2012年北航SDLTRADOS杯研究生科技英语翻译比赛原文
第七届翻译大赛英文原文

OpticsManini NayarWhen I was seven, my friend Sol was hit by lightning and died. He was on a rooftop quietly playing marbles when this happened. Burnt to cinders, we were told by the neighbourhood gossips. He'd caught fire, we were assured, but never felt a thing. I only remember a frenzy of ambulances and long clean sirens cleaving the silence of that damp October night. Later, my father came to sit with me. This happens to one in several millions, he said, as if a knowledge of the bare statistics mitigated the horror. He was trying to help, I think. Or perhaps he believed I thought it would happen to me. Until now, Sol and I had shared everything; secrets, chocolates, friends, even a birthdate. We would marry at eighteen, we promised each other, and have six children, two cows and a heart-shaped tattoo with 'Eternally Yours' sketched on our behinds. But now Sol was somewhere else, and I was seven years old and under the covers in my bed counting spots before my eyes in the darkness.After that I cleared out my play-cupboard. Out went my collection of teddy bears and picture books. In its place was an emptiness, the oak panels reflecting their own woodshine. The space I made seemed almost holy, though mother thought my efforts a waste. An empty cupboard is no better than an empty cup, she said in an apocryphal aside. Mother always filled things up - cups, water jugs, vases, boxes, arms - as if colour and weight equalled a superior quality of life. Mother never understood that this was my dreamtime place. Here I could hide, slide the doors shut behind me, scrunch my eyes tight and breathe in another world. When I opened my eyes, the glow from the lone cupboard-bulb seemed to set the polished walls shimmering, and I could feel what Sol must have felt, dazzle and darkness. I was sharing this with him, as always. He would know, wherever he was, that I knew what he knew, saw what he had seen. But to mother I only said that I was tired of teddy bears and picture books. What she thought I couldn't tell, but she stirred the soup-pot vigorously.One in several millions, I said to myself many times, as if the key, the answer to it all, lay there. The phrase was heavy on my lips, stubbornly resistant to knowledge. Sometimes I said the words out of con- text to see if by deflection, some quirk of physics, the meaning would suddenly come to me. Thanks for the beans, mother, I said to her at lunch, you're one in millions. Mother looked at me oddly, pursed her lips and offered me more rice. At this club, when father served a clean ace to win the Retired-Wallahs Rotating Cup, I pointed out that he was one in a million. Oh, the serve was one in a million, father protested modestly. But he seemed pleased. Still, this wasn't what I was looking for, and in time the phrase slipped away from me, lost its magic urgency, became as bland as 'Pass the salt' or 'Is the bath water hot?' If Sol was one in a million, I was one among far less; a dozen, say. He was chosen. I was ordinary. He had been touched and transformed by forces I didn't understand. I was left cleaning out the cupboard. There was one way to bridge the chasm, to bring Solback to life, but I would wait to try it until the most magical of moments. I would wait until the moment was so right and shimmering that Sol would have to come back. This was my weapon that nobody knew of, not even mother, even though she had pursed her lips up at the beans. This was between Sol and me.The winter had almost guttered into spring when father was ill. One February morning, he sat in his chair, ashen as the cinders in the grate. Then, his fingers splayed out in front of him, his mouth working, he heaved and fell. It all happened suddenly, so cleanly, as if rehearsed and perfected for weeks. Again the sirens, the screech of wheels, the white coats in perpetual motion. Heart seizures weren't one in a million. But they deprived you just the same, darkness but no dazzle, and a long waiting.Now I knew there was no turning back. This was the moment. I had to do it without delay; there was no time to waste. While they carried father out, I rushed into the cupboard, scrunched my eyes tight, opened them in the shimmer and called out'Sol! Sol! Sol!' I wanted to keep my mind blank, like death must be, but father and Sol gusted in and out in confusing pictures. Leaves in a storm and I the calm axis. Here was father playing marbles on a roof. Here was Sol serving ace after ace. Here was father with two cows. Here was Sol hunched over the breakfast table. The pictures eddied and rushed. The more frantic they grew, the clearer my voice became, tolling like a bell: 'Sol! Sol! Sol!' The cupboard rang with voices, some mine, some echoes, some from what seemed another place - where Sol was, maybe. The cup- board seemed to groan and reverberate, as if shaken by lightning and thunder. Any minute now it would burst open and I would find myself in a green valley fed by limpid brooks and red with hibiscus. I would run through tall grass and wading into the waters, see Sol picking flowers. I would open my eyes and he'd be there,hibiscus-laden, laughing. Where have you been, he'd say, as if it were I who had burned, falling in ashes. I was filled to bursting with a certainty so strong it seemed a celebration almost. Sobbing, I opened my eyes. The bulb winked at the walls.I fell asleep, I think, because I awoke to a deeper darkness. It was late, much past my bedtime. Slowly I crawled out of the cupboard, my tongue furred, my feet heavy. My mind felt like lead. Then I heard my name. Mother was in her chair by the window, her body defined by a thin ray of moonlight. Your father Will be well, she said quietly, and he will be home soon. The shaft of light in which she sat so motionless was like the light that would have touched Sol if he'd been lucky; if he had been like one of us, one in a dozen, or less. This light fell in a benediction, caressing mother, slipping gently over my father in his hospital bed six streets away. I reached out and stroked my mother's arm. It was warm like bath water, her skin the texture of hibiscus.We stayed together for some time, my mother and I, invaded by small night sounds and the raspy whirr of crickets. Then I stood up and turned to return to my room.Mother looked at me quizzically. Are you all right, she asked. I told her I was fine, that I had some c!eaning up to do. Then I went to my cupboard and stacked it up again with teddy bears and picture books.Some years later we moved to Rourkela, a small mining town in the north east, near Jamshedpur. The summer I turned sixteen, I got lost in the thick woods there. They weren't that deep - about three miles at the most. All I had to do was cycle forall I was worth, and in minutes I'd be on the dirt road leading into town. But a stir in the leaves gave me pause.I dismounted and stood listening. Branches arched like claws overhead. The sky crawled on a white belly of clouds. Shadows fell in tessellated patterns of grey and black. There was a faint thrumming all around, as if the air were being strung and practised for an overture. And yet there was nothing, just a silence of moving shadows, a bulb winking at the walls. I remembered Sol, of whom I hadn't thought in years. And foolishly again I waited, not for answers but simply for an end to the terror the woods were building in me, chord by chord, like dissonant music. When the cacophony grew too much to bear, I remounted and pedalled furiously, banshees screaming past my ears, my feet assuming a clockwork of their own. The pathless ground threw up leaves and stones, swirls of dust rose and settled. The air was cool and steady as I hurled myself into the falling light.光学玛尼尼·纳雅尔谈瀛洲译在我七岁那年,我的朋友索尔被闪电击中死去了。
中英文翻译

外文翻译系别信息工程系专业网络工程班级B841111学号B84111117姓名任贺指导教师孟桂英负责教师沈阳航空航天大学北方科技学院2012年6月The Design and Realization of Digital Signature Based on RSARSA algorithms is introducedRSA public key cryptography. So-called public key cryptography system is to use different encryption and decryption key keys, is a "known encryption key is deduced by declassified in calculations is key to be done" password system.In a public-key cryptosystem, encryption key (i.e. public key) PK is the public information, and decryption key (namely, the private key) SK is needed to remain confidential. Encryption algorithm E and decryption algorithm D also are in the open. Although the secret key SK is by public key PK decision, but cannot PK calculated according to SK. It is based on this theory, appeared in 1978 the famous RSA algorithms, it is usually into a pair of Mr RSA keys, one of which is kept secret key, save by users; Another for public key, can be made public, and even can be registered in the network server. In order to improve the secrecy intensity, RSA keys at least 500 bits long, generally recommend using 1024 bits. This makes the calculation amount of encryption is very large. To reduce the computational complexity, sending the information, often USES traditional encryption methods and public key encryption method unifies means, that information with the improved DES or IDEA dialogue key encryption, and use the RSA encryption keys and information the dialogue. Each other after receiving information, with different keys decryption and can check the information.RSA algorithms is the first not only can be used for encryption but also can be used for digital signature algorithm, and it is also easy to understand and operation. RSA is most widely studied public key algorithm, and put forward to the now from more than 30 years, experienced the test of all kinds of attacks, for the people to accept gradually, generally, is now one of the most outstanding public key solutions.The safety of the RSARSA security depends on the larger decomposition, but whether or not equal to tarsus decomposition theory has been failed to get the certificate, and for no proof that break RSA will need to be larger decomposition. Assuming there are a large without decomposition algorithm, it must be larger decomposition algorithm can be modified. At present, some variant of RSA algorithms have been proved equivalent to tarsusdecomposition. Anyway, the decomposition n is the most obviously method of assault. Now, people already can break down more than 140 decimal big primes. Therefore, must choose a big modulus n some, for application is up.RSA speedBecause of the large is calculated, make the fastest RSA than DES 100 times on slow, whether software or hardware implementation. Speed has been the defects of RSA. Generally speaking only for a few data encryption.RSA's chosen-ciphertext attackRSA in chosen-ciphertext before the attack is weak. Generally the attacker is will certain information is the camouflage (Blind), let the private key with the entity to sign. Then, after calculation can get what it wanted information. In fact, attack the same weaknesses are using, that is such a fact that have been retained the multiplication of the input structure: (XM) ^ d = X ^ d * M ^ d mod n front have already mentioned, the inherent problems from the public key cryptography is the most useful features-everyone can use public key. But from the algorithm can't solve the problem, the main measures are two: one is the good public key agreement, guarantee the process not produce any other entity entity of the information the decryption, you know nothing wrong information signature; The other One is never sent to strangers random document signature, the first to use One sign of a document for-Way HashFunction HASH processing, or use at the same time different signature algorithm.RSA encryption algorithm faults⑴produce key is very troublesome, produced by a prime technical limitations, so hard to do it once a secret. ⑵security, the safety of RSA depends on the large factor decomposition, but did not prove theoretically decipher the difficulty of tarsus and RSA decomposition difficulty equivalent, and most people tend to academic password factor decomposition is not NPC problem. At present, people already can break down more than 140 decimal big primes, it is required to use more long key, speed, more slowly; Moreover, the people are actively looking for attack RSA methods, such as chosen-ciphertext attack, general attackers will certain information is the camouflage (Blind), let the private key with the entity to sign. Then, after calculation can get what it wanted information. In fact, attack the same weaknesses are using, that is such a fact that have been retained the multiplication of the input structure: (XM) d = Xd * Md mod n front have alreadymentioned, the inherent problems from the public key cryptography is the most useful features-everyone can use public key. But from the algorithm can't solve the problem, the main measures are two: one is the good public key agreement, guarantee the process not produce any other entity entity of the information the decryption, you know nothing wrong information signature; The other One is never sent to strangers random document signature, the first to use One sign-Way Hash Function of document for Hash processing, or use at the same time different signature algorithm. In addition to using public modulus, people also try s ome use decryption index or φ (n) and so on attack.