Key Centre of Design Computing
《飞行器综合电子系统》课程教学大纲
This course mainly introduces theaircrafts’avionicssystem, includingandevelopmentoverview and keytechnologiesoftheavionicssystem,the designrequirement andprinciple ofdisplay system, the parameter computing methods of theaircraftinstruments,thedesign and architectureof the system,thecomposition, principle and realizationofflight management system,thestructureandworkingprinciple ofautomatic flight control system, thekeyalgorithmsand threshold analysis methodsofenvironmentalsurveillancesystem,the navigation andcommunication system, andthe powersystem.
AVEVA最新三维工厂设计软件E3D
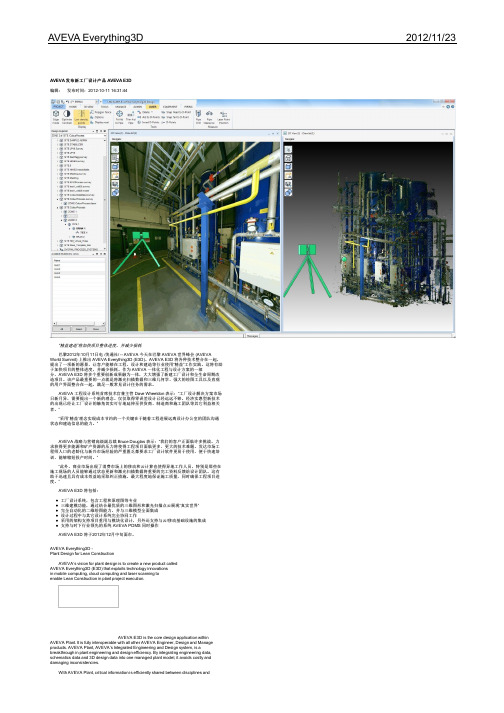
“精益建造”将加快项目整体进度,并减少损耗巴黎2012年10月11日电 /美通社/ -- AVEVA 今天在巴黎 AVEVA 世界峰会 (AVEVA World Summit) 上推出 AVEVA Everything3D (E3D)。
AVEVA E3D 将各种技术整合在一起,提出了一项新的愿景,让客户能够在工程、设计和建造等行业使用“精益”工作实践。
这将有助于加快项目的整体进度,并减少损耗。
作为 AVEVA 一体化工程与设计方案的一部分,AVEVA E3D 将多个重要创新成果融为一体,大大增强了新建工厂设计和全生命周期改造项目。
该产品最重要的一点就是将激光扫描数据和三维几何学、强大的绘图工具以及直观的用户界面整合在一起,满足一般常见设计任务的需求。
AVEVA 工程设计系统首席技术官兼主管 Dave Wheeldon 表示:“工厂设计解决方案市场日新月异,需要提出一个新的理念。
仅仅取得零误差设计已经远远不够。
经济实惠型新技术的出现已经让工厂设计的触角切实可行地延伸至供货商、制造商和施工团队等其它利益相关者。
”“采用‘精益’理念实现成本节约的一个关键在于随着工程进展远离设计办公室的团队沟通状态和建造信息的能力。
”AVEVA 战略与营销高级副总裁 Bruce Douglas 表示:“我们的客户正面临许多挑战。
力求获得更多能源和矿产资源的压力将使得工程项目面临更多、更大的技术难题。
发达市场工程师人口的老龄化与新兴市场经验的严重匮乏都要求工厂设计软件更易于使用、便于快速培训、能够缩短投产时间。
”“此外,商业市场出现了消费市场上的移动和云计算也使得异地工作人员,特别是那些在施工现场的人员能够通过状态更新和激光扫描数据将重要的完工资料反馈给设计团队。
这有助于迅速且具有成本效益地采取纠正措施,最大程度地保证施工质量,同时确保工程项目进度。
”AVEVA E3D 将包括:工厂设计系统,包含工程和原理图等专业三维建模功能,通过结合最优质的三维图形和激光扫描点云展现“真实世界”完全自动化的二维绘图能力,并与三维模型全面集成设计过程中与其它设计系统完全协同工作采用的架构支持项目重用与模块化设计,另外还支持与云/移动基础设施的集成支持与时下行业领先的系统 AVEVA PDMS 同时操作AVEVA E3D 将于2012年12月中旬面市。
水碳比对尿素合成系统的影响

水碳比对尿素合成系统的影响莫彩利 刘 亮 中原大化集团公司 濮阳 457004摘要 分析水碳比对尿素合成系统转化率的影响以及改进的方法。
关键词 水碳比 尿素合成 转化率中原大化集团公司520kt/a 尿素装置合成塔设计转化率65%,但实际转化率只有55%左右。
影响转化率的原因很多,其中水碳比是一个十分重要的因素。
本文着重介绍了如何减少系统水量以控制合成系统水碳比,从而提高转化率,增加产量。
1 基本原理及影响氨和二氧化碳在合成塔反应生成尿素,反应式:2NH 3+CO 2=CO (NH)2+H 2O从化学反应式可知,水的存在是不可避免的,有尿素生成就有水的生成,并且水的含量直接影响尿素的转化率。
根据斯纳姆公司提供的数据,在合成塔100%的负荷下,有约22t/h 水生成。
这些水一部分经中、低压系统加热分离后排出系统,一部分与氨、二氧化碳一起以碳铵液的形式存在,并在高压泵的作用下返回高压合成系统再次反应生成尿素。
水碳比对合成反应的影响见图1。
图1 水碳比对合成反应转化率的影响由图1可知,转化率随水碳比的增加而下降。
在工业生产条件下,一些实验表明,在其他影响条件不变情况下,水碳比每增加0 1,转化率将下降1 0%~1 05%。
在188 、氨碳比为3 5(摩尔比)时不同的水碳比对转化率的影响见表1。
表1 水碳比对转化率的影响水碳比(摩尔)0 30 50 70 91 1转化率,%73 2769 7566 2362 5959 19装置原设计合成塔出料水碳比为0 65,但在实际生产运行中,水碳比远远大于设计值,一般在0 9左右,有时高达1 4,使得合成转化率与设计转化率相差较大,降低了装置的生产能力。
2 原因及改进措施2 1 合成塔2 1 1 原因合成塔筒体高40m ,内径2 2m,每层塔板间距2 5m,共10层。
合成塔上部为塔板,物料在这一部分反应好,返混小,转化率高。
合成塔下部有15m 空间,占全部容积的3/8,反应推动力小,物料易返混,反应不好,转化率低,使反应后有更多的水生成,后系统不能完全消化这部分水,从而使过多的水又回到了合成塔,导致系统水碳比高。
英语作文loong和dragon的区别

英语作文loong和dragon的区别全文共3篇示例,供读者参考篇1A Tale of Two Processors: Loong and Dragon Chips ComparedAs a computer science student, I've become fascinated by the world of processors – those tiny yet incredibly powerful computing engines that make our digital devices run. Recently, two homegrown Chinese processor architectures have caught my attention: the Loong and the Dragon chips. While both are designed and manufactured in China, they have distinct characteristics that set them apart. In this essay, I'll delve into the key differences between these processors, exploring their performance, architecture, and potential applications.Performance: The Need for SpeedOne of the most critical factors in evaluating a processor is its performance, measured in terms of clock speed, instructions per cycle (IPC), and overall throughput. The Loong architecture, developed by Loongson Technology Corporation, boasts impressive performance capabilities. The latest Loong64 3A5000processor, for instance, features a clock speed of up to 3.0 GHz and supports up to 256 cores, making it a formidable contender in the high-performance computing (HPC) arena.On the other hand, the Dragon chips, designed by Higon Information Technology Co., Ltd., have been primarily focused on delivering cost-effective performance for general-purpose computing tasks. The Dragon V9 processor, for example, operates at a modest clock speed of 1.8 GHz but offersquad-core processing capabilities, making it suitable for applications that don't require extreme computational power.Architecture: Diverging PathsThe Loong and Dragon processors have taken different architectural approaches, each with its own strengths and weaknesses. The Loong architecture is based on the MIPS64 instruction set architecture (ISA), which has a long history and is known for its simplicity and efficiency. This design philosophy has allowed Loongson to optimize the Loong chips forhigh-performance computing tasks, such as scientific simulations, data analysis, and artificial intelligence (AI) workloads.In contrast, the Dragon processors adopt the GroundMedia ISA, which is derived from the ARM architecture. This decisionwas likely driven by the widespread adoption of ARM-based processors in mobile and embedded devices, as well as the vast ecosystem of software and development tools available for ARM. The GroundMedia ISA aims to strike a balance between performance and power efficiency, making Dragon chipswell-suited for applications in consumer electronics, Internet of Things (IoT) devices, and mobile computing.Ecosystem and Software SupportThe success of any processor architecture heavily depends on the availability of software and development tools. In this regard, the Loong and Dragon chips have taken divergent paths, each with its own challenges and opportunities.The Loong processors benefit from the well-established MIPS ecosystem, which includes a wide range of compilers, libraries, and development tools. Additionally, the open-source nature of the MIPS architecture has fostered a vibrant community of developers and researchers, contributing to the ongoing improvement and optimization of the Loong chips.On the other hand, the Dragon processors face the challenge of building a robust software ecosystem around the GroundMedia ISA. While ARM-based software can be ported to the Dragon architecture, the process can be complex and mayrequire significant effort from developers. However, the growing interest in Chinese-developed processors could spur the creation of dedicated development tools and libraries for the Dragon chips, potentially attracting a new generation of developers and software vendors.Applications and Use CasesGiven their distinct characteristics, the Loong and Dragon processors are better suited for different applications and use cases.The Loong chips, with their high-performance capabilities and support for massive parallelism, are well-positioned for applications in scientific computing, data centers, and artificial intelligence. These processors could power supercomputers, high-performance clusters, and specialized hardware accelerators for tasks like deep learning and large-scale data analysis.In contrast, the Dragon processors are more aligned with general-purpose computing tasks, such as desktop and mobile applications, embedded systems, and Internet of Things (IoT) devices. Their focus on cost-effectiveness and power efficiency makes them attractive choices for consumer electronics, smarthome appliances, and other devices that require moderate processing power while maintaining energy efficiency.Security and TrustworthinessIn an increasingly digital world, security and trustworthiness have become paramount concerns, particularly for critical infrastructure and sensitive applications. Both the Loong and Dragon processors have made efforts to address these concerns, but their approaches differ.The Loong architecture implements hardware-based security features, such as memory protection mechanisms and secure boot capabilities. These measures aim to prevent unauthorized access to sensitive data and ensure the integrity of the system during the boot process. Additionally, the open-source nature of the MIPS architecture allows for thorough security audits and community-driven security improvements.On the other hand, the Dragon processors leverage the security features inherited from the ARM architecture, including TrustZone technology and secure enclaves. These features enable hardware-based isolation and secure execution environments, protecting sensitive data and code from potential threats.ConclusionThe Loong and Dragon processors represent China's growing technological prowess and ambition to develop homegrown computing solutions. While they share a common goal of providing high-performance and energy-efficient processing capabilities, their architectural differences and design philosophies make them suitable for distinct applications and use cases.The Loong chips, with their MIPS-based architecture and focus on high-performance computing, are well-suited for scientific simulations, data analysis, and AI workloads. Their support for massive parallelism and hardware-based security features make them attractive choices for mission-critical applications and sensitive computing tasks.In contrast, the Dragon processors, built upon the GroundMedia ISA, offer a balance between performance and power efficiency, making them suitable for general-purpose computing tasks, consumer electronics, and IoT devices. Their ARM-based heritage provides a familiar development ecosystem, albeit with the challenge of building a robust software stack around the GroundMedia ISA.As these homegrown Chinese processors continue to evolve and gain traction, it will be fascinating to observe their impact on the global technology landscape. The competition between the Loong and Dragon architectures could drive innovation, foster the development of new software and hardware ecosystems, and ultimately benefit end-users by providing more choices and tailored computing solutions.篇2The Differences Between Loong and Dragon ProcessorsAs a student studying computer science, one area that has always fascinated me is the world of processors. These tiny yet incredibly complex components are the beating heart of our computers, responsible for executing instructions and performing calculations at lightning-fast speeds. In recent years, the processor market has witnessed the emergence of two fascinating architectures: the Loong and the Dragon. While both are designed to power our digital devices, they exhibit distinct characteristics that set them apart. In this essay, I will delve into the key differences between these two processor families, exploring their origins, architectures, performance, and potential applications.Origins and Background:The Loong processor finds its roots in China, developed by Loongson Technology Corporation, a company based in Beijing. Loongson's mission has been to create a domestic,high-performance processor architecture that can compete with established players like Intel and AMD. The first Loong processor, the Loongson 1, was introduced in 2001, marking the beginning of China's journey towards self-sufficiency in the processor domain.On the other hand, the Dragon processor emerged from the United States, born out of the collaborative efforts of several technology giants, including Google, Amazon, and Ampere Computing. The Dragon architecture was designed to address the growing demand for energy-efficient and scalable processors, particularly in the realm of cloud computing and data centers.Architectural Differences:One of the most fundamental differences between the Loong and Dragon processors lies in their underlying architectures. The Loong processors are based on the MIPS (Microprocessor without Interlocked Pipeline Stages) instruction set architecture (ISA), which has a long history dating back to the1980s. MIPS is known for its simplicity, efficient pipeline design, and compatibility with a wide range of software and operating systems.In contrast, the Dragon processors are built upon the Arm instruction set architecture (ISA), which has become increasingly popular in the mobile and embedded systems market. Arm's strength lies in its power-efficient design, making it an attractive choice for devices with limited power budgets, such as smartphones, tablets, and Internet of Things (IoT) devices.Performance and Capabilities:When it comes to performance, both the Loong and Dragon processors have their strengths and weaknesses. The Loong processors have traditionally been geared towardhigh-performance computing (HPC) applications, offering impressive computational power and support for advanced features like vector processing and multithreading. However, they have sometimes lagged behind their Intel and AMD counterparts in terms of raw processing power and software ecosystem support.The Dragon processors, on the other hand, have been optimized for cloud computing and data center workloads. They excel in areas such as parallel processing, virtualization, andenergy efficiency. While they may not match the raw performance of high-end server processors from Intel and AMD, the Dragon processors offer a compelling balance of performance and power efficiency, making them well-suited for large-scale deployments in cloud environments.Applications and Use Cases:The differing architectures and capabilities of the Loong and Dragon processors lend themselves to different applications and use cases.Loong processors have found their niche inhigh-performance computing environments, such as scientific simulations, weather forecasting, and computational fluid dynamics. They are also utilized in certain server and workstation applications where performance is the primary consideration. Additionally, the Loong architecture has garnered interest from the Chinese government and military for national security and defense applications, as it provides a domestic alternative to foreign-made processors.On the other hand, Dragon processors are primarily targeted at cloud computing and data center infrastructure. Their energy-efficient design and scalability make them well-suited for powering large-scale cloud services, web servers, and