services. Local communities were increasingly critical of the slum clearance process and the lack of quality in the replacement housing offered, be it in situ or in overspill locations. At the same time central government was becoming concerned about the costs of slum clearance and seeking cheaper alternatives less demanding upon public expenditure. By 1968 it was also becoming apparent that many inner city areasharboured concentrations of social problems and deprivation. This powerful cocktail of pressures led to the beginnings of a new policy known as urban regeneration. Slum clearance was to be replaced by area improvement and attempts were made to reverse urban decline and tackle deprivation through a series of new managerial and fiscal measures. Thus from this period urban sprawl is not only seen as a problem of inefficient urban growth that detracted from the amenity of the countryside but also as a phenomenon that damaged the inner cities and therefore needed to be brought under yet further control. (It is interesting to note however that echoes of the ‘slum clearance’ type policies have again re-emerged in UK cities (such as Liverpool) where under-populated areas are again being cleared to be replaced with lower density housing under the Housing Market Renewal Initiative.)The urban regeneration approach is typified by Merseyside County Council whose strategy proposed to:“Concentrate investment and development within the urban county and particularly in those areas with the most acute problems, enhancing the environment and encouraging housing and economic expansion on derelict and disused sites. It would restrict development on the edge of the built-up areas to a minimum. There would bea reciprocal effort to enhance and conserve the natural features of the county’s openland and its agriculture while ensuring that its capacity to meet the county’s needs for leisure, recreation and informal education is exploited” (Merseyside County Council, 1975, p8, quoted in Couch, 2003).Such an approach was complemented by central government’s ‘Urban Programme’, which, since 1968 had been an instrument for subsidising public investment in inner urban areas, and the ‘Inner Areas Partnerships’ instigated under the Inner Urban Areas Act 1978. Although critical of the partnership idea, the incoming Conservative Government in 1979 maintained a commitment to urban regeneration that facilitated the re-use of vacant and derelict urban land by means of ‘Enterprise Zones’, ‘Urban Development Corporations’ and ‘Urban Development/City Grant’. This so-called ‘property-led’ approach to urban regeneration saw major successes in the redevelopment of urban land during the 1980s and early 1990s that undoubtedly contributed to a slackening in the rate of urban sprawl. Declining urban populations and a downturn in economic activity, especially in the north of England, also reduced demand for urban expansion.However, the Conservative Government had an ambivalent view of green belts and the release of land for housing development. Initially the government sought to reduce the effectiveness of green belts in order to facilitate more private housing development but so moves were opposed by an alliance of environmentalists and Conservative MPs whose constituencies might the be recipients of unwanted urban sprawl. In 1984 the government settled for housing circulars (9/80 Land for Private Housebuilding and 15/84 Land for Housing) that required local planning authorities to consult with housebuilders to ensure a five-year supply of developable land. This ‘predict and provide’ method of determining the amount of land to be zoned for housing inevitably had the effect of requiring constant additions to the amount of rural land zoned for future urbanisation on the periphery of cities: in other words the circulars encouraged urban sprawl.At this point it is worth noting some characteristics of the relationship between successive governments and the property development industry. It was developers who played a large part in encouraging the government to take seriously the problem of derelict urban land (the waste of a valuable resource). And it was private housebuilders who lobbied to maintain a steady supply of developable rural land. On the other hand, by the mid-1970s, with the exception of London, there was virtually no new private housing investment within existing urban areas of the major conurbations in England and the conventional wisdom of the time suggested that private investment could not be attracted because of a host of socio-economicand environmental factors. Liverpool City Council in 1975 took the unprecedented step of offering for sale housebuilding land in the inner city. They had one bidder: Wimpey, who, paying around £75 per building plot, successfully built and sold a development of more than 150 dwellings. Further developments followed. Also in Liverpool, Barretts successful converted and sold blocks of redundant council flats. Thus began what has now become commonplace: at the right price private developers proved themselves willing and able to invest heavily in the redevelopment and regeneration of inner urban areas.Virtually all British governments since the 1950s, especially those on the right, have been committed to the idea of a ‘property owning democracy’ within which encouraging home ownership (owner occupation) has been an important policy goal. The effect of this has been to increase owner occupation in Great Britain from 29% in 1951 to 70% in 2001. By the millennium more than 80% of all new housing was built speculatively for owner occupation. This has significant implications for the dynamics and control of urban sprawl. Virtually all control of urban sprawl involves the state intervening in the private market, hardly any investment is controlled through the direction of public investment. An essential feature of the private owner occupied housing market is the need to maintain, and preferably increase, property values. In these circumstances land with development potential is ever more valuable, the profits from development higher, and the pressure for development greater. It is this pressure that has to be controlled by the planning system if urban sprawl is to be brought under control.Through much of the 1980s the Thatcher Government pursued a neo-liberal ideology, viewing town and country planning as little more than an unnecessary impediment to private enterprise. However, towards the end of the decade their approach began to change. A combination of an emerging international concern for the environment (The Brundtland Commission had reported in 1987) and in 1988 the Department of the Environment introduced a series of Planning Policy Guidance Notes (PPGs) in order to clarify and strengthen the aims of aims of development plans across the country. An important driver of policy change at this time was the publication of This Common Inheritance (The Environment White Paper (Cabinet Office, 1990) which required a review of all planning policies in light of the conclusions of the Brundtland Report.One of the most important PPGs affecting urban sprawl was PPG3 ‘Housing’. First published in 1988 and slightly modified in 1992 this document pursued the ‘predict and provide’ approach in order to ensure ‘a continuous supply of housing land which addressed market demand’ although in a modest concession to the environmental lobby there was the ‘encouragement of local authorities to make optimum use of brownfield sites’. To be fair to the Government, by the mid-1990s they had stated another, parallel policy goal of increasing the amount of housing to be built on existing urban land, to over 50%.It was the ‘new’ Labour Government, elected in 1997 that moved away from the inevitability of ‘predict and provide’ to a more sophisticated approach to housing land allocations and release known as ‘plan, monitor and manage’. What this meant in practice was that a revised PPG3 ‘Housing’, in 2000, called for a ‘sequential’ approach to the release of housing land in which local authorities should ‘provide sufficient land, giving priority to re-using previously developed land within urban areas, bringing empty homes back into use and converting existing buildings, in preference to the development of Greenfield sites’ (Lowe H, 2003, p18). Figure 1 provides an indication of the growing effectiveness of planning and urban regeneration policies in controlling the sprawl of housing developments beyond existing urban areas. It shows the proportion of new dwellings built on previously developed land rising from around 55% in 1989 to over 60% in 2002.Figure 1. The proportion of new dwellings built on previously developed land.Another dimension of policy that is relevant to the control of urban sprawl is contained in PPG6 ‘Town Centres and Retailing’. Since 1996, PPG6 has required a sequential approach to commercial development whereby: ‘there should be a preference in the first instance for town centres, followed only then by edge-of-centre sites and out-of-centre schemes where these are well served by public transport’ (Mappin G & Allmendinger P, 2000, p194).Figure 2 shows how the growth of out-of-centre retail schemes have gradually been brought under stricter control in recent years.Figure102030405060199519961997199819992000Figure 2. Major Out of Centre Retail and Leisure Applications.A recent evaluation of PPG6 published by the ODPM found retailers and developers are tending to alter ‘their development strategies and store formats to keep them in line with PPG6….One of the clear effects of PPG6 has been to bring about an increase in the number of refusals of applications for out of town development’ (CB Hillier Parker, 2004, p10). It was also found that:“in the comparison retail sector, one of the most marked effects of PPG6 has been toeffectively bring to an end the supply of new regional shopping centres….In the retailwarehouse sector, the evidence suggests that the supply pipeline has fallen, and thereare examples of new edge-of-centre retail warehouse developments, which successfully combine the benefits of this format with a more central location…whilst…In the convenience sector…there is evidence of an increase in openings of town centre stores and neighbourhood stores, and a significant decline inthe