⑶ speed too slow, because the grouping of RSA too large length, to ensure safety, n at least 600 bitx above, make the operation cost is high, especially at a slower speed, a symmetric cryptosystem several orders of magnitude slower; Along with the development of the larger decomposition technique, the length is increasing, go against the standardization of data format. At present, the SET (Secure Electronic Transaction) agreement with 2048 bits long requirements CA keys, other entity USES 1024 bit key. In order to speed, at present the widely use of single, the method of using a combination of public key password, complementary advantages and disadvantages: ChanYao password encryption speed, people use it to encrypt a long documents, and then using the RSA encryption to give document, extremely good solve the problem of ChanYao password key distribution.Modern cryptography has become the core of information security technology, cryptography, is the communication security confidential subject research, that is, to study the type of secret information transmission of transformation in order to prevent the third party to steal information. Cryptography include two branches: password code to learn and password analytics. Password code to learn the main information exchange, to protect information in the channel's relay in to steal, decryption and use method, and the password analysis learning is and password code learning instead, it mainly studies how to analyze and crack password. Both between both opposition to each other and promote each other. The classification of the password system has a lot of, one of them is based on encryption algorithm and decryption keys used algorithms are same, password system can be divided into symmetrical encryption system (ChanYao password system) and asymmetric encryption system (public key cryptosystems), the two password system each have their own advantages and disadvantages, so now USES two hybrid. Public key cryptosystems features are: the receiving party B produces a pair of keys (PK and SK);PK public, SK confidential; PK from launch SK is very difficult; A and B both sides communication, A in any way obtained B public key, use the B public key encryption information, encrypted information can be obtained by any unsafe channel sent. B received ciphertext information, with their own private key recovering the decryption plaintext. Public key cryptography system to ensure the security of information have become the key technology. RSA public key cryptosystems so far or a recognised as safe system. RSA public key encryption algorithm is the first can used for data encryption can also be used as a digital signature algorithm. It is easy to understand and operation, is also very popular. As more commercial application and standardization work, RSA has become the most representative of the public key encryption technology. VISA, MasterCard, IBM, Microsoft and other companies for the safety of Electronic trading work standard (Secure Electronic Transactions, SET) adopt the standard RSA algorithms, this makes the RSA in our life almost everywhere. Online transactions encrypted connection, the bank on the net identity authentication, all kinds of credit card the use of digital certificate, intelligent mobile phone memory card and validation of chips and so on the function, most use RSA technology.In 1995, has been put forward a very unexpected attack way: if E younger sister to huang hardware are fully know, and know it to some specific message when the time needed to encrypt words, so she can be quickly is deduced from the d. This attack will be established the way, mainly because of the encryption on the mode of the index when computing is a bit a bit, and bits of 1 spent than a yuan for 0 computation of a operation, so if you can get more information and its encryption of time, will have a chance to launch the private key content. The most popular attack on RSA is generally larger factor decomposition based on. In 1999, the RSA-155 (512 bits) be successful decomposition, spent five months time (about 8000 MIPS years) and 224 CPU hours in a 3.2 G the central memory Cray C916 finished on the computer. In 2002, the RSA-158 was also success factor decomposition. On December 12, 2009, Numbers for RSA-768 (768 bits, 232 digits) number also be successful decomposition. Beijing time February 15 morning news, according to the New York times reported Tuesday, European and American mathematicians and cryptographers accidental discovery, at present is widely spoken all over the world's public key encryption algorithm RSA existence of loopholes. They found that, in 7 million the experiment of 27000 sample public key and not according to thetheory of randomly generated. That is, maybe someone can find out the secret of produce public key prime Numbers. This research project was made by the independent cryptographers James P.H ughes and Dutch mathematician Arjen k. Lenstra lead. Their report said: "we found the vast majority of the public key all is according to the theory of generation, but every one thousand public key will have two unsafe." The report says, to prevent someone USES the vulnerability, a public key from the public access database has been removed. To ensure the security of the system, the website needs to be in the terminal to change.Over the years, RSA mainly focuses on information security market in several fields, is also have distinguishing feature each field. In the identity authentication field, RSA attention to many online trading enterprise including financial, search, and industry, the user to the extent of the identity authentication concern obviously different. Another fishing, Trojan than before more widespread. Online identity authentication, the growth is strong fraud. In addition, the enterprise internal control, at present, China is still in the process of maturity. In the data leak in some new "Trojan RSA services to society and to the strong identity authentication, also have some new business breakthrough.The financial industry in anywhere in the world, there are the highest safety risk industry, whether the reality of crime or cyber crime, financial is a sweet BoBo. Along with the development of the network bank, financial industry to information security solutions needs always very strong, the financial industry is the largest RSA development space, and in the future for a period of time will still is. How to keep the financial industry information security, prevent data leak, and deal with the financial services, and become the focus of future business development RSA.Digital signature is introducedDigital signature, is the only information to produce the sender of the others can't fake a digital string, the string is also a number of information of the sender sends information a valid proof of authenticity.Digital signature is symmetrical encryption technology and the application of digital technology.Digital signature of the file is easy to verify the integrity of the (don't need at the chapter, at the signature, also do not need the handwriting expert), and digital signature is not deny sex (don't need the handwriting expert to verify).Say simply, the so-called digital signature is additional data unit in on some of the data, or of data elements of the password change. This kind of data or transform allow data unit receiver to confirm our units of data source and the units of data integrity and protect data, to prevent being (such as the receiver) forged. It is to the electronic form of news to sign one method, a signature news can be in a communication network transmission. Based on the public key cryptography system and a private key password system can get digital signature, mainly is based on public key cryptosystems digital signature. Including ordinary digital signatures and special digital signature. Ordinary digital signature algorithm has RSA, ElGamal, Fiat-Shamir, Guillou-Quisquarter, Schnorr, Ong-Schnorr-Shamir digital signature algorithm, Des/DSA, elliptic curve digital signature algorithm and finite automata digital signature algorithm, etc. Special digital signatures have blind signature, proxy signature, group signature, undeniable signature, fair blind signature, threshold signature, with news of the signature restore function, it is closely related with the specific application environment. Obviously, the application of digital signature involving legal problems, the federal government based on limited domain of discrete logarithm problem develop their own digital signature standard (DSS).Digital Signature (Digital Signature) technology is asymmetric encryption algorithm of typical application. The process of application of digital signature, sending data sources to use his private key to data validation and or other relevant variables and data content to encrypt and the completion of legal "signature" data, data receiving party is use the other public key to interpret received "digital signatures", and will interpret results are used to test the integrity of the data, to confirm the legitimacy of the signature. Digital signature technology in network system is virtual environment identified important technology, and can completely replace the reality in the process of holograph signs ", in the technology and the law is guaranteed. In the application of digital signature, the sender's public key can be easily get, but his private key requires strictly confidential.Digital signature functionEnsure the integrity of the information transmission, the sender's identity authentication, to prevent trade in deny happen. Digital signature technology is will the information with sender's private key encryption, and the original transfer to the recipient together. The receiver only in sending public key can decrypt encrypted information, then use HASH function of received the original produce a the information, and thedeclassified information contrast. If the same, show the information received is complete, the transfer of the process not be amended, modified or information that was, so digital signatures can verify the integrity of the information. Digital signature is a encryption process, digital signature verification is a decryption process.Digital signature process"Send a message sender, with a hash function from the message of the generation text message digest, and in her own private key to encrypt the the, the encrypted the will of a message as a digital signature and a message sent to the receiving party together, the receiving party first used to send party the same hash function from the receiving of the original message to calculate the message in the abstract, then use the sending of a message of public key to additional digital signature decryption, if the two the same, so the receiving party can confirm the digital signature is the sender.Digital signature has two functions: one is the message is really can be determined by the sender signed the concurrent out, because people can't fake sender's signature. 2 it is digital signatures can determine the integrity of the news. Because the characteristics of digital signature is that it represents the characteristics of documents, file if change, the value of the digital signature will change. Different file will get different digital signature.A digital signature involves a hash function, the sender's public key, the sender's private key. "MD5 algorithm introducesMD5 news the algorithm is designed by Rivest one-way hash function, MD5 not based on any hypothesis and the password system, it is the direct structure way, quickly, very practical.MD5 algorithm is the typical application of information to a produce news the MD, to prevent being tampered with. For example, in the Unix has many software in the download of a file name is same, file extensions. MD5 files, in the file usually only one line of text, general structure such as:MD5 (tanajiya. Tar. Gz) = 0 ca175b9c0f726a831d895e269332461This is tanajiya. Tar. Gz file digital signature. The entire file MD5 as a large text information, through its irreversible text transform algorithm, produced this only the MD5 information. If in the future of this file transmission process, whatever happened to the content of the document any form of change, as long as you to this file recount MD5 willfind information in different, thus make sure you get is a doubtful file. If have a third party certification institution, with MD5 also can prevent file the author's "deny", this is the so-called digital signature applications. MD5 also widely for encryption and decryption technology. For example in the Unix system password of user to MD5 encryption is stored in the after file system. When users log on, the system the password of user input into MD5 value calculation, and then to and stored in file system of MD5 value is used in the comparison, we determine the input password is correct. Through such steps, the system does not know in user password plain code under the situation that can determine the user login system legitimacy. It could not only avoid the password of user with system administrator rights by the users know, but also to a certain extent increase the difficulty of the password has been cracked.基于RSA的数字签名系统的设计与实现RSA算法介绍RSA公开密钥密码体制。
11-11-0287-00-000s-p802-11s-sponsor-ballot-2nd-recirc-comments
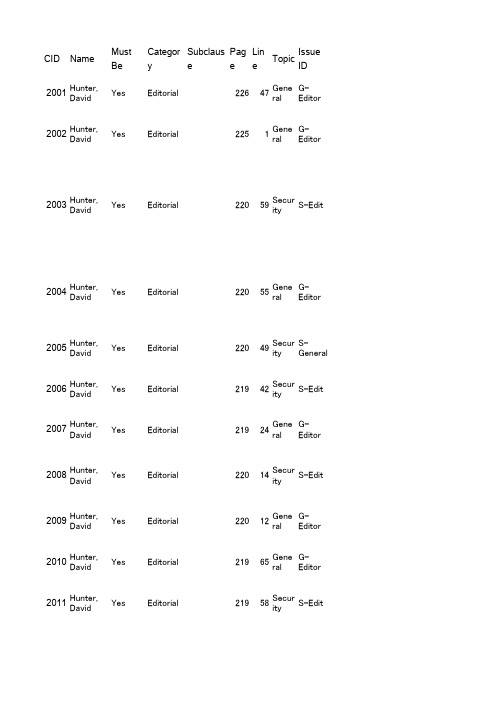
CID Name MustBeSatisfieCategorySubclausePageLineTopicIssueID2001Hunter,DavidYes Editorial22647GeneralG-Editor2002Hunter,DavidYes Editorial2251GeneralG-Editor2003Hunter,DavidYes Editorial22059SecurityS-Edit2004Hunter,DavidYes Editorial22055GeneralG-Editor2005Hunter,DavidYes Editorial22049SecurityS-General2006Hunter,DavidYes Editorial21942SecurityS-Edit2007Hunter,DavidYes Editorial21924GeneralG-Editor2008Hunter,DavidYes Editorial22014SecurityS-Edit2009Hunter,DavidYes Editorial22012GeneralG-Editor2010Hunter,DavidYes Editorial21965GeneralG-Editor2011Hunter,DavidYes Editorial21958SecurityS-Edit2012Hunter,DavidYes Editorial21954SecurityS-Edit2013Hunter,DavidYes Editorial21952SecurityS-Edit2014Hunter,DavidYes Editorial21949SecurityS-Edit2015Hunter,DavidYes Editorial21936GeneralG-Editor2016Hunter,DavidYes Editorial21934SecurityS-Edit2017Hunter,DavidYes Editorial21924SecurityS-Edit2018Hunter,DavidYes Editorial21921SecurityS-Edit2019Hunter,DavidYes Editorial21918SecurityS-Edit2020Hunter,DavidYes Editorial21916SecurityS-Edit2021Hunter,DavidYes Editorial21913SecurityS-Edit2022Hunter,DavidYes Editorial21912SecurityS-Edit2023Hunter,DavidYes Editorial21911SecurityS-Edit2024Hunter,DavidYes Editorial2198SecurityS-Edit2025Hunter,DavidYes Editorial2196SecurityS-Edit2026Hunter,DavidYes Editorial2191SecurityS-Edit2027Hunter,DavidYes Editorial21863SecurityS-Edit2028Hunter,DavidYes Editorial21861SecurityS-Edit2029Hunter,DavidYes Editorial21860SecurityS-Edit2030Hunter,DavidYes Editorial21829GeneralG-Editor2031Hunter,DavidYes Editorial21826SecurityS-Edit2032Hunter,DavidYes Editorial21826GeneralG-Editor2033Hunter,DavidYes Technical2179SecurityS-MPM2034Hunter,DavidYes Editorial2171GeneralG-Editor2035Hunter,DavidYes Technical20943SecurityS-Edit2036Hunter,DavidYes Editorial20722SecurityS-Edit2037Hunter,DavidYes Technical20718SecurityS-Edit2038Hunter,DavidYes Editorial20718SecurityS-Edit2039Hunter,DavidYes Technical20338SecurityS-Edit2040Hunter,DavidYes Technical20335SecurityS-Edit2041Hunter,DavidYes Editorial17639GeneralG-Prim2042Hunter,DavidYes Editorial17639GeneralG-Prim2043Hunter,DavidYes Editorial17639GeneralG-Prim2044Hunter,DavidYes Editorial17639GeneralG-Prim2045Hunter,DavidYes Editorial17639GeneralG-Prim2046Hunter,DavidYes Editorial17414GeneralG-Prim2047Hunter,DavidYes Technical16321MACM-MCCA2048Hunter,DavidYes Editorial15853GeneralG-Prim2049Hunter,DavidYes Editorial15724GeneralG-Prim2050Hunter,DavidYes Editorial1561GeneralG-Prim2051Hunter,DavidYes Editorial15439GeneralG-Prim2052Hunter,DavidYes Editorial1538GeneralG-Prim2053Hunter,DavidYes Editorial1531GeneralG-Prim2054Hunter,DavidYes Editorial15224GeneralG-Prim2055Hunter,DavidYes Editorial15222GeneralG-Prim2056Hunter,DavidYes Editorial15054GeneralG-Prim2057Hunter,DavidYes Technical14964MAC M-PM2058Hunter,DavidYes Editorial14958GeneralG-Prim2059Hunter,DavidYes Editorial14950GeneralG-Prim2060Hunter,DavidYes Editorial14950GeneralG-Prim2061Hunter,DavidYes Editorial14336GeneralG-Editor2062Hunter,DavidYes Technical14335GeneralG-Editor2063Hunter,DavidYes Technical14332GeneralG-Editor2064Hunter,DavidYes Technical14327GeneralG-Editor2065Hunter,DavidYes Technical13836GeneralG-Editor2066Hunter,DavidYes Editorial13624GeneralG-Editor2067Hunter,DavidYes Editorial11239MACM-MCCA2068Hunter,DavidYes Technical10556SecurityS-Edit2069Hunter,DavidYes Technical9242SecurityS-SAE2070Hunter,DavidYes Technical9046SecurityS-SAE2071Hunter,DavidYes Technical9043SecurityS-SAE2072Hunter,DavidYes Technical909SecurityS-SAE2073Hunter,DavidYes Technical8940SecurityS-SAE2074Hunter,DavidYes Technical8740SecurityS-SAE2075Hunter,DavidYes Technical8722SecurityS-SAE2076Hunter,DavidYes