distributedcomputing applications. Companies like Amazon and Google have already begun deploying Dragon-based processors in their data centers, taking advantage of their cost-effectiveness and power savings.Future Outlook and Implications:As technology continues to evolve, both the Loong and Dragon processor architectures are poised to play significant roles in shaping the future of computing.For the Loong processors, the primary challenge lies in gaining wider adoption and software ecosystem support. While China's push for domestic technology has driven the development of the Loong architecture, its adoption outside of specialized domains has been limited. Overcoming this hurdle and fostering a robust software ecosystem will be crucial for the Loong processors to compete on a global scale.The Dragon processors, backed by industry giants like Google and Amazon, have a strong foundation and significant resources invested in their development. As cloud computing and data center demands continue to grow, the need for energy-efficient and scalable processors will likely increase, positioning the Dragon architecture as a compelling solution. However, competition from established players like Intel andAMD, as well as emerging architectures like Arm's Neoverse, will keep the landscape dynamic and competitive.Conclusion:In the ever-evolving world of processors, the Loong and Dragon architectures represent two distinct approaches to addressing the computational demands of our digital age. While the Loong processors excel in high-performance computing and offer a domestic alternative for China, the Dragon processors have carved out a niche in the cloud computing and data center realm, leveraging their energy efficiency and scalability.As a student fascinated by these technologies, I find it exciting to witness the advancements and innovations happening in the processor space. The competition between different architectures and the pursuit of performance, efficiency, and versatility will undoubtedly drive further technological breakthroughs. Regardless of which architecture ultimately prevails, one thing is certain: the relentless pursuit of computing power will continue to shape our digital future in ways we can scarcely imagine.篇3The Loong and Dragon: A Tale of Two Chinese CPUsAs a student of computer science, I've become fascinated by the world of processors and the companies that design them. While most of us are familiar with the big names like Intel and AMD, there are other players in the game, particularly in China. Two such processors are the Loong and the Dragon, both designed and manufactured by Chinese companies. At first glance, they may seem similar, but upon closer inspection, some significant differences emerge.The Loong processor is developed by Loongson Technology Corporation Limited, a company based in Beijing. It is a RISC (Reduced Instruction Set Computer) processor, which means it has a relatively simple instruction set architecture (ISA) compared to more complex designs like x86. The Loong family includes several different models, such as the Loong3A4000 and the Loong3C3000, each with varying levels of performance and power efficiency.One of the key advantages of the Loong processor is its compatibility with the MIPS instruction set, which has been around since the 1980s. This compatibility allows the Loong to run a wide range of existing software that has been compiled for MIPS architectures. Additionally, the Loong processors are designed with a focus on low power consumption, making themsuitable for use in embedded systems and other applications where energy efficiency is crucial.On the other hand, the Dragon processor is developed by Higon Information Technology Co., Ltd., a company based in Tianjin. Unlike the Loong, the Dragon is a CISC (Complex Instruction Set Computer) processor, which means it has a more complex instruction set architecture. The Dragon family includes models such as the Dragon V9, which is designed for use in servers and high-performance computing applications.One of the key advantages of the Dragon processor is its compatibility with the x86 instruction set, which is widely used by many popular operating systems and applications. This compatibility allows the Dragon to run a vast array of software that has been compiled for x86 architectures, without the need for emulation or recompilation. Additionally, the Dragon processors are designed with a focus on high performance, making them suitable for use in demanding applications such as scientific simulations and data processing.Despite their differences, both the Loong and the Dragon processors share a common goal: to reduce China's reliance on foreign-made processors and foster the growth of a domestic semiconductor industry. This goal has become increasinglyimportant in recent years, as tensions between China and the United States have escalated, and concerns over supply chain security have grown.From a technical standpoint, one of the key differences between the Loong and the Dragon processors lies in their instruction set architectures. As mentioned earlier, the Loong is a RISC processor, while the Dragon is a CISC processor. RISC architectures are generally simpler and more energy-efficient, while CISC architectures are more complex and can execute more complex instructions in a single cycle.Another important difference is their respective performance capabilities. While the Loong processors are designed with a focus on low power consumption, they tend to lag behind the Dragon processors in terms of raw computational power. The Dragon processors, on the other hand, are designed to deliver high performance, making them better suited for demanding applications such as scientific simulations and data processing.It's worth noting that both the Loong and the Dragon processors are still relatively new players in the market, and their adoption and development are closely tied to the broader goals of China's semiconductor industry. As such, it's likely that we'llcontinue to see ongoing improvements and innovations in both processor families as time goes on.From a student's perspective, the competition between the Loong and the Dragon processors is fascinating to observe. On one hand, the Loong's compatibility with the MIPS instruction set and its focus on low power consumption make it an interesting option for embedded systems and other applications where energy efficiency is a priority. On the other hand, the Dragon's compatibility with the x86 instruction set and its focus on high performance make it a compelling choice for demanding applications such as scientific simulations and data processing.Ultimately, the choice between the Loong and the Dragon processors will likely depend on the specific needs of the application and the priorities of the user or organization. For students like myself, the opportunity to learn about and work with these processors can be invaluable, as it provides exposure to different architectures and design philosophies.As I continue my studies in computer science, I'll be keeping a close eye on the developments in the Loong and Dragon processor families, as well as the broader landscape of China's semiconductor industry. It's an exciting time to be in this field,and I can't wait to see what the future holds for these homegrown Chinese processors.。