pipeline of out-of-centre stores” (C B Hillier Parker, 2004, pp11-12).However, the same research also comments that whilst the policy guidance purports to cover all ‘key town centre uses’, there has been, in practice, a strong emphasis on the planning and control of retail developments, with ‘little or no useful guidance on leisure, offices and other town centre uses’ (ODPM, 2004, p8). The data indicates that the amount and proportion of out of town and out of centre leisure developments increased over the period 1994 – 2001 (ODPM, 2004, p63)A third element of policy guidance, PPG13 ‘Transport’ has sought to:o Promote choice (of mode of transport) by increasing the relative advantage of means of travel other than the car, especially walking, cycling and public transport;o Reducing dependence on the private car; ando Increasing the competitiveness and attractiveness of urban centres against peripheral development (Carr C & Docherty I, 2000, p220)However, it is in the field of transport policy that government policy has been least successful. The provision and quality of transport infrastructure has some causal relationship with urban sprawl. But whilst the laying down of suburban railways and tramways helped shape suburban growth in the late 19th and early 20th centuries, the more recent car-based suburbanisation process has needed no such investment. Instead, in more recent times, it is urban sprawl that has tended to dictate the location of peri-urban highway investment and to a lesser extent, the provision of public transport services. Indeed, the failure to provide adequate opportunities and support for walking, cycling and public transport in the UK, especially in areas of urban sprawl, has led to a continuing growth in the use of the motor vehicle for more and longer journeys, as shown in figure 3.Figure 3. Road Traffic Volumes.Whilst the aims of this policy guidance are laudable, it remains to be seen over time how effective they will be in achieving more sustainable patterns of urban development and reducing urban sprawl. One of the more intractable problems lies with the transport system. Whilst policies may call for a shift in modal split, decades of under-investment in provision for public transport, cycling and walking make significant changes in patterns of travel extremely difficult to achieve.Nevertheless, today, in 2004, the rate at which urban sprawl is occurring in Britain is lower than at almost any time over the last century. This has been achieved by a combination of socio-economic circumstances combined with strong planning controls at the urban fringe and effective subsidies and managerialist interventions to encourage the regeneration of older urban areas.The issue facing policy makers is whether these policies can remain effective into the future and whether they should be strengthened to reduce urban sprawl still further and encourage the type of compact urban development that the Government and the environmental lobby now favour.The FutureThe question now is how can policy be developed to further reduce urban sprawl and to reduce the adverse impacts of such sprawl? Beyond the trite ambitions for more ‘compact cities’, ‘decentralised concentration’, ‘greening the city’ and ‘reducing car-dependency’ there are difficult questions about the precise nature of the policies to be developed, their implementation, effectiveness, side-effects and political acceptability.The following discussion is structured around two issues:• How might urban sprawl be reduced, through policy changes at the national and local levels of planning?• How might the adverse social, economic and environmental consequences of urban sprawl be reduced?The evidence used in the discussion has been derived from:• the findings of the Liverpool/Wirral case studies about the causes and consequences of urban sprawl;• the conclusions of the URBS PANDENS ‘Stakeholder Workshop’ held in Vienna in January 2004.• policy debates in the planning literature;• a survey of expert opinion in North West England1.How might urban sprawl be reduced, through policy changes at the national and local levels of planning?Evidence from the Wirral case study.From our own earlier paper (Couch & Karecha 2003a), based on a study of trends in Wirral MBC, we noted a number of causal influences on urban sprawl, particularly in relation to residential locational choice.Changes in housing costs appeared to be a very significant influence. Firstly, particularly in the inner areas of Wirral and amongst younger householders, being in an area of affordable housing was a frequently cited influence on household locational choice. That is to say lower dwelling prices stimulated their demand. On the other hand, amongst movers to the outer areas of Wirral, ‘trading-up’ was the most frequently cited reason for moving. This would conform with the notion of owner occupied housing as an investment good and suggest that rising dwelling prices affected their locational choice and stimulated demand in the outer areas.Income levels appeared to be significant in that those likely to be on lower incomes (those not in employment and non-car owners) are more influenced in their location decisions by proximity to shopping facilities, railway stations and bus links: features that are more difficult to provide in sprawling locations. On the other hand those likely to be on higher incomes (professionals and managers and 2+ car owners) were slightly more influenced in their location decisions by quietude and proximity to countryside/coast: features more associated with sprawl.Infrastructure investment was an influence on some groups. Movers in all areas and especially the elderly frequently identified good road connections as a very important or crucial influence. The elderly were also frequently influenced by proximity to a railway station and being in an area of good bus services.Age structure clearly had important implications for urban sprawl. The elderly identified many more very important or crucial influences on household location decisions than younger age groups. Household structure was also important. The inner and outer areas exhibited quite different characteristics in terms of household types, with single adults, sharing adult households and single-parent families more represented amongst movers to the inner areas1 It was our intention to survey expert opinion using the Delphi technique. However, despite contacting a number of experts from the private and public sectors, the response rate in the first round of consultation was poor. We therefore modified the process and rather than have a series of successive rounds of consultation in order to move towards consensus on policy, we moved straight to the preparation of our own draft paper and invited expert comment through interviews and correspondence.and adult couples, two-parent families and the single elderly more represented amongst movers to the outer areas.The quality of the environment was an important influence on household location decisions. Being in a low crime neighbourhood and being in a quiet neighbourhood were amongst the most frequently cited influences on location decisions in all areas and across all age groups. In the outer areas and amongst the elderly, proximity to the countryside/coast was another very frequently cited environmental or landscape influence. On the other hand being near a park was of only limited influence on any group.However, within a labour market area, such as Wirral, neither a change in the place of work nor a desire for greater proximity between home and work seemed to be significant causes of household moves or choice of location.These findings suggest that any future policies intended to reduce residential urban sprawl need to:• Tackle perceived levels of crime and lack of quietude and environmental quality in existing urban neighbourhoods;• Improve the profitability to owner-occupiers of home ownership in existing urban neighbourhoods.• Deal with the issue of owner-occupied housing being an investment good and the perception that house prices increase faster in peripheral locations.Evidence from the ‘Stakeholder Workshop’.As part of the workshop activity around 30 stakeholders (expert professional planners and academics from the seven case study areas) were asked to rank 13 possible causes of urban sprawl in terms of their importance. Each individual stakeholder was limited to voting for a maximum of only 4 possible causes. The results are shown in table 1 below.Table 1. Stakeholder ranking of the importance of potential causes of urban sprawl.Causal factor Number of votes achievedPersonal lifestyle choices and behaviour 23Land use planning and property taxation22Dwelling prices and income changes 18Infrastructure investment 17Land speculation 11Economic change 6Inward investment 6Quality of landscape 4Demographic or household changes 4Social segregation 4Migration 1Lack of space in the inner city 1Quality of townscape 0Whilst the exercise might be criticised on a number of grounds (the definitions of some factors are ambiguous; the stakeholders were not randomly selected nor evenly representative of the case study areas), the results are nevertheless interesting.Overall there was an impressively high level of expert agreement about the major factors causing urban sprawl in a variety of different cities across Europe. Personal lifestyle choices and behaviour are perceived to be the most important cause. Coupled with the third mostimportant cause, dwelling prices and income changes, this clearly suggests that there is a strong demand-side dimension to the creation of urban sprawl. To this extent it may be argued that developers are merely responding to the desire of the population to live at certain densities; in certain types of environment; in certain locations; in affordable and, in the case of owner occupation, profitable dwellings.On the other hand there is also expert agreement that the planning system can encourage urban sprawl through land use zoning and providing infrastructure investments such as highways and utility services. Other important factors are thought to be local variations in property taxes and land speculation by potential developers.Thus responding to these arguments, governments wishing to control urban sprawl would