Enumerating permutation polynomials over finite fields by degree II
人工智能领域中英文专有名词汇总
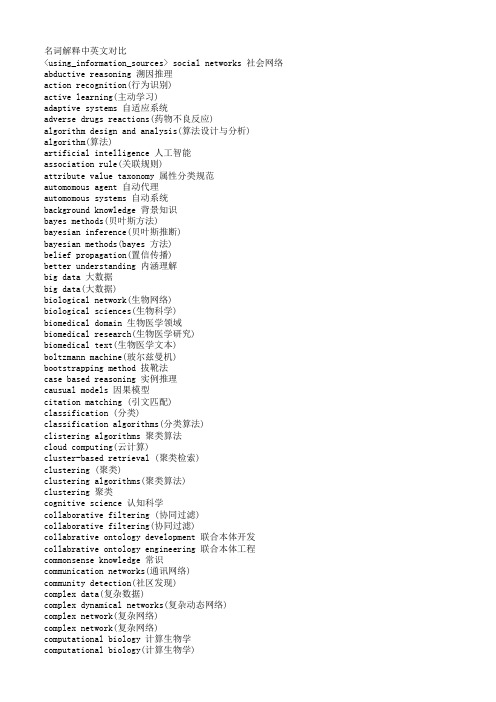
名词解释中英文对比<using_information_sources> social networks 社会网络abductive reasoning 溯因推理action recognition(行为识别)active learning(主动学习)adaptive systems 自适应系统adverse drugs reactions(药物不良反应)algorithm design and analysis(算法设计与分析) algorithm(算法)artificial intelligence 人工智能association rule(关联规则)attribute value taxonomy 属性分类规范automomous agent 自动代理automomous systems 自动系统background knowledge 背景知识bayes methods(贝叶斯方法)bayesian inference(贝叶斯推断)bayesian methods(bayes 方法)belief propagation(置信传播)better understanding 内涵理解big data 大数据big data(大数据)biological network(生物网络)biological sciences(生物科学)biomedical domain 生物医学领域biomedical research(生物医学研究)biomedical text(生物医学文本)boltzmann machine(玻尔兹曼机)bootstrapping method 拔靴法case based reasoning 实例推理causual models 因果模型citation matching (引文匹配)classification (分类)classification algorithms(分类算法)clistering algorithms 聚类算法cloud computing(云计算)cluster-based retrieval (聚类检索)clustering (聚类)clustering algorithms(聚类算法)clustering 聚类cognitive science 认知科学collaborative filtering (协同过滤)collaborative filtering(协同过滤)collabrative ontology development 联合本体开发collabrative ontology engineering 联合本体工程commonsense knowledge 常识communication networks(通讯网络)community detection(社区发现)complex data(复杂数据)complex dynamical networks(复杂动态网络)complex network(复杂网络)complex network(复杂网络)computational biology 计算生物学computational biology(计算生物学)computational complexity(计算复杂性) computational intelligence 智能计算computational modeling(计算模型)computer animation(计算机动画)computer networks(计算机网络)computer science 计算机科学concept clustering 概念聚类concept formation 概念形成concept learning 概念学习concept map 概念图concept model 概念模型concept modelling 概念模型conceptual model 概念模型conditional random field(条件随机场模型) conjunctive quries 合取查询constrained least squares (约束最小二乘) convex programming(凸规划)convolutional neural networks(卷积神经网络) customer relationship management(客户关系管理) data analysis(数据分析)data analysis(数据分析)data center(数据中心)data clustering (数据聚类)data compression(数据压缩)data envelopment analysis (数据包络分析)data fusion 数据融合data generation(数据生成)data handling(数据处理)data hierarchy (数据层次)data integration(数据整合)data integrity 数据完整性data intensive computing(数据密集型计算)data management 数据管理data management(数据管理)data management(数据管理)data miningdata mining 数据挖掘data model 数据模型data models(数据模型)data partitioning 数据划分data point(数据点)data privacy(数据隐私)data security(数据安全)data stream(数据流)data streams(数据流)data structure( 数据结构)data structure(数据结构)data visualisation(数据可视化)data visualization 数据可视化data visualization(数据可视化)data warehouse(数据仓库)data warehouses(数据仓库)data warehousing(数据仓库)database management systems(数据库管理系统)database management(数据库管理)date interlinking 日期互联date linking 日期链接Decision analysis(决策分析)decision maker 决策者decision making (决策)decision models 决策模型decision models 决策模型decision rule 决策规则decision support system 决策支持系统decision support systems (决策支持系统) decision tree(决策树)decission tree 决策树deep belief network(深度信念网络)deep learning(深度学习)defult reasoning 默认推理density estimation(密度估计)design methodology 设计方法论dimension reduction(降维) dimensionality reduction(降维)directed graph(有向图)disaster management 灾害管理disastrous event(灾难性事件)discovery(知识发现)dissimilarity (相异性)distributed databases 分布式数据库distributed databases(分布式数据库) distributed query 分布式查询document clustering (文档聚类)domain experts 领域专家domain knowledge 领域知识domain specific language 领域专用语言dynamic databases(动态数据库)dynamic logic 动态逻辑dynamic network(动态网络)dynamic system(动态系统)earth mover's distance(EMD 距离) education 教育efficient algorithm(有效算法)electric commerce 电子商务electronic health records(电子健康档案) entity disambiguation 实体消歧entity recognition 实体识别entity recognition(实体识别)entity resolution 实体解析event detection 事件检测event detection(事件检测)event extraction 事件抽取event identificaton 事件识别exhaustive indexing 完整索引expert system 专家系统expert systems(专家系统)explanation based learning 解释学习factor graph(因子图)feature extraction 特征提取feature extraction(特征提取)feature extraction(特征提取)feature selection (特征选择)feature selection 特征选择feature selection(特征选择)feature space 特征空间first order logic 一阶逻辑formal logic 形式逻辑formal meaning prepresentation 形式意义表示formal semantics 形式语义formal specification 形式描述frame based system 框为本的系统frequent itemsets(频繁项目集)frequent pattern(频繁模式)fuzzy clustering (模糊聚类)fuzzy clustering (模糊聚类)fuzzy clustering (模糊聚类)fuzzy data mining(模糊数据挖掘)fuzzy logic 模糊逻辑fuzzy set theory(模糊集合论)fuzzy set(模糊集)fuzzy sets 模糊集合fuzzy systems 模糊系统gaussian processes(高斯过程)gene expression data 基因表达数据gene expression(基因表达)generative model(生成模型)generative model(生成模型)genetic algorithm 遗传算法genome wide association study(全基因组关联分析) graph classification(图分类)graph classification(图分类)graph clustering(图聚类)graph data(图数据)graph data(图形数据)graph database 图数据库graph database(图数据库)graph mining(图挖掘)graph mining(图挖掘)graph partitioning 图划分graph query 图查询graph structure(图结构)graph theory(图论)graph theory(图论)graph theory(图论)graph theroy 图论graph visualization(图形可视化)graphical user interface 图形用户界面graphical user interfaces(图形用户界面)health care 卫生保健health care(卫生保健)heterogeneous data source 异构数据源heterogeneous data(异构数据)heterogeneous database 异构数据库heterogeneous information