香港金融管理局电子银行监管手册
中国香港的中央银行制度

中国香港的中央银行制度
中国香港的中央银行是香港特别行政区的货币当局,负责制定和执行货币政策,发行货币,并维护香港的货币稳定。
以下是关于中国香港中央银行制度的主要特点:
香港金融管理局(HKMA):香港的中央银行实际上是香港金融管理局,简称HKMA。
HKMA是香港特别行政区的一个政府部门,于1993年成立。
货币发行:HKMA负责发行和管理香港的货币,包括香港元。
香港的货币政策主要以与美元的货币连系制度为基础,确保香港元的稳定性。
汇率制度:香港的货币与美元挂钩,即港元与美元的固定汇率关系。
这种制度有助于保持货币的稳定和国际信誉。
货币政策:HKMA通过货币政策来维护香港的货币和金融稳定。
该机构定期进行利率决策,以影响货币供应和需求。
金融监管:除了货币发行和政策制定外,HKMA还担任金融监管机构,监督香港金融机构,确保其合规运营。
国际金融中心:作为国际金融中心之一,香港的中央银行制度在维护货币和金融稳定的同时,还促进了香港作为全球金融枢纽的地位。
总体而言,香港的中央银行制度是与美元挂钩的货币连系制度,并由香港金融管理局负责执行货币政策、发行货币、进行金融监管等职责。
香港非银行业金融机构内控管理措施

设立详细书面合规手册、政策及程序及向全部员工提供,并予以检讨和依从。
身为持牌人士的员工须出席持续专业培训。
核心业务通过特别设计的系统经营,并维持足够的审核汇总程序。
本集团利用独立、声誉良好及可信的托管银行保障客户资产。
所有申购/赎回款项直接向/自托管银行支付。
进行客户识别及防治洗黑钱及恐怖分子融资程序,以核实身份及资金来源。
公司按照监管要求建立健全了信息隔离墙、未公开信息知情人登记、内幕信息知情人登记管理等制度并落实执行,有效防范了敏感信息的不当使用和传播。同时,公司严格按照法律、法规和公司《章程》的规定,真实、准确、完整、及时地披露信息,确保所有投资者均有平等的机会及时获得公司信息。
公司名称:惠理集团有限公司
公司性质:基金类
上市地:H股
公司治理架构:
董事会下设委员会:审核委员会、薪酬委员会、提名委员会、风险管理委员会。
内部控制情况:
内部监控的主要程序:
本集团内部监控制度组织架构设有明确汇报流程并将监督及报告的责任授予具有资格的经验人士。
每年制定业务计划及预算,由高级管理团队审阅及批准。
以行之有效的授权参数管理业务决策。
本公司将根据内部控制评价结果,对发现的内部控制缺陷进行持续整改,定期跟进措施评估。
本公司根据相关法律法规的要求,对公司2015年度的内部控制情况在控制环境、风险识别和评估、控制活动、信息与沟通、监督方面进行了自我评价,内部控制评估小组全面复核后得出评价结果。评价结果表明公司建立和加强了内部控制组织结构,不断完善风险管理体系,优化业务控制流程,改进资讯系统控制,强化内控管理和监督,从组织、人员、制度、流程和执行等方面确保公司内部控制目标的实现,并根据外部政策变化不断建立和加强内控体系。内控机制基本健全、合理,并得到有效执行,公司内部控制体系运行情况良好,为公司经营管理目标的实现提供了合理的保证,未发现存在重大缺陷。
初探香港银行卡收单业务监管

20 年 ,金管 局颁布 了 ( 08 ( 监管政 策手 册 ,对银 行业 引还 是非 法定 指 引 ),其是 否仍 符合 银行 业条 例 的最 ( 包括但 不限于银 行卡 产业 )从业 机构 的银行 卡业 务提供 低资 质要 求将 受到 质疑 。此 外 ,如果银 行业 机构 未 有限公 司信用 卡0, 于洁静 6 中国银联 战略发展 与法律 合规部 丁康吉
一
、
香港银行卡产业监管概 览
二 、有关银行卡收单业务的监管政策
金 管局 对银 行卡收 单业 务 的监 管主 要体 现在 监 管政
香 港特 别 行政 区 的法 律体 系 不但 完 善 , 且 公开 、透 而
的主 要 风 险 ” 、 “ 事 局 及 高 级 管 理 层监 察 ” 、 “ 董 招揽
活的商 业运作 空 间。金管 局宣称 ,其 制定 的银行业 监管 制 新 客 户及核 批程 序” 、 “ 户 及业务 管理 ” 、 “ 备及 撇 帐 拨
度符合 巴塞尔 银行监 管委 员会颁 布的 ( ( 监管银 行业 的 帐 ”共6 条 。其 中的第2 “ 用卡 业务 的主要 风 险” 、 有效 大 条 信 主 要原 则》 。金管局 主要 依据 银行业 条例 、 结算 及 第4 8 “ .条 批核 新商 户 ”、第 52 “ 户帐 户管理 ” 、第 .条 商 交 收系统 条例 ,对 银行 、接受 存款 公司 、支付结 算 系统 54 “ 控欺 诈活动 ”对收单业 务进行 了监管 。 .条 监 等 机构 实施监 管 ,促 进银行 体 系的安全 、有 效 、健 全 、稳
2 .手 册的具体 规定
手册 对 收 单 业 务 的监 管 条 款 充 分 体 现 金 管 局 一 贯 的 “ 险为本 ” 的监管 精神 和 “ 风 持续监 管 ”的监 管 作风 。手
香港黄金交易市场的交易监管如何执行

香港黄金交易市场的交易监管如何执行香港作为全球重要的金融中心之一,其黄金交易市场在国际金融领域占据着重要地位。
为了保障市场的公平、公正、透明和稳定,香港实施了一系列严格而有效的交易监管措施。
首先,香港金融管理局(简称金管局)在交易监管中发挥着关键作用。
金管局负责制定和执行相关的金融政策,确保黄金交易市场的稳健运行。
它对参与黄金交易的金融机构进行严格的监管,包括银行、证券公司等。
这些金融机构需要满足一系列的资本充足率、风险管理和内部控制等要求。
金管局会定期对它们进行检查和评估,以确保其合规运营。
在法律框架方面,香港拥有完善的金融法规体系。
《证券及期货条例》等相关法律为黄金交易提供了明确的法律规范。
这些法律涵盖了交易行为、市场操纵、内幕交易等多个方面。
对于违反法律法规的行为,制定了严厉的处罚措施,包括高额罚款、监禁甚至吊销从业资格等,从而对潜在的违法违规行为起到强大的威慑作用。
在市场准入方面,香港对黄金交易商和经纪商设定了严格的准入标准。
申请者需要具备一定的资金实力、良好的信誉记录和专业的管理团队。
此外,还需要通过严格的审批程序,包括对其业务模式、风险管理能力和合规制度的审查。
只有获得相关牌照和许可的机构,才能在香港从事黄金交易业务。
为了确保交易的透明度,香港要求黄金交易参与者必须及时、准确地披露相关信息。
这包括交易价格、成交量、交易对手等重要信息。
同时,交易所还会对交易数据进行监控和分析,以便及时发现异常交易行为和潜在的市场风险。
香港的黄金交易市场还注重对投资者的保护。
金融监管机构会通过各种渠道向投资者普及金融知识和风险教育,帮助他们了解黄金交易的特点和风险。
此外,还设立了投资者赔偿基金,为在合法交易中遭受损失的投资者提供一定程度的赔偿。
在交易结算和清算方面,香港采用了先进的系统和制度。
确保交易的款项和黄金交割能够及时、准确地完成,减少交易风险和纠纷。
同时,清算所还承担着风险管理的职责,对会员的交易头寸进行监控和风险评估。
内地与香港银行合规监管的差异与合作

内地与香港银行合规监管的差异与合作
内地与香港的银行合规监管存在一些差异,但也开展了一定的合作。
以下是它们的主要差异和合作方面:
1. 差异:
- 法律体系:内地银行合规监管受到中国法律体系的制约,而香港则有独立的法律体系。
- 监管机构:内地的银行合规监管主要由中国银行业监督管理委员会(简称“银监会”)负责,而香港由香港金融管理局(简称“金管局”)负责。
- 监管标准:内地的监管标准相对更严格,因为内地金融风险更为敏感,而香港更注重市场化和国际接轨。
- 控制措施:内地银行合规监管更强调管理和控制措施,而香港则更注重市场自律和信息披露。
2. 合作:
- 信息共享:内地与香港的监管机构会进行信息的共享和交流,以便更好地监管跨境金融活动。
- 金融合作:内地与香港在金融方面有许多合作机制,如互联互通机制、债券市场互联互通等,这也需要对合规进行合作监管。
- 培训交流:监管机构之间定期进行培训和交流,以提高监管人员的专业水平和合规意识。
总体来说,内地与香港的银行合规监管存在一些差异,但也都致力于保护金融体系的稳定和健康发展,通过合作与交流来提高银行的合规水平。
监管政策手册

監管政策手冊IN引言V. 1 – 19.01.01本章應連同目錄及收錄本手冊所用縮寫語及其他術語的辭彙㆒起細閱。
若使用本手冊的網㆖版本,可按動其㆘劃有藍線的標題,以接通有關章節。
_______________1. 範圍1.1 本手冊列述金管局的監管政策及執行手法、預期認可機構為符合《銀行業條例》的規定而應遵守的最低標準,以及建議認可機構應致力達到的最佳經營手法的建議。
編製本手冊的主要目的,是供認可機構、其審計師及顧問,以及金管局的監管㆟員參閱。
1.2 本手冊只能述及《銀行業條例》部分條款。
由於性質所限,本手冊無法鉅細無遺,就所有可能情況提供指引,而這亦非編製本手冊的本意。
認可機構及其高層㆟員仍須最終負責確保本身遵行適用的法律條文。
任何情況㆘,認可機構均責無旁貸,而須貫徹掌握本港有關法律,並徵詢適當的法律意見,以確保符合預期達到的標準。
1.3 本手冊取代金管局以往發出的有關的監管指引及通告。
本手冊每章均詳細註明其所取代的具體指引及通告。
2. 目的2.1 金管局的監管目標是透過規管及監管認可機構與其業務活動,為存戶提供保障及促進銀行體系的整體穩定及有效運作。
2.2 金管局採用風險為本的監管模式,以判斷認可機構是否已制定適當的風險管理及內部管控制度。