need to:• Reduce household demand for urban sprawl, either by satisfying that demand in other locations or changing the nature of that demand;• Strengthen land-use zoning policies against urban sprawl, and/or strengthen the implementation of existing policies;• Re-orientate infrastructure investments away from areas of potential urban sprawl;• Reduce spatial differences in local property tax yields;• Limit the scope for land speculation at or near the urban fringe.Evidence from the survey of expert opinion in North West EnglandRespondents were asked to consider changes in planning policy that would reduce urban sprawl in North West England.At the national/regional scale of planning, the bulk of responses focused on the importance of brownfield development and development within existing urban areas, and the protection (and also the extension) of the greenbelt, as central aspects of policy responses/actions for the reduction of urban sprawl. It was also argued that there was scope for more effective implementation and enforcement of existing land use planning policies that were not being adhered to as strongly as they might be. Other responses discussed the merits of improving the quality of existing urban areas as a measure to stem the demand for and the attractiveness of ‘urban sprawl’ residential locations. There was also some discussion over whether environmental issues could be raised in terms of importance, over and above economic and social matters. One suggestion was that quality residential development could be channelled into land adjacent to rural settlements, with the view being that this could be preferable to sprawling suburbs. A further suggestion was that settlements could be categorised to form a hierarchical list starting with ‘the most preferred settlement for development’, moving to ‘the least preferred settlement’, ordered according to categories such as accessibility.At the metropolitan/city scale of planning, the discussion focused on the challenge of making cities attractive to people other than the young. There was some comment on having very clear and firm boundaries for urban areas set in local plans, and also having more precise and directive details for example on matters such as site capacities. A suggestion was made that by a better integration of (public) transport planning and land use planning, that urban sprawl could be reduced.At the local/neighbourhood scale of planning, there was some debate as to whether urban sprawl could be addressed at this level with some participants believing that it was not possible. Among the suggestions among those who did answer, was the view that the promotion of mixed communities might form part of the solution for reducing urban sprawl, presumably because it was felt that this could create places where the more affluent would。
龙之崛起完全攻略(免费)

<龙之崛起>官方战役攻略龙之崛起原版战役攻略提示:本攻略不包含夏(教学关)部份,且难度均为正常级。
商1:王朝的开端城市:博过关:*一年生产12瓷器*600人住广舍极易的上手关,被它套进来就完蛋了呵呵。
1个泥坑和2个瓷器房就可达成目标。
注意规划土地,第3关还要回来建汤庙和升级住宅区。
商2:渭水之滨城市:宝鸡过关:*4个贸易伙伴*年利润1200不久就会冒出第四个城市,能将铜器全卖出去过关是轻而易举的事,算是让玩家充份了解出口创汇的重要性的一关。
可以不必收税,木材生产和运输都是很麻烦的事,还有那个衙门也费不少人工的。
商3:商王汤的寺庙城市:博过关:*圣地汤庙完成*1000人住美舍*神停留9月第一关建的好这一关就省事了,粮仓的食物要增加到3种。
用瓷器祭神很管用,9个月后就可以送走它了。
汤庙的建设虽然耗时耗力但在众多奇观中算是开胃菜,应趁机熟悉一下。
多半是木工用木材打好模板,劳工运上夯土填平,打好地基再用木工建庙,最后是陶匠用陶土修饰。
以上材料事先准备好可事半功倍。
商4:郑州的城墙城市:郑州过关:*人口1300*20人住普通四合院*1个同盟城第一级的贵族区不需要食物,但是需要美化环境和麻布与瓷器的库存才能建造。
商5:迁都到殷城市:殷过关:*人口1500*40人住高档四合院*一年生产10铜器*1100人住美舍需要认真规划土地,因为最后一关还得回来建圣地。
第二级贵族区和美舍都需要3种食物,所以食物供应最好要盈余。
商6:稻米河谷城市:盘龙城过关:*圣地女娲庙完成*一年生产40稻米*800人住华宅打猎供应怕不稳定的话第3种食物可以靠进口,女娲庙工程不是很大。
商7:妇好之墓城市:殷过关:*圣地妇好墓完成*皇宫有4种动物*80人住简单公馆妇好墓需要劳工挖开土地,摆上陪葬品后还得重新填上,还得建上好几层,挺费时的,在建城时细水长流吧。
招来女娲抓2种动物与周边城市交换就行,与友好无关一定会回礼的。
弄到第四种食物时一定要把其它商店关掉,只留给贵族区食店进货。
Lower Bounds and Impossibility Results for

Lower Bounds and Impossibility Results forConcurrent Self Composition∗Yehuda LindellIBM T.J.Watson Research19Skyline Drive,HawthorneNew York10532,USAlindell@April4,2005AbstractIn the setting of concurrent self composition,a single protocol is executed many times con-currently by a single set of parties.In this paper,we prove lower bounds and impossibility resultsfor secure protocols in this setting.First and foremost,we prove that there exist large classesof functionalities that cannot be securely computed under concurrent self composition,by anyprotocol.We also prove a communication complexity lower bound on protocols that securelycompute a large class of functionalities in this setting.Specifically,we show that any protocolthat computes a functionality from this class and remains secure for m concurrent executions,must have bandwidth of at least m bits.The above results are unconditional and hold for anytype of simulation(i.e.,even for non-black-box simulation).In addition,we prove a severe lowerbound on protocols that are proven secure using black-box simulation.Specifically,we showthat any protocol that computes the blind signature or oblivious transfer functionalities andremains secure for m concurrent executions,where security is proven via black-box simulation,must have at least m rounds of communication.Our results hold for the plain model,where notrusted setup phase is assumed.While proving our impossibility results,we also show that formany functionalities,security under concurrent self composition(where a single secure protocolis run many times)is actually equivalent to the seemingly more stringent requirement of securityunder concurrent general composition(where a secure protocol is run concurrently with otherarbitrary protocols).This observation has significance beyond the impossibility results that arederived by it for concurrent self composition.Keywords:secure computation,protocol composition,self and general composition,impossibility results,lower bounds,non-black-box and black-box simulation.∗This paper combines results that appeared in extended abstracts in[25]and[28].Contents1Introduction1 2Definitions62.1Concurrent Self Composition of Secure Two-Party Protocols (7)2.2Concurrent General Composition of Secure Two-Party Protocols (12)2.3Functionalities With Fixed Versus Interchangeable Roles (14)2.4Functionalities That Enable Bit Transmission (15)3Self Composition Versus General Composition173.1Equivalence for Functionalities That Enable Bit Transmission (17)3.2Equivalence For Functionalities with Interchangeable Roles (20)3.3Separation for Other Functionalities (21)4Impossibility Results for Concurrent Self Composition23 5Communication Complexity Lower Bound245.1The Lower Bound (24)5.2Concurrent General Composition With Independent Inputs (29)6Black-Box Lower Bounds on Round Complexity296.1The Main Result (30)6.2Impossibility For Concurrent Oblivious Transfer (38)6.3Extensions of the Black-Box Lower Bounds (40)References411IntroductionIn the setting of two-party computation,two parties with respective private inputs x and y,wish to jointly compute a functionality f(x,y)=(f1(x,y),f2(x,y)),such that thefirst party receives f1(x,y)and the second party receives f2(x,y).This functionality may be probabilistic,in which case f(x,y)is a random variable.Loosely speaking,the security requirements are that nothing is learned from the protocol other than the output(privacy),and that the output is distributed according to the prescribed functionality(correctness).These security requirements must hold in the face of an adversary who controls one of the parties and can arbitrarily deviate from the protocol instructions(i.e.,in this work we consider malicious,static adversaries).Powerful feasibility results have been shown for this problem,demonstrating that any two-party probabilistic polynomial-time functionality can be securely computed,assuming the existence of trapdoor permutations[36,19]. Security under concurrent composition.The feasibility results of[36,19]relate only to the stand-alone setting,where a single pair of parties run a single execution.A more general(and realistic)setting relates to the case that many protocol executions are run concurrently within a network.Unfortunately,the security of a protocol in the stand-alone setting does not necessarily imply its security under concurrent composition.Therefore,it is important to re-establish the fea-sibility results of the stand-alone setting for the setting of concurrent composition,or alternatively, to demonstrate that this cannot be done.The notion of protocol composition can be interpreted in many ways.A very important distinc-tion to be made relates to the context in which the protocol is executed.This refers to the question of which protocols are run together in the network,or in other words,with which protocols should the protocol in question compose.There are two contexts that have been considered,defining two classes of composition:1.Self composition:A protocol is said to be secure under self composition if it remains securewhen it alone is executed many times in a network.We stress that in this setting,there is only one protocol that is being run many times.This is the type of composition considered, for example,in the entire body of work on concurrent zero-knowledge(e.g.,[11,34]).2.General composition:In this type of composition,many different protocols are run togetherin the network.Furthermore,these protocols may have been designed independently of one another.A protocol is said to maintain security under general composition if its security is maintained even when it is run along with other arbitrary protocols.This is the type of composition that was considered,for example,in the framework of universal composability[5]. We stress a crucial difference between self and general composition.In self composition,the pro-tocol designer has control over everything that is being run in the network.However,in general composition,the other protocols being run may even have been designed maliciously after the secure protocol isfixed.This additional adversarial capability has been shown to yield practical attacks against real protocols[23].1Another distinction that we will make relates to the number of times a secure protocol is run. Typically,a protocol is expected to remain secure for any polynomial number of sessions.This is the“default”notion,and we sometimes refer to it as unbounded concurrency.A more restricted notion,first considered by[1],is that of bounded concurrency.In this case,afixed bound on the 1Although the attacks shown in[23]are due to key reuse,they demonstrate the point that the setting of general composition poses a real security threat.Specifically,[23]show how the adversary can construct new protocols whose entire aim is to compromise the security of existing protocols.1number of concurrent executions is given,and the protocol only needs to remain secure when the number of concurrent executions does not exceed this bound.