network(异构信息网络) heterogeneous network(异构网络)heterogenous ontology 异构本体heuristic rule 启发式规则hidden markov model(隐马尔可夫模型)hidden markov model(隐马尔可夫模型)hidden markov models(隐马尔可夫模型) hierarchical clustering (层次聚类) homogeneous network(同构网络)human centered computing 人机交互技术human computer interaction 人机交互human interaction 人机交互human robot interaction 人机交互image classification(图像分类)image clustering (图像聚类)image mining( 图像挖掘)image reconstruction(图像重建)image retrieval (图像检索)image segmentation(图像分割)inconsistent ontology 本体不一致incremental learning(增量学习)inductive learning (归纳学习)inference mechanisms 推理机制inference mechanisms(推理机制)inference rule 推理规则information cascades(信息追随)information diffusion(信息扩散)information extraction 信息提取information filtering(信息过滤)information filtering(信息过滤)information integration(信息集成)information network analysis(信息网络分析) information network mining(信息网络挖掘) information network(信息网络)information processing 信息处理information processing 信息处理information resource management (信息资源管理) information retrieval models(信息检索模型) information retrieval 信息检索information retrieval(信息检索)information retrieval(信息检索)information science 情报科学information sources 信息源information system( 信息系统)information system(信息系统)information technology(信息技术)information visualization(信息可视化)instance matching 实例匹配intelligent assistant 智能辅助intelligent systems 智能系统interaction network(交互网络)interactive visualization(交互式可视化)kernel function(核函数)kernel operator (核算子)keyword search(关键字检索)knowledege reuse 知识再利用knowledgeknowledgeknowledge acquisitionknowledge base 知识库knowledge based system 知识系统knowledge building 知识建构knowledge capture 知识获取knowledge construction 知识建构knowledge discovery(知识发现)knowledge extraction 知识提取knowledge fusion 知识融合knowledge integrationknowledge management systems 知识管理系统knowledge management 知识管理knowledge management(知识管理)knowledge model 知识模型knowledge reasoningknowledge representationknowledge representation(知识表达) knowledge sharing 知识共享knowledge storageknowledge technology 知识技术knowledge verification 知识验证language model(语言模型)language modeling approach(语言模型方法) large graph(大图)large graph(大图)learning(无监督学习)life science 生命科学linear programming(线性规划)link analysis (链接分析)link prediction(链接预测)link prediction(链接预测)link prediction(链接预测)linked data(关联数据)location based service(基于位置的服务) loclation based services(基于位置的服务) logic programming 逻辑编程logical implication 逻辑蕴涵logistic regression(logistic 回归)machine learning 机器学习machine translation(机器翻译)management system(管理系统)management( 知识管理)manifold learning(流形学习)markov chains 马尔可夫链markov processes(马尔可夫过程)matching function 匹配函数matrix decomposition(矩阵分解)matrix decomposition(矩阵分解)maximum likelihood estimation(最大似然估计)medical research(医学研究)mixture of gaussians(混合高斯模型)mobile computing(移动计算)multi agnet systems 多智能体系统multiagent systems 多智能体系统multimedia 多媒体natural language processing 自然语言处理natural language processing(自然语言处理) nearest neighbor (近邻)network analysis( 网络分析)network analysis(网络分析)network analysis(网络分析)network formation(组网)network structure(网络结构)network theory(网络理论)network topology(网络拓扑)network visualization(网络可视化)neural network(神经网络)neural networks (神经网络)neural networks(神经网络)nonlinear dynamics(非线性动力学)nonmonotonic reasoning 非单调推理nonnegative matrix factorization (非负矩阵分解) nonnegative matrix factorization(非负矩阵分解) object detection(目标检测)object oriented 面向对象object recognition(目标识别)object recognition(目标识别)online community(网络社区)online social network(在线社交网络)online social networks(在线社交网络)ontology alignment 本体映射ontology development 本体开发ontology engineering 本体工程ontology evolution 本体演化ontology extraction 本体抽取ontology interoperablity 互用性本体ontology language 本体语言ontology mapping 本体映射ontology matching 本体匹配ontology versioning 本体版本ontology 本体论open government data 政府公开数据opinion analysis(舆情分析)opinion mining(意见挖掘)opinion mining(意见挖掘)outlier detection(孤立点检测)parallel processing(并行处理)patient care(病人医疗护理)pattern classification(模式分类)pattern matching(模式匹配)pattern mining(模式挖掘)pattern recognition 模式识别pattern recognition(模式识别)pattern recognition(模式识别)personal data(个人数据)prediction algorithms(预测算法)predictive model 预测模型predictive models(预测模型)privacy preservation(隐私保护)probabilistic logic(概率逻辑)probabilistic logic(概率逻辑)probabilistic model(概率模型)probabilistic model(概率模型)probability distribution(概率分布)probability distribution(概率分布)project management(项目管理)pruning technique(修剪技术)quality management 质量管理query expansion(查询扩展)query language 查询语言query language(查询语言)query processing(查询处理)query rewrite 查询重写question answering system 问答系统random forest(随机森林)random graph(随机图)random processes(随机过程)random walk(随机游走)range query(范围查询)RDF database 资源描述框架数据库RDF query 资源描述框架查询RDF repository 资源描述框架存储库RDF storge 资源描述框架存储real time(实时)recommender system(推荐系统)recommender system(推荐系统)recommender systems 推荐系统recommender systems(推荐系统)record linkage 记录链接recurrent neural network(递归神经网络) regression(回归)reinforcement learning 强化学习reinforcement learning(强化学习)relation extraction 关系抽取relational database 关系数据库relational learning 关系学习relevance feedback (相关反馈)resource description framework 资源描述框架restricted boltzmann machines(受限玻尔兹曼机) retrieval models(检索模型)rough set theroy 粗糙集理论rough set 粗糙集rule based system 基于规则系统rule based 基于规则rule induction (规则归纳)rule