体现“两性一度”的计算机类服务学习课程设计与实践

第 22卷第 6期2023年 6月Vol.22 No.6Jun.2023软件导刊Software Guide体现“两性一度”的计算机类服务学习课程设计与实践戴开宇1,洪浏2,徐珂2(1.复旦大学计算机科学与技术学院; 2.复旦大学社会发展与公共政策学院,上海 200433)摘要:通常情况下,理工科类服务学习课程对专业知识的学习较浅,服务手段较为简单,难以满足“两性一度”的“金课”标准。
为此,以计算思维与信息素养课程教学设计与实践为例,分析如何针对计算机类专业体现“两性一度”的服务学习类课程建设。
通过确定知识、能力和价值观层面的学习目标,采用“逆向设计”原则制定学习评测方法,设计结合专业知识学习和服务实践环节的学习活动,以体现符合“一致性建构”的教学设计。
教学实践表明,该方法取得了良好的教学效果。
关键词:服务学习;两性一度;计算机类课程;逆向设计;一致性建构DOI:10.11907/rjdk.221829开放科学(资源服务)标识码(OSID):中图分类号:TP311.5;G434 文献标识码:A文章编号:1672-7800(2023)006-0007-06Design and Practice of Computer Related Service Learning Course Embodying“Two Characteristics and One Degree”DAI Kai-yu1, HONG Liu2, XU Ke2(1.School of Computer Science, Fudan University;2.School of Social Development and Public Policy, Fudan University, Shang⁃hai 200433, China)Abstract:Generally speaking, science and engineering service learning courses have a shallow understanding of professional knowledge and simple service methods, making it difficult to meet the "golden course" standard of "two characteristics and one degree". Therefore, taking the teaching design and practice of computational thinking and information literacy as an example, analyze how to build a service learning curricu‐lum that reflects "two characteristics and one degree" for computer majors. By determining learning objectives at the level of knowledge, abili‐ty, and values, adopting the principle of "reverse design" to develop learning evaluation methods, designing learning activities that combine professional knowledge learning and service practice, to reflect teaching design that conforms to the "consistency construction". Teaching prac‐tice has shown that this method has achieved good teaching results.Key Words:service learning; two characteristics and one degree; computer related courses; reverse design; constructive alignment0 引言服务学习(Service-Learning)是将学术知识与社区志愿服务合二为一的体验式教学方法[1],在国内属于较为新型的教学方式,也是复旦大学正在重点建设的一类课程。
顶级期刊排名

顶级期刊排名Get:小虫 21:07:18/doc/878268801.html/loi/coli小虫 21:07:40/doc/878268801.html/science?_ob=PublicationURL&_tockey=%23TOC%2356 17%232010%23998259981%232520777%23FLP%23&_cdi=5617 &_pubType=J&_auth=y&_acct=C000050165&_version=1&_urlVersion=0&_userid=1002903& md5=fa794527d6fa620604 73b0b181eb1ab4小虫 21:07:46/doc/878268801.html/RankList?entitytype=4&domainID=5&last=0&start=1&end=100小虫 21:07:54/doc/878268801.html/citation.cfm?id=J1206&picked=prox小虫 21:08:00/doc/878268801.html/xpl/RecentIssue.jsp?punumber=9670小虫 21:08:08/doc/878268801.html/doi/10.1111/coin.2010.26.issue-4/issuetocAREA: Artificial IntelligencePremium:Artificial IntelligenceComputational LinguisticsIEEE Trans on Pattern Analysis and Machine IntlIEEE Trans on Robotics and AutomationIEEE Trans on Image ProcessingJournal of AI ResearchNeural ComputationMachine LearningIntl Jnl of Computer V isionIEEE Trans on Neural NetworksLeading:Artificial Intelligence ReviewACM Transactions on Asian Language Information ProcessingAI MagazineAnnals of Mathematics and AIApplied Artificial IntelligenceApplied IntelligenceArtificial Intelligence in Medic ineAutonomous Agents and Multi-Agent SystemsComputational IntelligenceComplex SystemsComputer Speech and LanguageComputer Support for Collaborative Learning (CSCL)Computer V ision and Image UnderstandingConnection ScienceCVGIP: Graphical Models & Image Processing CVGIP: Image UnderstandingExpert Systems with Applications: An Intl JnlIEEE Transaction on Speech and Audio ProcIEEE Trans on Systems, Man, & Cybernetics, Part A & B Intl Jnl on Artificial Intelligence ToolsJnl of Experimental & Theoretical AIJournal of East Asian LinguisticsKnowledge Engineering ReviewMachine TranslationNeural NetworksNetwork Computing in Neural SystemsPattern Analysis and ApplicationsPattern RecognitionNeurocomputingUser Modelling & User-Adapted Interaction: an Intl JnlReputable:Communications of COLIPSComputer Processing of Chinese & Oriental Languages Computers and Artificial IntelligenceCybernetics and SystemsEngineering Intelligent Systems for EE and CSExpert SystemsEvolutionary ComputationIntelligent Instruments & ComputersIntl Jnl for AI in EngineeringIntl Jnl of Applied Expert SystemsIntl Jnl of Approximate ReasoningIntl Jnl of Intelligent SystemsIntl Jnl of Neural SystemsIntl Jnl of Pattern Recognition & AIIntl Journal of Document Analysis and Recognition IEEE Transactions on Fuzzy SystemsJournal of Intelligent and Fuzzy SystemsKnowledge Acquisition JnlKnowledge-Based SystemsKybernetikaNatural Language EngineeringNeural Computing & ApplicationsNetwork SocietyNeural Processing LettersPattern Recognition LettersIEE Proceedings: Vision, Image and Signal Proc Speech CommunicationsJournal of Neural Network ComputingMinds and Machines: Jnl for AI, Philosopy and Cog. ScIntl Jnl of Uncertainty, Fuzziness and KBSHeuristics: Jnl of Knowledge EngineeringEngineering Applications of AIJnl. of Japanese Soc. of AIAustralian Jnl of Intelligent Information Proc SysIntelligent Data AnalysisImage and V ision ComputingJournal of Artificial Neural NetworksNeural, Parallel and Scientific ComputationsRoboticaOthers:AIAA JournalCanadian Artificial IntelligenceJournal of Advanced RoboticsJournal of Artificial Intelligence in EducationJournal of Artificial Intelligence in Engineering, Automation, and Manufacturing Journal of Artificial Intelligence, Neural Networks and ComplexJournal of Computational AcousticsJournal of Computational NeuroscienceJournal of Computational VisionJournal of Card. ImagingJournal of CyberneticsJournal of Cybernetics and Information ScienceJournal of Design Automation of Embedded SystemsJournal of Knowledge-Based Intelligent Engineering Systems Journal of Intelligent Robotic Systems: Theory and ApplicationsJournal of Systems Automation: Research and Applications Journal of Automation and Remote ControlJournal of Intelligent Automation & Soft ComputingJournal of Intelligent Control and SystemsJournal of Intelligent and Robotic SystemsJournal of Intelligent ManufacturingJournal of Intelligent Systems EngineeringJournal of Intelligence SystemJournal of Intelligent TechnologyJournal of Literary and Linguistic ComputingJournal of Machine V ision and ApplicationsJournal of Man-Machine StudiesJournal on Neural and Mass-Parallel Computing and Information Systems Journal of Robotics and Mechatronics Journal of Robotic SystemsJournal of Robotics and Autonomous SystemsJournal of Robotics ResearchJournal of the Robotics Society of JapanJournal of Computational NeurologyInternational Journal of LexicographyJournal of intelligent