(When the bound is m,we call this m-bounded concurrency.)We note that the protocol design may depend on this bound.Finally,we will distinguish between a setting where parties havefixed roles versus a setting where they may have interchangeable roles.For the sake of this distinction,note that protocols typically involve different roles.In general,in a two-party protocol,one role may be the protocol initiator while the other is the protocol responder.More notable examples of roles arise in specific cases.For example,in zero-knowledge,there are two different roles:the prover role and the verifier role.Now,in the setting of composition withfixed roles,each party assumes the same role in all of the executions.In contrast,in the setting of composition with interchangeable roles,parties may assume different roles in different executions.The latter setting,of interchangeable roles,is more general and in many cases is what is needed.However,there are some cases wherefixed roles also make sense(for example,when one party is a server and the other a client).Feasibility of secure computation under composition.Thefirst definition and composition theorem for security under concurrent general composition was provided by[31]who considered the case that a secure protocol is executed once concurrently with another arbitrary protocol.2The unbounded case,where a secure protocol can be run any polynomial number of times in an arbitrary network,was then considered in the framework of universal composability[5].Informally speaking, a protocol that is proven secure under the definition of universal composability is guaranteed to remain secure when run any polynomial number of times in the setting of concurrent general com-position.This setting realistically models the security requirements in modern networks.Therefore, the construction of protocols that are secure by this definition is of great importance.On the posi-tive side,it has been shown that in the case of an honest majority,essentially any functionality can be securely computed in this framework[5].Furthermore,even when there is no honest majority,it is possible to securely compute any functionality in the common reference string(CRS)model[9]. (In the CRS model,all parties have access to a common string that is chosen according to some distribution.Thus,this assumes some trusted setup phase.)However,it is desirable to obtain protocols in a setting where no trusted setup phase is assumed.Unfortunately,in the case of no honest majority and no trusted setup,broad impossibility results for universal composability have been demonstrated[6,5,8].Recently,it was shown in[27]that these impossibility results extend to any security definition that guarantees security under concurrent general composition(including the definition of[31]).Thus,it seems that in order to obtain security without an honest majority or a trusted setup phase,we must turn to self composition.Indeed,as afirst positive step,it has been shown that any functionality can be securely computed under m-bounded concurrent self composition[25,30]. Unfortunately,however,these protocols are highly inefficient:The protocol of[25]has many rounds of communication and both the protocols of[25]and[30]have high bandwidth.(That is,in order to obtain security for m executions,the protocol of[25]has more than m rounds and communication complexity of at least mn2.In contrast,the protocol of[30]has only a constant number of rounds, but still suffers from communication complexity of at least mn2.)These works still leave open the following important questions:1.Is it possible to obtain protocols that remain secure under unbounded concurrent self compo-sition,and if yes,for which functionalities?2.Is it possible to obtain highly efficient protocols that remain secure under m-bounded con-2An earlier reference to this problem with general ideas about how to define security appeared in[3,Appendix A].2current self composition?(By highly efficient,we mean that the dependence on the bound m is either additive(e.g.,m+poly(n)or poly(m)+poly(n)),or sublinear(e.g.,mǫ·poly(n)for some small constant0<ǫ<1).3)As we have mentioned,these questions are open for the case that no trusted setup phase is assumed and when there is no honest majority,as in the important two party case.Our results.In this paper,we provide negative answers to the above two questions.More precisely,we show that there exist large classes of functionalities that cannot be securely computed under unbounded concurrent self composition,by any protocol.We also prove a communication complexity lower bound for protocols that are secure under m-bounded concurrent self composition (by communication complexity,we mean the bandwidth or total number of bits sent by the parties during the execution).This is thefirst lower bound of this type,connecting the communication complexity of a protocol with the bound on the number of executions for which it remains secure. We begin with our impossibility result.Theorem1.1(impossibility for unbounded concurrency–informal):There exist large classes of two-party functionalities that cannot be securely computed under unbounded concurrent self compo-sition,by any protocol.In order to prove this result,in Section3we show that for many functionalities,obtaining security under unbounded concurrent self composition is actually equivalent to obtaining security under concurrent general composition(that is,a protocol is secure under one notion if and only if it is secure under the other).This may seem counter-intuitive because in the setting of self composition, the protocol designer has full control over the network.Specifically,the only protocol that is run in the network is the specified secure protocol.In contrast,in the setting of general composition,a protocol must remain secure even when run concurrently with arbitrary other protocols.Further-more,these protocols may be designed maliciously in order to attack the secure protocol.Despite this apparent difference,we show that equivalence actually holds.We now briefly describe how this is proven.The above-described equivalence between concurrent self and general composition is proven for all functionalities that“enable bit transmission”.Loosely speaking,such a functionality can be used by each party to send any arbitrary bit to the other party.In the setting of interchangeable roles(described above),essentially any functionality that depends on the parties’inputs(and so is non-trivial)enables bit transmission.In the setting offixed roles,it is also required that both parties receive non-trivial output;see Section2.4.Now,many executions of a protocol that securely computes a functionality that enables bit transmission can be used by the parties to send arbitrary messages to each other.Essentially, this means that many executions of one secure protocol can be used to emulate the execution of any arbitrary protocol.Thus,the setting of general composition,where a secure protocol runs concurrently with other arbitrary protocols,can be emulated(using the bit transmission property) by many executions of a single secure protocol.We therefore obtain that security under concurrent self composition implies security under concurrent general composition.Since,trivially,security under general composition implies security under self composition,we obtain equivalence between these two notions.We conclude that although general composition considers a very difficult scenario 3Notice that a protocol whose complexity has no dependence on m can be used to achieve unbounded concurrency by setting m=n log n.Therefore,given that unbounded concurrency cannot be achieved,some dependence on m is necessary.3(in which arbitrary network activity must be considered),for many functionalities it is actually equivalent to the seemingly more restricted setting of self composition.That is,we have the following theorem:Theorem1.2(equivalence of self and general composition–informal):Let f be any two-party functionality.Then,in the setting of interchangeable roles,f can be securely computed under unbounded concurrent self composition if and only if it can be securely computed under concurrent general composition.If f is a functionality that enables bit transmission,then equivalence also holds in a setting withfixed roles.As stated in Theorem1.2,in the setting of interchangeable roles,we obtain full equivalence be-tween concurrent self and general composition(without any additional requirement regarding bit transmission).This is the case because when interchangeable roles are allowed,all functionalities are either trivial(to the extent that they can be computed without any interaction)or enable bit transmission.A natural question to ask is whether or not in the setting offixed roles,equivalence also holds for functionalities that do not enable bit transmission.In Section3.3,we show that in the setting offixed roles,there exists a functionality that can be securely computed under concurrent self com-position but cannot be securely computed under concurrent general composition(specifically,this is the zero-knowledge proof of knowledge functionality).Thus,when there is no bit transmission, it can be“easier”to obtain security under self composition than under general composition.Returning back to the proof of Theorem1.1,impossibility is derived by combining the equiv-alence between concurrent self and general composition as stated in Theorem1.2with the im-possibility results for concurrent general composition that were demonstrated in[27].The actual impossibility results obtained are described in Section4.This answers thefirst question above,at least in that it demonstrates impossibility for large classes of functionalities.