Technical8713SecurityS-SAE2077Hunter,DavidYes Technical8655SecurityS-SAE2078Hunter,DavidYes Technical868SecurityS-SAE2079Hunter,DavidYes Technical868SecurityS-SAE2080Hunter,DavidYes Technical8545SecurityS-SAE2081Hunter,DavidYes Technical8544SecurityS-SAE2082Hunter,DavidYes Technical6528RFIR-Proxy2083Hunter,DavidYes Technical6161RFIR-HWMP2084Hunter,DavidYes Technical5548MACM-MCCA2085Hunter,DavidYes Technical3643SecurityS-SAE2086Hunter,DavidYes Technical3628SecurityS-SAE2087Hunter,DavidYes Technical3611SecurityS-SAE2088Hunter,DavidYes Editorial3611SecurityS-SAE2089Hunter,DavidYes Technical3549SecurityS-SAE2090Hunter,DavidYes Editorial3423GeneralG-Editor2091Hunter,DavidYes Technical1536SecurityS-Edit2092Hunter,DavidYes Technical1316GeneralG-Emergency2093Hunter,DavidYes Technical1321GeneralG-Emergency2094Hunter,DavidYes Technical1264RFIR-Proxy2095Hunter,DavidYes Editorial1260GeneralG-Editor2096Hunter,DavidYes Technical1254GeneralG-Editor2097Hunter,DavidYes Editorial126GeneralG-Editor2098Hunter,DavidYes Editorial1131GeneralG-Editor2099Hunter,DavidYes Editorial1130GeneralG-Editor2100Hunter,DavidYes Editorial1129GeneralG-Editor2101Hunter,DavidYes Editorial1129GeneralG-Editor2102Hunter,DavidYes Editorial1123GeneralG-Editor2103Hunter,DavidNo Editorial118GeneralG-Editor2104Hunter,DavidYes Editorial1057GeneralG-Editor2105Hunter,DavidYes Editorial1042GeneralG-Editor2106Hunter,DavidYes Technical102GeneralG-Editor2107Hunter,DavidYes Editorial865GeneralG-Arch2108Hunter,DavidYes Editorial859GeneralG-Arch2109Hunter,DavidYes Technical859GeneralG-Arch2110Hunter,DavidYes Technical856GeneralG-Arch2111Hunter,DavidYes Editorial856GeneralG-Editor2112Hunter,DavidYes Technical849GeneralG-Base2113Hunter,DavidYes Editorial838GeneralG-Base2114Hunter,DavidYes Editorial836GeneralG-Base2115Hunter,DavidYes Editorial830GeneralG-Arch2116Hunter,DavidYes Editorial828GeneralG-Arch2117Hunter,DavidYes Editorial823GeneralG-Arch2118Hunter,DavidYes Technical816GeneralG-Arch2119Hunter,DavidYes Editorial816GeneralG-Editor2120Hunter,DavidYes Technical815GeneralG-Editor2121Hunter,DavidYes Technical87GeneralG-Editor2122Hunter,DavidYes Technical81GeneralG-Arch2123Hunter,DavidYes Editorial81GeneralG-Editor2124Hunter,DavidYes Editorial764GeneralG-Editor2125Hunter,DavidYes Editorial739GeneralG-Arch2126Hunter,DavidYes Technical733GeneralG-Arch2127Hunter,DavidYes Technical730GeneralG-Arch2128Hunter,DavidYes Technical716GeneralG-Arch2129Hunter,DavidNo Editorial542GeneralG-Editor2130Hunter,DavidYes Technical528MACM-MCCA2131Hunter,DavidYes Editorial515MAC M-PM2132Hunter,DavidYes Editorial51RFIR-General2133Hunter,DavidYes Technical45GeneralG-Arch2134Hunter,DavidYes Technical349RFIR-MeshGate2135Hunter,DavidYes Editorial318GeneralG-Editor2136Bahr,MichaelYes Technical336GeneralG-Base2137Bahr,MichaelYes Technical7.1.3.1.71929MAC M-PM2138Bahr,MichaelYes Technical7.1.3.1.71923MAC M-PM2139Bahr,MichaelYes Technical7.1.3.6.32337GeneralG-Frame2140Bahr,MichaelYes Technical7.3.2379GeneralG-Frame2141Bahr,MichaelNo Technical7.3.23761GeneralG-Editor2142Bahr,MichaelYes Technical7.3.23761MACM-MCCA2143Bahr,MichaelYes Technical7.3.23739MACM-MCCA2144Bahr,MichaelYes Technical7.3.23737MACM-MCCA2145Bahr,MichaelNo Editorial7.3.2.904145GeneralG-Emergency2146Bahr,MichaelYes Technical7.3.2.98.74547GeneralG-Frame2147Bahr,MichaelYes Technical7.3.2.98.94655GeneralG-General2148Bahr,MichaelYes Technical7.3.2.1055221MAC M-BS2149Bahr,MichaelNo Editorial7.3.2.1085464MACM-MCCA2150Bahr,MichaelNo Editorial7.3.2.1085440MACM-MCCA2151Bahr,MichaelNo Editorial7.3.2.1085440MACM-MCCA2152Bahr,MichaelNo Editorial7.3.2.1085536MACM-MCCA2153Bahr,MichaelNo Editorial7.3.2.1085526MACM-MCCA2154Bahr,MichaelNo Editorial7.3.2.1085510MACM-MCCA2155Bahr,MichaelNo Technical7.3.2.109.25664MACM-MCCA2156Bahr,MichaelNo Technical7.3.2.109.25660MACM-MCCA2157Bahr,MichaelNo Editorial7.3.2.109.15632MACM-MCCA2158Bahr,MichaelNo Editorial7.3.2.109.15623MACM-MCCA2159Bahr,MichaelNo Editorial7.3.2.109.15616MACM-MCCA2160Bahr,MichaelNo Editorial7.3.2.109.35728MACM-MCCA2161Bahr,MichaelNo Technical7.3.2.109.35725MACM-MCCA2162Bahr,MichaelNo Technical7.3.2.109.2571MACM-MCCA2163Bahr,MichaelNo Editorial7.3.2.1136047RFIR-MeshGate2164Bahr,MichaelNo Technical7.3.2.1166513RFIR-Proxy2165Bahr,MichaelNo Editorial7.4.15784MACM-MCCA2166Bahr,MichaelNo Editorial7.4.15.97958MACM-MCCA2167Bahr,MichaelNo Editorial9.9a.3.211343MACM-MCCA2168Bahr,MichaelYes Technical9.9a.3.111334MACM-MCCA2169Bahr,MichaelNo Technical9.9a.3.111339MACM-MCCA2170Bahr,MichaelNo Editorial9.9a.3.111315MACM-MCCA2171Bahr,MichaelNo Editorial9.9a.3.311416MACM-MCCA2172Bahr,MichaelNo Editorial9.9a.3.7.4b12060MACM-MCCA2173Bahr,MichaelNo Editorial9.9a.3.7.4a12040MACM-MCCA2174Bahr,MichaelNo Editorial9.9a.3.7.412022MACM-MCCA2175Bahr,MichaelNo Editorial9.9a.3.7.4b1215MACM-MCCA2176Bahr,MichaelNo Editorial9.9a.3.1012427MACM-MCCA2177Bahr,MichaelNo Technical9.22.212558RFI R-FWD2178Bahr,MichaelNo Technical9.22.212616RFI R-FWD2179Bahr,MichaelNo Editorial9.22.312754RFI R-FWD2180Bahr,MichaelNo Technical10.3.81.1.216318MACM-MCCA2181Bahr,MichaelNo Editorial10.3.81.7.116852MACM-MCCA2182Bahr,MichaelNo Editorial10.3.81.8.216959MACM-MCCA2183Bahr,MichaelNo Editorial10.3.81.8.216953MACM-MCCA2184Bahr,MichaelNo Editorial10.3.81.7.316918MACM-MCCA2185Bahr,MichaelNo Editorial10.3.81.8.216941MACM-MCCA2186Bahr,MichaelNo Editorial10.3.81.10.217127MACM-MCCA2187Bahr,MichaelNo Editorial10.3.81.10.217115MACM-MCCA2188Bahr,MichaelYes Technical11.119034MAC M-BS2189Bahr,MichaelYes Technical11.1.319035MAC M-BS2190Bahr,MichaelYes Technical11.119034MAC M-BS2191Bahr,MichaelNo Editorial11.1.1.319026MAC M-BS2192Bahr,MichaelNo Technical11.1.1.319029MAC M-BS2193Bahr,MichaelNo Editorial11C.9.723762GeneralG-Editor2194Bahr,MichaelYes Technical11C.9.8.323961RFIR-HWMP2195Bahr,MichaelYes Technical11C.9.9.324249RFIR-HWMP2196Bahr,MichaelYes Technical11C.9.9.324357RFIR-HWMP2197Bahr,MichaelYes Technical11C.9.9.324615RFIR-HWMP2198Bahr,MichaelYes Technical11C.9.9.4.325119RFIR-HWMP2199Bahr,MichaelNo Technical11C.9.11.325746RFIR-HWMP2200Bahr,MichaelNo Technical11C.9.11.325952RFIR-HWMP2201Bahr,MichaelYes Technical11C.9.11.4.326044RFIR-HWMP2202Bahr,MichaelYes Technical11C.9.11.4.326038RFIR-HWMP2203Bahr,MichaelYes Technical11C.9.11.4.326033RFIR-HWMP2204Bahr,MichaelNo Technical11C.10.4.326910RFIR-Proxy2205Bahr,MichaelNo Technical11C.12.2.2.127340MAC M-BS2206Bahr,MichaelYes Technical11C.12.2.2.127337MAC M-BS2207Bahr,MichaelNo Technical11C.12.2.2.227354MAC M-BS2208Bahr,MichaelNo Technical11C.12.2.127311MAC M-BS2209Bahr,MichaelNo Technical11C.12.2.227322MAC M-BS2210Bahr,MichaelNo Editorial11C.12.2.2.227365MAC M-BS2211Bahr,MichaelNo Technical11C.12.2.2.127332MAC M-BS2212Bahr,MichaelYes Technical11C.12.2.2.327424MAC M-BS2213Bahr,MichaelNo Technical11C.12.2.2.22741MAC M-BS2214Bahr,MichaelNo Technical11C.12.2.2.327463MAC M-BS2215Bahr,MichaelYes Technical11C.12.2.2.327456MAC M-BS2216Bahr,MichaelYes Technical11C.12.2.2.327457MAC M-BS2217Bahr,MichaelYes Technical11C.12.2.2.327437MAC M-BS2218Bahr,MichaelNo Technical11C.12.2.2.327424MAC M-BS2219Bahr,MichaelYes Technical11C.12.2.2.327435MAC M-BS2220Bahr,MichaelYes Technical11C.12.2.2.327456MAC M-BS2221Bahr,MichaelYes Technical11C.12.2.2.327446MAC M-BS2222Bahr,MichaelNo Technical11C.12.2.2.327430MAC M-BS2223Bahr,MichaelNo Technical11C.12.2.2.227417MAC M-BS2224Bahr,MichaelNo Editorial11C.12.2.2.22746MAC M-BS2225Bahr,MichaelNo Technical11C.12.3.127513MAC M-BS2226Bahr,MichaelNo Technical11C.12.3.227530MAC M-BS2227Bahr,MichaelNo Editorial11C.12.4.127564MAC M-BS2228Bahr,MichaelNo Technical11C.12.4.127562MAC M-BS2229Bahr,MichaelNo Editorial11C.12.3.227530MAC M-BS2230Bahr,MichaelNo General11C.12.3.227540MAC M-BS2231Bahr,MichaelNo Editorial11C.12.3.227534MAC M-BS2232Bahr,MichaelYes Technical11C.12.4.2.327665MAC M-BS2233Bahr,MichaelNo Editorial11C.12.4.2.327663MAC M-BS2234Bahr,MichaelYes Technical11C.12.4.2.227654MAC M-BS2235Bahr,MichaelNo Technical11C.12.4.2.227652MAC M-BS2236Bahr,MichaelNo Editorial11C.12.4.2.227640MAC M-BS2237Bahr,MichaelNo Editorial11C.12.4.2.227634MAC M-BS2238Bahr,MichaelNo Technical11C.12.4.2.127611MAC M-BS2239Bahr,MichaelNo Technical11C.12.4.2.12768MAC M-BS2240Bahr,MichaelNo Technical11C.12.4.2.12767MAC M-BS2241Bahr,MichaelYes Technical11C.12.4.22761MAC M-BS2242Bahr,MichaelNo Editorial11C.12.4.2.427755MAC M-BS2243Bahr,MichaelNo Editorial11C.12.4.2.427749MAC M-BS2244Bahr,MichaelNo Editorial11C.12.4.2.427748MAC M-BS2245Bahr,MichaelNo Editorial11C.12.4.2.427735MAC M-BS2246Bahr,MichaelNo Editorial11C.12.4.2.427734MAC M-BS2247Bahr,MichaelNo Editorial11C.12.4.2.427734MAC M-BS2248Bahr,MichaelNo Editorial11C.12.4.2.427732MAC M-BS2249Bahr,MichaelNo Editorial11C.12.4.2.32771MAC M-BS2250Bahr,MichaelNo Technical11C.12.4.2.32771MAC M-BS2251Bahr,MichaelNo Editorial11C.12.4.327864MAC M-BS2252Bahr,MichaelNo Technical11C.12.4.327856MAC M-BS2253Bahr,MichaelNo Technical11C.12.4.2.527817MAC M-BS2254Bahr,MichaelYes Technical11C.12.4.2.527815MAC M-BS2255Bahr,MichaelNo Editorial11C.12.4.2.527848MAC M-BS2256Bahr,MichaelNo Technical11C.12.4.2.527843MAC M-BS2257Bahr,MichaelNo Editorial11C.12.4.2.527829MAC M-BS2258Bahr,MichaelNo Editorial11C.12.4.2.527821MAC M-BS2259Bahr,MichaelNo Editorial11C.12.4.2.42781MAC M-BS2260Bahr,MichaelYes Technical11C.12.4.4.127923MAC M-BS2261Bahr,MichaelNo Technical11C.12.4.4.127922MAC M-BS2262Bahr,MichaelYes Technical11C.12.4.4.127915MAC M-BS2263Bahr,MichaelNo Editorial11C.12.4.4.127915MAC M-BS2264Bahr,MichaelYes Technical11C.12.4.32792MAC M-BS2265Bahr,MichaelNo Editorial11C.12.4.4.327953MAC M-BS2266Bahr,MichaelYes Technical11C.12.4.4.327962MAC M-BS2267Bahr,MichaelYes Technical11C.12.4.4.327958MAC M-BS2268Bahr,MichaelNo Technical D31310MACM-MCCA2269Bahr,MichaelNo Technical Y.733549RFIR-HWMP2270Strutt,GuenaelNo Technical11C.4.320814SecurityS-MPM2271Strutt,GuenaelNo Technical11C.4.220644SecurityS-MPM2272Strutt,GuenaelNo General11C.4.220644SecurityS-MPM2273Strutt,GuenaelNo Technical11C.3.220359SecurityS-MPM2274Strutt,GuenaelNo General11C.4.3.420949SecurityS-MPM2275Strutt,GuenaelNo General11C.4.3.320918SecurityS-MPM2276Strutt,GuenaelNo General11C.4.3.220844SecurityS-MPM2277Strutt,GuenaelNo Technical11C.32039SecurityS-MPM2278Sakoda,KazuyukiNo Technical11C.82311RFI R-LM2279Sakoda,KazuyukiNo Technical11.319152GeneralG-General2280Sakoda,KazuyukiNo Technical10.3.85.2.218325RFI R-LM2281Sakoda,KazuyukiNo Technical9.9.1.211232MACM-General2282Sakoda,KazuyukiNo Technical7.4.15.17513GeneralG-Frame2283Sakoda,KazuyukiNo Technical7.3.2.1166534RFIR-Proxy2284Sakoda,KazuyukiNo Technical7.2.3.103259SecurityS-General2285Sakoda,KazuyukiNo Technical5.2.3.1721GeneralG-Base2286Sakoda,KazuyukiNo Editorial 5.2.14.4108GeneralG-Base2287Sakoda,KazuyukiNo Editorial 5.2.14.498GeneralG-Base2288Malinen,JouniNo Editorial8.2a.7.2.49351SecurityS-General2289Malinen,JouniNo Technical7.3.23761MACM-MCCA2290Housley,RussellYes Technical11C.3.2.1SecurityS-General2291Mccann,StephenNo Technical11.23.61976GeneralG-EmergencyComment Proposed Change Resoluti on StatusNames of state machines do not need to be in caps.Replace the figure name with "Table 11C-3--Finite state machine of the authenticated mesh peering exchange protocol"Names of state machines do not need to be in caps.Replace the table name with "Table 11C-2--Authenticated mesh peering exchange finite state machine"English clean up.Replace "element" with "elements"after both "RSN" and "AMPE".Insert "the" before "Authenticated"and, since the following terms do notrefer to the field names, on lines 61through 64 replace "AuthenticatedMesh Peering Exchange" with"authenticated mesh peeringexchange".(twice) and "Mesh PeeringManagement" with "mesh peeringThe capitalized names do not refer to frame, field, primitve, etc. names.Replace "Authenticated Mesh Peering Exchange" with "authenticated mesh peering exchange".and "Mesh Peering Management" with "mesh peering management" throughout the draft when the terms do not directly refer to frames, fields, primitive names, etc.In this heading "exchange" is not Replace "Mesh Peering Management"with "mesh peering management". The indicator "the" for the peer STAbrings up the question "which one?".Replace "the peer" with "its peer".Need colon.Place a colon at the end of the line. Passive.Replace "When verifying .. followed:"with:"When the mesh STA verifies a MeshPeering Management frame, it shallfollow the procedure:"Need period.Place a period at the end of the line. Need colon.Place a colon at the end of the line.Passive.Replace "When constructing ...followed:" with "When the mesh STAconstructs a Mesh PeeringManagement frame, it shall follow theRequirements can't be stated in informative notes, and "required" and "must" are both deprecated in IEEE Replace "NOTE--" with "Note that". Replace "is required to" with "shall". Replace "must" with "shall".Need a pause after "FAIL".Insert a comma after "FAIL". Subortinate clause needs a comma.Insert a comma after "authenticating"In references to action frames, the word "Action" is not capitalized.Replace "Action" with "action" on both lines 29 and 40."protection in the Mesh Peering Open action frame' sounds like the protection is inside the frame.Replace this complete paragraph with "A mesh STA shall announce in a Mesh Peering Open action frame the group cipher suite it uses for broadcast protection. When it receives a Mesh Peering Open frame from a candidate peer, it shall verify that it supports the candidate's announced group cipher suite . In addition, if the mesh STA receives a Mesh Peering Confirm frame, it shall verify that it supports the group cipher suite listed in that frame. If either selection fails, the mesh STA shall issue the appropriate reply frame with the MESH-INVALID-SECURITY-CAPABILITY reason code.""selector of the selected"""if generating" is not clear enough.Insert "it is" before "generating". Passive.Insert "the mesh STA shall generatethe" before "failure" and delete "shallbe generated".Confusing writing Replace "the chosen pairwise ciphersuites as the result of step b). If theydo not match," with "the pariwisecipher suite chosen in step b). Ifthere is no match,".Passive.Insert "the mesh STA shall generatethe" before "failure" and delete "shallbe generated"."chosen" needs to be closer to the name of the entity doing the choosing.Move "chosen" from its current location to one immediately following "suite".Too many repetitions of "the mesh STA" for clarity.Replace "the mesh STA supports" with "it supports" (since it is clear that this reference is the decisionmaker mesh STA)."STA with the largest" is vague.Replace "with" with "that has" andreplace "in the lexicographic ordering"with "(in lexicographic order)"."not empty and contains more than oneentry" is redundant.Delete "is not empty and".Missing indicator and passive.Replace "and" with ", the mesh STAgenerates the" before "failure" andreplace "shall be generated andcorresponding actions shall be takenaccording to" with " and then takesthe corresponding actions specified English clean up.Replace "shall independently makedecision on" with "shall make itsdecision about" and "based onintersection" with "based on theintersection".Missing indicator.Insert "the" before "last".Bulky writing.Replace "most preferred cipher suiteby the mesh STA" with "mesh STA'smost preferred cipher suite".In references to action frames, the word "Action" is not capitalized.Replace "Action" with "action" on both lines 29 and 40.Misplaced apostrophe.Replace "STAs'" with "STA's" as thisrefers to a single STA. Alternatively,could replace just with "STA"."Mesh" in "Mesh TKSA" does not need to be capitalized.Replace "Mesh TKSA" with "mesh TKSA"."via the active authenticaion protocol" is confusing at best.Delete "via the active authentication protocol" as that concept is incorporated in "initiation of the protocol".In this heading "Authenticated Mesh Peering Management" does not refer to a frame, field, primitive name, parameter name, etc.Replace "Authenticated Mesh Peering Exchange" with "Authenticated mesh peering exchange" throughout the draft, whenever this term does not apply directly to a frame, field, primitive name, etc."NOTE--" is used only with informative statements, while "is required to" and "must" indicate normative behavior.Replace "NOTE--" with "Note that". Replace "is required to" with "shall". Replace "must" with "shall".Antecedent clause needs a comma.Insert a comma after "STA". "must" is deprecated in IEEE standards.Replace "must be" with "is". Antecedent clause needs a comma.Insert a comma after "AMPE". "must" is deprecated in IEEE standards.Replace "must" with "shall". "must" is deprecated in IEEE standards.Replace "must" with "shall".In the 802.11 naming style "MLME-" primitive names are in all-caps.Replace "MLME-MWMPMeshPathSelection" with "MLME-MWMPMESHPATHSELECTION"In the 802.11 naming style "MLME-" primitive names are in all-caps.Replace "MLME-MeshLinkMetricReport" with "MLME-MESHLINKMETRICREPORT" throughout the draft.In the 802.11 naming style "MLME-" primitive names are in all-caps.Replace "MLME-MeshLinkMetricRead" with "MLME-MESHLINKMETRICREAD" throughoutIn the 802.11 naming style "MLME-" primitive names are in all-caps.Replace "MLME-MBSSGateAnnouncement" with "MLME-MBSSGATEANNOUNCEMENT"In the 802.11 naming style "MLME-" primitive names are in all-caps.Replace "MLME-MBSSProxyUpdate" with "MLME-MBSSPROXYUPDATE" throughout the draft.In the 802.11 naming style "MLME-" primitive names are in all-caps.Replace "MLME-MBSSCongestonControl" with "MLME-MBSSCONGESTIONCONTROL"。