本手冊是為配合風險為本監管制度而編製,旨在鼓勵認可機構經營業務時遵守適當標準,監管政策手冊IN引言V. 1 – 19.01.01並採取審慎的風險管理經營手法,以能符合穩健及安全的經營之道。
具體來說,本手冊:•闡明金管局如何詮釋認可機構在《銀行業條例》㆘的責任;•建議認可機構在履行責任時應執行的當前最佳的手法;•釐定金管局預期認可機構應達到的最低審慎標準。
2.3 金管局規定所有認可機構須遵守本手冊所載的最低標準,並鼓勵它們按照本身業務需要致力達到最佳經營手法。
認可機構管理層的首要責任,是確保認可機構適當遵守這些標準及執行手法,以管理認可機構的業務風險、保障資產,以及遵守《銀行業條例》及其他適當法律。
第五章 香港的金融监管

充足标准,保持不少于8%的法定资本充足率。 4.CAMEL评级制度 CAMEL评级制度是一套国际公认的制度。这套评级制度包 括五个基本项目,即:资本充足率(Capital Adequacy); 资产质量(Assets quality);管理能力(Management);盈 利性(Earning);流动性(Liquidity)。通过以上五个方面 评价以衡量金融机构的资信等级。由于这五个项目的第一 个字母组成CAMEL一词,因此,也被叫做“骆驼评级制度”。 香港金管局在1995年正式引入这个评级制度。
图1 :香港的金融监管框架图
资料来源:香港监管局等网站
(二)香港金管局 香港金管局成立于1994年4月,金管局根据《银行业条 例》的授权,对持牌银行、有限制持牌银行和接受存款公 司实行审慎监管。其监管方法有现场审查和非现场审查。 除了监管银行业外,金管局的其它功能和目标包括维持港 元稳定、提高金融制度的效率及促进其发展,以及维护廉 洁公正的金融制度,这与世界各地中央银行的功能和目标 大致相同。在1993年,政府把外汇基金办事处及银行业监 理处合并为金管局,主要目的是确保维持金融体制及银行 业稳定等中央银行的功能,能够由一个具专业知识的机构 执行,并保持政策的延续性,从而维系港人及国际财经界 对香港的信心。
(4)盈利性。以税后净收益与总资产之比衡量,并根据金 融机构资产规模大小加以区别。例如,小于1亿美元总资 产的银行,此比例达到1.15%以上为1等,达到0.95%为2 等,达到O.75%为3等,小于0.75%为4等,净亏损则为5 等 (5)流动性。主要观察短期投资、主要存款、贷款与租赁、 变动债务等与总资产的比例。
第二节 各行业的监管
(一)银行业监管 1.法律基础 《银行业条例》是香港银行业监管的法律基础。 2.监管制度 建立符合国际标准的银行监管制度,特别是巴塞尔银行 监督管理委员会建议的制度。 3.监管目标 通过规定银行业务和接受存款业务,以及监管机构认可 机构,促进银行体系的安全和稳定。所有本地注册认可机 构均须按照巴塞尔委员会1988年《本协议》所订明的资本
香港金融管理局《监管政策手册》
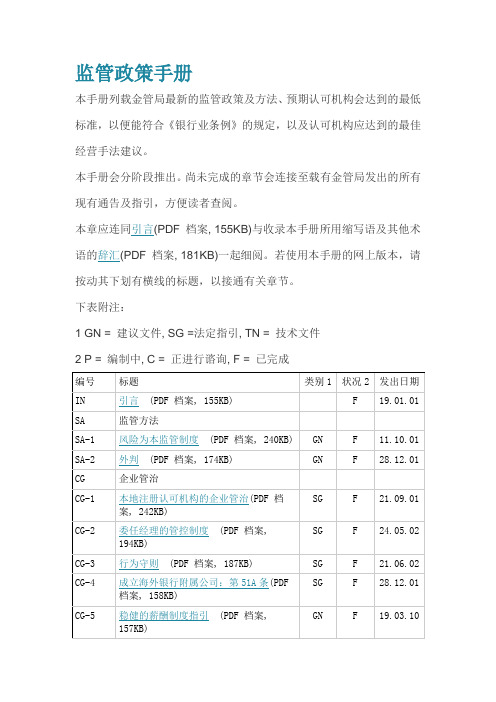
监管政策手册
本手册列载金管局最新的监管政策及方法、预期认可机构会达到的最低标准,以便能符合《银行业条例》的规定,以及认可机构应达到的最佳经营手法建议。
本手册会分阶段推出。
尚未完成的章节会连接至载有金管局发出的所有现有通告及指引,方便读者查阅。
本章应连同引言(PDF 档案, 155KB)与收录本手册所用缩写语及其他术语的辞汇(PDF 档案, 181KB)一起细阅。
若使用本手册的网上版本,请按动其下划有横线的标题,以接通有关章节。
下表附注:
1 GN = 建议文件, SG =法定指引, TN = 技术文件
2 P = 编制中, C = 正进行谘询, F = 已完成。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Supervisory Policy ManualTM-E-1Supervision of E-banking Consultation This module should be read in conjunction with the Introduction and with the Glossary, which contains an explanation of abbreviations and other terms used in this Manual. If reading on-line, click on blue underlined headings to activate hyperlinks to the relevant module.—————————PurposeTo set out the HKMA’s approach to the supervision of AIs’ electronic banking (e-banking) services and to provide AIs with guidance on general principles for risk management of e-bankingClassificationA non-statutory guideline issued by the MA as a guidance notePrevious guidelines supersededGuideline 15.1 “Electronic Banking” dated 07.07.97Guideline 15.1.1 “Security of Banking Transactions over the Internet”dated 25.11.97Guideline 15.3 “Public Key Infrastructure and Legal Environment for Development of Internet Banking” dated 07.10.98Circular “Guidance Note on Management of Security Risks in Electronic Banking Services” dated 06.07.00Circular “Guidance Note on Independent Assessment of Security Aspects of Transactional E-banking Services” dated 26.09.00Circular “Overseas Fraud Cases involving Fake E-mails or Websites”dated 19.05.03ApplicationTo all AIsStructure1.Introduction1.1 Terminology1.2 Backgroundapproach2. SupervisorySupervisory Policy ManualTM-E-1Supervision of E-banking Consultationobjective2.1 Supervisory2.2 Supervisory framework of e-banking2.3 Introduction or major enhancements of e-banking services2.4 Regular independent assessmentsand other monitoring processexaminations2.5 On-site2.6 Supervision of cross-border e-banking services3. Board and senior management oversight3.1 Planning and organisation3.2 Risk management process3.3 Formulation of information security policy4. Major technology-related controls relevant to e-banking4.1 Authentication of customers4.2 Confidentiality and integrity of informationsecurity4.3 Applicationinfrastructure and security monitoring4.4 Internet4.5 Incident response and management4.6 Business continuity considerationsmanagement4.7 Outsourcing5. Customer security and other risk management controlsprotection5.1 Consumer5.2 Administration of e-banking accounts5.3 Controls over fund transfers5.4 Monitoring of unusual activities5.5 Preventive controls relating to fake e-mails or websiteseducation5.6 Customer5.7 Legal and reputation risk managementAnnex A:Scope and