(It is still far,however, from a full characterization of feasibility.)Regarding the second question,in Section5,we prove the following theorem that rules out the possibility of obtaining“efficient”protocols that remain secure under m-bounded concurrent self composition.Theorem1.3(communication complexity lower bound–informal):There exists a large class of two-party functionalities with the property that any protocol that securely computes a functionality in this class under m-bounded concurrent self composition,must have communication complexity of at least m.Theorem1.3is essentially proven by directly combining the proof of Theorem1.2with proofs of impossibility from[27]and[8];see Section5.We remark that our definition of security under concurrent self composition is such that hon-est parties may choose their inputs adaptively,based on previously obtained outputs.This is a seemingly harder definition to achieve than one where the inputs to all the executions arefixed ahead of time.We stress that allowing the inputs to be chosen adaptively is crucial to the proof of Theorems1.1to1.3.Nevertheless,we believe that this is also the desired definition(since in real settings,outputs from previous executions may indeed influence the inputs of later executions). Black-box lower bound.The above lower bounds and impossibility results are unconditional. That is,they hold without any complexity assumptions and assume nothing about the simulation; in particular it is not assumed that the simulator is“black-box”.4In addition to the above,in 4A black-box simulator uses only oracle access to the real adversary A;see the paragraph that follows Definition1.4Section6,we prove a severe lower bound on the round complexity of protocols that can be proven secure using black-box simulation.This lower bound is proven specifically for the functionalities of blind signatures[10]and1-out-of-2oblivious transfer[33,12].Theorem1.4(black-box lower bound–informal):Any protocol that securely computes the blind signature or oblivious transfer functionalities under m-bounded concurrent self composition,and can be proven using black-box simulation,must have more than m rounds of communication. Black-box lower bounds do not imply infeasibility in general.In fact,constant-round protocols for m-bounded concurrent self composition have been demonstrated[30].Nevertheless,Theorem1.4 shows that any such protocol must use non-black-box simulation techniques.Note also that all known highly efficient protocols are proven via black-box simulation;therefore,Theorem1.4may indicate a certain difficulty in obtaining very efficient protocols in this setting.The idea behind the proof of Theorem1.4is to show that when concurrent self composition is considered,the“rewinding capability”of the simulator is severely limited.In fact,for a protocol of m rounds that is run m times concurrently,there exists a scheduling of messages so that in one of the executions,the simulator is unable to carry out any rewinding of the adversary.However, informally speaking,a black-box simulator must rewind in order to successfully simulate.Therefore, any protocol that remains secure for m concurrent executions must have more than m rounds of communication.Theorem1.4stands in stark contrast with concurrent zero-knowledge,where black-box sim-ulation does suffice for obtaining unbounded concurrent composition[34].In fact,a logarithmic number of rounds suffice for obtaining security for any polynomial number of executions[32].Thus, in the“black-box world”and in the setting of concurrent self composition,zero-knowledge is strictly easier to achieve than blind signatures and oblivious transfer.We remark that Theorems1.1,1.3and1.4hold even if at any given time,at most two executions are running simultaneously.(Loosely speaking,in such a case the m-bounded concurrency means that m different protocol executions may overlap.)This shows that our lower bounds do not stem from deep protocol nesting(in contrast to[7],for example).Indeed,a nesting depth of at most two is needed.Extensions to multi-party computation.We note that although Theorems1.1and1.3are stated for two-party functionalities,they immediately imply impossibility results for multi-party functionalities as well.This is because secure protocols for multi-party functionalities can be used to solve two-party tasks as well.Likewise,by appropriately defining“bit transmission”for multi-party functionalities,it is possible to prove Theorem1.2for this setting as well.A new result for concurrent general composition.While proving Theorem1.3,we also obtain a new impossibility result for concurrent general composition.Specifically,we show that even if the inputs used by an honest party in a secure protocol are independent of the inputs used in the other arbitrary protocols,then impossibility still holds.See Section5.2for more details. (Interestingly,as shown in[14]and discussed in Section6.2,oblivious transfer under concurrent self composition and withfixed roles can be achieved in the case that all inputs are independently chosen.This does not contradict the above result for general composition because oblivious transfer does not enable bit transmission.Therefore,the equivalence between self and general composition of Theorem1.2does not hold.)Other related work.The focus of this work is the ability to obtain secure protocols for solving general tasks.However,security under concurrent composition has also been studied for specific5tasks of interest.Indeed,the study of security under concurrent composition was initiated in the context of concurrent zero knowledge[13,11],where a prover runs many copies of a protocol with many verifiers.Thus,concurrent zero-knowledge is cast in the setting of concurrent self composition.This problem has received much attention;see[34,7,1]for just a few examples. Other specific problems have also been considered,but are not directly related to this paper. One work that requires mentioning is the(black-box)protocol for unbounded concurrent oblivious transfer of[14].This construction seems to be in direct contradiction to Theorem1.4.However, in the model of[14],all the inputs in all the executions are assumed to be independent of each other.In contrast,we consider a more standard model where quantification is over all inputs,and in particular,over possibly correlated inputs.Open questions.As we have mentioned,the constant-round protocol of[30]has very high communication complexity.Specifically,the number of bits sent in the protocol isΩ(m(n2+|Π|)), whereΠis a protocol that remains secure under concurrent self composition when given access to an ideal zero-knowledge functionality.Thus,the factor of m is multiplicative in the communication complexity.In contrast,Theorem1.3only shows that a linear dependence on m(or an additive factor)is necessary.This gap is very significant because a bandwidth of m+|Π|may be acceptable in practice,in contrast to the very high communication complexity of the protocol of[30].Another interesting question relates to the feasibility of obtaining security under concurrent self composition and withfixed roles,for functionalities that do not enable bit transmission.As we have mentioned,the zero-knowledge functionality does not enable bit transmission and can be securely computed under concurrent self composition.However,it is not known which other functionalities can also be securely computed.The oblivious transfer functionality would be of specific interest here;both because of its importance as a cryptographic primitive,and because by Theorem1.4,it cannot be securely computed using black-box simulation.Thus,the question remains whether or not non-black-box simulation can be used to achieve oblivious transfer under unbounded concurrent self composition.2DefinitionsIn this section,we present definitions of security under concurrent self composition and concur-rent general composition.In addition,we define functionalities with“interchangeable roles”and functionalities that“enable bit transmission”.Our definitions are presented for the special case of two-party protocols.The extension to the multi-party case is straightforward.Preliminaries.We denote the security parameter by n.A functionµ(·)is negligible in n(or just negligible)if for every polynomial p(·)there exists a value N such that for all n>N it holds thatµ(n)<1/p(n).Let X={X(n,a)}n∈N,a∈{0,1}∗and Y={Y(n,a)}n∈N,a∈{0,1}∗be distribution ensembles.Then,we say that X and Y are computationally indistinguishable,denoted X c≡Y,if for every probabilistic polynomial-time distinguisher D there exists a functionµ(·)that is negligible in n,such that for every a∈{0,1}∗,|Pr[D(X(n,a))=1]−Pr[D(Y(n,a))=1]|<µ(n)When X and Y are equivalent distributions,we write X≡Y.We adopt a convention whereby a machine is said to run in polynomial-time if its number of steps is polynomial in the security parameter,irrespective of the length of its input.(Formally,each machine has a security-parameter tape upon which1n is written.The machine is then polynomial in the contents of this tape.)62.1Concurrent Self Composition of Secure Two-Party ProtocolsWe begin by presenting the definition for security under concurrent self composition.The basic description and definition of secure computation follows[20,2,29,4].Two-party computation.A two-party protocol problem is cast by specifying a random process that maps pairs of inputs to pairs of outputs(one for each party).5We refer to such a process as a functionality and denote it f:{0,1}∗×{0,1}∗→{0,1}∗×{0,1}∗,where f=(f1,f2).That is,for every pair of inputs(x,y),the output-pair is a random variable(f1(x,y),f2(x,y))ranging over pairs of strings.Thefirst party(with input x)wishes to obtain f1(x,y)and the second party(with input y)wishes to obtain f2(x,y).We often denote such a functionality by(x,y)→(f1(x,y),f2(x,y)).Thus,for example,the zero-knowledge proof of knowledge functionality for a relation R is denoted by((x,w),λ)→(λ,(x,R(x,w))).In the context of concurrent composition, each party actually uses many inputs(one for each execution),and these may be chosen adaptively based on previous outputs.We consider both concurrent self composition(where the number of executions is unbounded)and m-bounded concurrent self composition(where the number of simultaneously concurrent executions is a priori bounded by m and the protocol design can depend on this bound).Adversarial behavior.In this work we consider a malicious,static adversary that runs in polynomial time(recall that this