北外2012年硕士研究生入学考试试题

北外2012年硕士研究生入学考试试题招生专业:英语同声传译科目名称:英汉互译一、将下列段落译为汉语Fifteen years ago at the Fourth World Conference on Women. Governments pledged to advance equality, development and peace for all women everywhere. The landmark Beijing Declaration has had a deep and wide-ranging impact. It has guided policymaking and inspired new national laws. It has sent a clear message to women and girls around the world that equality and opportunity are their inalienable rights. There are many examples of progress, thanks in large part to the resolute efforts of civil society organizations. A growing number of countries have legislation that supports sexual and reproductive health and promotes gender equality.Nonetheless, much work remains. Maternal mortality remains unacceptably high, too few women have access to family planning, and violence against women remains a cause for global shame. In particular, sexual violence during conflict is endemic.One key lesson of the past decade and a half is the importance of addressing broader discrimination and injustice. Gender stereotyping and discrimination remain common in all cultures and communities. Early and forced marriage. sexual abuse and trafficking of young women andgirls are disturbingly prevalent and, in some areas, on the rise. Whether looking through the lens of poverty. or in times of disaster, we see that women still bear the greatest burden.15年前,在第四次妇女问题世界会议上,各国政府承诺为造福世界各地所有妇女而推进平等、发展与和平。
外文翻译

Accurate Computation of a Streamflow Drought IndexSergio M.Vicente-Serrano 1;Juan I.López-Moreno 2;Santiago Beguería 3;Jorge Lorenzo-Lacruz 4;Cesar Azorin-Molina 5;and Enrique Morán-Tejeda 6Abstract:In this study,the authors investigated an approach to calculate the standardized streamflow index (SSI),which allows accurate spatial and temporal comparison of the hydrological conditions of a stream or set of streams.For this purpose,the capability of six three-parameter distributions (lognormal,Pearson Type III,log-logistic,general extreme value,generalized Pareto,and Weibull)and two different approaches to select the most suitable distribution the best monthly fit (BMF)and the minimum orthogonal distance (MD),were tested by using a monthly streamflow data set for the Ebro Basin (Spain).This large Mediterranean basin is characterized by high variability in the magnitude of streamflows and in seasonal regimes.The results show that the most commonly used probability distributions for flow frequency analysis provided good fits to the streamflow series.Thus,the visual inspection of the L -moment diagrams and the results of the Kolmogorov-Smirnov test did not enable the selection of a single optimum probability distribution.However,no single probability distri-bution for all the series was suitable for obtaining a robust standardized streamflow series because each of the distributions had one or more limitations.The BMF and MD approaches improved the results in the expected average,standard deviation,and the frequencies of extreme events of the SSI series in relation to the selection of a unique distribution for each station.The BMF and MD approaches involved using different probability distributions for each gauging station and month of the year to calculate the SSI.Both approaches are easy to apply and they provide very similar results in the quality of the obtained hydrological drought indexes.The proposed procedures are very flexible for analyses involving contrasting hydrological regimes and flow characteristics.DOI:10.1061/(ASCE)HE.1943-5584.0000433.©2012American Society of Civil Engineers.CE Database subject headings:Droughts;River flow;Streamflow;Precipitation;Runoff;Low flow.Author keywords:Hydrological drought;River flows;Standardized streamflow index;Standardized precipitation index;Low flows;Runoff index;Flow index.IntroductionDrought is one of the greatest natural hazards,affecting many sec-tors and systems and having major effects on agriculture,water resources,and natural ecosystems.Droughts affect many people worldwide,are responsible for famine,epidemics,and land degra-dation in developing countries (Obasi 1994;Nicholson 2001),andcause large economic losses in developed regions (Meehl et al.2000;Fink et al.2004;United Nations 2008).Drought is a natural phenomenon that occurs when water avail-ability is significantly below normal levels over a long period and cannot meet demand (Havens 1954;Redmond 2002).Drought conditions are much more difficult to identify than other natural hazards because drought is commonly the result of a number of factors that are only apparent after a long period of precipitation deficit.It is consequently very difficult to determine the onset,the extent,and the end of droughts (Wilhite 1993).In contrast to other natural hazards (including floods)that are typically restricted to small regions and occur over well-defined temporal intervals,drought is difficult to pinpoint in time and space because it affects wide areas over long time periods.It is moreover very difficult to objectively quantify a drought ’s severity,which is a combination of the duration,magnitude,and spatial extent of a drought (Dracup et al.1980).Much effort has been devoted to developing robust approaches to calculate climate drought indexes (see a review in Heim 2002)because they have the potential to accurately quantify the severity of droughts in magnitude,duration,and spatial extent.A key fea-ture of drought indexes is that they must enable the severity of droughts in different locations to be compared independently of the local climatic characteristics.Therefore,the procedures for quantifying climate drought conditions are commonly calculated by using standardized series (z -scores with the average ¼0and a standard deviation ¼1)from the magnitudes of hydroclimatic variables of interest,which include precipitation and water balances.This enables the relative severity of water deficits to1Tenured Scientist,Instituto Pirenaico de Ecología,CSIC (Spanish National Research Council),Campus de Aula Dei,P.O.Box 202,Zaragoza 50080,Spain (corresponding author).E-mail:svicen@ipe.csic.es 2Tenured Scientist,Instituto Pirenaico de Ecología,CSIC (Spanish National Research Council),Campus de Aula Dei,P.O.Box 202,Zaragoza 50080,Spain.3Tenured Scientist,Estación Experimental de Aula Dei CSIC (Spanish National Research Council),Campus de Aula Dei,P.O.Box 202,Zaragoza,Spain.4Predoctoral Fellowship,Instituto Pirenaico de Ecología,CSIC (Spanish National Research Council),Campus de Aula Dei,P.O.Box 202,Zaragoza 50080,Spain.5Postdoctoral Assistant,Instituto Pirenaico de Ecología,CSIC (Spanish National Research Council),Campus de Aula Dei,P.O.Box 202,Zaragoza 50080,Spain.6Postdoctoral Fellowship,Instituto Pirenaico de Ecología,CSIC (Spanish National Research Council),Campus de Aula Dei,P.O.Box 202,Zaragoza 50080,Spain.Note.This manuscript was submitted on September 20,2010;approved on May 19,2011;published online on May 21,2011.Discussion period open until July 1,2012;separate discussions must be submitted for indi-vidual papers.This paper is part of the Journal of Hydrologic Engineer-ing ,V ol.17,No.2,February 1,2012.©ASCE,ISSN 1084-0699/2012/2-318–332/$25.00.J . H y d r o l . E n g . 2012.17:318-332.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y H e f e i U n i v e r s i t y O f T e c h n o l o g y o n 07/19/12. F o r p e r s o n a l u s e o n l y .N o o t h e r u s e s w i t h o u t p e r m i s s i o n . C o p y r i g h t (c ) 2012. A m e r i c a n S o c i e t y o f C i v i l E n g i n e e r s . A l l r i g h t s r e s e r v e d .be determined independently of the seasonal and spatial character-istics of the variable.Following this approach,a climate drought index can be obtained from long time series by using the cumulative distribution function corresponding to each value i t of the hydroclimatic vari-able of interest.This is commonly obtained by using the probability distribution showing the best fit to the data.For example,calcula-tion of the standardized precipitation index (SPI)(McKee et al.1993),which is a very commonly used climate drought index,is based on the gamma (McKee et al.1993)or the Pearson Type III distribution (Guttman 1999;Vicente-Serrano 2006),whereas calcu-lation of the standardized precipitation evapotranspiration index (SPEI)is based on the log-logistic distribution (Vicente-Serrano et al.2010a ).Several studies have shown that these distributions are able to fit the time series of precipitation and water balance over a wide range of climate regions (Guttman 1999;Vicente-Serrano et al.2010b ).Hydrological drought refers to a decrease in surface or ground water resources-usually river flows,reservoir storages,and aquifers (Tallaksen and Van Lanen 2004).Hydrological droughts can have widespread impacts by reducing or eliminating water supplies,deteriorating water quality,restricting water for irrigation and caus-ing crop failure,reducing power generation,disturbing riparian habitats,limiting recreation activities,and affecting a diversity of economic and social activities (Mishra and Singh 2010).The origin of hydrological droughts is commonly climate droughts (Zaidman et al.2001;Hisdal and Tallaksen 2003;Beersma and Buishand 2004;Vasiliades and Loukas 2009;Edossa et al.2010;Hannaford et al.2011;Lorenzo-Lacruz et al.2010;Vidal et al.2010)however,the quantification of hydrological droughts as independent phenomena has also received much attention in the scientific community.This is because usually no direct spatial or temporal relationship exists between climate and hydrological droughts (Vicente-Serrano and López-Moreno 2005;Tallaksen et al.2009;Hannaford et al.2011;Lorenzo-Lacruz et al.2010;Vidal et al.2010).Moreover,the analysis of hydrological droughts allows direct quantification of the deficits in usable water sources.In contrast to climate droughts,the quantification of hydrolog-ical droughts is not usually on the basis of indexes,but on the theory of runs (Yevjevich 1967).A drought event is defined as a period during which the hydrological variable is below a predetermined truncation level.By using this approach,the duration of drought is the time when the streamflow is below the truncation level,and drought severity is the cumulative deviation below the trunca-tion level during that period.Therefore,the selection of the trun-cation level is critical in defining a drought and can use the average of a series (Dracup et al.1980),a percentile (Zelenhasic and Salvai 1987),or relative values with respect to the average (Clausen and Pearson 1995).Some studies have improved the identification of droughts by considering a mutual dependence among drought events (Tallaksen et al.1997;Fleig et al.2006).This approach has the advantage of considering the real low-flow periods,during which the availability of water is unable to meet demand,with the subsequent environmental and socioeconomic impacts (Smakhtin 2001).Given the contrasting river regimes and flow magnitudes that can occur among neighboring basins,the spatial comparison of drought severity and the development of drought maps are impossible when using the method of runs.This is because the same drought magnitude may have different implications,depend-ing on the basin.In addition,the seasonality of river flows must be taken into account when quantifying hydrological droughts.In riv-ers with high seasonality,the low-flow periods usually correspond to reduced water availability in summer.A reduction in discharges during high flow periods can nevertheless have negative effectson natural systems adapted to a particular river regime.Therefore,relatively low flows during high flow periods can reduce reservoir storages downstream and affect the availability of water resources for certain uses some months later.For these reasons,in addition to the use of low-flow analysis by the run theory (see reviews in Smakhtin 2001;Tallaksen and Van Lanen 2004),it would be advantageous to develop a standardized hydrological drought indi-cator that allows comparisons of drought severity across time and space,including in basins with different characteristics in regimes,flow variability and the magnitude of flows.Such an indicator could be implemented following the same theoretical approach used to calculate climate drought indexes.Stahl (2001)developed the regional deficiency index (RDI)to characterize hydrological droughts.The RDI uses daily flow data and removes the influence of streamflow seasonality on droughts.Nevertheless,the index does not indicate the magnitude of a drought –it only quantifies the duration from a binary time series –and it quantifies drought severity by the surface affected.This makes comparisons of hydrological droughts at different sta-tions impossible.Two hydrological drought indexes have recently been developed that follow the approach commonly used for climate drought indexes.They are the streamflow drought index (Nabaltis and Tsakiris 2009)and the standardized runoff index (Shukla and Wood 2008).These indexes have the same theoretical background because they derive the hydrological drought index by transforming monthly streamflows into z -scores.The problem with this approach is that selecting the most suitable probability distribution to calculate the index and the consequences of the selection on the final series have not been tested in depth.In developing the SPI,various prob-ability distributions were carefully tested to select the most suitable (McKee et al.1993;Guttman 1999).The same approach was fol-lowed in developing the SPEI (Vicente-Serrano et al.2010a ).These studies showed the suitability of the Pearson Type III and log-logistic distributions to fit precipitation and water balance series,respectively,across a wide range of climate regimes and time scales.Streamflow commonly shows a greater spatial variability than climatic variables that are used to derive drought indicators.This is because of the influence of a number of factors,including topog-raphy,lithology,vegetation,and human management;it is also a consequence of the spatial aggregation of the flows,which changes the statistical properties of the series downstream (Mudelsee 2007).Therefore,a high degree of spatial variability occurs in the prob-ability distributions that best fit the monthly streamflow data (Riggs 1973;Kroll and V ogel 2002;Yue and Wang 2004;Yue and Pilon 2005;McMahon et al.2007;Yue and Hashino 2007),which makes it difficult to select the most appropriate distribution to calculate a streamflow drought index over a wide area.In this study,the authors tested the performance of several prob-ability distributions (assuming that each month may fit different probability distributions),to calculate a standardized streamflow index (SSI).This has enabled the authors of this paper to propose an accurate procedure to obtain a hydrological drought index that is useful for making spatial and temporal comparisons over a wide variety of river regimes and flow characteristics.MethodsData SetThe authors used the Ebro River basin (in northeast Spain)to calculate and test the performance of the SSI.This basin is char-acterized by large spatial variability in the river regimes and flowJ . H y d r o l . E n g . 