ComputingInternational Journal of Intelligent Systems in Accounting Finance and Management International Journal of SpeechTechnologyEngineering Design and Automation JournalInternational Journal of Machine Tools & ManufacturingInternational Journal of Corpus LinguisticsJournal of Chinese Information ProcessingAREA: Algorithms, Theory and Related AreasPremium:AlgorithmicaComputational ComplexityDiscrete & Computational GeometryIEEE Trans on Information TheoryInformation & ComputationJnl of AlgorithmsJnl of Computer and System SciencesJnl of the Association for Computing MachinerySIAM Jnl on ComputingACM Trans on Computational Logic (TOCL)Leading:Acta InformaticaChicago Journal of Theoretical Computer ScienceDesigns, Codes and CryptographyJnl of Symbolic ComputationJournal of Automated ReasoningJournal of Graph Algorithms and ApplicationsJournal of ComplexityJournal of CryptologyJOTA - J. of Optimization: Theory and ApplicationsMathematics of ComputationMathematical ProgrammingOptimization: A J. of Mathematical Programming andOperations ResearchORSA Journal of ComputingNordic J of Computing (BIT)SIAM Journal on OptimizationRandom Structures & AlgorithmsTheoretical Computer ScienceReputable:Applicable Algebra in Eng., Comm., and ComputingApplied Maths and ComputationBIT: Computer Science and Numerical MathematicsBulletin of the European Assoc. for Theoretical CSComputational and Applied MathsComputers & Mathematics With ApplicationsCombinatorics, Probability & ComputingEuropean Journal of ORJournal of Computer and System Sciences International Intl Jnl of Foundations of Computer ScienceOthers:Problem Solving T echnologiesJournal of Algebraic CombinatoricsJournal of Combinatorial DesignsJournal of Combinatorial OptimizationJournal of Experimental AlgorithmicsJournal of Electronic ImagingIntl Jnl for Numerical Methods in EngineeringSIAM Journal of Algorithms and Discrete MethodsSIAM Journal on Algebraic and Discrete MethodsSIAM Journal on Numerical AnalysisSIAM Journal on Matrix Analysis and ApplicationsNaval Journal of Operations ResearchJournal of SchedulingElectronic Journal of CombinatoricsJournal of Mathematical Modeling and Scientific Computing Journal of Mathematical Structures in Computer ScienceInternational Journal on Mathematical and Computer ModelsJournal of Global OptimizationJournal of Computational Statistics and Data Analysis微软学术搜索总结的人工智能(AI)领域顶级期刊2010-07-08 20:16Publications CitationsA I - Artificial Intelligence2502 96833 J AIR - Journal of Artificial Intelligence Research515 11757 I JRR - International Journal of Robotic Research1394 17018 A IM - AI Magazine1146 13937 A AMAS - Autonomous Agents and Multi-Agent Systems339 5119 A ROBOTS - Autonomous Robots583 7211 A LIFE - Artificial Life440 5637 J AR - Journal of Automated Reasoning766 7982 J IIS - Journal of Intelligent Information Systems448 5312 E XPERT - IEEE Expert / IEEE Intelligent Systems1578 13138 A IR - Artificial Intelligence Review495 4054 A MAI - Annals of Mathematics and Artificial Intelligence848 5688 A AI - Applied Artificial Intelligence809 5076 JETAI - Journal of Experimental and Theoretical Artificial407 3064 IntelligenceA RTMED - Artificial Intelligence in Medicine865 5196 J VCIR- Journal of Visual Communication and Image Representation472 3114 A ICOM - AI Communications422 2526 I JAR - International Journal of Approximate Reasoning1102 4756 I JIS - International Journal of Intelligent Systems828 3718 A IL - Artificial Intelligence and Law268 1304 J ournal of Scientific Computing 610 2171 International Journal of Humanoid Robotics167 473 J ournal of Field Robotics377 716 J IFS - Journal of Intelligent and Fuzzy Systems426 607 R obotica559 461 I JHIS - International Journal of Hybrid Intelligent Systems125 92 IJMTM - International Journal of Manufacturing Technology and447 164 ManagementI JSN - International Journal of Security and Networks114 80A nnual Reviews in Control56 46I JIQ - International Journal of Information Quality35 22A CM SIGSMALL Newsletter23 13I EEE Transactions Automation Science and Engineering64 13I JIA - International Journal of Information Acquisition173 11J OCCH - ACM Journal on Computing and Cultural Heritage18 3A CM SIGMOD Digital Symposium Collection 4 0A CM SIGPC Notes计算机视觉、IP、AI方向的一些顶级会议和期刊收藏计算机视觉方面的三大国际会议是ICCV, CVPR和ECCV,统称之为ICE。
基于工作流引擎的构件组装体系结构
ISSN 1000-9825, CODEN RUXUEW E-mail: jos@Journal of Software, Vol.17, No.6, June 2006, pp.1401−1410 DOI: 10.1360/jos171401 Tel/Fax: +86-10-62562563© 2006 by Journal of Softwar e. All rights reserved.∗基于工作流引擎的构件组装体系结构李海波1,2+, 战德臣1, 徐晓飞11(哈尔滨工业大学计算机科学与技术学院企业智能计算研究中心,黑龙江哈尔滨 150001)2(东北农业大学工程学院,黑龙江哈尔滨 150030)Architecture of Component Composition Based on Workflow EngineLI Hai-Bo1,2+, ZHAN De-Chen1, XU Xiao-Fei11(Centre of Intelligent Computing of Enterprises, School of Computer Science & Technology, Harbin Institute of Technology, Harbin150001, China)2(Engineering Institute, Northeast Agricultural University, Harbin 150030, China)+ Corresponding author: Phn: +86-451-55116600, Fax: +86-451-86412664, E-mail: lihaibo@, Li HB, Zhan DC, Xu XF. Architecture of component composition based on workflow engine. Journal ofSoftware, 2006,17(6):1401−1410. /1000-9825/17/1401.htmAbstract: Nowadays, SA (software architecture) and CBSD (component-based software development), haveshown great advantage in software development. CBSD is a successfully applied down-top methodology to softwaredevelopment; whereas SA still lacks a top-down component composition methodology, especially in processcomponent. Based on workflow and the background of Web application, a component composition method isinvestigated. Being started with the key elements of business process, such as business object, control flow and dataflow, characteristics and interactions between them are formalized. A workflow engine based SA of processcomponent composition is proposed. Except for the control flow, the SA can deal with data flow between businessactivities, and provide a reference to others in applying archive workflow to component composition.Key words: workflow; workflow engine; component composition; process component; control flow; data flow摘要: 近年来,软件体系结构(SA)、基于构件的软件开发技术(CBSD)等开始在软件开发中发挥出重要的作用.CBSD应用的成功主要体现在自底向上构造系统的方法上.目前,对SA的研究还缺乏一种自顶向下的构件动态组装方法,尤其是过程构件的组装.以工作流技术为基础,以基于Web应用为背景,研究了基于工作流引擎的构件组装方法.从业务过程的基本要素——业务对象、控制流和数据流入手,详细分析了这些要素在构件环境下的特点和交互模式,并以此为基础提出了一种基于工作流的引擎的过程构件组装体系结构.该体系结构中除了考虑常规的控制流驱动的构件组装外,还深入研究了文档型的数据流驱动的构件组装机制,能够为其他研究者将文档型工作流技术应用于软件构件组装提供借鉴和参考.关键词: 工作流;工作流引擎;构件组装;过程构件;控制流;数据流中图法分类号: TP301文献标识码: A∗ Supported by the National Natural Science Foundation of China under Grant No.60573086 (国家自然科学基金); the NationalHigh-Tech Research and Development Plan of China under Grant No.2003AA4Z3210 (国家高技术研究发展计划(863)); the NationalResearch Foundation for the Doctoral Program of Higher Education of China under Grant No.20030213027 (国家教育部博士点基金)Received 2005-12-14; Accepted 2006-03-131402 Journal of Software软件学报 V ol.17, No.6, June 2006基于构件的软件工程(component based software engineering,简称CBSE)逐渐成为软件开发的主流范型,是软件开发工程化的现实可行途径.