means that it is polynomial in the security parameter,irrespective of the length of its input).Such an adversary controls one of the parties(who is called corrupted) and may then interact with the honest party while arbitrarily deviating from the specified protocol. Our definition does not guarantee any fairness.That is,the adversary always receives its own output and can then decide when(if at all)the honest party will receive its output.The scheduling of message delivery is decided by the adversary.Security of protocols(informal).The security of a protocol is analyzed by comparing what an adversary can do in the protocol to what it can do in an ideal scenario that is clearly secure.This is formalized by considering an ideal computation involving an incorruptible trusted third party to whom the parties send their inputs.The trusted party computes the functionality on the inputs and sends each party its designated output.Unlike in the stand-alone model,here the trusted party computes the functionality many times,each time upon different inputs.Loosely speaking, a protocol is secure if any adversary interacting in the real protocol(where no trusted third party exists)can do no more harm than if it was involved in the above-described ideal computation. Concurrent executions in the ideal model.An ideal execution with an adversary who controls P2proceeds as follows(when the adversary controls P1the roles are simply reversed):Inputs:Party P1and P2’s inputs are respectively determined by probabilistic polynomial-time Turing machines M1and M2,and initial inputs x and y to these machines.As we will see below,these Turing machines determine the values that the parties use as inputs in the protocol executions.These input values are computed from the initial input,the current session number and outputs that were obtained from executions that have already concluded.Note that the number of previous outputs ranges from zero(for the case that no previous outputs have yet been obtained)to some polynomial in n that depends on the number of sessions initiated by the adversary.65Thus,our specific definition is for“secure function evaluation”only.However,it can be generalized to reactive functionalities in a straightforward way.6Notice that we place no restriction on the lengths of the input values output by M1and M2.It is known that7。
源于《出埃及记》的8个词组(中英双语)

源于《出埃及记》的8个词组(中英双语)长期以来,⼀直有着改编⾃《圣经》和基督教⼿稿的电影,如《出埃及记》、《耶稣受难记》、《摩西⼗诫》,甚⾄是不太相关的《蒙提·派森之布莱恩的⼀⽣》也取材于此。
2013年,我们测试了读者对圣经(及莎⼠⽐亚)的了解程度,看⼤家是否能够辨识出有哪些⽇常表达是源于圣经或莎⼠⽐亚的。
《出埃及记》(the Book of Exodus)(旧约全书第⼆部,第⼀部为创世纪)本⾝就蕴含着丰富的语料,那就让我们看看出⾃英⽂版《出埃及记》的⽤词和短语吧。
Exodus 成群迁徙While the earliest known examples of Exodus in English have a capitalized initial letter and refer to Christian and Jewish Scripture, the word comes from the Greek exodus, from ex- ‘out of’+ hodos ‘way’. This refers to the departure of the Israelites from Egypt, led by Moses, and isalso applied more widely (as exodus) to any mass departure of people.现在已知最早出⾃英⽂版《出埃及记》的⼀个词就是 Exodus,⾸字母⼤写,指代基督徒和犹太⼈的词,这个词源于希腊语 exodus,由 ex-“...之外”+ hodos“路”组成。
这个词是说以⾊列⼈在摩西的带领下离开埃及,还可以更⼴泛地⽤于⼤批⼈⼝的迁徙。
Bricks without straw ⽆⽶之炊Before the Israelites were led out of Egypt, one of their mistreatments (while in slavery) was being forced to make bricks without straw (Exodus 5). This has led to the proverb ‘you can’t make bricks without straw’ – meaning that nothing can be accomplished without proper or adequate material or information. This is actually based on a misinterpretation of the chapter, where in Pharaoh commands the Israelites togather their own straw, rather than to make bricks without using any.以⾊列⼈离开埃及之前,其中⼀名奴⾪(当时正值奴⾪时代)被强迫在没有稻草的情况下制作砖头(在《出埃及记》第五章)。
法老王攻略

前王朝时期Pre-dynastic Period任务场景1.1:努步Nubt \ Naqada新的村庄诞生了场景目标:6简单木屋(6 Meager Shanties)建立一个住宅区,就可看到移民迁入初始金钱:非常简单5000,简单、一般、困难2500,非常困难1875入口出口:下方入,上方出任务提示:如同游戏《凯撒III》一样,游戏开头的第一个任务都非常简单,其目的在于使玩家有一个熟悉游戏的过程。
在道路旁放置一些房子并在房子附近安排好水井,水井必须建在草地上,有效范围是周围2格(包括斜的方向)。
放置地基时,最好是4个挨一起形成2*2的一组,建7、8组就够了。
等移民迁进来后,每一组会变成一个2*2大小的整体坚固小屋(可以住28人。
如果是1*1大小的,可以住7人;如果不建水井,则是简陋小屋,每个1*1大小的可以住5人,2*2大小的可以住20人),每组中间最好空2格,尤其是要留出一个2*2大小的草地位置,以便以后建供水站,有了供水站,水井就不需要了(所以开始时可以不建水井)。
随后耐心地等到居民人口达到150 。
等出现农业和商业后,在离居民区稍远一点的路边建造一个猎人小屋(hunting lodge)、一个谷仓(granary)和一个市场(bazaar),猎人们会猎杀驼鸟加工成食物放入谷仓,再通过集市向居民们分发,有了供水站提供的干净饮水和市场分发的食物之后,居民的简陋小屋就会升级到简单木屋了。
一般游戏开始6、7个月后,城市会发生火灾,建一个消防站就可以了。
如果时间再长的话,可能会出现房屋倒塌,就需要建一个建筑师事务所了。
提示:1.为了防止行人乱跑,可以把村庄通往外界的道路铲断。
2.猎人小屋、谷仓有负影响,所以要离住宅稍远一点。
任务场景1.2:希尼斯(Thinis)文明的破晓场景目标:10座普通农舍(10 Ordinary Cottages)开采金矿,充实宫殿的财库初始金钱:非常简单6000,简单、一般、困难3000,非常困难2250入口出口:下方入,上方出任务提示:与上一个任务相比,本任务稍有些难度。
埃及王子_The_Prince_of_Egypt_中英文剧本

埃及王子 The Prince of Egypt[ Male Chorus ] Mud 泥浆Sand 沙子- Water - [ Yells ] 水Straw -稻草Faster -快点儿- Mud, and lift - [ Groans ] 泥浆,提上来Sand, and pull 沙子,使劲拉Water, and raise up 水,抬上来- Straw - Faster ! -稻草…… -快点儿!With the sting of the whip - On my shoulder - Aah !我的肩膀受到鞭挞With the salt of my sweat On my brow我的脸上流着咸汗Elohim, God on high啊,天上的神灵Can You hear Your people cry您可听到子民的哀嚎Help us now This dark hour帮帮我们在这黑暗的时刻Deliver us拯救我们Hear our call Deliver us听我们的呼喊,拯救我们Lord of all remember us万物之主,别忘了我们Here in this burning sand在火热的沙滩上挣扎Deliver us解救我们There's a land You promised us您曾应许我们一块土地Deliver us to the Promised Land将我们解救到您所应许之地[ Men Shouting ln Distance ]Yal-di ha-tov veh ha-rachAl ti-ra veh al tif-cha-dMy son l have nothing l can give孩子,我不能给你什么But this chance that you may live只能给你活下去的机会l pray we'll meet again我祈祷我们能再见面- lf He will deliver us - [ Men ] Deliver us希望他将解救我们- Hear our prayer - Ohh ! - [ Woman Vocalizing ] - Deliver us from despair 听我们祈祷,将我们从绝望中解救出来These years of slavery Grow too cruel to stand多年来的奴役我们已忍无可忍Deliver us拯救我们There's a land You promised us您曾应许我们一块土地Deliver us Out of bondage解开枷锁解救我们And Deliver us并引导我们[ Baby Coos ][ Whining ]Hush now, my baby别出声,我的宝贝儿Be still, love Don't cry静静地,心爱的,不要哭Sleep as you're rocked By the stream让小河摇你入睡Sleep and remember沉睡吧,但要记住My last lullaby我最后唱的摇篮曲So l'll be with you When you dream 当你进入梦乡时我将陪你左右[ Yawns ]River, oh, river尼罗河,啊,尼罗河Flow gently for me为我缓缓而流Such precious cargo You bear载着我的心肝宝贝Do you know somewhere你知道在什么地方He can live free他才能自由自在地生活?River大河Deliver him there请把他带到那里[ Mother Vocalizing ][ Vocalizing Continues ][ Chittering ][ Roaring ][ Gasps ][ Chorus Vocalizing ][ Gasps ][ Birds Squawking ][ Gasps ][ Gasps ][ Cooing ]Brother You're safe now and safe may you stay兄弟,你现在安全了祝你永远平安For l have a prayer just for you我特意为你祷告Grow, baby brother好好长大,小弟弟- Come back someday - Mmm. 有一天回到这里Come and deliver us too回来也解救我们Mommy ! 妈咪!Come, Rameses. We will show Pharaoh your new baby brother--来,兰姆西斯,我们带你的新弟弟去见法老- [ Coos ] - Moses. 摩西斯[ Chorus ] Deliver us拯救我们Send a shepherd to shepherd us And deliver us 派一名牧羊人来带领我们Deliver us带领我们To the Promised Land到应许之地[ Moses' Mother ] Deliver us拯救我们[ Fast Hoofbeats Approaching ]- Ha, ha ! - Faster, you beasts ! You run like mules.快点儿,畜生!你们像驴子一样慢!- Hey, Rameses, how'd you like your face carved on a wall ? - Someday, yes. 兰姆西斯,把你的脸,刻在墙上怎么样?有一天会的How about now ? [ Groans ] 现在如何?[ Grunts, Yells ] You almost killed me ! 你差点害死我!Oh, come on. Where's your sense of fun ? 你看,你历险的精神哪去了?- Oh, it's fun you want ? - [ Horses Whinny ] 啊,你要冒险?- Whoa ! - [ Horses Whinnying ][ Rameses Laughs, Yelling ]Whoa ! Aah !Ohh. Moses ? 摩西斯?Whoa ! [ Laughing ]Whoa ! [ Continues Laughing ][ Men ] Whoa !Come on, you. Whoa !Come on, Moses. Admit it. You've always looked up to me.承认吧,你一直都在向我看齐Yes, but it's not much of a view. 没错,不过没什么看头[ Laughs ] Hyah ! Whoo !- [ Horses Whinny ] - Hey !-[ Rameses ] Second born, second place. -Not for long.次子永远是第二名!马上就会改变的[ Both Whooping ][ All Chanting ]Whoa !- Whoa ! - Aah ! Aaah !Jump ! 跳![ Both Yelling ][ Both Panting ]- [ Both Laughing ] - [ Rumbling ][ Both ] Whoa ![ Screaming, Grunting ][ Both Hooting, Whooping ]Whoo ![ Rameses ] You don't think we'll get in trouble for this, do you ?我们闯了祸不会受到惩罚吧?[ Moses ] No, not a chance. 当然不会!with such reckless, destructive, - blasphemous sons ?神明为什么派这么两个轻浮莽撞的儿子来折磨我?- Father, hear what l-- -父王,请听我……Be still ! Pharaoh speaks. -闭嘴,法老在说话l seek to build an empire, 我要建立一个帝国and your only thought is to amuse yourselves... by tearing it down.而你们只想搞破坏使自己高兴Have l taught you nothing ? 我白教你们了吗?You mustn't be so hard on yourself, Your Majesty. You're an excellent teacher. 别太自责,陛下lt's not your fault your sons learned nothing. 他们不学乖并非您的错- They learned blasphemy. - True. -他们学会了亵渎神明 -是这样Father, the fault is mine. 父王,这是我的错l goaded Rameses on, and so l am responsible. 是我煽动了兰姆西斯,我要负责Hmm. Responsible. 嗯,“负责”Do you know the meaning of that word, Rameses ? 你明白这字的意思,兰姆西斯?l understand, Father. 我明白,父王And do you understand the task for which your birth has destined you ?你知道你与生俱来的使命吗?The ancient traditions. 古老的传统When l pass into the next world, 等我到了另一个世界then you will be the morning and evening star. 你将成为日月星辰之王One damaged temple does not destroy centuries of tradition.一座倒塌的神庙,不能毁掉我们的传统But one weak link can break the chain... of a mighty dynasty !脆弱的一环,却能毁掉整个王朝[ Disgusted Sigh ]You have my leave to go. 你可以退下了Father. 父王Father ? 父王?You know it was really my fault. 您知道其实是我的错Must you be so hard on him ? 您一定要如此严厉地对他吗?Moses, you will never have to carry a burden...摩西斯,你不必背负那样的重担like the crown l will pass to Rameses. 我要传位给兰姆西斯He must not allow himself to be led astray, 他不能让别人领入歧途not even by you, my son. 连你也不行,儿子All he cares about is-- is your approval. 他只想要得到您的肯定……l know he will live up to your expectations. 他绝对不会辜负您的期望He only needs the opportunity. 您要给他一个机会Maybe. Maybe so. 也许吧,也许是吧Go now. l shall see you both tonight. 退下吧,今晚再见你俩[ Whistling ]- Well, that went well. - [ Rameses ] Just go away. -还算不错 -走开Could have been worse. 可能会更糟''The weak link in the chain.'' That's what he called me.他说我是脆弱的一环[ Sighs ]Well, you are rather pathetic. 嗯,你是挺可悲的lrresponsible, ignorant of the traditions. 不负责任、幼稚无知He practically accused me of bringing down the dynasty.他只差没说我毁了整个王朝Yeah, l can see it now. There go the pyramids ! 是啊,我看金字塔会被你弄垮- [ Chuckling ] - You can laugh about it. 你尽管笑吧Statues cracking and toppling over. The Nile drying up.雕像崩裂倒塌、尼罗河干枯Single-handedly, you will manage to bring the greatest kingdom on Earth to ruin. 你一个人把世上最伟大的王朝搞垮Tell me this, Moses. Why is it that every time you start something,告诉我,摩西斯,为什么你每次胡闹l'm the one who ends up in trouble ? 到头来都是我倒霉?- [ Loud Splash ] - Ah, man ! Oh. -啊,伙计- Ah, it's Rameses. You're in trouble. - Get down here !-兰姆西斯,你闯祸了给我们下来- l think you owe us an apology. - Oh, my new thing !!