2012.17:318-332.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y H e f e i U n i v e r s i t y O f T e c h n o l o g y o n 07/19/12. F o r p e r s o n a l u s e o n l y .N o o t h e r u s e s w i t h o u t p e r m i s s i o n . C o p y r i g h t (c ) 2012. A m e r i c a n S o c i e t y o f C i v i l E n g i n e e r s . A l l r i g h t s r e s e r v e d .magnitudes.The Ebro basin is the largest in Spain (surface area 85;362km 2)and covers 17.3%of the country.The Ebro River flows from the Cantabrian Range to the Mediterranean Sea;it is the main river in the Ebro basin,with a total length of 910km.The basin is bounded to the north by the Cantabrian Range and the Pyrenees,which have maximum altitudes of more than 3000m above sea level (asl),and by the Iberian Mountains (maximum altitudes 2000–2300m above sea level (asl))enclose by the Ebro basin to the south.The heterogeneous topography and contrasting Atlantic and Mediterranean influences generate a complex spatial distribution of climate parameters and generate large variations in precipitation and evapotranspiration throughout the region (Cuadrat et al.2007;Vicente-Serrano et al.2007).Therefore,the annual precipitation varies from 307to 2;451mm yr À1;most pre-cipitation occurs in the autumn and spring (Cuadrat et al.2007),although in some areas the maximum precipitation occurs in winter and summer (Beguería et al.2009).The average annual tempera-ture varies from 0.8to 16.2°C.The marked differences in topographic and climatic conditions explain the high variability of river flows and regimes.In the head-waters in the Pyrenees and the Iberian Range,the rivers are snow-fed,with flow regimes characterized by marked seasonality.The mid-courses of the rivers are also subject to large seasonal variabil-ity that is driven by dry summers;high flow episodes are common in winter and autumn in response to extreme precipitation events (Ollero et al.2004).The basin is highly regulated,with 126cur-rently active reservoirs.These reservoirs manage the water resour-ces for hydropower production,irrigation,and urban consumption.Most of the dams were built between the 1950s and the 1980s,and their construction increased the storage capacity from 500to 6;500hm 3,which represents 50%of the average annual out-flow to the Mediterranean Sea (in 1945to 2005the average was 12;208hm 3).The Ebro Water Management Agency (Confederación Hidrográfica del Ebro)provided the hydrological records used in this study.The authors used monthly streamflow data from 98of 420gauging stations located across the basin;the data covered the period of 1945to 2005.Selection of the data series followed the criterion that gaps resulting from missing data should not represent more than 10%of the total length of the series.Gaps were filled by multiple linear regression by using highly correlated stations located on the same river or in very close proximity (Hirsch 1982;V ogel and Stedinger 1985).Therefore,the objective series had a Pearson ’s correlation coefficient of at least R ¼0:8.Fig.1shows the spatial distribution of the selected stations.Calculation of the SSIVarious probability distributions have been used to obtain hydro-logical drought indexes.A unique probability distribution is usually selected to fit all the available series and/or variables.For example,Zaidman et al.(2001)used the lognormal distribution to fit river flow series for the period of 1960to 1995for 2781stations from sites in the UK,Ireland,France,Germany,the Netherlands,Belgium,Denmark,Switzerland,Austria,and the Czech Republic.The same distribution was used by Nalbantis and Tsakiris (2009)in the Evinos basin (Greece).Other authors have assessed the performance of various distributions that are used to derive hydrological drought indexes.López-Moreno et al.(2009)andFig.1.Location of the study area and spatial distribution of the gauging stations used in the studyJ . H y d r o l . E n g . 2012.17:318-332.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y H e f e i U n i v e r s i t y O f T e c h n o l o g y o n 07/19/12. F o r p e r s o n a l u s e o n l y .N o o t h e r u s e s w i t h o u t p e r m i s s i o n . C o p y r i g h t (c ) 2012. A m e r i c a n S o c i e t y o f C i v i l E n g i n e e r s . A l l r i g h t s r e s e r v e d .Lorenzo-Lacruz et al.(2010)used the Pearson Type III distribution to fit monthly streamflow series in the central Iberian Peninsula.The same distribution was used by Mo (2008)to obtain standard-ized runoff series in the US.However,Shukla and Wood (2008)noted the role of varying hydroclimatic regimes in the US in rela-tion to selection of the best probability distribution for adjusting the data.They reported that the two-parameter gamma and lognormal distributions generally performed well,and they showed that the three-parameter lognormal and the generalized extreme value dis-tributions were applicable.Some studies have shown that the regionalization of river flows can be established according to a particular probability distribution,with the potential to apply common parameters to the various run-off series (Hosking and Wallis 1993;Bobee et al.1996;Burn 1997;Yue and Wang 2004;Modarres and Sarhadi 2010;Shi et al.2010).The use of a unique probability distribution function for different river sectors and months nevertheless requires high spatial homo-geneity among the series,which is unlikely to be found in rivers with physical characteristics,climatic,hydrological regimes,and hierarchy that differ,even over very short distances.It can therefore be assumed that the most suitable probability distribution to fit individual streamflow series will rge seasonal variations in streamflow characteristics can similarly cause differences in the 12monthly series at a single station.For example,Fig.2shows the frequency histograms of the streamflow series for January,March and May at the Sástago station in the Ebro River;Fig.2also indicates the theoretical probability distributions that show the best fit to the data.This example illustrates how fitting the monthly runoff series from the same location to different distribu-tions can affect the procedure for calculating hydrological drought indexes.In this study,the authors applied two approaches to using prob-ability distributions to obtain a standardized streamflow ing a Unique Distribution of ProbabilityIn the first approach,the authors used a unique probability distribution to fit the monthly streamflow series with independent fitted parameters at each site and month.The authors selected six three-parameter distributions that are widely used in hydrological analysis (Chow et al.1988;Bobée and Ashkar 1991;V ogel et al.1993;Rao and Hamed 2000):the general extreme value (GEV),Pearson Type III (PIII),log-logistic,lognormal,and generalized Pa-reto and Weibull distributions.For example,Fig.3shows the May series for the Sástago station (Ebro River)with the six theoretical distributions that fit the data.The flexibility of having a wide range of distributional shapes,given the three-parameters of the distribu-tions,allows a good fit to the observed frequencies.Therefore,for each streamflow series the authors calculated six SSI series,corre-sponding to each of the six probability distributions.Table 1shows the cumulative distribution functio (Fx)for each of the six selected distributions.The calculation of F ðx Þis essential for obtaining the SSI.The table includes the equations used to cal-culate the parameters of the six probability distributions.These used the L -moment method (see below).Once F ðx Þis calculated,the SSI (in z -scores)can easily be determined by following the classical approximation of Abramowitz and Stegun (1965).For exampleSSI ¼W ÀC 0þC 1W þC 2W 21þd 1W þd 2W 2þd 3W 3;whereW ¼ffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiffiÀ2ln ðP Þp for P ≤0:5P is the probability of exceeding a determined x value,and P ¼1ÀF ðx Þ.If P >0:5,P is replaced by 1ÀP and the signFig.3.Frequency histogram of the May runoff series at the Sástago station (Ebro River)and the curves of the six theoretical distributionsFig.2.Frequency histograms of the runoff series at the Sástago station (Ebro River)and the theoretical curves of the log-logistic,Weibull,and Pearson Type III distributions:(a)January;(b)March;(c)MayJ . H y d r o l . E n g . 2012.17:318-332.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y H e f e i U n i v e r s i t y O f T e c h n o l o g y o n 07/19/12. F o r p e r s o n a l u s e o n l y .N o o t h e r u s e s w i t h o u t p e r m i s s i o n . C o p y r i g h t (c ) 2012. A m e r i c a n S o c i e t y o f C i v i l E n g i n e e r s . A l l r i g h t s r e s e r v e d .of the resultant SSI is reversed.The constants are C 0¼2:515517;C 1¼0:802853;C 2¼0:010328;d 1¼1:432788;d 2¼0:189269;and d 3¼0:001308.If the probability distribution is suitable for fitting the monthly streamflow series,the average value of the SSI and the standard deviation must equal 0and 1,respectively.The SSI is a standardized variable and can therefore be compared with other SSI values across time and space.Using Different Distributions for Each Monthly SeriesThe second approach used the selection of the most suitable probability distribution for each monthly streamflow series.By us-ing this approach an SSI was created for each monthly streamflow series,whereby the 12monthly streamflow series could be fitted by different probability distributions.To select the most suitabledistribution for each series,the authors tested the capability of two different approaches:1.The selection of the most suitable distribution according to L -moment ratio diagrams (Hosking 1990;Peel et al.2001),which gives a visual indication of how well the probability dis-tributions fits the data.The L -moment ratios τ3and τ4are calculated,as follows:τ3¼λ3λ2τ4¼λ4λ2;where λ2,λ3,and λ4are the L -moments of the river flow or reservoir storage series,and are obtained from probability-weighted moments (PWMs)by using the formulasTable 1.Cumulative Distribution Functions of the Generalized Pareto,Log-Logistic,Lognormal,Pearson Type III,General Extreme Value,and Weibull Distributions,and the Equations Used to Obtain the Distribution Parameters in Accordance with the L -moment Procedure Distribution F ðx ÞParameter estimationReferences Generalized ParetoF ðx Þ¼1À½1Àκαðx ÀεÞ 1=κκ¼ð1À3τ3Þð1þτ3Þα¼λ2ð1þκÞð2þκÞε¼λ1Àλ2ð2þκÞHosking (1990)Log-logisticF ðx Þ¼½1þðαx ÀγÞβÀ1β¼2w 1Àw 06w 1Àw 0À6w 2α¼ðw 0À2w 1ÞβΓð1þ1=βÞΓð1À1=βÞγ¼w 0ÀαΓð1þ1=βÞΓð1À1=βÞSingh et al.(1993)LognormalF ðx Þ¼Φ ln ðx Àa ÞÀμσ,where Φis the standard normal cumulativedistribution functionσ¼0:999281z À0:006118z 2þ0:000127z 5z ¼ffiffi8q ΦÀ1 1þτ3μ¼ln h λ2ðσÞiÀσ2erf is the Gauss error function:erf ðσÞ¼2Φðσffiffiffi2p ÞÀ1a ¼λ1Àe μþσ2Hosking (1990)Pearson Type IIIF ðx Þ¼1αΓðβÞR xγðx ÀγαÞβÀ1e Àðx ÀγαÞIf τ3≥1=3,then τm ¼1Àτ3:β¼ð0:36067τm À0:5967τ2m þ0:25361τ3m ÞmmmIf τ3<1=3,then τm ¼3πτ23:β¼ð1þ0:2906τm Þðτm þ0:1882τ2m þ0:0442τ3m Þα¼ffiffiffiπp λ2ΓðβÞΓðβþ1=2Þγ¼λ1ÀαβHosking (1990)GEVF ðx Þ¼e À½1Àκðx ÀμαÞ 1κκ¼7:859C þ2:9554C 2C ¼23À0:6309α¼λ2κΓð1þκÞð1À2ÀκÞμ¼λ1þακ½Γð1þκÞÀ1Hosking et al.(1985)WeibullF ðx Þ¼1Àe Àðx Àm Þbb ¼1C ¼23À0:6309a ¼λ2ΓÀ1þ1ÁÀ1À2À1Ám ¼λ1Àa ΓÀ1þ1ÁHosking (1986)J . H y d r o l . E n g . 2012.17:318-332.