reporting of independent assessmentAnnex B:Sound practices for the establishment of internetinfrastructure—————————Supervisory Policy ManualTM-E-1Supervision of E-banking Consultation1.Introduction1.1Terminology1.1.1In this module terms are used with the followingmeanings:•“Demilitarised zone” (or DMZ) refers to a networksegment inserted between a trusted internalnetwork and an external network such as theinternet, in order to prevent parties of the externalnetwork from getting direct access to the trustedinternal network, and vice versa;•“Electronic banking” (or e-banking) refers tobanking services involving the transmission ofconfidential customer information (includingtransactions) through the internet1. For thepurpose of this module, e-banking coversservices for personal, corporate and institutionalcustomers;devices (with hardware andto• “Firewall”referssoftware) that can examine the packets, pattern ofpackets and network services flowing betweentwo or more networks, such as the trusted internalnetworks, the DMZ and the internet so as todetermine whether the packets and networkservices should be given access into, or allowedto move between, these networks;•“Intrusion Detection System” (or IDS) refers tocomputer systems which collect relevantinformation from host computers, servers ornetworks for detecting signs of intrusion andmisuse of computer resources, and alertingrelevant personnel to these activities; and1E-banking does not cover (i) automated teller machines or self-service machines connected through private networks; (ii) phone banking; (iii) personal computer (PC) banking connected through dial-up telephone lines; and (iv) mobile banking services that do not involve connection through the internet.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultation•“Routers” refer to network devices which are usedto direct network traffic between networks.Routers are often used as security devices oncomputer networks to allow only certain types ofpackets and network services from a network toenter the other network.1.2 Background1.2.1 The development of e-banking services brings risks aswell as benefits to AIs. While the types of risks arisingfrom e-banking are generally not new to an AI, thecharacteristics of e-banking may shift the AI’s riskprofiles to some degree and create new riskmanagement challenges. In particular:•the internet is a global and open networkaccessible from anywhere in the world byunknown parties. The security of the internet anddevices used by customers to access e-bankingare outside AIs’ direct control. It therefore adds toAIs’ operational risk in respect of securitybreaches and service interruptions;•the operational risk and reputation risk of AIs maybe increased as the growing dependence ontechnology and the technical complexity of e-banking may lead to more reliance upon outsidetechnology service providers such astelecommunications operators, and applicationand security vendors;•it may be a strategic challenge for AIs todetermine whether and when specific e-bankingservices should be introduced. This is particularlyrelevant if it is unclear whether the benefits ofoffering or maintaining the services will outweighthe initial investment and the ongoing expensesneeded to maintain an appropriate level ofsecurity of the services; and•e-banking may expose AIs to reputation and legalrisks if overseas authorities regard the services astargeting at overseas residents and requiringauthorization in their jurisdictions.