learning (规则学习)rule learning 规则学习schema mapping 模式映射schema matching 模式匹配scientific domain 科学域search problems(搜索问题)semantic (web) technology 语义技术semantic analysis 语义分析semantic annotation 语义标注semantic computing 语义计算semantic integration 语义集成semantic interpretation 语义解释semantic model 语义模型semantic network 语义网络semantic relatedness 语义相关性semantic relation learning 语义关系学习semantic search 语义检索semantic similarity 语义相似度semantic similarity(语义相似度)semantic web rule language 语义网规则语言semantic web 语义网semantic web(语义网)semantic workflow 语义工作流semi supervised learning(半监督学习)sensor data(传感器数据)sensor networks(传感器网络)sentiment analysis(情感分析)sentiment analysis(情感分析)sequential pattern(序列模式)service oriented architecture 面向服务的体系结构shortest path(最短路径)similar kernel function(相似核函数)similarity measure(相似性度量)similarity relationship (相似关系)similarity search(相似搜索)similarity(相似性)situation aware 情境感知social behavior(社交行为)social influence(社会影响)social interaction(社交互动)social interaction(社交互动)social learning(社会学习)social life networks(社交生活网络)social machine 社交机器social media(社交媒体)social media(社交媒体)social media(社交媒体)social network analysis 社会网络分析social network analysis(社交网络分析)social network(社交网络)social network(社交网络)social science(社会科学)social tagging system(社交标签系统)social tagging(社交标签)social web(社交网页)sparse coding(稀疏编码)sparse matrices(稀疏矩阵)sparse representation(稀疏表示)spatial database(空间数据库)spatial reasoning 空间推理statistical analysis(统计分析)statistical model 统计模型string matching(串匹配)structural risk minimization (结构风险最小化) structured data 结构化数据subgraph matching 子图匹配subspace clustering(子空间聚类)supervised learning( 有support vector machine 支持向量机support vector machines(支持向量机)system dynamics(系统动力学)tag recommendation(标签推荐)taxonmy induction 感应规范temporal logic 时态逻辑temporal reasoning 时序推理text analysis(文本分析)text anaylsis 文本分析text classification (文本分类)text data(文本数据)text mining technique(文本挖掘技术)text mining 文本挖掘text mining(文本挖掘)text summarization(文本摘要)thesaurus alignment 同义对齐time frequency analysis(时频分析)time series analysis( 时time series data(时间序列数据)time series data(时间序列数据)time series(时间序列)topic model(主题模型)topic modeling(主题模型)transfer learning 迁移学习triple store 三元组存储uncertainty reasoning 不精确推理undirected graph(无向图)unified modeling language 统一建模语言unsupervisedupper bound(上界)user behavior(用户行为)user generated content(用户生成内容)utility mining(效用挖掘)visual analytics(可视化分析)visual content(视觉内容)visual representation(视觉表征)visualisation(可视化)visualization technique(可视化技术) visualization tool(可视化工具)web 2.0(网络2.0)web forum(web 论坛)web mining(网络挖掘)web of data 数据网web ontology lanuage 网络本体语言web pages(web 页面)web resource 网络资源web science 万维科学web search (网络检索)web usage mining(web 使用挖掘)wireless networks 无线网络world knowledge 世界知识world wide web 万维网world wide web(万维网)xml database 可扩展标志语言数据库附录 2 Data Mining 知识图谱(共包含二级节点15 个,三级节点93 个)间序列分析)监督学习)领域 二级分类 三级分类。
有限域上的置换多项式

dd#0,_是為/2中的元素,。2 +_2 = 0.我们可得(1)有唯一的解/(x)是鱼上的一个置换多项式.
定理2 设5eF2m且Tr(5)=1,其中肌三0(mod4),那么满足(2m/2 —2)力三2^/2 — 1(mod 2m — 1)的正整 数%,/(x)= (x2 +x+5)k +x是 唇上的一个置换多项式.
1 /( ax^+ax+5) Et - (_+d)旳1.
唯一的解.由于Tr(5)=1,对于所有的x e F2m,因此ax^+ax+5^0.方程f(_)= d等价于
进一步等价于
(ax" +a_+5)k - x+d.
ax^+ax+5二(x+d)旳1.
即
_2k+1 +( d+a)_2k + ( d2k +a)x+d2©1 +5- 0. 因为 a e F?k,所以我们有 a2k - a ,即 _2k+1 +( d+a) _2k + ( d+a) "x+d2®1 +5 = 0.公式等价于
—x2+ax +5+1 -
ax =
_ +5+d.
(5)
x2+d
比较(3)(5)我们有
_2(d(x2+d) +1 ] (x2+ax +5+1)+(x2+d) (5+d) 2
a [ z-0 =
],
因此
简化可得
[d(x2+d) +1] (x2+d) = [ (x2+x +5+1) +(x2+d) (5+d) ] 2.
基于RPMDE-MKSVM的锂离子电池剩余使用寿命预测

2021年4月第28卷第4期控制工程Control Engineering of ChinaApr.2021Vol.28,No.4文章编号:1671-7848(2021)04-0665-07DOI: 10.14107/ki.kzgc.20190644基于R PM D E-M K S V M的锂离子电池剩余使用寿命预测简献忠l a,韦进l b,王如志2(1.上海理工大学a.光电信息与计算机工程学院;b.机械工程学院,上海200090;2.北京工业大学材料科学与工程学院,北京100020)摘要:为了提高锂离子电池剩余使用寿命预测的精度,提出了一种基于随机参数机制差分进化(random parameter machine differential evolution,R P M D E)算法与多核支持向量机(multi-kernel support vector machine,M K S V M)的锂离子电池剩余使用寿命预测模型。
首先,将差分变异策略和随机搜索算子引入差分进化算法中来增强算法种群多样性,提高全局搜索能力。
然后,通过R P M D E算法优化M K S V M的惩罚因子和核参数来提高预測模型的精度。
最后,利用美国国家航空航天局的锂离子电池測试数据验证R P M D E-M K S V M模型的准确性。
实验结果表明,相比于差分进化算法模型和粒子群优化算法模型,R P M D E-M K S V M模型不仅具有更快的收敛速度,而且具有更优的预測精度。
关键词:锂离子电池;剩余使用寿命预测;R P M D E算法;多核支持向量机中图分类号:T M912 文献标示码:ARemaining Useful Life Prediction of Lithium-ion Battery Based onRPMDE-MKSVMJ I A N X i a n-z h o n g x\ W E I J i n l b,W A N G R u-zhi2(1.a.School of Optical-electrical and Computer Engineering;b.School of Mechanical Engineering,University of Shanghai forScience and Technology,Shanghai200090, China;2.School of Materials Science and Engineering,Beijing University ofTechnology,Beijing 100020, China)Abstract:In order to improve the prediction accuracy of remaining useful life(R U L)of lithium-ion battery,a R U L prediction model of lithium-ion battery based on ran d o m parameter machine differential evolution (R P M D E)algorithm and multi-kernel support vector machine(M K S V M)is proposed in this paper.Firstly,the differential mutation strategy and rand o m search operator are introduced into the differential evolution (D E) algorithm to enhance the diversity of the algorithm population and improve the global search ability.T h e n, R P M D E algorithm is used to optimize the penalty factors and kernel parameters of M K S V M to improve the accuracy of the prediction m o d e l.Finally,the battery test data of National Aeronautics and Space Administration(N A S A)are used to verify the accuracy of R P M D E-M K S V M m o d e l.T h e experimental results s h o w that R P M D E-M K S V M model not only has faster convergence speed,but also has better prediction accuracy compared with D E algorithm model and particle s w a r m optimization algorithm m o d e l.K e y w o r d s:Lithium-ion battery;remaining useful life prediction;R P M D E algorithm;multi-kernel support vector machineOi引言随着新能源发电技术的发展,国内外已有很多 学者和工程技术人员开展了新能源发电管理系统方 面的研究。