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y H e f e i U n i v e r s i t y O f T e c h n o l o g y o n 07/19/12. F o r p e r s o n a l u s e o n l y .N o o t h e r u s e s w i t h o u t p e r m i s s i o n . C o p y r i g h t (c ) 2012. A m e r i c a n S o c i e t y o f C i v i lE n g i n e e r s . A l l r i g h t s r e s e r v e d .Fig.4shows the L -moment ratio diagrams for the runoff monthly series.The symbols group the monthly series by sea-son (i.e.,winter,spring,summer and autumn),which enables visual assessment.The diagram shows that most of the runoff monthly series had a positive skew.However,no clear patterns were evident in relation to the most suitable probability distri-bution to fit the series,suggesting that it was impossible to select a unique probability distribution on the basis of a visual inspection.Kroll and V ogel (2002)used a quantitative ap-proach to select the most suitable distribution to fit low-flow series according to the orthogonal distance between the sample L -moments at site i and the L -moment relationship for a spe-cific distribution.They indicated that the closer the sample L -moment ratios are to a probability distribution ’s L -moment ratio relationship,the choice of distribution is better for describing the series.The authors of the present paper have followed this approach to select the most suitable distribution for each monthly streamflow series,by calculating the ortho-gonal distance between the sample L -moments at site i and the L -moment relationship for the six distributions described previously.The authors always selected the distribution that showed the minimum orthogonal distance to the sample to ob-tain the F ðx Þfor each monthly streamflow series.This method is known as the minimum orthogonal distance (MD).2.The second approach is known as the best monthly fit approach (BMF),which uses the Kolmogorov-Smirnov (KS)test (Siegel and Castelan 1988).This test was used to compare a stream-flow series with a reference probability distribution.It uses theIf the runoff series comes from a given cumulative distri-bution function,then D converges to 0.In other words,smaller values of D imply a better fit of the streamflow series to the probability distribution.Therefore,to obtain the F ðx Þfor each monthly streamflow series,the authors selected the probability distribution that showed the smallest D statistic.The distribu-tion was rejected if D was greater than the critical value (α¼0:05).For the results obtained from each approach,the authors compared the statistical properties of the constructed SSI series by the average,standard deviation,and expected frequencies of the most extreme values.ResultsFig.5shows 12box-plots of the KS D statistic for the monthly streamflow series of the 98stations.On the basis of the critical level (α¼0:05),the six analyzed distributions provided an adequate fit to the streamflow series because the D values were in most cases below the critical value of D ¼0:169.Fig.5shows it is very difficult to determine which probability distribution provides the best fit to the series because there are marked differences among the various months of the year.Fig.6shows 12box-plots with the orthogonal distance between the sample L -moments and the L -moment relationship for each one of the distributions.Some sea-sonal contrasts (e.g.,higher orthogonal distances in the summer than in the winter months)exist,but the main pattern is the large differences between the distributions with low distances for each monthly series.Figs.7and 8moreover indicate no clear spatial pattern in the probability distributions showed the best fit and the minimum dis-tance to the monthly streamflow series,respectively.Therefore,the probability distribution providing the best fit for gauging stations along the same river course often changed.In addition to a large spatial variability,a high seasonal variability existed.The most common situation was to find a different probability distribution that showed the best fit to the streamflow series of each month.No probability distribution showed a better overall fit for a particu-lar region or month.Noticeable differences exist in the selected distributions,in accordance with the BMF or MD approaches.Table 2shows the frequency with which each distribution was selected for each month in accordance with the two different approaches.The num-bers represent the percentage of the monthly streamflow series in which the minimum D statistic of the KS test or the MD is obtained for each distribution.For the BMF,the generalized Pareto distribu-tion showed the best fit for 22%of the series;the lognormal and log-logistic distributions showed the best fit for 18%of the series;and the Weibull showed the best fit for 17%of the series.The two least suitable were the GEV and the PIII distributions,which showed the best fit in 13%and 12%of series,respectively.There were some seasonal differences.For example,the generalized Pareto distribution showed the best fit in the highest percentage (23to 30%)of stations in the spring;the lognormal distributionFig.4.L -moment ratio diagrams in which different symbols represent the statistics of various seasonal series;black triangles represent winter;white triangles,autumn;white circles,summer;and black squares,springJ . H y d r o l . E n g . 2012.17:318-332.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y H e f e i U n i v e r s i t y O f T e c h n o l o g y o n 07/19/12. F o r p e r s o n a l u s e o n l y .N o o t h e r u s e s w i t h o u t p e r m i s s i o n . C o p y r i g h t (c ) 2012. A m e r i c a n S o c i e t y o f C i v i l E n g i n e e r s . A l l r i g h t s r e s e r v e d .。
第七届 “北京外国语大学-《英语世界》杯”翻译大赛英译汉一等奖译文

翻译大赛 1 第七届 “北京外国语大学-《英语世界》杯”翻译大赛英译汉一等奖译文开阔的领地文/[美)奥尔多利奥波德译/蒋怡颖按县书记员的话来说,眼前一百二十英亩的农场是我的领地。
不过,这家伙可贪睡了,不到日上三竿,是断然不会翻看他那些记录薄的。
那么拂晓时分,农场是怎样的一番景象,是个值得讨论的问题。
管他有没有记录在册呢,反正破晓时漫步走过的每一英亩土地都由我一人主宰,这一点我的爱犬也心领神会。
地域上的重重界限消失了,那种被秷楛的压抑感也随之抛诸脑后。
契据和地图上没法标明的无边光景[1],其美妙展现在每天的黎明时分。
而那份独处的悠然,我本以为在这沙郡中已觅而不得,却不想在每一颗露珠上寻到了它的踪影。
和其他大农场主一样,我也有不少佃户。
他们不在乎租金这事,划起领地来却毫不含糊。
从四月到七月,每天拂晓时刻,他们都会向彼此宣告领地界限,同时以此表明他们对我的臣服。
这样的仪式天天有,都在极庄严的礼节中拉开帷幕,这恐怕和你所设想的大相径庭。
究竟是何方神圣立下这些规矩礼仪,我不得而知。
凌晨三点半,我从这七月的拂晓中汲取了威严,昂扬地走出小屋,一手端着咖啡壶,一手拿着笔记本,这两样象征了我对农场的主权。
望着那颗闪烁着白色光辉的启明星,我在一张长椅上坐下,咖啡壶先搁在一旁,又从衬衣前襟的口袋里取出一只杯子,但愿没人注意到,这么携带杯子确实有点随意。
我掏出手表,给自己倒了杯咖啡,接着把笔记本放在膝盖上。
一切就绪,这意味着仪式即将开始。
三点三十五分到了,离我最近的一只原野春雀用清澈的男高音吟唱起来,宣告北到河岸、南至古老马车道的这片短叶松树林,统统都归他所有。
附近的原野春雀也应声唱起歌来,一只接一只地声明着自己的领地。
歌声里没有争执,至少此时此刻没有。
我就这么聆听着,打心眼里希望在这幸福和谐中,他们的雌雀伴侣也能默许原先的领地划分。
原野春雀的吟唱声还在林中回荡,而这边大榆树上的知更鸟已开始鸣l转,歌声哦亮,他在宣告,这被冰暴[2]折断了枝丫的树权是他的地盘,当然附带着周围的一些也归他所有(对这只知更鸟而言,其实就是指树下草地里的所有蚚划,那里并不算宽敞)。
汉译英——北航英文二学位
11.17名词从句1.我不知道你干吗为这么一件小事生这么大的气。
I have no idea why you got so angry aboutsuch a small matter. / It battles me why you hit the roof because of such a trifling matter. / such a trifle2.你知道你的错误给公司造成了多大的损失吗?Do you realize what heavy losses thecompany suffered because of your mistake? / Do you have any idea how much the company paid for your mistake?3.董事们一致认为,除非发生奇迹,公司难逃倒闭的命运。
The directors all agreed thatnothing short of a miracle could save the company from bankruptcy.4.原来他背着我干了这个。
So he did this without my knowledge. / So this is what he didbehind my back.5.只有在紧急情况下才能动用储备基金。
We can use the reserve found only in emergencies. /It is only under emergencies that the reserve found is to be used.6.如今孩子心目中的超级英雄往往令其父母不敢恭维。
Nowadays what the children regardas supe rheroes are often looked upon with distaste by their parents. / Today’s parents usually have a low opinion of what their children regard as superheroes.7.前言中概括论述了读者需要预先掌握什么知识才能透彻理解本书所探讨的课题。
英文翻译
外文翻译工学部工学二部专业机械设计制造及其自动化班级B642132学号B64213202姓名李芳欣指导教师陈伟负责教师沈阳航空工业学院北方科技学院2010年6 月原文:Introduction die casting mold1. Casting process in real terms andPressure die casting is short, and its essence is under pressure to liquid or semi-liquid metal to a high speed filling chamber die casting model, and solidified under pressure forming and casting methods obtained.High pressure and high speed is when the molten alloy die-casting forming process of filling two major characteristics, is also a die-casting and other casting methods, the fundamental difference lies. In addition, the casting mold has high dimensional accuracy and surface roughness is to . Because of the above characteristics, making the structure or quality of casting and die casting process and the performance of ﹑production process has its own characteristics.Alloy die-casting machine and die casting mold die-casting production process are the three basic elements.2. The advantages of casting1)The size of high precision die-castingLow-dimensional precision surface roughness up to IT11 ~ IP13-class, sometimes up to IT9 level. Product interchangeability good.2)High utilization ratioAs the die-casting with precision ﹑size and low surface roughness, generally no longer be directly assembled using mechanical processing, or processing of very small, only a small amount of machining can be assembled through the use of metal so that increased utilization also reduces the amount of processing equipment and working hours.3)Can create a clear outline of complex shape ﹑﹑thin wall deep cavity in the metal parts because the molten metal under high pressure to maintain high liquidity, and thus have access to other processes are difficult to process the metal parts.4)In die-cast parts can be directly embedded in other materials, parts, to save your material and processing timeThis will not only meet the requirement, to expand product applications, but also reduce the workload of assembly to simplify the manufacturing process5)Die casting organizations, intensive, high strength and hardnessBecause the liquid metal is solidified under pressure, because of filling time is very short, fast cooling, so close to the surface of casting a layer of metal grains smaller, organization-intensive, not only to improve the surface hardness and good wear resistance and corrosion resistance.6)Productivity highAs easy to suppress the production mechanization and automation of operation, short production cycle, high efficiency, may be suitable for mass production. In all casting method, die-casting is the most productive way.3. The application of die-castingModern metal casting is to develop faster processing of a high efficiency, low non-cutting metal forming precision casting method. Because of the above advantages of die casting, this technology approach has been widely applied in all walks of life in thenational economy . die-casting except for automobiles and motorcycles, instruments, industrial electronics, but also widely used in household appliances, farm machinery, radio, telecommunications, machine tools, transportation, shipbuilding, cameras, watches, computers, textile equipment and other industries. including automobiles and Motorcycle manufacturing is the most important areas of application, about 70% of cars, motorcycles accounted for about 10%.Some die-casting parts currently produced only a few grams of the smallest, the largest aluminum alloy casting, see the quality up to 50kg, the largest diameter of up to 2m.Current methods used to produce aluminum die casting, zinc, magnesium and copper alloys. Based on the characteristics of die-casting process, because there are not any good high temperature die materials, ferrous metal die-casting is still in the research trials. Non-ferrous alloy die casting in the aluminum alloy had the highest rate; zinc alloy followed. But with the development of automotive electronic communications industry and product requirements of lightweight, magnesium alloy die-casting technology coupled with the recent maturing, so that magnesium alloy die-casting market attention. now in the world have formed a certain scale of the automobile industry, IT industry, infrastructure, parts of the magnesium alloy production groups,The application of magnesium alloy die castings gradually increased its production significantly increased, and there will be greater development is expected in the future.4. Die Casting Design1)Die casting process on the structure of the requirementsThe quality of die casting process not only by various factors, the structural design process of its parts is a very important factor of its structure and process rationality determines the order for the work can proceed smoothly. If the choice of parting, runner design, layout introduction agencies, Shrinkage control ﹑guarantee the accuracy, the type and extent of defects are casting and casting their own advantages and disadvantages of the related technology.Casting a direct impact on the structural design of the structural design of the die casting mold and ease of manufacturing productivity and die life ﹑fields, so in the design of die casting of many adverse factors are considered and be excluded in advance. If designers are familiar with the casting process, then the design of the structure of die castings is usually quite satisfied. Design die-casting to consider the following questions when.2)Castings basic design of the basic structureCompact thin wall castings, and can increase the relative strength and abrasion resistance. Die-casting wall thickness increases and the internal defects such as porosity ﹑shrinkage also increased, thus guaranteeing the casting of sufficient strength and stiffness of the premise should be to minimize the thickness of thin and add ribs to resolve. Design of reinforcement to increase strength and rigidity of parts, but also to improve the casting process, to reveal smooth metal, to eliminate relying solely on increasing the pore wall thickness and contraction caused by defects. Rib thickness should not exceed the thickness of the wall connected with desirable thickness of unreinforced Office 2 / 3 3 / 4. When the casting wall thickness less than 2mm, the easy to feel suffocated in the baroffice,It is not appropriate based reinforcement; such as bars to be set, will enable the tendons connected to office with wall thickening.Although the wall thick casting casting quality of the negative impact, but not too thin, otherwise the liquid filling bad metal, casting forming difficult. Casting appropriate thickness; aluminum alloy for the 1 ~ 6mm, zinc alloy for the 1 ~ 4mm, magnesium alloy is 1.5 ~ 5mm, copper alloy for the 2 ~ 5mm.Wall and the wall, die-casting parts in the junction, whether acute or obtuse angle ﹑should be designed to be rounded, and only when the estimated selected as the site of the parting was not connected with rounded corners. Casting corner help the flow of molten metal to reduce the eddy current, gas easily discharged, help shape; while avoiding the sharp corners of office stress concentration and cracking. On the need for plating and coating of the die-casting is more important is to obtain uniform coating and rounded corners to prevent sharp corners Office indispensable condition for the deposition. The terms mold, casting mold corner to extend the use of time. No stress concentration will occur casting corner, die easily collapse angleThis phenomenon of high melting point alloy (such as copper alloy) is particularly noteworthy.For the parts required by the principle of the use of selected out of the corner is too large, then the preferred slightly smaller, but the connection should be not less than half of the thinnest wall thickness. For smaller radius, though it can die out, but only in the special purpose use only small parts of the fillet, then r = 0.3 ~ 0.5mm.3)Stripping gradientFor ease of casting extrusion mold cavity and core, die-casting should be as large as possible with adequate and stripping slope. Preferably in the part design, to take into account the slope. Stripping gradient of size and geometry, such as casting ﹑wall thickness and height or depth of the cavity, or cores, such as surface roughness of the surface state. Within the allowable range, the larger the ejection should slope to reduce the required impetus4)Cast hole designOne of the features die-casting process is more directly cast a deep hole. Parts Die hole diameter and depth of a certain relationship between the small aperture can only die shallower depth. Molten metal filling process will be the impact of cores, and make it in the state of the thermal stress, deterioration of working conditions. After the metal casting mold filling solidification contraction of the die on the cores (for die-casting parts Kong) have a great hold of power, while the slender cores are often unable to withstand such force and contractility Hold role of the bent and broken. So when the part design, die casting out hole diameter should not be too small,And should also be considered an appropriate pore size and depth consistent with the ratio between the same time, the hole should be slightly larger slope.As the pitch size of the space where the wall thickness ﹑and cores forming the root of the fillet (or angle) is the force of the cores have a great impact, so pitch the greater the hole where the wall thickness of more thick, rounded cores forming the root of the smallerhole depth should be shallower. This is, for the thick-walled castings and large castings should pay attention.5)Die insertsCasting can be cast into metal or non-metallic die-casting parts on the workpiece, so that a part of die casting can have a special nature or purpose. The inserts cast into the shape of a lot, usually screw (screw gauge) axis ﹑﹑﹑nut holder, such as tubular ﹑sheet workpieces. The materials are mostly copper, iron and non-metallic materials, steel ﹑also useful for performance than metal casting itself, or with a special character (such as wear-resistant conductive ﹑﹑﹑magnetic insulation, etc.)5. The basic structure and die-casting mold parting surface designCasting mold is important to ensure the quality of die casting process and equipment, which directly affects the shape, size casting accuracy ﹑﹑surface quality. Casting production process can proceed smoothly, whether casting quality assurance, to a large extent depend on the structure of die casting mold rationality and technological advance. In the die casting mold design process, the structure must be a comprehensive analysis of die casting, die-casting machine and die-casting process to understand and master the different casting conditions, the metal filling characteristics and mobility to, and taking into account economic factors, to design a realistic and meet the production requirements of the casting mold.Die Die Die by the fixed mold and the dynamic of two major components. Fixed in the fixed mold die-casting machine scheduled to die mounting plate, pouring system connected with the pressure chamber. Fixed in the die casting machine dynamic model of dynamic module mounting plate, with the dynamic model will be fitted with plate movement ﹑mold mold mold. Clamping time, the dynamic model and fixed model to separate open the body cavity of the die-casting from the launch.Die Die Die dynamic mode and set the combination of the surface is called sub-surface. Sub-surface design is die-casting mold design an important part. Sub-surface and casting of the shape and size ﹑die casting in the casting mold is closely related to the location and direction. Determination of sub-surface structure of the die-casting and die casting mold will have a great impact on quality.In accordance with the shape of sub-surface, sub surface generally can be divided into straight parting parting ﹑ladder inclined surface and surface sub-sub-surface.Casting mold is usually only a sub-surface, known as the single sub-surface; but sometimes because the special structure of die casting, die casting or production process to meet the requirements, often need to add one or two secondary sub-surface, said for the multisection surface. Multisection single surface can be a variety of sub-surface combinatorial synthesis. The choice of sub-surface structure of the die casting mold and die casting dimensional accuracy has a decisive influence. The choice of sub-surface structure of the die casting mold and casting quality is multifaceted and must be a reasonable choice under the circumstances.译文:压铸模介绍一.压铸的实质及工艺过程压铸是压力铸造的简称,其实质是在高压作用下,使液态或半液态金属以较高的速度充填压铸模型腔,并在压力下成形和凝固而获得铸件的方法.高压力和高速度是压铸时熔融合金充填成形过程的两大特点,也是压铸与其他铸造方法最根本的区别所在.此外,压铸模具有很高的尺寸精度和很地的表面粗糙度值.由于具有以上所述特点,使得压铸件的结构﹑质量和有关性能﹑压铸工艺以及生产过程都具有自己的特征.合金材料﹑压铸机及压铸模是压铸生产工艺过程的三个基本要素.二.压铸的优点1、压铸件的尺寸精度高表面粗糙度值低尺寸精度可达IT11~IP13级,有时可达IT9级。
北京航空航天大学翻译硕士英语2012
北京航空航天大学2012年翻译硕士英语考研真题Part I Vocabulary (60 minutes, 30%)Directions: There are 30 incomplete sentences in this part. For each sentence there are four choices marked A, B, C and D. Choose the ONE answer that best completes the sentence.1. The doctor _______a medicine for my headache.A) subscribedB) describedC) prescribedD) inscribed2. This song _______his life’s dream and ardent love of life.A) incorporatedB) initiatedC) exposedD) embodied3. It is said that the reconstruction of the Grand Theatre is a _______project of Shanghai government this year.A) prestigeB) superiorityC) priorityD) publicity4. Such a toy with musical sounds and animal noises will ________any young child.A) dismayB) astonishC) fascinateD) perplex5. After reading ______of books by great authors for some time, the boy decided to go on to read the originals.A) themesB) insightsC) digestsD) leaflets6. In the poem, he depicted the happy ________of girls playing on a swing in early spring.A) perspectiveB) viewC) landscapeD) scene7. She _______all criticism and went on with her project.A) warded offB) shrugged offC) gave awayD) set aside8. The teacher ________from her custom and gave no assignments for the weekend.A) deviatedB) disconnectedC) detachedD) distorted9. The little chair _______when the fat man sat down on it without thinking.A) crushedB) collapsedC) crumpledD) yielded10. Her chief _______was her not packing a raincoat for her trip to Yunnan last July.A) drawbackB) handicapC) bruiseD) blunder11. It advocated by the book that a man, no matter how_______ his origin may be, can besuccessful with unremitting efforts and strong will.A) inferiorB) awkwardC) minorD) humble12. Eric was _______at being told he would have to wait two weeks for an appointment.A) integratedB) irreverentC) irresistibleD) indignant13. It took them four hours to decide that this vicious, ________killer should die.A) remorselessB) raspingC) restiveD) relevant14. Always protect _________files by locking them with a password.A) complimentaryB) confidentialC) compulsiveD) commonsense15. Any store that has had its license _________for more than 30 days will have to apply for apermit.A) slumpedB) strainedC) squintedD) suspended16. We’ve ________salt. Ask Mrs. Jones to lend us some.A) run away withB) run overC) run off17. He was always ill for a time, but he managed to_________.A) pull onB) pull inC) pull upD) pull through18. The actors have to ________before they appear in front of the strong lights on television.A) cover upB) make upC) paint upD) do up19. They have left New York ________good; they’ll never go back and live there again.A) forB) atC) byD) in20. Would you please ________these books to your classmates?A) hand outB) hand downC) hand inD) hand over21. No agreement was reached in the discussion as neither side would give way to_______.A) the otherB) any otherC) anotherD) other22. I regret ________you that your application has been refused.A) informingB) to informC) to be informedD) being informed23. Do you feel like ______to a film or would you rather ______at home?A) going…stayB) to go…stayC) going…stayingD) going…to stay24. “Has he gained weight?”“He would gai n weight, but he _______much.”A) does not eatB) did not eatC) hadn’t eatenD) couldn’t eat25. His use of technical terms left his audience_______.A) confusingB) with confusionD) to confusion26. While we are young, we are continually_______ new ideas, altering our thought patterns,making up our minds afresh.A) taking toB) taking onC) taking inD) taking out27. There has been a growing concern _______pollution. But those who concern themselves______ this problem need government support.A) for, aboutB) over, withC) about, forD) on, to28. You hear me _______! This is important. Don’t treat it ______a joke.A) of, asB) from, likeC) out, asD) about, like29. She is always complaining _________something. It _______my nerves.A) of, gets toB) about, gets onC) about, got onD) for, is getting on30. They are an odd couple .She is as tall _____he is short, and he is as fat _____she is thin. Butthey are both ______happy as they are old.A) as, as, soB) while, while, asC) and, and, asD) as, as, asPart ⅡReading Comprehension (60 minutes, 40%)Section ADirections: There are 3 passages in this part. Each passage is followed by some questions or unfinished statements. For each of them there are four choices marked A, B, C and D. You should decide on the best choice and mark the corresponding letter on the Answer Sheet with a single line through the center. (30%)Passage OneQuestions 31 to 35 are based on the following passage.Practically speaking, the artistic maturing of the cinema was the single-handed achievement of David W. Griffith (1875-1948). Before Griffith, photography in dramatic films consisted of little more than placing the actors before a stationary camera and showing them in full length as they would have appeared on stage. From the beginning of his career as a director, however, Griffith, because of his love of Victorian painting, employed composition. He conceived of thecamera image as having a foreground and a rear ground, as well as the middle distance preferred by most directors. By 1910 he was using close-ups to reveal significant details of the scene or of the acting and extreme long shots to achieve a sense of spectacle and distance. His appreciation of the camera’s possibilities produced novel drama tic effects. By splitting an event into fragments and recording each from the most suitable camera position, he could significantly vary the emphasis from camera shot to camera shot.Griffith also achieved dramatic effects by means of creative editing. By juxtaposing images and varying the speed and rhythm of their presentation, he could control the dramatic intensity of the events as the story progressed. Despite the reluctance of his producers, who feared that the public would not be able to follow a plot that was made up of such juxtaposed images, Griffith persisted, and experimented as well with other elements of cinematic syntax that have become standard ever since. These included the flashback, permitting broad psychological and emotional exploration as well as narrative that was not chronological, and the crosscut between two parallel actions to heighten suspense and excitement. In thus exploiting fully the possibilities of editing, Griffith transposed devices of the Victorian novel to film and gave film mastery of time as well as space.Besides developing the cinema’s language, Griffith immensely broadened its range and treatment of subjects. His early output was remarkably eclectic: it included not only the standard comedies, melodramas, westerns, and thrillers, but also such novelties as adaptations from Browning and Tennyson, and treatments of social issues. As his successes mounted, his ambitions grew, and with them the whole of American cinema. When he remade Enoch Arden in 1911, he insisted that a subject of such importance could not be treated in the then conventional length of one reel. Griffith’s introduction of the American-made multi-reel picture began an immense revolution. Two years later, Judith of Bethulia, an elaborate historicophilosophical spectacle, reached the unprecedented length of four reels, or one hour’s running time. From our contemporary viewpoint, the pretensions of this film may seem a trifle ludicrous, but at the time it provoked endless debate and discussion and gave a new intellectual respectability to the cinema.31. The primary purpose of the passage is to ______.(A) discuss the importance of Griffith to the development of the cinema(B) document Griffith’s impact on the choice of subject matter in American films(C) deplore the state of American cinema before the advent of Griffith(D) analyze the changes in the cinema wrought by the introduction of the multi-reel film32. The author suggests that Griffith’s film innovations had a direct effect on all of the followingEXCEPT: ______.(A) film editing(B) camera work(C) scene composing(D) sound editing33. It can be inferred from the passage that before 1910 the normal running time of a film was______.(A) 15 minutes or less(B) between 15 and 30 minutes(C) 1 hour or more(D) between 45 minutes and 1 hour34. The author asserts that Griffith introduced all of the following into American cinema EXCEPT:______.(A) consideration of social issues(B) adaptations from Tennyson(C) the flashback and other editing techniques(D) dramatic plots suggested by Victorian theater35. The author suggests that Griffith’s contributions to the cinema had which of the followingresults?Ⅰ. Literary works, especially Victorian novels, became popular sources for film subjects.Ⅱ. Audien ce appreciation of other film directors’ experimentations with cinematic syntax was increased.Ⅲ. Many of the artistic limitations thought to be inherent in filmmaking were shown to be really nonexistent.(A)Ⅱ only(B) Ⅲ only(C) I and Ⅱ only(D) Ⅱ and Ⅲ onlyPassage TwoQuestions 36 to 40 are based on the following passage.The molecules of carbon dioxide in the Earth’s atmosphere affect the heat balance of the Earth by acting as a one-way screen. Although these molecules allow radiation at visible wavelengths, where most of the energy of sunlight is concentrated, to pass through, they absorb some of the longer-wavelength, infrared emissions radiated from the Earth’s surface, radiation that would otherwise be transmitted back into space. For the Earth to maintain a constant average temperature, such emissions from the planet must balance incoming solar radiation. If there were no carbon dioxide in the atmosphere, heat would escape from the Earth much more easily. The surface temperature would be so much lower that the oceans might be a solid mass of ice.Today, however, the potential problem is too much carbon dioxide. The burning of fossil fuels and the clearing of forests have increased atmospheric carbon dioxide by about 15 percent in the last hundred years, and we continue to add carbon dioxide to the atmosphere. Could the increase in carbon dioxide cause a global rise in average temperature, and could such a rise have serious consequences for human society? Mathematical models that allow us to calculate the rise in temperature as a function of the increase indicate that the answer is probably yes.Under present conditions a temperature of -18℃can be observed at an altitude of 5 to 6 kilometers above the Earth. Below this altitude (called the radiating level), the temperature increases by about 6℃per kilometer approaching the Earth’s surface, where the average temperature is about 15℃. An increase in the amount of carbon dioxide means that there are more molecules of carbon dioxide to absorb infrared radiation. As the capacity of the atmosphere to absorb infrared radiation increases, the radiating level and the temperature of the surface must rise. One mathematical model predicts that doubling the atmospheric carbon dioxide would raise the global mean surface temperature by 2.5℃: This model assumes that the atmosphere’s relative humidity remains constant and the temperature decreases with altitude at a rate of 6.5℃per kilometer. The assumption of constant relative humidity is important, because water vapor in the atmosphere is another efficient absorber of radiation at infrared wavelengths. Because warm aircan hold more moisture than cool air, the relative humidity will be constant only if the amount of water vapor in the atmosphere increases as the temperature rises. Therefore, more infrared radiation would be absorbed and reradiated back to the Earth’s surface. The resultant warming at the surface could be expected to melt snow and ice, reducing the Earth’s reflectivity. More solar radiation would then be absorbed, leading to a further increase in temperature.36. The primary purpose of the passage is to ______.