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultationapproach2. Supervisoryobjective2.1 Supervisory2.1.1 The HKMA’s supervisory objective is to establish andmaintain a safe and sound environment for thedevelopment of e-banking in Hong Kong withoutstanding in the way of progress.2.1.2 To achieve this objective, the HKMA believes thatmaintaining technological neutrality is crucial for allowingAIs to have the flexibility to choose and implementtechnologies that are appropriate to their e-bankingservices. Setting absolute risk managementrequirements or rigid technological standards in the areaof e-banking is impractical and counter-productive.2.1.3 The general principle is that AIs are expected toimplement the relevant risk management controls thatare “fit for purpose”, i.e. commensurate with the risksassociated with the types and amounts of transactionsallowed, the electronic delivery channels adopted andthe risk management systems of individual AIs.2.1.4 In developing this module, the HKMA has taken intoconsideration supervisory approach and guidance of theinternational regulatory community, particularly thoserecommended by the Basel Committee on BankingSupervision2. However, it should be emphasised thatthis module is not intended to prescribe uniform or all-inclusive principles and practices in managing the risksfor all kinds of e-banking services.2.2 Supervisory framework of e-banking2.2.1 In line with the risk-based supervisory methodology, theHKMA’s supervisory framework of e-banking aims toprovide an appropriate level of continuous supervision ofAIs’ e-banking activities. This supervisory frameworkcomprises an effective supervisory approach to e-banking, which is conducted in a continuing cycle, in2The Basel Committee on Banking Supervision has issued a number of papers on e-banking, in particular: “Risk Management Principles for Electronic Banking” of July 2003 (/publ/bcbs98.htm) and “Management and Supervision of Cross-Border Electronic Banking Activities” of July 2003 (/publ/bcbs99.htm).Supervisory Policy ManualTM-E-1Supervision of E-banking Consultationensuring the adequacy of AIs’ management oversightand risk management of their e-banking services (seesections 3 to 5 below). An overview of the supervisoryframework of e-banking is illustrated below.Supervisory Policy ManualTM-E-1Supervision of E-banking ConsultationSupervisory Policy ManualTM-E-1Supervision of E-banking Consultation2.3 Introduction or major enhancements of e-banking services2.3.1 Although AIs do not need to seek formal approval fromthe HKMA to offer new e-banking services, AIs shoulddiscuss their plans with the HKMA in advance beforelaunching such new services. They should also discusswith the HKMA their plans to introduce majorenhancements3 to existing services. In general, thediscussion should satisfy the HKMA that the followingissues are properly addressed:•Board and senior management oversight (seesection 3);•major technology-related controls relevant to e-banking (see section 4) and, in particular, theresult of an independent assessment of theservice (see also subsection 2.4 below);security and other risk management• customercontrols (see section 5) and, particularly, whetherthe terms and conditions of the service complywith the Code of Banking Practice if the service isoffered to personal customers; and•any other relevant supervisory issues related toactivities such as outsourcing (see SA-2“Outsourcing”), conducting certain regulatedactivities specified in the Securities and FuturesOrdinance through the internet (see SB-1“Supervision of Regulated Activities of SFC-Registered Authorized Institutions”) and cross-border e-banking activities (see subsection 2.6below).2.4 Regular independent assessments2.4.1 The senior management of an AI are required to appointtrusted independent experts (the “assessor(s)”) to carryout an independent assessment before the launch ofnew e-banking services or major enhancements toexisting services. Moreover, independent assessmentsshould also be performed generally thereafter at leastonce a year, or whenever there are substantial changes3These refer to major service enhancements or changes in technologies which have material risk implications for the AI concerned or its customers.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultationto the risk assessment of services being provided,significant modification of an AI’s internet infrastructureand e-banking applications, or major security breaches.The scope and items to be reported in the independentassessment should cover, at a minimum, the areasspecified in Annex A. The independent assessmentreport should be submitted to the HKMA for reference.2.4.2 An assessor should have, and can demonstrate, thenecessary expertise in the field to perform theindependent assessment. To ensure impartiality, theassessor should be independent from the parties thatdevelop, implement or operate the services and not beinvolved in the operations to be reviewed or in selectingor implementing the relevant control measures to bereviewed. The assessor should be able to report itsfindings freely and directly to the senior management ofthe AI as appropriate.2.4.3 As long as the assessor meets the above requirementson expertise and independence, the assessor can be anexternal party (e.g. an external auditor or third-partysecurity consultant), an AI’s internal staff (e.g. internalauditors) or an independent unit of the vendor of therelevant e-banking system.2.5 On-site examinations and other monitoring process2.5.1 The HKMA will, in the course of its on-site examinationsand off-site reviews, determine as appropriate theadequacy of AIs’ risk management of e-bankingservices, having regard to the principles set out in thismodule (see sections 3 to 5 below).2.5.2 AIs should report promptly to the HKMA of anysuspected or confirmed fraud cases relating to e-banking, major security breaches, any material serviceinterruption or other significant issues related to their e-banking services. The HKMA may also implement othermonitoring process (e.g. supervisory control self-assessment) to facilitate its ongoing supervision of e-banking.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultation2.6 Supervision of cross-border e-banking services2.6.1 The HKMA observes the guidance of the BaselCommittee’s Concordat4, its later supplements and thepaper “Management and Supervision of Cross-BorderElectronic Banking Activities” of June 2003 forsupervisory cooperation and sharing of informationbetween home and host supervisors in respect ofsupervision of cross-border e-banking services.2.6.2 In general, a locally incorporated AI planning tointroduce a cross-border e-banking service to anotherjurisdiction in which it does not have a physical presenceshould discuss with the HKMA in advance. The HKMAneeds to be satisfied that the AI has conductedadequate due diligence (e.g. through AIs’ consultationwith the appropriate local supervisors) to determine theapplicability of laws, regulations and supervisorystandards in the foreign jurisdiction. Further, AIs shouldhave an effective and on-going risk managementprocess for its cross-border e-banking activities.3. Board and senior management oversight3.1 Planning and organisation3.1.1 The unique characteristics and relatively high up-frontinvestment of the e-banking service may have materialrisk implications for AIs. In this connection, the HKMAexpects the Board5 or its designated committee, andsenior management of AIs to ensure that the e-bankingservice that is new to their AI should be subject tocareful evaluation (see also IC-1 “General RiskManagement Controls” on new products and services).3.1.2 The objective of the evaluation is to ensure that theBoard or its designated committee, and seniormanagement fully understand the risk characteristics 4See “Principles for the Supervision of Bank’s Foreign Establishments”, generally known as the “Concordat”, issued by the Basel Committee on Banking Supervision in May 1983. 5For the purpose of this module, the responsibility for the oversight of e-banking in respect of the Hong Kong operations of an overseas incorporated AI would rest with its local management.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultationand that there are adequate staffing, expertise,technology and financial resources to launch andmaintain the service.3.1.3 A new e-banking service that could have a significantimpact on an AI’s risk profile should be brought to theattention of the Board or its designated committee. Ingeneral, the Board or its designated committee shouldensure that their AI does not offer that service unless ithas the required expertise to exercise effective riskmanagement oversight.3.1.4 The Board or its designated committee, and seniormanagement should also ensure that a formal businessstrategy for introducing a new e-banking service is inplace. Moreover, the e-banking strategy should formpart of the AI’s overall business strategy.3.2 Risk management process3.2.1 The Board or its designated committee should ensurethat the risk management of e-banking is an integral partof the AI’s risk management system (see IC-1 “GeneralRisk Management Controls” and TM-G-1 “GeneralPrinciples for Technology Risk Management”). As aresult, the applicable risk management policies andprocesses, and the relevant internal controls and auditsas required in the AI’s risk management system shouldbe enforced and carried out as appropriate for the AI’s e-banking services.3.2.2 In addition, the Board or its designated committeeshould ensure that the AI’s risk management controlsand system are modified and enhanced as necessary tocope with the risk management issues associated withe-banking. The e-banking-related risk managementcontrols normally cover, at a minimum, the controlsmentioned in sections 4 and 5 of this module.3.3 Formulation of information security policy3.3.1 The senior management should ensure that the AIdevelops and maintains, on a regular basis,comprehensive information security policies relating toits e-banking services. The policies should be approvedand issued by the senior management. The documentsshould set forth the policies, procedures and controls tosafeguard the AIs’ operations against security breachesSupervisory Policy ManualTM-E-1Supervision of E-banking Consultationand intrusions, define individual responsibilities, anddescribe enforcement and disciplinary actions for non-compliance.3.3.2 Apart from the issuance and maintenance of informationsecurity policies, the senior management should alsopromote a security culture within the institution bydemonstrating their commitment to high standards ofinformation security in relation to e-banking, and widelycommunicating this to all relevant staff.4. Major technology-related controls relevant to e-banking4.1 Authentication of customers4.1.1 AIs should select reliable and effective authenticationtechniques to validate the identity and authority of theire-banking customers. Customer authentication isusually stronger when combining the following twofactors:knows (e.g. user IDs andcustomer• somethingapasswords); and•something a customer has (e.g. one-timepasswords6 generated by a security token or asmart card, and the customer’s private key7stored in a smart card or other physical devices).4.1.2 AIs need to evaluate carefully whether a particularauthentication method is sufficiently mature, and to whatextent the method remains secure even if a customer’sPC is compromised, e.g. by a Trojan horse program8. In6“One-time password” is a password that is valid for authentication only for a single access attempt or a limited period of time (e.g. around sixty seconds) so that even if this one-time password is captured by a hacker, the password cannot be reused for subsequent authentication.7In simple terms, “private key” is a secret cryptographic key that is provided only to the customer for authenticating the customer’s identity through public key cryptography.8 A Trojan horse is a computer program in which a harmful code is contained inside anapparently harmless program (e.g. a computer game). Trojan horses can infect a PC in circumstances such as when the attacker exploits the vulnerabilities of certain operating systems, and the victim opens contaminated e-mail attachments or visits malicious websites. Trojan horses can be used to capture screen displays and keystrokes, to steal information stored in, or to take over the control of, victims’ PCs.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultationgeneral, the HKMA expects AIs to employ strongercustomer authentication such as a combination of theabove methods9 for authenticating their customers’transactions with higher risk (e.g. unregistered third-party transfers and large-value transactions for corporateor institutional customers).4.1.3 If AIs determine to use only user IDs and passwords toauthenticate their e-banking customers after carefulconsideration of other relevant factors, they shouldimplement adequate customer security measures toprotect their customers’ passwords and to adopt aneffective monitoring mechanism to detect any unusualactivities (see section 5 below).4.1.4 Other than measures for authentication of customers,AIs should also implement appropriate means (e.g.installing digital certificates and related keys on their e-banking servers) for customers to validate the identityand genuineness of their websites (see also para. 5.5.1below).4.2 Confidentiality and integrity of information4.2.1 E-banking services entail transmission of sensitiveinformation (e.g. e-banking passwords) over the internetand AIs’ internal networks. AIs should thereforeimplement appropriate techniques to maintainconfidentiality and integrity of sensitive information whileit is in passage over the internal and external networks,and also, when it is stored inside AIs’ internal systems.4.2.2 Cryptographic technologies can be used to protect theconfidentiality and integrity of sensitive information. AIsshould choose cryptographic technologies that areappropriate to the sensitivity and importance ofinformation and the extent of protection needed. AIs arerecommended to adopt cryptographic technologies thatmake use of internationally recognised cryptographic 9For instance, employment of a two-factor authentication such as a combination of passwords and digital certificates will provide stronger customer authentication for higher risk transactions than a single factor authentication. AIs may consider exploring the feasibility of using the public key infrastructure developed and digital certificates issued locally (e.g. by Hongkong Post) to strengthen their customer authentication process.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultationalgorithms where the strengths of the algorithms havebeen subjected to extensive tests. AIs should implementsound key management practices to safeguard theircryptographic keys.4.2.3 AIs should consider the need to apply strong “end-to-end” encryption to the transmission of highly sensitiveinformation (e.g. e-banking passwords) so that it isencrypted all the way between customers’ devices andAIs’ trusted internal networks. This would help reducethe risk of highly sensitive information beingcompromised if AIs’ web servers10 or DMZ werepenetrated.4.2.4 If the technology selected by AIs does not allow “end-to-end” encryption and there is a decryption process atsome point between the customers’ devices andinstitution’s trusted internal networks, AIs should takeappropriate measures11 to protect the sensitiveinformation during the decryption process.4.2.5 In addition to the cryptographic techniques, AIs shouldalso implement other controls necessary to maintainconfidentiality and integrity of information processed bytheir e-banking systems. For examples, these include:•checks and controls incorporated in theapplication systems so as to reconcile data filebalances after transaction updates and to checkthe integrity of data transmitted between differentsystems;•segregation of e-banking transaction processingand monitoring functions so that no singleindividual will be allowed to initiate, authorize,process and dispose of an e-banking transactionor account without the collaboration of otherfunctions which serve to check the actions of thatindividual; and10 A web server is a computer dedicated to connect with the internet and serves the filesthat form the web page for access by any users on the internet.11One of the possible measures is that any cryptographic process (e.g. decryption) should be performed in a secure environment that is highly tamper-resistant.