图像奇异性表征机理分析比较

第32卷第2期206年6月金陵科技学院学报J O U R N A L O F J IN U N G IN S T IT U T E O F T E C H N O L O G YV o l.32,N o.2J unc,2016图像奇异性表征机理分析比较郑玮(金陵科技学院计算机工程学院,江苏南京211169)摘要:图像奇异性包含的许多重要信息对于图像的进一步分析具有重要作用。
对于图像中的不同奇异性通常需要采用不同的方法表示。
小波变换和曲波变换作为稀疏表示中的重要方法,具有广泛的应用。
分析了小波变换和曲波变换对于图像奇异性表证的不同效果。
实验结果和理论分析均表明小波变换对于图像中的点奇异性具有很好效果,但对于线奇异性表示则不够稀疏,曲波则可以高效地表示图像边缘的曲线奇异性。
关键词:稀疏表示;图像分类;稀疏编码;寺征编码;小波;曲波中图分类号:T P391 文献标志码:A文章编号:1672 755X(2016)02 0034 05Image Singularity Analysis and ComparisonZH EN G Wei(Jinling Institute of Technology,Nanjing 211169, China)Abstra c t: Singularity in images carry massive essential inform ation,which is crucial to furtheranalysis. Wc need to adopt different methods according to the elements in image singularity.Wavelet transform and curvelet transform are two important methods for sparse representationand are widely used in numerous fields. In this paper,wavelet transform and curvelettransform are used to analyze the effects of different singularity in images. The experimentalresults and theoretical analysis both dem onstrate that wavelet is good at noises in images butcannot represent the edges effectively. On the contrary,curvelet is very suitable for the edge.Key word s :sparse representation ;image classification ;sparse coding ;feature coding ;w avelet; curvelet图像奇异性表征机理分析主要是指对图像噪声点、图像边缘信息的分析。
代数中常用英语词汇

(0,2) 插值||(0,2) interpolation0#||zero-sharp; 读作零井或零开。
0+||zero-dagger; 读作零正。
1-因子||1-factor3-流形||3-manifold; 又称“三维流形”。
AIC准则||AIC criterion, Akaike information criterionAp 权||Ap-weightA稳定性||A-stability, absolute stabilityA最优设计||A-optimal designBCH 码||BCH code, Bose-Chaudhuri-Hocquenghem codeBIC准则||BIC criterion, Bayesian modification of the AICBMOA函数||analytic function of bounded mean oscillation; 全称“有界平均振动解析函数”。
BMO鞅||BMO martingaleBSD猜想||Birch and Swinnerton-Dyer conjecture; 全称“伯奇与斯温纳顿-戴尔猜想”。
B样条||B-splineC*代数||C*-algebra; 读作“C星代数”。
C0 类函数||function of class C0; 又称“连续函数类”。
CA T准则||CAT criterion, criterion for autoregressiveCM域||CM fieldCN 群||CN-groupCW 复形的同调||homology of CW complexCW复形||CW complexCW复形的同伦群||homotopy group of CW complexesCW剖分||CW decompositionCn 类函数||function of class Cn; 又称“n次连续可微函数类”。
Cp统计量||Cp-statisticC。
完全置换多项式专栏序言(中英文)

密码学报ISSN2095-7025CN10-1195/TN Journal of Cryptologic Research,2019,6(5):639–642©《密码学报》编辑部版权所有.E-mail:jcr@ Tel/Fax:+86-10-82789618完全置换多项式专栏完全置换多项式专栏序言(中英文)曾祥勇湖北大学数学与统计学学院应用数学湖北省重点实验室,武汉430062通信作者:曾祥勇,E-mail:xzeng@中图分类号:TP309.7文献标识码:A DOI:10.13868/ki.jcr.000329中文引用格式:曾祥勇.完全置换多项式专栏序言(中英文)[J].密码学报,2019,6(5):639–642.英文引用格式:ZENG X Y.Preface of complete permutation polynomials column[J].Journal of Cryptologic Research,2019,6(5):639–642.Preface of Complete Permutation Polynomials ColumnZENG Xiang-YongHubei Key Laboratory of Applied Mathematics,Faculty of Mathematics and Statistics,Hubei University, Wuhan430062,ChinaCorresponding author:ZENG Xiang-Yong,E-mail:xzeng@置换多项式在分组密码算法设计中具有广泛的应用.一般情况下,分组密码算法中明密文之间的关系就是密钥控制下的置换.另外,密码算法的许多重要组成部分也是置换.例如,具有良好密码学性质的置换常被用来设计对称密码算法中唯一的非线性部件S盒.完全置换多项式是一类特殊的置换,其概念是Mann在上个世纪四十年代提出的,早期的研究结果与正交拉丁方联系紧密.完全置换多项式具有优良的密码学性质.例如,偶特征有限域上的完全置换多项式只有一个不动点.此外,非线性完全置换具有良好的位独立性和雪崩特性,使得基于完全置换的密码算法具备良好的扩散和混淆作用.因此,完全置换多项式的研究具有重要的理论和实际意义.完全置换多项式在密码学中的较早应用是由美国Teledyne电子技术公司的Mittenthal提出的.他分别在1995年和1997年发表的论文《Block substitutions using orthomorphic mapping》和专利《Nonlinear dynamic substitution devices and methods for block substitutions employing coset decompositions and direct geometric generation》中讨论了完全置换的构造和基本性质,首次公开了如何使用完全置换多项式来设计密码算法以及非线性动力系统装置.这些成果为完全置换在密码学中的应用奠定了基础,并使人们对完全置换多项式这一数学对象产生浓厚的兴趣.在随后的十年里,国内外学者在这一研究方向上取得了一系列进展.在密码应用方面比较有代表性成果的是Vaudenay在1999年证明了添加完全置换或几乎完全置换的Lai-Massey结构具有更好的伪随机性.另外,国内的标志性成果是2006年公布的基于完全置换的分组密码算法SMS4,该算法被指定用于无线局域网WAPI且被我国商用密码管理局确定为国家密码行业标准,在密码行业中有着极为重要的作用.收稿日期:2019-09-16定稿日期:2019-10-11640Journal of Cryptologic Research密码学报Vol.6,No.5,Oct.20192007年之后的几年里,完全置换多项式的研究进展非常缓慢,主要原因是判断多项式的完全置换性质是一个十分困难的问题,即使最简单的单项式的完全置换性质也不容易被刻画.直到2014年,Tu,Zeng 和Hu提出了用加法特征和极坐标表示的方法来将完全置换单项式的问题转化成有限域上特殊方程解的问题.受到其启发,从2015年开始国际学术界重新兴起了研究有限域上完全置换多项式的热潮.在最近五年,涌现了一大批有代表性的成果,例如基于例外多项式、AGW准则或密码结构的完全置换.完全置换多项式在流密码、Hash函数、编码设计、校验位系统设计等领域也有一定的应用.虽然最近几年完全置换多项式的研究已经取得了一系列进展,但是已有的完全置换多项式类依然十分稀少,完全置换多项式的研究尚处于初级阶段,还存在许多有待进一步研究的重要问题,其中完全置换多项式的构造以及相关密码学性质分析是该方向的重点研究内容.在本期“完全置换多项式”专栏中共收录三篇文章,其中包含一篇综述论文和两篇研究论文,希望对完全置换多项式的理论和应用研究起到促进作用.第一篇是综述论文《完全置换多项式的研究进展》.该论文较全面地总结分析了近二十多年来有限域上完全置换多项式的相关理论研究成果,从完全置换多项式的构造方法和多项式的形式出发给出了已有完全置换的分类,阐述了完全置换多项式的存在性、代数次数、圈结构以及广义完全置换多项式的相关研究进展.此外,还指出了一些值得进一步研究的问题.该论文是一篇较好的介绍完全置换多项式的综述,对想了解完全置换多项式的研究者有很高的参考价值和很好的指导意义.第二篇论文题目是《有限域上几类置换和完全置换》.因为判定一个多项式构成完全置换的条件是相当复杂的,所以研究特殊类型的完全置换多项式具有重大的意义.该论文运用迹函数、线性置换和Dickson置换构造了有限域F q n上六类形如γx+Tr q n q(h(x))的置换多项式,证明了其中三类为完全置换并分析了其余三类不构成完全置换的原因.另外,在已知的置换判定法则基础上他们还研究了形如xh(x s)的二项式的完全置换性质,得到了有限域上几类新的完全置换.第三篇论文题目是《有限域上完全置换多项式的构造》.稀疏型完全置换多项式因其具有简洁的代数表达式以及便于硬件实现的特点而备受关注.该论文构造了特征2有限域F q2上形如xh(x q−1)q+1的两类完全置换多项式,给出了这些多项式是完全置换多项式的充要条件或者充分条件.通过选取适当的函数,得到了几类完全置换三项式和完全置换七项式.两篇研究论文均考虑完全置换多项式的构造问题,研究成果丰富了已有完全置换多项式的构造,具有重要的理论意义.Permutation polynomials are widely used in the design of block cipher algorithms.In general,the relationship between plaintext and ciphertext in block cipher algorithms is a permutation under the control of keys.In addition,many important components of cryptographic algorithms are permuta-tions.For example,permutations with good cryptographic properties are often used to design S-box which is the unique nonlinear component of symmetric cryptographic algorithms.Complete permutation polynomials are a special class of permutation polynomials.The concept of complete permutation polynomials was proposed by Mann in the1940s.Earlier research results are closely related to orthogonal Latin plete permutation polynomials have good crypto-graphic properties.For example,complete permutation polynomials over finite fields of even charac-teristic have a single fixed point.Moreover,nonlinear complete permutations have bit independence and avalanche characteristics,so the cryptographic algorithms based on complete permutations have good diffusion and confusion effects.Therefore,the research of complete permutation polynomials has important theoretical and practical significance.The early application of complete permutation polynomials in cryptography was proposed by Mit-tenthal who comes from Teledyne Electronics Technology Company of the United States.He published the paper“Block substitutions using orthomorphic mapping”in1995and the patent“Nonlinear dy-namic substitution devices and methods for block substitutions employing coset decompositions and direct geometric generation”in1997,respectively.In this paper and this patent,the constructions and曾祥勇:完全置换多项式专栏序言(中英文)641properties of complete permutations were discussed.In addition,he firstly presented how to use com-plete permutation polynomials to design cryptographic algorithms and nonlinear dynamic substitution devices.These achievements laid the foundation for the application of complete permutations in cryp-tography and aroused great interest in the mathematical object complete permutation polynomials. In the following ten years,scholars worldwide have made a series of achievements in this field.The representative achievement in cryptographic application is that Vaudenay proved that the Lai-Massey scheme with complete permutations or almost complete permutations has better pseudo-randomness in1999.In addition,the landmark achievement in China is that the block cipher algorithm SMS4 was designed by use of complete permutations and published in2006.This algorithm has been desig-nated for WAPI in WLAN and has been designated as the national cryptographic industry standard by China’s Commercial Cryptographic Administration.It plays an extremely important role in the cryptographic industry.In the years after2007,the research on complete permutation polynomials has developed very slowly,since the problem of judging a polynomial to be a complete permutation is very difficult, even for the simplest monomials.In2014,Tu,Zeng,and Hu proposed the method of using the additive characters of the underlying finite fields and the technique of polar coordinate representation to transform the problem of complete permutation monomials over finite fields into that of determining the number of the solutions to certain equations over finite fields.Inspired by their works,a new upsurge of studying complete permutation polynomials over finite fields has arisen in the international academic circles in2015.In the past five years,a large number of representative achievements have emerged, such as complete permutations based on exceptional polynomials,the AGW criteria or cryptographic structures.Complete permutation polynomials also have some applications in stream ciphers,Hash functions, coding design,check digit systems,and other fields.In recent years,a series of achievements have been obtained in the study of complete permutation polynomials,but the known classes of complete permutation polynomials are very rare.The research of complete permutation polynomials is still in primary stage,and there exist many important problems which need to be studied in the future.The construction of complete permutation polynomials and the analysis of cryptographic properties for these polynomials are the key research problems in this field.The special column“Complete permutation polynomials”has collected three papers involving one review article and two research articles,hoping to promote the development of this field.The first paper is review article“Overview on complete permutation polynomials”.This paper comprehensively summarizes and analyzes the related theoretical research results of complete permu-tation polynomials over finite fields in the past twenty years,and gives the classification of known complete permutation polynomials from the construction methods and the form of polynomials.The existence,algebraic degree,cycle structure of complete permutation polynomials and generalized com-plete permutation polynomials are also discussed.In addition,some problems worthy to study in the future are pointed out.This paper is a good summary of complete permutation polynomials.It is of a high reference value and a good guiding significance for researchers who intend to learn about complete permutation polynomials.The second paper is“A few classes of permutations and complete permutations over finite fields”. To characterize the conditions of a polynomial to be a complete permutation is very difficult,so it is of great significance to study complete permutation polynomials with special forms.This paper constructs six classes of permutations with the formγx+Tr q n q(h(x))by using some trace functions, linear permutations,and Dickson permutations.Three of them are proved to be complete computations and they give the reasons why the other three types are not complete permutation polynomials.In642Journal of Cryptologic Research 密码学报Vol.6,No.5,Oct.2019addition,based on the known criteria of permutations,they study the permutation properties of binomials with the form xh (x s )and obtain a few new classes of complete permutation binomials over finite fields.The third paper is “Construction of complete permutation polynomials over finite fields”.Sparse complete permutation polynomials have attracted much attention due to their concise algebraic expres-sions and features for easy implementation on hardware.This paper constructs two classes of complete permutation polynomials of the form xh (x q −1)q +1over F q 2with characteristic 2and characterizes the necessary and sufficient conditions or sufficient conditions for these polynomials to be complete per-mutation polynomials.By choosing appropriate functions,several types of complete permutation trinomials and complete permutation with seven terms are obtained.The construction of complete permutation polynomials is considered in both research articles.The research results enrich the existing constructions of complete permutation polynomials and have important theoretical significance.作者信息曾祥勇(1973–),博士,教授,博士生导师.主要研究领域为密码与编码.xzeng@ ZENG Xiang-Yong (1973–),Ph.D.,Pro-fessor,Doctoral Tutor.The main research covers cryptology and coding.xzeng@。
基于拉普拉斯特征映射的鲁棒视频哈希方法

Ro u t i e a hn a e n La lca g n p b s v d oh s i gb s d o p a in Eie ma s
NI usa QI inpn 。 Qr e gl 2 EXi-hn , AO J —ig, a NF n —n i
Abtat b s vdoh sigfr ie o ydtc o ae nL pai ie mas (E ipo oe . I i me o , ky s c:A r ut ie ahn d ocp eet nb sdo alca Egnh h
(.山 东财政 学 院 计 算机 信 息 工程 学 院 , 山 东 济 南 20 1;2 1 504 .山 东大学 信 息科 学与 工程 学院 , 山 东 济 南 200 ;3 5 10 .山 东师 范 大学 传 播 学 院 ,山 东 济 南 20 1) 504
摘 要: 针对 视 频拷 贝检 测 问题 , 出了基 于拉 普拉 斯特征 映射 (al i i n p , E 的视 频哈 希方 法 , 提 L pa a Eg ma sL ) cn e 该方 法利用视 频
明 , 方法具 有较好 的鲁棒性 和 区分性 。 该 关 键词 : 拉普 拉斯特 征 映射; 视频哈 希 ;拷 贝检 测; 鲁棒 性; 区分性
中图法 分类号 :P 9 T31
文献标 识码 : A
文章 编号 :0072 ( 1 1 39. 10.04 2 1 1 790 0 ) - 4
层 析 成像技 术和 服从 均 匀分布 的向量对 视 频进行 镜 头分割 和关键 帧提取 ,以 高阶 累计量 作为视 频在 高维 空间 的特征 ,并利 用L E进 行 降维 , 到视频 在三 维 空间 中的轨迹 , 得 利用 三维 空 间中点 的范数构 造视 频哈希 来 实现 视频拷 贝检 测。 实验 结果表
origin计算赝电容

origin计算赝电容赝电容是指在某些材料中由于界面效应或电荷分布不均匀等原因而产生的等效电容。
在计算赝电容时,可以采用原子尺度的第一性原理计算方法,如密度泛函理论(DFT)等。
首先,进行赝电容的计算需要确定材料的晶体结构。
可以通过实验技术如X射线衍射或电子显微镜等手段得到晶体结构参数,或者使用计算方法如晶体结构预测等来获取晶体结构信息。
接下来,需要进行电子结构计算。
可以使用密度泛函理论(DFT)等第一性原理方法来计算材料的电子结构。
DFT方法可以通过求解Schrödinger方程来得到材料中电子的能级分布和电荷密度分布等信息。
在电子结构计算中,需要选择合适的赝势(pseudopotential)来描述电子与离子核的相互作用。
赝势是一种有效的近似方法,可以用较少的自由度来描述离子核的运动,从而减小计算量。
选择合适的赝势可以保证计算结果的准确性。
计算得到材料的电子结构后,可以通过计算电荷密度分布来获得材料内部的电荷分布情况。
赝电容的计算通常涉及到界面效应,因此需要考虑材料的界面结构和界面电荷分布情况。
赝电容的计算还需要考虑材料的几何结构和电场分布。
可以通过构建模型或使用实验测量得到的几何结构来进行计算。
同时,可以通过引入外界电场来模拟实际应用中的电场分布情况。
最后,可以使用数值方法如有限元法或有限差分法等来计算赝电容。
这些方法可以将材料的几何结构、电子结构和电场分布等信息输入计算模型,并求解相应的方程,从而得到赝电容的数值结果。
需要注意的是,赝电容的计算是一个复杂的过程,结果的准确性受到多个因素的影响,如材料的晶体结构、电子结构计算的方法和参数选择、赝势的选择以及模型的建立等。
因此,在进行赝电容计算时,需要仔细选择计算方法和参数,并进行合理的验证和分析。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Finite Fields and Their Applications12(2006)26–37/locate/ffa Enumerating permutation polynomials overfinitefields by degree IISergei Konyagin a,Francesco Pappalardi b,∗a Department of Mechanics and Mathematics,Moscow State University,Vorobjovy Gory,119992Moscow,Russiab Dipartimento di Matematica,UniversitàDegli Studi Roma Tre,Largo S.L.Murialdo,1,I-00146Roma,ItalyReceived21July2003;revised31August2004Communicated by Gerhard TurnwaldAvailable online5February2005AbstractThis note is a continuation of a paper by the same authors that appeared in2002in the same journal.First we extend the method of the previous paper proving an asymptotic formula for the number of permutations for which the associated permutation polynomial has d coefficients in specifiedfixed positions equal to0.This also applies to the function N q,d that counts the number of permutations for which the associated permutation polynomial has degree<q−d−1. Next we adopt a more precise approach to show that the asymptotic formula N q,d∼q!/q d holds for d q and =0.03983.©2005Elsevier Inc.All rights reserved.Keywords:Permutation polynomials;Finitefields;Exponential sumsCorresponding author.Fax:+390654888080.E-mail addresses:konyagin@ok.ru(S.Konyagin),pappa@mat.uniroma3.it(F.Pappalardi).1071-5797/$-see front matter©2005Elsevier Inc.All rights reserved.doi:10.1016/j.ffa.2004.12.006S.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–3727 1.IntroductionLet F q be afinitefield with q>2elements.For any permutation of the elements of F q the permutation polynomialf (x)=c∈F q (c)1−(x−c)q−1∈F q[x](1)has the property that f (a)= (a)for every a∈F q.From the definition,it follows that for every ,the degree*(f ) q−2.In[2]the authors proved that if S(F q)denotes the group of permutations on F q, then#∈S(F q)|*(f )<q−2−(q−1)!2eq q.A similar result has also been proved by Das[1].Here we consider a more general function.Fix d integers k1,k2,...,k d with the property that0<k1<···<k d<q−1and defineN q(k1,...,k d)=#∈S(F q)|∀i=1,...,d,the k i-th coefficient of f is0,where by k-th coefficient of a polynomial f we mean its coefficient of x k. We will extend the method of[2]proving the following:Theorem1.Nq(k1,...,k d)−q!q d<1+1eq((q−k1−1)q)q/2.The above result also applies toN q,d=#∈S(F q)|*(f )<q−d−1sinceN q,d=N q(q−d−1,...,q−3,q−2). We also haveCorollary1.If d qlog q12log log q−log log log q,then N q,d∼q!/q d(q→∞).28S.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–37In the case when d is larger with respect to q,the above statement for N q,d can be improved.In Section3we will prove:Theorem2.Suppose =(e−2)/3e=0.08808···,and d< q.ThenN q,d−q!q d<2d dq2+q−dqd2dq−d(q−d)/2.Therefore we haveCorollary2.The asymptotic formula N q,d∼q!/q d holds for q→∞,d 0q and 0=0.03983is a suitable constant.2.The method of[2]—Proof of Theorem1The coefficient of x i in f (x)in(1)equals(−1)q−iq−1ic∈F qc q−i−1 (c)for i>0.Observe thatq−1i=(−1)i for i=1,...,q−1(the equality is consideredin F q;see[3,Exercise7.1]).Hence the j th coefficient of f (x)is0if and only ifc∈F qc q−j−1 (c)=0.We will follow the proof in[2]that uses exponential sums defining auxiliary functions for each S⊆F q:n S(k1,...,k d)=#⎧⎨⎩ff:F q−→S andc∈F qc q−k i−1f(c)=0,for i=1,...,d⎫⎬⎭.By inclusion–exclusion,it is easy to check thatN q(k1,...,k d)=S⊆F q(−1)q−|S|n S(k1,...,k d).(2)S.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–3729 Now we need to evaluate n S(k1,...,k d).If e p(u)=e2 iu p and Tr( )∈F p denotes the trace of ∈F q,thenn S(k1,...,k d)=1q d(a1,...,a d)∈F d qf:F q−→Se p⎛⎝c∈F qTrf(c)di=1a i c q−k i−1⎞⎠=1q(a1,...,a d)∈F d qc∈F qt∈Se pTrtdi=1a i c q−k i−1=|S|qq d+R S,(3)where|R S| q d−1q dmax(a1,...,a d)∈F d q\{0}c∈F qt∈Se pTrtdi=1a i c q−k i−1.Furthermore,since the geometric mean is always bounded by the arithmetic mean,c∈F qt∈Se pTrtdi=1a i c q−k i−1⎛⎝1qc∈F qt∈Se pTrtdi=1a i c q−k i−12⎞⎠q/2⎛⎝1qu∈F q(q−k1−1)t∈Se p(Tr(tu))2⎞⎠q/2.By the identityu∈F qt∈Se p(Tr(tu))2=q|S|(4)we getc∈F qt∈Se pTrtdi=1a i c q−k i−1((q−k1−1)|S|)q/2.30S.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–37 Using inclusion–exclusion for counting the mappings F q→F q we see thatS⊆F q(−1)q−|S||S|q=q!.(5)Now let us plug the estimate for|R S|in Eq.(3)and then in Eq.(2).By(5)we obtainNq(k1,...,k d)−q!q d=N q(k1,...,k d)−S⊆F q(−1)q−|S|q d|S|qqd−1q dS⊆F q((q−k1−1)|S|)q/2.Next,using the inequality1+x e x(6) we getNq(k1,...,k d)−q!q d<(q−k1−1)q/2qu=0u q/2qu(q−k1−1)q/2qu=0quq exp−q−uqq/2 =((q−k1−1)q)q/2qu=0qu1eq−u=((q−k1−1)q)q/21+1eq.This completes the proof.Proof of Corollary1.From Theorem1since N q,d=N q(q−d−1,q−d,...,q−2), we haveN q,d−q!q d<2q(dq)q/2.S.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–3731 By the Stirling formulalim q→∞q!qeq√2 q=1,(7)we obtain that the error term is dominated by the main term if(dq)q/22q=o1q dqeq√q(q→∞).The above is satisfied ifd q =o1q(q→∞).(8)Replace d=u·q log log qlog qand obtain that(8)holds foru 12−log log log qlog log qand q large enough.3.Proof of Theorem2The key ingredient is to use the special properties of N q,d to estimate(3)more accurately.Assume that d is a positive integer and d<q.Let F q(d)denote the vector space of polynomials with degree up to d with constant term equal to0.If P(x)∈F q(d),then define(P)=minT⊂F q,|T|=d|P(T)|.In view of identity(5)and from(2)and(3)we can write:N q,d−q!q d=N q,d−S⊆F q(−1)q−|S||S|qq d=1qS⊆F q(−1)q−|S|P∈F q(d)\{0}c∈F qt∈Se p(Tr(tP(c)))32S.Konyagin,F .Pappalardi /Finite Fields and Their Applications 12(2006)26–37=1qdS ⊆F q(−1)q −|S |dP ∈F q (d)\{0} (P )=c ∈F qt ∈Se p (Tr (tP (c))).(9)In order to estimate the above we will need some lemmas.Lemma 1.Given an integer ∈N ,let H be the set of polynomials P ∈F q (d)such that (P )= .Then|H | dq qd.Proof.Let us fix one of the q dsubsets of F q with d elements and denote it with T .It is sufficient to show that the number of polynomials P ∈F q (d)with |P (T )|= is at most d q.There are qchoices for the set U =P (T ).Take an arbitrary a ∈F q \T and observe that the polynomials of degree d correspond to functions T ∪{a }→F q .Therefore,the number of polynomials P of degree d such that P (T )⊂U is equal to q d and the number of polynomials P of degree d such that |P (T )|= is atmost q d q.Finally,observe that |P (T )|does not change if we add a constant to any polynomial P .Thus the number of polynomials P ∈F q (d)such that |P (T )|= is at most d qas required.Lemma 2.Assume that d q/3and S ⊆F q .If P ∈F q (d)is such that (P ) 2,thenc ∈F q t ∈Se p (Tr (tP (c))) q 2 (q +d)/2 d −1q q −d (q −d)/2while if (P )=1,P =0,thenc ∈F q t ∈Se p (Tr (tP (c))) q 2 (q +d)/2 dq q −d (q −d)/2Proof.Assume (P ) and writeP (F q )={u 1,u 2,...}S.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–3733 where the order is chosen in such a way that#P−1(u1) #P−1(u2) ···.Note that since (P) ,#P−1(u1)+···+#P−1(u −1)<d.(10) Therefore for j= −1, ,...we have#P−1(u j)<dprovided that 2.By(10),there is a set T⊂F q such that|T|=d andT⊃{t:P(t)∈{u1,...,u −1}}.Hence,for each c∈T we have that P(c)∈{u ,u +1,...}.Therefore there are at most d/( −1)elements c of F q with P(c )=P(c).If =1then we use the observation that there are at most d elements c with this property.Denoting =max( ,2),we see that there are at most d/( −1)elements c of F q with P(c )=P(c).Now,bounding from the above the geometric mean with the arithmetic mean,we deducec∈F qt∈Se p(Tr(tP(c)))=c∈Tt∈Se p(Tr(tP(c)))×c∈F q\Tt∈Se p(Tr(tP(c)))|S|d⎛⎝1q−dc∈F q\Tt∈Se p(Tr(tP(c)))2⎞⎠(q−d)/2|S|d⎛⎝1q−dd−1u∈F qt∈Se p(Tr(tu))2⎞⎠(q−d)/2=|S|d1q−dd−1q|S|(q−d)/2,where we used once again(4).This concludes the proof of the lemma in the case |S| q/2.34S.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–37If|S|>q/2then,by the identityt∈F qe p(Tr(tP(c)))=0for P(c)=0,we can reduce the product for S to the product for F q\S.Also, the identity combined with the supposition d<q shows that the product is zero for |S|=q.Thus,we can consider q/2<|S|<q.If is the number of the zeros of the polynomial P in F q then we havec∈F qt∈Se p(Tr(tP(c)))=|S|q−|S|c∈F qt∈F q\Se p(Tr(tP(c))).Therefore,c∈F qt∈Se p(Tr(tP(c)))|S|q−|S|d(q−|S|)d1q−dd−1q(q−|S|)(q−d)/2=(|S|(q−|S|))d(q−|S|)(q−3d)/21q−dd−1q(q−d)/2q24dq2(q−3d)/2 1q−dd−1q(q−d)/2,as required.We have taken into account that(q−3d)/2 0by our supposition.The proof of the lemma is complete.Lemma3.If d<e−23eq then we have the following estimate:d =21−1(q−d)/2·qd 2d−1(d−1)q2.Proof.The lemma is trivial for d=1.Consider d>1and define the functionf( )=1−1(q−d)/2·qd.Let d=uq,u<e−23e.Taking into account(6),we havef( +1)/f( )=−1(q−d)/2+1dq+1q−1S.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–3735<−1(1−3u)q/2q<exp−(1−3u)q2q.By our supposition,(1−3u)/2>1/e.Denoting v=q/ we havef( +1)/f( )<ve−v/e.But,by(6),ve−v/e 1for any v.Therefore,f( +1)/f( )<1.Thus,the function f( )is decreasing for2 d.Hence,d =21−1(q−d)/2·qd=d=2f( ) (d−1)f(2).This implies the statement of Lemma3. We are in the condition to prove Theorem2.Proof of Theorem2.In view of Lemma2(recall that d<e−23e q)and Lemma1,theabsolute value of the right-hand side of(9)isS⊆F q1q dqdq2(q+d)/2 dqq−d(q−d)/2⎛⎝q+d=21−1(q−d)/2·qd⎞⎠.By Lemma3,we obtain that the above is<2qq dqdq2(q+d)/2 dqq−d(q−d)/22d dq2=2d dq2+q−d qd2dq−d(q−d)/2.(11)This concludes the proof by using(9).4.Range of uniformity(proof of Corollary2)In this last section we want to establish how large d can be in order for the asymptotic formula N q,d∼q!/q d to hold.36S.Konyagin,F .Pappalardi /Finite Fields and Their Applications 12(2006)26–37Since 0< ,we can use Theorem 2.Substitute d = q ( 0)in (11)and note that in order to have an asymptotic formula it is enough to verify that2 q q 3+q qq 2 1− q(1− )/2=o(q !)(q →∞).(12)From the Stirling formula (7),qq > 1 (1− )1− q ,we obtain that (12)is satisfied uniformly over 0if we havesup ∈(0, 0]g( )<−1,(13)whereg( )=log 2 −log (1− )1− +log ⎛⎝ 2 1−1− 2⎞⎠.It is easy to see that the functionslog 2 ,−log (1− )1− ,log ⎛⎝ 21− 1− 2⎞⎠are increasing on (0,1/3].Hence,g is also increasing,and (13)follows from the inequality g( 0)<−1.This completes the proof of the corollary.In a future paper we are planning to adopt the method of Theorem 2to prove an asymptotic formula for N q (k 1,...,k d )with arbitrary k 1,...,k d where d is fixed or grows slowly as q →∞.It would be of interest to enumerate permutation polynomials with degree approx-imately √q .Unfortunately our approach cannot reach this range since we know that for q odd there are no permutation polynomials of degree (q −1)/2(see[3,Corollary 7.5]).AcknowledgmentsThe authors are grateful to the referee for a careful reading of the paper.Due to his (or her)remarks,a series of shortcomings have been corrected.Also,we would like toS.Konyagin,F.Pappalardi/Finite Fields and Their Applications12(2006)26–3737 thank Igor Shparlinski and Mike Zieve for useful comments on thefirst draft of this paper.The project was performed during the visit of thefirst author to the UniversitàRoma Tre in April2003supported in part by G.N.S.A.G.A.from Istituto Nazionale di Alta Matematica.References[1]P.Das,The number of permutation polynomials of a given degree over afinitefield,Finite FieldsAppl.8(2002)478–490.[2]S.Konyagin,F.Pappalardi,Enumerating permutation polynomials overfinitefields by degree,FiniteFields Appl.8(2002)548–553.[3]R.Lidl,H.Niederreiter,Finite Fields,second ed.,Cambridge University Press,Cambridge,1997.。