(A) warn of the dangers of continued burning of fossil fuels(B) discuss the significance of the amount of carbon dioxide in the atmosphere(C) demonstrate the usefulness of mathematical models in predicting long-range climaticchange(D) describe the ways in which various atmospheric and climatic conditions contribute to theEarth’s weather37. According to the passage, the greatest part of the solar energy that reaches the Earth is ______.(A) reflected back to space by snow and ice(B) concentrated at visible wavelengths(C) absorbed by carbon dioxide molecules(D) absorbed by atmospheric water vapor38. According to the passage, atmospheric carbon dioxide performs all of the following functionsEXCEPT: ______.(A) absorbing radiation at visible wavelengths(B) absorbing infrared radiation(C) absorbing outgoing radiation from the Earth(D) helping to retain heat near the Earth’s surface39. It can be concluded from information contained in the passage that the average temperature atan altitude of 1 kilometer above the Earth is about ______.(A) 15℃(B) 9℃(C) 2.5℃(D) -12℃40. According to the passage, which of the following is true of the last hundred years?(A) Fossil fuels were burned for the first time.(B) Greater amounts of land were cleared than at any time before.(C) The average temperature at the Earth’s surface has become 2℃ cooler.(D) The amount of carbon dioxide in the atmosphere has increased measurably.Passage ThreeQuestions 41 to 45 are based on the following passage.“Popular art”has a number of meanings, impossible to define with any precision, which range from folklore to junk. The poles are clear enough, but the middle tends to blur. The Hollywood Western of the 1930’s, for example, has elements of folklore, but is closer to junk than to high art or folk art. There can be great trash, just as there is bad high art. The musicals of George Gershwin are great popular art, never aspiring to high art. Schubert and Brahms, however, used elements of popular music—folk themes—in works clearly intended as high art. The case of Verdi is a different one: he took a popular genre—bourgeois melodrama set to music (an accurate definition of nineteenth-century opera)—and, without altering its fundamental nature, transmutedit into high art. This remains one of the greatest achievements in music, and one that cannot be fully appreciated without recognizing the essential trashiness of the genre.As an example of such a transmutation, consider what Verdi made of the typical political elements of nineteenth-century opera. Generally in the plots of these operas, a hero or heroine—usually portrayed only as an individual, unfettered by class—is caught between the immoral corruption of the aristocracy and the doctrinaire rigidity or secret greed of the leaders of the proletariat. Verdi transforms this naive and unlikely formulation with music of extraordinary energy and rhythmic vitality, music more subtle than it seems at first hearing. There are scenes and arias that still sound like calls to arms and were clearly understood as such when they were first performed. Such pieces lend an immediacy to the otherwise veiled political message of these operas and call up feelings beyond those of the opera itself.Or consider V erdi’s treatment of character. Before Verdi, there were rarely any characters at all in musical drama, only a series of situations which allowed the singers to express a series of emotional states. Any attempt to find coherent psychological portrayal in these operas is misplaced ingenuity. The only coherence was the singer’s vocal technique: when the cast changed, new arias were almost always substituted, generally adapted from other operas. Verdi’s characters, on the other hand, have genuine consistency and integrity, even if, in many cases, the consistency is that of pasteboard melodrama. The integrity of the character is achieved through the music: once he had become established, V erdi did not rewrite his music for different singers or countenance alterations or substitutions of somebody else’s arias in one of his operas, as every eighteenth-century composer had done. When he revised an opera, it was only for dramatic economy and effectiveness.41. The author refers to Schubert and Brahms in order to suggest ______.(A) that their achievements are no less substantial than those of Verdi(B) that their works are examples of great trash(C) the extent to which Schubert and Brahms influenced the later compositions of Verdi(D) that popular music could be employed in compositions intended as high art42. According to the passage, the immediacy of the political message in Verdi’s operas stems fromthe ______.(A) vitality and subtlety of the music(B) audience’s familiarity with earlier operas(C) verisimilitude of the characters(D) individual talents of the singers43. According to the passage, all of the following characterize musical drama before VerdiEXCEPT: ______.(A) music used for the purpose of defining a character(B) adaptation of music from other operas(C) psychological inconsistency in the portrayal of characters(D) expression of emotional states in a series of dramatic situations44. It can be inferred that the author regards V erdi’s revisions to his operas with ______.(A) regret that the original music and texts were altered(B) concern that many of the revisions altered the plots of the original work(C) approval for the intentions that motivated the revisions(D) puzzlement, since the revisions seem largely insignificant45. According to the passage, one of Verdi’s achievements within the framework ofnineteenth-century opera and its conventions was to ______.(A) limit the extent to which singers influenced the musical compositions and performance ofhis operas(B) use his operas primarily as forums to protest both the moral corruption and dogmaticrigidity of the political leaders of his time(C) portray psychologically complex characters shaped by the political environmentsurrounding them(D) incorporate elements of folklore into both the music and plots of his operasSection BDirections: There is one passage in this part. The passage is followed by some questions. Please answer the questions briefly. (10%)The Game of the NameHere comes John Smith walking toward me. Even though he is but a passing acquaintance, the American greeting ritual demands that I utter a few words to reassure him of my good will. But what form of address should I use? John? Smith? Dr. Smith? A decision such as this is usually made unconsciously.As native speakers in the American speech community, we have grown up learning the rules of address at the same time that we were acquiring the grammatical rules of American-English. At first thought, it might seem a trivial pursuit to examine the ways in which we address one another. But forms of address reveal many assumptions we make about members of our speech community.Our initial decision about the appropriate address form is based on relative ages. If the person being addressed is a child, then almost all the rules that we have unconsciously assimilated can safely be ignored, and we use the simple formula First Name. The child, in turn, addresses an adult by using the formula Title plus Last Name.But defining a “child” is not always easy. I address my son’s roommate at college by FN, even though he is an adult under the law. I, too, have the relative age of a child to a 75-year-old acquaintance who calls me Pete. Let us assume that John Smith is not a child who can be addressed by FN but is either my contemporary or my elder. The next important determiner for the form of address will then be the speech situation.If the situation is a formal one, then I must disregard all other rules and use social identity plus Last Name. John Smith will always be addressed as Dr. Smith (or sometimes simply as Doctor, with Last Name understood) in the medical setting of office or hospital. (I am allowed to call him if my status is at least as high as his or if we are friends outside of our social roles, but the rest of my utterance must remain respectful.)We are also obliged to address certain other people by their social identity in formal situation: public officials (Congressman: Your Honor), educators (Professor or Doctor), leaders of meetings (Mr. Chairman), Roman Catholic priests (Father Daffy) and nuns (Sister Anna), and so forth. By the way, note the sexist distinction in the formulas for priests and nuns .The formula for a priest is Father plus Last Name, but for a nun it is Sister plus Religious Name (usually an FN).Most conversations, however, are not carried on in formal speech situations, and so the basic decision is when to use FN to TLN. A social acquaintance or newly hired colleague of approximately the same age and rank is usually introduced on an FN basis. “Pete, I’d like you tomeet Harry.” Now a problem arises if both age and rank of cone of the parties are higher: “Pete, I'd like you to meet Attorney Brown.”Attorney Brown may, of course, at any time signal me that he is willing to suspend the rules of address and allow an FN basis. Such a suspension is his privilege to bestow, and it is usually handled humorously, with a remark like, “I answer quicker to Bruce.”Complications arise when relative age and relative rank are not both the same. A young doctor who joins a hospital finds it difficult to address a much older doctor. They are equal in rank (and therefore FN should be used) but the great disparity in ages calls for TLN. In such cases, the young doctor can use the No-Name (NN) formula, phrasing his utterances adroitly to avoid using any term of address at all.English is quite exceptional among the world’s languages in this respect. Most European languages oblige the speaker to choose between the familiar and formal second person singular (as in the French tu and V ous), as English once did when “thou” was in use.This is the basic American system, but the rules vary according to speech situations, subtle friendship or kin relationships between the speakers, regions of the country, and so forth.Southern speech, for example, adds the formula Title plus First Name (Mr. Charlie) to indicate familiar respect. Southerners are also likely to specify kin terms (as in Cousin Jane) whereas in most of the United States FN is used for cousins.Address to strangers also alters some of the rules. A speaker usually addresses a stranger whose attire and behavior indicate higher status by saying sir. But sometimes speakers with low status address those with obviously higher status by spurning this rule and instead using Mac or buddy—as when a construction worker asks a passing executive, socially identified by his attachécase, “You got a match, buddy?”Questions:1. According to the author, what are the important determiners for the form of address in the basic American system? (3%)2. What does the speaker mean in the underlined part “I answer quicker to Bruce.” of Paragraph 8? Please explain it in your own words. (2%)3. Which formula is used when a young man addresses an elder person but with the same rank? (2%)4. What are some exceptions to the rules of the basic American system? Give an example. (3%)Part ⅢWriting (60 minutes, 30%)Directions: Please write an essay of about 400 words on the following topicChinese-English Translation of Internet Buzzwords参考答案及解析Part I Vocabulary (30%)1.C 句意:医生给我开了治头疼的药。
2012年北京航空航天大学翻译硕士英语真题试卷
2012年北京航空航天大学翻译硕士英语真题试卷(总分:98.00,做题时间:90分钟)一、 Vocabulary(总题数:29,分数:58.00)1.The doctor______a medicine for my headache.(分数:2.00)A.subscribedB.describedC.prescribed √D.inscribed解析:解析:句意:医生给我开了治头疼的药。
prescribe开处方,给医嘱。
subscribe捐赠;签署;题名。
describe描述,描写。
inscribe雕刻;题写。
2.This song______his life"s dream and ardent love of life.(分数:2.00)A.incorporatedB.initiatedC.exposedD.embodied √解析:解析:句意:这首歌表达了他的梦想以及对生活的热爱。
expose表达,显示;揭露,揭发。
incorporate 包含;吸收。
initlate发起,始创。
embody表现,象征;包含。
3.It is said that the reconstruction of the Grand Theatre is a______project of Shanghai government this year.(分数:2.00)A.prestigeB.superiorityC.priority √D.publicity解析:解析:句意:据说今年上海市对大剧院的重建工作是一项优先工程。
priority优先,优先考虑的事情。
prestige威信,威望。
superiority优越性,优等。
publicity公开;宣传;广告。
4.Such a toy with musical sounds and animal noises will______any young child.(分数:2.00)A.dismayB.astonishC.fascinate √D.perplex解析:解析:句意:这样一个能发出音乐和动物叫声的玩具娃娃将吸引所有的小孩。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
The Fermi–Hart Paradox: Where are the Aliens?
Fermi is reported to have mused over lunch that there could not beintelligent lifeforms elsewhere than Earth because they would havecolonized space and already be here. Conversely, the presence of lifeon the Earth implies its presence elsewhere. This problem, though itoriginated with Fermi, has been worked on by many people, mostnotably Hart. Over the years, the absence of evidence for aliens hasemerged as one of the few solid data in the field of exobiology. In thissection, we therefore confine our attention to the Fermi–Hart paradoxand how it may be resolved.
Drake’s formula is the traditional way to quantify the frequencyof extraterrestrial civilizations. Itinvolves a product of probabilities,ranging from the astrophysical (e.g. the fraction of stars which havehabitable planets) to the sociological (e.g. the relative timescale forthe development of technology). However, each of the componentprobabilities is poorly known, so the result has a high degree ofuncertainty. The nearest tecபைடு நூலகம்nological civilization to us may bearound a nearby star, or in one of the most remote galaxies.
It is important to realize in the application of Drake’s formula thatthere is a continuum of systems to which it can be applied: the stars ofthe Milky Way, the local group of galaxies, or all of the objects in thevisible universe. To order of magnitude, there are as many galaxies inthat part of the universe accessible to observation as there are stars inthe Milky Way. Signals from extraterrestrial civilizations involve, fortheir detection, a balance between the number of sources (which goesup approximately as the cube of the distance) and the signal strength(which goes down for electromagnetic radiation as the square ofthe distance). This is like the situation we encountered before inregard to Olbers’ paradox. The American program on the Search forExtraterrestrial Intelligence has concentrated on nearby stars, butprevious Russian surveys focused on distant galaxies. The fact thatno signals have been detected from either class of objects brings usback to the Fermi–Hart paradox.
An immediate suggestion for a resolution is, of course, that aliencivilizations are sparse in the universe.Indeed, Tipler and others haveargued that human civilization may be unique and that we are trulyalone. This view is distasteful to many, and some researchers such asClarke and Sagan have reached theopposite conclusion, that life(and by implication civilization) is common. The reason for thisdivergence of opinion lies simply in a lack of data.