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultation•monitoring of unusual activities including any e-banking transactions or records being tamperedwith (see subsection 5.4 below).security4.3 Application4.3.1 Inadequate application security in e-bankingsystems increases the risk of successfulpenetration or security attacks. As a result, AIsshould ensure an appropriate level of applicationsecurity in respect of their e-banking systemshaving regard to the following sound practices12:•when AIs select system development tools orprogramming languages for developing e-bankingapplication systems, they should evaluate thesecurity features that can be provided by differenttools or languages to ensure that effectiveapplication security can be implemented. In thecase of selecting a third-party developed e-banking system, AIs should take into account theappropriateness of the application security of thesystem;•comprehensive and effective validation of inputparameters (including user-supplied data anddatabase queries that may be submitted by theusers’ computers) should be performed on serverside. This prevents intentional invalid inputparameters from being processed by the e-banking system that may result in unauthorizedaccess to data, execution of commandsembedded in the parameters or a buffer overflowattack13. Moreover, e-banking systems shouldoperate with the least possible system privileges;12AIs may find it useful to draw other references on application security, e.g. The Open Web Application Security Project () and the SANS (SysAdmin, Audit, Network, Security) Institute ().13 A buffer overflow attack aims at sloppily written programs which can read in more inputdata than it is designed to handle and causes parts of the computer memory being overwritten by the accepted data. These excessive input data could be manipulated to result in crashing of programs or execution of some sensitive instructions for unauthorized purposes in the targeted computer.Supervisory Policy ManualTM-E-1Supervision of E-banking Consultation•error messages generated by the applicationsystem for e-banking customers should not revealtechnical details of the system and errors shouldbe appropriately logged. Similarly, the HTML14source code on the production web server shouldnot contain sensitive information such as anyreferences or comments that relate to the designfeatures of the web application code;•the mechanism for managing an active e-bankingsession should be secure. For example, asession should be terminated after a definedperiod of inactivity. Web pages containingsensitive information should not be cached in thetemporary files of browsers;•the application should ideally prohibit thecustomers’ browsers from memorising ordisplaying the e-banking user IDs and passwordspreviously entered by customers and the e-banking web pages previously accessed bycustomers;•when a known vulnerability related to the e-banking application system is identified orreported, a review of the relevant program sourcecode should be conducted as appropriate toensure that the vulnerability is appropriatelyaddressed. A security standard may be definedfor the purpose of system development and codereview. For third-party developed systems, thepatches provided by vendors from time to timeshould be appropriately applied to these systems;•hidden directories that contain administrativepages or sensitive information of the web siteshould either be removed from the productionweb server or protected by effectiveauthentication and access control mechanisms.Back-up files and common files15 should be 14HTML refers to the Hypertext Markup Language, which is a standardised web page description language for creating web pages.15Back-up files and common files may contain file logs, pages, scripts or old versions of the website. The attacker normally searches through every file directory for these back-up and common folder names and file extension to obtain sensitive information of the site.。