构件必须经过组装才能形成应用系统,所以构件组装技术是关键[1].构件组装的本质是,在构件之间建立关联,根据这种关联协调它们的行为,把它们组织成为一个有机的整体.构件组装策略之一是自顶向下的组装方法,它开始于系统的集中模型,而忽略底层细节,通过逐步求精把细节逐渐引入到框架中来;构件组装的策略之二是自底向上的方法,对各子系统单独建模而忽略它们之间的相互作用.近年来,软构件应用比较成功的模式就是基于标准化运行级构件的规范进行开发,如CORBA,EJB和DCOM,中间件技术作为存在于系统软件与应用之间的特殊层次,抽象了典型的应用模式,是一种自底向上构造软件系统的途径.但当通过组装,构件的粒度由原子构件逐渐变大到过程构件(业务过程)的时候,构件间开始存在一种偏序关系,它描述了活动的执行顺序,是工作流视图[2].目前,对构件组装的研究大多侧重于较高层次的抽象描述,比如接口规约、功能规约等.从工作流角度、业务过程逻辑和业务活动实现分离的思想,使得过程的组装更贴近于自顶向下的组装途径,而当前的研究缺乏一种按照过程的抽象描述组装过程构件的方法.构件按照执行顺序进行组装不能仅仅满足于构件的接口规约,还应该考虑运行时构件的状态.通过与用户以及其他构件的不断交互,构件的状态不断发生变化,在控制条件的约束下,不断地选择、实例化新构件.对执行顺序的处理虽然适合采用工作流技术[2],但在构件环境下,执行顺序的引入增加了过程维的考虑,为构件组装提出了新需求.过程视角体现在工作流技术的两个最基本的特征——控制流和数据流上,前者体现了工作流活动间的执行偏序;后者体现的是活动间的数据依赖关系.因此,从工作流的基本特征分析入手,必然能够准确地掌握基于工作流引擎的构件组装系统结构.因此需要研究:1) 工作流引擎和执行构件(活动)的交互模式,即控制流;2) 可执行构件间的数据交互模式;3) 基于角色的权限控制模式,体现了一种构件重用方法;4) 基于工作流引擎的过程构件组装的系统结构.为此,以基于Web的应用为背景,提出一种基于工作流引擎的过程构件组装体系结构.从分析工作流的基本特征入手,提出了工作流引擎和构件、构件之间的交互模式,以及基于这种交互模式的工作流引擎内部结构,最后给出了按照过程描述组装过程构件的系统结构,并通过一个具体实例加以说明.1 相关工作构件组装研究主要包括两部分:复合构件形成过程研究和基于体系结构(或者组装框架)的研究.其中,前者是为了得到性能稳定、有较强可靠性的复合构件,以用于构件组装,后者则是寻求良好的组装策略以实现开发目的.基于软件体系结构的构件组装方法是构件组装的主流研究方向,是实现构件生产与组装的技术基础,目前取得了一定的进展,如基于软件体系结构的构件组装技术——ABC方法[1,3].对构件组装的研究主要分为如下几个方面:1) 通过体系结构的建模和高层描述进行构件的组装方法[4,5],研究高层的一些性质;2) 通过过程结构[6]以及基于语义和知识[7]的方法,研究过程构件的组装方法;3) 分布式环境下过程构件组装研究主要包括服务组合[8]和构件调度优化[9]等方面.Avoca[10]是软构件技术应用中比较成功的例子.该系统可以利用现有的构件和通信协议组装软件系统,但是,构件的修改必须了解足够的领域知识.SA提供了一种自顶向下构造软件系统的方法,但目前对其研究大多局限于建模和高层描述[4,5]上.对于过程构件的组装方法,多数研究主要集中在过程结构[6]、优化[11]和适应性[9]等方面.对采用SA进行过程构件组装并映射到实现层的研究相对较少,并且,过程中的数据流是构件交互的基础,对数据流的交互模式则考虑得更少.2 概述2.1 基本概念企业日常经营活动中涉及到的相关信息实体与物理实体,如订单、报表、设备、员工等,我们称这类信息为业务对象.业务对象是指企业中所有物理资源和信息资源在信息系统中的抽象,通过一组连续的操作,使得业李海波 等:基于工作流引擎的构件组装体系结构 1403务对象的属性不断改变,最终完成对一个业务对象的处理过程.业务对象之间的交互是工作流系统的数据特性之一[12].因此,首先给出几个相关概念.定义1(业务对象). 业务对象可以用一个三元组表示,记为bo =(ID ,A ,M ).其中:(1) ID 为该业务对象的唯一标识;(2) A 为bo 的属性a i (i=1,2,…,m )的集合,a j (bo )表示bo 的属性集合a j ;(3) M 为作用于bo 上的业务操作m i (i=1,2,…,n )的集合.定义2(业务操作). 业务操作表示为op =(r ,bo ,A ).op 是由一个特定角色r 作用于bo 上的一个原子性动作,并使bo 的属性发生变化;A 表示op 作用的业务对象bo 的属性集合,业务操作与业务对象中的业务操作一一 对应.定义3(业务活动). 业务活动定义为三元组ba =(r ,OP ,),是由一个特定角色r 不间断地执行的一组业务操作的集合OP .是业务操作构成的偏序关系.p p 定义4(业务过程). 业务过程bp 是为实现特定的业务目标,由不同角色执行的一组具有偏序关系的、逻辑上相互关联的、作用于一组相关业务对象上的业务活动,业务活动间的偏序关系由约束条件确定.业务过程可定义为五元组bp =(R ,BA ,BO ,P ,):p (1) R 为角色的集合;(2) BA 表示业务活动ba i (i =1,2,…,n )的集合;(3) BO 表示业务对象的集合;(4) P 表示约束条件的谓词集合;(5) 表示业务活动之间的执行偏序关系.p 上述定义说明:业务过程是由一系列存在执行偏序关系的活动组成,体现了业务活动间的控制流.而业务活动可以进一步分解成一系列业务操作,使业务对象属性发生变化,数据流是在不同业务对象间交互时产生的.2.2 交互式Web 文档(Web document )的多重作用Web 技术对于解决大规模且异构的系统具有其他技术所不可比拟的优势,所以,我们以Web 应用为背景研究构件组装.工作流活动的实现方法之一就是提供交互式的Web 文档(Web page),所以,Web 文档最明显的一个作用就是与用户进行交互:接收用户的输入以及显示处理结果.此外,如果交互式Web 文档的处理涉及到工作流,那么该文档接收的数据可以直接用于确定工作流的路由,或者作为工作流相关数据[13]被提交给工作流引擎,用于确定活动的状态或者计算后续活动.另外,交互式Web 文档之间也随时交换各自的数据.所以在构件环境下,如果考虑工作流,交互式Web 文档共有3个作用:与用户进行交互;与工作流引擎进行交互;活动间的数据交互.因此,Web 文档具有如下定义:定义5(Web 文档). Web 文档表示成WDoc =(C ,D ).其中:C 是构件的集合,包含两类构件,C =(FC ,IC ),分别表示功能构件和界面构件.功能构件用于处理业务逻辑(业务操作),界面构件负责业务对象属性的表示,二者最终组装成业务活动ba ; D 是文档中的数据,包含3类数据,记为D =(UD ,WfRD ,WfID ).其中:UD 是用户数据;WfRD 是工作流相关数据,是用于计算活动间执行偏序的用户数据的子集[13];WfID 是工作流实例数据,并用于控制Web 文档中的数据流.一个Web 文档可以实现一个业务活动.3 基于工作流引擎的构件环境工作流管理技术的主要贡献就是业务过程逻辑和业务活动实现的分离.在运行阶段,工作流引擎根据过程模型调度业务活动的执行,在构件环境下,则是过程构件动态组装的集中体现.过程构件组装时不一定实例化模型中的所有构件,对构件实例化排序就是对过程构件的调度.基于对交互式Web 文档的认识,工作流引擎和构件间的关系总体上概括为两个方面:执行调度和数据交互.下面从工作流技术的两个最基本的特征:控制流和数据流以及权限控制方面进一步分析构件环境下工作流引擎的调度和交互机制.1404Journal of Software 软件学报 V ol.17, No.6, June 20063.1 控制流3.1.1 过程控制方式 从定义4可以看出,业务活动间存在一种执行偏序关系,这种偏序关系被抽象为过程描述,并作为调度规则由工作流引擎进行翻译,结果就是活动的执行顺序(工作流引擎的结构见第3.5节).用户不断地与Web 文档进行交互,使业务对象的属性不断发生变化,并依据静态的过程描述和运行时业务对象属性的取值计算后续活动.定义6(执行偏序关系). 对于∀ba i ,ba j ∈BA ,设bo i 和bo j 分别为ba i 和ba j 操作的两组业务对象,如果在4种基本控制结构[13]的作用下,依据谓词P (a 1,a 2,…,a n ), a i ∈a i (bo i ),能够确定出执行顺序,则称活动ba i 和ba j 之间具有执行偏序关系,记为(ba i p ba j )p ;反之,记为(ba j p ba i )p.工作流引擎依据业务过程中的谓词P (a 1,a 2,…,a n )在运行时的取值计算后续活动,属性a 1,a 2,…,a n 称为工作流相关数据,其含义实质上与工作流管理联盟(WfMC)给出的定义相同.图1是制造企业典型的设备维修过程,其中,实线表示执行偏序关系.根据运行时故障的大小(谓词P ),确定维修申请审批的后续活动是派工还是领料.Fig.1 Equipment maintenance process 图1 设备维修过程在基于构件的Web 环境下,过程构件实际上是集成在一起的、具有执行偏序关系的多个Web 文档.因此,Web 环境下过程构件的定义如下: 定义7(过程构件). 过程构件是由多个Web 文档以及Web 文档(活动)之间的执行偏序关系组成,表示成PC =(WDoc ,).p 过程构件是一系列构件按照执行偏序关系组装而成的更大粒度的构件,而业务活动则是由若干无执行偏序关系的构件组装而成.过程构件必须解决工作流引擎和工作流相关数据交互问题.3.1.2 与运行数据交互采用XML 作为Web 应用间的数据交换格式具有许多优点,比如结构化、易于校验、人与计算机均可读等.加之采用XSLT 样式表(style sheet)进行界面布局,则可以使Web 文档数据与表示方式相分离,因而常利用Web 及XML 来解决分布式环境下的互操作问题.为了实现对过程的调度,所采用的描述方法必须有能力与工作流相关数据进行交互.按照定义5,工作流相关数据对确定活动执行顺序起着关键作用.在交互式Web 文档中则具体体现为对业务对象操作的使能控制,比如,业务对象的“创建”按钮处于Disabled 状态,就表示业务对象暂时不满足创建条件,这种工作流调度模式见第3.3节.所以,既然运行数据最终要体现到Web 文档界面上,那么运行数据就可以生成XML 文件,然后再利用XSLT 样式表在构件组装时控制Web 文档的操作.为此,我们在语法上给出基于XSLT 样式表的相关描述方法.(1) 获取工作流相关数据当处理〈xsl: for-each 〉元素时,处理过程依赖于工作流相关数据的变量x 1,x 2,…,x n 的取值,因此,获取x i 以及获取多个数据在语法上可以分别表示为〈xsl: variable name =“Function (x i )” select =“…”/〉,〈xsl: variable name =“…” select =“Function (query )”/〉,这里,query 以及Function (query )依赖于具体的实现机制,一般来讲,大多采取XPath 和XQuery 语言.(2) 测试谓词真值依据工作流相关数据以及谓词表达式,谓词条件表达成〈xsl: for-each select =“Function (P (x 1,x 2,…,x n ))”〉…〈/xsl: for-each 〉,其中,谓词P 的表达依赖于具体的实现.如果谓词P 中的参数x 1,x 2,…,x n 的取值有多种组合使得P =true,则可以李海波等:基于工作流引擎的构件组装体系结构1405借助于if子元素,表达式如下:〈xsl: if test=“Function(P(x1,x2,…,x n))”〉…〈/xsl: if〉,把那些所有使P=true的参数取值都包含在子元素〈xsl: if〉中,而且,为了使每个判断分支能够执行一定的行为,我们允许每个子元素〈xsl: if〉分支中包含一个模板规则.(3) 工作流活动和Web文档的绑定工作流过程描述中的活动最终应被转换成Web文档,提交给用户执行.界面开发者可以在工作流活动和交互式Web文档中的form或者link建立起映射关系,语法上表示为〈xsl: submit action=“Function(x1,x2,…,x n)” actionElement=“actionID”〉…〈/xsl: submit〉,元素submit将活动Function和HTML中的form元素绑定起来.其中:form元素由actionID标识;变量x1,x2,…,x n 的取值来自于HTML中的form或者XSLT中的变量;XSLT中的变量定义可以参见(1)中的情况.3.2 数据流根据业务对象的定义以及对交互式Web文档的分析可知,业务对象间的交互产生了数据流.因此,业务对象之间在数据上存在着依赖关系,下面给出定义:定义8(数据依赖关系). 设ba j.bo和ba i.bo分别是活动ba j和ba i所操作的业务对象,若ba j.bo的属性集合d j(ba j.bo)的产生需要读取ba i.bo的属性集合d i(ba j.bo),则称业务对象属性d j和d i之间存在着数据依赖关系,记作d i(ba j.bo)→d j(ba j.bo);如果不需要区分属性集合,则简称ba i.bo和ba j.bo之间存在着数据依赖关系,记作ba i.bo →ba j.bo.数据依赖关系是个一般性的概念,只要业务对象之间存在读写操作,都称作具有数据依赖关系.图1中的虚线表示数据依赖关系,其中两个业务对象维修申请单a和派工单b分别由两个业务活动维修申请和派工进行操作,d1是数据集合,包括故障记录号No和故障发生时间Time.此时,A.a和 B.b之间就存在数据依赖关系:No(A.a)→No(B.b)和Time(A.a)→Time(B.b).在工作流引擎的调度下,同一类型的多个活动可能会同时运行.因此,在说明如何调度数据流之前,首先给出活动实例和过程实例的定义:定义9(业务活动实例). 业务活动实例表示为三元组bai=(id,u,ba),是特定用户u对业务活动ba的一次执行,id是活动实例ID.定义10(业务过程实例). 业务过程实例表示为三元组bpi=(id,U,bp),id表示过程实例ID,是特定用户集合U 对业务过程逻辑bp的一次执行.对∀bai∈bpi,其id都等于过程实例的id.在同一个过程实例中,活动实例a i和a j具有相同的过程实例ID,数据流的调度控制主要是指控制同过程实例下的数据交互.同一个Web文档内部业务对象间的交互可以直接进行变量引用,不同Web文档间业务对象的交互不仅需要传递数据,并且要求能够从共享数据中准确定位业务对象.所以,工作流引擎除了能够调度活动外,还应该发挥对数据流的控制能力.Web文档间的数据交互模式实际上是一种多任务表之间的交互模式.3.3 多任务表模式按照WfMC的定义,任务表是指分配给某用户并等待用户处理的任务项队列.不同角色的用户登陆后,从任务表中选取任务项,然后再打开与之关联的应用对其进行处理.在这一管理模式下,任务表成了业务对象间交互的场所.工作流任务表管理器可以作为工作流管理系统的一部分提供给用户,也可以是用户自己编写的程序[14].任务项的表示虽然可以采取多种形式,如列表、E-mail(Metro项目)等,但其目的都是为了管理用户要执行的任务.所以,除了给用户分配任务以外,任务列表还起两个作用:角色的权限控制和业务对象管理,而基于Web文档的业务对象管理模式更能体现这两个作用.基于以上理解,Web文档就是任务表管理器,Web文档中待处理的业务对象就是任务项.因此,这是一种多任务列表模式,集成到一起就是一个过程构件,表示一个业务过程.多任1406 Journal of Software软件学报 V ol.17, No.6, June 2006务列表模式一方面简化了用户操作,使用户对业务对象的操作更加直接;另一方面也便于数据流的控制.