你得向我们道歉-我的新衣裳!- l am so upset ! - You might as well.-我很生气一不做,二不休- You'll pay for this. - We're gonna tell the Pharaoh !我们要告诉法老!- Hmm. - [ Both Chattering, Exclaiming ]- Oh, look at me. l'm drenched again. 啊,瞧,我又湿透了!- Hey. l figured it out. - You know what your problem is, Rameses ?我弄明白了,兰姆西斯,你知道你的毛病在哪儿?- What ? - You care too much.-什么? -你担心得太多- And your problem is, you don't care at all. 而你却什么都不在乎Oh, in that case, l suppose you care a lot more than l do...你担心的事一定比我多……that we're late for the banquet, for example. 譬如我们赴宴要迟到了[ Panting ] l'm done for. - Father will kill me. 完了!父王会宰了我- Don't worry. Nobody will even notice us coming in.别担心,我们进去时,不会有人注意的[ Crowd Cheering ]''Nobody will even notice.'' “不会有人注意”?[ Laughs, Groans ]Ah, the young princes. 啊,两位年轻的王子Rameses, you were just named prince regent. 兰姆西斯,你刚被命为摄政王You are now responsible for overseeing all the temples.你现在负责监管所有的神庙l suggest you get over there... 我建议你过去……and thank your father. 谢谢你的父王- [ Cheering Continues ] - Apparently, Moses, someone thought he... just needed the opportunity.很明显,摩西斯,有人觉得他……需要这个机会- [ Cheering Continues ] - My lord Pharaoh. 伟大的法老l propose that the high priests offer tribute... to their new regent.我提议请祭司为摄政王献礼[ Pharaoh ] An excellent idea. Hotep ! Huy ! 好主意,荷泰!休伊!- Huy. - Hmm ? -休伊 -嗯?- The Midian girl. - That's a good idea ! -那个米甸女孩 -好主意!Go get her. 把她带来By the power of Ra, 借太阳神的力量we present for your delectation and delight... 我们为您的欢乐和幸福献上an exotic apparition stolen from a faraway land. 来自远方的异国美女[ Crowd Gasps ][ Angry Grunt ]- [ Applause ] - [ Moses Gasps ]- We offer you this delicate desert flower. - [ Camel Grunts ]一朵娇嫩的沙漠之花- [ Screams ] - [ Crowd Chuckling ][ Grunting ]Let us inspect this... desert flower. 让我看看……这朵沙漠之花- [ Crowd Gasping, Laughing ] - More like a desert cobra.更像一条沙漠眼镜蛇![ Laughing ] Not much of a snake charmer, are you ? 你可不是个会耍蛇的人That's why l give her to you. 所以我把她……送给你- No, that's generous, but-- - l won't be given to anyone.-不,你太慷慨了,但…… -我不属于任何人Especially an arrogant, pampered palace brat ! 尤其是一个骄纵无礼的王子! [ Chuckling ] Are you going to let her talk to you like that ?你就让她这样对你说话?You will show the proper respect for a prince of Egypt.你要对埃及王子尊重点儿But l am showing you all the respect you deserve-- none !你只配得到这个,不配得到尊重- [ Gasping ] - No. Wait ! 不,等等- Be still. - Untie this rope ! -别乱动 -把绳子松开!- l demand you set me free ! - Be still. -放我走 -别动!- Let go ! - As you wish. -放手! -就听你的Aah ! Ohh ![ Crowd Laughing ][ Laughing ] You there ! 你!Have her dried off... and sent to Prince Moses' chambers.给她擦干身子……把她送到摩西斯王子的寝室lf it pleases you, Father, my first act as regent...如果您允许的话,父王,我的第一个行动是……is to appoint Moses... 任命摩西斯……as royal chief... 担任皇家……architect. 建筑大臣[ Crowd Cheering ][ Sighs ][ Mutters ] Well--嗯……好吧[ Clears Throat ] Right.[ lnhales ]- [ Gasps ] - [ Muffled Speaking ][ Muffled Whining ][ Gasps ][ Camel Groaning ]Shh. Come on. 快![ Men Chattering Quietly ]Guards. 卫兵![ Both ] Prince Moses. 摩西斯王子!Uh...there's a-a man tied up in my room. 有人被绑在我的寝室里- Well, look into it. - [ Both ] Right away, sire.-快去查看! -马上去,殿下[ Chuckles ][ Midian Girl ] Please, l need water. - l have a long journey ahead of me. 请给我水,我要长途跋涉- May God protect you. Thank you.-愿上帝保佑你 -谢谢你Hut-hut. 驾,驾!- [ Clattering ] - Oh. Oh, l'm sorry. l'm so sorry. l--对不起,对不起,我……- Oh, please forgive me. l-- - [ Chuckles ] 啊,请原谅我,我……l didn't expect to see... you... 我没想到会在……这里碰到你here, of all places, at-at-at our door. 在我们家门口……- Mmm, at last ! - [ Chuckles ] At last ? -嗯,终于见面了! -终于?Didn't l tell you, Aaron ? l knew he would return to us when he was ready. 我说过他一定会回来的,亚伦Miriam, do you want us flogged ? l knew you cared about our freedom.-米利安…… -我知道你关心我们的自由- Miriam ! - Freedom ? Why would l care about that ?自由?我为何要关心自由?Because you're-- well, you're our brother. 因为你是……我们的兄弟- What ? - Be-- -什么? -是[ Sighs ]- They never told you ? - Who never told me what ?他们从来没告诉过你?谁没告诉我什么?But you're here. You must know. 但你来了,你一定得知道- Be careful, slave ! - Oh, my good prince. -别碰我,奴隶! -啊,我的王子Um, she's-she's exhausted from the day's work. 她今天一定累坏了Uh, not that it was too much. We-- We quite enjoyed it.活儿并不多,我们很喜欢干But-But she's confused and knows not to whom she speaks.她糊涂了,不知道在跟谁说话l know to whom l speak, Aaron. l know who you are.我当然知道,亚伦,也知道你是谁- You are not a prince of Egypt. - Miriam. -你不是埃及王子 -米利安!- What did you say ? - Your Highness, pay her no heed.-你在说什么? -殿下,别理她C-Come, Miriam. May l discuss something with you ?来,米利安我可以跟你谈谈吗?No, Aaron. No ! Please, Moses, you must believe ! - That's enough. - You were born of my mother, Yocheved.摩西斯,你要相信我!你是我妈妈约基别之子- Stop it. - You are our brother ! -别说了 -你是我们的兄弟!Now you go too far. You shall be punished. 你太过分了,我要惩罚你No ! Please, uh, Your Highness. 不,求求您,殿下She's ill. She's very ill. We beg your forgiveness.她病得很重,请你原谅她- Please, Miriam, let us go. - No, Aaron. -米利安,走吧 -不,亚伦Our mother set you adrift in a basket to save your life !母亲为了救你,把你放在篮子中漂走Save my life ? From who ? 救我?谁想害我?Ask the man that you call ''Father.''去问问你称之为父王的人吧- How dare you ? - God saved you to be our deliverer.-大胆 -神要你当我们的救世主- Enough of this. - And you are, Moses. You are the deliverer.-别再说了 -摩西斯,你就是救世主- l said, enough ! - [ Moans ] 我说,够了!You will regret this night. 今晚你会后悔的[ Groans, Pants ]Hush now, my baby别出声,我的宝贝儿Be still, love Don't cry静静的,心爱的,不要哭Sleep as you're rocked By the stream让小河摇你进入梦境Sleep and remember沉睡吧,但要记住My last lullaby我最后唱的摇篮曲So l'll be with you When you dream当你进入梦乡时我将伴你左右[ Both Grunt ]-[ Gasping ] -[ Man ] Did you see him ? lt's Moses.你看到了吗?摩西斯王子![ Panting ][ Moses ] Gleaming in the moonlight [ Panting ] 在月光下闪烁的王宫Cool and clean and all l've ever known我所熟悉凉快、干净的地方All l ever wanted我别无所求Sweet perfumes of incense散发着香气的沉香And graceful rooms of alabaster stone由雪花岩砌成的房间All l ever wanted这就是我的需求This is my home这就是我的家With my father mother, brother我的父亲、母亲和兄弟Oh, so noble Oh, so strong啊,多么高贵,多么强大Now l am home现在我回到家中Here among my trappings and belongings身边尽是熟悉的服饰和东西l belong我属于这里- And if anybody doubts it - [ Whimpering ] 如果有人怀疑They couldn't be more wrong他们将大错特错l am a sovereign prince of Egypt我是正宗的埃及王子A son of the proud history that's shown Etched on every wall 是雕刻在每一面墙上光荣历史王朝的儿子Surely this is all l ever wanted这就是我所要得到的All l ever wanted我所要得到的All l ever Wanted我这一生别无所求[ Breathing Deeply ]- [ Screaming ] - [ Gasps ][ Baby Crying ][ Woman Humming Lullaby ][ Gasps, Panting ][ Gasps ]The Hebrews grew too numerous. 希伯来人越来越多They might have risen against us. 他们可能会群起反抗Father, tell me you didn't do this. 父王,告诉我您没下令Moses, 摩西斯……sometimes, for the greater good, sacrifices must be made.有时候为了多数人的利益不得不牺牲少数人[ Panting ]Sacrifices ? 牺牲?Oh, my son. 啊,我的儿子They were only slaves. 他们只是奴隶Moses ? 摩西斯?ls this where you found me ? 你就是在这里发现我的?Moses, please try to understand. 摩西斯,你要理解So-- So everything l thought, 难道说……我一切的信念everything l am, is a lie. 有关我的一切……全都是谎言?No. 不You are our son, and we love you. 你是我们的儿子,我们爱你Why did you choose me ? 你们为什么选上我?We didn't, Moses. 不是我们,摩西斯The gods did. 是神明的选择This is your home my son这里就是你的家,孩子Here the river brought you大河把你带到这里And it's here the river meant 这是大河的旨意To be your home这里就是你的家Now you know the truth, love既然你已知道了真相Now forget and be content忘了它,高高兴兴When the gods send you a blessing当神明为你祝福时You don't ask why it was sent不要问是为什么[ Sighs ]Last night, the gods granted me a vision. 昨晚神明带给我一个启示l'm not merely going to restore this temple, l will make it more grand, 我不仅要把这座神殿修好,还要让它更宏伟more splendid than any other one in Egypt. 比埃及任何的神庙都壮观[ Grunts, Moaning ][ All Groaning ][ Grunts ] Aah.- Get up ! - Aah ![ Sighs ]Moses ! Look. 摩西斯,瞧……Fate has turned our little misadventure into a great opportunity.命运把我们小小的错误,转变成一个良机- [ Guard ] Get up, old man ! - Father will be so pleased---起来,老头! -父王一定会高兴的……Put your back into it ! 加把劲儿!Faster ! 快一点儿![ Rameses ] This is just the beginning. 这只是个开端A gateway will open to an entire new city of white limestone,要盖一座石灰岩城市more dazzling than the sun. 比太阳还要灿烂耀眼- And here, a statue of Hapi. - [ Whip Cracks ] 这里放哈比的雕像……l said, hurry ! 快!- ...two great column halls. - [ Miriam ] Stop it ! -两列圆柱大厅 -停下- Somebody's got to stop this ! - There's nothing we can do.-一定要阻止他! -我们没办法[ Man Screaming ][ Quietly ] Stop it.- [ Louder ] Stop. Stop it ! - [ Whip Cracks ] 住手,住手!- Leave that man alone ! - Moses ! 别再打他了!Out of my way. Out of my way. Move ! 给我让开,让开!Who did this ? 这是谁干的?[ Man ] Up there ! lt's him. Up there. 他在上面,就是他!在上面[ Panting ][ All Gasping ]Moses !Moses, what's going on ? Moses ! 摩西斯,怎么回事,摩西斯?Moses !- Moses ! - Let me go ! -让我走!- No, wait. - You saw what happened. l just killed a man.-等等!你看到了,我刚杀了个人We can take care of that. 我们可以解决这个问题l will make it so it never happened. 我会让大家忘掉这件事Nothing you can say can change what l've done. 你怎么说都改变不了事实l am Egypt, the morning and the evening star. 我就是埃及日月星辰之王lf l say day is night, it will be written, 我可以颠倒是非and you will be what l say you are. 我说你什么没人敢反对l say you are innocent. 我说你是无辜的What you say does not matter. You don't understand.你说什么都没用,你不明白l can't stay here any longer. 我不能待下去了- Moses ! - No !All l've ever known to be true is a lie. 我所相信的事实都是谎言[ Panting ]l'm not who you think l am. 我不是你认为的那样What are you talking about ? 你在说什么?Go ask the man l once called ''Father.''去问我曾称之为父王的人吧[ Sighs ]Moses ? 摩西斯?Please. 请别走Good-bye, brother. 再见了,哥哥Moses !Moses ![ Grunts ] No.[ Grunts ] Aah ![ Frustrated Grunt ][ Wind Howling ]- Aaah ! - [ Camel Snorts ][ Grunting ][ Coughs ] Hey, wait. 嗨,等等!Please. 求你[ Sheep Bleating ]- [ Head Hits Rock ] - Ohh !- [ Bleating Continues ] - Oh !- [ Screaming ] - [ Girl ] What are you doing ?- Help ! - Let our sheep drink ! 让我们的羊喝水!Leave us alone ! Get away ! 别过来,滚开!- [ Children Yelling, Screaming ] - Stop it ! 站住!My father's the high priest of Midian. You're going to be in big trouble. 我父亲是米甸的大祭司,你们遇到大麻烦了!- Aah ! - [ Moses ] Hey, you. 嗨,你!Aren't these your camels ? 这不是你们的骆驼吗?- Hut-hut ! - No, no ! No, no ! 啊,别,不要!- Wait ! - Wait, stop ! -等等 -站住![ Groaning ]Whoa ![ Water Splashes ][ All Grunting ]What are you girls doing ? 你们在干什么?We're trying to get the funny man out of the well. 把一个怪家伙拉上来Trying to get the funny man out of the well. 把一个怪家伙拉上来?- Well, that's one l've never heard before. - [ Moses Yells ]这倒是件新鲜事[ Gasps ] Oh, my. Oh, uh, don't worry down there ! 啊,我的天啊!你不要怕Uh, we'll get you out. Hold on ! 我们会救你上来,挺住![ Grunting ]You. 是你?Huh ? [ Nervous Chuckling ]- Ohh ! - [ Water Splashes ]Mm-hmm.That's why Papa says she'll never get married. 怪不得爸爸说她嫁不出去You don't have to do this. Ladies, please, l'm really-- l'm really quite-- 你们不必这样,真的,我……No, not there, please. [ Laughs ] 别洗那儿,拜托,好痒哦!That tickles. Ladies, you've cleaned every inch of me.你们把我身上每一英寸都洗过了- Whoa, l-- l was wrong. - [ Children Laughing ] 我错了Let me through. Let me through. l want to see him. 让我过去,我要见他Ah ! You are most welcome. 你千万不要客气You should not be a stranger in this land. 你不是这里的生人You have been sent as a blessing. 你是神明送来的祝福-Tonight, you shall be my honored guest. -[ Coughs ] 今晚你将是我的贵宾- [ Laughing ] - [ Chuckles ]My father, Jethro, High Priest of Midian. 我父亲伽斯罗,米甸的大祭司[ Chattering ][ Giggling ]Psst. Sit with me. Um, all right. -跟我坐一起吧 -好吧Psst. Not yet. - Oh, sorry.-还不能吃 -对不起- [ Jethro ] My children, let us give thanks for this bountiful food.我的孩子们,感谢有这些丰盛的食物And let us also give thanks for the presence... of this brave, young man whom we honor here tonight.也感谢今晚的贵宾这名勇敢的年轻人- [ Chattering, Applauding ] - Please, sir, l wish you wouldn't.请先生不要这么客气l've done nothing in my life worth honoring. 我这辈子没做过值得赞赏的事First, you rescue Tzipporah from Egypt, 首先你把西泊娜从埃及救出来- then you defend my younger daughters from brigands. - [ Giggling ]其次你赶走了强盗救了我女儿You think that is nothing ? 你觉得这不算什么?lt seems you do not know what is worthy of honor. 看来你不懂得荣誉的价值A single thread in a tapestry挂毯中的一根线Though its color brightly shine就算十分光彩夺目Can never see its purpose ln a pattern of the grand design它也无法体会到整体设计的美感And the stone that sits on the very top Of the mountain's mighty face大山雄伟山顶上最顶端的石头Does it think it's more important Than the stones that form the base它认为比山底的石头更为重要吗?So how can you see what your life is worth你怎么知道你生命的价值Or where your value lies或你价值之所在?You can never see through the eyes of man 凡人无法衡量You must look at your life Look at your life through heaven's eyes你得透过上天的眼睛来衡量你生命的价值[ Crowd ] La-la-la-la-la-la-la La-la-la-la-la-la-la-laLa, la-la-la-la-la-laLa-la-la-la-la-la- Lai-lai-lai, lai-lai-lai-lai Lai-lai-lai, lai-lai-la - Dance with me. 跟我跳舞吧!No, l don't know how. 不行,我不会跳[ Singing Continues ][ Continues ][ Jethro ] A lake of gold in the desert sand ls less than a cool, fresh spring 沙漠中一湖的黄金,也比不上一股清泉And to one lost sheep a shepherd boy ls greater than the richest king对迷途的羊羔来说,牧羊人比最富的国王伟大lf a man lose everything he owns 失去一切的人Has he truly lost his worth 难道就没有价值了吗?Or is it the beginning - Of a new and brighter birth - [ Bleating ]也许这正是灿烂新生的开端So how do you measure the worth of a man 该怎样衡量一个人的价值ln wealth or strength or size 以财富、力量或大小?ln how much he gained or how much he gave 以获得或付出的多少?The answer will come The answer will come to him who tries这一切都将会有答案,只要他……To look at his life through heaven's eyes 透过上天的眼睛衡量生命And that's why we share all we have with you 这就是为啥我们与你分享Though there's little to be found 尽管我们家徒四壁When all you've got is nothing当你一无所有时There's a lot to go around 有许多可以分享No life can escape being blown about 每一个人都逃不过By the winds of change and chance命运的各种安排- And though you never know all the steps尽管你不知道下一步该怎么走- Dance with me. - No, l-- No. No ! -跟我跳舞 -不……- You must learn to join the dance 你一定要学会和大家跳舞You must learn to join the dance你一定要学会和大家跳舞So how do you judge what a man is worth 该怎么衡量一个人的价值?By what he builds or buys 看他盖的房子和买的东西?You can never see with your eyes on earth 凡人的双眼永远看不透Look through heaven's eyes 你得透过上天的眼睛Look at your life来衡量你的生命Look at your life 来衡量你的生命Look at your life through heaven's Eyes透过上天的眼睛[ Drumming ]Mmm.l love you. 我爱你[ Bleating ][ lnhales Deeply ]Ahh ![ Bleats ][ Sighs ][ Bleats ]lt's too early for this. 现在未免太早了[ Sighs ][ Bleating ][ Gasps ][ Whispering Voice ] Moses. 摩西斯……Here l am. 我在这儿[ Voice ] Take the sandals from your feet, 把你的凉鞋脱下来for the place on which you stand is holy ground. 因为你站在圣地之上[ Rolling Sounds ]Who are you ? 您是谁?[ Echoing ] l am that l am. 我就是我l don't understand. 我不明白l am the God of your ancestors, 我是你祖先的神Abraham, lsaac and Jacob. 亚伯拉罕、艾萨克、雅各布的神[ Miriam's Voice ] You were born of my mother, Yocheved. You are our brother. 你是约基别之子,我们的兄弟What do You want with me ? 您要我做什么?l have seen the oppression of My people in Egypt...我看见我的子民在埃及受苦and have heard their cry. 我听见他们的哀嚎- [ Man Screams ] - [ Moses ] Stop it ! Leave that man alone !住手,别打他了![ God ] So l have come down to deliver them out of slavery...我来救他们摆脱埃及人的奴役and bring them to a good land, 带他们到美好之地a land flowing with milk and honey. 流淌着奶与蜜之地And so, unto Pharaoh, l shall send...因此我要派你去见法老you. 你……Me ? Wh-Who am l to lead these people ? 我?我怎么能领导他们?They'll never believe me. They won't even listen. 他们不会相信也不会听我的l shall teach you what to say. 我将教你怎么说[ Moses' Voice ] Let my people go ! 把我的人民放走But l was their enemy. 但我曾是他们的敌人l was the prince of Egypt, the son of the man who slaughtered their children. 我曾是埃及王子是屠杀他们孩子的法老之子You've-- You've chosen the wrong messenger.您选错了使者,H-How can l even speak to these people ? 我怎么能领导这些人?Who made man's mouth ? 谁使人有了嘴?Who made the deaf, the mute, the seeing or the blind ?谁使人耳聋口哑、目明眼瞎?Did not l ? Now go ! 不是我吗?现在去吧![ Panting ]Oh, Moses, 啊,摩西斯l shall be with you when you go to the king of Egypt.你去见法老时我会与你同去But Pharaoh will not listen. 但法老不会听我的So l will stretch out My hand... and smite Egypt... with all My wonders. 那我将伸出手来用我的神法毁灭埃及Take the staff in your hand, Moses. 摩西斯,要拿着你手里的杖With it, 你用它you shall do My wonders. 来实施我的神法l shall be with you, Moses. 我会与你同在,摩西斯- [ Panting ] - Moses.[ Whispering ] Moses.[ Bleating ][ No Audible Dialogue ]But, Moses, 但是,摩西斯……you are just one man. 你只有一个人Tzipporah, 西泊娜……please. 请你看看- [ Sighs ] - [ Laughter ]Look at your family. 看看你的家人[ Chattering ]They are free. 他们是自由的They have a future. 他们有美好的未来They have hopes and dreams... 他们有希望和梦想and the promise of a life with dignity. 还有过尊严生活的指望That is what l want for my people. 我要我的人民也能如此And that is why l must do the task... 因此我必须去完成that God has given me. 神交给我的使命l'm coming with you. 我要跟你一起去[ All Grunting ][ Native lnstruments ][ Continues ][ Stops ]Rameses. 兰姆西斯Moses ? ls it really ? 摩西斯?真的是你?[ Chuckling ] Moses ! -摩西斯- Rameses ! - Where have you been ? l took you for dead.你上哪里了?我以为你死了! -兰姆西斯[ Both Laughing ]Look at you ! Pharaoh. 看看你!法老!Well, look at you. What on earth are you dressed as ?看看你,你怎么这副打扮?Oh, Rameses, it's so good to see you. 兰姆西斯,见到你真高兴![ Hotep ] Excuse me, Your Majesty. 对不起,陛下We are compelled to remind you this man committed a serious crime against the gods.我们得提醒您此人对神明犯下了重大罪行We are loathe to bring it up, mind you. 我们不想提起此事The law clearly states the punishment for such a crime--法律明文规定了应受的惩罚……- Death ! - We hesitate to say it. -死刑! -我们并不想说Be still. Pharaoh speaks. 闭嘴,法老在说话l am the morning and the evening star. 我是日月星辰之王Rameses. 兰姆西斯……- lt shall be as l say. - [ Sighs ] 我说的话才算数l pardon forever all crimes of which he stands accused...我永远赦免他犯的一切罪行and will have it known that he is... our brother Moses, the prince of Egypt. 并昭告世人他是……我的兄弟摩西斯是埃及王子[ Crowd Gasping, Murmuring ]Rameses, 兰姆西斯……in my heart, you are my brother, 在我心里,你是我兄弟but things cannot be as they were. 但情况已经不同了l see no reason why not. 我看不出有什么不同You know l am a Hebrew, and the God of the Hebrews came to me.你知道我是希伯来人 ,希伯来的神来找过我了What ? 什么?He commands that you let His people go. 他命令你把他的子民放走[ Crowd Murmuring ]Commands ? 命令?Behold... the power of God. 看着……神的力量[ Crowd Gasps ][ Hissing ]Well, uh, impressive. 哦,挺厉害的Hmm.Very well, Moses. l'll play along. 好吧,摩西斯,我就陪你玩玩[ Chuckles ] Hotep. Huy. 荷泰,休伊Give this snake charmer our answer. 让这个江湖术士瞧瞧厉害[ Chuckling ][ Rumbling ][ Both ] By the power of Ra. 太阳神的力量Mut. 姆特神Nut. 奴特神- Khnum. - Ptah. 山羊神,布塔神- Nephthys. - [ Huy ] Nekhbet. 奈芙提斯女神,鹰神- Sobek. - Sekhmet. 鳄鱼神,西米神Sokar. Selket. Reshpu. 苏卡神,战神- Wadjet. - Anubis. 洛西夫神……瓦桀神- Anukis. - Seshmu. 死神、塞斯努神- Meshkent. - Hemsut. 米斯罕神,命运神- Tefnut. - Heket. 露神,蛙神- Mafdet. - Ra, Mut, Nut, Ptah. 马特神Hemsut, Tefnut, Sokar, Selket. 太阳神、奴特神、布塔神……Seshmu, Reshpu, Sobek, Wadjet. 战神、瓦杰神、鳄鱼神、奈芙Heket, Mafdet, Nephthys, Nekhbet, Ra ! 提斯女神、蛙神、太阳神So you think you've got friends ln high places With the power to put us on the run 你以为你有一个天上的朋友就能把我们吓跑Well, forgive us these smiles On our faces 不要让我们笑掉大牙You'll know what power is when we are done等我们施展法力你就知道厉害[ Both ] Son. 小子You're playing with the big boys now你这是自不量力- Playing with the big boys now - Oh, that's pretty.你这是自不量力……啊,真漂亮!- Every spell and gesture - Tells you who's the best-每一道符咒和魔术 -都让你招架不住[ Both ] You're playing with the big boys now你这是自不量力You're playing with the big boys now你这是自不量力- You're playing with the big boys now - [ Chanting ] 你这是自不量力Stop this foolish mission结束愚蠢的行动吧Watch a true magician让真正的魔法师Give an exhibition how给你展示法力[ Huy ] Pick up your silly twig, boy捡起你的小树枝,小子You're playing with the big boys now你这是自不量力- Ha-ha-ha-ha-ha ! - [ Priests ] By the power of Ra太阳神、布塔神、奴塔神Mut, Nut 鳄鱼神、战神Khnum, Ptah 蛙神、马特神的力量Sobek, Sekhmet Sokar, Selket Anubis, Anukis, Hemsut Tefnut, Meshkent, Mafdet 死神、命运神、塞斯努神You're playing with the big boys now你这是自不量力You're playing with the big boys now你这是自不量力By the might of Horus you will kneel before us你将屈服于荷鲁斯神,跪在我们面前。
雷顿教授与不可思议的小镇全谜题图解攻略
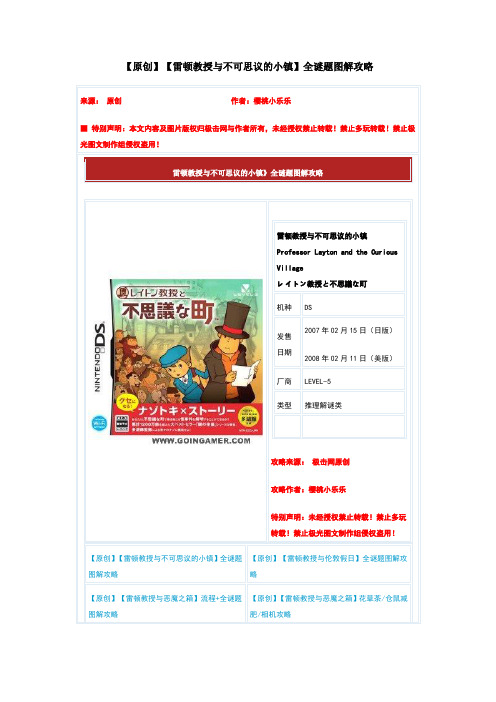
【原创】【雷顿教授与不可思议的小镇】全谜题图解攻略来源:原创作者:樱桃小乐乐■ 特别声明:本文内容及图片版权归极击网与作者所有,未经授权禁止转载!禁止多玩转载!禁止极光图文制作组侵权盗用!雷顿教授与不可思议的小镇》全谜题图解攻略雷顿教授与不可思议的小镇Professor Layton and the CuriousVillageレイトン教授と不思議な町机种DS发售日期2007年02月15日(日版)2008年02月11日(美版)厂商LEVEL-5类型推理解谜类攻略来源:极击网原创攻略作者:樱桃小乐乐特别声明:未经授权禁止转载!禁止多玩转载!禁止极光图文制作组侵权盗用!【原创】【雷顿教授与不可思议的小镇】全谜题图解攻略【原创】【雷顿教授与伦敦假日】全谜题图解攻略【原创】【雷顿教授与恶魔之箱】流程+全谜题图解攻略【原创】【雷顿教授与恶魔之箱】花草茶/仓鼠减肥/相机攻略れ?007狼と小鳥屋敷の庭(宅院的庭院)1. 2只狼到右边2. 1只狼驾驶木筏返回3. 2只狼过河到右边4. 1只狼返回5. 2只鸟到右边6. 1只狼、1只小鸟返回左边7. 2只鸟移动到右边8. 1只狼返回左边9. 2只狼移动到右边10. 1只狼返回左边11. 2只狼移动到右边008種まきの報酬屋敷の庭(宅院的庭院)>>>调查对岸河边的花丛50009マッチ犬の悲劇屋敷の玄関(宅院的玄关)010仲間はずれの漢字屋敷の玄関(宅院的玄关)>>>调查书架知011円弧と直線屋敷の大広間(宅院的大客厅)10012合わせて四角屋敷の大広間(宅院的大客厅)013沈没船のナゾ屋敷の庭(宅院的庭院)>>>调查小船13014イス選び雑貨屋(杂货屋) >>>调查左边座椅E015残ったのは?雑貨屋(杂货屋)>>>调查台上蜡烛3016ペンと三角形町役場(小镇事务所)7017仲間はずれ1町の入り口(小镇的入口)ジェリア018ちりホテル(旅馆) 1. 中间的横火柴棒往左移动半格とりとゴミ2. 右上的竖火柴棒往左下移动019込んだ駐車場町への「はね橋」(往小镇的「吊桥」)>>>调查河对岸的车1. 右移红色车上面的横向的车。
SA2 1F LOBBY 立面 布局1 (1)

不锈钢踢脚
石材饰面
ELEVATION A、C 立面图 A、C
2
ID.SA2.1F.01
ELEVATION C
SCALE 1:50
SA2 1ST LOBBY
服务公寓2 大堂
ID.SA2.1F.06.01
立面 C
比例 1:50
1: 50
2
12
2800 2800 300 1150 1300 3100 2750 700 2550 2700 2100 2550 3000
C
4
21890 6800 4150
20 20
D
13 5 8
2750 2000 20 1460 900 1200 20 60 20 1000 20 60 20 525 150 525 100 1000 3650
E
F
G
2400
930
20
1000
6100 100 600 150
600 100
1100
100 700
不锈钢踢脚 不锈钢踢脚 白色乳胶漆
白色乳胶漆
3
ID.SA2.1F.01
ELEVATION E
SCALE 1:40
SA2 1ST LUGGAGE
立面 E
服务公寓2 行李间
比例 1:40
4
ID.SA2.1F.01
ELEVATION F
SCALE 1:40
SA2 1ST LUGGAGE
服务公寓2 行李间
不锈钢踢脚
SCALE 1:50
SA2 1ST LOBBY
服务公寓2 大堂
立面 A
比例 1:50
G
6100 3880 20 1300 20 1060