图2(a)中,业务对象BOA1和BOB1之间的数据交互需要两个Web文档都处于打开状态,而我们提出的多任务表模式(图2(b))更加适合数据流的控制.与传统的人工检索获取数据的方式相比,基于工作流引擎的数据流控制能够自动完成数据的正确交互.这里所说的“正确”是指两个交互的业务对象应该属于同一个过程实例.(a) Work list pattern defined by WfMC (b) Multi-Work-List pattern(a) 工作流管理联盟定义的任务列表模式(b)多任务列表模式Fig.2 Difference of work list pattern图2 任务列表模式的差别3.4 权限控制企业人员的权限最终表现为对业务对象的操作控制上.一个业务对象经常由多个角色共同操作完成,每个角色负责一类属性,比如,一个设备对象的3类属性——基本属性、使用属性和固定资产属性,就分别由设备管理员、车间人员和固定资产管理员分别处理.角色和业务对象的映射关系可以表示为M rd={m rd|m rd∈(2R→D)∪(R→2D)},其中R和D分别表示角色集合和业务对象属性集合.除了这种现实的业务模式,不同角色在同一个Web文档中所能执行的操作也不同,比如只读、可写权限.考虑组装后的Web文档的空间视图,我们提出一种基于Web文档全局视图、按照角色的权限配置进行过滤的权限控制模式.这种模式大大增加了构件本身的可重用性.比如,采用传统的方法处理设备对象,3类属性需要开发3个Web文档(用户视图),而我们提出的权限控制模式只需要开发一个全局视图,通过权限配置就可以直接对Web文档的布局产生影响,而且当M rd需要局部调整时,只需修改配置文件即可.采用XSLT对Web文档进行权限过滤的描述方法举例如下:〈xsl: template match=“INPUT//input”〉〈xsl: for-each select=“child::display”〉〈td〉〈input type=“text” name=“…” value=“…”/〉〈xsl: value-of select=“display”/〉〈/td〉〈/xsl: for-each〉上述描述对Web界面中的每一个input进行处理,依据变量display确定该input属性是只读还是可写.3.5 工作流引擎多任务表管理模式、权限控制模式决定了工作流引擎对构件的调度控制机制,工作流引擎的内部结构如图3所示.调度的结果最终体现在Web文档上,包括业务对象属性和功能操作.矩形框表示计算,矩形框间的箭头表示过程实例的处理过程.图中涉及了活动状态,考虑到现实情况,由于业务活动未必都能顺利地执行完毕,因此首先引入并解释活动状态.从定义5可知,如果活动执行前需要满足谓词P,则P称作活动执行的前提条件,记为P pre,例如,判断某些数据是否已经准备好.若活动执行完毕后需要满足谓词P,则称P为活动执行的后置条件,记为P post,例如,某些数据是否全部生成.活动在前提条件不满足或者未被执行完时需要等待,直到条件满足为止.活动状态变迁过程如图4所示.当活动的状态从READY变化至COMPLETED,表示活动已经执行完毕;或者变化至ABORT,表示活动被取消.活动状态的变迁主要依据P pre和P post这两类判定条件,如果用户考虑活动执行的时间因素,可以扩充增加OVERTIME和ABORT两个状态,活动执行时通过和用户交互确定活动状态的变迁.李海波等:基于工作流引擎的构件组装体系结构1407活动状态变迁至COMPLETED后,依据过程逻辑定义开始计算后续活动,根据人员角色定义确定出后续活动的执行角色,写入工作流实例数据库,同时,根据工作流数据模型(型)构造工作流相关数据(值),如图3所示.计算出的后续活动用来准备产生Web文档的XSL,工作流实例数据对产生Web文档的XSL起3个作用:1) 根据工作流实例数据,控制业务对象的创建.比如,某Web文档下的一个业务对象,当其状态是CONSTRUCT时,该业务对象的创建操作由disabled变为enabled,表明该活动的执行已经满足了前提条件;2) 获取工作流实例信息,用于控制数据流,如工作流实例ID.比如某Web文档下,一个业务对象属性的产生需要读取其他Web文档下的业务对象属性,此时就需要工作流实例ID作为控制条件;3) 部署视图.根据登陆用户的角色所对应的权限配置,对界面构件全局视图进行权限过滤,以及控制对业务对象属性的操作方式.Fig.3 Structure of workflow engine图3 工作流引擎结构Fig.4 State transformation schema of workflow activity图4 工作流活动状态变迁图4 系统结构基于对构件环境的分析,我们开发了一个开放式、支持企业复杂应用系统建模的开发平台ERP-Modeling. ERP-Modeling完成了从业务建模到软件系统建模,最终到软构件生成以及应用系统部署的全过程,实现了从高层抽象描述到具体实现的映射.通过对实际应用的大量研究,我们总结出了若干种处理业务对象的典型界面模式.这些界面模式能够覆盖企业应用的大部分需求,并且可以由程序自动生成,实现了代码的批量生产.无论按照典型界面模式生成的构件还是由开发人员编写的构件,最终在工作流引擎的调度下组装(集成)在一起,实现业务过程,系统结构如图5所示.很明显,组装过程构件时,工作流引擎起到调度、协调的作用,主要体现在3个方面:(1) 根据用户登陆角色对全局视图进行权限过滤,形成用户视图提供给用户.一个业务对象往往由多个角色共同完成,除了第3节中设备对象的例子,还有维修计划对象、派工单对象等都属于这种情形.我们的方法不是按照角色生成构件,而是先生成构件的全局视图,再根据用户权限配置形成用户视图.因此,这种权限控制模式提高了构件的可复用性,如图5中左侧部分所示.这种设计为修改业务对象属性的访问权限带来了巨大的方便,用户只需修改系统配置,就可以快速完成用户权限的设置,并在下一次打开Web文档或者刷新后生效.。
有关电脑的短语英语作文
有关电脑的短语英语作文Title: Exploring the Wonders of Computing: A Journey Through Computer Phrases。
Computers have become an integral part of our lives, revolutionizing the way we work, communicate, and entertain ourselves. In this essay, we will embark on a journey through the realm of computing by exploring various phrases that have become synonymous with this ever-evolving field.1. Bits and Bytes: At the core of computing lies the fundamental unit of digital information the bit. A bit, represented as either a 0 or a 1, forms the building blocks of all digital data. When eight bits are grouped together, they form a byte. These simple yet powerful units underpin everything we do in the digital world, from storing files to browsing the internet.2. Binary Code: The language of computers is binary, relying on combinations of 0s and 1s to represent data andinstructions. This binary code is the foundation of all software and hardware operations, enabling computers to process vast amounts of information with lightning speed and precision.3. Hardware and Software: Computers are composed of two essential components: hardware and software. Hardwarerefers to the physical components of a computer system, such as the central processing unit (CPU), memory modules, and storage devices. On the other hand, software encompasses the programs and applications that enable users to perform specific tasks, ranging from word processing to graphic design.4. Graphical User Interface (GUI): The graphical user interface revolutionized the way we interact with computers by providing intuitive visual representations of digital tasks. GUIs utilize graphical icons, windows, and menus to facilitate user-friendly navigation and operation, making computing accessible to people of all ages and backgrounds.5. Ctrl + Alt + Delete: This iconic key combination,often referred to as the "three-finger salute," is a lifesaver when encountering system freezes or unresponsive programs. By pressing Ctrl + Alt + Delete simultaneously, users can access the Task Manager, allowing them to terminate problematic processes and regain control of their computer system.6. Cloud Computing: In recent years, cloud computinghas emerged as a game-changer in the world of technology.By leveraging remote servers and networks, cloud computing enables users to store, manage, and access data and applications over the internet, eliminating the need for local storage and infrastructure.7. Artificial Intelligence (AI): As technology advances, so too does the field of artificial intelligence. AI encompasses a range of techniques and algorithms thatenable computers to mimic human intelligence, learn from data, and make autonomous decisions. From virtualassistants to autonomous vehicles, AI is reshaping the way we interact with technology.8. Cybersecurity: With the proliferation of digital threats and cyberattacks, cybersecurity has become paramount in safeguarding our digital assets and privacy. From antivirus software to encryption protocols, cybersecurity measures are essential for protecting sensitive information and maintaining the integrity of computer systems.9. Internet of Things (IoT): The Internet of Things refers to the network of interconnected devices and objects that are embedded with sensors, software, and connectivity, enabling them to collect and exchange data. From smart thermostats to wearable devices, the IoT is transforming our homes, cities, and industries, ushering in a new era of connectivity and convenience.10. Virtual Reality (VR) and Augmented Reality (AR): VR and AR technologies immerse users in virtual environments or enhance their perception of the real world by overlaying digital information. Whether it's exploring distant galaxies or visualizing architectural designs, VR and AR are pushing the boundaries of human-computer interactionand unlocking new possibilities in entertainment, education, and beyond.In conclusion, the world of computing is vast and dynamic, encompassing a myriad of concepts, technologies, and innovations. From the humble beginnings of bits and bytes to the cutting-edge realms of artificial intelligence and virtual reality, computers continue to shape our livesin profound ways. As we navigate this digital landscape,let us embrace the endless possibilities that computing offers and strive to harness its power for the bettermentof society.。
机器人机构设计中英文对照外文翻译文献
(
FEM Optimization for Robot Structure
Wang Shijun, Zhao Jinjuan*
Department of Mechanical Engineering, Xi'anUniversity of Technology
Shaanxi Province, People's Republic of Chinarobot is a kind of machine, which is controlledby computers. Because efficiency and maneuverabilityare higher than traditional machines, industrial robot isused extensively in industry. For thesakeof efficiencyand maneuverability, reducing mass and increasingstiffness is more important than traditional machines,instructure design of industrial robot.
Fig. 1 shows the main framework of a parallel robot withthree bars. When the length of three bars are changed,conjunct end of three bars can follow a given track,where robot handisinstalled. Coreof top beamistriangle, owing to three bars used inthedesign,whichisshowed in Fig.2. Use of three bars makes top beamnonsymmetrical along the plane that is defined by twocolumns. According to a qualitative analysis from Fig.1,Stiffness values along z-axis are different at three jointlocations on the top beam and stiffness at the locationbetween bar 1 and top beam is lowest, which isconfirmed by computing results of finite element, too.According to design goal, stiffness difference at threejoint locations must he within a given tolerance.Inconsistent of stiffness will have influence on themotion accuracy of the manipulator under high load,soit is necessary to find the accurate location of top beamalong x-axis.
德国最大科研机构亥姆霍兹联合会介绍
GERMAN RESEARCH ORGANISATIONS 德国大科研机构之间的比较
Budget/ billion Staff Centres/ Institutes 18
Helmholtz Association
€ 3.4 亥姆霍兹:着眼应用的前瞻式基础研究
33.634
Max Planck Society
Earth & Environment
Health
Aeronautics, Space and Transport
Key Technologies
Structure of Matter
Assembly of Members
(Two per Helmholtz Centre)
PAGE 13
16,800
87
2012基本科技事业拨款与横向经费
SEITE 14
BROAD VARIETY OF STRATEGIC PARTNERSHIPS 形式多样的战略伙伴合作模式
230 joint appointments 联合聘任教授 Promoting joint initiatives through: 合作模式
WE PROMOTE TALENT 多种方式培养青年才俊
Structured training of 5,320 PhD students 25 Helmholtz Graduate Schools and Helmholtz Research Schools 151 Helmholtz Young Investigators Groups with tenure option Helmholtz Management Academy Mentoring 1,627 vocational trainees 25 Helmholtz School Labs Little Scientists’ House
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
WHAT ARE WE LEARNING FROM DESIGNERS AND ITS ROLE IN FUTURECAAD TOOLS
JOHN S GEROKey Centre of Design ComputingUniversity of Sydney
Recent research into the activity and behaviour of human designers as they designhas provide an impetus to carry out research which underpins the development ofnew CAAD support tools. However, there are computational processes of interestin designing which are not modeled on human design processes. This paperoutlines some of the design processes which are being researched based on ourunderstanding of human designers and provides examples from some earlyimplementations.
1. IntroductionGiven the large body of design research it is surprising how little we know about designing:the activity carried out by designers. There has been an upsurge in interest in studyinghuman designers formally. Much of this interest has been driven by the efforts of theartificial intelligence in design research community, which has developed a range ofcomputer-implementable designing processes (Gero and Sudweeks, 1994; 1996). However,more recently, studying human designers has been founded on the development and laterformalisation of experimental methods based on protocol analysis (Ericsson and Simon,1993; van Someren et al., 1994; Cross et al., 1996).Protocol analysis provides a rich source of information on designing as a time-basedactivity. This then allows design researchers to develop richer models of designing based onthe behaviour of human designers. These models in turn provide the basis for a betterunderstanding of designing. Such an understanding then feeds into the development ofcomputer-based support tools for computer-aided architectural design.Section 2 briefly introduces some results from studying human designers. Section 3proceeds to describe a computer implementation of a model of designing based ondeveloping cross-domain analogies drawn from the putative behaviour of human designers.Section 4 introduces the notion ambiguity and emergence in images and describes acomputer implementation of a model of designing based on utilising such notions.2. Results from Protocol and Related StudiesProtocol studies are a means of obtaining data from verbal utterances. Designers are asked to“think aloud” while they are designing. While they are designing they are video and audiotaped. The designer’s verbal utterances are transcribed. The transcription is then used, alongwith design theory, to develop a coding scheme. The transcription in then coded and finallyanalysed. The step are listed below:
• taping• transcription• code development• coding• analysis
Protocol studies are providing detailed evidence of how designers spend their time as theyare designing. At a gross level a designer’s time can be spent either on postulatingsolutions, called structure, or in reasoning about the function and behaviour of possible orpostulated designs. Figure 1 shows a typical distribution of the time spent between thesetwo large classes of activities by experienced designers. It is interesting to note that it isalmost twenty minutes into the session, for this design, before any structure is proposed.Such behaviour is in contrast to that of inexperienced designers who appear to need to“put pencil to paper” very early in order to have something to work with. This isexemplified in Figure 2.
Figure 1. Typical plot of distribution of time spent on function and behaviour (light), asagainst structure (dark), for experienced designer (Gero and McNeill, 1997).Averaged Over 10 Minutes% Function & Behaviour0%25%50%75%
100%
0:00:000:10:000:20:000:30:000:40:000:50:001:00:001:10:00Figure 2. Typical plot of distribution of time spent on function and behaviour (light), asagainst structure (dark), for inexperienced designers (Gero and McNeill, 1997).
Such studies of designers support previous cognitive studies of human problem solvingin areas such as analogy, fixation, emergence and visual ambiguity. They provide detailedinformation on how designers use such concepts in the development of their designproposals.
3. Using Cross-Domain AnalogiesAnalogy has long been recognised as an approach in the elicitation of design ideas. Inarchitecture, the most obvious analogies are visual analogies. Here, the surface similaritiesof the structure are used and transferred to a new design, as shown in Figure 3. However,deep rather than surface similarities require a different approach to their recognition.Similarities associated with function and behaviour provide the locus for deep similarities.While function specifies what a design does, behaviour specifies how it achieves itfunctions. We may extend the definition of analogous designs to:
